1. Introduction
Industry 4.0, synonymously known as cyber–physical production systems (CPPSs), is a concept formed in 2011 at the Hannover Fair to describe how cyber–physical systems (CPSs) can be applied within production and manufacturing industries with enabled automation [
1,
2,
3,
4]. From the inception of the visionary notion specifically for factories and large-scale enterprises, CPSs’ reach have extended beyond production enterprises linking the Industry 4.0 concept with aspects of smart city initiatives [
3,
4]. Smart cities have evolved and transformed over the past two decades becoming deeply integrated within the society facilitating an interconnected digital environment [
3,
4,
5]. The estimated growth of the urban population is estimated to reach 5 billion by 2030 globally [
6]. A variety of definitions for the term “smart city” [
7,
8,
9,
10,
11,
12], its sectors and components [
3,
13,
14,
15,
16,
17], the variants [
8] and concepts of the term “smart” [
6,
14,
18,
19,
20,
21] have been suggested. The description of smart cities is heterogeneous and commonly agreed facets converge sustainability, ICT-based technology and community needs. Therefore, in this study, we consider the smart city as an urban space using technology and resources innovatively, intelligently and securely to improve the lives of its citizens focusing on the spectrum of attributes that improve the cyber resilience of smart cities.
A key component of smart cities, CPSs can be described as smart, embedded and networked systems within production systems [
22]; a tangible element that is not completely controlled by an automated system and a cyber element that focuses on the digital information form CPS entities capable of autonomous interaction regardless of human supervision [
23]. Furthermore, these complex and growing networks of connected objects incorporate human-users and form complex cyber–physical–natural (CPN) ecosystems interrelating systems, software, people and services. As such, a problem within this complex cyberspace, including cybersecurity challenges, can have a cascading effect on the entirety of the ecosystem [
24,
25].
The motivation and tactics of the cyber threats landscape shifted from individuals hobby hacking to gain kudos amongst their peers toward well-organised cybercrime [
26,
27,
28]. The motivations are often intensified by the possibilities to gain sensitive information, which can be used in subsequent attacks including cyberattacks against industrial control systems (ICSs) or critical national infrastructure (CNI). Verizon reported in their 2016 Data Breach Investigation Report the outcome of the investigation of 500 cybersecurity incidents in over 40 countries. In 89% of the cases, the key motives reported were described as “financial” and “espionage” fixated on targets including manufacturing, healthcare, utilities and public services by organised crime and state-affiliated groups. Many of these attacks had a secondary motive to aid an intrusion of another target [
29,
30]. This class of attacks known as advanced persistent threats (APTs) characterise a well-resourced group of attackers that carry out multi-stage and often multi-year persistent targeted campaigns. Traditional incident response (IR) methods fail in mitigating APTs because they assume successful intrusion before IR takes place. A kill chain model enables one to map such campaigns, identify patterns linking individual intrusions and through an iterative intelligence gathering enables the development of a resilient intelligence-driven mitigation approach [
31]. In 2018, although the key motives remained largely unchanged, the most noteworthy attack vectors reported by the European Union Agency for Network and Information Security (ENISA) included malicious attachments, URLs in emails targeting the human element, web browser-based malicious scripts, malvertising, exploit kits and password reuse or weak service credentials in Internet exposed assets [
26]. In 2019, law enforcement agencies responded to more attacks on CNI than we ever saw before; this trend was highlighted as a key emerging threat by Europol [
32]. CNI such as smart energy, water or transport are complex, large-scale interconnected CPSs converging physical and cyber domains and utilise geographically dispersed ubiquitous distribution networks, which extend beyond the boundary of a smart city, often across national borders and legal jurisdictions.
The rise of cybercrime has been greatly facilitated by the proliferation of modern advanced electronic communication technologies and the integration of IoT with physical systems [
17,
28,
33]. High profile cyberattacks on ICSs have been well reported for some years, such as the Stuxnet malware targeting the Iranian nuclear plant [
34], the attack on the Ukrainian power grid [
35] or Norsk Hydro, a renewable energy supplier and the world’s largest aluminium producer, which was compromised by the LockerGoga ransomware [
32]. In case of a successful cyberattack, the disruption of power, water or fuel supplies to these facilities could have a potentially serious socio-economic impact including civilian unrest; however, consequences could be more profound. For example, in the widely reported Kemuri Water Company attack, the mixture of chemicals used to treat a water plant was altered. In this attack, the sensors responsible for monitoring the water treatment plants were compromised [
29]. Due to the distributed nature and heterogeneity of CPSs, human interactions and the omnipresence of the underpinning technologies create hugely diverse attack vectors which increase the threat of cyberattacks on critical systems.
Comparatively, smart cities, smart healthcare and smart homes are in the earlier stages of development with several evolving projects including initiatives to improve the wellbeing of elderly people through early changes detection [
36] or application of digital forensics as a service in the context of smart homes [
37]. Furthermore, connected appliances and app-based utility management will become the norm in connected homes [
38] whilst automated congestion control, smart traffic lights or parking [
39,
40] will be part of smart cities’ digitalization projects [
14]. The cyber challenges in these smart sectors differ but the effect could be just as profound. For example, the ransomware attack against the San Francisco Municipal Transportation Agency’s transport service only resulted in financial impact [
41]. Accidents caused by cyberattacks including GPS ghosting, hijacking command and control systems, ransomware or attacks targeted at sensors, actuators or controllers could result in serious accidents and increase the pressure on healthcare systems. Digital transformation utilising mobile and emerging technologies such as artificial-intelligence (AI)-enabled networked medical devices or wearable health sensors are identified as enablers for healthcare organisations. However, healthcare does not escape cyberattacks as learnt from the WannaCry incident in May 2017 affecting over 300,000 computers, some of which belonged to 80 National Health Service (NHS) Trusts across the UK [
26,
32,
42].
Due to the attacks becoming more sophisticated and targeted, the countermeasures also need consistency and coordination [
5,
26,
28,
32]. Therefore, a new paradigm must address cyber threats and cybercrime. Formulating cyber resilience to counter cybersecurity threats is required to resist cyberattacks and continue to function effectively under adverse conditions [
43]. Accepting that not all cyberattacks are avoidable and computer-related crime is on the increase, the IR becomes an important component of CPS security management [
32] including the need for digital evidence (DE). Forensic DE gathering must be carried out without compromising the integrity and authenticity of the DE to ensure admissibility in a court of law [
44]. Therefore, the cybersecurity paradigm needs to shift to withstand cyberattacks, to function effectively under adverse conditions and support digital forensic investigations by producing DE that is admissible in the court of law. Collaborative practice and interdisciplinary approaches across smart sectors based on threat information sharing could increase situational awareness and help deal with potential threats or incidents more effectively.
Although CPS-related research is an active area, there seems to be substantially less empirical research available on frameworks and systems that address CPS in smart cities. For example, the following study [
45] defines its framework as a risk-based approach to reducing cybersecurity risk consisting of three tiers: core, profile and implementation. Another study [
46] defines a CPS framework as activities and outputs that support CPS engineering, which provides not a one-size-fits-all approach but a flexible way to address cybersecurity across the physical, cyber and people dimensions. Therefore, to make a meaningful contribution, we use a broad definition for frameworks as a common carefully designed organising structure of multiple approaches [
47,
48,
49]. Furthermore, systems described by the National Institute of Standards and Technology (NIST) as a combined set of complex and coherent elements that constitute a use-case [
46] can operate in different smart city sectors creating highly complex systems of systems. Systems can be represented by scientific modelling to describe hypothetical behaviour of phenomena that are challenging to observe directly. To help discover contributions in the literature of the specific research area we include systems to gain a deeper understanding of addressing support for cyber resilience across the physical, cyber and people dimensions in cross-sector applications within smart cities [
50,
51].
Specifically, concerning frameworks and systems that address cyber resilience and modern digital forensics and incident response (DFIR), there appears to be lack of available systematic literature review (SLR) based on recognised methodology, comprehensive protocols and quality assessment. For instance, to identify how CPS-related frameworks and systems support cyber resilience and to determine the support for modern DFIR in smart cities it is important to conclude what research has been published and systematically review relevant and available studies. Therefore, one of the key objectives of this study is to identify the current gaps in this research area. Overarchingly, the focus of this paper is on reported empirical evidence in existing literature concerning cyber resilience and DFIR support in CPSs across smart city sectors. Traditionally, “resilience” in a mechanical context was the materials’ resistance to shock, in the conventional networking context resilience focused on fault tolerance; however, the scope of this term extends to the cybersecurity discipline. In this study, we consider cyber resilience as the ability of the frameworks addressing smart cities to resist cyberattacks across the physical and digital domains regardless of an external or insider attack [
43,
52,
53,
54].
