Optimizing Performance in Federated Person Re-Identification through Benchmark Evaluation for Blockchain-Integrated Smart UAV Delivery Systems
Abstract
:1. Introduction
- We propose a performance optimization approach for federated person re-identification in blockchain-enabled edge-based smart UAV delivery systems, utilizing a decentralized FL mechanism to address data privacy concerns. Furthermore, we conduct experiments to evaluate the effectiveness of our proposed approach, focusing on energy efficiency, confirmation time, and throughput, while also discussing the impact of the incentive mechanism and analyzing the solution’s resiliency under various security attacks.
- We introduce the FRC Consensus protocol, which enhances blockchain scalability to support the growing demands of smart UAV delivery systems. Furthermore, our comprehensive study provides valuable insights into the challenges and potential solutions associated with data privacy and security in smart UAV delivery systems, paving the way for future research and development in this rapidly growing field.
2. Related Work
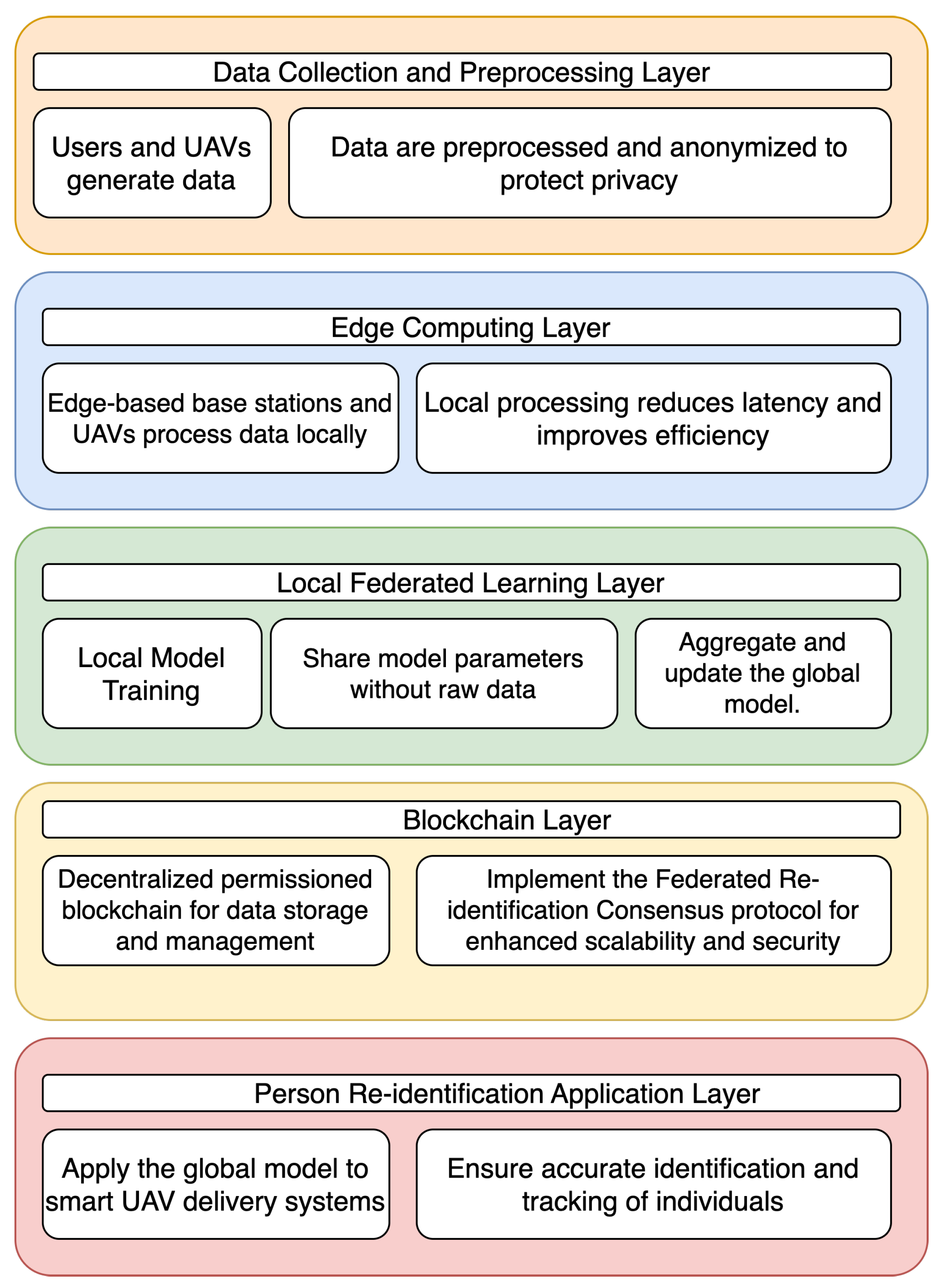
3. System Design
3.1. System Layers
- Data Collection and Preprocessing Layer: During the normal operation of the smart UAV delivery system, users and UAVs generate data primarily in the form of images or videos captured by the onboard cameras on the UAVs. These images or videos contain visual information about users, which is essential for the person’s ReID task. To protect user privacy, it is crucial to preprocess these data by removing personally identifiable information and anonymizing the data. Anonymization techniques may include data normalization, noise addition, or data transformation. These preprocessing steps ensure that sensitive information is not leaked or misused, while still allowing the system to perform accurate person re-identification tasks based on the anonymized data.
- Edge Computing Layer: Edge devices, such as UAVs and base stations, process the preprocessed data locally, rather than sending it to a central server. This reduces latency and improves overall system efficiency. Local processing may involve tasks such as feature extraction, data compression, or other analytics to prepare data for the federated learning process.
