Abstract
To balance the information security and energy harvest for massive internet-of-things (IoT) devices, an unmanned aerial vehicle (UAV)–assisted secure communication model is proposed in this paper. We extend the secure transmission model with physical layer security (PLS) to simultaneous wireless information and power transfer (SWIPT) technology and optimize the UAV trajectory, transmission power, and power splitting ratio (PSR). The nonconvex object function is decomposed into three subproblems. Then a robust iterative suboptimal algorithm based on the block coordinate descent (BCD) method is proposed to solve the subproblems. Numerical simulation results are provided to show the effectiveness of the proposed method. These results clearly illustrate that our resource allocation schemes surpass baseline schemes in terms of both transmit power and ratio of harvesting energy, while maintaining an approximately instantaneous secrecy rate.
1. Introduction
With the development of 5G, internet-of-things (IoT) devices are becoming more and more popular. Due to the limited battery energy of ground IoT devices [1] and the high mobility of the unmanned aerial vehicle (UAV), simultaneous wireless information and power transfer (SWIPT) technology is exploited in UAV-assisted wireless communication for IoT ground devices [2,3,4]. In [5], the authors propose to exploit the UAV as a mobile relay to solve the end-to-end cooperative throughput maximization problem with SWIPT. In [2], the authors consider the UAV-assisted SWIPT communication system with a nonlinear energy harvesting model, which proves that the power splitting (PS)–based system is superior to the time switching (TS)–based system.
On the other hand, the openness of air-to-ground wireless channels increases the security risk of information transmissions for a UAV-assisted system [4]. The traditional information encryption technology is complex and energy-consuming, which is not suitable for a UAV communication system. Therefore, the physical layer security (PLS) technology is introduced as an improvement technology [4,6]. The PLS technology uses the randomness of wireless media to protect information transmission from eavesdropping, which is considered to be a promising method to realize confidentiality in wireless communication [7]. At the same time, the technique inspired by the principles of blockchain for maintaining security in UAV communication networks under the context of surveillance is prompted [8], through corroborating information about events from different sources and using a secure asymmetric encryption with a preshared list of official UAVs to improve reliability effectively and efficiently.
Nowadays, many papers start to investigate the combination of the UAV-assisted communication, SWIPT and PLS. In [9], two collaborating UAVs with SWIPT technology are considered, one UAV transmits confidential information to the destination node, and the other sends jamming signals to prevent the other nodes from eavesdropping. By jointly optimizing the transmission power and trajectory of UAVs, and power splitting ratio (PSR), researchers formulate an average secrecy rate maximization problem. However, it is complex to safely transmit information to a node by two UAVs, and the system only cares about the confidentiality of one node by two UAVs. In order to avoid the inevitable eavesdroppers, in [10], the authors study the problem of secrecy rate maximum by jointly optimizing the trajectory and transmit power of a UAV with an energy receiver and information receiver, respectively, which is difficult to realize due to the limited size of IoT devices.
Though a lot of papers have studied UAV-assisted wireless energy transmission [9,11] and secure wireless communication [12] with different perspectives, UAV-assisted energy harvesting or secure wireless communication is studied independently. Therefore, a UAV-assisted secure communication system for IoT nodes is considered in this paper. There are two kinds of IoT nodes: one is the destination node, which can receive the information and energy by SWIPT, and the other is the energy node, which can only receive the energy. The information transmission security of the destination node is ensured by joint trajectory and resource allocation with a PLS technique. We extend the secure transmission model in [12] to SWIPT technology and optimize the PSR at the nodes. In order to enhance the information security [13], some restrictions are added on the information threshold and energy harvesting threshold of nodes. The challenge of the proposed model is to maximize the information security transmission capacity while balancing the energy storage capacity by optimizing the UAV trajectory, transmission power, and PSR. The object function is nonconvex due to the coupling of multiple variables. Consequently, the objective function is decomposed into three subproblems and solved by an iterative algorithm based on block coordinate descent (BCD) and successive convex approximation (SCA).
In this article, we will introduce the UAV-assisted system model and problem formulation in Section 2. The proposed optimization algorithm, including optimizing transmit power, trajectory, PSR, etc., is presented in Section 3. Then numerical simulation results are provided in Section 4 to show the effectiveness of our proposed method. Finally, we conclude this paper in Section 5.
2. System Model and Problem Formulation
2.1. System Model
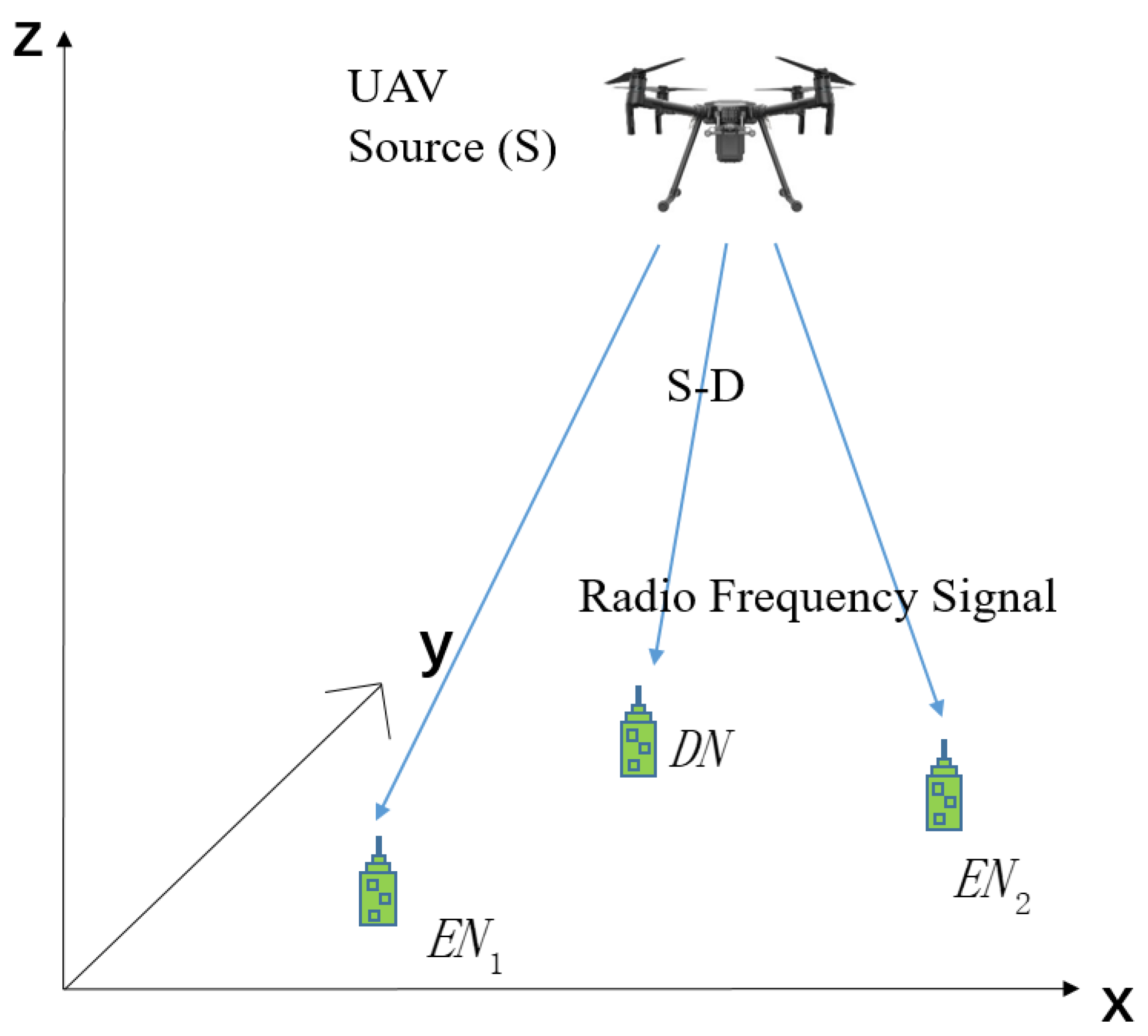
As shown in Figure 1, three IoT nodes (one destination node, , and two energy nodes, , ) equipped with SWIPT technology are considered. The UAV flies from the initial position to the final position and transmits confidential information to by the main link . Meanwhile, all nodes could harvest energy. We maximize the information security transmission capacity by optimizing the trajectory and transmission power of the UAV, the PSR of the nodes. The power of the information and the harvested energy of , are constrained to improve the information security and balance energy collection.