A small number of SLR studies in the realm of CPS have been published. These are outlined to examine the difference between the authors’ focus on topics and our research. The author of [
55] performed an SLR focusing on smart grid and related cybersecurity. In this study, the author presents results aimed at addressing cybersecurity by identifying all standards which define cybersecurity requirements for smart grids and reviews applicable standards and guidelines. In reference [
56], the authors provide analysis to address cybersecurity issues in an Industry 4.0 context and focus on the physical Internet-connected systems. The authors concentrated on four areas, the definition of concepts relevant to Industry 4.0 and cybersecurity, the industrial focus, the characterization of cybersecurity and the management of the cybersecurity issues. Authors in reference [
57] presented their SLR findings concerning smart cities focusing on instrumented, interconnected and intelligent systems investigating four areas including security. One of the authors’ conclusions was that little was mentioned in the newly emerging security and privacy challenges. Although the studies into this growing area of research provide valuable knowledge consolidation, they answer questions about the wider use of CPS and related cybersecurity. No other SLR on this research topic was found by the authors during the preparation of the study. The focus of our SLR remains specifically on CPS-related cyber resilience and modern DFIR informed by cyber threat intelligence (CTI) to strengthen and accelerate the cyber defence in smart cities.
Narrative reviews were found to focus on various Internet of Things (IoT) aspects and applications addressing challenges, threats and solutions. For example, the authors in reference [
58] provided a brief review of IoT concepts and models. The paper focused on the IoT network model and related modelling challenges from the interconnections’ perspective and briefly discussed the concept of interdependent infrastructure resilience. Another recent study investigated the autonomy, integration and level of intelligence in emerging applications related to CPSs across a range of application domains in smart cities [
59] including big data challenges and data and communication security. Further, the authors explored the intelligence and interconnectivity of systems into a shared environment from a simulation perspective. Interestingly, the study concluded that the security of collected data and distributed systems are a persistent challenge that must be continually addressed. They expressed the need to design systems with agility to react to the changing security landscape. A study focusing on the IoT from the edge computing perspective was published in reference [
60]. The focus of this study was on improving IoT networks’ performance utilising edge computing exploring the relevant confidentiality, integrity and availability strategies. Another survey [
61] examined the integration of the IoT and fog/edge computing. The paper clarified the difference between CPSs and the IoT and investigated the relationships and issues affecting the IoT and fog/edge computing; however, the paper’s approach remained high-level and general. All the previous studies address broader aspects related to the IoT, but do not specifically investigate CPSs with a focus on improving cyber resilience, the value of CTI- or CPS-specific DFIR support in smart cities. The field of research related to CPSs is still emerging, but the advancement is accelerating. Therefore, a comprehensive SLR is required focusing on ways that current CPSs deal with cyber resilience and DFIR to guide future research.
This paper’s main aim is to provide a systematic literature review (SLR) that consolidates primary studies’ research investigating what empirical evidence has been reported for existing frameworks and systems that address CPS cyber resilience in smart cities. Second, we investigate how current CPS applications address modern DFIR. Finally, we explore existing integration proposals or applications that leverage CPSs across smart city sectors to improve digital forensics. We critically examine existing research and use the insights to conclude with suggestions for future research. The remainder of this paper covers our methodology in
Section 2 which also discusses the research questions and the protocol including the data extraction strategy.
Section 3 contains the results, analysis and key findings from the included primary studies followed by a discussion in
Section 4. Finally, the conclusion and future research suggestions are in
Section 5.
2. Materials and Methods
The aim of this study was achieved with an evidence-based systematic literature review (SLR) as the means to objectively address our research questions. The protocol is based on the SLR guidelines for the computer engineering discipline proposed by Kitchenham and Charters [
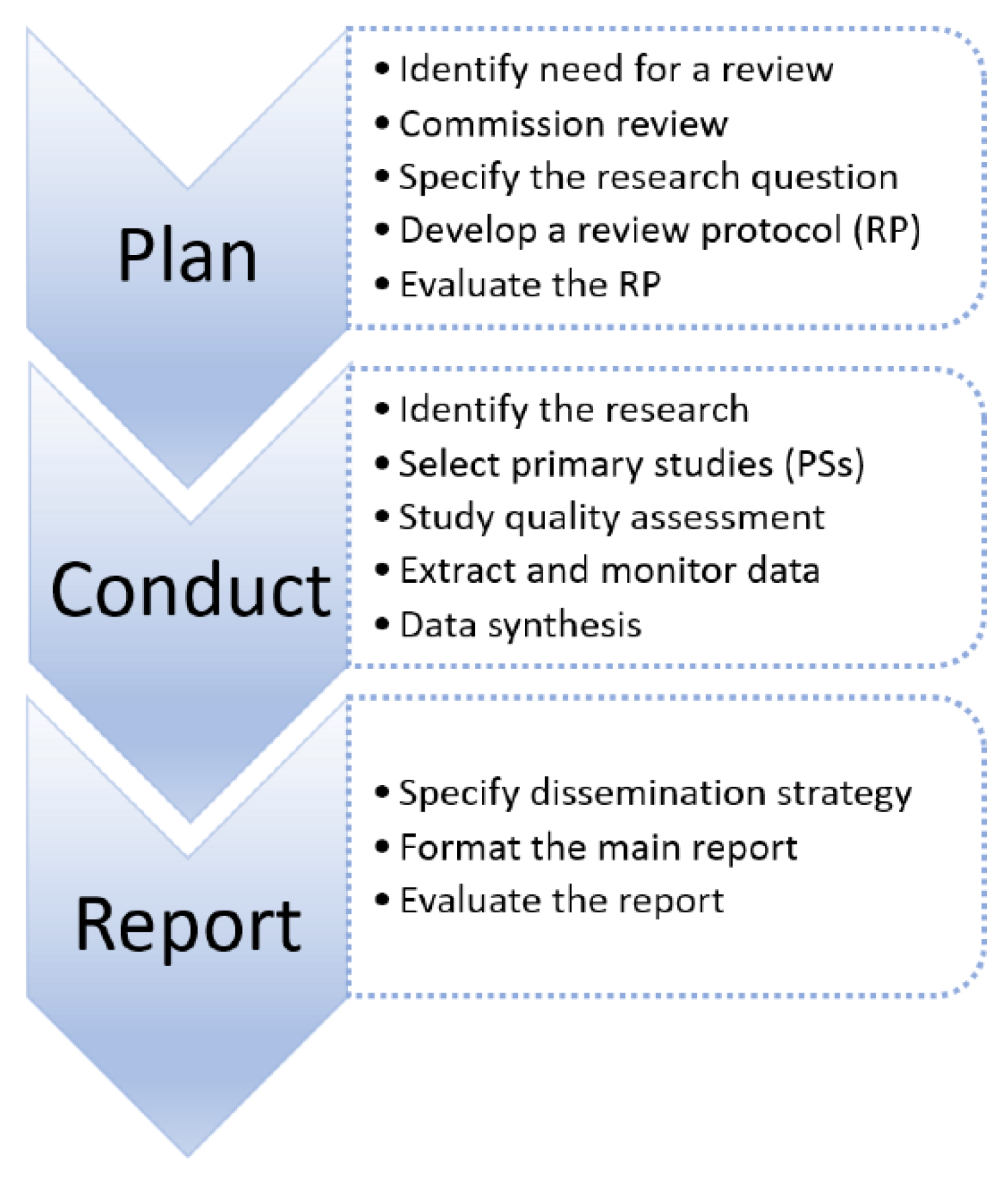
62]. These guidelines, which aim to present a rigorous and credible methodology, are based on three key phases: planning, conducting and reporting, as demonstrated in
Figure 1. We demonstrate the discreet activities in each phase in the subsequent sections to allow replication of findings. Summarily, the core aspects of the systematic review protocol, the key contributions and the research questions are identified within the planning phase. The conducting phase consists of identifying the search strategy including the selection criteria for the primary studies, selection procedure, the search strings and the quality assessment criteria. This phase involves the development of the data extraction strategy, data synthesis and critical analysis. Finally, the information dissemination strategy is considered in the reporting phase. Each phase of the SLR is conducted iteratively to ensure a comprehensive evaluation. To maintain objectivity and mitigate bias, each phase was subject to a review and an approval process between the team before moving onto the next phase.
