A Survey on Reputation Systems for UAV Networks
Abstract
1. Introduction
Paper Selection and Review Process
- What are the primary vulnerabilities affecting current UAV reputation systems?
- How do various reputation management approaches mitigate these vulnerabilities?
- Which future research directions are suggested by current findings in UAV reputation systems?
2. Classes/Types of UAV Devices
2.1. Single-Rotor UAVs
2.2. Multi-Rotor UAVs
2.3. Fixed Wing UAVs
3. An Overview of Trust and Reputation Systems in UAV Networks
3.1. A Brief Overview
3.2. Trust in UAVs
3.3. Security and Privacy in UAVs
3.4. Novelty of this Survey
4. Survey on UAV Reputation, Trust, and Feedback Systems
4.1. Trust
4.1.1. Reliability Trust
4.1.2. Decision Trust
4.1.3. Behavioral Trust
4.1.4. Direct Trust
4.1.5. Derived Trust
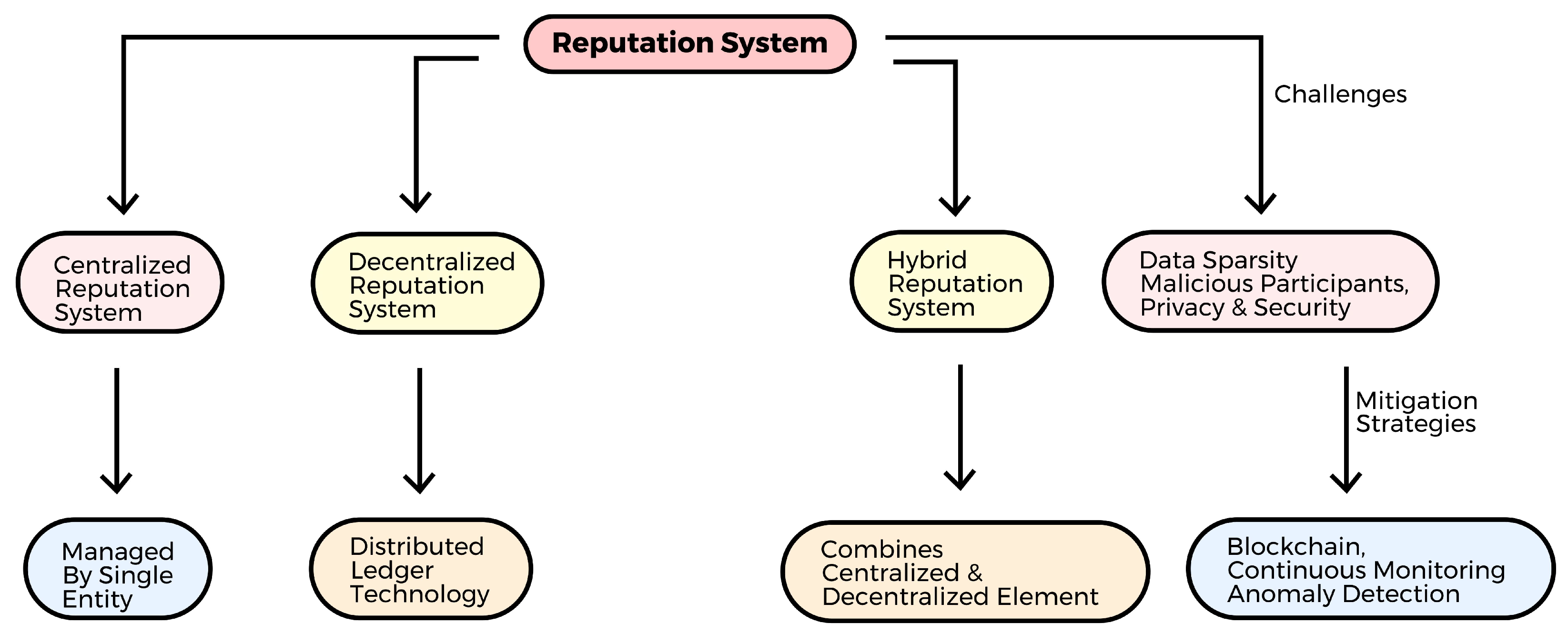
4.2. Reputation Systems
4.2.1. Centralized Reputation System
4.2.2. Decentralized Reputation System
4.2.3. Hybrid Reputation System
4.3. Reputation Data
4.4. Challenges of Reputation Systems
4.4.1. Data Sparsity
4.4.2. Malicious Participant
4.4.3. Privacy and Security
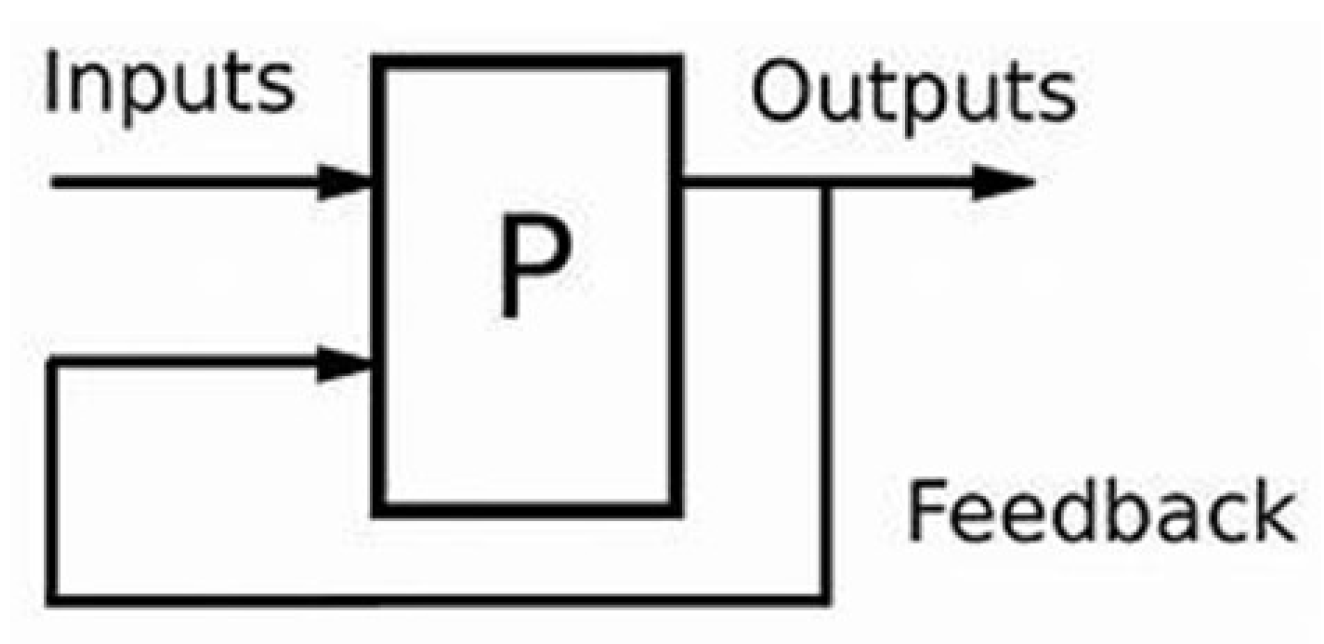
4.5. Feedback
4.5.1. Input Unit
4.5.2. The Processing Unit
4.5.3. Output Unit
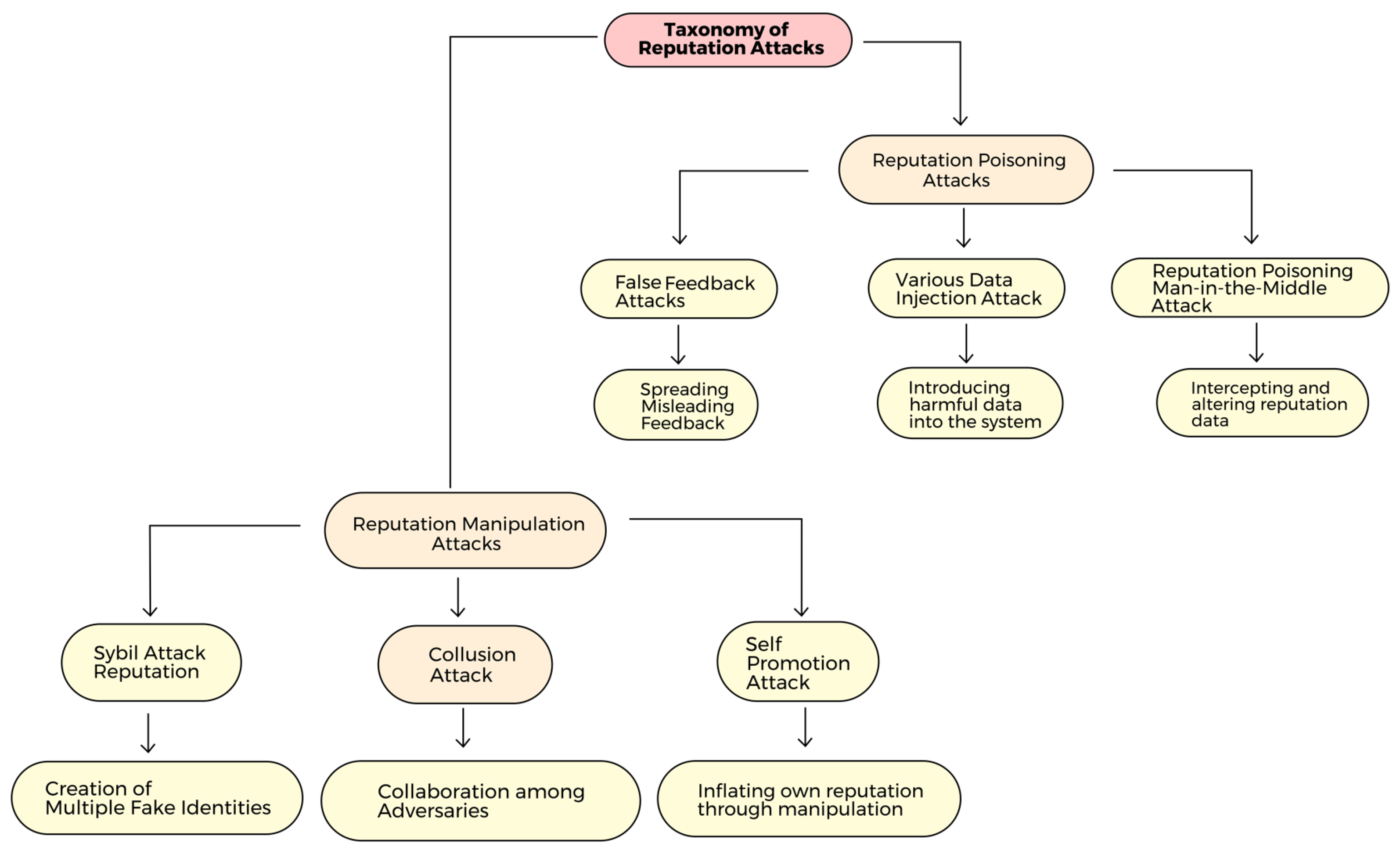
5. Taxonomy of Reputation Attacks
5.1. Reputation Manipulation Attacks
5.1.1. Sybil Attack
- Decentralized Blockchain: Implementing a decentralized blockchain-based system for managing UAV reputation can significantly augment security measures [84]. The inherent characteristics of blockchain technology guarantee that once a reputation has been recorded and stored, it becomes resistant to modification or tampering. Verifying reputation updates is facilitated through a consensus process, mitigating a potential vulnerability to Sybil assaults. Incorporating a proof of work (PoW) or proof of stake (PoS) method can introduce a supplementary level of security. UAVs must solve a computational challenge or stake a certain amount of resources to provide reputation feedback [84]. Creating several fraudulent identities is rendered economically and computationally burdensome for potential attackers.
- Reputation Source Validation: One viable strategy for mitigating Sybil attacks involves verifying reputation data sources. UAVs ought to exclusively consider reputation inputs originating from trustworthy sources. Reputation information can be reliably sourced from trusted nodes or authorities, which can then be cryptographically authenticated to guarantee its veracity.
- Continuous Monitoring and Anomaly Detection: Continuous monitoring and anomaly detection play a crucial role in upholding the integrity and security of a UAV reputation system. These strategies facilitate detecting anomalous activities, such as abrupt increases in reputation scores, which could signify a Sybil attack or other types of manipulation [46]. Utilization of continuous monitoring and anomaly detection tools can detect abrupt increases in reputation scores or atypical patterns of conduct. When the UAV system identifies such irregularities, it can implement proactive measures to mitigate attacks on the system.
5.1.2. Collusion Attack
5.1.3. Self-Promotion Attack
5.2. Reputation Poisoning Attack
5.2.1. False Feedback Attack
5.2.2. Malicious Data Injection Attack
5.2.3. Reputation Poisoning Man-in-the-Middle Attack
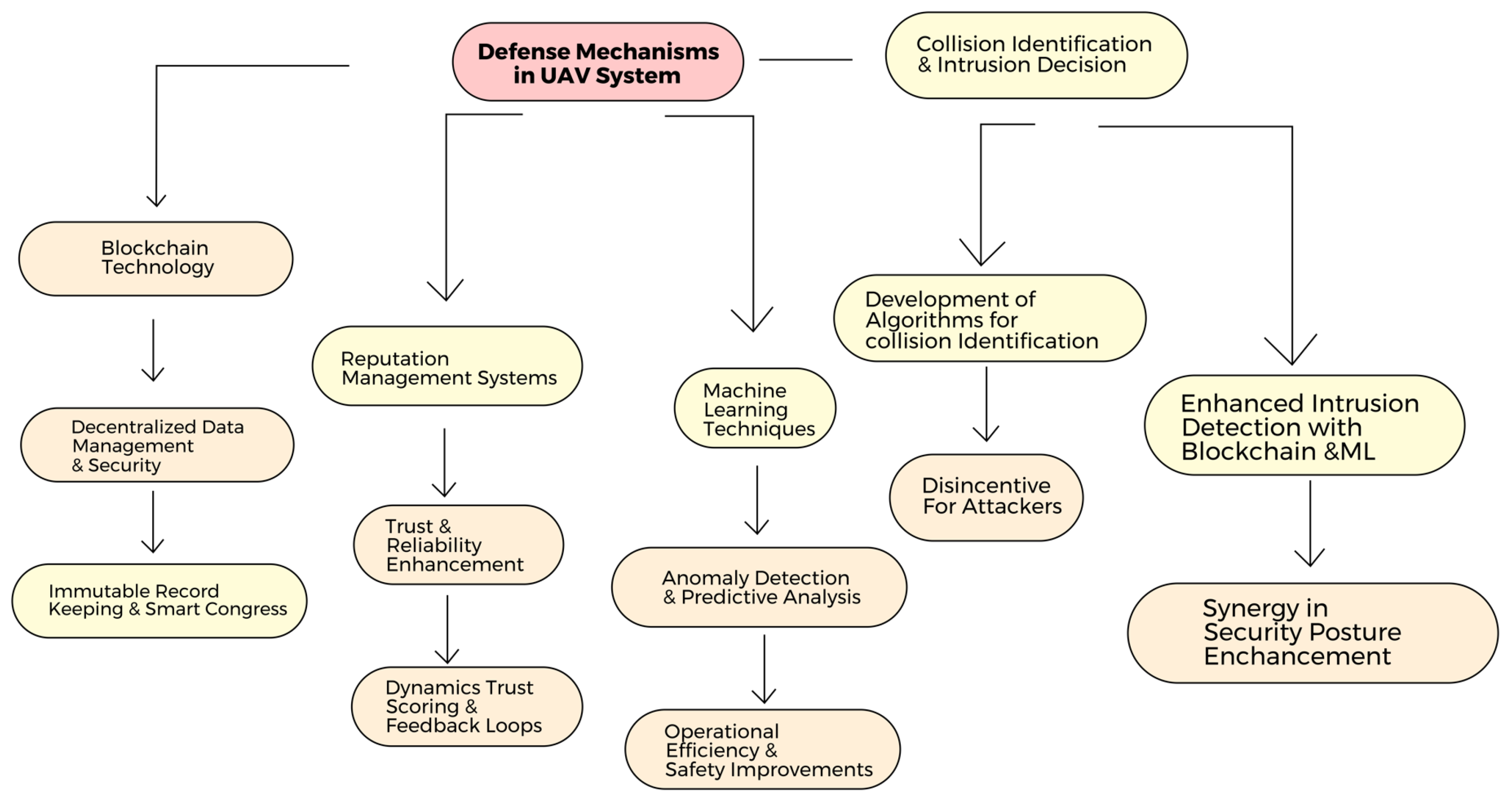
6. Defense Mechanism
6.1. Blockchain Technology
6.2. Reputation Management System
6.3. Machine Learning
6.4. Collusion Identification
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation |
| AIS | Artificial Immune System |
| BARS | Blockchain-based Anonymous Reputation System |
| BES | Behavior-based Reputation Assessment Scheme |
| CA | Certificate Authority |
| CerBC | Certificate Blockchain |
| CPU | Central Processing Unit |
| FL | Federated Learning |
| HMM | Hidden Markov Chains |
| IDS | Intrusion Detection System |
| IIoT | Industrial Internet of Things |
| IoT | Internet of Things |
| LEA | Law Enforcement Authority |
| MDA | Malicious UAV Detection Algorithm |
| MILP | Mixed Integer Linear Program |
| ML | Machine Learning |
| ORES | Organization Reputation Evaluation Scheme |
| PKI | Public Key Infrastructure |
| PoS | Proof of Stake |
| PoW | Proof of Work |
| QoE | Quality of Experience |
| QoS | Quality of Service |
| RevBC | Revocation Blockchain |
| RSU | Roadside Units |
| SCA | Successive Convex Approximation |
| SDN | Software-Defined Network |
| UAANET | Unmanned Aerial Vehicle Ad Hoc Networks |