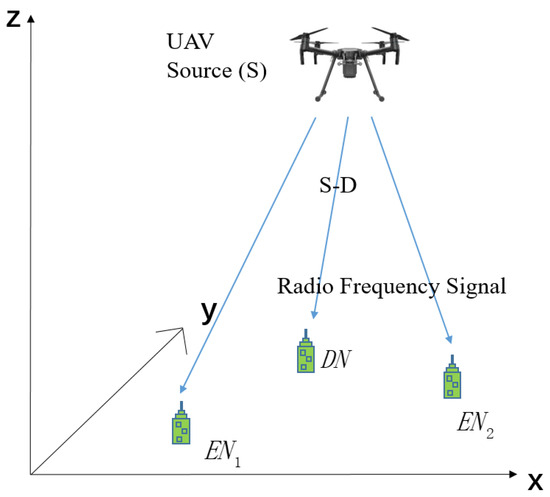
Figure 1.
System model of UAV-assisted IoT node secure communication system.
The horizon coordinates of are given by , and is located at . The UAV is assumed to fly at an allowable relatively fixed height H. Its flight time is T, so its time-varying coordinates are expressed as . The take-off time and landing time are neglected. The initial position and final position are supposed to be known [4]. The flight time T is divided into N time slots; i.e., , is the duration of each time slot. The maximum flight distance of the UAV in each time slot is . Let the PSR be denoted by , where [14]. The constraints are as follows:
Motivated by [9,10], we adopt a channel model in which both line-of-sight (LoS) and non-LoS propagations are considered. By averaging the surrounding environments and small-scale fading, the expected channel power of the UAV-ground (UG) link is [9]
where denotes the time-varying distance between the UAV and the ground node g. Additionally, denotes the path-loss exponent . Then is the environmental constants following homogeneity. Let denote the UAV transmission power in the nth time slot, and the transmit power constraint is
where the average power is and the maximum power is , . The harvested energies of and are denoted by and , respectively:
where represents the energy conversion efficiency of . The harvested information of is denoted by
Motivated by [10], the achievable information rates from the UAV to and from the UAV to in bits/second/Hertz (bps/Hz) are denoted by and , respectively. Additionally, represents the noise power.
Hence, the secrecy rate [4] of is given as (7), where .
2.2. Problem Formulation
In this work, a conjoint optimization of the UAV trajectory, transmission power allocations, and PSR is adopted to maximize the secrecy rate within a limited flight time T. We assume that the average and maximum power constraints, mobility constraints, initial and final position constraints of the UAV, and energy harvesting constraints of each EN are satisfied. Let . Thus, the maximum of the secret rate of can be expressed as
Here, the constant is the minimum average harvested energy. and have imposed basic constraints on Emin, which enable all nodes to collect energy. The constant is the minimum energy required for decoding. prevents from decoding the information transmitted to the main link (). The information threshold is smaller than the power threshold . C2–C5 and C7 are the formulations defined in Section 2.1.
3. Proposed Optimization Algorithm
The objective function in is nonsmooth at zero due to . Therefore, Lemma 1 is proposed to solve it.
Lemma 1.
is equivalent to [15] given by
However, is still a nonconvex problem due to the coupling of multiple variables. Hence, a three-stage alternating optimization algorithm is proposed to solve it. The details are as follows.
3.1. Optimal Transmit Power of UAV
With the given feasible UAV trajectory Q and PSR, the UAV transmit power optimization problem is given as
Let , . Then, the objective function is simplified to
where . Obviously, if , it is necessary to let the optimized power to prevent information leakage. Additionally, if , the information sent by the UAV to will not be decoded. Therefore, becomes a convex optimization problem, which satisfies Slater’s condition and could be solved by the Lagrange duality method. Then the solution of is given as
The closed-form expression of the optimized power is
where , and , , , are the the Lagrange multipliers associated with the constraints , , , and , respectively. Finally, we update the Lagrange multipliers with the subgradient method as follows: y
3.2. Optimal UAV Trajectory
For a given UAV power allocation and PSR, the UAV trajectory optimization problem is given as
In and , we note that the energy function is a convex function for and . Let denote the given UAV trajectory in the rth iteration; by a first-order Taylor expansion of and at and , respectively, we can have the minimum value and for and , respectively. Similarly, we expand at to obtain the minimum value .
Then, we introduce a slack variable and to the objective function and the minimum value of , respectively. Finally, is transformed into a convex optimization problem , which can be solved by standard convex optimization tools, such as CVX.
3.3. Optimal Power Splitting Ratio
To optimize the PSR with the given workable transmit power and trajectory of the UAV, the problem becomes
Let .
