Joint Trajectory Planning, Service Function Deploying, and DAG Task Scheduling in UAV-Empowered Edge Computing
Abstract
:1. Introduction
- A 0–1 integer optimization problem is built after establishing the system model for the UAV-empowered edge computing scenario. The completion time of all DAG tasks is minimized with restrictions, such as data dependency among subtasks, and the computational resources available to the UAVs, etc.
- To solve the established NP-hard problem, a genetic-algorithm-based joint deployment and scheduling algorithm, named GA-JoDeS, is put forward. In the GA-JoDeS algorithm, the subtask offloading decision and UAV position are encoded into the chromosome, and the fitness value of an individual is decided by the maximum completion time of all DAG tasks. Through selection, alternating crossover and mutation, the GA-JoDeS algorithm evolves until it finds individuals with the optimal fitness values.
- A series of simulations is conducted to evaluate the effectiveness of the GA-JoDeS algorithm, and three algorithms are chosen as comparison benchmarks. Results show that the GA-JoDeS algorithm can greatly reduce the maximum completion time of DAG tasks.
2. Related Work
3. System Model and Problem Statement
3.1. System Model
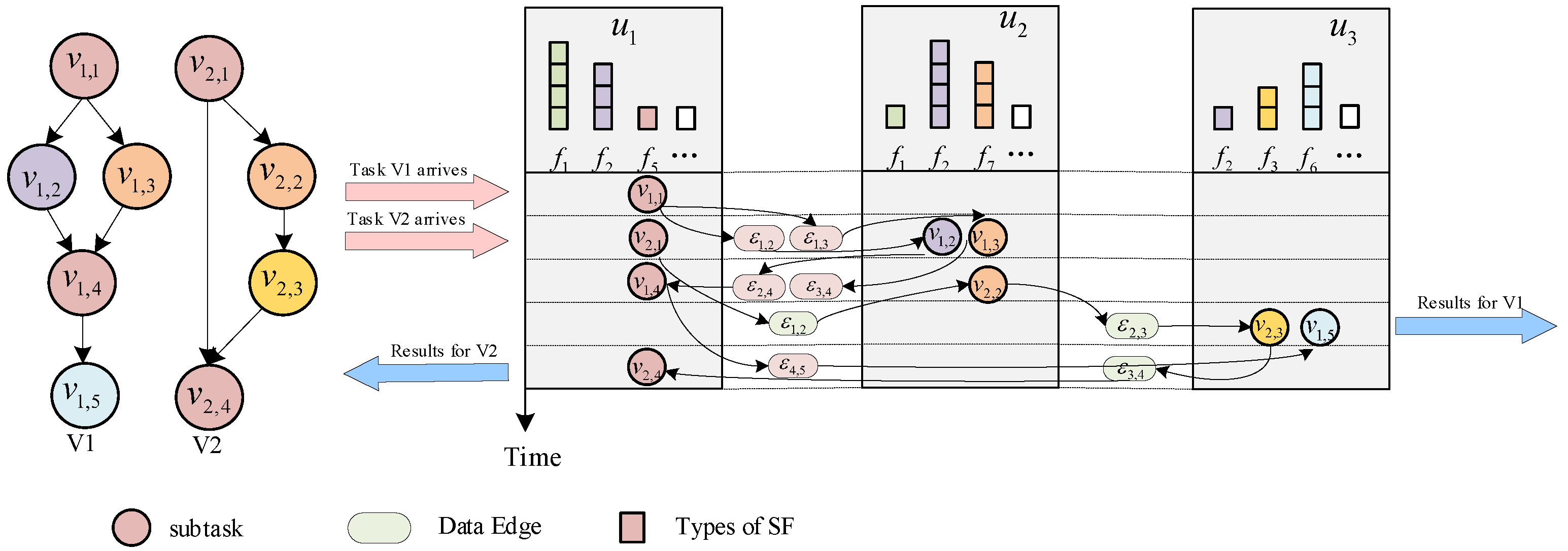
3.1.1. DAG Task Model