2.1. Research Questions and Rationale
The main aim of this research is to identify and present scientific evidence of gaps in current research and help inform the direction for further research. The aim can be achieved by answering the following three research questions (RQs):
RQ1: How do existing frameworks and systems that address CPSs in smart cities support cyber resilience and what empirical evidence has been reported? Use cases and application of CPSs have diversified, and complexities of these ecosystems have evolved. In addition to frameworks, we investigate how complex systems support cyber resilience identifying commonalities. Within the many diverse definitions used in existing studies addressing smart cities [
7,
8,
9,
10,
11,
12] and the numerous terminologies used in literature to describe frameworks and systems [
51,
52,
63,
64,
65], providing an answer to RQ1 helps us conclude a list of all existing and relevant frameworks and systems that address CPSs in smart cities supporting cyber resilience as defined by the scope of this SLR.
RQ2: How do the identified frameworks and systems in smart cities address modern digital forensics and incident response (DFIR)? Application of DFIR in the context of a smart city is a new field of study [
37]. Whilst the research focuses on the applications of IoT-enabled CPSs, smart cities are found to be vulnerable to cyberattacks [
40]. It is acknowledged that DFIR methodologies are lacking in smart city sectors [
17,
66] and research suggests that DFIR faces more challenges in smart cities than other forms of digital breach investigations [
67]. However, apart from the complexity to the cyberspace, the IoT enabled CPSs to create opportunities to facilitate modern DFIR [
44]. RQ2 investigates how the components of the CPS frameworks help address modern DFIR.
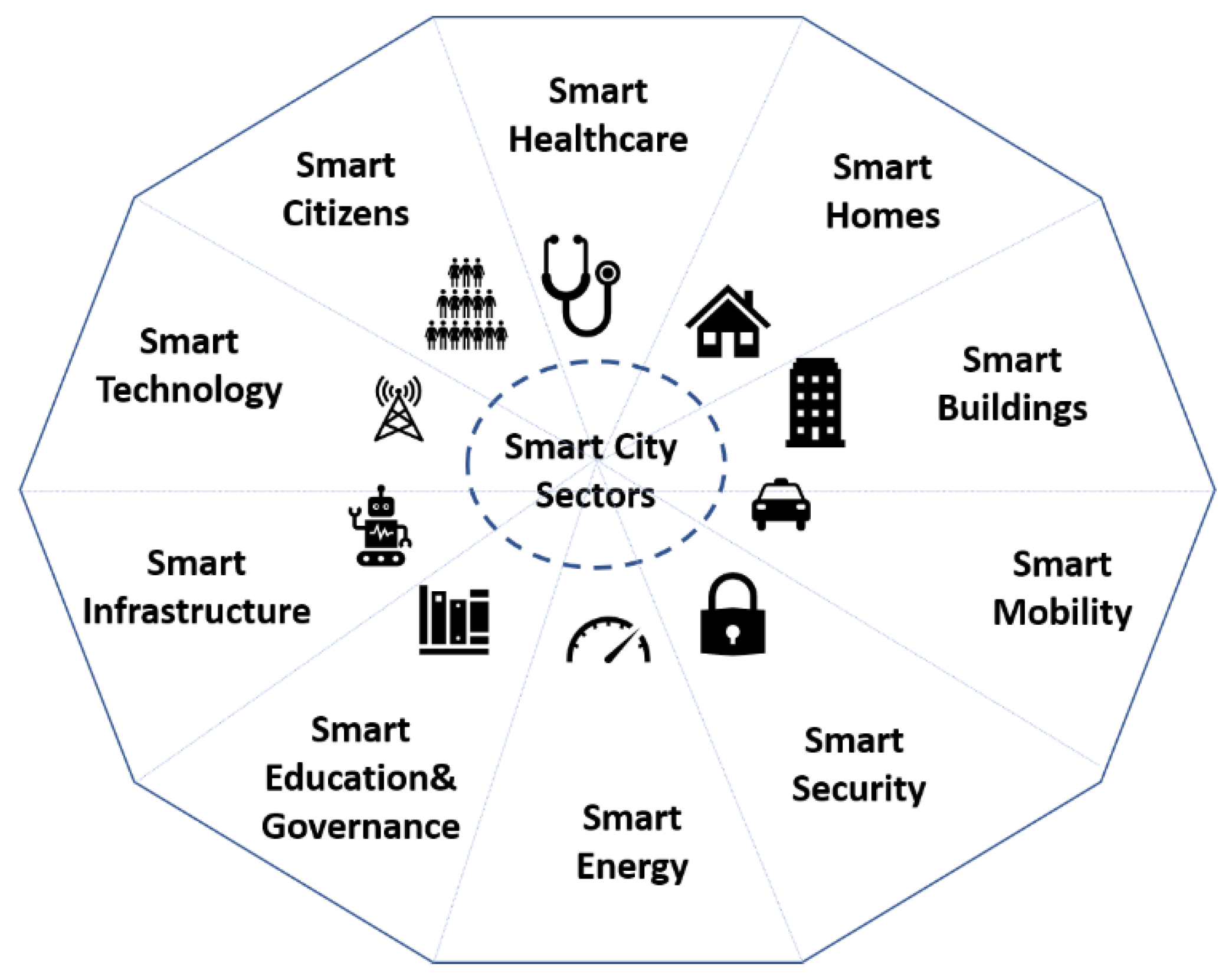
RQ3: What are the current cross-sector proposals or applications in smart cities that attempt to utilise interactions in CPSs for the purpose of improving DFIR? This RQ explores the transferable solutions and cross-sector interactions between smart buildings, smart homes, smart healthcare, smart energy and others as illustrated in
Figure 2. Despite digitalisation in smart cities, information security strategies are limited to the sector boundary with little evidence of cross-sector information security practice sharing [
28]. We draw on the use of the term of cross-sector partnerships in reference [
68] as intensive and long-term interactions between organisations from at least two sectors such as business and healthcare. Throughout this study, cross-sector collaborations are used as interactions to adopt, share or coordinate cyber defence practice between at least two different smart city sectors. To address the existing and emerging cyberattacks, transferable and innovative solutions should emerge from individual sectors within a smart environment to support modern digital forensics [
28,
68]. RQ1, RQ2 and RQ3 help uncover key themes and gaps in current literature and suggestions for future research direction.
The PICOC (population, intervention, comparison, outcomes, context) criteria as demonstrated in
Table 1 is used from an engineering point of view, as proposed by Kitchenham and Charters [
62] to frame the research questions effectively.
2.2. Primary Studies’ Data Sources and the Search Strategy
Digital library (DL) sources for computer science research publications were used. To help answer the RQs, keywords representative of the research topic were pre-defined and a search string was constructed using Boolean operators, key terms and synonyms to fetch all relevant studies. The Boolean operators were limited to AND and OR. The following search string was used:
(‘Cyber Physical Systems’ OR ‘Cyber-Physical Systems’ OR ‘CPS’ OR ‘Cyber Physical Object’ OR ‘CPO’ OR ‘smart device’ OR ‘IoT device’) AND (‘cybersecurity’ OR ‘cybersecurity’ OR ‘cyber-resilience’ OR ‘resilience’) AND (‘smart cities’ OR ‘smart city’) AND (‘model’ OR ‘modeling’ OR ‘technique’ OR ‘framework’ OR ‘information modeling’ OR ‘modeling technique’ OR ‘analytical modeling’ OR ‘reference architecture’ OR ‘reference model’ OR ‘Security Solutions’ OR ‘IoT Architecture’).
The DLs used in this SLR were the Institute of Electrical and Electronics Engineers (IEEE), Association of Computing Machinery Digital Library (ACM DL), Science Direct, Web of Knowledge and Scopus. The search string was aligned to the built-in options within the DLs’ search engines to filter the results. Where possible, searches were performed to match the search string from the title, abstract, keywords, and the full text. The search of the specified DLs concluded by 5 April 2019 taking into consideration all studies returned by the defined search string published to that date. In addition to the set of studies produced through the search of the DLs, we applied a snowballing approach in our search strategy, as outlined by Wohlin [
69], which produced a further set of relevant studies. This was a manual process applied to the studies collected by the pre-identified search criteria until no further studies met the inclusion criteria. Subsequent to identifying studies from the specific data sources using the defined search string, the rest of the protocol outlined in
Section 2.3,
Section 2.4,
Section 2.5,
Section 2.6 and
Section 2.7 was applied to the studies identified by the initial search.
2.3. Selection Criteria
Rigorous inclusion and exclusion criteria, as defined in
Table 2, were applied to the produced set of studies from the DLs to ascertain that only relevant studies are retained in response to the research questions.