- Local Federated Learning Layer: Each edge device trains a federated learning model using its locally processed data. This ensures that the raw data remain on the device, preserving privacy. After local training, edge devices share their model parameters (e.g., weights, gradients) with the decentralized FL mechanism, instead of sharing raw data. The shared parameters are used to aggregate and update the global model, which is then distributed back to the edge devices for further training and refinement.
- Blockchain Layer: A decentralized permissioned Ethereum blockchain is integrated into the system for secure data storage and management. The Federated Re-identification Consensus protocol is implemented within the blockchain network, addressing scalability issues and ensuring enhanced security during the FL process.
- Person Re-identification Application Layer: The global model obtained from the federated learning process is applied to the smart UAV delivery system to perform person re-identification tasks. This enables the system to accurately identify and track individuals, improving the overall efficiency and effectiveness of the delivery process.
3.2. Blockchain-Enabled System Design
| Algorithm 1: Fed-UAV with Cosine Distance Weight |
|
3.3. FRC Consensus
- Energy efficiency: Unlike traditional consensus protocols such as Proof of Work (PoW), FRC does not require solving complex cryptographic puzzles, which can consume a significant amount of computational power and energy. By allocating weights based on the contributions to the federated learning process, FRC promotes a more energy-efficient consensus mechanism.
- Scalability: By considering the quality factors of nodes, including computational capacity, connectivity bandwidth, and reliability, FRC effectively distributes the verification workload among participating nodes, leading to improved scalability compared to traditional consensus mechanisms that may rely on a few powerful nodes.
- Incentivizes cooperation: Nodes are incentivized to actively participate in the federated learning process and maintain high-quality contributions, as their verification weights depend on their contributions. This encourages more nodes to join the network, increasing the overall performance and security of the system.
- Enhanced security: FRC improves the security of the network by considering node reliability in the weight calculation. This reduces the likelihood of a malicious node gaining control over the consensus process.
- Privacy-preserving: As FRC is designed for federated learning, it inherently preserves data privacy by sharing only model parameters and not the raw data. This is particularly important in the context of person re-identification, where sensitive personal information is involved.