Then the objective function is given by
where . Similarly, with , only if , the confidential information cannot be decoded. Then can be solved by a Lagrangian dual method. While , we set to prevent decoding. Therefore, the solution of is given as
By the same method as , we can have
where and , are the dual variables associated with the constraints , , and , respectively. Then, , and can be updated by the subgradient method:
3.4. Overall Algorithm
is solved by the BCD and SCA method with the overall iterative solution in Algorithm 1. The convergence analysis of the proposed iterative algorithm is carried out as below. Let , , , and denote the objective value of , , , and for given conditions, respectively.
| Algorithm 1 Alternative optimization algorithm for P1.1 |
| 1. Setting: T, N, , and the tolerance error 2. Initialization: The iteration index , . 3. Repeat: 3.1. Calculate according to (12) with the given . Update , , , by the subgradient algorithm 3.2. Calculate according to (19) with the given . Update and by the subgradient algorithm 3.3. Solve P3 by CVX with given and if where Break; else Update the iterative number m = m + 1; End if Until 4. Obtain solutions: , and |
Similarly, with the given and , we obtain the optimal solution for by (17), then
where is the optimal PSR of and by (19). Since Taylor expansion is tight, it follows
Then for the given feasible , , it follows
where (a) holds since problem P4 is solved optimally with solution , , and (b) holds since the objective value of is the lower bound of the original problem. Based on (22)–(25), we can obtain that
Equation (26) indicates that the objective value of does not decrease after each iteration, which guarantees the convergence of the algorithm. Let and denote the number of iterations required for the outer loop and the inner loop of the proposed algorithm, respectively, and the total complexity of ours is . Compared with the algorithm complexity provided by the baseline [10], the complexity of our proposed method is much lower.
4. Simulation Results and Numerical Analysis
In this paper, we adopt the information transmission model in [10] and set it as the baseline scheme. We compare it with our optimized scheme. In our study, we employed the SDP3 solver from CVX MATLAB and made 592 calls to CVX within the algorithm. The experimental setup involved the utilization of an Intel 64 Family 6 Model 142 Stepping 10 GenuineIntel 1401 MHz processor. The convergence time of the algorithm, under these hardware conditions, was observed to be approximately 269.02 s. The simulation parameters are given in Table 1.

Table 1.
Simulation parameter.
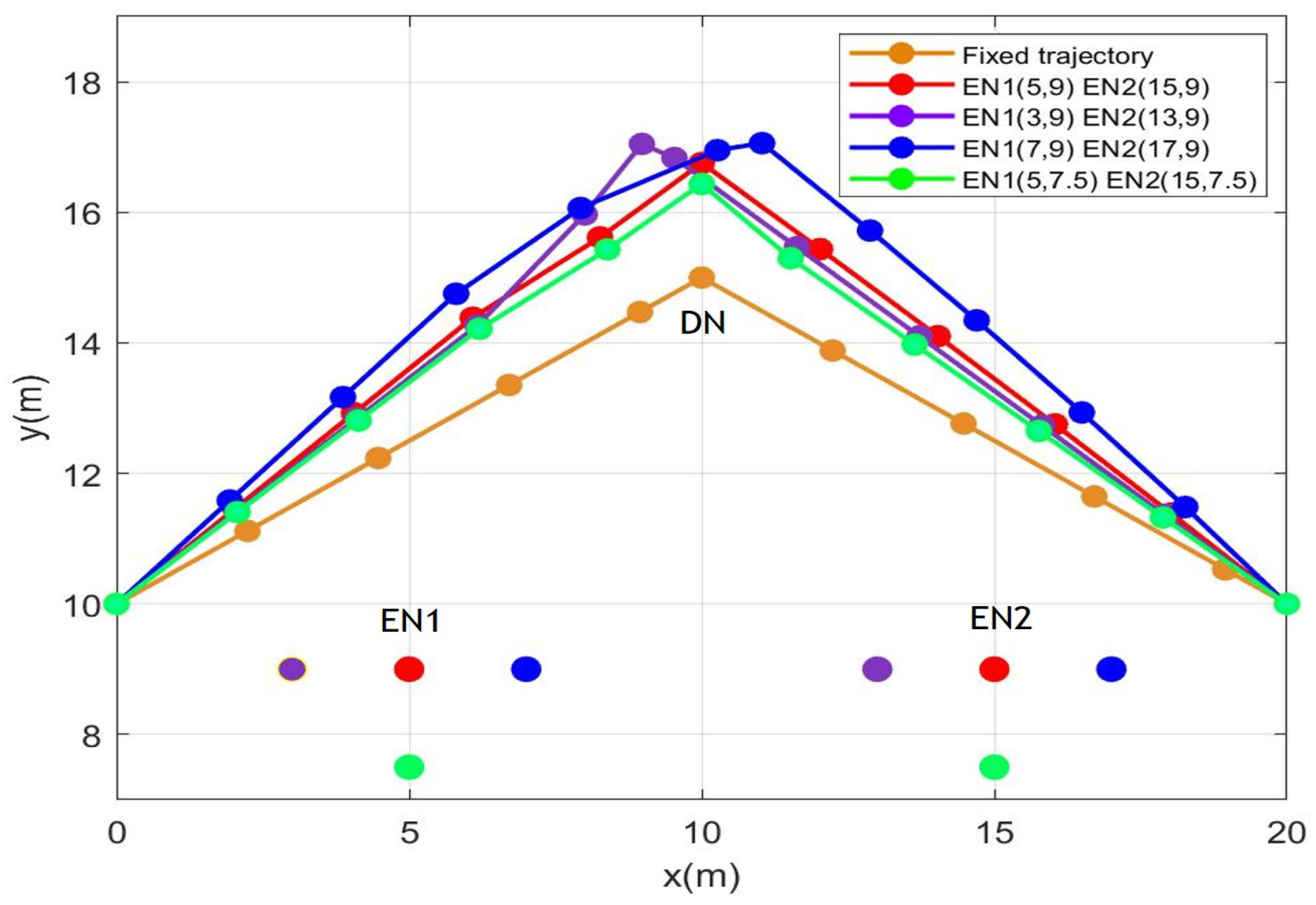
Figure 2 illustrates the optimal UAV’s trajectory with the proposed algorithm considering conjoint optimization of different at the same time. We obtain the different UAV trajectories for different positions compared with the fixed trajectory. The UAV flies to with maximum speed, then it hovers close to to facilitate the transmission of information and energy. Finally, the UAV flies to with the fastest possible speed. In Figure 2, the peak coordinate of the green trajectory is (10, 16.75), the red one is (10, 16.43), the blue one is (11.03, 17.06), while the peak coordinate of the purple trajectory is (8.977, 17.05). These observations suggest that as are positioned either closer or farther away, or deviate to the left or right of , the flight trajectory exhibits similar trends in response.
