Abstract
Barriers are utilized for various tasks in security, environmental monitoring, penetration detection and reconnaissance. It is highly necessary to consider how to support pedestrian tracking and target detection in theme park areas having multiple obstacles. In this paper, we create security barriers through cooperation between mobile robots and UAVs for use in theme park areas where multiple obstacles of undetermined forms are placed. We formally define the problem and the goals. The goals are the following: to maximize the number of convex hull obstacle-aware tracking barriers using mobile robots and UAVs, to satisfy given detection accuracy, and to ensure that all environments are protected by convex hull obstacle-aware tracking barriers without disturbance from irregular obstacles. To address the problem, we propose two different algorithms, to improve security barriers and avoid various forms of obstacles, in a bid to work towards a 6G-enabled virtual emotion environment. Then, the proposed schemes are executed through simulations with various settings, and the numerical results evaluated with detailed discussions and demonstrations.
1. Introduction
Thanks to advances in mobile operations and intelligent technology, mobile robots have recently worked in extreme conditions, such as in severe disaster and accident areas, non-terrestrial spaces, harsh environments, isolated places, etc. Instead of single operations, a group of mobile robots have been applied to various industrial fields and smart cities. Mobile robots have been used to form cooperative groups consisting of multiple robots, or to perform specific tasks, within 5G considerations and promising 6G considerations, such as the following: basic control operations, information processing, and location tracking [1,2,3,4,5,6]. As applicable fields expand gradually, an optimal strategy, involving a group of mobile robots constructing obstacle-aware barriers to fit with required mission objectives and conditions, is indispensable. Cooperation between the Internet of Things (IoT) and artificial intelligence is advantageous in deciding optimal construction and in supporting effective obstacle recognition [7,8,9,10,11,12].
Unmanned aerial vehicles (UAVs) are widely used in commercial areas, and are increasingly applied to public and research fields. They play important roles in air traffic, and improving transmission optimization of terrestrial networks, including theme park applications, and smart cities [13,14,15,16,17,18,19,20,21,22]. Furthermore, the use of UAVs is expanding into academic fields and into numerous industrial areas, including blockchain, edge computing, neural networks, marine targets and so on [23,24,25,26,27,28,29,30,31,32,33].
On the other hand, the use of barriers has extended to various applications for future use in more diverse places and the conducting of tasks such as security provision, environmental monitoring, prevention, surveillance, reconnaissance, and virtual emotion surveillance [34,35,36,37]. Among these, the intrusion prevention system is a security system that has attracted the attention of next generation interests and is expected to form very active domestic and foreign markets. Rather than using mobile robots and UAVs separately, building barriers through mutual cooperation can improve accuracy in finding mission-specific formations that accord with a region, so as to successfully complete tasks. Cooperation and smooth communication in the execution of work facilitates high accuracy.
However, when mobile robots and UAVs work together, a route may be blocked, or communication interfered with, if there is an obstacle in the area, and this may cause operations to fail. Hence, the issue of avoiding obstacles that are not of fixed form, but irregular, should be considered an important issue. For successful work, a stable operation must be accomplished without any collisions with obstacles. Previous studies have not addressed the problem by setting convex hull obstacles with deformed cases. If an obstacle does not have the specified shape, problems may arise in recognizing the shape of the obstacle or in constructing the barrier. So, we differentiate ourselves by focusing on constructing barriers efficiently in regard to the research problem of irregular obstacles, by transforming obstacles into various shapes to investigate how these deformed obstacles can be avoided.
Based on the above motivations, the main content of this paper can be identified as follows:
- We design a convex hull obstacle-aware pedestrian tracking and target detection system for theme park applications, to achieve obstacle avoidance when mobile robots and UAVs work together to build tracking barriers in situations having multiple obstacles set with irregular shapes, not fixed shapes.
- We formally define the research problem associated with mobile robots and UAVs with the aim of building as many convex hull obstacle-aware tracking barriers as possible for obstacle avoidance.
- Two different methods are proposed, with their applied strategies and varied settings, to solve problems through simulation, to compare performance by arbitrarily regularizing obstacles, and to find and rearrange routes in advance.
