Abstract
Privacy preservation of image data has been a top priority for many applications. The rapid growth of technology has increased the possibility of creating fake images using social media as a platform. However, many people, including researchers, rely on image data for various purposes. In rural areas, lane images have a high level of importance, as this data can be used for analyzing various lane conditions. However, this data is also being forged. To overcome this and to improve the privacy of lane image data, a real-time solution is proposed in this work. The proposed methodology assumes lane images as input, which are further classified as fake or bona fide images with the help of Error Level Analysis (ELA) and artificial neural network (ANN) algorithms. The U-Net model ensures lane detection for bona fide lane images, which helps in the easy identification of lanes in rural areas. The final images obtained are secured by using the proxy re-encryption technique which uses RSA and ECC algorithms. This helps in ensuring the privacy of lane images. The cipher images are maintained using fog computing and processed with integrity. The proposed methodology is necessary for protecting genuine satellite lane images in rural areas, which are further used by forecasters, and researchers for making interpretations and predictions on data.
1. Introduction
The number of active Internet users across the world is 4.66 billion, which constitutes 59.57 percent of the world’s population. Many images and videos are being produced on social media of which nearly 50 percent are not authentic. Lots of images and videos are being tampered with for financial and other gains [1,2,3]. Anyone can make extremely believable fake images utilizing software tools that are readily available online [4]. Satellite lane images are also being tampered with, which causes a lot of trouble for researchers and scientists to use them in their predictions. Hence, there is a need for classifying and preserving the satellite lane images for utilizing them in further predictions.
There are various models such as Random Forest, VGG-19, and robust hashing for the classification of lane images as fake or authentic. Moreover, there are models such as YOLO, which is an autoencoder for lane image detection. However, these models are not efficient when compared with the proposed solution. The accuracy is also low and the training time required for the above models is high. To overcome the hurdles discussed above, a real-time solution is proposed. The proposed methodology makes use of the ANN algorithm for the classification of an image as fake or genuine. An ANN algorithm allows backpropagation, which helps in increasing the accuracy. The U-Net algorithm is used in the detection of lane images. The proxy re-encryption (PRE) technique is used in the encryption process for enhancing security [5].
1.1. Problem Statement and Motivation
There are some machine learning algorithms involved in the classification and detection of satellite images such as Random Forest, Naïve Bayes, RCNN, and Support Vector Machine (SVM). However, these achieved less accuracy and are also computationally very expensive. Machine learning algorithms involving convolutional neural networks (CNN), artificial neural networks (ANN), and U-Net, which are used in the proposed methodology, can achieve better accuracy when compared with the above algorithms [6]. Security plays a vital role in daily life. Heavy-weight encryption algorithms such as AES-112 and RSA-118 require high computational memory when compared with lightweight encryption algorithms such as RC4, RC6, ECC, etc. [7,8]. Ensuring the non-sharing of secret keys in the encryption process is a preliminary task which strengthens the encryption algorithm. The main motivation of PRE techniques is to prevent the sharing of secret keys and it can be defined through the following equation:
is the public key of user A, with which encryption is performed at one end. depicts the proxy re-encryption technique which decrypts the cipher data and re-encrypts the original message with the help of user B’s public key. is the secret key of user B, with which decryption is performed at the other end.
1.2. Research Contributions in the Proposed Work
- Provided an overview of the security mechanisms and challenges faced in securing satellite lane images.
- Performed a literature survey on various security mechanisms such as proxy re-encryption techniques for securing the data.
- Reviewing the state-of-the-art, we have identified that proxy re-encryption has not been implemented practically, which points out the novelty in our paper.
- Identified that the proxy re-encryption technique has better performance and can survive various security threats.
- Researched many classification algorithms and compared those classification algorithms with the proposed classification algorithm (ANN).
- Various models, and security mechanisms are analyzed and the key features of the proposed methodology are compared against them.
1.3. Outline of the Paper
2. Related Works
Ahmed Elmogy et al. developed a cipher for text messages [9]. In the proposed methodology, the encryption of the characters is linked with the previous characters, enhancing security. The encryption can be performed on letters, numbers and symbols based on their ASCII codes. The encryption formula is stated as follows:
where is the cipher value and , are the ASCII codes for the corresponding characters. A disadvantage is that the encryption can be performed only on the character data and it does not apply to image data and the architecture is also complex. The main contribution of the author is to propose an encryption scheme with less computation and processing power, which made us to perform a survey in this area.
Ahmad et al. proposed a multi-chaos computationally efficient encryption for digital images [10]. In the proposed solution, the original image is converted using lifting wavelet transform (LWT) and the quarter part of the image that is transformed in the previous step is encrypted using lightweight Chebyshev and intertwining maps. In this model, the LWT and SHA-512 algorithms are used to generate a hash value. Encryption standards are increased to an extent with the help of this algorithm and it also achieves integrity which became a motivation for the survey process. The process is complicated as the key size is larger and contains a greater number of computations. The contour mapping of nuclear radiation is simulated in this work [11,12] as part of two scenarios for nuclear radiation detection using numerous UAVs. There are several limitations in the current methodologies. The dataset utilized is minimal as it cannot deal with huge amounts of data. The extracted features are not accurate as well when compared with the characteristics of human visual attention. The methodology consumes a large amount of processing power.
Joslin et al. [13] came up with a methodology to detect the fake images that are created using GANs. The analysis and attribution of fake images in the proposed model are performed by considering two datasets of real images and four GAN models that were trained. The methodology first takes a known GAN model and performs fast Fourier Transform on the images in the network. The main achievement of this work is to utilize GAN for the creation of tampered images which aid in the selection of datasets. The model does not work for the detection of fake images that are created using other modification techniques.