4. Evaluation
4.1. Experimental Setup
4.2. Performance Evaluation
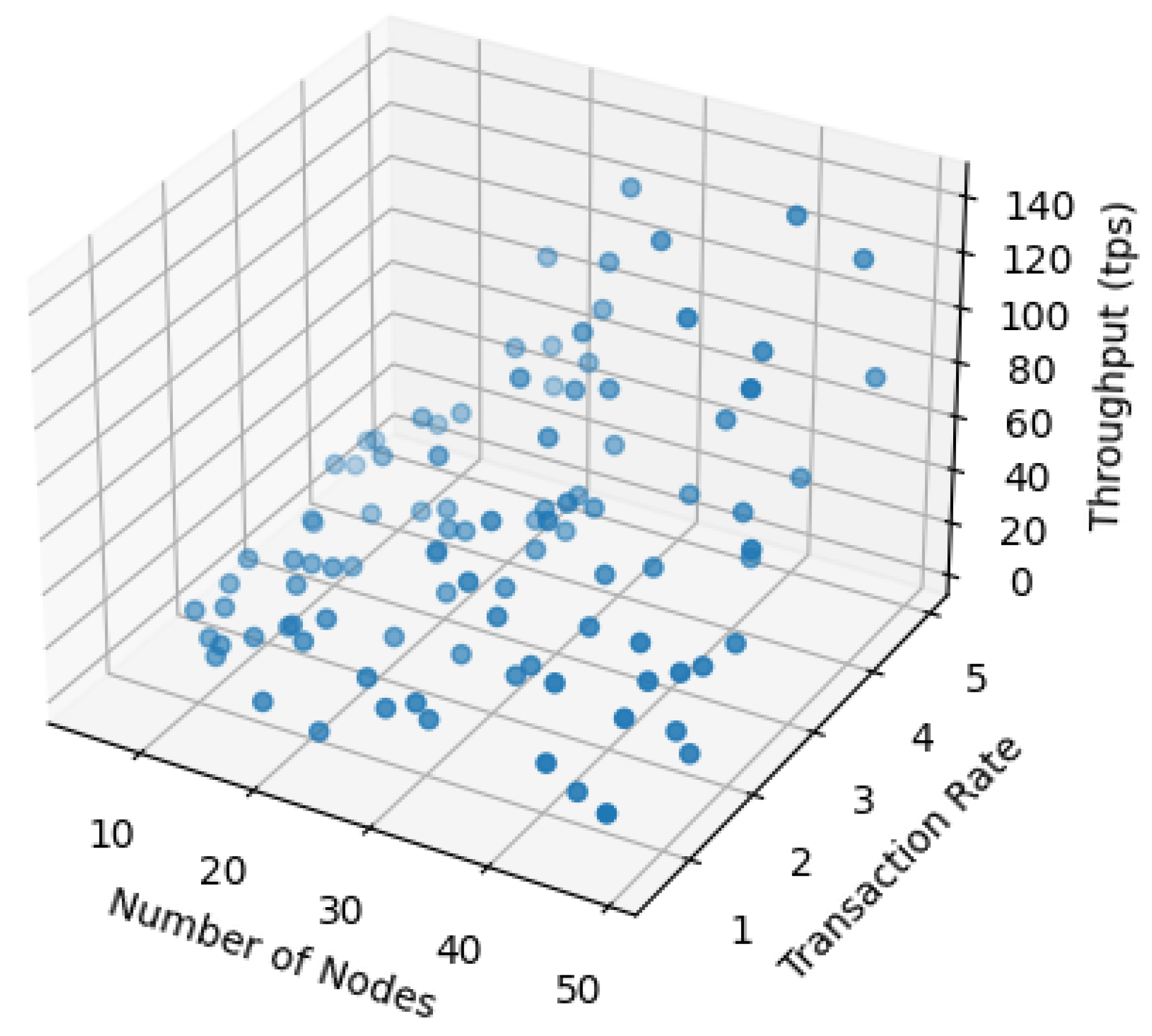
4.3. Permissioned Chain throughput Evaluation
| Algorithm 2: Blockchain Throughput |
|
5. Conclusions and Future Work
- Exploring and integrating advanced security mechanisms, such as zero-knowledge proofs or secure multi-party computation, can further enhance the privacy and security of the federated learning process.
