Abstract
Having access to a unique quantum circuit that one wants to protect against use by others is a very likely scenario in industrial computing. However, currently, users rely on classical computer security schemes, which have known shortcomings. In this paper, we introduce a novel protection scheme along with a survey of other known methods to protect quantum information. In particular, we review physically unclonable functions (PUFs), obfuscation, and introduce quantum logic locking (QLL). The latter technique provisions end users to protect their circuit from an adversary through the use of a secret key.
1. Introduction
Quantum computers have become practical in the last decade rapidly, with quantum computers containing over a hundred qubits available today. As opposed to traditional computers, quantum computers rely on qubits, which can take an infinite amount of states during computation only to be collapsed to a final 0 or 1 at measurement time. Furthermore, the qubits can be coupled to each other. This is another feature that is not naturally present in traditional computing.
Each qubit can be applied against a certain set of gates to change its state. Thus, it seems logical to place such gates along a timeline, with the first gate being applied to be on the left, the next one to its right, etc. Two qubit gates can change the states of two qubits at once, or more commonly use the state of one qubit to alter another one. Such two-qubit operations also end up coupling the two qubits from that point on.
Some examples of one-qubit gates are Hadamard (H), (X), Pauli rotation (, , ), and Identity (I). Example two-qubit gates are Controlled Pauli-X () or Controlled Pauli-Z (). Controlled two-qubit gates can be identified with a vertical control signal that is tied to another qubit. Qubits are eventually measured into a 0 or 1 state as classical computing operates based on these binary values.
It is difficult to cover many aspects of quantum computing in one paper. However one can refer to complete and reputable sources, such as [1,2,3,4]. A quick introduction by the author can also be found in [5].
Qubits and gates constitute a quantum circuit through which an algorithm can be implemented. It could be helpful to illustrate these concepts on an actual quantum circuit that implements a meaningful function. The quantum circuit shown in Figure 1 is an implementation of Grover’s algorithm, which is a search function described in [6]. It aims to find the input that would produce a specific output for a black box function that a user could evaluate. As mentioned in [7], this algorithm solves an NP-complete problem in processing time that is correlated to the square root of time, as opposed to a classical algorithm, which is correlated with time directly. Hence, significant speedup can be achieved with the quantum implementation.
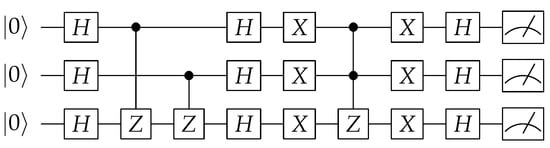
Figure 1.
Quantum circuit implementing Grover’s algorithm.
While our paper will not delve into the mechanics of Grover’s algorithm, the circuit can serve as a general example of how quantum circuits operate. There are various ways to implement the quantum circuit for Grover, including the use of different types of gates. In this example, we utilize the implementation proposed in [8], which involves the use of Hadamard and Pauli-Z gates.
Each line in Figure 1 represents a qubit, with processing beginning from the left side of each line. As we move towards the right, gate operations are applied on the qubits. Although not shown, the gates are applied at specific time intervals, which are determined based on the quantum hardware being used. The time step of choice is determined by adding some buffer time to the duration of the slowest gate operation.
In the first time interval, a set of Hadamard gates is applied to three qubits simultaneously. In the second interval, no operation is performed on the second qubit to avoid altering its information. Meanwhile, the top qubit acts as a control for a Pauli-Z gate applied on the bottom qubit. This results in entanglement between the top and bottom qubits. In the third time interval, the top qubit proceeds, while the middle qubit acts as a control for a Pauli-Z gate applied on the bottom qubit. Following a series of Hadamard and Pauli-X applications, the top and middle qubits control a Pauli-Z gate applied on the bottom qubit. Notice that the gate at this step involving three qubits would be mapped into two-qubit gates in the hardware implementation. Finally, after the last set of Pauli-X and Hadamard applications, the output is measured at the far end of each qubit line. The measurement process returns the system to the classical domain.