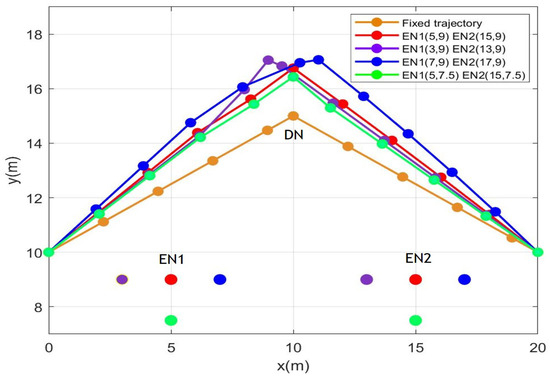
Figure 2.
Trajectories of a UAV with a different location of . H = 5.0 m, = 2 W. The coordinates of the UAV’s initial and final location are set as = (0, 10) and = (20, 10).
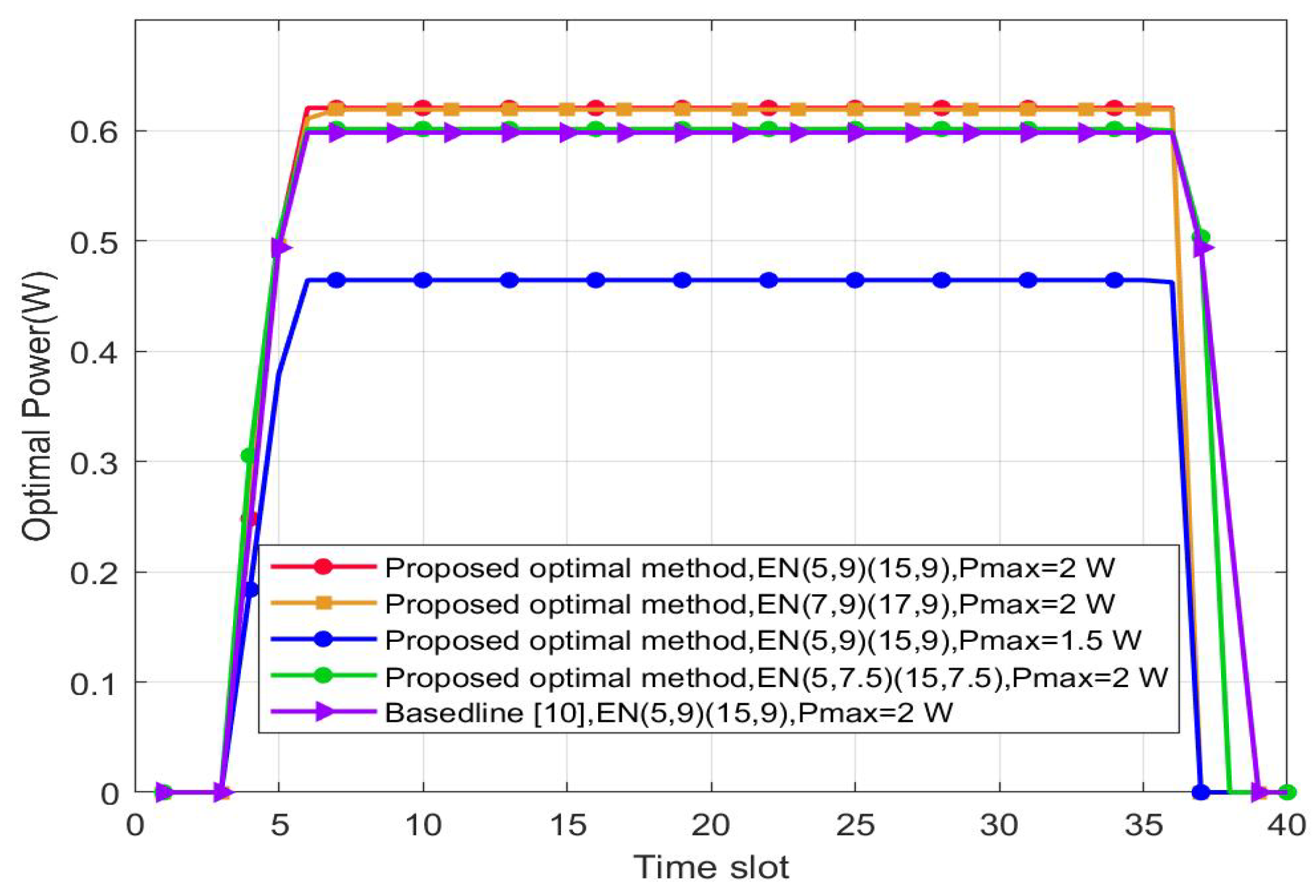
Figure 3 shows the UAV’s transmit power over time slots. The optimized power first increases when the UAV is close to , and then it remains constant while the UAV hovers at a certain position. The value of the baseline in the middle constant part is 0.5984 W, which is smaller than the optimized scheme of 0.6207 W. Finally, it decreases to zero when the UAV flies away from . The optimized power decreases with decreasing . The closer are to , the higher the optimized power will be. Compared with the separated receiver mode, we sacrifice some power to obtain the desired secrecy rate due to a PS mode. In a separated receiver mode, the energy received by each antenna does not need to be split. However, in an in vivo case, the separated receiver mode is difficult to implement.
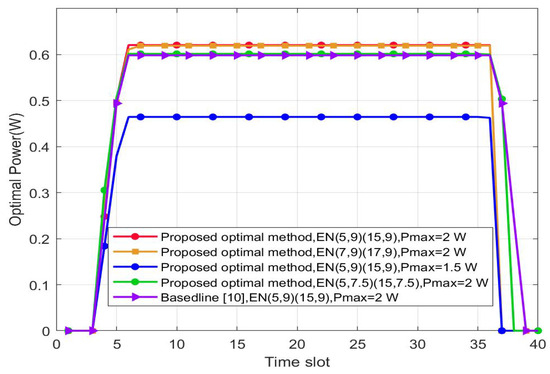
Figure 3.
Optimized transmit power versus the time slot. H = 5.0 m.