- Researching methods to enable interoperability between different blockchain platforms and federated learning systems can promote collaboration and expand the range of applications in various industries.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Feng, C.; Liu, B.; Yu, K.; Goudos, S.K.; Wan, S. Blockchain-empowered decentralized horizontal federated learning for 5G-enabled UAVs. IEEE Trans. Ind. Inform. 2021, 18, 3582–3592. [Google Scholar] [CrossRef]
- Beer, K.; Bondarenko, D.; Farrelly, T.; Osborne, T.J.; Salzmann, R.; Scheiermann, D.; Wolf, R. Training deep quantum neural networks. Nat. Commun. 2020, 11, 808. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yan, K.; Liu, L.; Xiang, Y.; Jin, Q. Guest editorial: AI and machine learning solution cyber intelligence technologies: New methodologies and applications. IEEE Trans. Ind. Inform. 2020, 16, 6626–6631. [Google Scholar] [CrossRef]
- Zhou, M.G.; Cao, X.Y.; Lu, Y.S.; Wang, Y.; Bao, Y.; Jia, Z.Y.; Fu, Y.; Yin, H.L.; Chen, Z.B. Experimental quantum advantage with quantum coupon collector. Research 2022, 2022, 9798679. [Google Scholar] [CrossRef] [PubMed]
- Sharma, K.; Cerezo, M.; Cincio, L.; Coles, P.J. Trainability of dissipative perceptron-based quantum neural networks. Phys. Rev. Lett. 2022, 128, 180505. [Google Scholar] [CrossRef] [PubMed]
- Zhou, M.G.; Liu, Z.P.; Yin, H.L.; Li, C.L.; Xu, T.K.; Chen, Z.B. Quantum Neural Network for Quantum Neural Computing. Research 2023, 6, 134. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J. Federated Learning With Blockchain for Autonomous Vehicles: Analysis and Design Challenges. IEEE Trans. Commun. 2020, 68, 4734–4746. [Google Scholar] [CrossRef]
- Zhang, C.; Liu, X.; Xu, J.; Chen, T.; Li, G.; Jiang, F.; Li, X. An Edge Based Federated Learning Framework for Person Re-Identification in UAV Delivery Service. In Proceedings of the 2021 IEEE International Conference on Web Services (ICWS), Chicago, IL, USA, 5–10 September 2021; pp. 500–505. [Google Scholar]
- Khan, M.A.; Ullah, I.; Alkhalifah, A.; Rehman, S.U.; Shah, J.A.; Uddin, M.I.; Alsharif, M.H.; Algarni, F. A provable and privacy-preserving authentication scheme for UAV-enabled intelligent transportation systems. IEEE Trans. Ind. Inform. 2021, 18, 3416–3425. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pham, Q.V.; Pathirana, P.N.; Ding, M.; Seneviratne, A.; Lin, Z.; Dobre, O.; Hwang, W.J. Federated learning for smart healthcare: A survey. ACM Comput. Surv. 2022, 55, 1–37. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Karimipour, H. Federated learning for drone authentication. Hoc Netw. 2021, 120, 102574. [Google Scholar] [CrossRef]
- Pokhrel, S.R. Blockchain brings trust to collaborative drones and leo satellites: An intelligent decentralized learning in the space. IEEE Sensors J. 2021, 21, 25331–25339. [Google Scholar] [CrossRef]
- Pokhrel, S.R. Federated Learning Meets Blockchain at 6G Edge: A Drone-Assisted Networking for Disaster Response. In Proceedings of the 2nd ACM MobiCom Workshop on Drone Assisted Wireless Communications for 5G and Beyond, New York, NY, USA, 25–25 September 2020; pp. 49–54. [Google Scholar]
- Ch, R.; Srivastava, G.; Gadekallu, T.R.; Maddikunta, P.K.R.; Bhattacharya, S. Security and privacy of UAV data using blockchain technology. J. Inf. Secur. Appl. 2020, 55, 102670. [Google Scholar] [CrossRef]