Next, we discuss specific security implications of quantum circuits. Our goal is to protect a quantum circuit from an adversary such that, even if the adversary had access to the circuit, it would not be able to utilize the circuit. The existing methods based on physically unclonable functions and obfuscation cannot target this application; hence, we introduce a new technique.
2. Previous Work on Quantum Hardware Security
In this section, we review two approaches in the quantum hardware security domain, and both are related to the problem that our paper is targeting.
2.1. Quantum Physically Unclonable Functions (QPUFs)
A QPUF circuit can be utilized to provide a unique signature that cannot be replicated by another QPUF circuit and a quantum computer that it is run on. Such uniqueness comes from the errors inherent in qubits, gates, and measurement circuitry for a particular quantum computer. We have shown that it would be possible to observe that such a signature is consistent for a specific quantum hardware and different from other hardware.
Phalak et al. [9] provide a practical implementation of a quantum PUF, as shown in Figure 2. Readers could also refer to [10] for a theoretical treatment of the topic. Furthermore, Pirnay et al. [11] extend the idea in [9] to have multiple cycles of rotation gates instead of a single cycle, as shown in Figure 3. Following [10], Kumar et al. [12] present an implementation via a regular and entangled configuration utilizing Pauli-X, Pauli-Z, and gates, as shown in Figure 4.
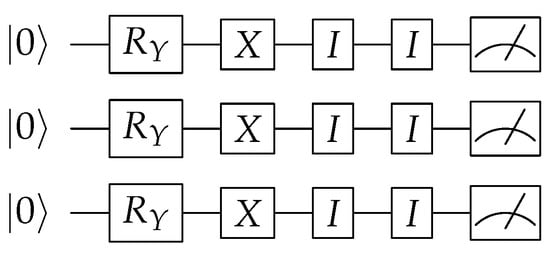
Figure 2.
QPUF implementation from [9]. There can be multiple I stages; only two such stages shown here for brevity.
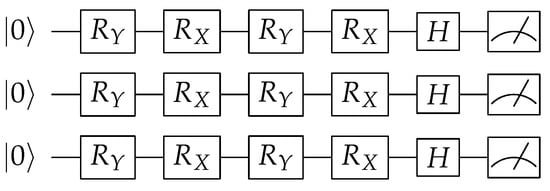
Figure 3.
QPUF implementation [11] uses multiple and stages with different rotation degrees; only two shown.
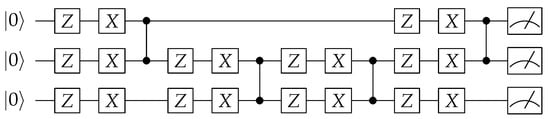
Figure 4.
Another QPUF implementation [12] uses multiple Pauli-Z, Pauli-X, and (controlled Pauli-Z) stages; only three qubit versions shown.
While a QPUF provides a unique signature and can have interesting security applications, it does not as is target the concern where an adversary may have access to a quantum circuit and obtain results akin to what the original owner would. In the next section, we review another method that more closely targets the main concern of this paper.
2.2. Quantum Obfuscation
Obfuscation can be a closer solution against our main concern of an adversary stealing our unique quantum circuit. Alagic and Fefferman [13] define obfuscation simply as encryption of functionality. In that work, it is shown that a quantum obfuscator cannot obfuscate a classical circuit. Herein, we focus on quantum obfuscating a quantum circuit. To enable the obfuscation, additional quantum gates can be inserted to obfuscate the original design. Insertion of additional gates corresponds to encrypting the circuit. Then, when the quantum circuit is actually run, the newly added gates are removed. This step is decryption. The adversary does not know which gates should be removed to obtain the correct circuit even when they have access to the encrypted circuit and thus would waste a great deal of time to remove gates by trial and error to identify the correct circuit. In addition to time lost by such trial and error, the adversary would have exponentially fewer chances of figuring out which result is correct as only one would be the correct one out of the many an adversary may try. Figuring out if a given output is correct may not be an easy choice.
