LLM-LCSA: LLM for Collaborative Control and Decision Optimization in UAV Cluster Security
Highlights
- The proposed LLM-LCSA architecture improves threat detection accuracy by an average of 7.92% and reduces total system response time by 44.52% compared to traditional methods.
- A Mixture of Experts (MoEs) mechanism incorporating a dynamic threat–expert association matrix enables adaptive and real-time identification of complex threats.
- The cloud–edge–end hierarchical framework provides a scalable and efficient architecture for secure, intelligent collaboration in large-scale UAV swarms.
- The resource-aware multi-objective decision model ensures reliable performance under stringent resource constraints, enhancing practicality for real-world deployments.
Abstract
1. Introduction
1.1. Motivation
1.2. State of the Art
1.3. Comparison of Related Work
- 1.
- We propose LLM-LCSA for secure multi-UAV collaboration. Through a cloud–edge–terminal collaborative computing architecture, LLM-LCSA integrates distributed data storage, sliding window aggregation, and data validity scoring mechanisms to achieve multilevel model collaborative inference. In comprehensive performance evaluations, all the components achieved excellent ratings.
- 2.
- An intelligent agent algorithm based on the MoEs was designed, implemented, and embedded within edge servers. Through the designed threat–expert dynamic correlation matrix and expert weight dynamic adjustment mechanism, the accuracy of the system in identifying complex dynamic threats and its dynamic adaptability significantly increased. Simulation experiments demonstrate that compared with traditional methods, the average recognition accuracy for multiple threat types increased by 7.92%.
- 3.
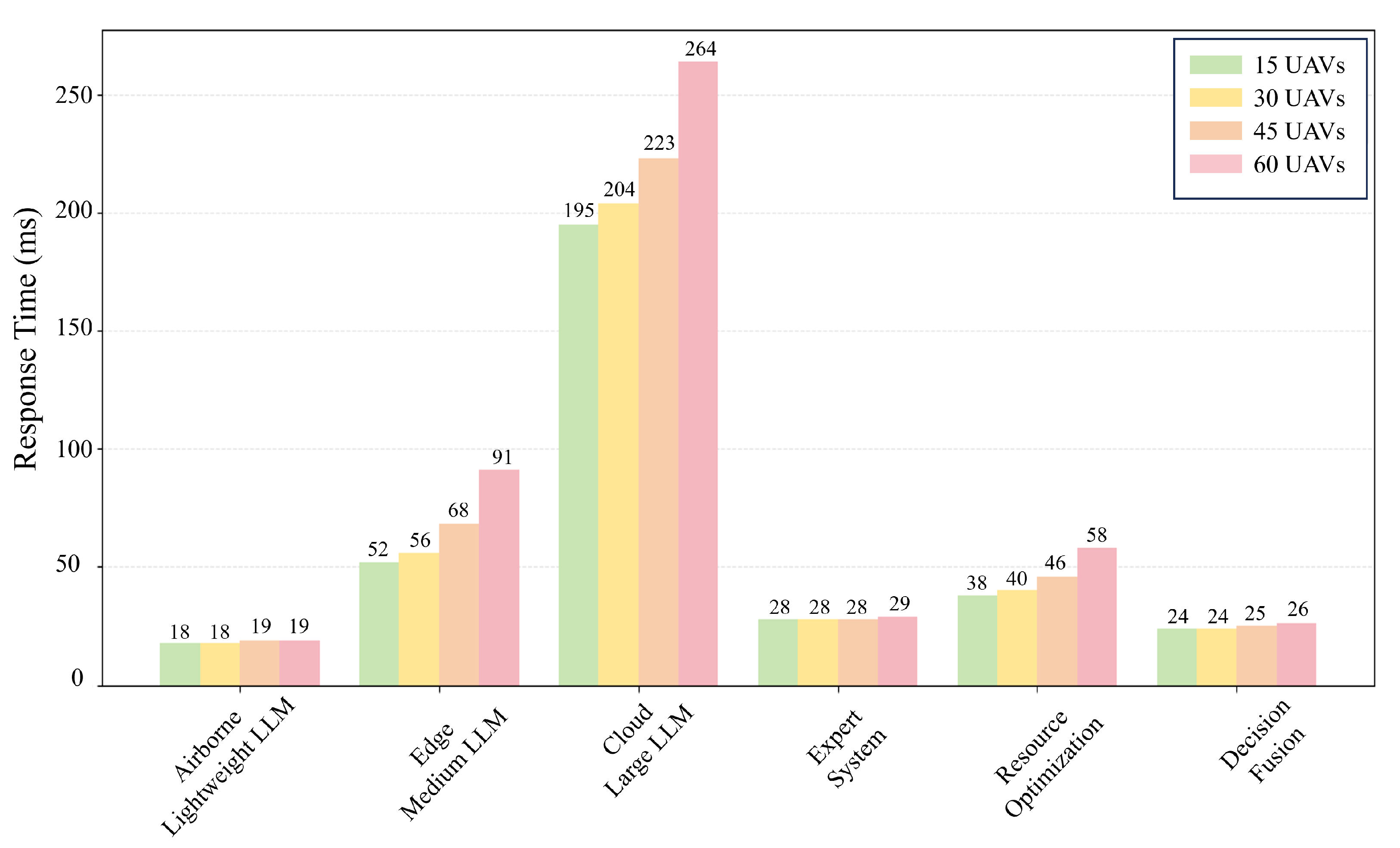
- A multi-objective optimization model under resource constraints was constructed to achieve resource-aware intelligent decision-making. This model comprehensively considers expert recommendation costs and multidimensional resource consumption constraints and develops an optimization solution strategy that incorporates slack variables. The simulation results demonstrate that compared with traditional methods, the system reduces the total response time by 44.52%, significantly improving resource utilization.
