Security Supply Chain Using UAVs: Validation and Development of a UAV-Based Model for Qatar’s Mega Sporting Events
Abstract
:1. Introduction
- To identify the challenges in the SCM process;
- To propose a research framework for the implementation of UAS-based cybersecurity for SCM at Qatar’s mega sporting events;
- To assess the upstream, midstream, and downstream stages in the implementation of the UAS-based cybersecurity model for SCM at Qatar’s mega sporting events;
- To develop a testable UAV-based security framework for the SCM of security and safety measures.
2. Literature Review
2.1. Diffusion of Innovation (DOI) Theory
2.2. Cyber Threats and Attacks at Mega Sporting Events
2.3. Challenges in UAS-Based Security at Mega Sporting Events
2.4. Unmanned Aerial Vehicle-Based Security and SCM
3. Research Methodology
3.1. Research Method
3.2. Conceptualization of the Measurement Scales
3.3. Data Collection Procedure
3.4. Data Analysis
- (1)
- Data reduction: It simplifies data by grouping correlated variables into smaller factors, making it easier to understand and interpret the data;
- (2)
- Identifying underlying constructs: EFA helps to reveal the latent factors or constructs that underpin the relationships among variables;
- (3)
- Construct validity: EFA provides evidence of construct validity by showing that the variables in a factor are related and measure the same underlying construct.
- (1)
- Model testing: CFA tests whether the observed data fit the hypothesized factor structure, which is specified by the researcher beforehand;
- (2)
- Construct validity: CFA examines the relationships among the variables and the factors, assessing convergent validity, discriminant validity, and nomological validity;
- (3)
- Reliability: CFA evaluates the reliability or internal consistency of the factors by examining the factor loadings, composite reliability, and average variance extracted.
4. Data Analysis and Findings
4.1. Common Method Bias (CMB)
4.2. Exploratory Factor Analysis (EFA)
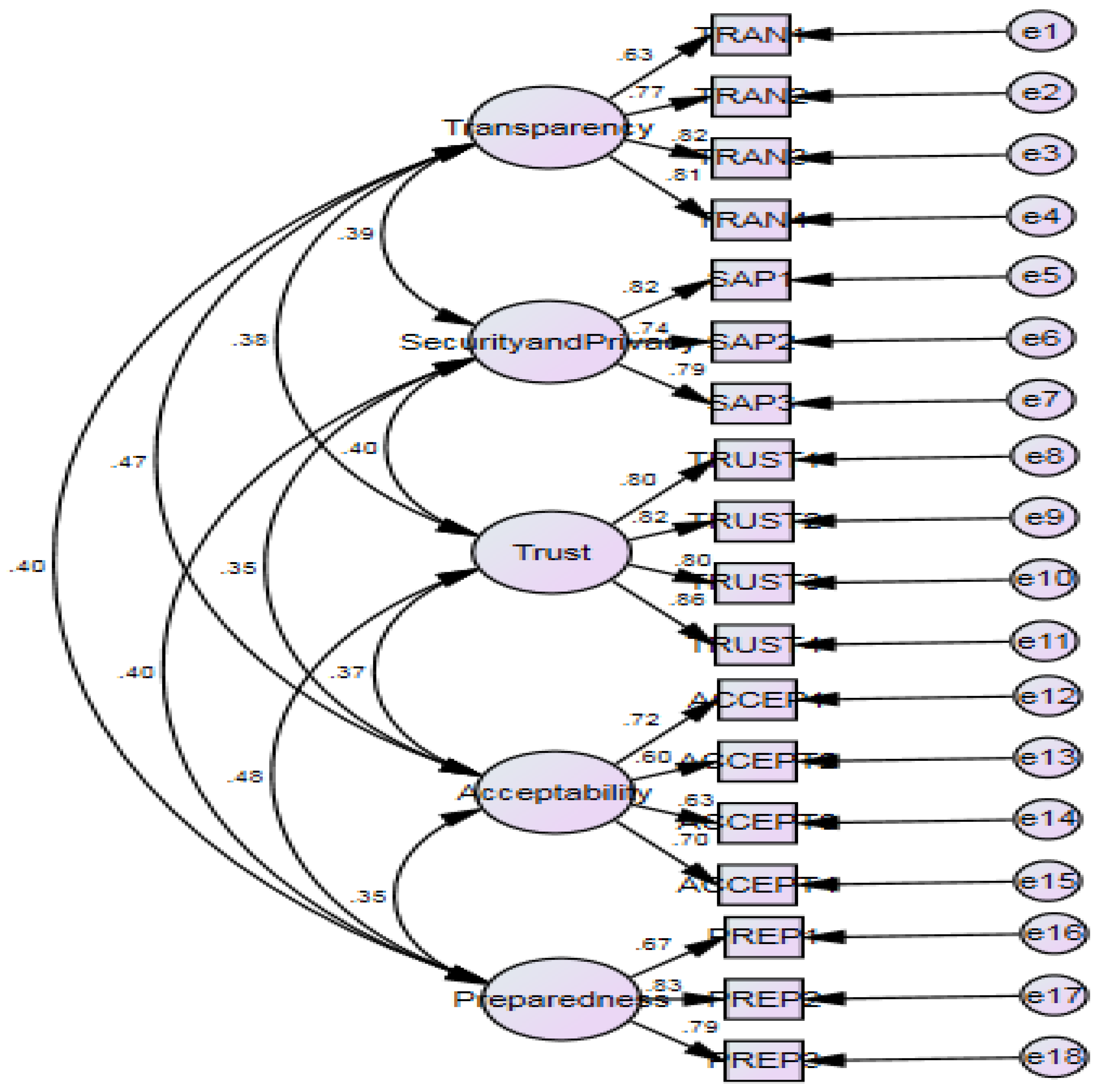
4.3. Confirmatory Factor Analysis (CFA)
4.4. Model Fit Indices
5. Discussion
5.1. Managerial Implications
5.2. Limitations and Future Directions
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Survey Questionnaire
| Demographic Variables | ||
|---|---|---|
| Gender |
| |
| Company nature |
| |
| Company age |
| |
| Working experience |
| |
| Number of employees |
| |
| Education level |
| |
| Survey Items | ||
| Traceability | TRAN1 | I support the use of drones for the safety and security of mega sporting events. |
| TRAN2 | I think drones should be traceable. | |
| TRAN3 | A drone traces the information collected and stored. | |
| TRAN4 | I ensure drones are regulated to ensure traceability. | |
| TRAN5 | Drones share information with authorities or other stakeholders. | |
| Security and privacy | SAP1 | I am sure that drone operators respect your privacy during mega sporting events. |
| SAP2 | I trust the government to regulate drones to protect privacy and security at mega sporting events. | |
| SAP3 | I believe that drones are equipped with privacy and security features, such as the ability to blur faces or license plates. | |
| SAP4 | I am sure that drones are secured against hacking and other cyber threats at mega sporting events. | |
