Abstract
Security remains a top priority for those users in the hotel, even with the advent of innovative technological advances. This is because many tragic incidents, such as theft and crime, have occurred with unrestricted access. This paper proposes an intelligent door access system that would allow hotel guests to authenticate into their rooms without resorting to traditional closeness access methods. Therefore, research was conducted to solidify the understanding and refine the capabilities of the proposed system. This project aims to promote high-security aspects access system technology, which is Near-Field Communication with the use of application that have the function of simulated smart keys for explicit validation access. A Host-Card Emulator opens the opportunities for efficient financial benefit and the launch of a protective mechanism in the post-pandemic period. The suggested method was statistically and analytically accessed on hotel guests and staff from various hotels in Malaysia. The proposed system is a contactless NFC access control system that employs smartphone Host Card Emulation application technology to reduce the need for appropriate physical access, enhance security, and publicize the use of mobile access systems in the hospitality industry.
1. Introduction
Security is acknowledged as one of the most vital factors and words in the world for people [1] and it is supposed to be supplied anywhere in various businesses, making it the first concept that should be offered in every location with fulfilment and asset. Furthermore, security is a primary goal in the hotel sector because it is significant in a variety of additional fields, and sectors [2].
Hotel industries are considered the top contributors to the national economy. Hotels have become an important key growth in industrial economic assistance. As a result, the hotel’s maintenance, and the best experience is a major focus for both the visitors and representatives in the area [3]. Most people believe that the technological limits and shortcomings in hotels throughout global, which is assumed unusual, mainly in the modern market and the transformation potential of New Technologies. The hotel access points, and their management are one of the most significant components in hotels that are responsible for security and management efficiency [4].
Access points management systems apply a consistent approach to protect and control the access points, such as hotel doors placed in the staff or in the background of a hotel, or entryways for guests located in elevators or room doors in the hotel industry. With the advent of smartphones and technological advancement, technology is now required for many routine daily chores. The survey poll reveals that many hotel managers and visitors desire and call for further implementations of cutting-edge technologies in lodging [5].
Moreover, the epidemic of COVID-19 has resulted in basic and dramatic changes in the hotel industry [6] with a pessimistic effect. The most considerable of these are hotel guests’ anxieties about social distancing, cleanliness, and well-being. Since COVID-19 is a disease that spreads through the air, it is inevitable that the virus would adhere to objects and migrate through physical touch. In hotels, there are several doorknobs and switches that might be pressed, increasing the likelihood of contracting an infection. Consequently, the recent ordinary for the potential hotel industry has transformed to “high-tech” to “low-touch” [7]. NFC offers exceptionally innovative applications that are utilized smartphone Host Card Emulation (HCE) running in Google Android operating systems only in different fields and applications that underline security levels of contactless activities. Most NFC frameworks incorporate a label peruser, which ought to have the option to peruse any inactive or dynamic tag to trade information or the previous. There are three kinds of tasks or as known to be conceivable application situations, which incorporate read/compose labels, distributed labels, and the card emulator [8]. Each type’s determinations are point by point and represented to give a worked-on clarification in Figure 1.
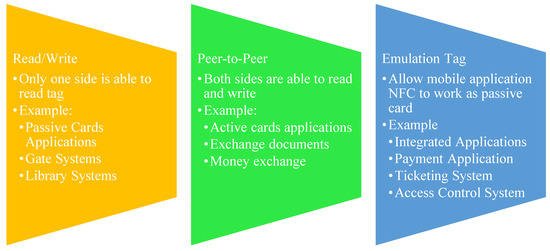
Figure 1.
NFC Components Diagram.
1.1. Problem Statement
With the advancement of technologies, security is the most significant factor and concept in the world [9]. It is vital to every industry. Security is physically determined with numerous troubles that could prompt numerous sad mishaps and issues, notwithstanding the bother caused at the hotels’ access point in the hospitality industry [10,11]. As we all know, the hotel and hospitality sectors are essential for the nation’s economy. As a result, it is critical to take the necessary steps to maintain the hotel and provide the world’s best experience for guests and staff in the sector. However, Malaysia’s hospitality and hotel industries have been severely impacted by the pandemic [12]. Moreover, COVID-19 significantly affects the hotel industry, reducing tourism to zero because of the rising number of cases. The hospitality sector is severely impacted as the infection will stay on put protests and is moved by contacting. Many actions need physical contact at the hotel. These measures will increase the probability of the virus infecting humans.