3.1.2. UAV Model
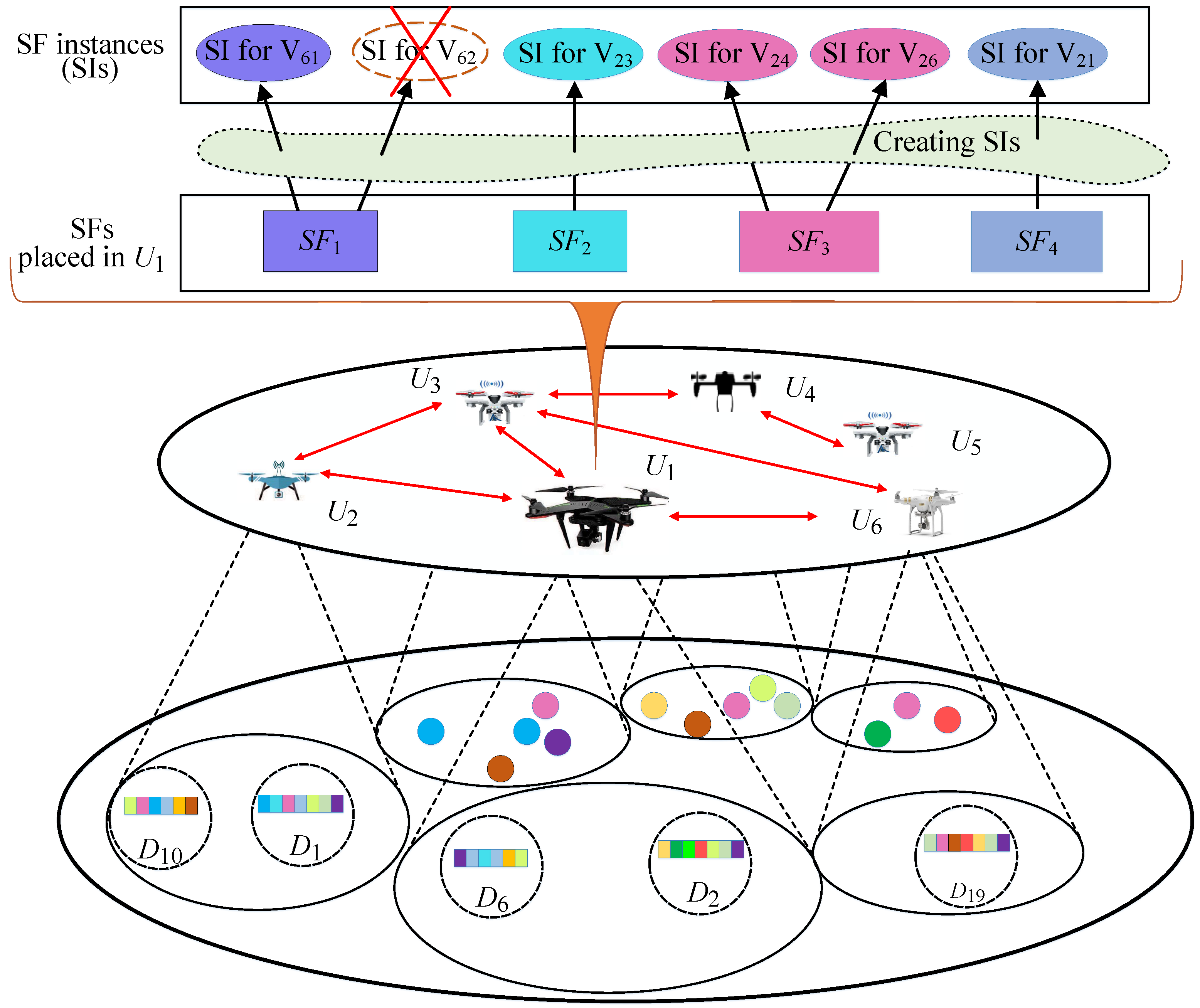
3.1.3. SF Deployment Model
3.2. Task Execution Model
3.2.1. Communications Model
3.2.2. Data Transmission Time
3.2.3. Waiting Time
3.2.4. Task Execution Time
3.3. Problem Statement
4. Algorithm Design
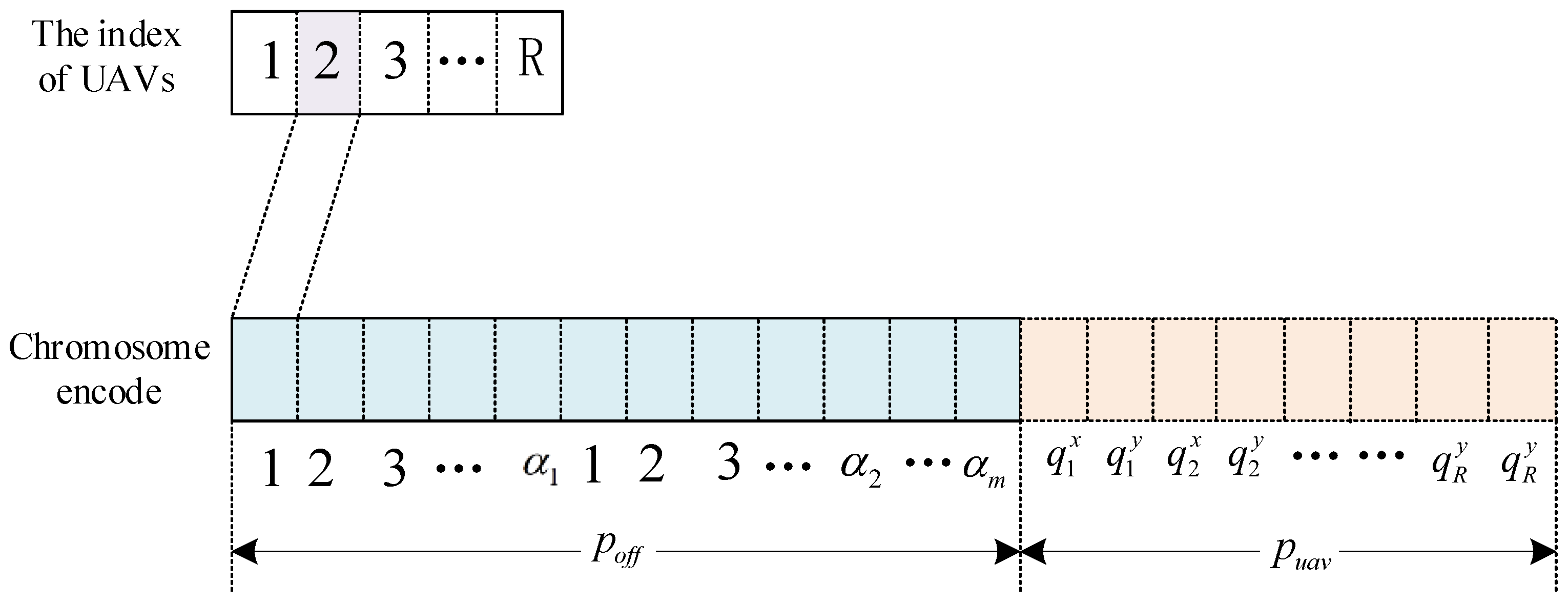
4.1. Chromosome Design
4.2. Algorithm Design
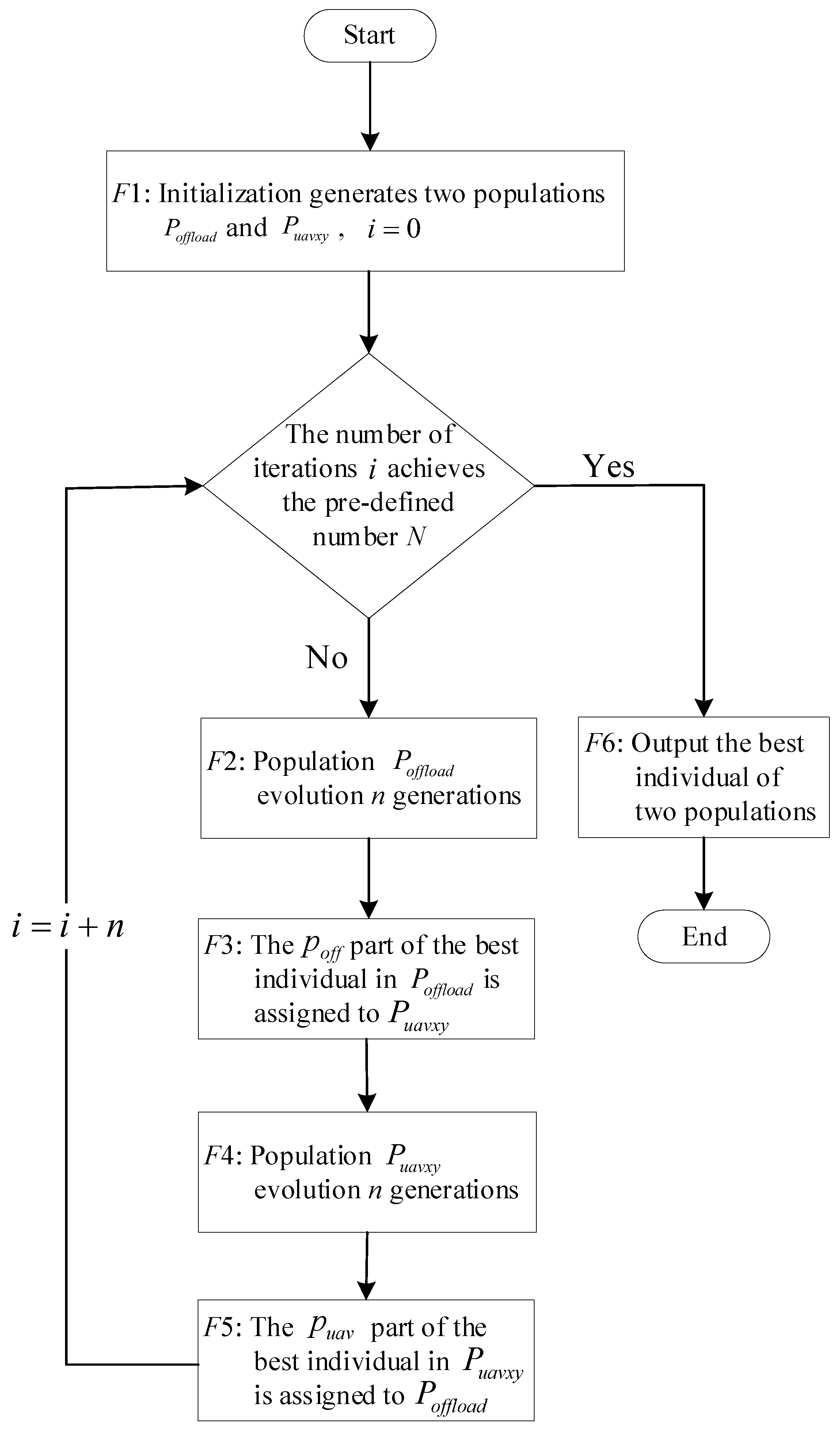
4.2.1. Overall Working Flow
4.2.2. Population Evolve Process
| Algorithm 1 Population evolution in GA-JoDeS algorithm. |
| Input: population P, population size G, crossing probability , mutation probability , evolved generations n |
Output: evolved population .