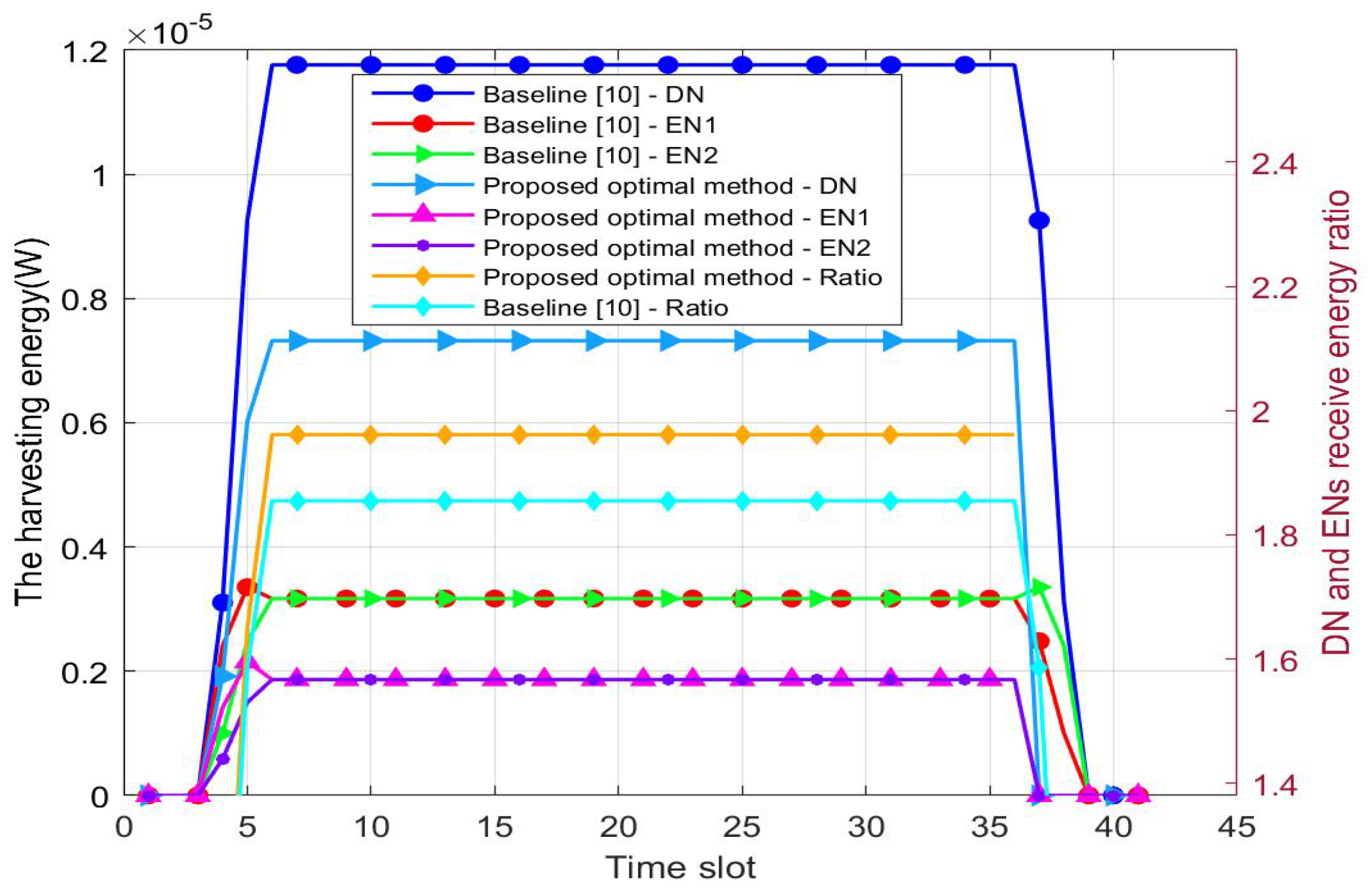
Figure 4 shows the energy collected by and over time slots. The energy collection increases gradually as the UAV approaches , and it remains unchanged when the UAV hovers over . After flying away from , the harvesting energy gradually decreases to zero. Similarly, the harvesting energy is higher than the baseline solution because the optimization of the PSR is not considered in [10]. Compared with the harvesting energy ratio of and , the value of the baseline is 1.8547, which is smaller than the optimized scheme of 1.9612. This indicates that the destination node receives more energy in the proposed method.
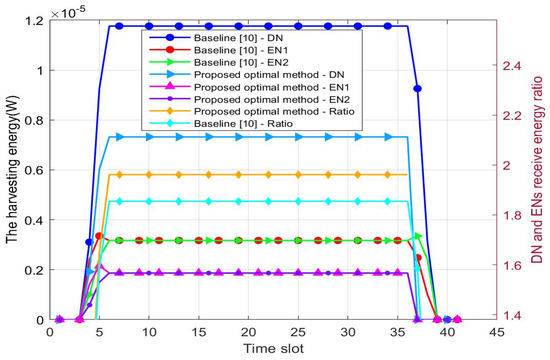
Figure 4.
The harvesting energy versus the time slot. H = 5.0 m. The coordinates for , , and are (5, 9), (15, 9), and (10, 15), respectively.