An intelligent door system could be a viable method to solve various problems in the hotel industry. In the hotel business or other fields, the suggested innovative door system technologies allow entry into the room without needing a physical key or card. Next, a face recognition system and the biometric system were introduced, and they provided multiple benefits relating to higher security; the other existing technologies are RFID, card verification, and authentication of digits to provide low-cost security. However, the existing technologies only focused on security services. NFC was proposed in 2015 as a new technology to control access points. Due to the COVID-19 epidemic, there is an urgent need for a contactless technique that uses NFC technology to control access management. In the review of past studies, even in the year 2021, there are several limits related to the lack of mobile applications created expressly to manage access points since prior studies showed more challenging data management algorithms to regulate the removal or restoration the data of the users.
Furthermore, the expense angle is predominantly overlooked because of the great degree of twofold security or incorporated frameworks that require high administration levels, trailed by the Coronavirus’ misconception of the fundamental prerequisite for contactless arrangements.
1.2. Research Objectives
RO1: To ensure hotel guests experience a high degree of security in the hotel.
RO2: To obtain a high level of innovation operation at a lost cost by eliminating the physical card in the hotel.
RO3: To innovate technology defence against contact-based viruses in the hotel.
RO4: To give hotel guest a comfortable contactless experience in the hotel.
1.3. Research Hypotheses
RH1: The NFC authentication technique will improve security in the hotel.
RH2: The cost of operating will be decreased by using an NFC smartphone in the hotel.
RH3: Contactless NFC smartphones will remove the pandemic infection in the hotel.
RH4: Using an NFC smartphone will reduce the user’s effort and actions in the hotel.
1.4. Value Creation
By providing hotel guests with a hassle-free and excellent experience, even more interesting is using NFC in a smartphone’s application technology. It was found that hotel visitors want to use smartphones as hotel technology to create novel experiences as frequently and as often as they need a mattress. NFC host-card emulation technology was creatively and distinctively employed to create a mobile application that, for the first time in Malaysia’s hotel industry, enables authentication. Additionally, the application was created to be a free anti-contagious tool for all smartphones, allowing users to participate in creating a defence plan against the spread of the COVID-19 virus using basic contactless technology.
2. Literature Review
The COVID-19 pandemic nearly put an end to global economic activity [13]. The hotel business has undergone significant and significant modifications because of the COVID-19 outbreak [14]. In order to guarantee the wellbeing and safety of their workforce and clients in addition to increase the number of people who are willing to visit their establishment, hotel businesses are anticipated to get major adjustments to their businesses in the pandemic industry climate [15].
As we all know, the hotel business is a crucial contributor to the national economy, and hotels have become a substantial significant rise in industrial and financial assistance. As a result, preserving the hotel and delivering the most fantastic experience for visitors and employees in the area are top priorities. While just one-third of people want to move to a destination and vacation in a hotel in the coming months during the pandemic’s peak phase, more than half of people do not want to stay in hotels or do not want to take a trip to a destination and remain in a hotel anytime soon [16]. These statistics provide credence to the idea that consumers are still hesitant to book a hotel stay and go to a destination. Many hotel businesses rely deeply on the rising mandate for customer services and goods to sustain themselves. The operating leverage in the hotel industry is powerful due to serious operational fees. Therefore, it is crucial to ascertain what will encourage hotel visitors to book again and doing so calls for extensive research [17]. The industry and academia need behavioural and operational research in hotel advertising and organization to help direct hotel during the COVID-19 epidemic.
Most hotel guests, or 70.42%, think using different techniques can help solve this problem. As a result, the “high-tech” and “high-touch” and “high-tech” and “low-touch” paradigms for the future of hospitality have changed. As a result, during the epidemic, a potentially innovative service was a touchless, flexible, and adjustable automated solution that was enabled by technology. Using contactless technology, hospitality businesses can improve strategies and customer services to provide importance and defend customers while reducing human-to-human contact. The core of contact-free services in hotel is using advance technology to avoid excessive bodily contact, resulting in the most secure service interaction for hotel guests and hotel staff. The report claims that contactless technology will significantly alter the hospitality industry.
Additionally, the hospitality sector needs help managing access points and implementing integrated innovation over time. As a result, numerous methodologies and implementations are rating from all existing innovation access systems that deliver ease to user. Unfortunately, numerous potential catastrophic flaws in the technologies employed have been identified, and they can be summed up as follows:
- Execution and support service is expensive
- It is difficult to inspect and simply access the database
- Calls for manual engagement with the apparutus
- Requires manual effort of users for fingerprint verification
- No high-level security
Many intelligent door system technologies are listed, explored, and compared using each technology’s strengths and weaknesses. This enables the suggested system to be confirmed based on the drawbacks of the competing technology in Table 1.

Table 1.
Comparison between Existing and Future Access System.