| UAV | Unmanned Aerial Vehicle |
References
- Muchiri, G.; Kimathi, S. A review of applications and potential applications of UAV. In Proceedings of the Sustainable Research and Innovation Conference, Daerah Istimewa Yogyakarta, Indonesia, 20–21 July 2022; pp. 280–283. [Google Scholar]
- Utsav, A.; Abhishek, A.; Suraj, P.; Badhai, R.K. An IoT based UAV network for military applications. In Proceedings of the 2021 Sixth International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 25–27 March 2021; pp. 122–125. [Google Scholar]
- Hildmann, H.; Kovacs, E. Using unmanned aerial vehicles (UAVs) as mobile sensing platforms (MSPs) for disaster response, civil security and public safety. Drones 2019, 3, 59. [Google Scholar] [CrossRef]
- Jøsang, A.; Ismail, R.; Boyd, C. A survey of trust and reputation systems for online service provision. Decis. Support Syst. 2007, 43, 618–644. [Google Scholar] [CrossRef]
- Tsouros, D.C.; Bibi, S.; Sarigiannidis, P.G. A review on UAV-based applications for precision agriculture. Information 2019, 10, 349. [Google Scholar] [CrossRef]
- Angraal, S.; Krumholz, H.M.; Schulz, W.L. Blockchain technology: Applications in health care. Circ. Cardiovasc. Qual. Outcomes 2017, 10, e003800. [Google Scholar] [CrossRef]
- Hein, D.; Kraft, T.; Brauchle, J.; Berger, R. Integrated uav-based real-time mapping for security applications. ISPRS Int. J. Geo-Inf. 2019, 8, 219. [Google Scholar] [CrossRef]
- Xu, R.; Wei, S.; Chen, Y.; Chen, G.; Pham, K. LightMAN: A Lightweight Microchained Fabric for Assurance-and Resilience-Oriented Urban Air Mobility Networks. Drones 2022, 6, 421. [Google Scholar] [CrossRef]
- Garau Guzman, J.; Baeza, V.M. Enhancing Urban Mobility through Traffic Management with UAVs and VLC Technologies. Drones 2024, 8, 7. [Google Scholar] [CrossRef]
- Newswire, G. Global Commercial UAV Market Report 2023: Smart City Applications will Drive up to 36.5% of Drone Fleet Deployments by 2028, 2023. Available online: https://www.globenewswire.com/en/news-release/2023/07/05/2699314/28124/en/Global-Commercial-UAV-Market-Report-2023-Smart-City-Applications-will-Drive-up-to-36-5-of-Drone-Fleet-Deployments-by-2028.html (accessed on 15 May 2024).
- Biswas, S.; Anavatti, S.G.; Garratt, M.A. Chapter 4—Path planning and task assignment for multiple UAVs in dynamic environments. In Unmanned Aerial Systems; Koubaa, A., Azar, A.T., Eds.; Advances in Nonlinear Dynamics and Chaos (ANDC); Academic Press: Cambridge, MA, USA, 2021; pp. 81–102. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Agrawal, A.; Goyal, A.; Luong, N.C.; Niyato, D.; Yu, F.R.; Guizani, M. Fast, reliable, and secure drone communication: A comprehensive survey. IEEE Commun. Surv. Tutor. 2021, 23, 2802–2832. [Google Scholar] [CrossRef]
- Fortino, G.; Fotia, L.; Messina, F.; Rosaci, D.; Sarné, G.M. Trust and reputation in the internet of things: State-of-the-art and research challenges. IEEE Access 2020, 8, 60117–60125. [Google Scholar] [CrossRef]
- Blasch, E.; Sabatini, R.; Roy, A.; Kramer, K.A.; Andrew, G.; Schmidt, G.T.; Insaurralde, C.C.; Fasano, G. Cyber awareness trends in avionics. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–8. [Google Scholar]
- Krishna, C.L.; Murphy, R.R. A review on cybersecurity vulnerabilities for unmanned aerial vehicles. In Proceedings of the 2017 IEEE International Symposium on Safety, Security and Rescue Robotics (SSRR), Shanghai, China, 11–13 October 2017; pp. 194–199. [Google Scholar]
- Fortino, G.; Messina, F.; Rosaci, D.; Sarné, G.M. Using blockchain in a reputation-based model for grouping agents in the Internet of Things. IEEE Trans. Eng. Manag. 2019, 67, 1231–1243. [Google Scholar] [CrossRef]
- Liang, Q.; Gan, X. Research on trust evaluation algorithm for e-commerce based on reputation. In Proceedings of the 2011 International Conference on Business Computing and Global Informatization, Shanghai, China, 29–31 July 2011; pp. 39–42. [Google Scholar]
- Fotia, L.; Delicato, F.; Fortino, G. Trust in edge-based internet of things architectures: State of the art and research challenges. ACM Comput. Surv. 2023, 55, 1–34. [Google Scholar] [CrossRef]
- Bhoi, S.K.; Jena, K.K.; Jena, A.; Panda, B.C.; Singh, S.; Behera, P. A Reputation Deterministic Framework for True Event Detection in Unmanned Aerial Vehicle Network (UAVN). In Proceedings of the 2019 International Conference on Information Technology (ICIT), Bhubaneswar, India, 19–21 December 2019; pp. 257–262. [Google Scholar] [CrossRef]