Suresh et al. [14] propose one such quantum obfuscation example. Here, gates are inserted strategically to ensure that the output of the circuit would be different than what is intended. insertion is the encryption step. The user or the quantum computer keeps track of where the gates are inserted and removes them before execution. Hence, the input/output relationship is kept intact while the obfuscated circuit cannot be directly used. An example of this obfuscation method is shown in Figure 5.
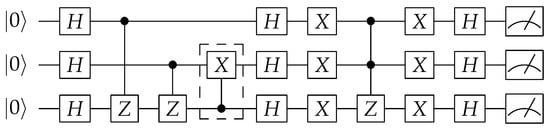
Figure 5.
Obfuscated version of Grover’s algorithm. location decided to ensure output is different than original.
Keeping track of specific gate locations, dropping them before execution may seem cumbersome to some users. Hence, in the next section, we introduce a more efficient alternative mechanism.
3. Quantum Logic Locking
In this section, we introduce quantum logic locking, a new technique targeting the main problem of this paper. Logic locking itself is not new as is; it was proposed for single flux quantum (SFQ) type circuits. These quantum circuits, however, implement classical digital electronic circuits but use superconducting devices. Hence, they are not considered universal quantum computers. Thus, logic locking for SFQ devices cannot target qubits that rely on transmon, trap-based, or spin implementations, which are projected to provide further enhancements in this area towards enabling universal quantum computing. For quantum circuits that rely on the aforementioned superconducting qubits, we introduce herein novelties, such as new ancillas, replacement of control gates, and insertion of dummy control gates.
3.1. Security Problem
Quantum circuit development for certain applications is sometimes a very difficult step requiring deep theoretical knowledge. For example, a novel quantum algorithm can be invented that targets a specific problem. One may then want to keep the quantum circuit implementation of such an algorithm a secret. However, an adversary may gain access to it and start using it elsewhere despite the presence of state-of-the-art software security techniques. Having access to the results of such a stolen quantum circuit provides the adversary undeserved benefits and causes significant monetary damages to the original owner (defender). Quantum logic locking as proposed herein has the potential to provide a remedy for this concern.
3.2. Steps of Quantum Logic Locking
We provide a method where, in addition to having access to the circuit, a defender or the quantum computer stores a secret key separately and without which the results of the quantum circuit become useless. The secret key in particular controls a set of special added ancilla qubits that we name “lock ancilla qubits”.
A user first determines the desired security complexity level for a given quantum application or circuit. Then, the user inserts the required number of lock ancilla qubits for the desired security complexity level. Following this step, we replace specific Pauli-X, Pauli-Y, Pauli-Z, Hadamard, Rotation, or Phase-Rotation gates with controlled versions. Here, control is one of the lock ancillas with value if the gate should be applied. This circuit change is summarized in Figure 6.
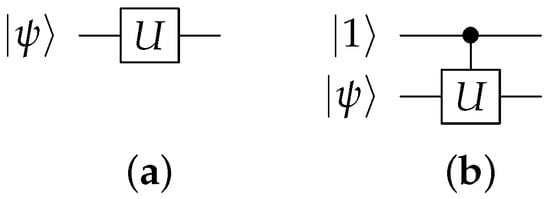
Figure 6.
(a) Original gate in quantum circuit, where U is a unitary. (b) A controlled version of the same gate. Control signal determines whether or not the gate is applied.
Notice that controlled versions of certain gates may not be readily available. For example, a controlled version of Pauli-Z or Hadamard may be lacking. However, we use a transformation such as in Figure 7 or Figure 8 to enable them.
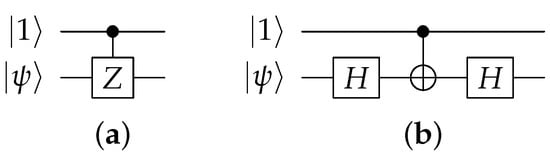
Figure 7.