The hospitality industry is known as the major contributor to the economic growth in Malaysia. However, according to a market analysis study conducted in 2021, the mobile application in smart doors is not yet implemented as shown in Table 2.

Table 2.
Features of current door systems in Malaysia.
Table 2 shows that many brands offer door access systems, but NFC is not used because Bluetooth is Malaysia’s only widely used technology. Additionally, because the approach is expensive and the technology employed primarily demands device contact, it is not easy to adopt in hotels. Because the hotel has numerous room doors, it is impossible to execute this method.
3. Methodology
The triangulation method will be used in the project research to reply to how and why inquiries more effectively from the target respondents as shown in Figure 2. Data will be gathered for the survey, interview, and experiment using Google Forms [27,28,29,30,31,32,33,34,35,36] and the strategy detailed in Table 3.
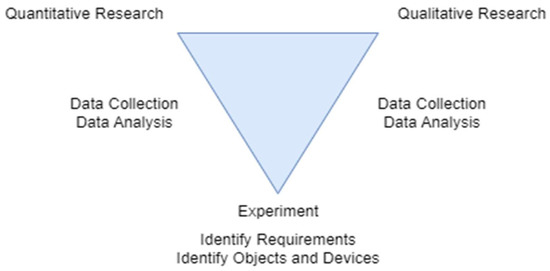
Figure 2.
Triangulation Method.

Table 3.
Research Methodologies.
Surveying the quantitative data collection was going to be used to gather the general facts and information. Randomly chosen respondents from the public from varied backgrounds were to be included in this poll. Responses to the NFC access system will vary depending on the respondents’ backgrounds. Quantitative data will be gathered via Google Forms utilising the Likert Scale Inquiry and Multiple-Choice Questions to ensure the accuracy of each question. After discovering the universal explanatory analysis, the qualitative data collection, or interview, will start. In other words, conducting interviews using Google Forms would wrap up the qualitative approach. The interview will provide information on the analysis and interpretation of quantitative research. After match expectations, all the data and information would then be summarised and described [27].
The questionnaire will be designed into four sections such as demographic, experience of using the access system, problems encounter using an access system, and user feedback and suggestion. The first section is demographics. It is intended to assist the project in visualizing the respondents based on their background and lifestyle preferences. The second section is to collect the respondent’s information about the experience of using the access system. Next, the section is to assemble the data on the problems they faced when using an access system. Lastly, it will allow respondents to express their feedback and suggestions for the proposed system.
The questions for interviewing will be designed in three sections like the questions in the questionnaire. The sections are divided into demographic, experiences and problems in the access system, and feedback and suggestions. The first section is to get the respondent’s information about their background. Next, it is designed to identify the experiences and problems in using the access system in the hotel. Finally, the last section will be collecting the system requirements from the interviewees [37].
There will be 33 survey respondents and 10 interview respondents in the actual data gathering. To answer the questionnaires, all respondents were picked at random. People who commonly use the access system method are invited to participate in an interview and survey to share their opinions on the use of NFC [37].
This study examines an intelligent, innovative hotel door system that uses contactless technology and cutting-edge NFC technology explicitly designed for Malaysian hotels. This system can be readily operated with smartphone applications. Due to the use of virtual NFC cards in smartphones rather than physical papers, which are expensive to produce and easily forgotten or lost, The software maintenance and data management application would be free and extremely convenient [38]. It would also eliminate any possibility of crucial loss. The mobile application was created to eliminate the need for physical effort when unlocking doors because the use of NFC [38]. As seen in Table 4 and Figure 3, the necessary tools must be used to implement a prototype of the suggested system.

Table 4.
Hardware and Software Requirements [39].
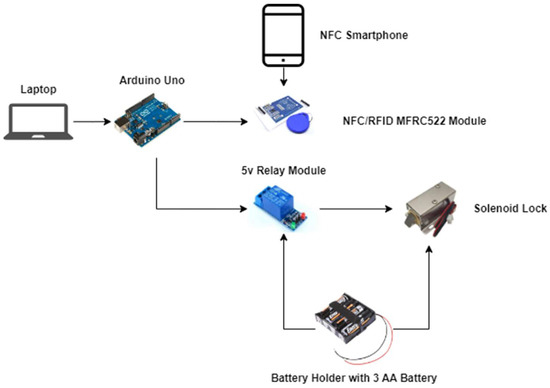
Figure 3.
Devices’ Diagram.
3.1. Arduino Uno
The ATmega328p-based Arduino Uno is a microcontroller board. It is a straightforward, minimal expense open-source prototyping stage that might be extended to incorporate equipment and programming. It has 14 computerized I/O pins (6 PWM yields), six simple data sources, a 16 MHz earthenware resonator, a USB connector, a power connector, and a reset button. Everything expected to help the microcontroller is incorporated. We should either utilize a USB link to connect it to a PC or an air conditioner to-DC connector to drive it. The Arduino circuit associates the undertaking programming and equipment parts.