| Trust | TRUST1 | I trust drone operators to follow safety and security protocols at mega sporting events. |
| TRUST2 | I trust the government to regulate drones for safety and security at mega sporting events. | |
| TRUST3 | I trust the technology used in drones to ensure their safe and secure operation at mega sporting events. | |
| TRUST4 | I trust that drones are secured against hacking and other cyber threats. | |
| Acceptability | ACCEPT1 | I am comfortable with drones flying near mega sporting events. |
| ACCEPT2 | I support the use of drones for delivering security tools during mega sporting events. | |
| ACCEPT3 | I keep using drones for search and rescue operations at mega sporting events. | |
| ACCEPT4 | I keep trying to implement drones in international mega sporting events. | |
| Preparedness | PREP1 | I am confident that drones can ensure safety and responsibility at mega sporting events. |
| PREP2 | I am prepared to deal with concerns about using drones at mega sporting events. | |
| PREP3 | I am confident in drones’ ability to use technology for search and rescue missions or other emergencies. | |
References
- Ardito, L.; Petruzzelli, A.M.; Panniello, U.; Garavelli, A.C. Towards Industry 4.0: Mapping digital technologies for supply chain management-marketing integration. Bus. Process Manag. J. 2018, 25, 323–346. [Google Scholar] [CrossRef]
- Tiwari, S.; Wee, H.M.; Daryanto, Y. Big data analytics in supply chain management between 2010 and 2016: Insights to industries. Comput. Ind. Eng. 2018, 115, 319–330. [Google Scholar] [CrossRef]
- Patnayakuni, R.; Rai, A.; Seth, N. Relational antecedents of information flow integration for supply chain coordination. J. Manag. Inf. Syst. 2006, 23, 13–49. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones’ systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Yeboah-Ofori, A.; Islam, S.; Lee, S.W.; Shamszaman, Z.U.; Muhammad, K.; Altaf, M.; Al-Rakhami, M.S. Cyber threat predictive analytics for improving cyber supply chain security. IEEE Access 2021, 9, 94318–94337. [Google Scholar] [CrossRef]
- Thakur, K.; Qiu, M.; Gai, K.; Ali, M.L. An investigation on cyber security threats and security models. In Proceedings of the 2015 IEEE 2nd International Conference on Cyber Security and Cloud Computing, New York, NY, USA, 3–5 November 2015; pp. 307–311. [Google Scholar]
- Theodoropoulou, I.; Alos, J. Expect amazing! Branding Qatar as a sports tourism destination. Vis. Commun. 2020, 19, 13–43. [Google Scholar] [CrossRef]
- Jago, L.; Dwyer, L.; Lipman, G.; van Lill, D.; Vorster, S. Optimising the potential of mega-events: An overview. Int. J. Event Festiv. Manag. 2010, 1, 220–237. [Google Scholar] [CrossRef]
- Greig, A.W.; Guoth, N. Abandon Hope All Ye Who Practice Here: Soccer and Sport Space in 1920s Australia. In Proceedings of the Annual Conference of the Australian Sociological Association (TASA 2011), Newcastle, UK, 28 November–1 December 2011. [Google Scholar]
- Cooper, B.; Chen, K.; Feist, Z.; Kapelke, C. The Cybersecurity of Olympics Sports: New Opportunities, New Risks; Center for Long-Term Cybersecurity: Berkeley, CA, USA, 2017. [Google Scholar]
- Finkelstein, A. Cyber Security at Major Sporting Events. Israel Defense, December 2016. Available online: http://www.israeldefense.co.il/en/content/cyber-security-major-sporting-events (accessed on 7 December 2016).