- Khan, A.A.; Khan, M.M.; Khan, K.M.; Arshad, J.; Ahmad, F. A blockchain-based decentralized machine learning framework for collaborative intrusion detection within UAVs. Comput. Netw. 2021, 196, 108217. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Kumar, A.; Franklin, A.A.; Jolfaei, A. Blockchain and Deep Learning Empowered Secure Data Sharing Framework for Softwarized Uavs. In Proceedings of the 2022 IEEE International Conference on Communications Workshops (ICC Workshops), Seoul, Republic of Korea, 16–20 May 2022; pp. 770–775. [Google Scholar]
- Liu, B.; Yu, K.; Feng, C.; Choo, K.K.R. Cross-Domain Authentication for 5G-Enabled UAVs: A Blockchain Approach. In Proceedings of the 4th ACM MobiCom Workshop on Drone Assisted Wireless Communications for 5G and Beyond, Online, 29–29 October 2021; pp. 25–30. [Google Scholar]
- Gupta, R.; Nair, A.; Tanwar, S.; Kumar, N. Blockchain-assisted secure UAV communication in 6G environment: Architecture, opportunities, and challenges. IET Commun. 2021, 15, 1352–1367. [Google Scholar] [CrossRef]
- Silva, S.H.; Rad, P.; Beebe, N.; Choo, K.K.R.; Umapathy, M. Cooperative unmanned aerial vehicles with privacy preserving deep vision for real-time object identification and tracking. J. Parallel Distrib. Comput. 2019, 131, 147–160. [Google Scholar] [CrossRef]
- Grigorev, A.; Liu, S.; Tian, Z.; Xiong, J.; Rho, S.; Feng, J. Delving deeper in drone-based person re-id by employing deep decision forest and attributes fusion. ACM Trans. Multimed. Comput. Commun. Appl. 2020, 16, 1–15. [Google Scholar] [CrossRef]
- Nguyen, T.; Katila, R.; Gia, T.N. A Novel Internet-of-Drones and Blockchain-Based System Architecture for Search and Rescue. In Proceedings of the 2021 IEEE 18th International Conference on Mobile Ad Hoc and Smart Systems (MASS), Denver, CO, USA, 4–7 October 2021; pp. 278–288. [Google Scholar]
- Jensen, I.J.; Selvaraj, D.F.; Ranganathan, P. Blockchain Technology for Networked Swarms of Unmanned Aerial Vehicles (UAVs). In Proceedings of the 2019 IEEE 20th International Symposium on A World of Wireless, Mobile and Multimedia Networks, Washington, DC, USA, 10–12 June 2019; pp. 1–7. [Google Scholar]
- Xu, X.; Zhao, H.; Yao, H.; Wang, S. A blockchain-enabled energy-efficient data collection system for UAV-assisted IoT. IEEE Internet Things J. 2020, 8, 2431–2443. [Google Scholar] [CrossRef]
- Psaras, Y.; Dias, D. The Interplanetary File System and the Filecoin Network. In Proceedings of the 2020 50th Annual IEEE-IFIP International Conference on Dependable Systems and Networks-Supplemental Volume (DSN-S), Valencia, Spain, 29 June–2 July 2020; p. 80. [Google Scholar]
- Fang, C.; Guo, Y.; Ma, J.; Xie, H.; Wang, Y. A privacy-preserving and verifiable federated learning method based on blockchain. Comput. Commun. 2022, 186, 1–11. [Google Scholar] [CrossRef]
- Zhuang, W.; Gan, X.; Wen, Y.; Zhang, S. Easyfl: A low-code federated learning platform for dummies. IEEE Internet Things J. 2022, 9, 13740–13754. [Google Scholar] [CrossRef]
- Ahmed, K.; Li, T.; Ton, T.; Guo, Q.; Chang, K.W.; Kordjamshidi, P.; Srikumar, V.; Van den Broeck, G.; Singh, S. PYLON: A PyTorch Framework for Learning with Constraints. In Proceedings of the NeurIPS 2021 Competitions and Demonstrations Track, Online, 6–14 December 2022; pp. 319–324. [Google Scholar]