- Battah, A.A.; Iraqi, Y.; Damiani, E. A Trust and Reputation System for IoT Service Interactions. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2987–3005. [Google Scholar] [CrossRef]
- Mrabet, K.; El Bouanani, F.; Ben-Azza, H. Dynamic Decentralized Reputation System from Blockchain and Secure Multiparty Computation. J. Sens. Actuator Netw. 2023, 12, 14. [Google Scholar] [CrossRef]
- Ogunbunmi, S.; Hatmai, M.; Xu, R.; Chen, Y.; Blasch, E.; Ardiles-Cruz, E.; Aved, A.; Chen, G. A Lightweight Reputation System for UAV Networks. In Proceedings of the Security and Privacy in Cyber-Physical Systems and Smart Vehicles; Chen, Y., Lin, C.W., Chen, B., Zhu, Q., Eds.; Springer Nature: Cham, Switzerland, 2024; pp. 114–129. [Google Scholar]
- Qu, Q.; Ogunbunmi, S.; Hatami, M.; Xu, R.; Chen, Y.; Chen, G.; Blasch, E. A Digital Twins Enabled Reputation System for Microchain-based UAV Networks. In Proceedings of the 2023 IEEE 12th International Conference on Cloud Networking (CloudNet), New York, NY, USA, 1–3 November 2023; pp. 428–432. [Google Scholar]
- Mrabet, K.; El Bouanani, F.; Ben-Azza, H. Generalized Secure and Dynamic Decentralized Reputation System with a Dishonest Majority. IEEE Access 2023, 11, 9368–9388. [Google Scholar] [CrossRef]
- El Husseini, A.; M’hamed, A.; El Hassan, B.; Mokhtari, M. Trust-Based Authentication Scheme with User Rating for Low-Resource Devices in Smart Environments. Pers. Ubiquitous Comput. 2013, 17, 1013–1023. [Google Scholar] [CrossRef][Green Version]
- Pereira, R.H.; Gonçalves, M.J.; Magalhães, M.A.G. Reputation Systems: A framework for attacks and frauds classification. J. Inf. Syst. Eng. Manag. 2023, 8, 19218. [Google Scholar] [CrossRef]
- Frew, E.W.; Argrow, B.; Houston, A.; Weiss, C. An Energy-Aware Airborne Dynamic Data-Driven Application System for Persistent Sampling and Surveillance. In Handbook of Dynamic Data Driven Applications Systems: Volume 2; Springer: Berlin, Germany, 2023; pp. 419–448. [Google Scholar]
- Ngu, A.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, Q.Z. IoT Middleware: A Survey on Issues and Enabling Technologies. IEEE Internet Things J. 2017, 4, 1–20. [Google Scholar] [CrossRef]
- Guo, L.; Zhang, C.; Fang, Y. A Trust-Based Privacy-Preserving Friend Recommendation Scheme for Online Social Networks. IEEE Trans. Depend. Secur. Comput. 2015, 12, 413–427. [Google Scholar] [CrossRef]
- Ghahramani, M.H.; Zhou, M.; Hon, C.T. Toward cloud computing QoS architecture: Analysis of cloud systems and cloud services. IEEE/CAA J. Autom. Sin. 2017, 4, 6–18. [Google Scholar] [CrossRef]
- Hoffman, K.; Zage, D.; Nita-Rotaru, C. A survey of attack and defense techniques for reputation systems. ACM Comput. Surv. (CSUR) 2009, 42, 1–31. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Jeon, G.; Hassan, M.M.; Hassan, M.R.; Kaur, K. Blockchain-Based Privacy-Preserving Authentication Model Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2023, 24, 7435–7443. [Google Scholar] [CrossRef]
- Xie, L.; Su, Z.; Chen, N.; Xu, Q. Secure Data Sharing in UAV-assisted Crowdsensing: Integration of Blockchain and Reputation Incentive. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Wu, H.; Zhang, W. Digital identity, privacy security, and their legal safeguards in the Metaverse. Secur. Saf. 2023, 2, 2023011. [Google Scholar] [CrossRef]
- Malik, S.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. Trustchain: Trust management in blockchain and iot supported supply chains. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 184–193. [Google Scholar]
- Su, Y. A trust based scheme to protect 5G UAV communication networks. IEEE Open J. Comput. Soc. 2021, 2, 300–307. [Google Scholar] [CrossRef]
- Kong, L.; Chen, B.; Hu, F. LAP-BFT: Lightweight asynchronous provable byzantine fault-tolerant consensus mechanism for UAV network. Drones 2022, 6, 187. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y.; Weng, W.; Chen, C.H.; Chiu, Y.J.; Wu, C.M. A traceable and privacy-preserving authentication for UAV communication control system. Electronics 2020, 9, 62. [Google Scholar] [CrossRef]
- Aljumah, A. UAV-Based Secure Data Communication: Multilevel Authentication Perspective. Sensors 2024, 24, 996. [Google Scholar] [CrossRef]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. Trust management in decentralized iot access control system. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Virtual, 2–6 May 2020; pp. 1–9. [Google Scholar]
- Jain, P.; Gyanchandani, M.; Khare, N. Differential privacy: Its technological prescriptive using big data. J. Big Data 2018, 5, 1–24. [Google Scholar] [CrossRef]