Included studies must satisfy all inclusion criteria. I.e., they must be primary, peer-reviewed, written in English and contain appropriate information on new applications or development of an existing mechanism for cyber resilience, modern DFIR or framework in CPSs, providing empirical findings.
2.4. Selection Process
The selection process consisted of three key phases as demonstrated in
Figure 3. The authors have critically reviewed this.
Phase 0—Keyword Filtering. During this phase, the identified search string was applied to each of the DLs utilised returning a combined result of 441 research studies. These studies were passed through to the next phase.
Phase 1—Title, Indexing Keywords, Abstract, and Conclusion Filtering. Following the initial keyword filtering, in phase 0, the titles, indexing keywords, abstracts and conclusion were scrutinised against the inclusion criteria. Studies showing relevance to the research topic were included in the next phase. In this phase, 319 studies were excluded and 122 were put through to the final phase.
Phase 2—
Full-Text Filtering. The full texts of the 122 studies were read. After applying the selection criteria in this final phase, some studies were excluded for several reasons. For example, references [
37,
70,
71] did not include an empirical study, references [
72,
73,
74] at the time of review were not peer-reviewed publications, reference [
75] is not an English language study, reference [
76] is a poster, the focuses of references [
77,
78,
79] were not specific to CPS cyber resilience or modern DFIR. Additionally, 10 studies were identified as duplicates and excluded from the final selection list. Snowballing identified an additional 159 studies. After applying the selection process, these studies were reduced to 19 after excluding nine duplicate studies and three PhD theses.
The final list of primary studies included in this SLR resulted in 52 articles, as shown in
Figure 3.
2.5. Quality Assessment
Motivated by the guidance in reference [
62], a checklist was developed according to references [
80,
81] to make sure all included studies satisfy quality assessment (QA) criteria. This evidence-based approach assesses the validity of experimental data and reduces bias. The following QA criteria were applied:
Phase 1: CPS. The study must be focused predominantly on CPS security or the application of the CPS framework to a specific cyber resilience problem and appropriately documented.
Phase 2: Context. The context of the study must be provided in sufficient detail to accurately interpret the research.
Phase 3: Detail. The framework details are critical to answering RQ1 and RQ2. Sufficient detail about the approach to build the framework and comparison with other approaches must be presented clearly in assisting to answer RQ3.
Phase 4: Data. Sufficient detail about the type of training and test data identified and how the data was acquired, measured and reported must be provided clearly to determine the accuracy of the results reported.
2.6. Validation Process
A random set of 30 primary studies from the pool of studies were selected and had the inclusion/exclusion criteria re-applied to validate the effectiveness and the objectivity of the process application. A further 30 random primary studies were selected from the pool of studies and had the QA criteria applied to validate the effectiveness and the application of the quality assessment process.
2.7. Data Extraction Strategy