- We propose a hierarchical collaborative security architecture that addresses the inefficiency of traditional simple-layered deployment models in processing multisource asynchronous spatiotemporal data fusion. This significantly enhances data processing efficiency, with simulation results validating the architecture’s effectiveness.
- We resolve the accuracy and adaptability limitations of traditional hybrid expert models when handling novel complex threats by introducing an online adaptive matrix. This enables real-time expert activation and continuous self-evolution.
- We design a resource-aware multi-objective optimization model to resolve the challenge of balancing decision quality with multidimensional resource consumption in resource-constrained edge environments. By incorporating slack variables and a multidimensional confidence mechanism, we ensure the system’s reliable performance and deployment capability under resource-limited conditions.
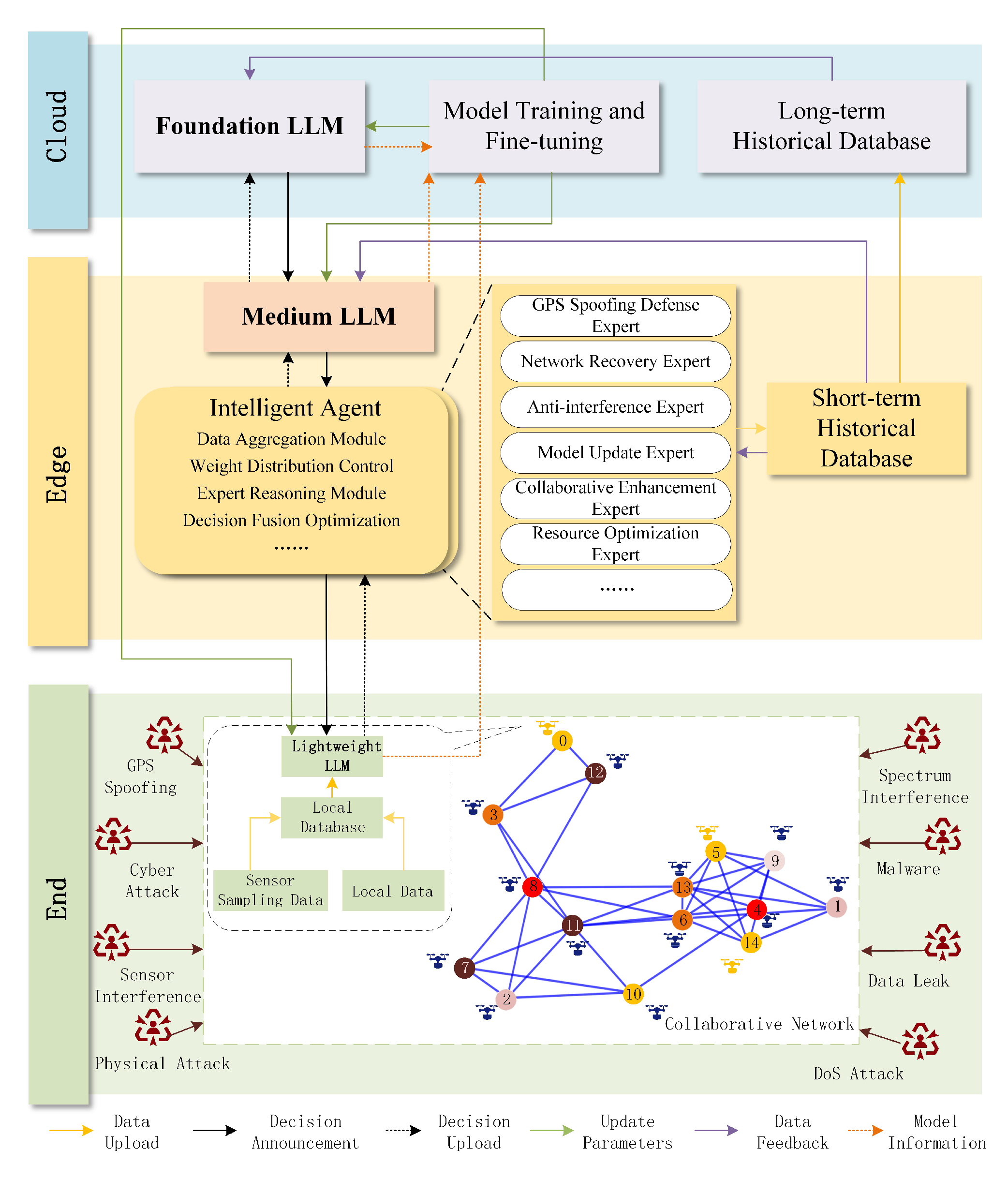
2. System Architecture Design
2.1. Cooperative Deployment of Layered Models
2.2. Distributed Data Storage Architecture
2.3. Embedded Intelligent Agent Algorithm
2.4. Performance Evaluation
3. System Model and Analysis
3.1. System Models
3.1.1. Network Topography
3.1.2. Threat Model
3.1.3. Data Processing Flow
3.1.4. Resource Constraints
3.2. Feature Vectors and Data Freshness
3.3. Threat–Expert Association Matrix
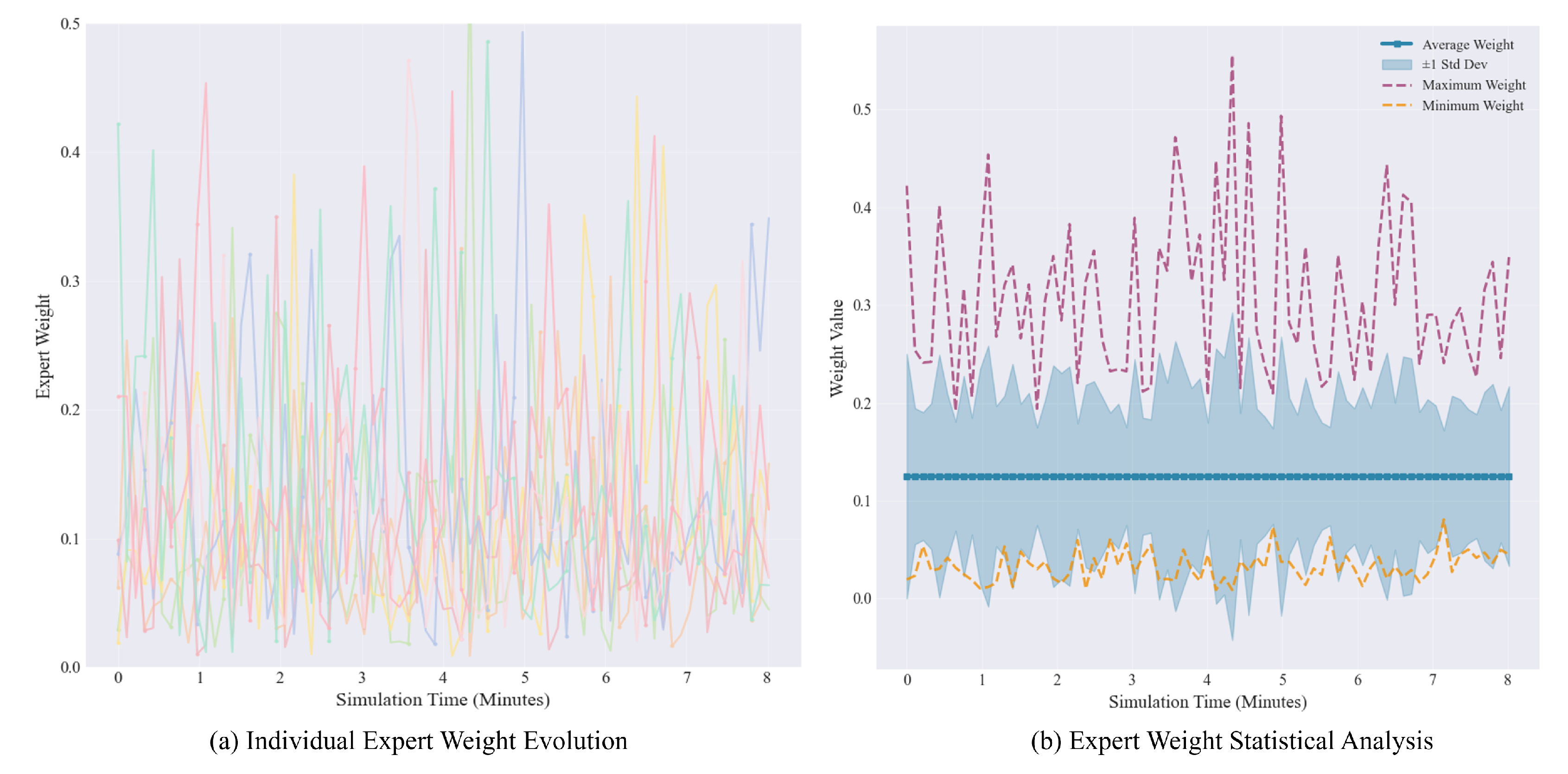
3.4. Expert Reasoning Module
| Algorithm 1: Layered collaborative threat detection algorithm. |
|
3.5. Complexity Analysis
4. Intelligent Decision Optimization
4.1. Resource-Constrained Decision Optimization
4.2. Expert Consensus Rating
4.3. Multi-Expert Collaborative Safety Decision-Making Algorithm
| Algorithm 2: Dynamic expert decision algorithm. |
|
4.4. Complexity and Deployment Analysis
5. Simulation and Results
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| BS | Base station |
| CPU | Central processing unit |
| DoS | Denial of service |
| GCS | Ground control station |
| GPS | Global positioning system |
| GSK | Group secret key |
| IAB | Integrated access and backhaul |
| KKT | Karush–Kuhn–Tucker |
| LLM | Large language model |
| LoS | Line-of-sight |
| MoEs | Mixture of experts |
| NLoS | Non-line-of-sight |
| RAG | Retrieval-augmented generation |
| RAM | Random access memory |
| SDN | Software-defined networking |
| UAV | Unmanned aerial vehicle |
| V2X | Vehicle-to-everything |
Appendix A
| Symbol | Description |
|---|---|
| E | Set of communication links. |
| G | Communication graph. |
| Security pattern analysis label. | |
| Long-term historical features. | |
| M | Number of threat types. |
| N | Number of UAVs. |
| R | System available resource vector. |
| Short-term historical features. | |
| Cloud-based time series prediction. | |