- Lee, H.; Yoon, J.; Jang, M.S.; Park, K.J. A robot operating system framework for secure uav communications. Sensors 2021, 21, 1369. [Google Scholar] [CrossRef]
- Levine, B.N.; Shields, C.; Margolin, N.B. A survey of solutions to the sybil attack. Univ. Mass. Amherst 2006, 7, 224. [Google Scholar]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil attacks and their defenses in the internet of things. IEEE Internet Things J. 2014, 1, 372–383. [Google Scholar] [CrossRef]
- Meamari, E.; Guo, H.; Shen, C.C.; Hur, J. Collusion attacks on decentralized attributed-based encryption: Analyses and a solution. arXiv 2020, arXiv:2002.07811. [Google Scholar]
- Marche, C.; Nitti, M. Trust-related attacks and their detection: A trust management model for the social IoT. IEEE Trans. Netw. Serv. Manag. 2020, 18, 3297–3308. [Google Scholar] [CrossRef]
- Sayghe, A.; Hu, Y.; Zografopoulos, I.; Liu, X.; Dutta, R.G.; Jin, Y.; Konstantinou, C. Survey of machine learning methods for detecting false data injection attacks in power systems. IET Smart Grid 2020, 3, 581–595. [Google Scholar] [CrossRef]
- Salem, O.; Alsubhi, K.; Shaafi, A.; Gheryani, M.; Mehaoua, A.; Boutaba, R. Man-in-the-Middle attack mitigation in internet of medical things. IEEE Trans. Ind. Inform. 2021, 18, 2053–2062. [Google Scholar] [CrossRef]
- Jensen, I.J.; Selvaraj, D.; Ranganathan, P. Blockchain Technology for Networked Swarms of Unmanned Aerial Vehicles (UAVs). In Proceedings of the 2019 IEEE 20th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Washington, DC, USA, 10–12 June 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Nigam, A.; Sharma, S.; Patel, R.K.; Agrawal, M. Man-in-the-middle-attack and proposed algorithm for detection. In Proceedings of the 2022 International Mobile and Embedded Technology Conference (MECON), Noida, India, 10–11 March 2022; pp. 83–88. [Google Scholar]
- Leahy, K.; Zhou, D.; Vasile, C.I.; Oikonomopoulos, K.; Schwager, M.; Belta, C. Persistent surveillance for unmanned aerial vehicles subject to charging and temporal logic constraints. Auton. Robots 2016, 40, 1363–1378. [Google Scholar] [CrossRef]
- Sun, S.; Ma, Z.; Liu, L.; Gao, H.; Peng, J. Detection of malicious nodes in drone ad-hoc network based on supervised learning and clustering algorithms. In Proceedings of the 2020 16th International Conference on Mobility, Sensing and Networking (MSN), Tokyo, Japan, 17–19 December 2020; pp. 145–152. [Google Scholar]
- Shen, Y.; Qu, Y.; Dong, C.; Zhou, F.; Wu, Q. Joint Training and Resource Allocation Optimization for Federated Learning in UAV Swarm. IEEE Internet Things J. 2023, 10, 2272–2284. [Google Scholar] [CrossRef]
- Chen, J.; Tian, Z.; Cui, X.; Yin, L.; Wang, X. Trust architecture and reputation evaluation for internet of things. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 3099–3107. [Google Scholar] [CrossRef]
- Chen, D.; Chang, G.; Sun, D.; Li, J.; Jia, J.; Wang, X. TRM-IoT: A trust management model based on fuzzy reputation for internet of things. Comput. Sci. Inf. Syst. 2011, 8, 1207–1228. [Google Scholar] [CrossRef]
- Tu, Z.; Zhou, H.; Li, K.; Song, H.; Yang, Y. A blockchain-based trust and reputation model with dynamic evaluation mechanism for IoT. Comput. Netw. 2022, 218, 109404. [Google Scholar] [CrossRef]
- Alaa, M.; Oumayma, A.; Mohamad, A. Towards Trust Model in Unmanned Aerial Vehicle Ad Hoc Networks. J. Commun. Softw. Syst. 2021, 17, 213–220. [Google Scholar] [CrossRef]
- Sharma, A.; Pilli, E.S.; Mazumdar, A.P.; Gera, P. Towards trustworthy Internet of Things: A survey on Trust Management applications and schemes. Comput. Commun. 2020, 160, 475–493. [Google Scholar] [CrossRef]
- Khan, A.S.; Chen, G.; Rahulamathavan, Y.; Zheng, G.; Assadhan, B.; Lambotharan, S. Trusted UAV Network Coverage Using Blockchain, Machine Learning, and Auction Mechanisms. IEEE Access 2020, 8, 118219–118234. [Google Scholar] [CrossRef]
- Li, X.; Li, R. A Comprehensive Review for Four-Dimensional Trust Management in Distributed IoT. IEEE Internet Things J. 2023, 10, 21738–21762. [Google Scholar] [CrossRef]
- Hu, N.; Tian, Z.; Sun, Y.; Yin, L.; Zhao, B.; Du, X.; Guizani, N. Building Agile and Resilient UAV Networks Based on SDN and Blockchain. IEEE Netw. 2021, 35, 57–63. [Google Scholar] [CrossRef]
- Ahamed Ahanger, T.; Aldaej, A.; Atiquzzaman, M.; Ullah, I.; Yousufudin, M. Distributed blockchain-based platform for unmanned aerial vehicles. Comput. Intell. Neurosci. 2022, 2022, 4723124. [Google Scholar] [CrossRef]
- Weerapanpisit, P.; Trilles, S.; Huerta, J.; Painho, M. A decentralized location-based reputation management system in the IoT using blockchain. IEEE Internet Things J. 2022, 9, 15100–15115. [Google Scholar] [CrossRef]