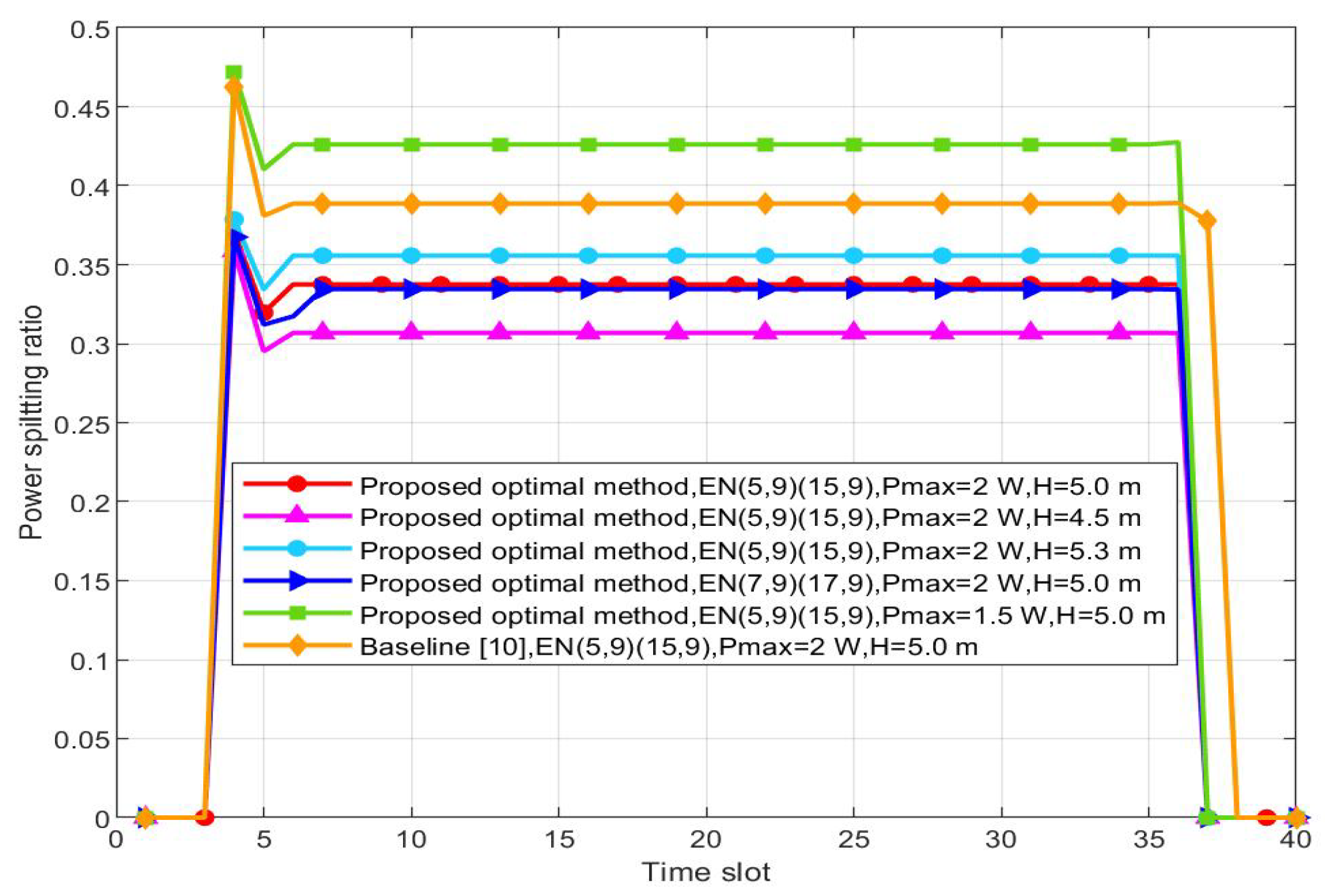
Figure 5 shows the variation of the PSR with time. When the PSR is low, the IoT device is mainly used as energy nodes; otherwise, it is mainly used as information nodes. When the UAV is far away from , the PSR is low to let energy nodes collect energy. If not, the PSR rises to let the node decode information. In order to meet the energy harvesting threshold requirement, the PSR increases with decreasing . However, the PSR decreases when are located close to to reach the information decoding threshold. From the simulation results, it can be observed that under the same , as the distance between and continues to increase, the corresponding maximum PSR will decrease. The values of three points mentioned in the scheme from near to far are 0.3375, 0.3346, and 0.2787, respectively. Considering height factors, as the flight height of the UAV increases, the stable value of the PSR increases, from low to high height, 0.3068, 0.3375, and 0.3557, respectively.
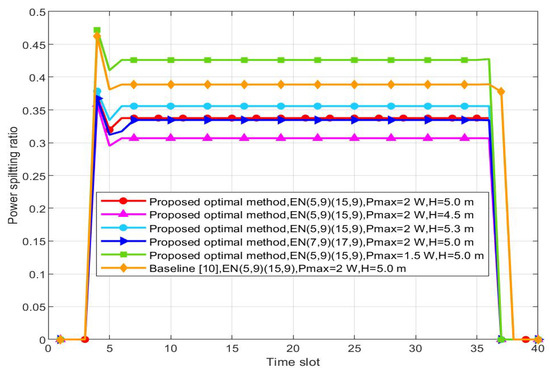
Figure 5.
Optimized power splitting ratio versus the time slot.
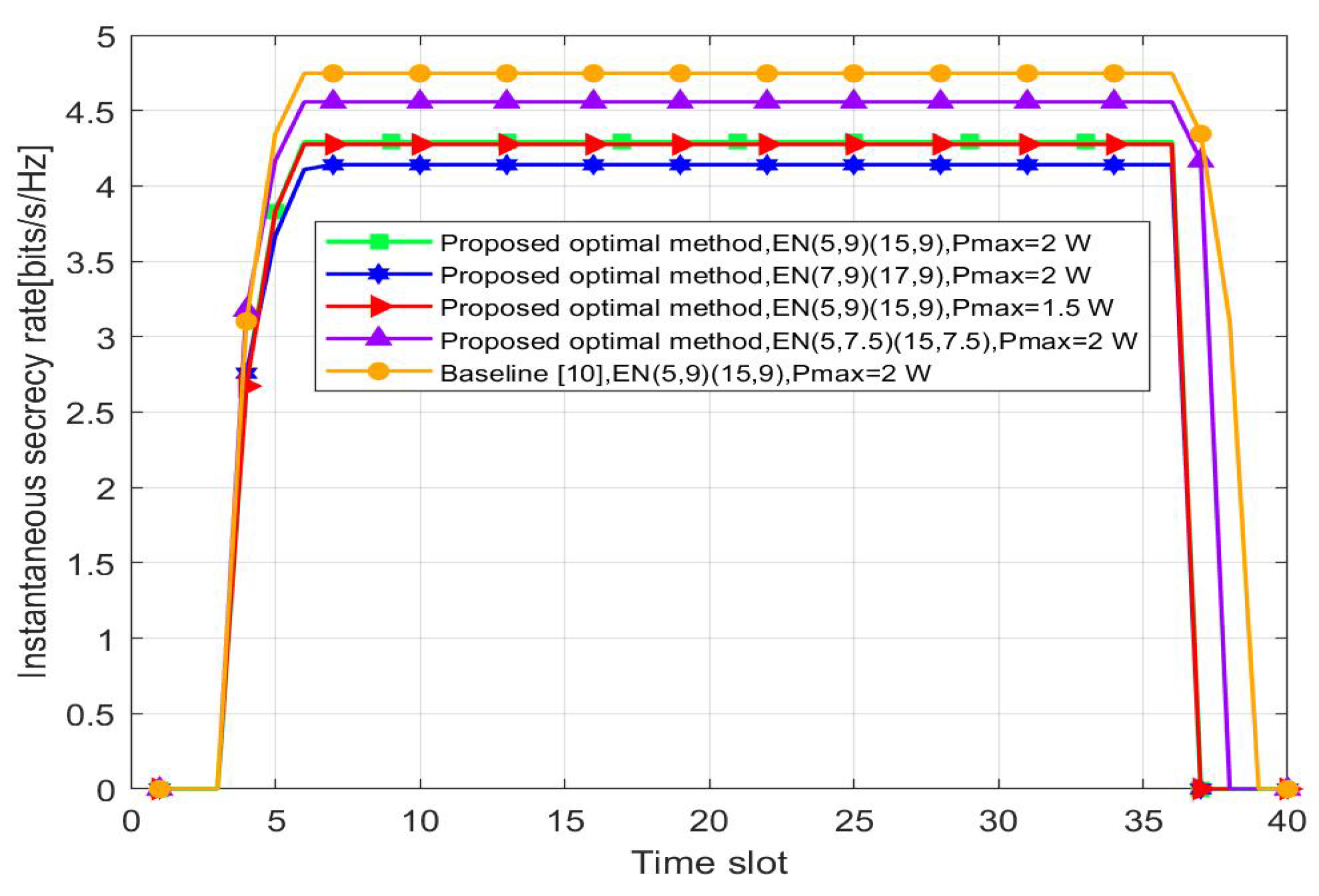
Figure 6 shows the variation of the instantaneous secrecy rate over time slots. They all have the same trend as that of the transmit power, PSR. When the UAV is hovering over , the channel quality of the main link and the transmission efficiency are the best. Additionally, the closer is to , the smaller the optimal secrecy rate is. The transmit power has little effect on the optimal secrecy rate. Meanwhile, the baseline and the optimal scheme have limited numerical differences (4.747 bits/s/Hz and 4.292 bits/s/Hz, respectively, less than 0.5 bit/s/Hz) due to the existence of the PSR, which can be neglected in applications.