| Set of threat types. | |
| V | Set of UAV nodes. |
| Set of experts. | |
| Resource consumption for resource k. | |
| Decision vector from expert i. | |
| Normalized communication distance. | |
| Overall optimization objective function. | |
| Base relevance score of expert i. | |
| Cost function for expert i. | |
| Probability of threat type j. | |
| Aggregated feature vector. | |
| Dynamic weight of expert i. | |
| x | Decision vector to be optimized. |
| Optimized decision vector. | |
| Slack variable for resource k. |
References
- Boroujeni, S.P.H.; Razi, A.; Khoshdel, S.; Afghah, F.; Coen, J.L.; O’Neill, L.; Fule, P.; Watts, A.; Kokolakis, N.M.T.; Vamvoudakis, K.G. A comprehensive survey of research towards AI-enabled unmanned aerial systems in pre-, active-, and post-wildfire management. Inf. Fusion 2024, 108, 102369. [Google Scholar] [CrossRef]
- Nahiyoon, S.A.; Ren, Z.; Wei, P.; Li, X.; Li, X.; Xu, J.; Yan, X.; Yuan, H. Recent Development Trends in Plant Protection UAVs: A Journey from Conventional Practices to Cutting-Edge Technologies—A Comprehensive Review. Drones 2024, 8, 457. [Google Scholar] [CrossRef]
- Mendu, B.; Mbuli, N. State-of-the-Art Review on the Application of Unmanned Aerial Vehicles (UAVs) in Power Line Inspections: Current Innovations, Trends, and Future Prospects. Drones 2025, 9, 265. [Google Scholar] [CrossRef]
- Betti Sorbelli, F. UAV-Based Delivery Systems: A Systematic Review, Current Trends, and Research Challenges. ACM J. Auton. Transport. Syst. 2024, 1, 1–40. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, Z.; Yi, L.; Ning, Z.; Guo, L.; Yu, F.R.; Guo, S. A Survey on Security of UAV Swarm Networks: Attacks and Countermeasures. ACM Comput. Surv. 2025, 57, 1–37. [Google Scholar] [CrossRef]
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned Aircraft Capture and Control Via GPS Spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Ko, Y.; Kim, J.; Duguma, D.G.; Astillo, P.V.; You, I.; Pau, G. Drone Secure Communication Protocol for Future Sensitive Applications in Military Zone. Sensors 2021, 21, 2057. [Google Scholar] [CrossRef]
- Ashraf, S.N.; Manickam, S.; Zia, S.S.; Abro, A.A.; Obaidat, M.; Uddin, M.; Abdelhaq, M.; Alsaqour, R. IoT empowered smart cybersecurity framework for intrusion detection in internet of drones. Sci. Rep. 2023, 13, 18422. [Google Scholar] [CrossRef]
- Tan, Y.H.; Lai, S.; Wang, K.; Chen, B.M. Cooperative control of multiple unmanned aerial systems for heavy duty carrying. Annu. Rev. Control 2018, 46, 44–57. [Google Scholar] [CrossRef]
- Raja, G.; Senthivel, S.G.; Balaganesh, S.; Rajakumar, B.R.; Ravichandran, V.; Guizani, M. MLB-IoD: Multi Layered Blockchain Assisted 6G Internet of Drones Ecosystem. IEEE Trans. Veh. Technol. 2023, 72, 2511–2520. [Google Scholar] [CrossRef]