- Alkadi, R.; Alnuaimi, N.; Yeun, C.; Shoufan, A. Blockchain Interoperability in Unmanned Aerial Vehicles Networks: State-of-the-Art and Open Issues. IEEE Access 2022, 10, 14463–14479. [Google Scholar] [CrossRef]
- Lin, X.; Zhang, J.; Xiang, L.; Ge, X. Energy Consumption Optimization for UAV Assisted Private Blockchain-based IIoT Networks. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference (VTC2021-Fall), Virtual, 27–28 September 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Obaid, A.A.; Koyuncu, H. Obstacle Avoidance in Unmanned Aerial Vehicles Using Image Segmentation and Deep Learning. In Proceedings of the 2022 International Symposium on Multidisciplinary Studies and Innovative Technologies (ISMSIT), Ankara, Turkey, 20–22 October 2022; pp. 912–915. [Google Scholar] [CrossRef]
- Hale, B.; Bossuyt, D.L.V.; Papakonstantinou, N.; O’Halloran, B. A Zero-Trust Methodology for Security of Complex Systems With Machine Learning Components. In Proceedings of the 41st Computers and Information in Engineering Conference (CIE), Virtual, Online, 17–21 August 2021; Volume 2. [Google Scholar] [CrossRef]
- Wu, Y.; Yan, C.; Ding, Z.; Liu, G.; Wang, P.; Jiang, C.; Zhou, M. A Novel Method for Calculating Service Reputation. IEEE Trans. Autom. Sci. Eng. 2013, 10, 634–642. [Google Scholar] [CrossRef]
- Hendrikx, F.; Bubendorfer, K.; Chard, R. Reputation systems: A survey and taxonomy. J. Parallel Distrib. Comput. 2015, 75, 184–197. [Google Scholar] [CrossRef]
- Lu, Z.; Wang, Q.; Qu, G.; Liu, Z. BARS: A Blockchain-Based Anonymous Reputation System for Trust Management in VANETs. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 98–103. [Google Scholar] [CrossRef]
- Rahman, M.M.; Rifat, M.M.H.; Tanin, M.Y.; Hossain, N. A feedback system using blockchain technology. In Proceedings of the 2020 3rd International Conference on Intelligent Sustainable Systems (ICISS), Coimbatore, India, 3–5 December 2020; pp. 1114–1118. [Google Scholar] [CrossRef]
- Huang, C.; Wang, Z.; Chen, H.; Hu, Q.; Zhang, Q.; Wang, W.; Guan, X. Repchain: A reputation-based secure, fast, and high incentive blockchain system via sharding. IEEE Internet Things J. 2020, 8, 4291–4304. [Google Scholar] [CrossRef]
- Gyawali, S.; Qian, Y.; Hu, R.Q. Machine learning and reputation based misbehavior detection in vehicular communication networks. IEEE Trans. Veh. Technol. 2020, 69, 8871–8885. [Google Scholar] [CrossRef]
- Liu, D.; Alahmadi, A.; Ni, J.; Lin, X.; Shen, X. Anonymous reputation system for IIoT-enabled retail marketing atop PoS blockchain. IEEE Trans. Ind. Inform. 2019, 15, 3527–3537. [Google Scholar] [CrossRef]
- Magaia, N.; Sheng, Z. ReFIoV: A Novel Reputation Framework for Information-Centric Vehicular Applications. IEEE Trans. Veh. Technol. 2019, 68, 1810–1823. [Google Scholar] [CrossRef]
- Yang, Z.; Zheng, K.; Yang, K.; Leung, V.C.M. A blockchain-based reputation system for data credibility assessment in vehicular networks. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Zhou, R.; Hwang, K. Gossip-Based Reputation Aggregation for Unstructured Peer-to-Peer Networks. In Proceedings of the 2007 IEEE International Parallel and Distributed Processing Symposium, Long Beach, CA, USA, 26–30 March 2007. [Google Scholar] [CrossRef]
- Carholt, O.; Fresk, E.; Andrikopoulos, G.; Nikolakopoulos, G. Design, modelling and control of a single rotor UAV. In Proceedings of the 2016 24th Mediterranean Conference on Control and Automation (MED), Athens, Greece, 21–24 June 2016; pp. 840–845. [Google Scholar]
- Ventura Diaz, P.; Yoon, S. High-fidelity computational aerodynamics of multi-rotor unmanned aerial vehicles. In Proceedings of the 2018 AIAA Aerospace Sciences Meeting, Kissimmee, FL, USA, 8–12 January 2018; p. 1266. [Google Scholar]
- Cazaurang, F.; Cohen, K.; Kumar, M. Multi-Rotor Platform Based UAV Systems; Elsevier: Amsterdam, The Netherlands, 2020. [Google Scholar]
- Panagiotou, P.; Yakinthos, K. Aerodynamic efficiency and performance enhancement of fixed-wing UAVs. Aerosp. Sci. Technol. 2020, 99, 105575. [Google Scholar] [CrossRef]
- Bhandari, V. Use of Technology in Disaster Management. Unity J. 2022, 3, 292–304. [Google Scholar] [CrossRef]
- Euronews. Researchers from Switzerland Are Using Drones to Monitor the Health of the Rainforest, 2023. Available online: https://www.euronews.com/next/2023/07/28/researchers-from-switzerland-are-using-drones-to-monitor-the-health-of-the-rainforest (accessed on 21 May 2024).