The rest of this paper has the following organization. In Section 2, we briefly review previous studies and works. In Section 3, a convex hull obstacle-aware pedestrian tracking and target detection system for theme park applications is introduced, with its system configuration, assumptions, and essential terms, and the problem is defined. In Section 4, two different algorithms are presented with their basic ideas and execution procedures. Moreover, in Section 5, we evaluate the performances of the proposed algorithms based on numerical outcomes through simulations. Then, we conclude this paper in Section 6.
2. Related Works
In this section, we review previous related works and studies. The barrier concept was initially introduced, in [38], to detect penetration in wireless sensor networks. The location fault and error-enabled tolerant barrier coverage in wireless sensor networks was developed by [39]. In [40], the authors introduced the concepts of weak barrier coverage and strong barrier coverage in wireless sensor networks, with applicable scenarios and cases. In [41], the authors formally defined the problem in terms of the objective of creating a minimal number of directional sensors on condition that every target area is protected by directional sensor nodes. In [42], the authors formally defined the research problem around maximizing a system’s lifetime to cover two different situations, those of neglected sensors and normal sensors. In [43], one-way barrier coverage was devised in consideration of a comprehensive sensor and its applicability. One direction of cross is inappropriate for specific intrusion detection services but the one-way barrier devised would allow detection with a pre-determined direction. Moreover, in [44], the authors introduced a critical research problem of coverage hole detection and its boundary discovery. To resolve the problem, a localized algorithm, based on Delaunay triangulation, was developed with geometric information. In [45], the authors suggested a distributed greedy approach to find paths, using cooperation between mobile sensors and static sensors, to improve the sensed coverage region. In [46], the authors introduced fault-tolerant barriers using virtual emotion surveillance operated by an intelligent group of smart UAVs. Furthermore, in [47], the authors studied the important research problem that seeks a minimally segmented barrier in a two-dimensional area within a polygonally bounded perspective. They formally defined the problem to reduce undetectable penetration using mobile sensors. In [48], the authors focused on positioning mobile devices on the boundary of the polygonal environment to track penetrations of attackers. In [49], a periodically monitoring scheduling method was proposed to support every member, and its position, in a line-based barrier consisting of mobile devices. Furthermore, in [50], the authors utilized GPS technology and its information when location errors were found in built barriers and introduced a scheduling scheme for barrier construction by mobile devices with possible location faults and errors. In [51], a critical research problem was formally defined to seek the maximal number of mobile devices and system components on condition that the movable devices had limited bounds within the targeted region. In [52], the authors envisioned dynamic objects in barrier coverage and introduced a distributed approach to provide proper coverage to region of interests. Moreover, in [53], the authors focused on the research problem of how to build line-based barriers composed of mobile devices or nodes. They also considered the optimization problem of minimizing the maximal moving distance for each component or sensor, as well as minimizing the total moving distance of mobile sensors.
Previous studies have generally assumed that there are no obstacles in the given area and create barriers [38,39,40,41,42,43,44,45,46,47]. Figure 1a represents a common security barrier in a square-shaped area. As shown in Figure 1a, three security barriers were formed by mobile robots and UAVs so that each security barrier detected any penetration from top to bottom, or from bottom to top, satisfying the requirement and objective of the existing barrier for the targeted area. Given the heterogeneous detection or communication ranges of system components, including mobile robots and UAVs, existing security barriers were gradually created by the adjusted, or changed, location of system components and by dealing with overlapping communication ranges. This method covers an entire area and it is easy to connect components to one another. However, only limited situations, having no obstacles, can be covered. So, additional consideration is necessary in regard to avoiding obstacles and creating appropriate barriers in a targeted area. Most previous works deliberated on the relatively simple case of regular shaped obstacles in a given area. It is reasonable to proceed with research on creating obstacle-aware barriers to fit with practical scenarios.

Figure 1.
Brief descriptions of basic security barrier formations and of obstacles in a target area: (a) an example of common security barriers, (b) overlapping coverage when obstacles intrude.
3. Proposed Framework
First, this section presents the initial system settings, configurations and assumptions. Additionally, the main problem is formally defined in consideration of convex hull obstacle-aware tracking and detection.