The main idea of the proposed model in [14] is to provide the navigation in automatic vehicles. Gaussian filter layers are used for the removal of noise from the given input aerial images. The model used five layers of CNN. The five layers are ReLu, pooling, fully connected, convolution and loss layers. The proposed approach fails for blurred images and it can accept only coloured images. The efficiency of the model is majorly affected by lights, barriers and reflections of lights. Liu et al. proposed a solution for lane detection with shadow interference [15]. An Inverse Perspective Mapping (IPM) technique is used for the top view generation of the lane image, and it is pre-processed to remove the unused features from the IPM map. They also used wavelet decomposition canny edge detection technique. Removal of unused features using the model is the main advantage, which became a reason for performing the survey. The limitation of the model is that the model is not built for working with satellite or aerial landscape images. It just describes the theoretical approach.
The authors in [16] came up with a reliable way of detecting and tracking roadways, which facilitates the safety of highways. The methodology includes capturing the image, calibration of the camera, canny edge detection, choosing ROI, Hough transformation, and outdoor fitting. This methodology achieves an efficient way of detecting lines on the roads, with the help of relevant algorithms such as canny edge detection and Hough transformation. The proposed model suffers from the disadvantage that it shows the lines on the roads rather than the roads and it fails in detecting the lanes.
Agyekum et al. proposed a proxy re-encryption scheme to perform data sharing in devices in the Internet of Things securely using blockchain technology [17,18]. In the proposed method, a blockchain and edge devices are added for more secure storage and transmission of data. Before granting access to data, the user must be validated using SHA-512. The main contribution of the author is to perform encryption efficiently using complex blockchain technology which became a motive for survey. Once the data are stored in the blockchain, they are immutable and consume more processing power which is not practical.
Khashan et al. proposed a unique parallel PRE workload allocation technique to dynamically route the massive data re-encryption operation into the fog network [19]. It also employs lightweight asymmetric encryption to ensure end-to-end security for users sharing large amounts of data. The proxy will use the generated key to send the encrypted data to the cloud. The data are re-encrypted at the fog nodes to send to the authorized person. The theoretical approach in the methodology of the paper helped us to gain insights about the practical implementation of proxy re-encryption. This work is not implemented on real platforms, so it cannot be considered practical. It also includes more complexities in implementation.
Ali et al. proposed a model to transfer medical data securely using fog technology [20]. The medical data are securely transferred after two encryption algorithms, namely Rivest–Shamir–Adleman (RSA) and Advanced Encryption Standards (AES). The AES and RSA algorithms are used for the encryption of data, and the algorithms are embedded inside a Raspberry PI and also used fog computing technology. The main contribution of the work is securing medical data in the IoT equipment with the help of efficient algorithms such as AES and RSA. This survey helped in the encryption process of our proposed methodology. The system suffers from limitations as it is time-consuming and using Raspberry PI is not completely secure. This method also fails in computing huge amounts of data. The related works are summarized in Table 1.

Table 1.
Comparison of related works.
3. Proposed Methodology
The input of the proposed methodology is a lane image. Features are extracted from the input lane images () and are classified as fake or authentic with the help of the ANN model. This image is given as input to the U-Net model. The U-Net model consists of encoders and decoders which help in identifying lanes of the input image () Further, a genuine lane-detected image is secured with the help of a proxy re-encryption technique over the fog (H()). Lightweight encryption algorithm such as Rivest–Shamir–Adleman (RSA) is used in the encryption of the lane-identified authentic image (). Elliptic Curve Cryptography (ECC) is used to re-encrypt the bona fide image over the proxy server. Decryption is performed and integrity is verified at the receiver side [32]. Figure 1 gives an overview structure of the proposed methodology.
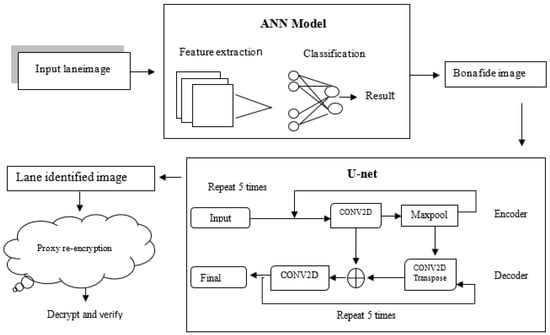
Figure 1.
Proposed architecture.
3.1. Demonstration of ANN Model
ANN model construction takes place with the help of three subsections. The first subsection deals with data acquisition and processing. In the second subsection, a brief description of the performance of ELA is mentioned. The final subsection deals with the construction of the ANN model.
3.1.1. Datasets and Requirement Analysis
The datasets utilized in the proposed methodology are taken from Kaggle. The CASIA dataset is utilized for feature extraction which is made up of 15K files. Satellite landscape images are applied to the U-Net model for training purposes. The total size of the datasets required for both feature extraction and lane detection constitutes 7.58 GB where 3.58 GB is the size of the CASIA dataset and 4 GB is the size of the landscape image dataset. The configurations required for the proposed methodology are given below in detail. The the proposed methodology requires Windows 7 as a minimum for performing its functionality. The development environment utilized here is Google Colab and Python programming language, a minimum of 4 GB RAM and hard disk space with 5 GB as a minimum are considered. Table 2 provides all acronyms used in the article.

Table 2.
Abbreviations and their representations.