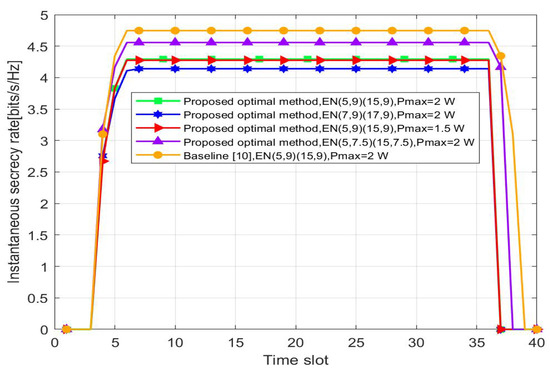
Figure 6.
Instantaneous secrecy rate versus the time slot. H = 5.0 m.
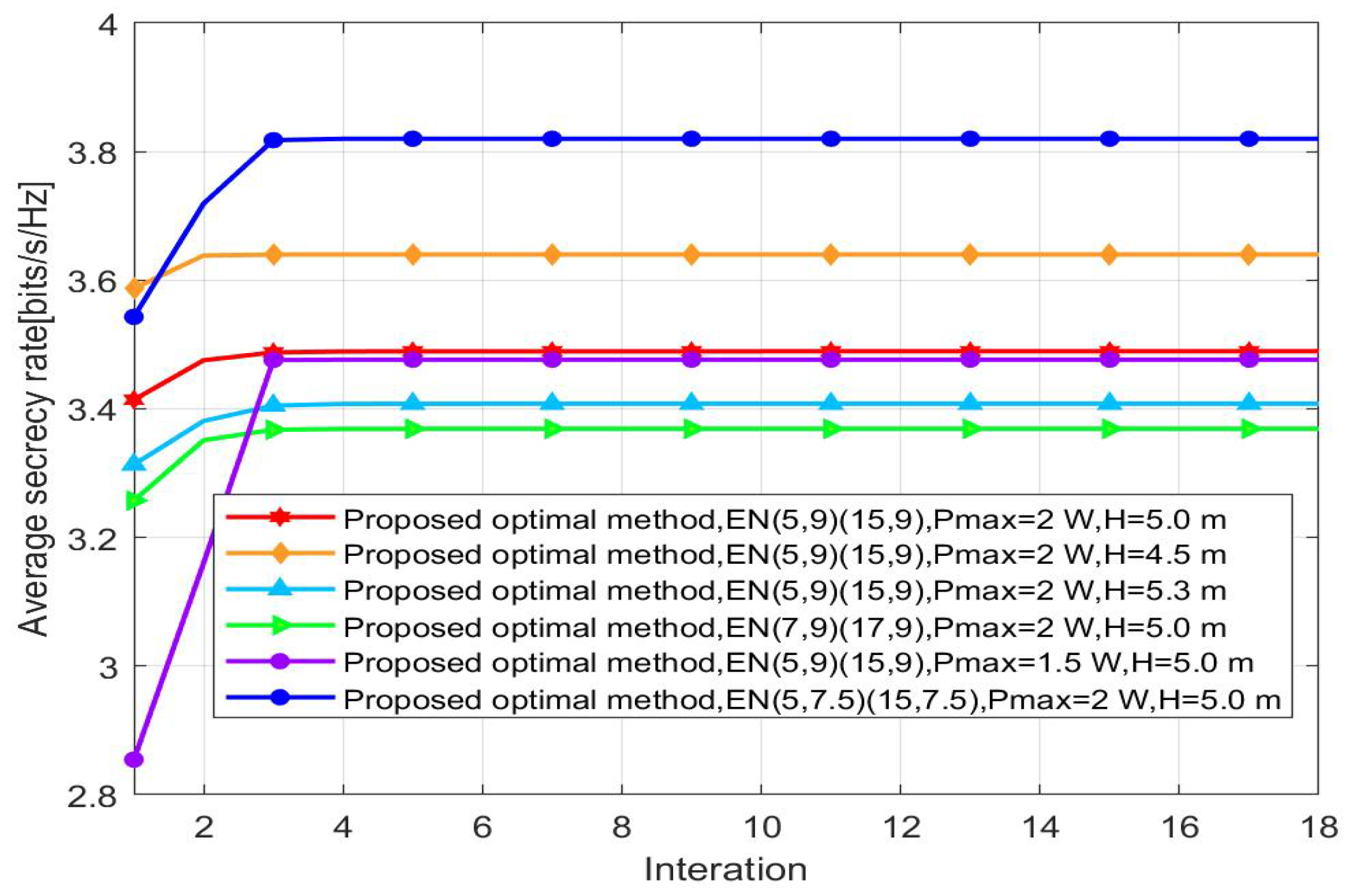
Figure 7 shows the curve of the average secrecy rate in terms of the number of iterations. All schemes converge to terminate at a threshold, which validate that the subproblem approximates to the convex problem. Additionally, the proposed algorithm converges very fast when we vary the location and the magnitude of the power of . It is an efficient solution for UAV applications. Considering height factors, as the flight height of the UAV increases, the stable value of the average secrecy rate decreases, from low to high height, 3.640 bits/s/Hz, 3.489 bits/s/Hz, and 3.408 bits/s/Hz, respectively.