- Karmakar, R.; Kaddoum, G.; Akhrif, O. A Blockchain-Based Distributed and Intelligent Clustering-Enabled Authentication Protocol for UAV Swarms. IEEE Trans. Mob. Comput. 2024, 23, 6178–6195. [Google Scholar] [CrossRef]
- Jangsher, S.; Al-Dweik, A.; Iraqi, Y.; Pandey, A.; Giacalone, J.P. Group Secret Key Generation Using Physical Layer Security for UAV Swarm Communications. IEEE Trans. Aerosp. Electron. Syst. 2023, 59, 8550–8564. [Google Scholar] [CrossRef]
- Viana, J.; Farkhari, H.; Sebastião, P.; Campos, L.M.; Koutlia, K.; Bojovic, B.; Lagén, S.; Dinis, R. Deep Attention Recognition for Attack Identification in 5G UAV Scenarios: Novel Architecture and End-to-End Evaluation. IEEE Trans. Veh. Technol. 2024, 73, 131–146. [Google Scholar] [CrossRef]
- Lopez, M.A.; Baddeley, M.; Lunardi, W.T.; Pandey, A.; Giacalone, J.P. Towards Secure Wireless Mesh Networks for UAV Swarm Connectivity: Current Threats, Research, and Opportunities. In Proceedings of the 2021 17th International Conference on Distributed Computing in Sensor Systems (DCOSS), Pafos, Cyprus, 14–16 July 2021; pp. 319–326. [Google Scholar]
- Jalil Hadi, H.; Cao, Y.; Li, S.; Hu, Y.; Wang, J.; Wang, S. Real-Time Collaborative Intrusion Detection System in UAV Networks Using Deep Learning. IEEE Internet Things J. 2024, 11, 33371–33391. [Google Scholar] [CrossRef]
- Hadi, H.J.; Cao, Y.; Khan, M.K.; Ahmad, N.; Hu, Y.; Fu, C. UAV-NIDD: A Dynamic Dataset for Cybersecurity and Intrusion Detection in UAV Networks. IEEE Trans. Netw. Sci. Eng. 2025, 12, 2739–2757. [Google Scholar] [CrossRef]
- Yang, Z.; Zhang, Y.; Zeng, J.; Yang, Y.; Jia, Y.; Song, H.; Lv, T.; Sun, Q.; An, J. AI-Driven Safety and Security for UAVs: From Machine Learning to Large Language Models. Drones 2025, 9, 392. [Google Scholar] [CrossRef]
- Javaid, S.; Fahim, H.; He, B.; Saeed, N. Large Language Models for UAVs: Current State and Pathways to the Future. IEEE Open J. Veh. Technol. 2024, 5, 1166–1192. [Google Scholar] [CrossRef]
- Liu, L.; Li, W.; Zhou, F. Enhancing 6G IoT Communications: UAV Relayed Satellite D2D with Large Language Model Optimization. IEEE Commun. Mag. 2025, 63, 90–96. [Google Scholar] [CrossRef]
- Aikins, G.; Dao, M.P.; Moukpe, K.J.; Eskridge, T.C.; Nguyen, K.D. LEVIOSA: Natural Language-Based Uncrewed Aerial Vehicle Trajectory Generation. Electronics 2024, 13, 4508. [Google Scholar] [CrossRef]
- Li, H.; Xiao, M.; Wang, K.; Kim, D.I.; Debbah, M. Large Language Model Based Multi-Objective Optimization for Integrated Sensing and Communications in UAV Networks. arXiv 2024, arXiv:2410.05062. [Google Scholar] [CrossRef]
- Han, B.; Chen, Y.; Li, J.; Li, J.; Su, J. SwarmChain: Collaborative LLM Inference for UAV Swarm Control. IEEE Internet Things Mag. 2025, 8, 64–71. [Google Scholar] [CrossRef]