3.1.2. Data Acquisition and Processing
This subsection deals with the processing of satellite lane images. The satellite lane images are normalized and transformed into a particular size of 128*128*3. The images are further processed and converted to NumPy arrays for maintaining compatibility. The entire process for data preparation and processing is demonstrated in the below steps.
- Step 1: Reading the input lane image = read
- Step 2: Resizing the image data / 255.0
- Step 3: Conversion of image data to array data is described as follows:
3.1.3. Performance of Error Level Analysis (ELA)
This subsection deals with the functioning of Error Level Analysis (ELA). ELA helps in the identification of tampered regions in a given input image. ELA differentiates tampered and authentic images by creating white and bright regions over the input image.
- Step 1: Assigning input image to ELA for the functioning of ELA:
- Step 2: The difference between the original and RGB image is computed as follows:
- Step 3: Common range for the above image data is generated as follows:
- Step 4: Enhancement of image with the help of ELA is performed as follows:
3.1.4. Generation of ANN Model
This subsection discusses the steps for constructing the ANN model. The ANN helps in the classification of satellite lane images as fake or authentic.
- Step 1: The model consists of many convergent, max pool layers for extracting features model.add(Conv, Maxpool)
- Step 2: 80% of train and 20% of test dataset is passed through the model:
- Step 3: The model consists of output layers whose sigmoid function is as below:
- Step 4: Confidence for the above model is computed as follows:
Figure 2 gives a detailed description of the ANN network model. The architecture of the ANN model consists of various convergent (Conv2D) and max pooling layers for the extraction of features from the input image. Classification of satellite lane images as fake or authentic is performed with the help of the softmax function.
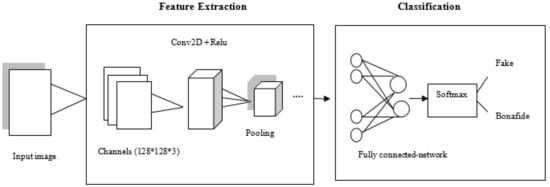
Figure 2.
ANN network model.
3.2. Lane Detection Using U-Net Model
Lane detection from genuine satellite images using U-Net model construction happens in mainly two steps. The steps include a loading of the image data along with their respective mask images and the construction of the U-Net model.
3.2.1. Construction of U-Net Model
The U-Net architecture has an encoder path and a decoder path. In the encoder path, the number of filters increases from 16 to 256 exponentially to obtain various layers in the model. The input image is passed into various numbers of filters by using the Conv2D method in the Tensor flow library. Every time batch normalization is performed after applying the Conv2D method followed by the application of the ReLu activation function. After every increment of the number of filters, max pooling, followed by dropout functions is applied to the obtained results. As a result of the operations in the encoder path, the size of the result is decreased. In the decoder path, Conv2DTranspose along with concatenation followed by dropout functions are performed which increases the final result size to the original size.
- Step 1: The number of filters considered for the U-Net model is defined as follows:
- Step 2: The Conv2D in the encoder path is applied as follows for every value in :and
- Step 3: TFor each increment the max pooling is applied as follows:y = MaxPooling2D((2,2))(x) and y=DropOut( )(x)
- Step 4: The Conv2DTranspose is applied on the layers obtained from the encoder path in decreasing order of the filters which eventually gives the original size of an image.
- If , are the previous layers in which the transpose function is performed, concatenate function is applied as follows:and z=Dropout( )(z)
3.2.2. Predicting Lanes Using Constructed Model
The input images are read from the user; resizing, and reshaping followed by conversion into NumPy array is performed. The transformed images are passed into the generated U-Net model as follows:
- The input image is resized as follows: Img=read(imagepath),shape = and
- The image is reshaped into shape as shown below:
- The image is transformed into a numerical array using the NumPy module and lanes are detected as follows:
Figure 3 shows the detailed procedure of the U-Net model construction through various layers. The architecture shows the output produced in each layer after applying various operations such as max pooling, batch normalization, and dropout. In the figure, Maxpooling refers to the max pooling operation followed by dropout whereas CONV2D refers the Conv2D function followed by batch normalization.
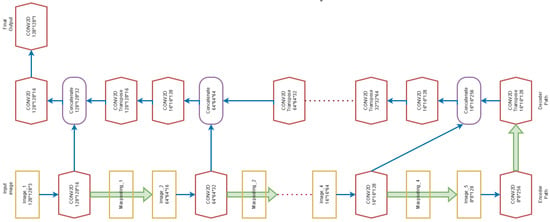
Figure 3.
U-Net Model System Architecture.
3.3. Secure Fog Computation with Proxy Re-Encryption Technique
Apart from checking the authenticity of the satellite landscape images before performing lane detection furthermore, there is an imperative need to provide confidentiality and integrity to the processed image. To provide confidentiality, the proxy re-encryption technique is used in the proposed system. In the proxy re-encryption technique, the sender performs encryption of lane-detected authentic images on their side using the RSA algorithm. To ensure integrity, the hash value of the image is generated on the sender’s side. The RSA encrypted cipher image along with generated hash value is uploaded to the proxy. In proxy, the cipher image is decrypted and integrity is verified. Later, re-encryption is performed using the ECC algorithm. The ECC-based cipher is sent to the receiver. The receiver performs decryption using the ECC algorithm and verifies integrity.