- Talavera, A.M.; Al-Ghamdi, S.G.; Koç, M. Sustainability in mega-events: Beyond Qatar 2022. Sustainability 2019, 11, 6407. [Google Scholar] [CrossRef]
- Giulianotti, R.; Klauser, F. Introduction: Security and surveillance at sport mega events. Urban Stud. 2011, 48, 3157–3168. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Blanco-Novoa, O.; Froiz-Míguez, I.; Fraga-Lamas, P. Towards an autonomous industry 4.0 warehouse: A UAV and blockchain-based system for inventory and traceability applications in big data-driven supply chain management. Sensors 2019, 19, 2394. [Google Scholar] [CrossRef]
- Hopkins, J.L. An investigation into emerging industry 4.0 technologies as drivers of supply chain innovation in Australia. Comput. Ind. 2021, 125, 103323. [Google Scholar] [CrossRef]
- Raji, I.O.; Shevtshenko, E.; Rossi, T.; Strozzi, F. Industry 4.0 technologies as enablers of lean and agile supply chain strategies: An exploratory investigation. Int. J. Logist. Manag. 2021, 32, 1150–1189. [Google Scholar] [CrossRef]
- Haji, M.; Kerbache, L.; Muhammad, M.; Al-Ansari, T. Roles of technology in improving perishable food supply chains. Logistics 2020, 4, 33. [Google Scholar] [CrossRef]
- Abbas, Y.; Martinetti, A.; Moerman, J.J.; Hamberg, T.; van Dongen, L.A. Do you have confidence in how your rolling stock has been maintained? A blockchain-led knowledge-sharing platform for building trust between stakeholders. Int. J. Inf. Manag. 2020, 55, 102228. [Google Scholar] [CrossRef]
- Roy, M.; Roy, A. Nexus of internet of things (IoT) and big data: Roadmap for smart management systems (SMgS). IEEE Eng. Manag. Rev. 2019, 47, 53–65. [Google Scholar] [CrossRef]
- Büyüközkan, G.; Göçer, F. Digital Supply Chain: Literature review and a proposed framework for future research. Comput. Ind. 2018, 97, 157–177. [Google Scholar] [CrossRef]
- Jahani, N.; Sepehri, A.; Vandchali, H.R.; Tirkolaee, E.B. Application of industry 4.0 in the procurement processes of supply chains: A systematic literature review. Sustainability 2021, 13, 7520. [Google Scholar] [CrossRef]
- Liu, K.S.; Lin, M.H. Performance Assessment on the Application of Artificial Intelligence to Sustainable Supply Chain Management in the Construction Material Industry. Sustainability 2021, 13, 12767. [Google Scholar] [CrossRef]
- Chen, Y.H.; Huang, L.C.; Lin, I.C.; Hwang, M.S. Research on the Secure Financial Surveillance Blockchain Systems. Int. J. Netw. Secur. 2020, 22, 708–716. [Google Scholar]
- Li, X.; Sun, Y. Network Evolutionary Game-Based Diffusion Mechanism regarding the Nonperformance of Farmers in Agricultural Supply Chain Finance. Discret. Dyn. Nat. Soc. 2022, 2022, 8550974. [Google Scholar] [CrossRef]
- Mukherjee, A.; Misra, S.; Chandra VS, P.; Obaidat, M.S. Resource-optimized multiarmed bandit-based offload path selection in edge UAV swarms. IEEE Internet Things J. 2018, 6, 4889–4896. [Google Scholar] [CrossRef]
- Jiménez López, J.; Mulero-Pázmány, M. Drones for conservation in protected areas: Present and future. Drones 2019, 3, 10. [Google Scholar] [CrossRef]