3.2. MFRC 522 NFC/RFID Module
The MFRC522 includes an inbuilt transmitter that can drive a reader/writer antenna without the requirement for active circuitry to connect with ISO/IEC 14443 A/MIFARE cards and transponders. The receiver module offers a trustworthy and effective solution for demodulating and decoding signals from ISO/IEC 14443 A/MIFARE compliant cards and transponders. In addition, the digital module handles the complete error checking (parity and CRC) and framing for ISO/IEC 14443 A. Products in the MF1xxS20, MF1xxS70 and MF1xxS50 families can all be used with the MFRC522. The MFRC522 uses MIFARE better transmit speeds of up to 848 kBd in either direction and facilitates contactless communication.
3.3. Relay Module
Computer boards known as relay boards include various relays and switches. They have input and output terminals for controlling the supply of voltage. Each onboard relay channel on relay boards is individually programmable and has real-time control. It is a single channel, 5 V relay. The relay’s open interface can handle a maximum load of AC 250 V/10 A and DC 30 V/10 A. The trigger current is 5 mA, and the working voltage is DC 5 V. A high or low level could be set by a connection on each relay channel. It is an architectural mistake because the relay won’t move if the control line isn’t connected. Status indicators for the 1-channel relay and power (green) are included (red). It is practical that the terminal block can link all module-size interfaces directly.
3.4. Solenoid Lock
The solenoid lock, which ultimately decides whether to grant or refuse the authenticated person entry to the restricted area, is controlled by the relay driver board. It is durable, long-lasting, and energy-efficient, and it has a long lifespan. The lock outperforms other varieties in terms of anti-theft and shockproof construction. After the power is on and the wires are connected, the electronic lock will automatically open and close the door. The plunger resets the latch, which relocks the door when the solenoid’s power source is cut off.
A circuit diagram is required for the graphical electrical association since the chart of the gadgets doesn’t obviously show the electrical wiring and request of the power supply. The electrical circuit schematic for the connection is shown in Figure 4.
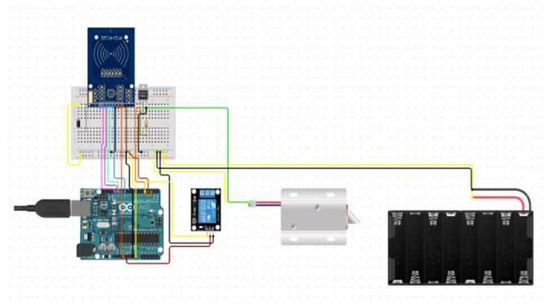
Figure 4.
Circuit Diagram.
Following database verification of the visitor or employee, the program enables users to sign up and log in using their login and password. At this point, the smartphone will simulate the NFC tag [40].
Direct access and authentication are possible using NFC Card Emulation of the application’s home page as shown in Figure 5; however the NFC capability needs to be turned on as shown in Figure 6 [9].

Figure 5.
Main Page.
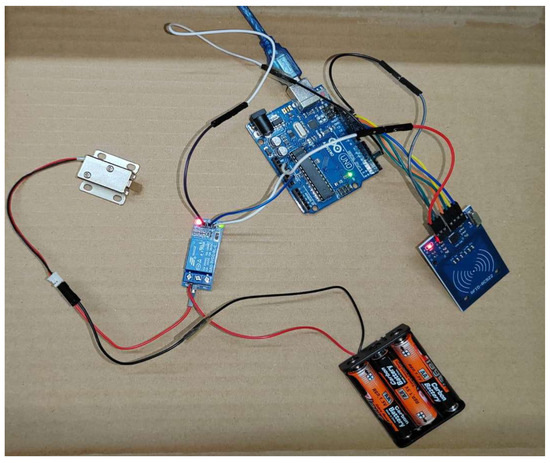
Figure 6.
Prototype Solution [32].
4. Findings and Discussion
Throughout gathering the responses on the questionnaire, a total of 33 responses are recorded. Some additional opinions and requirements are also collected from the respondents. After gathering an adequate number of responses, the analysis will then be accomplished to extract and transform the data from the questionnaire into useful information for further development of the proposed system. The analysis will be elaborated on in the following statements. Convenience sampling will be used in the quantitative study. Responses from random convenience sampling are a non-probability type of sampling utilised frequently in qualitative research in population studies. Convenience sampling for qualitative research is taken from people that are easy to contact or reach. The reason for using random convenience sampling responses is it is useful when used to generate a potential study objective. Besides that, it is popular because it is not costly, not time-consuming, and simplistic.