3.3.1. RSA-Based Encryption and Hash Generation
Encryption using the RSA algorithm and hash value generation using SHA-256 is performed as follows on the sender’s side:
- Step 1: RSA key generation is done by performing operations after generating two random prime numbers p, q as follows:
- Step 2: The is formed by encoding the lane-detected authentic image into ASCII format. Encryption of image using RSA algorithm is performed as below:
- Step 3: The hash value of the original image is generated using the SHA-256 algorithm as:
3.3.2. Proxy Re-Encryption and Integrity Verification
The decryption of the cipher image is performed on the proxy side using the RSA algorithm and integrity is verified.
- Step 1: is decrypted on the proxy-side using
- Step 2: New hash value is generated using SHA-256 to the image obtained after decryption using the RSA algorithm.
- Step 3: Verify integrity by comparing values. If both values are equal integrity is verified otherwise, is tampered with before reaching proxy.
- Step 4: After integrity checking, the is re-encrypted using ECC algorithm.
- Step 5: Generally, an elliptic curve is represented as and elliptic curve with parameters and where q is a prime number. G is a point on an elliptic curve.
- Step 6: The public key and Secret key .
- Step 7: Encryption is performed after encoding as follows:
3.3.3. ECC Decryption and Integrity Verification on Receiver’s Side
The proxy re-encrypted image received by the receiver is decrypted using the ECC algorithm [33] and integrity is verified to find any traces of modifications on .
- Step 1: ECC-based decryption is performed as follows:
- Step 2: New hash value is generated using SHA-256 to the image obtained after decryption using the ECC algorithm.
- Verify integrity by comparing and values. If both values are equal integrity is verified otherwise, is tampered with before reaching the receiver.
3.3.4. Secure Communication with Fog Authentication
Secure communication between the users is achieved with the help of fog as follows [34]. Each step discussed below gives a brief description of the secure communication between users and the proxy. It is carried out in three phases. In the first phase, authentication is verified. In the second phase, the encrypted lane image is transferred securely to Proxy-Server. In the third phase, the Proxy-Server helps in the conversion of a secret key with which User B can decrypt the image securely after successful authentication.
- User A request authentication from AS:
- Authentication of User A by AS:
- Secure transfer of encrypted data from User A to proxy server
- User B request authentication from AS:
- Authentication of User B by AS:
- Verification and decryption of the message
The detailed process of authentic communication between the users and the proxy server in the proposed system is as follows. The initial level of communication deals with authentication. User A authenticates with the Proxy-Server for achieving secure communication. In the later phase, auth is generated which acts as a token between User A and Proxy-Server. After successful authentication User A transfers the image encrypted using RSA to the Proxy-Server. Proxy-Server here converts the secret key of User A to the secret key of User B, allowing decryption at User B’s side. During re-encryption, the ECC algorithm is used by the Proxy-Server, enhancing security.
4. Results and Analysis
The proposed methodology constitutes of various networking models and cipher techniques. The results and analysis of each portion of the proposed methodology are briefly discussed below. It is made up of various contrasting techniques between the proposed methodology and other relevant works. This section mainly focuses on how well the proposed methodology works when compared with other relevant works.
4.1. Predictions of ANN Model
The proposed methodology constitutes of ANN model for classifying the satellite lane image as fake or bona fide. The model receives satellite lane images as input data. The model comprises the softmax function for classifying the lane image as fake or authentic. The model computes the fake or bona fide confidence using the formulae . The prediction obtained from the ANN model is termed as and is the max argument of the prediction. Figure 4 and Figure 5 are passed through the layers of the ANN model to identify them as fake or authentic. The outcome for the input Figure 4 is a fake image and the confidence is computed as 94.7%. The outcome for the input Figure 5 is a bona fide image and the confidence is computed as 89.7%.

Figure 4.
Fake image.

Figure 5.
Authentic image.
Outcome of U-Net Model
As mentioned in the proposed methodology section, the U-Net model is used in detecting the lanes from the input image. The U-Net model consists of various encoder and decoder paths for efficiently detecting the lanes from an input image. Only genuine images obtained from the ANN model are given as input to the U-Net model for detecting the lanes. Figure 6 is the outcome gained by passing the input image, Figure 5, through various layers of the U-Net model. Later, Figure 7 is secured with the help of a lightweight encryption algorithm known as RSA. Figure 6 is the cipher image generated with the help of the RSA encryption algorithm.
Figure 6.
Proxy re-encryption-based cipher image.
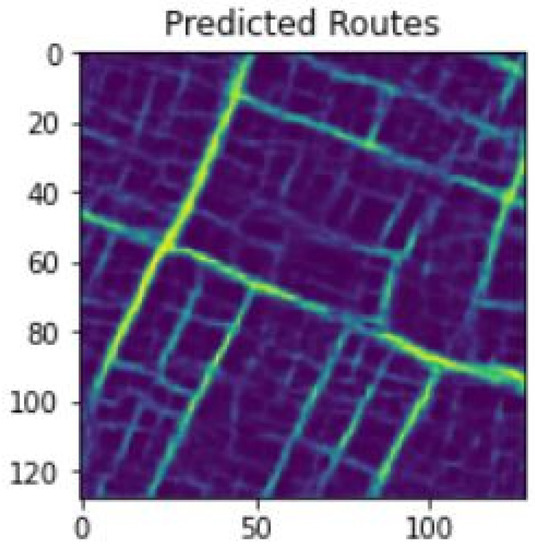
Figure 7.
Lane-predicted image.
4.2. Performance Analysis
The performance analysis for the proposed methodology is computed using relevant metrics such as accuracy, testing and validation curves, confusion matrix, etc. The summary of the ANN model is provided below in Figure 8. It gives a brief overview of the shapes and types of the layers used and the total number of parameters required for training the model.