If a native controlled version of a gate does not exist, a conversion is usually feasible. For example, a controlled version of the Pauli-Z gate in (a) can be implemented with Hadamard and gates as in (b).
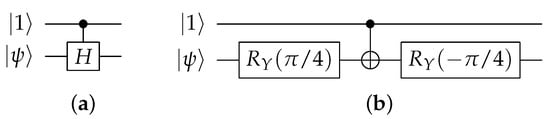
Figure 8.
Even a controlled version of the common Hadamard gate in (a) is feasible as shown in (b) using gates and a .
Next, we can also insert dummy control gates to select active qubit lines, where the control line is one of the lock ancillas with value and the controlled line is one of the active qubits. This is illustrated in Figure 9. Then, we mix the order of lock ancilla qubits randomly and store the and order of them separately from the quantum circuit. During regular operation of circuit, we apply the stored lock ancilla qubit inputs, perhaps from a separate memory storage, before running the quantum circuit.
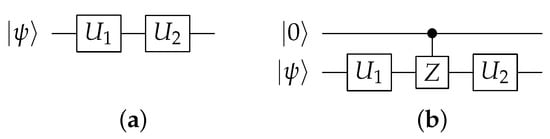
Figure 9.
A dummy control gate can also be inserted. and are unitaries. (a) Original circuit. (b) By keeping the hidden key as , Pauli-Z gate is not applied and acts as a dummy gate. Otherwise presence of Pauli-Z alters circuit output to deter an attacker.
A compact representation of the QLL scheme is shown in Figure 10. Figure 11 illustrates a logic-locked version of the Grover circuit.
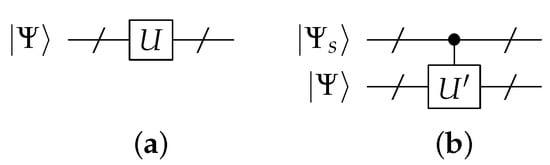
Figure 10.
(a) Original circuit. Unitary may take multiple inputs and compute multiple outputs. (b) Secret key qubits added and some gates are replaced with controlled versions.
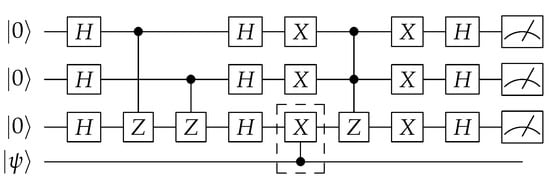
Figure 11.
Logic-locked version of Grover’s algorithm.
We introduce further circuits to show the generality of the proposed methodology. One of the most promising quantum algorithms has been Shor’s algorithm. Inspired by [15], we implement a modulus of multiple circuits, as shown in Figure 12. We had to modify our circuit, however, to make this computation work correctly. Unlike [15], we apply the swap operation between the two qubits that are measured eventually as the most significant bits in the result instead of the two qubits that are measured as the lowest significant bits. In particular, the circuit takes 4th multiple of 7 in modulus 15. A logic-locked version is shown in Figure 13.
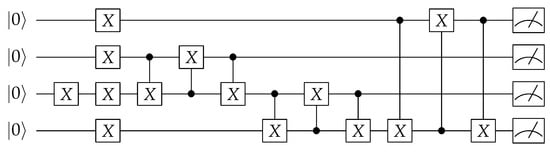
Figure 12.
Circuit for calculating modulus of a multiple.
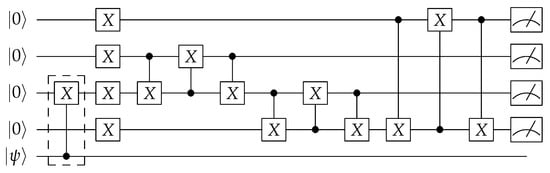
Figure 13.
Logic-locked version of circuit for calculating modulus of a multiple.