In Figure 7, the data shows that the respondents are mostly from Melaka, Negeri Sembilan, and Johor. Therefore, the research hotel is based in those states in Malaysia.
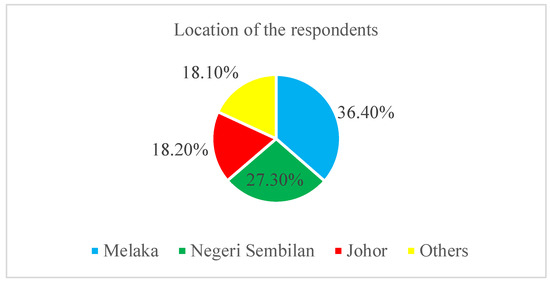
Figure 7.
Location of the respondents.
The problems encountered for using the current access system are increasing due to the traditional method and inconvenience. Besides that, the current access system does require high implementation costs. Figure 8 shows the number of respondents has faced the problem in the hotel.
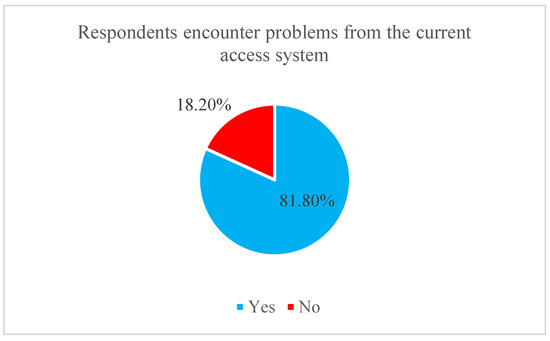
Figure 8.
The number of respondents who encounter a problem.
81.8% of the respondents encounter the problem from the current access system. While 18.2% of the respondents do not encounter the problem from the current access system. This can conclude that the current access systems have problems that require enhancing them.
The problems encountered by 81.80% of respondents are the key and the card being lost or damaged, the access system requiring manual and physical interaction, and the access system having low-level security and inconvenience. Hence, the solution is to develop an NFC access system, which allows users to use their smartphones to access the hotel room door. These can reduce the number of keys and cards lost and damaged, the access system is built to be a contactless access system and has a high level of security and convenience.
The respondents are excited to have a newly developed NFC access system in the hotel. The newly developed access system with the NFC function will improve the hotel industry business. The respondents agree to have an NFC access system in Figure 9.
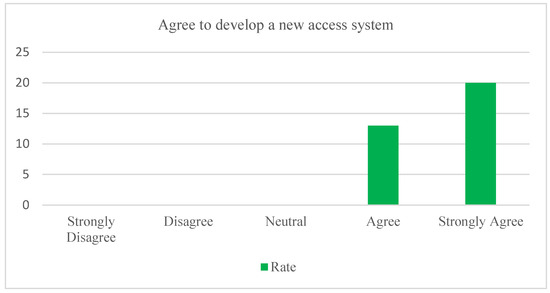
Figure 9.
Agree to develop a new access system.
As can be seen, a total of 100% of the respondents supported deploying the NFC access system in the real world. The comments are directly linked to the recommendation to use cell phones rather than the shown access system in Figure 9.
The impacts of using the NFC access system are NFC access system allows user to access their hotel room door without manual or physical interaction. NFC has a high level of security so that the user may feel more secure using the access system. Lastly, the NFC access system provides a contactless environment in the hotel. As a result, the NFC access system reduces the hotel guests’ and staff’s concern about the spread of the pandemic and enjoy a new technology environment in the hotel.
The respondents agree to use a single device gadget concept of access system in the hotel based on Figure 10.
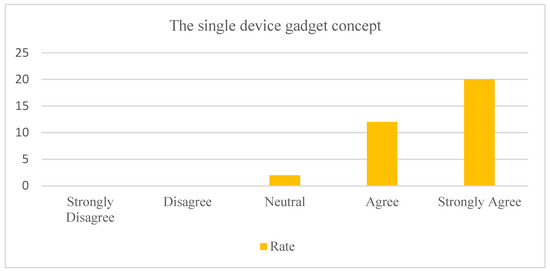
Figure 10.
Single device gadget idea.
There are 32 out of 33 respondents agreed to use the single device gadget idea. The reason is that it is convenient for users as the NFC access system only requires an NFC smartphone to access the hotel room in the hotel. As we know, the smartphone is one of the most important items in our life in this century. Therefore, the users will not lose and damage the traditional access system. They do not require to leave their belongings on the floor or have difficulty carrying a baby while opening the hotel room door as the NFC access system has unlocked the hotel room door once the NFC smartphone and the lock have detected each other within the range of 0–4 cm.