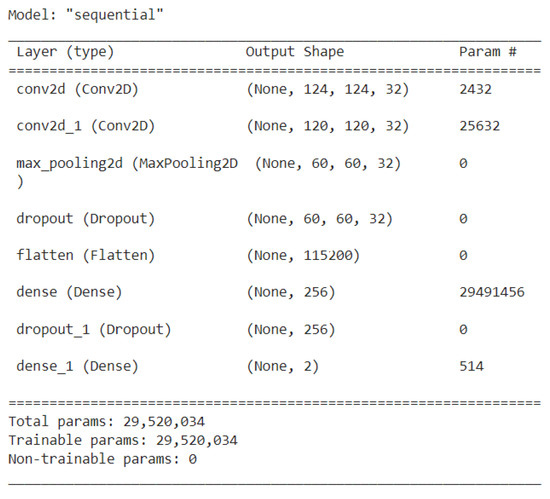
Figure 8.
Parameters used in the ANN model.
4.2.1. Confusion Matrix/Error Matrix
A confusion matrix is a metric which is used to measure the performance of a machine-learning model. It is an n * n matrix which uses the actual values and predicted values for computing accuracy. The accuracy of the model can be improved by maintaining low values for FPR, and FNR and high values for TPR, and TNR. Figure 9, Table 3 gives an overview of the predicted and actual values obtained through the ANN model.
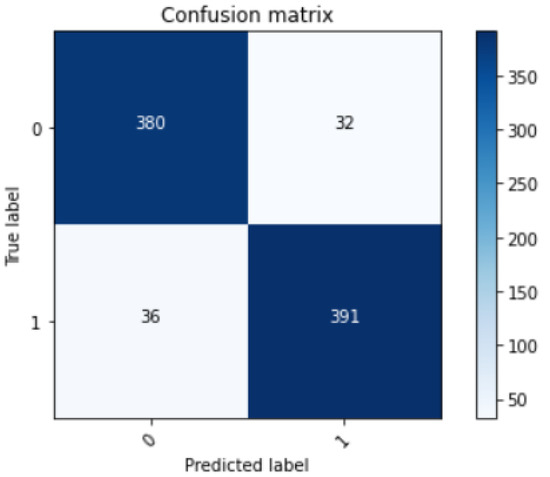
Figure 9.
Confusion matrix of ANN model.

Table 3.
Error matrix.
4.2.2. Accuracy and Precision
Accuracy is one of the factors considered for evaluating the efficiency of the proposed methodology. Accuracy gives the percentage of correct predictions made by the model. Higher accuracy results in greater performance of the model. Accuracy for the proposed model is calculated as follows:
This emphasizes that 92 predictions out of 100 predictions are made accurately by the model. Precision is also one of the factors for evaluating the model’s performance. The precision determines the true relevancy of predictions made by the model. The precision of the proposed methodology is computed as follows:
4.2.3. Training and Validation Curves
Figure 10 and Figure 11 depict the loss and accuracy curves for the proposed methodology, respectively. Figure 10 represents the validation and training loss, and accuracy for the ANN model used in the proposed methodology. Figure 10 summarizes that the accuracy of the training data increases concerning the number of epochs. This helps us to conclude that the model achieves the best accuracy and if the model is further trained it can lead to an overfitting curve. Figure 11 represents the curves generated from the U-Net model. It shows a summary of training curves. Here, the training loss decreases and the training accuracy increases which gives a positive notion of the accuracy.
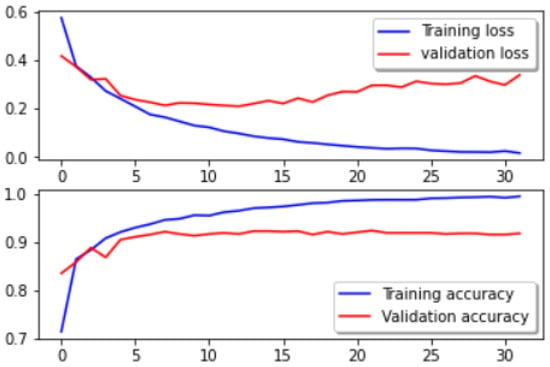
Figure 10.
Loss curves.
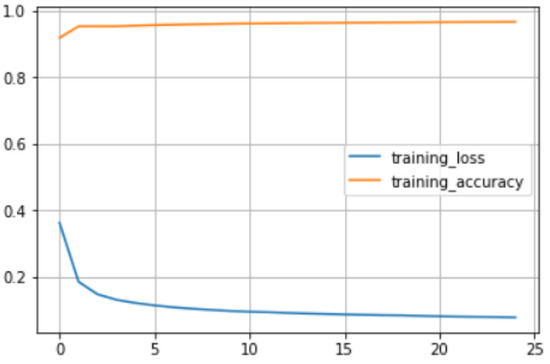
Figure 11.
Training gist curves.
4.2.4. Comparison of Relevant Models
Table 4 describes the various techniques involved in comparing the proposed methodology with the relevant methodologies. The proposed methodology gives a better processing time and throughput when compared with other works. This gives a positive notion of the efficiency of the proposed methodology. Moreover, the accuracy of the proposed methodology is high when compared with the other accuracy mentioned in the table below. This indicates that the precision of the model is greater than the compared models. On the other hand, the time complexity of the model is low, which results in better performance.

Table 4.
Comparison of relevant techniques.