|
5. Simulation and Results Analysis
5.1. Experimental Setup
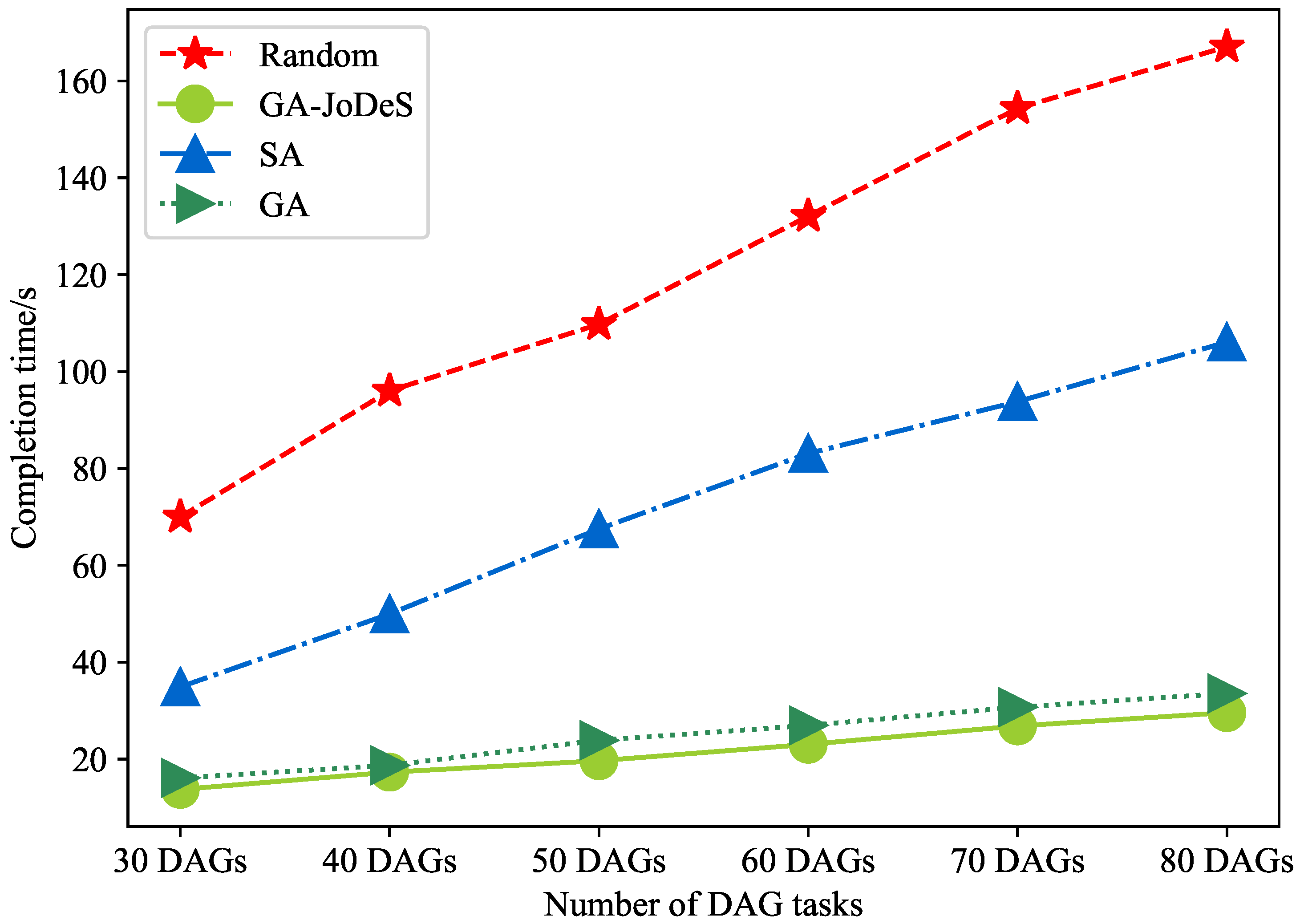
- Random algorithm: The subtasks randomly select UAVs to offload, and the positions of UAVs are also randomly generated within the range.
- Genetic algorithm (GA): The chromosome coding part is the same as the GA-JoDeS. G number of individuals is generated in the population. The opposite of the total task completion time of an individual is set as the fitness value. The roulette wheel algorithm is utilized to select good individuals to form a new population next by single-point crossover and mutation between individuals. N generations are generated to obtain the best individual.
- Simulated annealing (SA) algorithm: First, an initial solution is generated based on the task offloading schedule and the positions of the UAVs; then the maximum completion time of the solution is calculated. Afterwards, the initial temperature, end temperature, and temperature drop factor in the algorithm are determined. The initial solution is randomly changed several times, and the difference between the changed objective function value and the initial value is recorded. The metropolis criterion is utilized to determine whether the change would be accepted. If the new solution is accepted as the current solution, a new temperature is set according to the temperature drop factor. The above steps are repeated until the temperature is lower than the end temperature.