- Na, Z.; Liu, Y.; Shi, J.; Liu, C.; Gao, Z. UAV-supported clustered NOMA for 6G-enabled Internet of Things: Trajectory planning and resource allocation. IEEE Internet Things J. 2020, 8, 15041–15048. [Google Scholar] [CrossRef]
- Aslam, J.; Saleem, A.; Khan, N.T.; Kim, Y.B. Factors influencing blockchain adoption in supply chain management practices: A study based on the oil industry. J. Innov. Knowl. 2021, 6, 124–134. [Google Scholar] [CrossRef]
- Ganji, S.K. Leveraging the World Cup: Mega sporting events, human rights risk, and worker welfare reform in Qatar. J. Migr. Hum. Secur. 2016, 4, 221–259. [Google Scholar] [CrossRef]
- Gupta, R.; Shukla, A.; Mehta, P.; Bhattacharya, P.; Tanwar, S.; Tyagi, S.; Kumar, N. Vahak: A blockchain-based outdoor delivery scheme using uav for healthcare 4.0 services. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 255–260. [Google Scholar]
- Bhatti, B.M.; Mubarak, S.; Nagalingam, S. Information security implications of using NLP in IT outsourcing: A Diffusion of Innovation theory perspective. Autom. Softw. Eng. 2021, 28, 12. [Google Scholar] [CrossRef]
- Kolini, F. Two heads are better than one: A theoretical model for cybersecurity intelligence sharing (CIS) between organisations. In Proceedings of the ACIS 2017: The 6th Asian Conference on Information Systems, Phnom Penh, Cambodia, 12–14 December 2017. [Google Scholar]
- Nasser, A.L. Identification and prevention of expected cybersecurity threats during 2022 FIFA World Cup in Qatar. J. Poverty Investig. Dev. 2020, 5, 49–84. [Google Scholar]
- Haghirian, M.; Robles-Gil, P. Soft Power and the 2022 World Cup in Qatar: Learning from Experiences of Past Mega-Sporting Event Hosts. Tajseer J. 2021, 3. [Google Scholar] [CrossRef]
- Serdar, M.Z.; Al-Ghamdi, S.G. Resiliency assessment of road networks during mega sport events: The case of FIFA World Cup Qatar 2022. Sustainability 2021, 13, 12367. [Google Scholar] [CrossRef]
- Ponzio, R.; Kiel, R.; Larik, J.; Petcu, C.; Swanson, J. Reimagining Global Governance in a Multipolar World: Doha Forum 2019; The Stimson Center: Doha, Qatar, 2019. [Google Scholar]
- Lykou, G.; Moustakas, D.; Gritzalis, D. Defending airports from UAS: A survey on cyber-attacks and counter-drone sensing technologies. Sensors 2020, 20, 3537. [Google Scholar] [CrossRef]
- Corona, B.; Shen, L.; Reike, D.; Carreón, J.R.; Worrell, E. Towards sustainable development through the circular economy—A review and critical assessment on current circularity metrics. Resour. Conserv. Recycl. 2019, 151, 104498. [Google Scholar] [CrossRef]
- Schraven, D.; Bukvić, U.; Di Maio, F.; Hertogh, M. Circular transition: Changes and responsibilities in the Dutch stony material supply chain. Resour. Conserv. Recycl. 2019, 150, 104359. [Google Scholar] [CrossRef]
- Ellen Macarthur Foundation. Towards the Circular Economy. 2013. Available online: https://www.ellenmacarthurfoundation.org/assets/downloads/publications/Ellen-MacArthur-Foundation-Towards-the-Circular-Economy-vol.1.pdf (accessed on 12 June 2013).