- Zhu, B.; Bedeer, E.; Nguyen, H.H.; Barton, R.; Gao, Z. UAV Trajectory Planning for AoI-Minimal Data Collection in UAV-Aided IoT Networks by Transformer. IEEE Trans. Wireless Commun. 2023, 22, 1343–1358. [Google Scholar] [CrossRef]
- Emami, Y.; Zhou, H.; Nabavirazani, S.; Almeida, L. LLM-Enabled In-Context Learning for Data Collection Scheduling in UAV-Assisted Sensor Networks. IEEE Internet Things J. 2025, 1. [Google Scholar] [CrossRef]
- Golam, M.; Alam, M.M.; Kim, D.S.; Lee, J.M. BLM-Chain: AI-Driven Blockchain for UAV Threat Resistance in IoBT. In Proceedings of the 2024 15th International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 16–18 October 2024; pp. 1609–1613. [Google Scholar]
- Piggott, B.; Patil, S.; Feng, G.; Odat, I.; Mukherjee, R.; Dharmalingam, B.; Liu, A. Net-GPT: A LLM-Empowered Man-in-the-Middle Chatbot for Unmanned Aerial Vehicle. In Proceedings of the Eighth ACM/IEEE Symposium on Edge Computing, Wilmington, DE, USA, 6–9 December 2023; pp. 287–293. [Google Scholar]
- Sezgin, A. Scenario-Driven Evaluation of Autonomous Agents: Integrating Large Language Model for UAV Mission Reliability. Drones 2025, 9, 213. [Google Scholar] [CrossRef]
- Zhou, Q.; Wu, J.; Zhu, M.; Zhou, Y.; Xiao, F.; Zhang, Y. LLM-QL: A LLM-Enhanced Q-Learning Approach for Scheduling Multiple Parallel Drones. IEEE Trans. Knowl. Data Eng. 2025, 37, 5393–5406. [Google Scholar] [CrossRef]
- Usman, M.; Amin, R.; Aldabbas, H.; Alouffi, B. Lightweight Challenge-Response Authentication in SDN-Based UAVs Using Elliptic Curve Cryptography. Electronics 2022, 11, 1026. [Google Scholar] [CrossRef]
- Mughal, U.A.; Hassler, S.C.; Ismail, M. Machine Learning-Based Intrusion Detection for Swarm of Unmanned Aerial Vehicles. In Proceedings of the 2023 IEEE Conference on Communications and Network Security (CNS), Orlando, FL, USA, 2–5 October 2023; pp. 1–9. [Google Scholar]
- Deng, H.; Lu, Y.; Yang, T.; Liu, Z.; Chen, J. Unmanned Aerial Vehicles anomaly detection model based on sensor information fusion and hybrid multimodal neural network. Eng. Appl. Artif. Intell. 2024, 132, 107961. [Google Scholar] [CrossRef]
- Masadeh, A.; Alhafnawi, M.; Salameh, H.A.B.; Musa, A.; Jararweh, Y. Reinforcement Learning-Based Security/Safety UAV System for Intrusion Detection Under Dynamic and Uncertain Target Movement. IEEE Trans. Eng. Manag. 2024, 71, 12498–12508. [Google Scholar] [CrossRef]
- Li, J.; Sun, G.; Duan, L.; Wu, Q. Multi-Objective Optimization for UAV Swarm-Assisted IoT With Virtual Antenna Arrays. IEEE Trans. Mob. Comput. 2024, 23, 4890–4907. [Google Scholar] [CrossRef]
- Zhai, W.; Liu, L.; Ding, Y.; Sun, S.; Gu, Y. ETD: An Efficient Time Delay Attack Detection Framework for UAV Networks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2913–2928. [Google Scholar] [CrossRef]
- Tlili, F.; Ayed, S.; Fourati, L.C. A New Hybrid Adaptive Deep Learning-Based Framework for UAVs Faults and Attacks Detection. IEEE Trans. Serv. Comput. 2023, 16, 4128–4139. [Google Scholar] [CrossRef]