Circuits so far could be implemented on a 5-qubit quantum computer including their logic-locked variants. We implement modulus of exponentiation circuit and its logic-locked version in Figure 14a,b, respectively, on a 7-qubit computer computer. The circuit computes 3rd exponent of 11 in modulus 15.
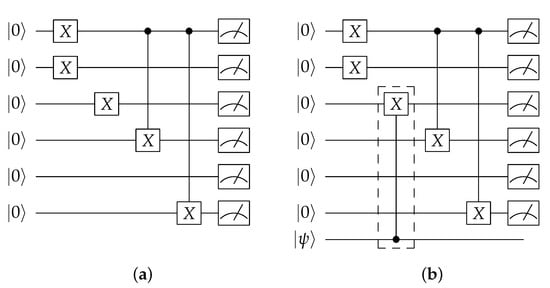
Figure 14.
(a) Circuit for modulus of exponentiation. (b) Logic-locked version of circuit for modulus of exponentiation.
3.3. Determining Desired Security Complexity Level
Depending on the desired security level, the number of lock ancillas can be adjusted. Lock ancilla qubit count relates to the security level exponentially. For example, adding only one lock ancilla qubit indicates quantum circuit should be executed by an adversary twice as many times as having no lock ancilla qubits. That is because the adversary should first assume the lock ancilla has value and in the second execution assume . Notice that, for each choice, there can be thousands of executions on the quantum computers to average out noise inherent in the system.
Having 10 lock ancilla qubits indicates quantum circuit should be executed by an adversary times the original amount! Depending on how much time a defender desires an adversary to waste, the number of lock ancillas can be increased. In addition to such execution time increase, an adversary can also not determine which solution is the correct one from all possible exponential outcomes.
When replacing select gates with controlled versions, one should first determine which gates have a controlled version available in the target quantum system. If a direct version is not available, alternative implementations can be considered, as discussed previously. From the available gates, a user selects from various qubit lines until the target security complexity level is met.
Inserting dummy controlled gates is handled by determining which qubit lines have more slack (empty time steps where no operation or idle operation takes place). After determining exact time slots available, we determine available controlled gate versions in the target quantum system.
Quantum read-only memory can be used to store secret keys and information on chip. A practical implementation of quantum read-only memory is provided in [16]. Alternatively, keys can be stored in a classical but disjoint storage device as opposed to where the circuit is kept.
Reliability Implication. Converting gates to a controlled version is subject to increased error rates. However, we only make such conversions to few gates; hence, this error would easily be negligible. It would be beneficial to avoid converting many gates from the same qubit to their controlled versions and disperse such conversion across multiple qubits. A final verification step could be utilized to ensure introduced gate errors are tolerable. A practical implementation could seek to limit number of conversions to a parameter, such as maximum two gate conversions per qubit line.
4. Experimental Results on Quantum Logic Locking
We conduct our experiments on real quantum computers. In particular, we use ibmq_belem for our 5-qubit experiments and ibmq_berth for our 7-qubit experiments, both in fairshare mode using 1024 shots. The ibm_belem quantum computer supports a quantum volume of 16 with 2.5 k circuit layer operations per second. At the time of execution, it displayed a T1 of 88.62 s, T2 of 91.89 s, error probability of , readout error probability of , frequency of 5.22 GHz, and gate time of 539 ns. Furthermore, ibm_belem has a T-shape topology for the qubits, and, enumerating the qubits starting with 0, qubit 1 (Q1) is connected to three other qubits, Q3 is connected to two other qubits, and the remaining qubits have only one neighboring qubit. The ibmq_berth quantum computer supports a quantum volume of 16 with 2.5 k circuit layer operations per second. At the time of execution, it displayed a T1 of 166.75 s, T2 of 118.16 s, error probability of , and readout error probability of . Furthermore, ibm_berth has an H-shape topology for the qubits, and, enumerating the qubits starting with 0, Q1 and Q5 are connected to three other qubits, Q3 is connected to two other qubits, and the remaining qubits have only one neighboring qubit.