- Bressanelli, G.; Perona, M.; Saccani, N. Challenges in supply chain redesign for the Circular Economy: A literature review and a multiple case study. Int. J. Prod. Res. 2019, 57, 7395–7422. [Google Scholar] [CrossRef]
- Mangla, S.K.; Luthra, S.; Mishra, N.; Singh, A.; Rana, N.P.; Dora, M.; Dwivedi, Y. Barriers to effective circular supply chain management in a developing country context. Prod. Plan. Control 2018, 29, 551–569. [Google Scholar] [CrossRef]
- Levering, R.; Vos, B. Organizational drivers and barriers to circular supply chain operations. In Operations Management and Sustainability; Palgrave Macmillan: Cham, Switzerland, 2019; pp. 43–66. [Google Scholar]
- Saroha, M.; Garg, D.; Luthra, S. Key Issues and Challenges in Circular Supply Chain Management Implementation-A SystematicReview. Int. J. Appl. Eng. Res. 2018, 13, 91–104. [Google Scholar]
- Pan, S.Y.; Du, M.A.; Huang, I.T.; Liu, I.H.; Chang, E.E.; Chiang, P.C. Strategies on implementation of waste-to-energy (WTE) supply chain for circular economy system: A review. J. Clean. Prod. 2015, 108, 409–421. [Google Scholar] [CrossRef]
- Verboeket, V.; Krikke, H. The disruptive impact of additive manufacturing on supply chains: A literature study, conceptual framework and research agenda. Comput. Ind. 2019, 111, 91–107. [Google Scholar] [CrossRef]
- Govindan, K.; Hasanagic, M. A systematic review on drivers, barriers, and practices towards circular economy: A supply chain perspective. Int. J. Prod. Res. 2018, 56, 278–311. [Google Scholar] [CrossRef]
- Aggarwal, A.; Gupta, S.; Ojha, M.K. Evaluation of key challenges to industry 4.0 in Indian context: A DEMATEL approach. In Advances in Industrial and Production Engineering; Springer: Singapore, 2019; pp. 387–396. [Google Scholar]
- Meisner, M. Financial consequences of cyber attacks leading to data breaches in healthcare sector. Copernic. J. Financ. Account. 2017, 6, 63–73. [Google Scholar] [CrossRef]
- Sahoo, S.; Mishra, S.; Peng, J.C.H.; Dragičević, T. A stealth cyber-attack detection strategy for DC microgrids. IEEE Trans. Power Electron. 2018, 34, 8162–8174. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.H.; Debbah, M. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef]
- Manesh, M.R.; Kaabouch, N. Cyber-attacks on unmanned aerial system networks: Detection, countermeasure, and future research directions. Comput. Secur. 2019, 85, 386–401. [Google Scholar] [CrossRef]
- Nguyen, T.; Tran, N.; Loven, L.; Partala, J.; Kechadi, M.T.; Pirttikangas, S. Privacy-aware blockchain innovation for 6G: Challenges and opportunities. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Goda, M.P. Blockchain Enabled Vaccine Supply Chain Provenance. Master’s Thesis, Penn State University, State College, PA, USA, 2021. [Google Scholar]
- Creswell, J.W.; Creswell, J.D. Research Design: Qualitative, Quantitative, and Mixed Methods Approaches; Sage Publications: Thousand Oaks, CA, USA, 2017. [Google Scholar]
- Hart, A.G.; Carpenter, W.S.; Hlustik-Smith, E.; Reed, M.; Goodenough, A.E. Testing the potential of Twitter mining methods for data acquisition: Evaluating novel opportunities for ecological research in multiple taxa. Methods Ecol. Evol. 2018, 9, 2194–2205. [Google Scholar] [CrossRef]
- Tranfield, D.; Denyer, D.; Smart, P. Towards a methodology for developing evidence-informed management knowledge by means of systematic review. Br. J. Manag. 2003, 14, 207–222. [Google Scholar] [CrossRef]
- Shelby, L.B.; Vaske, J.J. Understanding meta-analysis: A review of the methodological literature. Leis. Sci. 2008, 30, 96–110. [Google Scholar] [CrossRef]
- Gorsuch, R.L. Exploratory factor analysis: Its role in item analysis. J. Personal. Assess. 1997, 68, 532–560. [Google Scholar] [CrossRef]
- Kline, R.B. Principles and Practice of Structural Equation Modelling; Guilford Press: New York, NY, USA, 2011. [Google Scholar]