The respondents give their opinions about the NFC access system to help hotel industry business. There are plenty of similar opinions received from them in Figure 11.
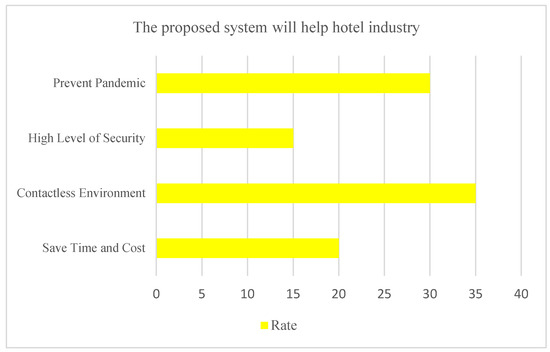
Figure 11.
Advantages of using the proposed system.
As the impressive total number from the opinions of the responses in Figure 11, those improvements are the project objectives which also means that the proposed system can prevent the pandemic based on the 30% responses. 15% of respondents mentioned that the security level will be high if the hotel uses the proposed system. Next, 35% of the respondents responded that the proposed system would provide a contactless environment in the hotel. Lastly, there is a 20% response with the usage of the proposed system can save time and cost.
The impacts of advantage are the NFC access system can reduce the target audiences’ concern such as the NFC access system does not require physical interaction. Thus, the users will not be affected by the pandemic. Moreover, the NFC access system has provided a high level of security and a contactless environment to the target audiences so they can feel safer and enjoy the contactless technology in the hotel [9]. Finally, the NFC access system helps the users to save time and costs as it is convenient for the user to unlock the hotel door at a certain distance and reduce the cost of making a new key or card due to the losses and damages.
5. Conclusions and Limitation
In this study paper, an intelligent NFC door access application is created for the first time in Malaysia, employing HCE innovation in the hotel industry to give high authentication with pocket-friendly pricing for management and users. On the other hand, with a sizable degree of user and human resources field convenience. In addition, the development has inspired the elimination of all interactions, resulting in a significant improvement in eliminating the contagiousness of pandemic. Although the project could provide a remarkable level of efficacy, safety, and convenience, it is unlikely to do so. The assessment study was restricted to online long-distance testing because of the pandemic lockdown; consequently, the test should be administered in a hotel site to obtain more detailed and more accurate real-time results, which would produce superior evaluation results. Future applications of this technology could include the medical sector, among others, as well as other industries. The future study will also explore the security impact. The project will be pushed into a more extensive sector of the economy with the potential to replace actual ID cards completely. Besides that, the project will employ NFC encryption that requires a decryption key for authenticity verification.
Author Contributions
Conceptualization, P.S.J. and P.S.B.; methodology, P.S.J.; validation, P.S.J. and K.Y.P.; investigation, P.S.B.; writing—original draft preparation, P.S.B.; writing—review and editing, P.S.J., P.S.B. and K.Y.P.; supervision, P.S.J.; funding acquisition, P.S.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not Applicable.
Informed Consent Statement
Not Applicable.
Data Availability Statement
All data is available inside the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Atallah, Z.; JosephNg, P.; Phan, K. JomNFC: Zero Effort Intelligent Access System. In Proceedings of the 2021 Innovations in Power and Advanced Computing Technologies (i-PACT), Kuala Lumpur, Malaysia, 27–29 November 2021; pp. 1–6. [Google Scholar]
- Atallah, Z.; JosephNg, P.; Phan, K. JomMedicMinder: Live or Dead. In Proceedings of the 2021 IEEE Symposium on Computer Applications & Industrial Electronics (ISCAIE), Penang, Malaysia, 3–4 April 2021; pp. 100–105. [Google Scholar]