4.2.5. Analysis of RSME Test
RSME (root-mean-square error) test is performed to confirm the originality of the image. It compares and contrasts the similarities between the decrypted cipher and the original image. Table 5 gives the results of the RMSE test. According to Table 5, it is confirmed that the decrypted cipher images and the original images are identical. This infers the fact that the image data are not modified or tampered with.

Table 5.
RSME analysis.
4.2.6. Encryption Time Analysis
Table 6 represents the comparison of encryption times for RSA and ECC algorithms when different sizes of JPG format images are given as input to the proposed system. The encryption times are less when compared to various other public key cryptographic algorithms. This facilitates the improved efficiency of the proposed system. Figure 12 represents the graphical representation of the comparison of encryption times for different sizes of JPG data.

Table 6.
Encryption time analysis.

Figure 12.
Comparison of encryption times.
Table 7 represents the comparison of encryption times for RSA and ECC algorithms when different sizes of JPG format images are given as input to the proposed system. The encryption times are less when compared to various other public key cryptographic algorithms. This facilitates the improved efficiency of the proposed system. Figure 13 represents the graphical representation of the comparison of encryption times for different sizes of JPG data.

Table 7.
Encryption time analysis for different image formats.
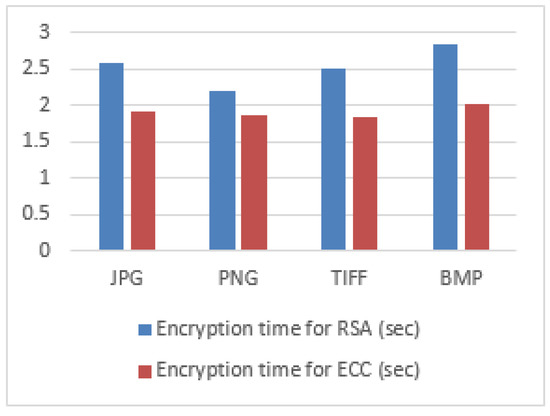
Figure 13.
Comparison analysis for various image formats.
4.3. Security Audit
The proposed methodology for proxy re-encryption consists of two security transformation algorithms RSA and ECC which provide resistance against various attacks as described in this section.
4.3.1. Cipher Text Only Attacks
In this type of attack, the cryptanalyst knows the encryption algorithm used and the cipher image. This type of attack can be effectively resisted by the proposed model as the secret keys which are required for obtaining the original lane detected image from the cipher image are generated by performing some operations on large randomly generated prime numbers. So, this process of key generation makes it difficult to crack the secret keys to obtain the original image from a known cipher image.
4.3.2. Brute Force Attacks
The brute force attack involves the attempt of the cryptanalyst to guess the secret key by trying all the possible combinations. The size of the secret key in the process is 1024 bits for RSA which makes it difficult to know the keys using brute force attacks. The ECC algorithm also provides good resistance to brute force attacks despite being of smaller key size than the RSA algorithm.
4.3.3. Timing Attacks
In timing attacks, the cryptanalyst tries to find the secret key of the user by analyzing the decryption times of different encrypted images. As stated before, the decryption times of lane-detected images are almost the same, which shows that the proposed model shows much resistance toward these types of attacks. The proxy re-encryption technique makes it much more complex for attackers to perform attacks on the cipher image data.
5. Conclusion
The proposed model performs efficiently to identify the authenticity of satellite landscape images using an artificial neural network model. The U-Net algorithm helps in discovering lanes from authenticated images with good accuracy. In the later phase, secure communication is achieved through fog computation along with the proxy re-encryption technique. To enhance security and avoid Man in the Middle attacks,, a hash value is generated and verified at each phase of the proposed methodology. This infers that the proposed model provides authenticity, confidentiality, and integrity of the system which gives better performance.
6. Future Work
In the future, the proposed methodology can be extended to secure various types of satellite and social data. The proposed model can be extended in terms of security to solve the real-time loopholes of security.
Author Contributions
Conceptualization, Y.N. and C.R.; methodology, C.R.; software, Y.N.; validation, T.R.G. and C.R.; formal analysis, P.A.; investigation, Y.N.; resources, T.R.G.; data curation, K.L.; writing—original draft preparation; writing—review and editing, K.L. and G.S.; visualization, K.L.; supervision, G.S.; project administration, K.L.; funding acquisition, T.R.G. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Available after direct request to authors.
Conflicts of Interest
The authors declare no conflict of interest.
Sample Availability
Samples of the compounds are available from the authors.