- Shrestha, N. Factor analysis as a tool for survey analysis. Am. J. Appl. Math. Stat. 2021, 9, 4–11. [Google Scholar] [CrossRef]
- Armstrong, J.S.; Overton, T.S. Estimating nonresponse bias in mail surveys. J. Mark. Res. 1977, 14, 396–402. [Google Scholar] [CrossRef]
- Podsakoff, P.M.; MacKenzie, S.B.; Lee, J.Y.; Podsakoff, N.P. Common method biases in behavioral research: A critical review of the literature and recommended remedies. J. Appl. Psychol. 2003, 88, 879. [Google Scholar] [CrossRef]
- Bag, S.; Yadav, G.; Dhamija, P.; Kataria, K.K. Key resources for industry 4.0 adoption and its effect on sustainable production and circular economy: An empirical study. J. Clean. Prod. 2021, 281, 125233. [Google Scholar] [CrossRef]
- Osborne, J.W.; Costello, A.B.; Kellow, J.T. Best practices in exploratory factor analysis. In Best Practices in Quantitative Methods; Sage Publishers: Thousand Oaks, CA, USA, 2008; pp. 86–102. [Google Scholar] [CrossRef]
- Shkeer, A.S.; Awang, Z. Exploring the items for measuring the marketing information system construct: An exploratory factor analysis. Int. Rev. Manag. Mark. 2019, 9, 87. [Google Scholar] [CrossRef]
- Kaiser, H.F. An index of factorial simplicity. Psychometrika 1974, 39, 31–36. [Google Scholar] [CrossRef]
- Polit, D.F.; Beck, C.T. Resource Manual for Nursing Research: Generating and Assessing Evidence for Nursing Practice, 10th ed.; Wolters Kluwer, Lippincott Williams & Wilkins: Philadelphia, PA, USA, 2012. [Google Scholar]
- Hadi, N.U.; Abdullah, N.; Sentosa, I. An easy approach to exploratory factor analysis: Marketing perspective. J. Educ. Soc. Res. 2016, 6, 215. [Google Scholar]
- Yong, A.G.; Pearce, S. A beginner’s guide to factor analysis: Focusing on exploratory factor analysis. Tutor. Quant. Methods Psychol. 2013, 9, 79–94. [Google Scholar] [CrossRef]
- Truong, Y.; McColl, R. Intrinsic motivations, self-esteem, and luxury goods consumption. J. Retail. Consum. Serv. 2011, 18, 555–561. [Google Scholar] [CrossRef]
- McNeish, D. Thanks coefficient alpha, we’ll take it from here. Psychol. Methods 2018, 23, 412. [Google Scholar] [CrossRef]
- Trizano-Hermosilla, I.; Alvarado, J.M. Best alternatives to Cronbach’s alpha reliability in realistic conditions: Congeneric and asymmetrical measurements. Front. Psychol. 2016, 7, 769. [Google Scholar] [CrossRef]
- Kiliç, S. Cronbach’s alpha reliability coefficient. Psychiatry Behav. Sci. 2016, 6, 47. [Google Scholar]
- Bruyn, G.A.W.; Pineda, C.; Hernandez-Diaz, C.; Ventura-Rios, L.; Moya, C.; Garrido, J.; Groen, H.; Pena, A.; Espinosa, R.; Möller, I.; et al. Validity of ultrasonography and measures of adult shoulder function and reliability of ultrasonography in detecting shoulder synovitis in patients with rheumatoid arthritis using magnetic resonance imaging as a gold standard. Arthritis Care Res. 2010, 62, 1079–1086. [Google Scholar] [CrossRef]
- Hair, J.F., Jr.; Sarstedt, M.; Hopkins, L.; Kuppelwieser, V.G. Partial least squares structural equation modeling (PLS-SEM): An emerging tool in business research. Eur. Bus. Rev. 2014, 26, 106–121. [Google Scholar] [CrossRef]
- Sarstedt, M.; Ringle, C.M.; Smith, D.; Reams, R.; Hair, J.F., Jr. Partial least squares structural equation modeling (PLS-SEM): A useful tool for family business researchers. J. Fam. Bus. Strategy 2014, 5, 105–115. [Google Scholar] [CrossRef]
- Arbuckle, J.L. IBM SPSS Amos 20 User’s Guide; Amos Development Corporation, SPSS Inn: Crawfordville, FL, USA, 2010; Volume 635, pp. 226–229. [Google Scholar]
- Sudarsono, B.; Tentama, F.; Ghozali, F.A. Employability Analysis of Students in Yogyakarta: Confirmatory Factor Analysis. AL-ISHLAH J. Pendidik. 2022, 14, 1451–1462. [Google Scholar] [CrossRef]
- Hisham, R.; Ng, C.J.; Liew, S.M.; Lai, P.S.M.; Chia, Y.C.; Khoo, E.M.; Hanafi, N.S.; Othman, S.; Lee, P.Y.; Abdullah, K.L.; et al. Development and validation of the Evidence Based Medicine Questionnaire (EBMQ) to assess doctors’ knowledge, practice and barriers regarding the implementation of evidence-based medicine in primary care. BMC Fam. Pract. 2018, 19, 98. [Google Scholar] [CrossRef]