5.2. Results and Analysis
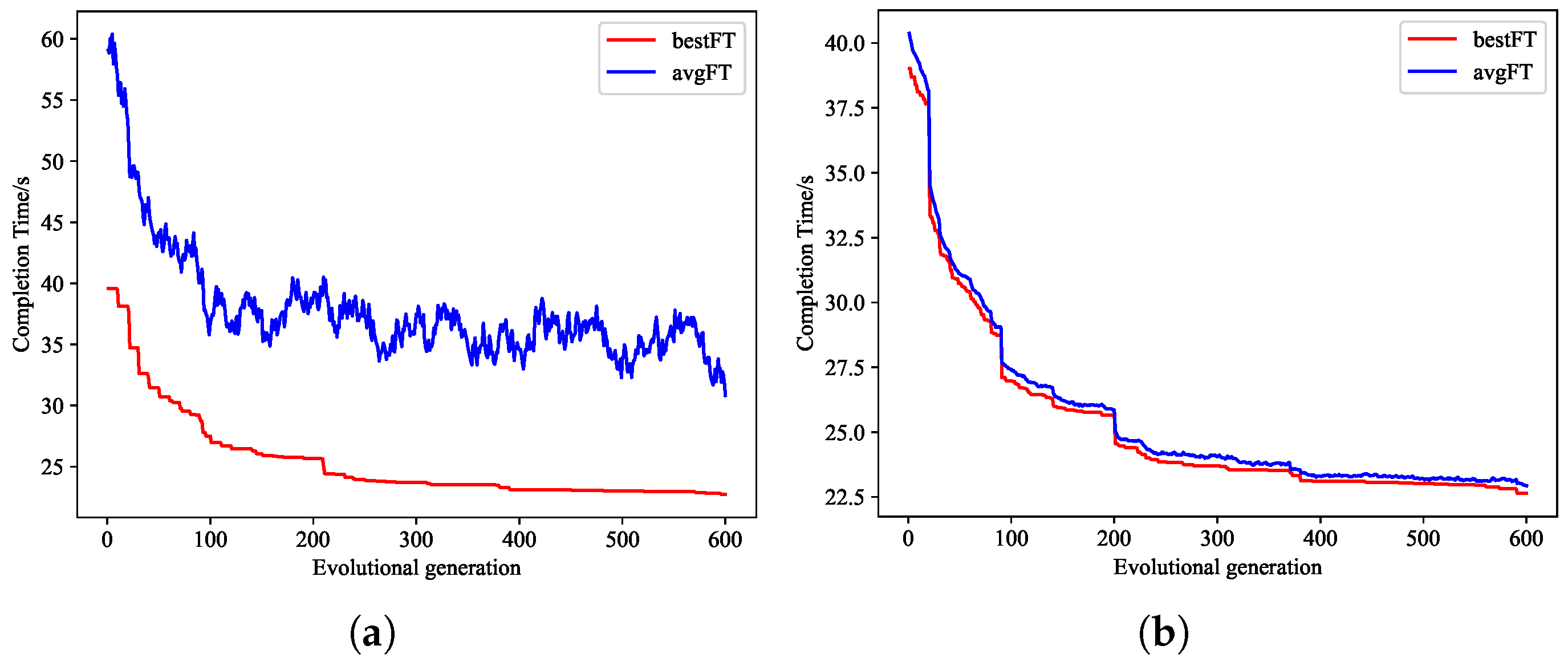
5.2.1. The Convergence of the GA-JoDeS
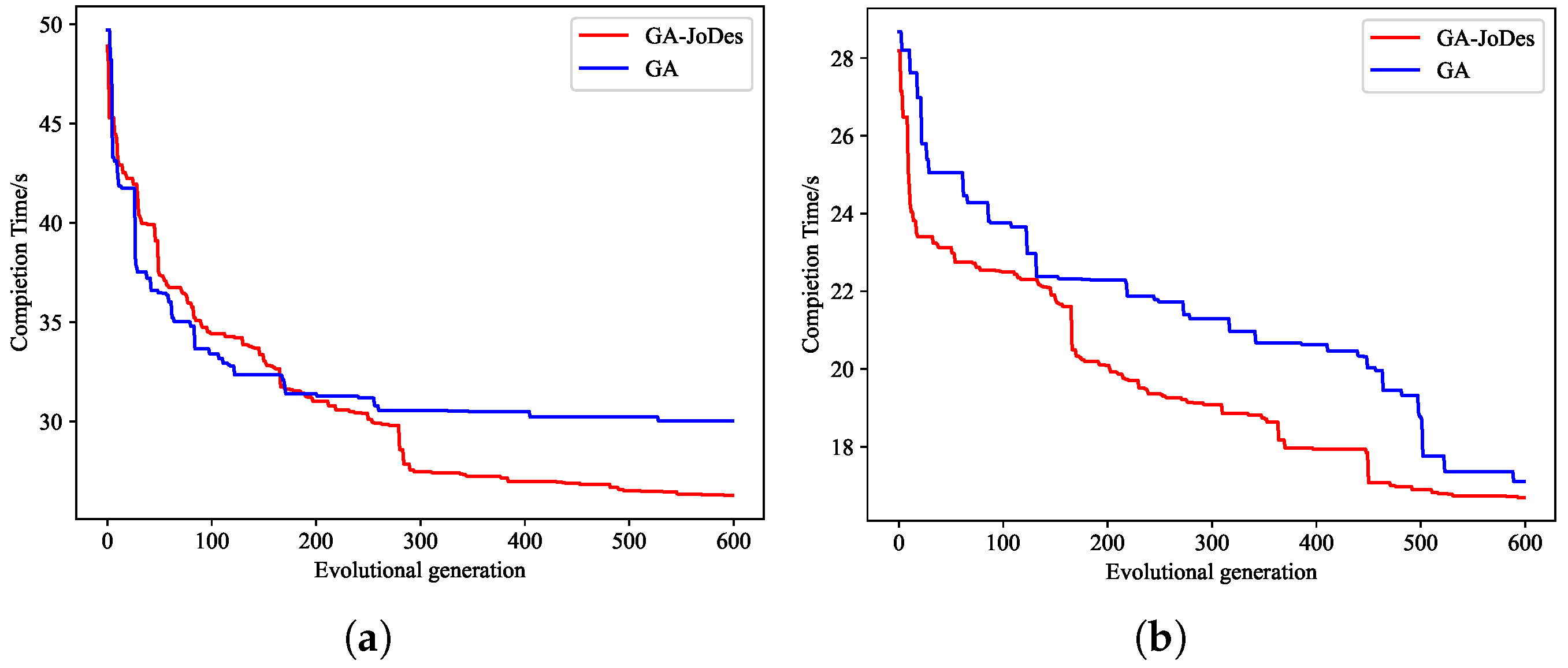
5.2.2. The Comparison of Rate of Convergence of GA-JoDeS and GA
5.2.3. Results Analysis with Different Number of Tasks
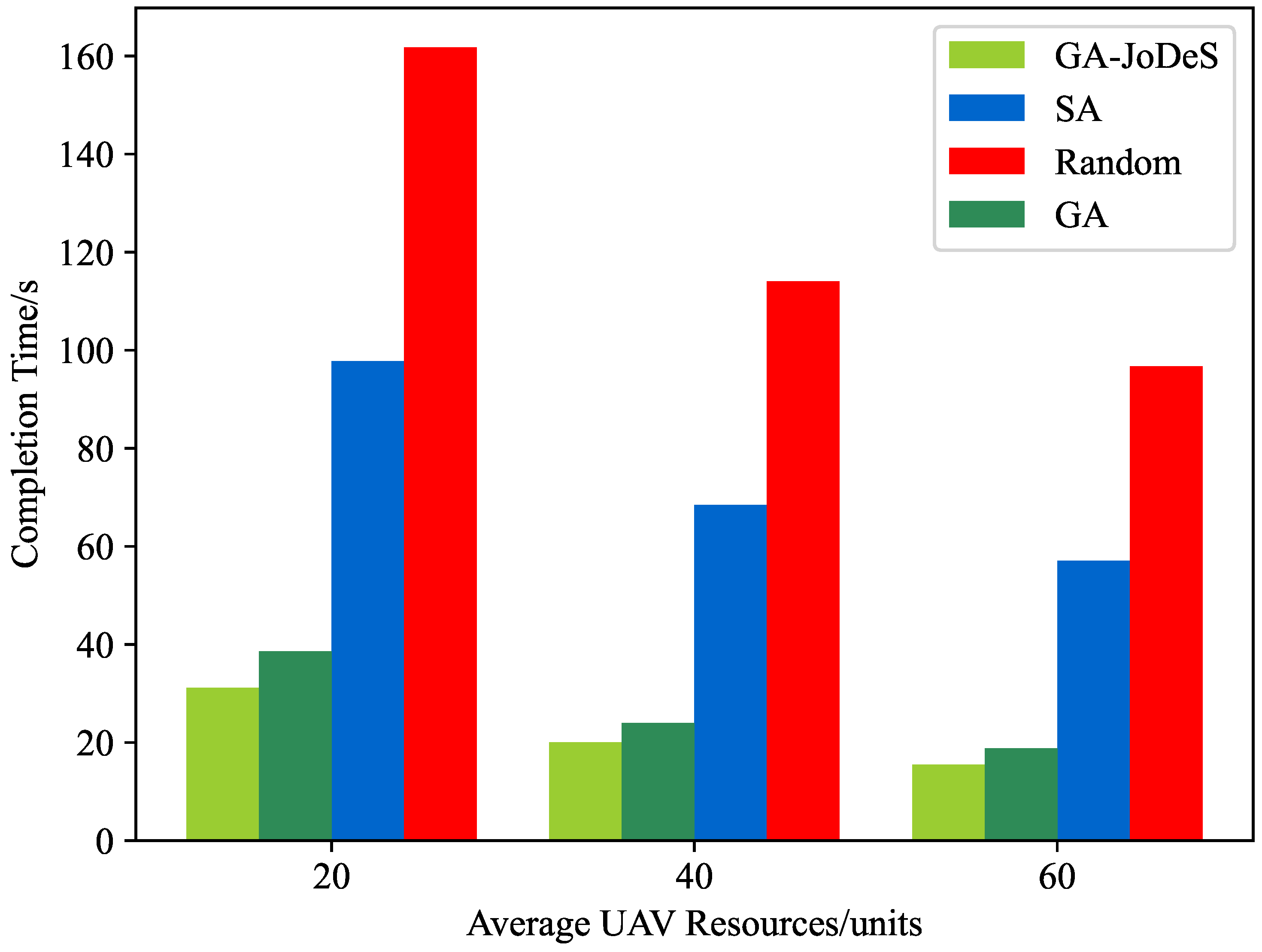
5.2.4. Results Analysis with Different Resources
5.2.5. The Distribution of SFs
5.2.6. The Positions of UAVs
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ra, M.R.; Sheth, A.; Mummert, L.B.; Pillai, P.; Govindan, R. Odessa: Enabling Interactive Perception Applications on Mobile Devices. In Proceedings of the International Conference on Mobile Systems, Washington, DC, USA, 28 June–1 July 2011. [Google Scholar]
- Wei, X.; Liu, J.; Wang, Y.; Tang, C.; Hu, Y. Wireless edge caching based on content similarity in dynamic environments. J. Syst. Archit. 2021, 115, 102000. [Google Scholar] [CrossRef]
- Wei, X.; Tang, C.; Fan, J.; Subramaniam, S. Joint optimization of energy consumption and delay in cloud-to-thing continuum. IEEE Internet Things J. 2019, 6, 2325–2337. [Google Scholar] [CrossRef]
- Hu, Q.; Cai, Y.; Yu, G.; Qin, Z.; Zhao, M.; Li, G.Y. Joint offloading and trajectory design for UAV-enabled mobile edge computing systems. IEEE Internet Things J. 2018, 6, 1879–1892. [Google Scholar] [CrossRef]
- Zhao, N.; Cheng, F.; Yu, F.R.; Tang, J.; Chen, Y.; Gui, G.; Sari, H. Caching UAV assisted secure transmission in hyper-dense networks based on interference alignment. IEEE Trans. Commun. 2018, 66, 2281–2294. [Google Scholar] [CrossRef] [Green Version]
- Yang, Z.; Pan, C.; Wang, K.; Shikh-Bahaei, M. Energy efficient resource allocation in UAV-enabled mobile edge computing networks. IEEE Trans. Wirel. Commun. 2019, 18, 4576–4589. [Google Scholar] [CrossRef]
- Yu, Z.; Gong, Y.; Gong, S.; Guo, Y. Joint task offloading and resource allocation in UAV-enabled mobile edge computing. IEEE Internet Things J. 2020, 7, 3147–3159. [Google Scholar] [CrossRef]