Abbreviations
The following abbreviations are used in this manuscript:
| MDPI | Multidisciplinary Digital Publishing Institute |
| DOAJ | Directory of open access journals |
| TLA | Three letter acronym |
| LD | Linear dichroism |
References
- Rupa, C.; Harshita, M.; Srivastava, G.; Gadekallu, T.R.; Maddikunta, P.K.R. Securing Multimedia using a Deep Learning based Chaotic Logistic Map. IEEE J. Biomed. Health Inform. 2022. early access. [Google Scholar] [CrossRef] [PubMed]
- Rehman, M.U.; Shafique, A.; Ghadi, Y.Y.; Boulila, W.; Jan, S.U.; Gadekallu, T.R.; Driss, M.; Ahmad, J. A Novel Chaos-Based Privacy-Preserving Deep Learning Model for Cancer Diagnosis. IEEE Trans. Netw. Sci. Eng. 2022, 9, 4322–4337. [Google Scholar] [CrossRef]
- Javed, A.R.; Jalil, Z.; Zehra, W.; Gadekallu, T.R.; Suh, D.Y.; Piran, M.J. A comprehensive survey on digital video forensics: Taxonomy, challenges, and future directions. Eng. Appl. Artif. Intell. 2021, 106, 104456. [Google Scholar] [CrossRef]
- Verdoliva, L. Media forensics and deepfakes: An overview. IEEE J. Sel. Top. Signal Process. 2020, 14, 910–932. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Srivastava, G.; Gupta, G.P.; Tripathi, R.; Gadekallu, T.R.; Xiong, N.N. PPSF: A privacy-preserving and secure framework using blockchain-based machine-learning for IoT-driven smart cities. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2326–2341. [Google Scholar] [CrossRef]
- Rajyalakshmi, V.; Lakshmanna, K. A review on smart city-IoT and deep learning algorithms, challenges. Int. J. Eng. Syst. Model. Simul. 2022, 13, 3–26. [Google Scholar] [CrossRef]
- Kavitha, A.; Reddy, V.B.; Singh, N.; Gunjan, V.K.; Lakshmanna, K.; Khan, A.A.; Wechtaisong, C. Security in IoT Mesh Networks based on Trust Similarity. IEEE Access 2022, 10, 121712–121724. [Google Scholar] [CrossRef]
- Ch, R.; Srivastava, G.; Gadekallu, T.R.; Maddikunta, P.K.R.; Bhattacharya, S. Security and privacy of UAV data using blockchain technology. J. Inf. Secur. Appl. 2020, 55, 102670. [Google Scholar] [CrossRef]
- Elmogy, A.; Bouteraa, Y.; Alshabanat, R.; Alghaslan, W. A New Cryptography Algorithm Based on ASCII Code. In Proceedings of the 2019 19th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA), Sousse, Tunisia, 24–26 March 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 626–631. [Google Scholar]
- Ahmad, J.; Tahir, A.; Khan, J.S.; Khan, M.A.; Khan, F.A.; Habib, Z. A partial ligt-weight image encryption scheme. In Proceedings of the 2019 UK/China Emerging Technologies (UCET), Glasgow, UK, 21–22 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–3. [Google Scholar]
- Han, J.; Xu, Y.; Di, L.; Chen, Y. Low-cost multi-UAV technologies for contour mapping of nuclear radiation field. J. Intell. Robot. Syst. 2013, 70, 401–410. [Google Scholar] [CrossRef]
- Vacanas, Y.; Themistocleous, K.; Agapiou, A.; Hadjimitsis, D. Building Information Modelling (BIM) and Unmanned Aerial Vehicle (UAV) technologies in infrastructure construction project management and delay and disruption analysis. In Proceedings of the Third International Conference on Remote Sensing and Geoinformation of the Environment (RSCy2015), Paphos, Cyprus, 16–19 March 2015; SPIE: Bellingham, WA, USA, 2015; Volume 9535, pp. 93–103. [Google Scholar]
- Joslin, M.; Hao, S. Attributing and Detecting Fake Images Generated by Known GANs. In Proceedings of the 2020 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 21 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 8–14. [Google Scholar]
- Dubey, G. Segmentation and Detection of Road Region in Aerial Images using Hybrid CNN-Random Field Algorithm. In Proceedings of the 2020 10th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 29–31 January 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 502–506. [Google Scholar]
- Liu, W.; Gong, J.; Ma, B. Research on lane detection method with shadow interference. In Proceedings of the 2019 Chinese Control Conference (CCC), Guangzhou, China, 27–30 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 7704–7709. [Google Scholar]
- Barua, B.; Biswas, S.; Deb, K. An Efficient Method of Lane Detection and Tracking for Highway Safety. In Proceedings of the 2019 1st International Conference on Advances in Science, Engineering and Robotics Technology (ICASERT), Dhaka, Bangladesh, 3–5 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Govada, K.A.; Jonnalagadda, H.P.; Kapavarapu, P.; Alavala, S.; Vani, K.S. Road Deformation Detection. In Proceedings of the 2020 7th International Conference on Smart Structures and Systems (ICSSS), Chennai, India, 23–24 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–5. [Google Scholar]
- Agyekum, K.O.B.O.; Xia, Q.; Sifah, E.B.; Cobblah, C.N.A.; Xia, H.; Gao, J. A Proxy Re-Encryption Approach to Secure Data Sharing in the Internet of Things Based on Blockchain. IEEE Syst. J. 2021, 16, 1685–1696. [Google Scholar] [CrossRef]
- Khashan, O.A. Parallel Proxy Re-Encryption Workload Distribution for Efficient Big Data Sharing in Cloud Computing. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Virtual, 27–30 January 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 554–559. [Google Scholar]
- Ali, A.B.R.; Alagumariappan, P.; Vijayalakshmi, S.; Gughan, N.; Bhaskar, K. Analysis of Secure Transfer of Healthcare Data using Fog Computing. In Proceedings of the 2020 International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 10–12 September 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 529–531. [Google Scholar]