The data extraction was applied to the final 52 primary studies. Initially, the process and format were trialled on a subset of studies before extending the process to all included studies. The data were categorized, stored in a spreadsheet and tabulated using the following characteristics.
Context: year of publication, type of article, application of the study, sector, model type and security approach.
Qualitative data: were recorded including the conclusion and future research directions provided by the authors.
Quantitative data: experiment observations were noted including the technique and dataset source.
To conclude, the protocol used in this SLR process, which is based on Kitchenham and Charters [
62] guidelines, was rigorously applied and documented to objectively address the research questions. The resulting set of primary studies after applying the protocol are summarised in
Figure 3. Therefore, this SLR consolidates previous research within the defined scope; however the methodology used can be applied iteratively to studies beyond this SLR’s defined scope as an extension and update of literature reviews to further expand the scientific body of knowledge.
4. Discussion
Our analysis revealed that in the last decade, CPSs have emerged as a new paradigm and as a result of the increased growth, complexity and heterogeneity of these infrastructures [
14,
82], the volume and the variety of vulnerabilities and attacks have evolved highlighting the need for defence mechanisms [
147], need for cyber resilience and capability to support DFIR [
26,
29,
30,
33]. In this paper, the analysis of the primary studies supports our assertion that CPS-related cyber resilience and DFIR are active research domains. As has been noted in our results analysis, several empirical research studies have focused on CPS-related cyber resilience and DFIR. For example,
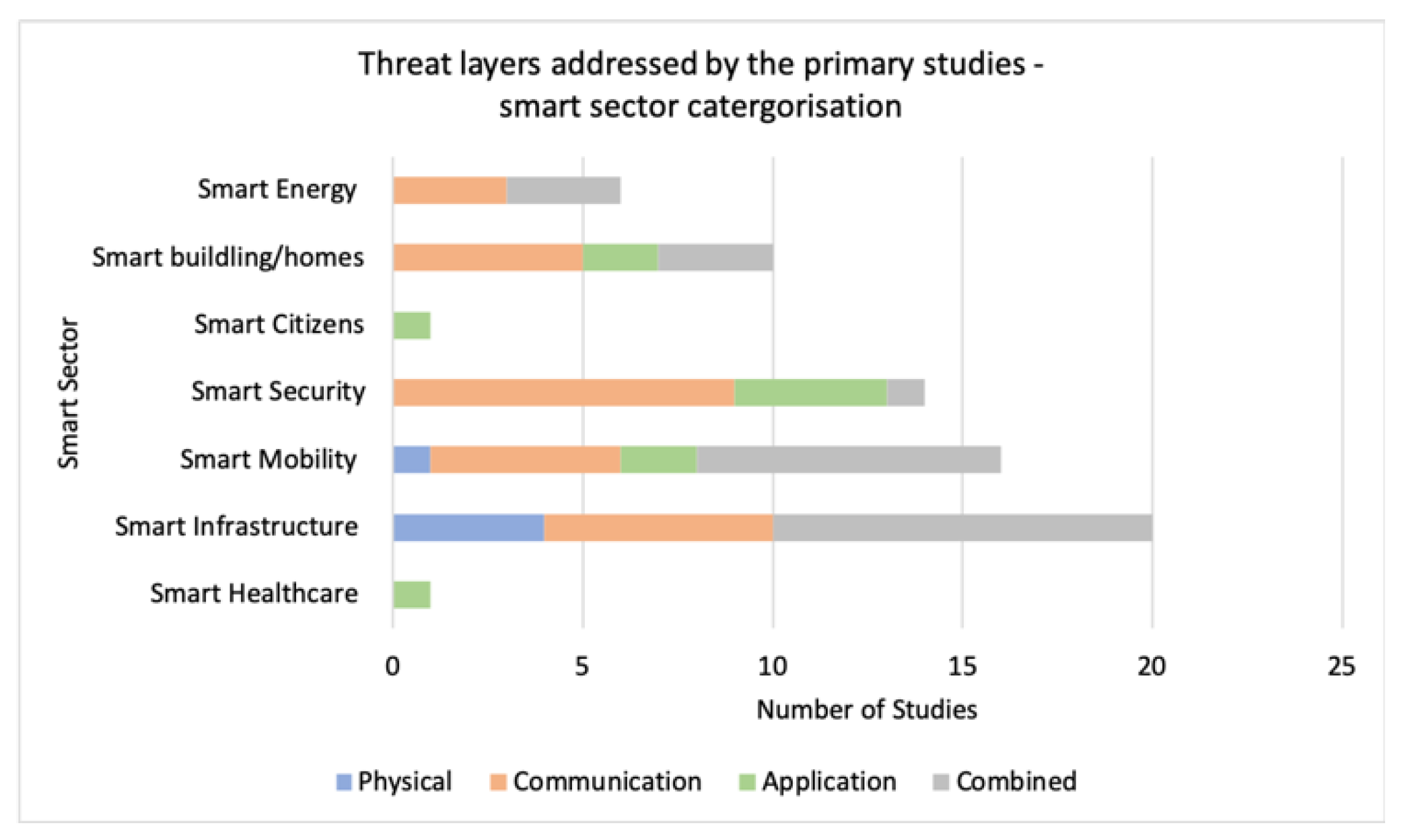
Table 5 summarises primary studies which focused on aspects of cyber resilience across a number of different smart sectors, whilst a summary of primary studies with focus on DFIR’s key stages in smart cities is shown in
Table 8. In fact, several empirical research papers studied presented ways to solve real problems [
37,
122,
135,
148]. However, despite the importance of cyber resilience and support for DFIR in smart cities, these aspects have not been extensively considered by researchers in the context of CPSs. As we already noted,
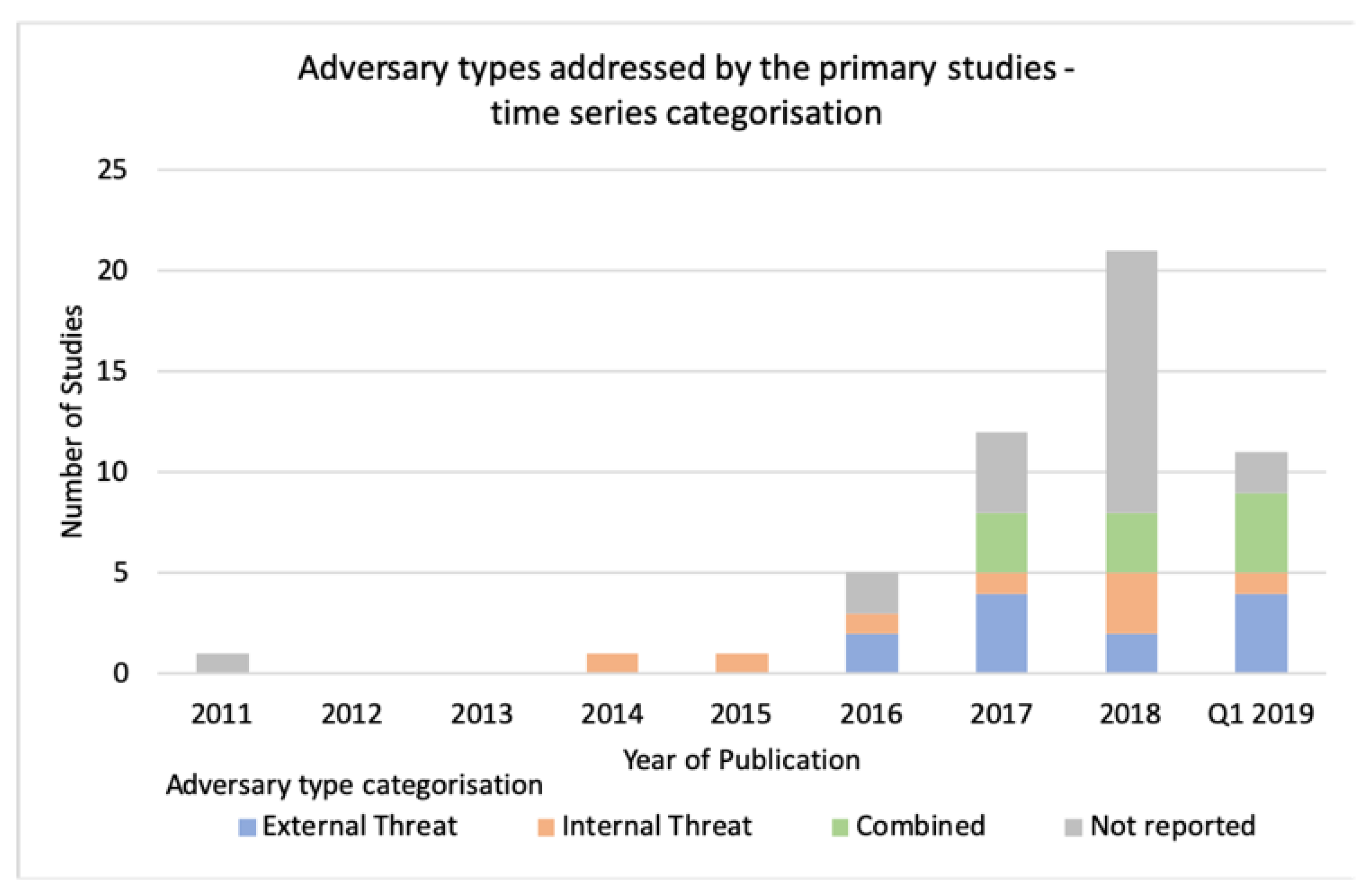
Figure 7 demonstrates a different level of scientific interest in adversary type research whilst
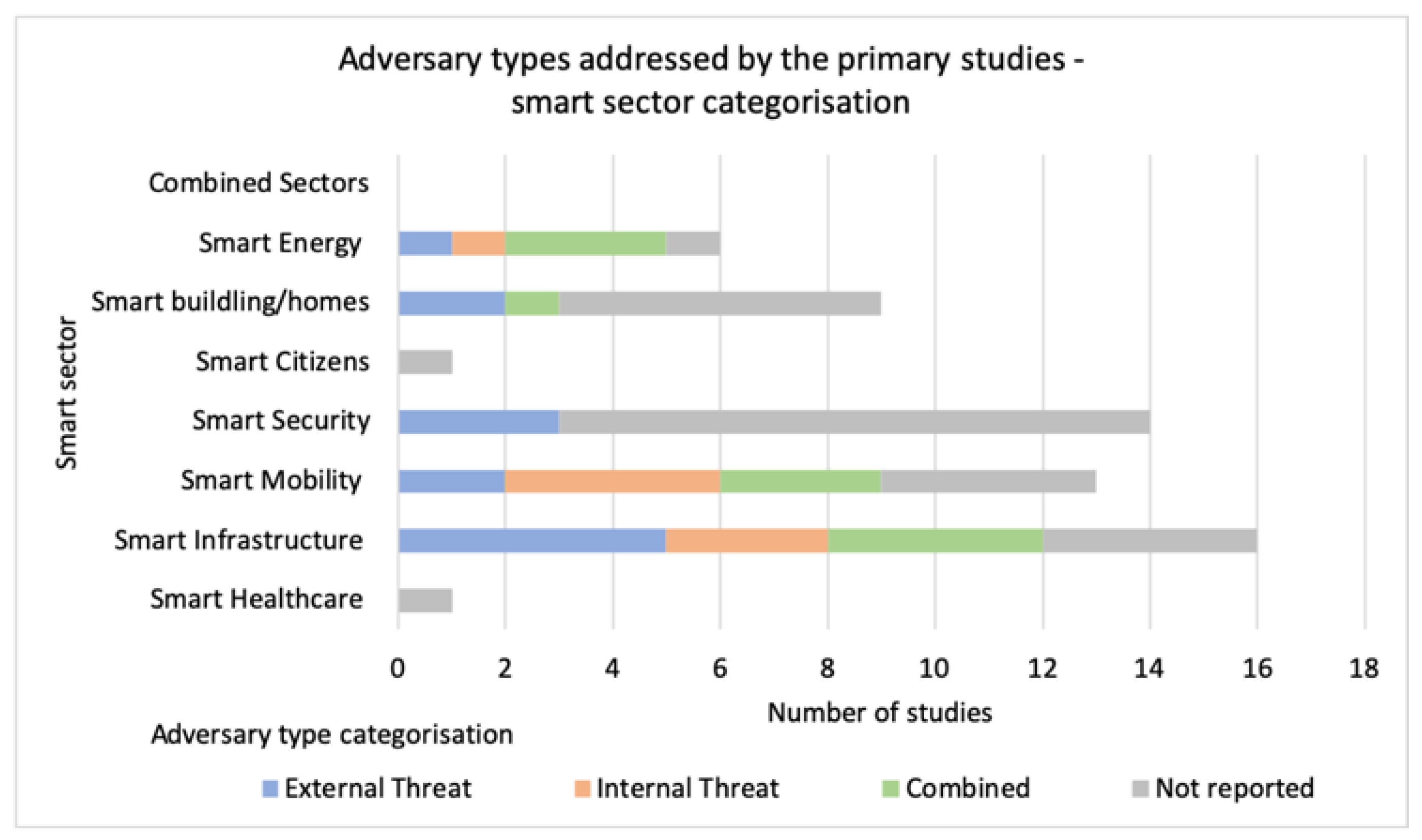
Figure 8 further analyses the phenomena and presents the gaps across specific smart sectors. Furthermore, summarised in
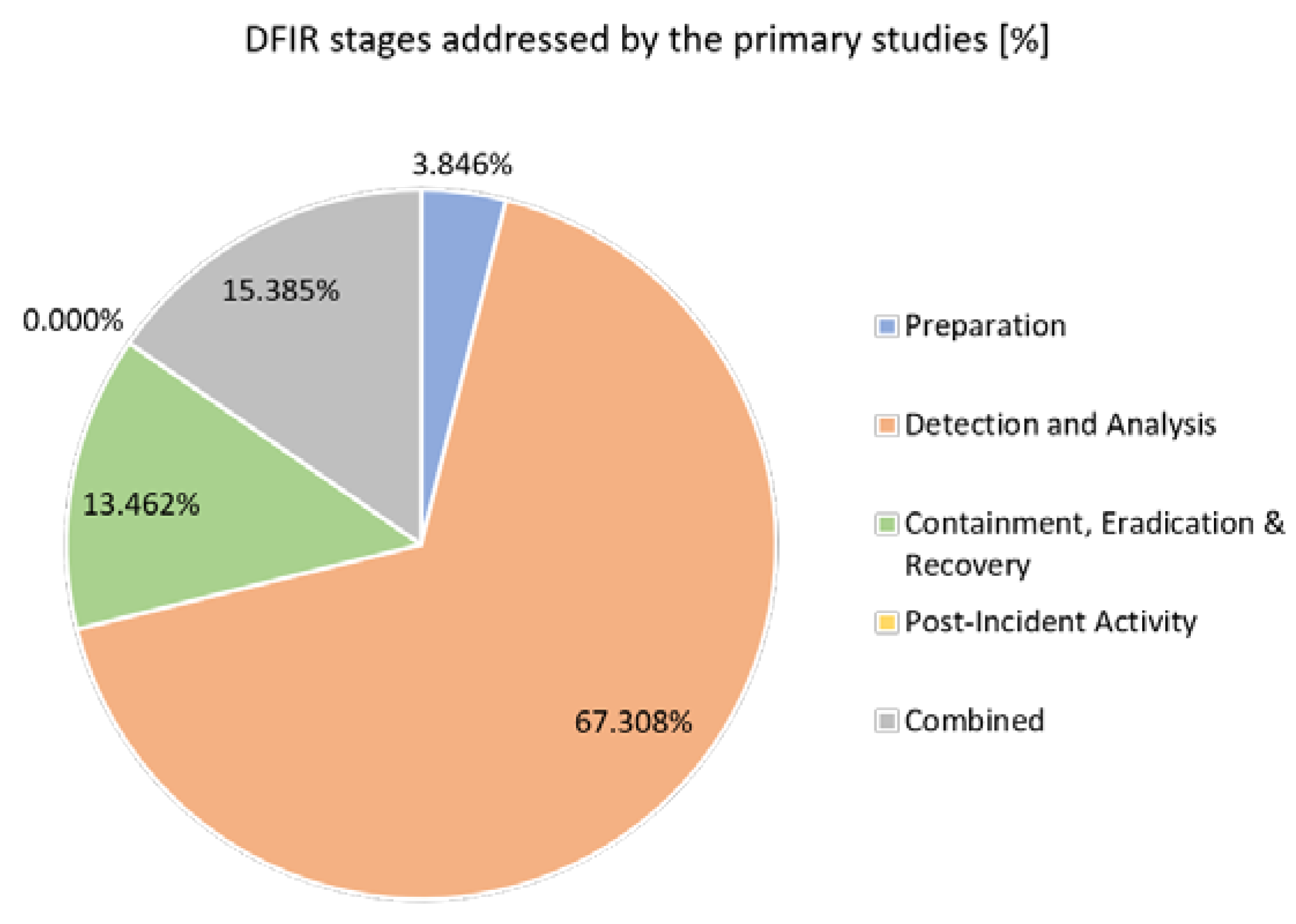
Figure 9 and
Figure 10, the analysis revealed differences in scientific interest in the DFIR stages with further variations across smart sectors. This poses an important question as to the reason for those differences. However, it is not the aim of this paper to provide the answer but to identify the gaps and present some open challenges and findings that can be used as future research directions [
107,
149].
The initial keyword searches highlighted that although there is an active research interest in the security of CPSs, frameworks addressing CPS cyber resilience, support for DFIR and their applications for developing cross-smart sector opportunities for collaborative cyber-defence practices are still emerging. Plans for cross-sector applications and diversifying the research to other areas of smart city sectors is often part of the future research direction [