3.1. System Configuration and Assumptions
The following settings and assumptions are applied to the proposed system.
- The proposed system is composed of mobile robots and UAVs as system components, where each component has different detection or communication ranges.
- Obstacles are not limited to squares but have various shapes.
- Several obstacles are not made by mobile robots and UAVs and obstacle-aware barriers are not made by placing them on top of obstacles.
- A convex hull obstacle-aware tracking barrier is created when the communication ranges of system components overlap with the obstacle.
Figure 1b describes how, in a situation where an obstacle is positioned between a mobile robot and smart UAV, equipped with wireless transceiver, receiver, and heterogeneous communication or detection range with an overlapped portion, an obstacle-aware security barrier can be generated by the system components in the two-dimensional environment.
Figure 2 presents a brief overview of convex hull obstacle-aware pedestrian tracking and detection in a theme park application. As seen in Figure 2, when there are several convex hull obstacles, the specific barrier type of convex hull obstacle-aware detection can be constructed for the purpose of pedestrian tracking and detection in theme parks.
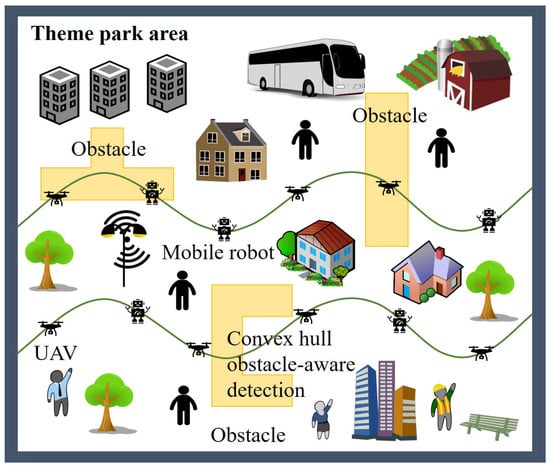
Figure 2.
A brief overview of convex hull obstacle-aware pedestrian tracking and detection in theme parks.
3.2. Essential Terms, Problem Definition and Notations
Now, the basic terms which are used in the proposed system are presented in this subsection.
Definition 1
(convex hull obstacle-aware tracking and detection barriers). Assume that a set of system components S covering a group of surveillance mobile robots and a group of UAVs are positioned in theme park area T, where multiple convex hull-shaped obstacles C are included. The convex hull obstacle-aware tracking barriers for the theme park, referred as ConvexAwareTheme, are generated by mobile robots and UAVs to track pedestrians, as well as to detect targets in the theme park.
If we have a given area, and there are various forms of obstacles, the problem is to maximize the total number of barriers. First, it is required that the detection accuracy of the mobile robots and UAVs is greater than, or equal to, the specified value. Then, the component communication range is adjusted to less than the size of the obstacle. The reason for this adjustment is that, if the communication range becomes larger than the size of the obstacle, the problem can be solved by using one component and there is no need to discuss the problem. A formal definition of the main research problem to be solved follows.
Definition 2
(MaxConvexAwareTheme problem). It is given that there is a situation having various forms of obstacles C in a given area, rather than a situation having common barriers. The MaxConvexAwareTheme problem is solved by maximizing the number of convex hull obstacle-aware tracking barriers, while avoiding convex hull obstacles to generate a ConvexAwareTheme. The detection accuracy q of mobile robots and UAVs must exceed a certain value, and the communication range r must not be greater than the size of the smallest obstacle in the region. The obstacle is not of a fixed shape, such as a square, but rather the obstacle is of varied shapes, and the component cannot be placed on the obstacle.
Then, the objective of the MaxConvexAwareTheme problem is to:
The basic notations, with their brief descriptions, are summarized in Table 1.

Table 1.
Notations.
4. Proposed Methods
This section specifies two different algorithms designed to solve the MaxConvexAwareTheme problem with irregular obstacles. A description of the execution procedure with input, output and code of all developed algorithms are presented.