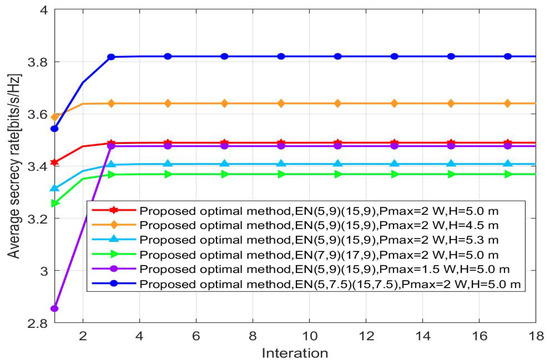
Figure 7.
Average secrecy rate versus iteration.
Based on the aforementioned results, we will proceed to summarize and compare the performances of the baseline [10] and the values obtained through the proposed optimal method. The selected environmental conditions include the coordinates of (5, 9), (15, 9), (10, 15), and = 2 W, H = 5.0 m. A comparative analysis data table is presented in Table 2 below.

Table 2.
Performance comparison.
The comparative analysis reveals that our proposed methodology excels in terms of optimal power allocation, the energy harvesting ratio for and . Furthermore, the instantaneous secrecy rate exhibits a close proximity. Our approach comprehensively considers various factors, including power, security, and transmission efficiency, leading to a superior overall performance, which demonstrates the superiority of our resource allocation schemes over the baseline scheme.
5. Conclusions
In this paper, we have considered a wireless communication system consisting of a UAV and three IoT nodes equipped with SWIPT technology. The UAV transmits confidential information to the destination node. All nodes could collect energy. The secure transmission of confidential information to the destination node is also considered. Therefore, we apply the PLS method with limitation on the harvested energy and information threshold of the energy nodes to prevent it from decoding information and help it to collect energy.
The objective function is achieved by the joint optimization of the UAV’s trajectory, transmit power, and PSR. Then it is solved by an iterative algorithm based on the BCD and SCA. Numerical simulation results are provided to show the effectiveness of our method. Compared with the baseline mode, the PS mode is more meaningful in an in vivo case, which not only meets the security rate but also optimizes the effective energy distribution of the node.
The current study focuses on a fixed number of IoT nodes equipped with SWIPT technology and a relatively low height range of UAVs. However, in practical scenarios, the number of IoT nodes and the flight altitude may vary dynamically. Therefore, our future work will further explore the scalability of our system. A variable number of nodes and a wider range of flight altitudes will be taken into consideration. More developing algorithms and protocols that can adapt to the dynamic network topology and optimize resource allocation accordingly will be investigated.
Author Contributions
Conceptualization, methodology, and software, B.M. and D.X.; formal analysis, X.R.; validation, J.L.; data curation, Y.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Natural Science Foundation of Guangdong Province under Grant Nos. 2023A1515011420, 2022A1515011830, 2021A1515011842.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Li, Y.; Liang, W.; Xu, W.; Xu, Z.; Jia, X.; Xu, Y.; Kan, H. Data collection maximization in IoT-sensor networks via an energy-constrained UAV. IEEE Trans. Mob. Comput. 2021, 22, 159–174. [Google Scholar] [CrossRef]
- Jiang, R.; Xiong, K.; Yang, H.C.; Fan, P.; Zhong, Z.; Letaief, K.B. On the coverage of UAV-assisted SWIPT networks with nonlinear EH model. IEEE Trans. Wirel. Commun. 2021, 21, 4464–4481. [Google Scholar] [CrossRef]
- Kim, K.W.; Lee, H.S.; Lee, J.W. Waveform design for fair wireless power transfer with multiple energy harvesting devices. IEEE J. Sel. Areas Commun. 2018, 37, 34–47. [Google Scholar] [CrossRef]
- Sun, X.; Ng, D.W.K.; Ding, Z.; Xu, Y.; Zhong, Z. Physical layer security in UAV systems: Challenges and opportunities. IEEE Wirel. Commun. 2019, 26, 40–47. [Google Scholar] [CrossRef]
- Yin, S.; Zhao, Y.; Li, L.; Yu, F.R. UAV-assisted cooperative communications with power-splitting information and power transfer. IEEE Trans. Green Commun. Netw. 2019, 3, 1044–1057. [Google Scholar] [CrossRef]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Garcia-Magarino, I.; Lacuest, R.; Rajarajan, M.; Lloret, J. Security in networks of unmanned aerial vehicles for surveillance with an agent-based approach inspired by the principles of blockchain. Ad Hoc Netw. 2019, 86, 72–82. [Google Scholar] [CrossRef]
- Mamaghani, M.T.; Hong, Y. Improving PHY-security of UAV-enabled transmission with wireless energy harvesting: Robust trajectory design and communications resource allocation. IEEE Trans. Veh. Technol. 2020, 69, 8586–8600. [Google Scholar] [CrossRef]
- Hong, X.; Liu, P.; Zhou, F.; Guo, S.; Chu, Z. Resource allocation for secure UAV-assisted SWIPT systems. IEEE Access 2019, 7, 24248–24257. [Google Scholar] [CrossRef]
- Hua, M.; Wang, Y.; Zhang, Z.; Li, C.; Huang, Y.; Yang, L. Energy-efficient optimisation for UAV-aided wireless sensor networks. IET Commun. 2019, 13, 972–980. [Google Scholar] [CrossRef]
- Shengnan, C.; Xiangdong, J.; Yixuan, G.; Yuhua, Z. Physical layer security communication of cognitive UAV mobile relay network. In Proceedings of the 2021 7th International Symposium on Mechatronics and Industrial Informatics (ISMII), Zhuhai, China, 22–24 January 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 267–271. [Google Scholar]
- Tegos, S.A.; Diamantoulakis, P.D.; Pappi, K.; Karagiannidis, G.K. Optimal simultaneous wireless information and power transfer with low-complexity receivers. In Proceedings of the 2018 IEEE 19th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Kalamata, Greece, 25–28 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Choi, K.W.; Hwang, S.I.; Aziz, A.A.; Jang, H.H.; Kim, J.S.; Kang, D.S.; Kim, D.I. Simultaneous wireless information and power transfer (SWIPT) for Internet of Things: Novel receiver design and experimental validation. IEEE Internet Things J. 2020, 7, 2996–3012. [Google Scholar] [CrossRef]
- Zhang, G.; Wu, Q.; Cui, M.; Zhang, R. Securing UAV communications via joint trajectory and power control. IEEE Trans. Wirel. Commun. 2019, 18, 1376–1389. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).