99,
114,
134].
The search criteria identified several non-empirical studies which provide concepts or theoretical bases to problem solutions and survey type studies that focused on consolidating the body of research related to our research scope aspects [
21,
55,
56,
57,
58,
59,
61,
150]. Whilst survey type studies are important, enable knowledge consolidation and identify areas of future research directions, several of the selected primary studies were empirical and provided practical solutions to a range of challenges related to cyber resilience and support for DFIR using innovative techniques.
The validation of the proposed solutions of the primary studies within the scope of our research inevitably always depends on carrying out cyberattacks or otherwise adversely impacting the infrastructure. Therefore, any validation must be carried out in a strictly controlled environment to avoid accidental disruption to CNI or compromise to data privacy. Validation can be economically challenging and requires funding to facilitate validations using a realistic simulation environment often involving physical infrastructure [
47,
51,
64,
109,
119,
131,
137,
142]. Almost three-quarters of the primary studies reported funding supported by research grants, defence or governmental sectors. Notable exceptions included only two primary studies which did not report funding and validated their proposal using infrastructure-based simulation utilising a smart home [
129] and smart water system [
116] infrastructures. In their current states, mainstream systems may not be equipped with infrastructure to facilitate such testing and would require significant change. Therefore, funding could be a contributing factor to empirical research in this field of study.
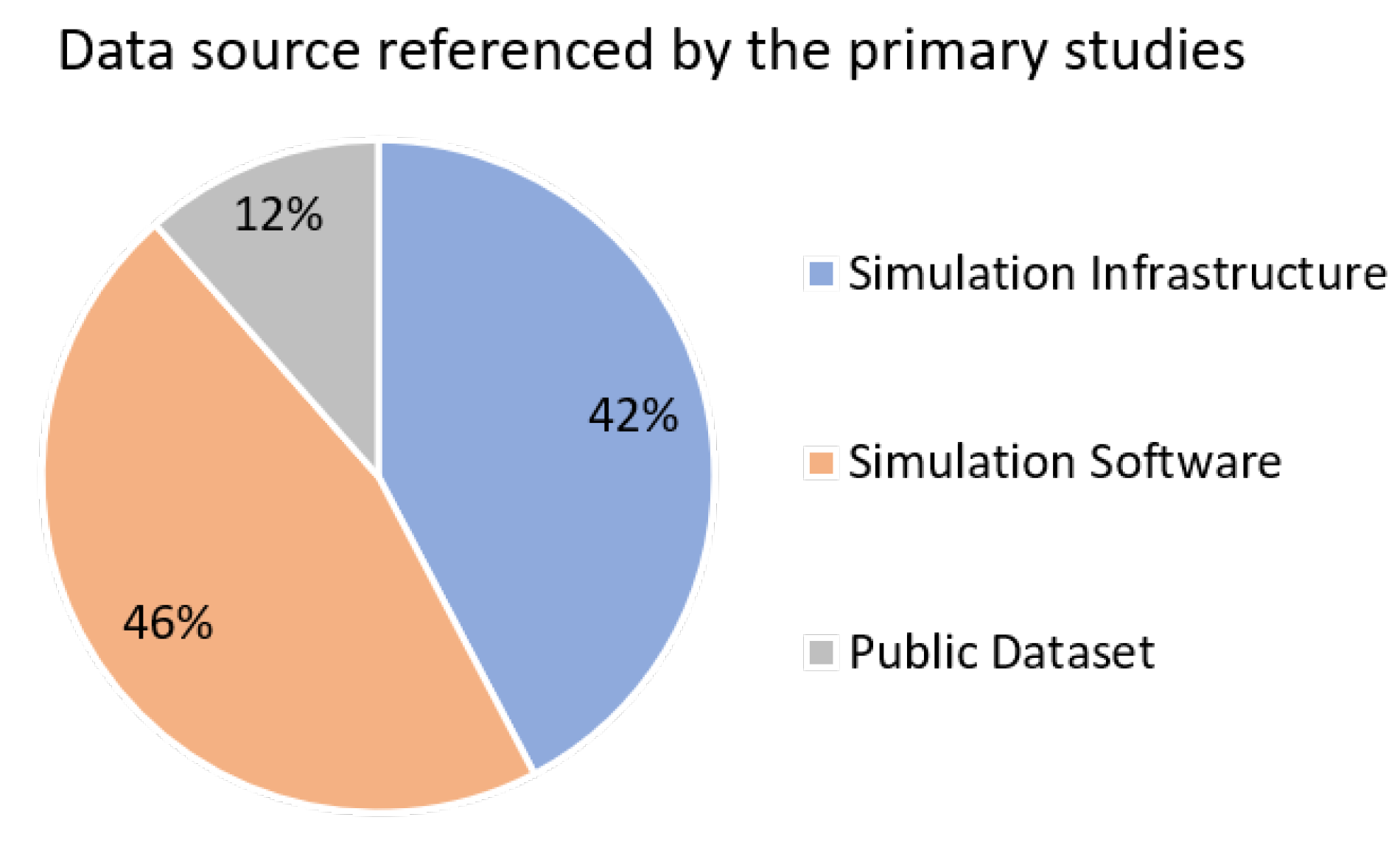
In addition to challenges accessing infrastructure-based simulators or testing in a production environment, there is a lack of publicly accessible datasets (
Figure 11). The following study [
18] stressed the need for access to public data to enable the successful adoption of technological innovations. To validate Industry-4.0-based proposals, the following study [
2] relied on a combination of datasets. The limitation of the dataset used by reference [
125] covering malicious IoT devices is the use of the CAIDA darknet datasets which predominantly contain malicious material. Based on the results, the research community appears to lean on software-based simulation using established platforms, predominantly Matlab [
39,
101,
117,
118,
132], but researchers also utilise UPPAAL [
118] and ProModel Process [
39] simulators. Therefore, software-based simulations are a frequent choice to test experimental concepts. However, using software-based simulations may not be most suitable in some cases, for example, in smart mobility scenarios involving driving where reactions could be very different in a simulated environment knowing that a simulator can be restarted in a click of a button compared to a non-simulated experiment. This may have profound consequences to the required acceleration of research of cyber defence of CPSs within smart cities since there is reliance on simulators for sufficient presentation of threats compared to reliable decision making in a real-world environment.