- Ab Hamid, M.R.; Sami, W.; Sidek, M.M. Discriminant validity assessment: Use of Fornell & Larcker criterion versus HTMT criterion. J. Phys. Conf. Ser. 2017, 890, 012163. [Google Scholar]
- Fornell, C.; Larcker, D.F. Structural equation models with unobservable variables and measurement error: Algebra and statistics. J. Mark. Res. 1981, 18, 382–388. [Google Scholar] [CrossRef]
- Hu, L.T.; Bentler, P.M. Cutoff criteria for fit indexes in covariance structure analysis: Conventional criteria versus new alternatives. Struct. Equ. Model. A Multidiscip. J. 1999, 6, 1–55. [Google Scholar] [CrossRef]
- West, S.G.; Taylor, A.B.; Wu, W. Model fit and model selection in structural equation modeling. Handb. Struct. Equ. Model. 2012, 1, 209–231. [Google Scholar]
- Fabrigar, L.R.; MacCallum, R.C.; Wegener, D.T.; Strahan, E.J. Evaluating the use of exploratory factor analysis in psychological research. Psychol. Methods 1999, 4, 272–299. [Google Scholar] [CrossRef]
- Catalini, C.; Gans, J.S. Some simple economics of the blockchain. Commun. ACM 2020, 63, 80–90. [Google Scholar] [CrossRef]
- Bithas, P.S.; Michailidis, E.T.; Nomikos, N.; Vouyioukas, D.; Kanatas, A.G. A survey on machine-learning techniques for UAV-based communications. Sensors 2019, 19, 5170. [Google Scholar] [CrossRef]
- Wang, J.; Liu, Y.; Song, H. Counter-unmanned aircraft system (s) (C-UAS): State of the art, challenges, and future trends. IEEE Aerosp. Electron. Syst. Mag. 2021, 36, 4–29. [Google Scholar] [CrossRef]

| Challenges | Sources |
|---|---|
| Lack of effective planning and management for CSCM concepts | Mangla et al. [42] Verboeket and Krikke [46] |
| Lack of management commitment and approach for CSCM adoption | |
| Lack of implementation of environmental management certifications and systems | |
| Lack of customer awareness of and participation in CSC activities | |
| Inadequacy in the knowledge and awareness of organizational members about CSCM initiatives | |
| Lack of appropriate training and development programs for SC members and HR | |
| Lack of coordination and collaboration among SC members | |
| Transportation and infrastructure | Bressanelli et al. [41] |
| Availability of suitable supply chain partners | |
| Data privacy and security | |
| Coordination and information sharing | |
| Eco-efficiency of technological processes | |
| Lack of vision | Saroha et al. [44] |
| Higher investment cost | |
| Lack of knowledge | |
| Lack of awareness | |
| Lack of information sharing | |
| Technologies made locally available | Pan et al. [45] |
| Measuring environmental impact (certification) | Levering and Vos [43] |
| Cost of developing unmanned vehicle alternatives | |
| Lack of a standard system for performance indicators with regard to measuring supply chains | Govindan and Hasanagic [47] |
| Unclear vision and lack of trust in technology | |
| Lack of transparency | |
| Lack of traceability | |
| Lack of skills by employees in SCM | |
| Cybersecurity and international supply threats | Aggarwal et al. [48] Meissner et al. [49] |
| Security and risk management | |
| Risk of security threats and vulnerabilities | Sahu et al. [50] |
| Frequency | Percentage | Valid Percentage | Cumulative Percentage | ||
|---|---|---|---|---|---|
| Gender | Male | 223 | 46.8 | 46.8 | 46.8 |
| Female | 253 | 53.2 | 53.2 | 100.0 | |
| Total | 476 | 100.0 | 100.0 | ||
| Company nature | IT companies | 248 | 52.1 | 52.1 | 52.1 |
| Security companies | 228 | 47.9 | 47.9 | 100.0 | |
| Total | 476 | 100.0 | 100.0 | ||
| Company age | 1–5 years | 176 | 37.0 | 37.0 | 37.0 |
| 6–10 years | 261 | 54.8 | 54.8 | 91.8 | |
| 11+ years | 39 | 8.2 | 8.2 | 100.0 | |
| Total | 476 | 100.0 | 100.0 | ||