- Hafeez, S.; Khan, A.R.; Al-Quraan, M.; Mohjazi, L.; Zoha, A.; Imran, M.A.; Sun, Y. Blockchain-Assisted UAV Communication Systems: A Comprehensive Survey. IEEE Open J. Veh. Technol. 2023, 4, 558–580. [Google Scholar] [CrossRef]
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV cellular communications: Practical aspects, standardization advancements, regulation, and security challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3417–3442. [Google Scholar] [CrossRef]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE Commun. Surv. Tutor. 2015, 18, 1123–1152. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhang, Y.; Guizani, M. Secure UAV communication networks over 5G. IEEE Wirel. Commun. 2019, 26, 114–120. [Google Scholar] [CrossRef]
- Liu, Y.; Gao, J.; Lu, Y.; Cao, R.; Yao, L.; Xia, Y.; Han, D. Lightweight Blockchain-Enabled Secure Data Sharing in Dynamic and Resource-limited UAV Networks. IEEE Netw. 2024. [Google Scholar] [CrossRef]
- Mehta, P.; Gupta, R.; Tanwar, S. Blockchain envisioned UAV networks: Challenges, solutions, and comparisons. Comput. Commun. 2020, 151, 518–538. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kumar, G. Machine learning for enhancing transportation security: A comprehensive analysis of electric and flying vehicle systems. Eng. Appl. Artif. Intell. 2024, 129, 107667. [Google Scholar] [CrossRef]
- Bithas, P.S.; Michailidis, E.T.; Nomikos, N.; Vouyioukas, D.; Kanatas, A.G. A survey on machine-learning techniques for UAV-based communications. Sensors 2019, 19, 5170. [Google Scholar] [CrossRef]
- Tlili, F.; Ayed, S.; Fourati, L.C. Exhaustive distributed intrusion detection system for UAVs attacks detection and security enforcement (E-DIDS). Comput. Secur. 2024, 142, 103878. [Google Scholar] [CrossRef]
- Zeng, Y.; Wu, Q.; Zhang, R. Accessing from the sky: A tutorial on UAV communications for 5G and beyond. Proc. IEEE 2019, 107, 2327–2375. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.H.; Debbah, M. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef]
- Mohsan, S.A.H.; Othman, N.Q.H.; Li, Y.; Alsharif, M.H.; Khan, M.A. Unmanned aerial vehicles (UAVs): Practical aspects, applications, open challenges, security issues, and future trends. Intell. Serv. Robot. 2023, 16, 109–137. [Google Scholar] [CrossRef]
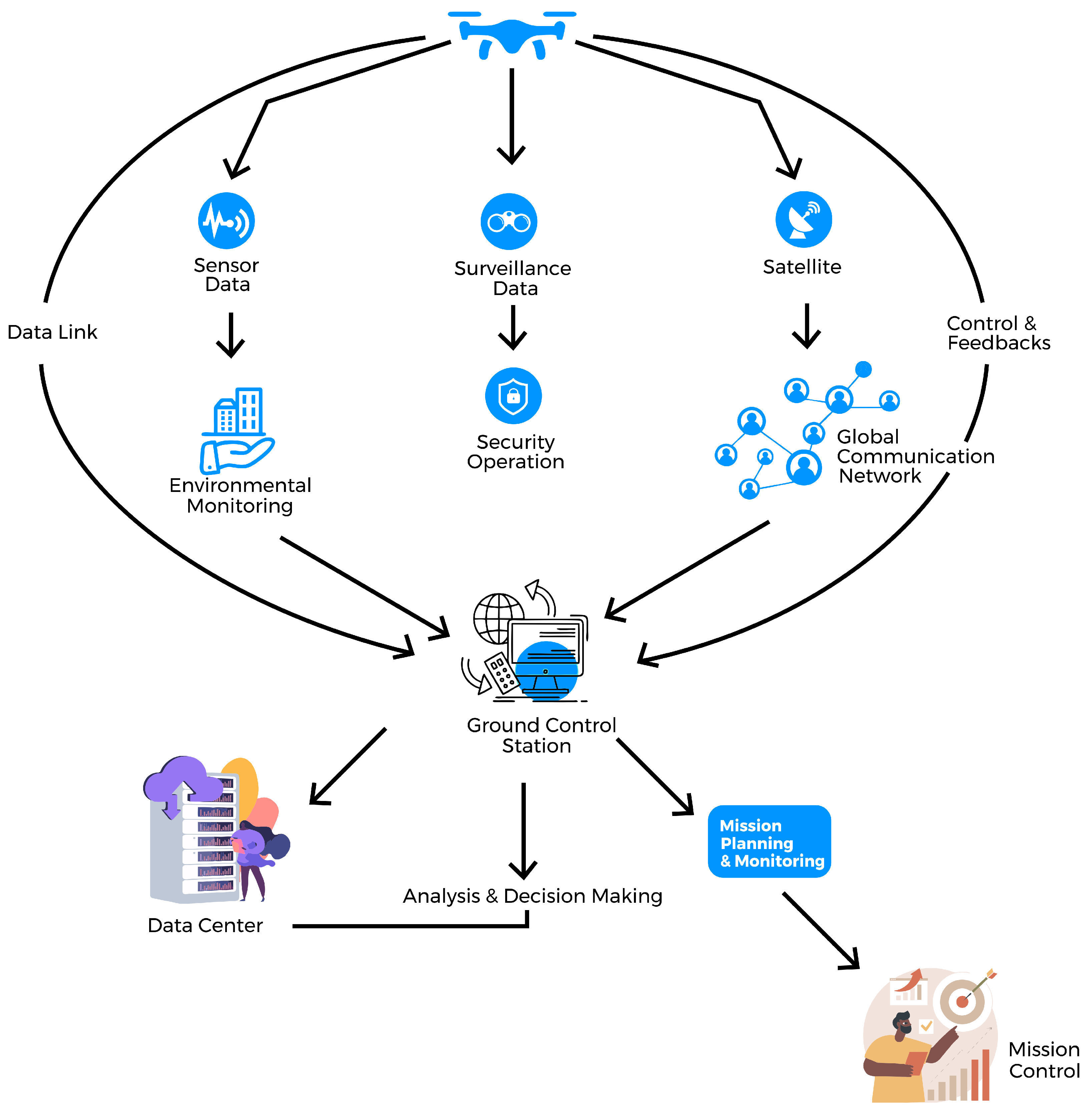
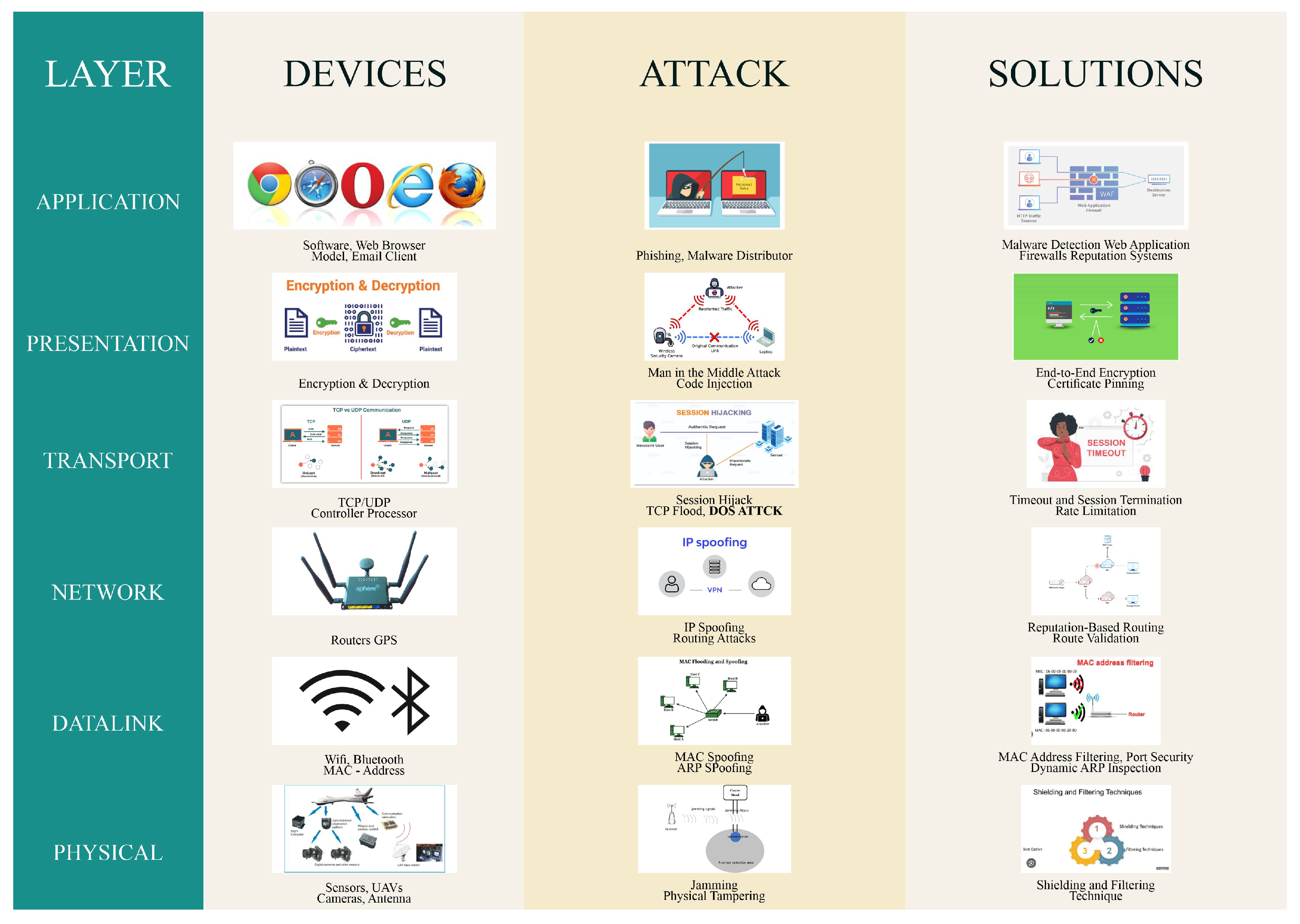
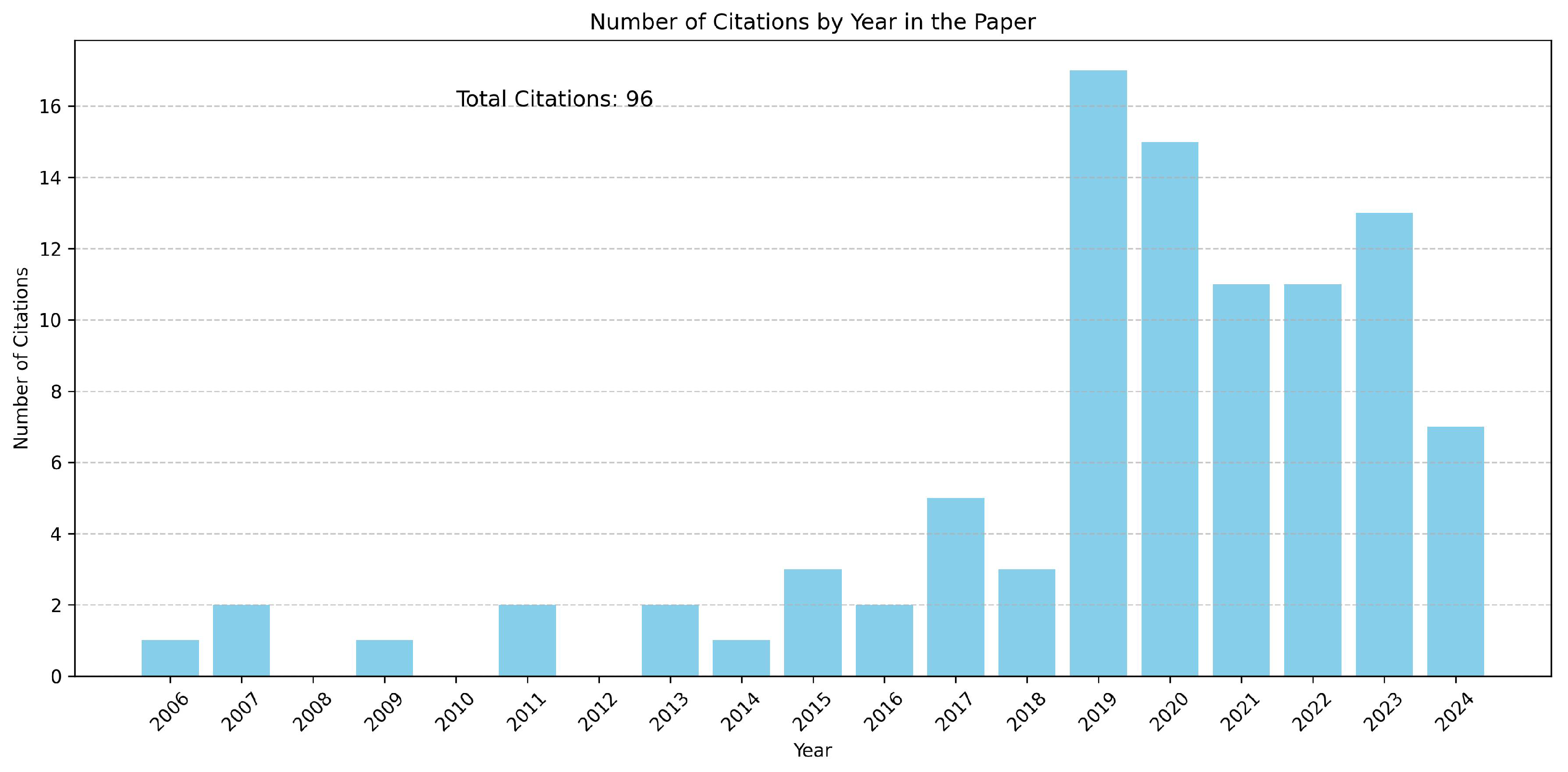
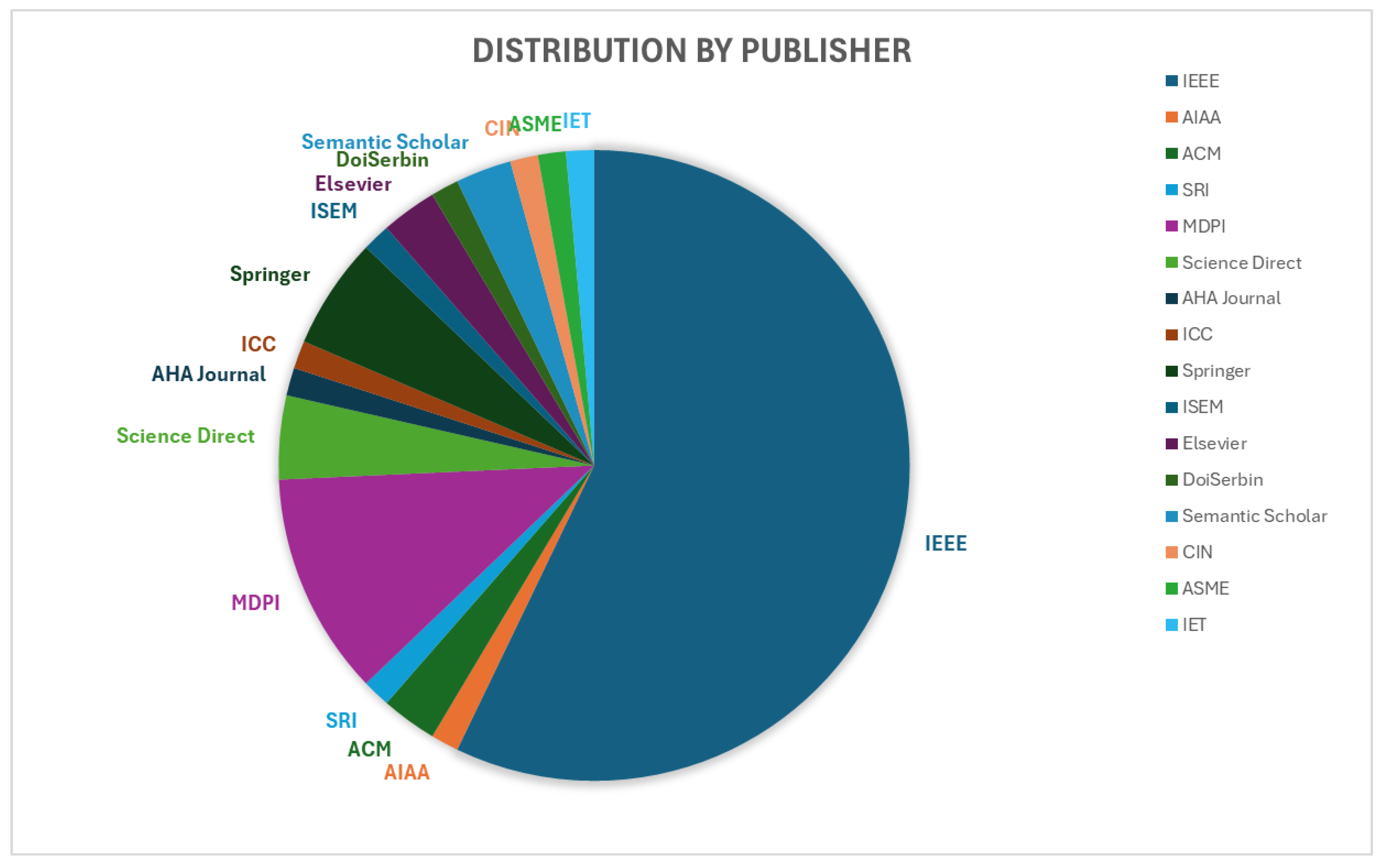
| Category | Papers |
|---|---|
| Security | [2,3,7,8,9,10,11,12,14,15,22,24,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53]. |
| Trust | [1,4,5,6,13,17,18,20,25,29,35,36,40,46,49,54,55,56,57,58,59,60,61,62,63,64,65,66,67]. |
| Reputation | [4,13,16,17,19,20,21,22,23,24,26,31,33,49,53,54,55,56,63,64,65,68,69,70,71,72,73,74,75,76,77]. |
| General | [78,79,80,81,82,83] |
| Approach | Model/Method | Goals | Weaknesses | |
|---|---|---|---|---|
| [62] | Computational intelligence approach, including ML algorithms for UAV systems | Semi-autonomous blockchain-based UAV framework | Enhancing the security, efficiency, and reliability of UAV communication networks using blockchain technology | The limited scalability of blockchain for UAV applications, as well as the potential vulnerabilities in smart contracts |
| [19] | Reputation management framework that determines the trust of an event message and the reputation of the message producer | Majority voting protocol | Enhances event detection, trust management, reliable data transmission, and security functions in UAVs and IoTs | It does not explicitly mention the trade-offs or limitations of the proposed reputation management framework |
| [59] | Auction-based game theory, ML, and blockchain | Machine Learning | The autonomous selection and operation of UAVs for network coverage, along with real-time service monitoring and SLA management in wireless networks | It does not explicitly mention the specific ML algorithm used in developing the service reputation-based trust model |