- Chze, N.; Markom, M.A.; HuI, O.X.; Chin, W.T.; Vern, K.Y.; Tan, E.S.M.M.; Nordin, N. Check-In Location System Using NFC Technology. In Proceedings of the International Conference on Man Machine Systems (ICoMMS 2021), Perlis, Malaysia, 19–20 October 2021; pp. 1–9. [Google Scholar]
- Atallah, Z.; JosephNg, P.; Phan, K. JomMobileKey: Opening Business Sense During Covid19 Pandemic. J. Telecommun. Electron. Comput. Eng. JTEC 2022, 14, 7–14. [Google Scholar]
- Shabani, M.N. A Review of Cyber Security Issues in Hospitality Industry. Adv. Intell. Syst. Comput. 2020, 1230, 482–493. [Google Scholar]
- Hao, F.; Xiao, Q.; Chon, K. COVID-19 and China’s hotel industry: Impacts, a disaster management framework, and post-pandemic agenda. Int. J. Hosp. Manag. 2020, 90, 102636. [Google Scholar] [CrossRef] [PubMed]
- Hao, F. Acceptance of contactless technology in the hospitality industry: Extending the unified theory of acceptance and use of technology 2. Asia Pac. J. Tour. Res. 2021, 26, 1386–1401. [Google Scholar] [CrossRef]
- Singh, N.K. Near-field Communication (NFC). Inf. Technol. Libr. 2020, 39, 1–14. [Google Scholar] [CrossRef]
- Sadiq, M.S.; Siddiqui, M.S.; Haque, M.I. Real Time Door Security System With Three Point Authentication. J. Mech. Contin. Math. Sci. 2020, 6, 53–64. [Google Scholar]
- Masurkar, N.K.; Pandey, P. Nfc Based Dual Authentication Access Control System With Biometric. Int. J. Sci. Res. Eng. Trends 2020, 6, 124–128. [Google Scholar]
- Vijetha, T.S.; Meghana, N.S.; Nayanashree, K.S.; Kavyashree, G.B.; Namratha, S.H. A Review: Antitheft Sensor Controlled Home Security System. Int. J. Res. Anal. Rev. 2020, 7, 634–637. [Google Scholar]
- Mazumdar, A.; JosephNg, P.; Eaw, H.; Phan, K.; Yeck, Y. JomNFCSignIN: Seamlessly Register Your Class Attendance. In Proceedings of the International Conference on Emerging Technologies and Intelligent Systems (ICETIS), Al Buraimi, Oman, 25–26 June 2021; Springer: Cham, Switzerland, 2021; Volume 299, pp. 207–216. [Google Scholar]
- Gursoy, D.; Geng, C. Effects of COVID-19 pandemic on hospitality industry: Review of the current situations and a research agenda. J. Hosp. Mark. Manag. 2020, 29, 527–529. [Google Scholar] [CrossRef]
- Bartik, A.; Bertrand, M.; Cullen, Z.B.; Glaeser, E.L.; Luca, M.; Stanton, C.T. How are small businesses adjusting to COVID-19? Early evidence from a survey. Natl. Bur. Econ. Res. 2020, 1–36. [Google Scholar] [CrossRef]
- Gössling, S.; Scott, D.; Hall, C.M. Pandemics, tourism and global change: A rapid assessment of COVID-19. J. Sustain. Tour. 2021, 29, 1–20. [Google Scholar] [CrossRef]
- Gursoy, D.; Chi, C.; Chi, O.H. COVID-19 Study 2 Report: Restaurant and Hotel Industry: Restaurant and hotel customers’ sentiment analysis. Would they come back? If they would, WHEN? UNWTO World Tour. Barom. 2020, 18, 1–21. [Google Scholar]
- Kim, J.J.; Han, H. Hotel Service Innovation with Smart Technologies: Exploring Consumers’ Readiness and Behaviors. Sustainability 2022, 14, 5746. [Google Scholar] [CrossRef]
- Gowthaman, Gunasheelan and Gurumoorthy. Face Recognition Door Lock System. Int. J. Res. Publ. Rev. 2022, 3, 1411–1416. [Google Scholar]
- Sabeenian, D.; Harirajkumar, J.; Cruz, L.D. Attendance Authentication System Using Face Recognition. J. Adv. Res. Dyn. Control Syst. 2020, 12, 1235–1248. [Google Scholar]
- Okafor, C.S.; Nnebe, S.U.; Alumona, T.L.; Onuzuluike, V.C.; Jideofor, U.C. Door Access Control Using RFID and Voice Recognition System. Int. J. Res. Appl. Sci. Eng. Technol. 2022, 10, 157–163. [Google Scholar]
- Goud, K.; Sindhuri, K. Enhanced Security for Smart Door Using Biometrics and OTP. In Modern Approaches in Machine Learning & Cognitive Science: A Walkthrough; Studies in Computational Intelligence; Springer: Cham, Switzerland, 2022; Volume 1027, pp. 517–526. [Google Scholar]
- Akanbi, O.; Ogundoyin, I.K.; Akintola, J.O.; Ameenah, K. A Prototype Model of an IoT-based Door System using Double-access Fingerprint Technique. Niger. J. Technol. Dev. 2020, 17, 142–149. [Google Scholar]