- Ren, Y.; Xie, Z.; Ding, Z.; Sun, X.; Xia, J.; Tian, Y. Computation offloading game in multiple unmanned aerial vehicle-enabled mobile edge computing networks. IET Commun. 2021, 15, 1392–1401. [Google Scholar] [CrossRef]
- Ei, N.N.; Kang, S.W.; Alsenwi, M.; Tun, Y.K.; Hong, C.S. Multi-UAV-assisted MEC system: Joint association and resource management framework. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Republic of Korea, 13–16 January 2021; pp. 213–218. [Google Scholar]
- Mach, P.; Becvar, Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Commun. Surv. Tutorials 2017, 19, 1628–1656. [Google Scholar] [CrossRef] [Green Version]
- Wei, X.; Cai, L.; Wei, N.; Zou, P.; Zhang, J.; Subramaniam, S. Joint UAV Trajectory Planning, DAG Task Scheduling, and Service Function Deployment based on DRL in UAV-empowered Edge Computing. IEEE Internet Things J. 2023, 1–13. [Google Scholar] [CrossRef]
- Li, D.C.; Chen, B.H.; Tseng, C.W.; Chou, L.D. A novel genetic service function deployment management platform for edge computing. Mob. Inf. Syst. 2020, 2020, 1–22. [Google Scholar] [CrossRef]
- Cai, L.; Wei, X.; Xing, C.; Zou, X.; Zhang, G.; Wang, X. Failure-resilient DAG task scheduling in edge computing. Comput. Netw. 2021, 198, 108361. [Google Scholar] [CrossRef]
- Zhan, C.; Hu, H.; Sui, X.; Liu, Z.; Niyato, D. Completion time and energy optimization in the UAV-enabled mobile-edge computing system. IEEE Internet Things J. 2020, 7, 7808–7822. [Google Scholar] [CrossRef]
- Zhang, T.; Xu, Y.; Loo, J.; Yang, D.; Xiao, L. Joint computation and communication design for UAV-assisted mobile edge computing in IoT. IEEE Trans. Ind. Inform. 2019, 16, 5505–5516. [Google Scholar] [CrossRef] [Green Version]
- Xu, Y.; Zhang, T.; Yang, D.; Xiao, L. UAV-assisted relaying and MEC networks: Resource allocation and 3D deployment. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Gao, Y.; Guan, H.; Qi, Z.; Yang, H.; Liang, L. A multi-objective ant colony system algorithm for virtual machine placement in cloud computing. J. Comput. Syst. Sci. 2013, 79, 1230–1242. [Google Scholar] [CrossRef]