- Monroe, M.E.; Tolić, N.; Jaitly, N.; Shaw, J.L.; Adkins, J.N.; Smith, R.D. VIPER: An advanced software package to support high-throughput LC-MS peptide identification. Bioinformatics 2007, 23, 2021–2023. [Google Scholar] [CrossRef] [Green Version]
- Wu, S.; Chen, Y.C.; Li, X.; Wu, A.C.; You, J.J.; Zheng, W.S. An Enhanced Deep Feature Representation for Person Re-Identification. In Proceedings of the 2016 IEEE Winter Conference on Applications of Computer Vision (WACV), Lake Placid, NY, USA, 7–10 March 2016; pp. 1–8. [Google Scholar]
- Baltieri, D.; Vezzani, R.; Cucchiara, R. 3dpes: 3d People Dataset for Surveillance and Forensics. In Proceedings of the 2011 Joint ACM Workshop on Human Gesture and Behavior Understanding, Scottsdale, AZ, USA, 28 November–1 December 2011; pp. 59–64. [Google Scholar]
- Zhou, R.; Chang, X.; Shi, L.; Shen, Y.D.; Yang, Y.; Nie, F. Person Reidentification via Multi-Feature Fusion with Adaptive Graph Learning. IEEE Trans. Neural Netw. Learn. Syst. 2019, 31, 1592–1601. [Google Scholar] [CrossRef] [PubMed]
- Zhuang, W.; Wen, Y.; Zhang, X.; Gan, X.; Yin, D.; Zhou, D.; Zhang, S.; Yi, S. Performance Optimization of Federated Person Re-Identification via Benchmark Analysis. In Proceedings of the 28th ACM International Conference on Multimedia, Seattle, WA, USA, 12–16 October 2020; pp. 955–963. [Google Scholar]





| Methodology | Reference | Year | Privacy Preservation |
|---|---|---|---|
| Fed-UAV | [8] | 2021 | × |
| Yazdinejad’s model | [11] | 2021 | √ |
| Pokhrel’s framework | [12] | 2021 | √ |
| Pokhrel’s approach | [13] | 2020 | √ |
| Rupa’s system | [14] | 2020 | √ |
| Khan’s framework | [15] | 2021 | × |
| Kumar’s framework | [16] | 2022 | √ |
| Liu’s solution | [17] | 2021 | × |
| Gupta’s solution | [18] | 2021 | × |
| Silva’s solution | [19] | 2019 | × |
| Grogorev’s solution | [20] | 2020 | × |
| Nguyen’s architecture | [21] | 2021 | × |
| Jensen’s system | [22] | 2019 | √ |
| Xu’s framework | [23] | 2020 | × |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dong, C.; Zhou, J.; An, Q.; Jiang, F.; Chen, S.; Pan, L.; Liu, X. Optimizing Performance in Federated Person Re-Identification through Benchmark Evaluation for Blockchain-Integrated Smart UAV Delivery Systems. Drones 2023, 7, 413. https://doi.org/10.3390/drones7070413
Dong C, Zhou J, An Q, Jiang F, Chen S, Pan L, Liu X. Optimizing Performance in Federated Person Re-Identification through Benchmark Evaluation for Blockchain-Integrated Smart UAV Delivery Systems. Drones. 2023; 7(7):413. https://doi.org/10.3390/drones7070413
Chicago/Turabian StyleDong, Chengzu, Jingwen Zhou, Qi An, Frank Jiang, Shiping Chen, Lei Pan, and Xiao Liu. 2023. "Optimizing Performance in Federated Person Re-Identification through Benchmark Evaluation for Blockchain-Integrated Smart UAV Delivery Systems" Drones 7, no. 7: 413. https://doi.org/10.3390/drones7070413
APA StyleDong, C., Zhou, J., An, Q., Jiang, F., Chen, S., Pan, L., & Liu, X. (2023). Optimizing Performance in Federated Person Re-Identification through Benchmark Evaluation for Blockchain-Integrated Smart UAV Delivery Systems. Drones, 7(7), 413. https://doi.org/10.3390/drones7070413