| [51] | Optimization models such as MILP, to achieve efficient task assignments and resource allocation for persistent and efficient missions | Optimization and scheduling aspects of surveillance missions | Enhances the ability to conduct continuous, long-term, and efficient surveillance missions with multiple UAVs | Mixed integer linear program (MILP) model |
| [60] | Analyzing the overall architecture of TM and its development | Subjective logic theory, fuzzy logic theory, theory of evidence, and neural network model | Addresses the need for trust management to detect false messages while enhancing the understanding of trust management in IoT environments and its impact on security and reliability | It does not explicitly mention the use of blockchain technology |
| [74] | Design and implementation of a blockchain-based reputation system, focusing on ensuring transparency, reliability, and privacy in reputation management | Cryptographic and blockchain-based design | High privacy guarantees for consumers, efficiency, and security when integrated with a PoS blockchain. Enhances transparency and reliability in reputation management | Implementation challenges of a blockchain-based architecture and the need for further improvement in the overall system efficiency |
| [70] | Exploits the features of blockchain to extend conventional public key infrastructure (PKI) with an efficient privacy-preserving authentication mechanism | Blockchain-based anonymous reputation system (BARS) | BARS extends conventional PKI with an efficient privacy-preserving authentication mechanism and eliminates linkability between the public key and the real identity of a vehicle | The paper makes assumptions about the security levels of the law enforcement authority (LEA) and the capability of adversaries to compromise roadside units (RSUs) |
| [75] | ReFIoV, which leverages ML and an artificial immune system (AIS) to address the data accessibility problem in vehicular networks | Bayesian learning and classification, K-Means clustering, and danger theory | Presents a slow convergence in reputation establishment | Enhances and solves the improvement of data accessibility in vehicular networks, providing incentives for caching and stimulating node cooperation |
| [24] | Dynamic decentralized reputation system that utilizes blockchain technology for reputation storage and update | Fully decentralization, general purpose, global reputation, privacy, and employed technologies | This enhances the security and decentralization of the reputation management system in decentralized environments | Potential limitations of blockchain scalability, which requires special attention for decentralized systems relying on blockchain |
| [32] | Use of blockchain technology, particularly the Ethereum blockchain, for privacy-preserving authentication in ITS networks | Not specific | The model aims to address the vulnerabilities and loopholes present in existing systems, such as fake message delivery and privacy concerns | Lack of detailed discussion on the specific ML techniques or classification models used in the proposed BPPAU model |
| [52] | A malicious UAV detection algorithm (MDA) based on linear regression and a Gaussian clustering algorithms | Linear regression and Gaussian clustering algorithms | It enhances the accuracy of malicious node detection, with the accuracy of MDA outperforming existing methods by 10–20% | Does not address the use of blockchain technology for enhancing security in a UAV ad hoc network |