| Working experience | Less than 1 year | 47 | 9.9 | 9.9 | 9.9 |
| 1–3 years | 174 | 36.6 | 36.6 | 46.4 | |
| 4–6 years | 135 | 28.4 | 28.4 | 74.8 | |
| More than 6 years | 120 | 25.2 | 25.2 | 100.0 | |
| Total | 476 | 100.0 | 100.0 | ||
| Number of employees | 10–20 | 58 | 12.2 | 12.2 | 12.2 |
| 21–40 | 115 | 24.2 | 24.2 | 36.3 | |
| 41–60 | 127 | 26.7 | 26.7 | 63.0 | |
| 61+ | 176 | 37.0 | 37.0 | 100.0 | |
| Total | 476 | 100.0 | 100.0 | ||
| Education level | 12 years of education | 6 | 1.3 | 1.3 | 1.3 |
| 14 years of education | 89 | 18.7 | 18.7 | 20.0 | |
| 16 years of education | 318 | 66.8 | 66.8 | 86.8 | |
| 18+ years of education | 63 | 13.2 | 13.2 | 100.0 | |
| Total | 476 | 100.0 | 100.0 | ||
| KMO and Bartlett’s Test | ||
|---|---|---|
| Kaiser–Meyer–Olkin measure of sampling adequacy | 0.860 | |
| Bartlett’s test of sphericity | Approx. chi-square | 4442.060 |
| Df | 190 | |
| Sig. | 0.000 | |
| a. Based on correlations | ||
| Factors | Items | Item Loading | Cronbach’s Alpha | Eigenvalues | Cumulative % |
|---|---|---|---|---|---|
| Traceability | TRAN1 | 0.702 | 0.841 | 32.890 | 32.890 |
| TRAN2 | 0.795 | ||||
| TRAN3 | 0.827 | ||||
| TRAN4 | 0.803 | ||||
| Security and privacy | SAP1 | 0.860 | 0.825 | 11.351 | 44.241 |
| SAP2 | 0.800 | ||||
| SAP3 | 0.802 | ||||
| Trust | TRUST1 | 0.785 | 0.890 | 8.437 | 52.678 |
| TRUST2 | 0.824 | ||||
| TRUST3 | 0.826 | ||||
| TRUST4 | 0.871 | ||||
| Acceptability | ACCEPT1 | 0.704 | 0.753 | 7.935 | 60.613 |
| ACCEPT2 | 0.718 | ||||
| ACCEPT3 | 0.703 | ||||
| ACCEPT4 | 0.732 | ||||
| Preparedness | PREP1 | 0.789 | 0.807 | 7.311 | 67.924 |
| PREP2 | 0.763 | ||||
| PREP3 | 0.822 |
| Factors | Items | Item Loading | Composite Reliability | Average Variance Extracted (AVE) |
|---|---|---|---|---|
| Traceability | TRAN1 | 0.627 | 0.844 | 0.577 |
| TRAN2 | 0.769 | |||
| TRAN3 | 0.819 | |||
| TRAN4 | 0.807 | |||
| Security and privacy | SAP1 | 0.820 | 0.826 | 0.614 |
| SAP2 | 0.737 | |||
| SAP3 | 0.791 | |||
| Trust | TRUST1 | 0.804 | 0.893 | 0.676 |
| TRUST2 | 0.821 | |||
| TRUST3 | 0.802 | |||
| TRUST4 | 0.860 | |||
| Acceptability | ACCEPT1 | 0.717 | 0.756 | 0.538 |
| ACCEPT2 | 0.603 | |||
| ACCEPT3 | 0.625 | |||
| ACCEPT4 | 0.696 | |||
| Preparedness | PREP1 | 0.667 | 0.810 | 0.589 |
| PREP2 | 0.832 | |||
| PREP3 | 0.794 |
| Preparedness | Traceability | Security and Privacy | Trust | Acceptability | |
|---|---|---|---|---|---|
| Preparedness | 0.768 | ||||
| Traceability | 0.404 | 0.759 | |||
| Security and Privacy | 0.403 | 0.389 | 0.783 | ||
| Trust | 0.480 | 0.380 | 0.395 | 0.822 | |
| Acceptability | 0.345 | 0.468 | 0.352 | 0.373 | 0.662 |
| Multi-Dimensionality of the UAV-Based SCM Model | |||||||
|---|---|---|---|---|---|---|---|
| Indicators | CMIN | RFI | NFI | TLI | CFI | RMSEA | p-Value |
| 18 | 2.716 | 0.898 | 0.915 | 0.932 | 0.944 | 0.060 | 0.000 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
AL-Dosari, K.; Deif, A.M.; Kucukvar, M.; Onat, N.; Fetais, N. Security Supply Chain Using UAVs: Validation and Development of a UAV-Based Model for Qatar’s Mega Sporting Events. Drones 2023, 7, 555. https://doi.org/10.3390/drones7090555
AL-Dosari K, Deif AM, Kucukvar M, Onat N, Fetais N. Security Supply Chain Using UAVs: Validation and Development of a UAV-Based Model for Qatar’s Mega Sporting Events. Drones. 2023; 7(9):555. https://doi.org/10.3390/drones7090555
Chicago/Turabian StyleAL-Dosari, Khalifa, Ahmed M. Deif, Murat Kucukvar, Nuri Onat, and Noora Fetais. 2023. "Security Supply Chain Using UAVs: Validation and Development of a UAV-Based Model for Qatar’s Mega Sporting Events" Drones 7, no. 9: 555. https://doi.org/10.3390/drones7090555
APA StyleAL-Dosari, K., Deif, A. M., Kucukvar, M., Onat, N., & Fetais, N. (2023). Security Supply Chain Using UAVs: Validation and Development of a UAV-Based Model for Qatar’s Mega Sporting Events. Drones, 7(9), 555. https://doi.org/10.3390/drones7090555