We transpile the circuit into , , and square root of gates. Figure 15 shows two results with 1024 shots each, one with and one without the correct lock ancilla inputs applied. The histogram shows that users would obtain a significantly different result by running the quantum circuit if they do not know the correct keys. For example, incorrect keys would provide `100’ and `111’ as output, whereas the correct outputs are `101’ and `110’. As one can see, the results are completely different when the circuit is run with the correct keys. This implies that having access to the circuit without the correct key is useless.
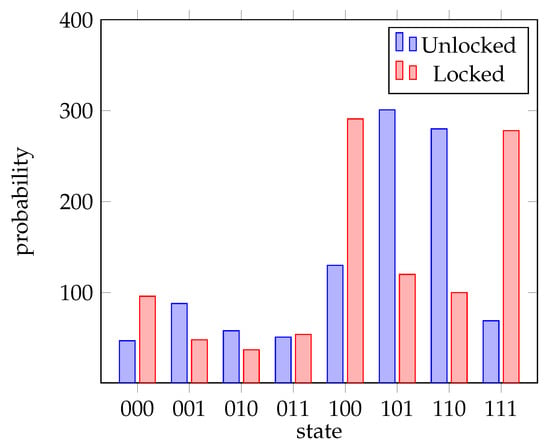
Figure 15.
Experimental results for Grover circuit. Unlocked results show the correct output from the circuit, whereas locked results show what happens if input keys are not applied.
In Figure 16, a locked circuit with the correct lock inputs yields `1101’, whereas the locked version yields `1111’. Similarly, in Figure 17, a locked circuit with the correct lock inputs yields `1010’, while the locked version provides `1011’. Again, these results imply that having access to and running the circuit without the correct key is useless as correct results can only be attained with correct keys.
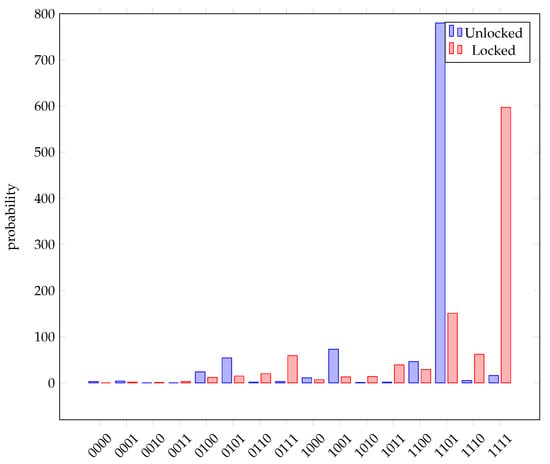
Figure 16.
Experimental results for modulus of multiple. Unlocked results show the correct output from the circuit, whereas locked results show what happens if input keys are not applied.
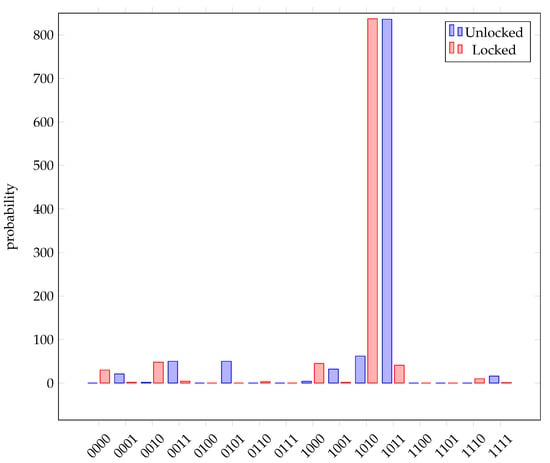
Figure 17.
Experimental results for exponentiation of multiple. Unlocked results show the correct output from the circuit, whereas locked results show what happens if input keys are not applied.