| [63] | Leveraging blockchain technology to manage the reputation values of IoT devices based on their geographical location. | Tree data structure | geocoding techniques and geospatial smart contracts for system performance and efficiency, and the decentralized management of device services and their reputation values | Gas limits in Ethereum transactions, hardware limitations of fog devices, and the lack of a positioning module for edge devices |
| [33] | Incentive scheme to choose UAVs with a high reputation to perform sensing tasks, protecting data sharing between UAVs and task publishers from internal attacks | Deep reinforcement learning model | The security of data sharing among UAVs and task publishers, as well as the successful mining of probabilities and utilities of UAVs | It does not thoroughly discuss the potential scalability issues or computational overhead associated with a blockchain-based secure data transmission scheme |
| [76] | A temporary center node called the miner is elected from vehicles through specific rules to generate rating blocks and broadcast them to other vehicles | Message detection accuracy | Improve credibility assessment of received messages based on observations of traffic environments and the consensus of ratings stored in the blockchain | Lack of specific details about the consensus protocol used in the blockchain-based reputation system |
| [77] | Fully distributed, secure, scalable, and efficient reputation aggregation scheme | Gossip-based reputation aggregation and decentralized reputation management | Enhances trustworthiness and cooperation in P2P networks by discouraging maliciousness | It does not guarantee computational efficiency and scalability |
| Key Area | Findings | Contributions |
|---|---|---|
| Trust in UAV Networks | Trust is critical for UAV operations, involving reliability, security, safety, transparency, and ethical conduct. | Detailed analysis of trust components and their impact on UAV network performance to improve the framework. |
| Security Measures | Essential security measures include encryption, authentication protocols, and intrusion detection systems. | Proposed robust security frameworks to protect data integrity and privacy in UAV networks. |
| Privacy Concerns | Privacy involves protecting sensitive data from unauthorized access and ensuring compliance with legal standards. | Suggested data anonymization and secure storage solutions to enhance privacy protections in UAV networks. |
| Centralized vs. Decentralized | Centralized networks face challenges from single points of failure and security risks, whereas decentralized architectures offer enhanced resilience. | Advocated for adopting decentralized systems, highlighting blockchain technology’s role in improving security and trust. |
| Reputation Systems | Reputation systems are vital for assessing trustworthiness and ensuring reliable data exchange in UAV networks. | Comprehensive survey of existing reputation systems and their application in UAV networks. |
| Mitigation Strategies | Strategies for mitigating vulnerabilities include robust encryption, secure communication channels, and regular security audits. | Provided actionable insights and best practices for enhancing UAV network security. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ogunbunmi, S.; Chen, Y.; Blasch, E.; Chen, G. A Survey on Reputation Systems for UAV Networks. Drones 2024, 8, 253. https://doi.org/10.3390/drones8060253
Ogunbunmi S, Chen Y, Blasch E, Chen G. A Survey on Reputation Systems for UAV Networks. Drones. 2024; 8(6):253. https://doi.org/10.3390/drones8060253
Chicago/Turabian StyleOgunbunmi, Simeon, Yu Chen, Erik Blasch, and Genshe Chen. 2024. "A Survey on Reputation Systems for UAV Networks" Drones 8, no. 6: 253. https://doi.org/10.3390/drones8060253
APA StyleOgunbunmi, S., Chen, Y., Blasch, E., & Chen, G. (2024). A Survey on Reputation Systems for UAV Networks. Drones, 8(6), 253. https://doi.org/10.3390/drones8060253