- Tanaka, M.; Kiya, H. Fake-image detection with Robust Hashing. In Proceedings of the 2021 IEEE 3rd Global Conference on Life Sciences and Technologies (LifeTech), Nara, Japan, 9–11 March 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 40–43. [Google Scholar]
- Kunbaz, A.; Saghir, S.; Arar, M.; Sönmez, E.B. Fake Image Detection Using DCT and Local Binary Pattern. In Proceedings of the 2019 Ninth International Conference on Image Processing Theory, Tools and Applications (IPTA), Istanbul, Turkey, 6–9 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Khashan, O.A. Hybrid lightweight proxy re-encryption scheme for secure fog-to-things environment. IEEE Access 2020, 8, 66878–66887. [Google Scholar] [CrossRef]
- Nida, N.; Irtaza, A.; Ilyas, N. Forged Face Detection using ELA and Deep Learning Techniques. In Proceedings of the 2021 International Bhurban Conference on Applied Sciences and Technologies (IBCAST), Islamabad, Pakistan, 12–16 January 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 271–275. [Google Scholar]
- Lian, Z.; Su, M.; Fu, A.; Wang, H.; Zhou, C. Proxy re-encryption scheme for complicated access control factors description in hybrid cloud. In Proceedings of the ICC 2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Ghanem, S.; Kanungo, P.; Panda, G.; Satapathy, S.C.; Sharma, R. Lane detection under artificial colored light in tunnels and on highways: An IoT-based framework for smart city infrastructure. Complex Intell. Syst. 2021, 1–12. [Google Scholar] [CrossRef]
- Hu, Y.; Xiang, Q.J.; Liu, Z.H.; Conrad, Z.J.; Cao, J.N.; Zhang, X.P. Hovering efficiency optimization of the ducted propeller with weight penalty taken into account. Aerosp. Sci. Technol. 2021, 117, 106937. [Google Scholar] [CrossRef]
- Zheng, W.; Liu, X.; Yin, L. Sentence representation method based on multi-layer semantic network. Appl. Sci. 2021, 11, 1316. [Google Scholar] [CrossRef]
- Ban, Y.; Liu, M.; Wu, P.; Yang, B.; Liu, S.; Yin, L.; Zheng, W. Depth estimation method for monocular camera defocus images in microscopic scenes. Electronics 2022, 11, 2012. [Google Scholar] [CrossRef]
- Zhou, G.; Bao, X.; Ye, S.; Wang, H.; Yan, H. Selection of optimal building facade texture images from UAV-based multiple oblique image flows. IEEE Trans. Geosci. Remote Sens. 2020, 59, 1534–1552. [Google Scholar] [CrossRef]
- Zhou, G.; Long, S.; Xu, J.; Zhou, X.; Song, B.; Deng, R.; Wang, C. Comparison analysis of five waveform decomposition algorithms for the airborne LiDAR echo signal. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2021, 14, 7869–7880. [Google Scholar] [CrossRef]
- Polyakov, Y.; Rohloff, K.; Sahu, G.; Vaikuntanathan, V. Fast proxy re-encryption for publish/subscribe systems. ACM Trans. Priv. Secur. (TOPS) 2017, 20, 1–31. [Google Scholar] [CrossRef]
- Chen, J.; Liu, Y.; Xiang, Y.; Sood, K. RPPTD: Robust privacy-preserving truth discovery scheme. IEEE Syst. J. 2021, 16, 4525–4531. [Google Scholar] [CrossRef]
- Wang, W.; Lin, H.; Wang, J. CNN based lane detection with instance segmentation in edge-cloud computing. J. Cloud Comput. 2020, 9, 1–10. [Google Scholar] [CrossRef]
- Meiliasari, R.P.; Syalim, A.; Yazid, S. Performance analysis of the symmetric proxy re-encryption scheme. In Proceedings of the 2019 International Workshop on Big Data and Information Security (IWBIS), Bali, Indonesia, 11 October 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 91–96. [Google Scholar]
- Singh, B.; Sharma, D.K. Predicting image credibility in fake news over social media using multi-modal approach. Neural Comput. Appl. 2021, 34, 21503–21517. [Google Scholar] [CrossRef] [PubMed]
- El-Latif, A.; Eman, I.; Taha, A.; Zayed, H.H. A passive approach for detecting image splicing based on deep learning and wavelet transform. Arab. J. Sci. Eng. 2020, 45, 3379–3386. [Google Scholar] [CrossRef]
- Varona, B.; Monteserin, A.; Teyseyre, A. A deep learning approach to automatic road surface monitoring and pothole detection. Pers. Ubiquitous Comput. 2020, 24, 519–534. [Google Scholar] [CrossRef]
- Shi, Y.; Xu, X.; Xi, J.; Hu, X.; Hu, D.; Xu, K. Learning to detect 3D symmetry from single-view RGB-D images with weak supervision. IEEE Trans. Pattern Anal. Mach. Intell. 2022. early access. [Google Scholar] [CrossRef]
- Zhou, W.; Liu, J.; Lei, J.; Yu, L.; Hwang, J.N. GMNet: Graded-feature multilabel-learning network for RGB-thermal urban scene semantic segmentation. IEEE Trans. Image Process. 2021, 30, 7790–7802. [Google Scholar] [CrossRef]
- Yin, M.; Zhu, Y.; Yin, G.; Fu, G.; Xie, L. Deep Feature Interaction Network for Point Cloud Registration, With Applications to Optical Measurement of Blade Profiles. IEEE Trans. Ind. Inform. 2022. early access. [Google Scholar] [CrossRef]
- Zhang, Y.; Luo, J.; Li, J.; Mao, D.; Zhang, Y.; Huang, Y.; Yang, J. Fast inverse-scattering reconstruction for airborne high-squint radar imagery based on Doppler centroid compensation. IEEE Trans. Geosci. Remote. Sens. 2021, 60, 5205517. [Google Scholar] [CrossRef]
- Lu, H.; Zhu, Y.; Yin, M.; Yin, G.; Xie, L. Multimodal Fusion Convolutional Neural Network with Cross-attention Mechanism for Internal Defect Detection of Magnetic Tile. IEEE Access 2022, 10, 60876–60886. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).