Concerning RQ1, during the primary studies’ selection process, the researchers observed the availability of studies related to CPS applications. Within those studies, aspects of security may have been mentioned but they were not the focus of the study and often cyber defence was omitted altogether [
18]. Moreover, although CPSs proliferate many aspects of modern lives and the demand and need for resilience in CPSs increases [
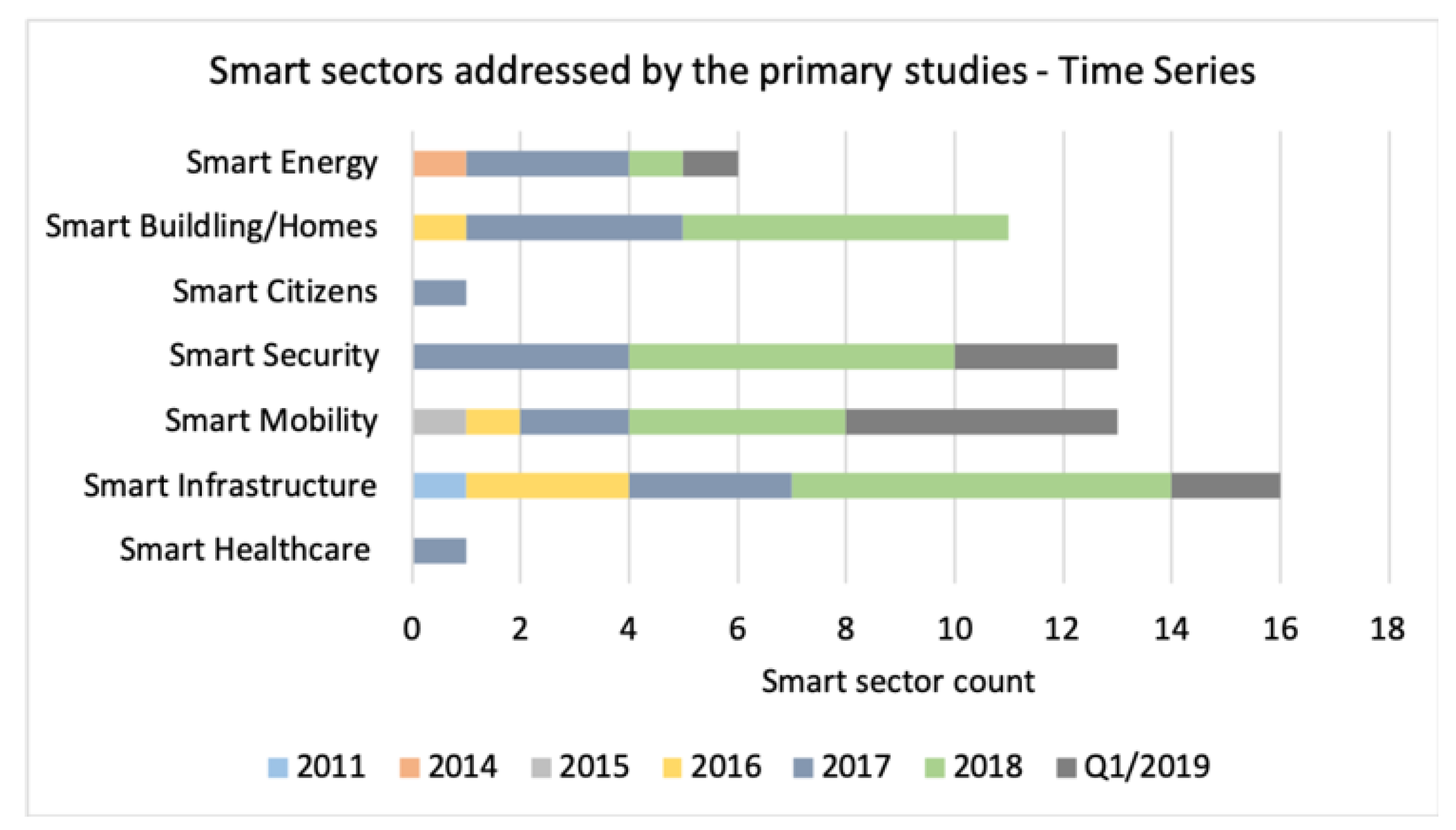
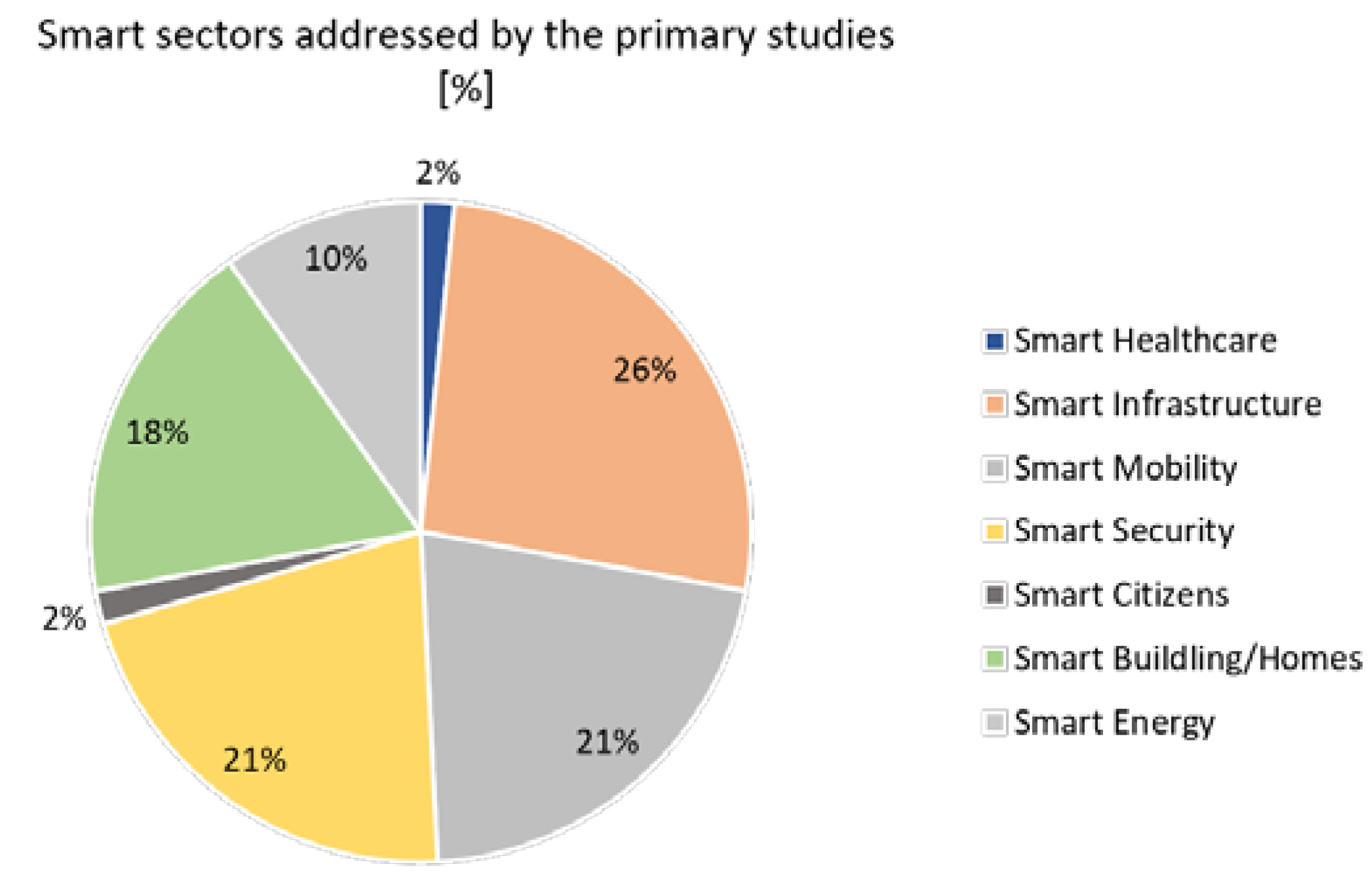
151], the analysis revealed a distinct lack of available empirical research focused on the cyber resilience in the smart healthcare and smart citizen sectors (
Figure 6). Possible reasons include the maturity of the Industry 4.0 technology compared with the smart sectors summarised in
Figure 4 [
84,
85]. Moreover, the scale of media coverage of attacks on CNI like the cyberattack on the Ukrainian power grid [
35] or Stuxnet [
34] could also contribute to the prominence of the research in those sectors. Likewise, smart-healthcare- and smart-citizen-related research has complex and diverse ethical challenges including privacy and confidentiality concerns [
145].