- Ding, Y.; Zhang, Q.; Lu, W.; Zhao, N.; Nallanathan, A.; Wang, X.; Yang, X. Collaborative Communication and Computation for Secure UAV-Enabled MEC Against Active Aerial Eavesdropping. IEEE Trans. Wirel. Commun. 2024, 23, 15915–15929. [Google Scholar] [CrossRef]
- Hao, J.X.; Chen, L.; Meng, L. Advancing Large Language Models with Enhanced Retrieval-Augmented Generation: Evidence from Biological UAV Swarm Control. Drones 2025, 9, 361. [Google Scholar] [CrossRef]
- El Alami, H.; Rawat, D.B. Lightweight Language Models in Autonomous Systems: In-Context Learning with Bidirectional Alignment for Fault Detection. In Proceedings of the ICC 2025—IEEE International Conference on Communications, Montreal, QC, Canada, 8–14 June 2025; pp. 4395–4400. [Google Scholar]
- Yan, W.; Sun, H.; Zhang, X.; Liang, X.; Zhu, S.; Jiang, Z. Boosting resilience design of cargo UAVs: A fault diagnosis method utilizing MRKG and LLM-FCT reasoning. J. Eng. Des. 2025, 1–27. [Google Scholar] [CrossRef]
- Yasser, M.; Shalash, O.; Ismail, O. Optimized Decentralized Swarm Communication Algorithms for Efficient Task Allocation and Power Consumption in Swarm Robotics. Robotics 2024, 13, 66. [Google Scholar] [CrossRef]













| Field | Technical Category | Ref. | Year | Technical Approach | Key Innovation / Strength |
|---|---|---|---|---|---|
| Traditional Method | Cryptography | [29] | 2022 | Lightweight challenge–response authentication using elliptic curve cryptography. | Suitable for SDN-based UAVs with low computational overhead. |
| [12] | 2023 | Proposed an efficient GSK protocol denoted as the sequential secret group key algorithm for distributed UAV communications. | Provided a reliable GSK generation process and offered a trade-off between transmission overhead and reliability. | ||
| Multilayer model | [30] | 2023 | Consensus control of large-scale UAV clusters based on a multilayer graph network model. | Improves scalability and robustness of large-scale cluster network topologies. | |
| [10] | 2025 | Proposed an innovative multilayer blockchain-assisted 6G drone internet (MLB-IoD) ecosystem. | Offered high security against attacks based on authentication and encryption. | ||
| Blockchain | [11] | 2024 | Designed a blockchain-based distributed identity verification mechanism for UAV clusters. | Enhanced the network performance of drone swarms and ensured the reliability of communications. | |
| Threat Identification | [14] | 2021 | Proposed a wireless mesh network security architecture and analyze security vulnerabilities and threats from the physical layer to the application layer. | Provides comprehensive security protection for UAV cluster communications. | |