- Lee, W.; Baek, S.Y.; Kim, S.H. Deep-Learning-Aided RF Fingerprinting for NFC Security. IEEE Commun. Mag. 2021, 59, 96–101. [Google Scholar] [CrossRef]
- Albattah, A.; Alghofaili, Y.; Elkhediri, S. NFC Technology: Assessment Effective of Security towards Protecting NFC Devices & Services. In Proceedings of the 2020 International Conference on Computing and Information Technology (ICCIT-1441), Tabuk, Saudi Arabia, 9–10 September 2020; Volume 1, pp. 253–257. [Google Scholar]
- Kulkarni, R.D. Near Field Communication (NFC) Technology and Its Application. In Techno-Societal 2020; Springer: Cham, Switzerland, 2021; pp. 745–751. [Google Scholar]
- Govender, C.; van Niekerk, B. Secure Key Exchange by NFC for Instant Messaging. In Proceedings of the 2021 Conference on Information Communications Technology and Society, Durban, South Africa, 10–11 March 2021; pp. 27–33. [Google Scholar]
- See, S.; JosephNg, P.; Phan, K.; Lim, J. JomWowNFC: Why NFC must be used for Merchant & Consumer? In Proceedings of the 2021 Innovations in Power and Advanced Computing Technologies (i-PACT), Kuala Lumpur, Malaysia, 27–29 November 2021; pp. 1–6. [Google Scholar]
- JosephNg, P. Economic Turbulence and EaaS Grid Computing. Int. J. Bus. Forecast. Mark. Intell. 2021, 7, 33–52. [Google Scholar] [CrossRef]
- JosephNg, P.S. EaaS Infrastructure Disruptor for “MSE”. Int. J. Bus. Inf. Syst. 2019, 30, 373–385. [Google Scholar] [CrossRef]
- JosephNg, P.S. EaaS Optimization: Available yet hidden information technology infrastructure inside “Medium Size Enterprise”. J. Technol. Forecast. Soc. Chang. 2018, 132, 165–173. [Google Scholar] [CrossRef]
- Soon, J.P.; Moy, K.C. Beyond barebone cloud infrastructure services: Stumbling competitiveness during economic turbulence. J. Sci. Technol. 2016, 24, 101–121. [Google Scholar]
- Soon, J.N.P.; Wan, W.S.; Yuean, P.K.; Heng, L.J. Barebone Cloud IaaS: Revitalisation Disruptive Technology. Int. J. Bus. Inf. Syst. 2015, 18, 107–126. [Google Scholar] [CrossRef]
- Joseph, N.P.S.; Mahmood, A.K.; Choo, P.Y.; Wong, S.W.; Phan, K.Y.; Lim, E.H. IaaS Cloud Optimization during Economic Turbulence for Malaysia Small and Medium Enterprise. Int. J. Bus. Inf. Syst. 2014, 16, 196–208. [Google Scholar]
- Joseph, N.P.S.; Mahmood, A.K.; Choo, P.Y.; Wong, S.W.; Phan, K.Y.; Lim, E.H. Battles in volatile information and communication technology landscape: The Malaysia small and medium enterprise case. Int. J. Bus. Inf. Syst. 2013, 13, 217–234. [Google Scholar] [CrossRef]
- Joseph, N.P.S.; Kang, C.M.; Mahmood, A.K.; Choo, P.Y.; Wong, S.W.; Phan, K.Y.; Lim, E.H. Exostructure Services for Infrastructure Resources Optimization. J. Telecommun. Electron. Comput. Eng. 2016, 8, 65–69. [Google Scholar]
- Joseph, N.P.S.; Choo, P.; Wong, S.; Phan, K.; Lim, E. Hibernating ICT Infrastructure During Rainy Days. J. Emerg. Trends Comput. Inf. Sci. 2012, 3, 112–116. [Google Scholar]
- Mishra, S.; Mohite, O.; Kharat, S. Smart Door Lock System Using Arduino. Int. Res. J. Mod. Eng. Technol. Sci. 2022, 4, 1503–1507. [Google Scholar]
- Sayanekar, P.; Rajiwate, A.; Qazi, L.; Kulkarni, A. Customized NFC enabled ID card for Attendance and Transaction using Face Recognition. Int. Res. J. Eng. Technol. 2021, 3, 1366–1368. [Google Scholar]
- Elmannai, W.; Paige, I.; Rexha, R.; Rivera, M. A Highly Secure Platform that Supports Smart Locks. In Proceedings of the 2020 IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), London, ON, Canada, 30 August–2 September 2020; pp. 1–6. [Google Scholar]
- Shanthini, M.; Vidya, G.; Arun, R. IoT Enhanced Smart Door Locking System. In Proceedings of the International Conference on Smart Systems and Inventive Technology (ICSSIT 2020), Tirunelveli, India, 20–22 August 2020; pp. 92–96. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).