Infrastructure in smart cities consists of a growing number of highly integrated CPSs including traditional devices or entire cities retrofitted with new technologies to facilitate IoT connectivity [
4,
7,
9]. Concerning RQ2, these devices contribute very little to support a systematic DFIR process in smart cities. Therefore, there is a need to develop a process-driven DFIR to deal with the evolving cyber threat landscape, the expanded attack surface and attack vector introduced through IoT connectivity [
17,
28]. Furthermore, as the sources of evidence evolve, digital evidence is contained within the physical artefacts [
44]. For example, image-based evidence can be gained through closed-circuit television (CCTV) surveillance or from social media. Behavioural anomaly detection can be used to detect unauthorised vehicle use through driver profiling [
152], detect attacks on smart water systems [
104] or unauthorised access within smart workplaces [
24].
Digital evidence, similar to physical evidence, seized at a crime scene or following a security incident, is relevant during digital forensic investigations [
67]. The majority of the primary studies have researched a subset of an IR process, predominantly focusing on the “detection and analysis” phase (
Figure 10) of an incident utilising different approaches including profile detection, behavioural anomaly, system monitoring or audit analysis [
47,
48,
65,
99,
100,
103,
104,
108,
120,
123,
124,
127]. Whilst incidents’ detection is a reactive activity by nature, it is a key enabler for subsequent digital forensic processes, which cannot occur without detection and identification of an incident. However, leaning on Locard’s theory, contact between items cause an exchange. Without CPS-specific support for modern DFIR, a forensic investigation from a complex interconnected cyber–physical environment may not extract digital evidence appropriately. Therefore, the important artefacts gathered during the acquisition stage may not be admissible in the court of law because the validity and integrity of the digital evidence is not appropriately maintained. Best practice guides are published—within UK jurisdiction, the Association of Chief Police Officers (ACPO) [
153] and, in the US, with the Best Practices for Seizing Electronic Evidence [
154]—to support incident practitioners.
In fact, the authors of the following study [
37] argue that in some smart sectors such as smart homes, the application of digital forensics is an emerging field of study and asserts that there is a distinct lack of formal methodologies addressing the application of digital forensics in incident responses. Furthermore, recent studies show that the integration of CPSs in smart cities would significantly benefit from a specific forensic methodology as part of forensic preparedness to deal with security incidents [
37,
66]. However, a lack of consensus and formal process models in the digital forensics field that can be used to determine the reliability of digital evidence in courts is argued by reference [
155]. Despite recognition of the importance of SbD by some researchers, our findings show an absence of references to a digital forensic process in response to incidents. Finally, the increasing integration of technology into modern lives and the breadth of digital technologies exploitable by criminals requires extensive research to develop appropriate frameworks.
Concerning RQ3, the significance of the primary studies investigated is that despite the transition from traditional to IoT-enabled environments, our research findings show limited evidence of cross-sector proposals or applications for improving digital forensics. The authors of [
28] claim that there is little evidence of cross-organisational information security sharing, structure and coordination. Considering this assertion within the context of CPSs, although researchers recognise the lack of shared practice, efforts are made to expand and improve cyber defence often as part of their future research direction. However, the various attempts to improve the ability to withstand targeted attacks [
102] remain within a smart sector; for example, discussions are initiated between groups like the control and security practitioners but very few studies exploit the idea of cross-sector efforts to improve digital forensics. For example, authors of [
64] consider their underlying idea applicable to multiple smart sectors which indicates recognition of more integrated approaches. The proposal of authors of [
51,
133] was to increase the flexibility and application of their system in several different environments. Generally, the explored research focused on developing and improving cyber defences within a single smart sector.
In summary, we draw on the results of the extensive SLR process, present and discuss the outcomes of our findings. Our extensive review showed number of gaps which could provide the basis and create opportunities for future research.
5. Conclusions
Smart cities are complex networks of connected devices including CPSs which utilise automation and AI to control several key functions. The initial keyword searches for this study highlighted CPSs as an emerging technology that creates an enormous range of possible applications across several smart sectors. It is clear from our SLR that there is an increasing interest in theoretical research and empirical implementations of CPS cyber resilience and support for modern DFIR within smart cities. The key influencing factors include the Industry 4.0 concept, government-led support and initiatives such as the National Cyber Security Strategy in UK [
5] or national infrastructure plans [
85,
88], innovative ideas [
36] and incidents [
34,
156].
Some smart sectors including smart healthcare and smart citizen were addressed only by a small number of studies, see
Figure 12; it is critical that future research recognises this limitation. It is also evident that interest is growing in cross-sector proposals and an interdisciplinary approach to solve real-life problems including cybercrime [
39,
51,
63,
64,
65,
100,
101,
102,
111,
131,
134]. Going forward, an interdisciplinary approach across smart sectors and aggregated sharing of CTI from multiple sources could increase situational awareness and provide a detailed, real-time and measurable body-of-knowledge to deal with the increased sophistication and coordination of cyberattacks.
We outlined and discussed the cyber threats landscape, particularly asserting that cyberattacks are increasingly more sophisticated, coordinated and targeted including advanced persistent threats (APTs). For example, the primary studies report on attacks that can originate from both within and from outside of the organisation. Having identified that there are limitations of the current IR methods in dealing with APT, we argue that existing efforts are insufficient to address emerging threats and there is a need for a CTI-driven mitigation approach [
31]. Therefore, there is much work to be done to prepare for a dynamic threat landscape, strengthen the CPS cyber resilience to have the ability to adapt and operate under adverse conditions and to recover from incidents. For example, future research could focus on applying CTI to modelling attacks on entities’ critical functions and underlying systems including its people, processes and technologies. This could help an entity to assess its protection, detection and response capabilities. Therefore, lessons can be gained from the IR lifecycle to minimise disruption and reduce the attack surface. The challenges need to be addressed through innovative solutions to support a modern defence-in-depth strategy.
Additionally, the increasing integration of CPS into modern lives diversifies the scope of forensic science and forensic investigations. Thus, alongside the conventional forensic disciplines, digital forensics has developed as a branch of forensic science covering diverse digital technologies including CPSs which can be exploited by criminals. The majority of the primary studies reported on the detection and analysis phase of the IR process. Therefore, more research is required to investigate the other phases of the IR process. This creates opportunities to reduce the backlog, the workload and the cost of the digital forensic investigation processes. Implementing an evidence-based body-of-knowledge by forming a robust CTI could solve real-life problems. Future work on addressing CPS in smart cities to support modern DFIR should consider integrating CTI into the IR. Such integration could enable faster threat detection, digital forensic investigation, repelling of attacks minimising disruption and escalated response time to prevent adversaries from successfully compromising their target.
Further, we identified a lack of available current publicly accessible real CPS-generated datasets that limit the ability of comparative experiments by other researchers, for example, to test and validate the accuracy of results robustly. Future works could consider addressing this limitation to create a pool of scientific resources. Publicly accessible datasets could accelerate the development of countermeasures against cybersecurity threats strengthening the cyber defence in smart cities to continue to function effectively under adverse conditions [
43].