| [31] | 2024 | Established a UAV cluster intrusion detection system using time probability automata (TPA). | Adapts to evolving attack patterns and identifies zero-day attacks. | ||
| [13] | 2024 | Developed a deep learning architecture for identifying attack behaviors in UAV communications in a 5G environment. | Accurate identification under both LoS and NLoS conditions. | ||
| LLM | Decision Optimization | [23] | 2023 | Transformer-based UAV trajectory planning algorithm. | Minimizes AoI, reduces latency, and lowers data tampering risk. |
| [21] | 2024 | Optimized UAV deployment and power control through LLMs. | Enhances anti-jamming capability in emergency communication scenarios. | ||
| Reasoning Enhancement | [26] | 2023 | Proposed an attack bot based on LLMs. It can simulate attacks that hijack communication sessions between GCS and UAV clusters. | Provided a better understanding of UAV threats and offered a convenient approach to enhancing the anti-attack capabilities of UAV clusters. | |
| [25] | 2024 | Utilized the contextual understanding capabilities of LLMs to perform semantic-level anomaly detection on UAV traffic data on the blockchain. | Enables online identification of novel threats without retraining. | ||
| [22] | 2025 | Proposed CoLLM, a distributed LLM collaborative reasoning framework for scenarios without a ground truth center. | Avoids single-point failure and prevents leakage of all intelligence. | ||
| Comprehensive Analysis | [17] | 2025 | Comprehensive analysis of LLM applications in UAV security. | Highlights LLMs’ capabilities in multimodal data fusion and real-time decision-making. | |
| Proposed Method | LLM-Layered Collaborative Security Architecture | Ours | 2025 | LLM-LCSA: A cloud–edge–end hierarchical architecture with MoEs-based smart agents and resource-aware optimization. | Integrates multi-level LLM collaboration, dynamic expert activation, and constrained decision-making for efficient and secure swarm operations. |
| Problem Domain | Specific Challenges | Existing Deficiencies |
|---|---|---|
| Specialized Design and Collaborative Mechanisms |
|
|
| Dynamic Threat Response and Knowledge Utilization |
|
|
| Decision Optimization under Resource Constraints |
|
|
| Methods | Ref. | Year | Dynamic Adaptability | Features | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| HDF | MTD | DO | RO | RL | RM | ED | ||||
| Traditional Method | [32] | 2022 | Medium | ✓ | ✓ | ✓ | ✓ | |||
| [33] | 2023 | Low | ✓ | ✓ | ✓ | ✓ | ||||
| [34] | 2023 | Medium | ✓ | ✓ | ✓ | |||||
| [35] | 2023 | Low | ✓ | ✓ | ✓ | |||||
| [36] | 2024 | Low | ✓ | ✓ | ✓ | ✓ | ||||
| LLM | [25] | 2024 | High | ✓ | ✓ | |||||
| [22] | 2025 | High | ✓ | ✓ | ✓ | ✓ | ||||
| [37] | 2025 | High | ✓ | ✓ | ✓ | ✓ | ||||
| [38] | 2025 | Low | ✓ | ✓ | ✓ | |||||
| [39] | 2025 | Medium | ✓ | ✓ | ✓ | |||||
| [27] | 2025 | High | ✓ | ✓ | ✓ | ✓ | ||||