- Kao, Y.H.; Krishnamachari, B.; Ra, M.R.; Fan, B. Hermes: Latency optimal task assignment for resource-constrained mobile computing. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Kowloon, Hong Kong, 26 April–1 May 2015. [Google Scholar]
- Zhang, W.; Wen, Y.; Wu, D.O. Collaborative Task Execution in Mobile Cloud Computing Under a Stochastic Wireless Channel. Wirel. Commun. IEEE Trans. 2015, 14, 81–93. [Google Scholar] [CrossRef]
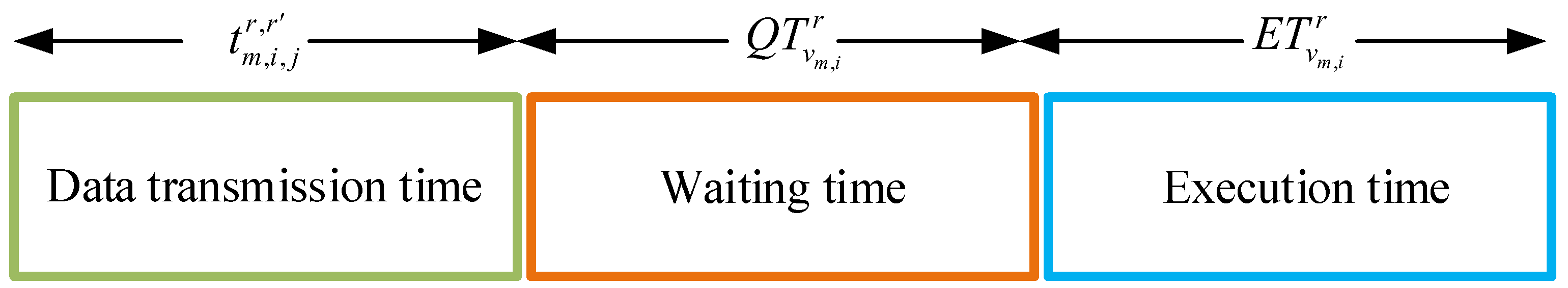


| References | Tasks Types | Optimize Characters | Optimization Objective | |||
|---|---|---|---|---|---|---|
| Single Tasks | DAG Tasks | UAV Position | Service Deployment | Task Scheduling | ||
| [5,6] | ✓ | ✓ | ✓ | Minimization of energy consumption | ||
| [7,8] | ✓ | ✓ | ✓ | Minimization of energy consumption and service latency | ||
| [9] | ✓ | ✓ | ✓ | Minimization of energy consumption | ||
| [11] | ✓ | ✓ | ✓ | Minimization of response time | ||
| [12] | ✓ | ✓ | Minimization of response time | |||
| [13] | ✓ | ✓ | Task completion time | |||
| [14] | ✓ | ✓ | Minimization of energy consumption | |||
| [4] | ✓ | ✓ | ✓ | Minimization of service delay | ||
| [15] | ✓ | ✓ | ✓ | Minimization of energy consumption | ||
| This work | ✓ | ✓ | ✓ | ✓ | Task execution time | |
| Symbol | Meaning |
|---|---|
| M | The total number of tasks in the overall DAG |
| R | The number of UAVs |
| The distance between the r-th UAV and the -th UAV | |
| The transmission rate between the r-th UAV and the -th UAV | |
| The position of the r-th UAV | |
| The position of the m-th DAG | |
| The i-th subtask in the m-th DAG task | |
| The size of the data at the edge of the and | |
| The amount of data being carried of the to | |
| The transmission time of the to | |
| The number of subtasks in the m-th DAG task | |
| The set of all SFs in the system | |
| Q | The total number of SFs |
| The SF corresponding to the | |
| The start time of the executed on the r-th UAV | |
| The completion time of the executed on the r-th UAV | |
| The task scheduling variable | |
| The deployment variable of SFs | |
| The set of predecessor subtasks of | |
| The execution time of the on the r-th UAV | |