5. Conclusions
We have reviewed the existing methods in quantum hardware security, namely QPUFs and obfuscation. We have also introduced quantum logic locking for gates used in universal quantum computing. While QPUFs can identify a given quantum computer and obfuscation enables encryption of a given quantum circuit, quantum logic locking presents an alternative security measure by reserving only a few additional qubits. We have experimentally demonstrated with multiple examples that having access to a quantum circuit that utilizes the logic locking methodology we introduce here is not sufficient to use that circuit. Only when users also know the correct key can they use the circuit to obtain meaningful results. The proposed logic locking methodology is also more efficient as compared to the existing methods, which require keeping track of gate locations and dropping such gates before execution.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Conflicts of Interest
The author declares no conflict of interest.
References
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Mermin, N.D. Quantum Computer Science; Cambridge University Press: Cambridge, UK, 2007. [Google Scholar]
- Yanofsky, N.S.; Mannucci, M.A. Quantum Computing for Computer Scientists; Cambridge University Press: Cambridge, UK, 2008. [Google Scholar]
- Rieffel, E.G.; Polak, W.H. Quantum Computing; MIT Press: Cambridge, MA, USA, 2014. [Google Scholar]
- Topaloglu, R.O. Fast Introduction to Quantum Computers. In Wiley Encyclopedia of Electrical and Electronics Engineering; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the 28th Annual ACM Symposium on the Theory of Computing (STOC), Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Bennett, C.H.; Bernstein, E.; Brassard, G.; Vazirani, U. Strengths and Weaknesses of Quantum Computing. SIAM J. Comput. 1997, 26, 1510–1523. [Google Scholar] [CrossRef]
- Figgatt, C.; Maslov, D.; Landsman, K.A.; Linke, N.M.; Debnath, S.; Monroe, C. Complete 3-Qubit Grover search on a programmable quantum computer. Nat. Commun. 2017, 8, 1918. [Google Scholar] [CrossRef] [PubMed]
- Phalak, K.; Saki, A.A.; Alam, M.; Topaloglu, R.O.; Ghosh, S. Quantum PUF for Security and Trust in Quantum Computing. IEEE J. Emerg. Sel. Top. Circuits Syst. 2021, 11, 333–342. [Google Scholar] [CrossRef]
- Arapinis, M.; Delavar, M.; Doosti, M.; Kashefi, E. Quantum Physical Unclonable Functions: Possibilities and Impossibilities. Quantum 2021, 5, 475. [Google Scholar] [CrossRef]
- Pirnay, N.; Pappa, A.; Seifert, J.P. Learning classical readout quantum PUFs based on single-qubit gates. Quantum Mach. Intell. 2022, 4, 14. [Google Scholar] [CrossRef]
- Kumar, N.; Mezher, R.; Kashefi, E. Efficient Construction of Quantum Physical Unclonable Functions with Unitary t-designs. arXiv 2021. [Google Scholar] [CrossRef]
- Alagic, G.; Fefferman, B. On Quantum Obfuscation. arXiv 2016. [Google Scholar] [CrossRef]
- Suresh, A.; Saki, A.A.; Alam, M.; Topaloglu, R.O.; Ghosh, S. A Quantum Circuit Obfuscation Methodology for Security and Privacy. In Proceedings of the Workshop on Hardware and Architectural Support for Security and Privacy (HASP’21), Virtual, 18 October 2021; Association for Computing Machinery: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- Markov, I.L.; Saeedi, M. Constant-Optimized Quantum Circuits for Modular Multiplication and Exponentiation. arXiv 2012, arXiv:1202.6614. [Google Scholar] [CrossRef]
- Phalak, K.; Alam, M.; Ash-Saki, A.; Onur Topaloglu, R.; Ghosh, S. Optimization of Quantum Read-Only Memory Circuits. In Proceedings of the 2022 IEEE 40th International Conference on Computer Design (ICCD), Olympic Valley, CA, USA, 23–26 October 2022; pp. 117–123. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).