| Proposed Method | Ours | 2025 | High | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Category | Name | Value |
|---|---|---|
| Lightweight LLM | Model size | 7 B parameters |
| Architecture type | Transformer-based lightweight inference model | |
| Inference latency | <15 ms | |
| Memory usage | <2 GB | |
| Attention weight | GPS weight: 0.25; communication weight: 0.20 | |
| Sensor weight | 0.15 | |
| Latency weight | 0.10 | |
| Spectrum weight | 0.15 | |
| CPU weight | 0.10 | |
| Memory weight | 0.05 | |
| Detection threshold | 0.4 | |
| Medium LLM | Model size | 13 B parameters |
| Number of Transformer layers | 24 | |
| Inference latency | <45 ms | |
| Memory usage | <8 GB | |
| Input dimensions | 12-dimensional feature vectors | |
| Output dimensions | 9 classes (8 threats + normal) | |
| Number of self-attention heads | 16 | |
| Feedforward network dimensions | 4096 | |
| Large LLM | Model size | 70 B parameters |
| Transformer layers | 80 layers | |
| Inference latency | <180 ms | |
| Memory usage | <40 GB | |
| Sequential prediction window | 240 historical points | |
| Context length | 2048 tokens | |
| Pattern memory capacity | 2000 threat patterns |
| Category | Name | Value |
|---|---|---|
| UAV Cluster | Number of UAVs | 15 |
| Flight altitude | 80∼150 m | |
| Cruising speed | 6∼10 m/s | |
| Maximum speed | 12 m/s | |
| Flight area | 3 km × 3 km | |
| Communication System | Communication frequency | 2.4 GHz/5.8 GHz |
| Transmit power | 100 mW | |
| Antenna gain | 2.15 dBi | |
| Communication range | 500–1000 m | |
| Data transmission rate | 1–10 Mbps | |
| Path loss index | 2.2 | |
| Shadowing attenuation standard deviation | 3 dB | |
| Network Topology | Topology type | Random geometric graph |
| Normalized connection distance | 0.35 | |
| Average node degree | 4–6 | |
| Network diameter | ≤5 hops | |
| Connectivity probability | >95% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, H.; Yang, Z.; Du, H.; Zhang, Y.; Zeng, J.; He, X. LLM-LCSA: LLM for Collaborative Control and Decision Optimization in UAV Cluster Security. Drones 2025, 9, 779. https://doi.org/10.3390/drones9110779
Song H, Yang Z, Du H, Zhang Y, Zeng J, He X. LLM-LCSA: LLM for Collaborative Control and Decision Optimization in UAV Cluster Security. Drones. 2025; 9(11):779. https://doi.org/10.3390/drones9110779
Chicago/Turabian StyleSong, Hua, Zheng Yang, Haitao Du, Yuting Zhang, Jie Zeng, and Xinxin He. 2025. "LLM-LCSA: LLM for Collaborative Control and Decision Optimization in UAV Cluster Security" Drones 9, no. 11: 779. https://doi.org/10.3390/drones9110779
APA StyleSong, H., Yang, Z., Du, H., Zhang, Y., Zeng, J., & He, X. (2025). LLM-LCSA: LLM for Collaborative Control and Decision Optimization in UAV Cluster Security. Drones, 9(11), 779. https://doi.org/10.3390/drones9110779