| The amount of data to be processed by the | |
| The queuing and waiting time of on the r-th UAV | |
| The queue length | |
| The number of CPU cycles allocated by the r-th UAV to the | |
| The total computing resource of the r-th UAV | |
| f | The carrier frequency |
| The path loss exponent | |
| c | Speed of light |
| Signal-to-interference-and-noise ratio | |
| Transmission rate between the UAV and the ground task | |
| The transmission rate between the subtasks | |
| Response time of the m-th DAG task | |
| The elevation angle between ground equipment and UAV | |
| The average UAVs resource |
| Simulation Parameters | Value |
|---|---|
| 20 | |
| R | 10 |
| [1, 500] m | |
| [1, 500] m | |
| H | 100 m |
| 11.95 | |
| 0.14 | |
| 2 | |
| 3 | |
| 10 | |
| f | 2 GHz |
| 200 MHz | |
| w | |
| w | 2 MHz |
| 0.8 | |
| 0.2 | |
| [2, 8] | |
| N | 600 |
| Average Resource of a UAV | 20 | 40 |
|---|---|---|
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| SFs deployed on | ||
| The maximum task completion time | 63.27 s | 18.77 s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jia, R.; Zhao, K.; Wei, X.; Zhang, G.; Wang, Y.; Tu, G. Joint Trajectory Planning, Service Function Deploying, and DAG Task Scheduling in UAV-Empowered Edge Computing. Drones 2023, 7, 443. https://doi.org/10.3390/drones7070443
Jia R, Zhao K, Wei X, Zhang G, Wang Y, Tu G. Joint Trajectory Planning, Service Function Deploying, and DAG Task Scheduling in UAV-Empowered Edge Computing. Drones. 2023; 7(7):443. https://doi.org/10.3390/drones7070443
Chicago/Turabian StyleJia, Runa, Kuang Zhao, Xianglin Wei, Guoliang Zhang, Yangang Wang, and Gangyi Tu. 2023. "Joint Trajectory Planning, Service Function Deploying, and DAG Task Scheduling in UAV-Empowered Edge Computing" Drones 7, no. 7: 443. https://doi.org/10.3390/drones7070443
APA StyleJia, R., Zhao, K., Wei, X., Zhang, G., Wang, Y., & Tu, G. (2023). Joint Trajectory Planning, Service Function Deploying, and DAG Task Scheduling in UAV-Empowered Edge Computing. Drones, 7(7), 443. https://doi.org/10.3390/drones7070443