4.1. Algorithm 1: Pre-Filled Convex Hull-Aware Construction
Firstly, an algorithm for solving the MaxConvexAwareTheme problem, called Pre-Filled Convex Hull-Aware Construction, is proposed. Then, the execution procedures are described.
- Verify initial random locations of the system components S, including the mobile robots and UAVs, with their communication ranges r in theme park area T.
- A position of a convex hull obstacle in the whole area is grasped.
- Check the shape and area of the obstacle.
- The concave shape of the obstacle is arbitrarily filled in to form a square having the minimum area.
- The following procedures are iterated until a new convex hull obstacle-aware tracking barrier is not found.
- −
- Find a convex hull obstacle-aware tracking barrier consisting of a mobile robot and UAVs to satisfy the given detection accuracy q.
- −
- If a new convex hull obstacle-aware tracking barrier is sought, then, add the found barrier to the set of convex hull obstacle-aware tracking barriers H;
- Calculate the size of H;
- The number of convex hull obstacle-aware tracking barriers are returned as the final result.
Originally, it draws a square as close as possible to the size of the obstacle and fills in the missing parts arbitrarily. Since it is made into a square with the smallest area of the obstacle, it can reduce the amount of space wasted and reduce the number of parts to consider, reducing the execution time of the algorithm.
Figure 3 shows various situations that occur during the execution of Algorithm 1: Pre-Filled Convex Hull-Aware Construction. Figure 3a represents an initial state in which components are randomly arranged, and Figure 3b represents the square after filling in the missing parts of the obstacle. Figure 3c avoids obstacles and forms a barrier.
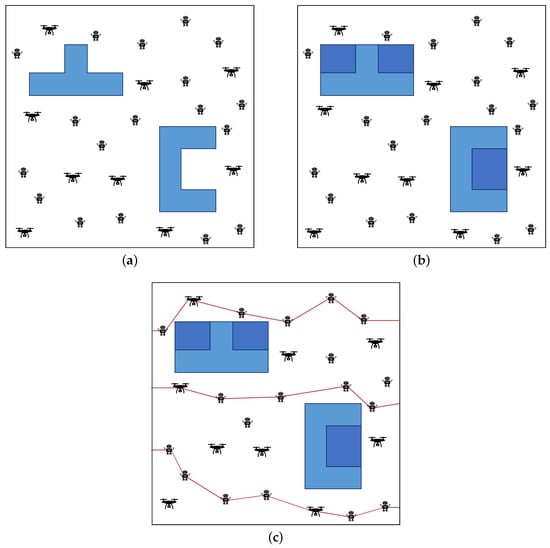
Figure 3.
The execution status and procedure of Algorithm 1. (a) Initial state: randomly placed components. (b) Recognition of obstacle shape rectangles. (c) Forming a convex hull obstacle-aware tracking barrier.
The pseudocode, with the implementation procedures, is explained in Algorithm 1.
| Algorithm 1 Pre-Filled Convex Hull-Aware Construction Inputs: , Output: |
|
4.2. Algorithm 2: Pre-Drawn Virtual Lines Relocation
Secondly, Algorithm 2, referred as Pre-Drawn Virtual Lines Relocation is devised to resolve the problem. Its basic idea is to find a route in advance and rearrange all system members in a given area to solve the obstacle problem. The execution stages are specified as follows.
- Randomly locate a set of system components S covering the mobile robots and UAVs in the theme park region T.
- Confirm convex hull obstacles within T;
- A mobile robot is arbitrarily selected to draw all the virtual paths from the edge of the area to the diagonal edge, avoiding obstacles.
- After that, all the mobile robots and UAVs are rearranged on the drawn virtual path.
- The below steps are iterated until a new convex hull obstacle-aware tracking barrier is not built.
- −
- With virtual lines, seek a convex hull obstacle-aware tracking barrier consisting of a mobile robot and UAVs to meet the required detection accuracy q.
- −
- If a new convex hull obstacle-aware tracking barrier is found, add the found barrier to the set of convex hull obstacle-aware tracking barrier H;
- Calculate the size of H;
- The number of convex hull obstacle-aware tracking barriers created by relocation are returned as the final result.
A virtual path drawn from end to end in a given region is drawn arbitrarily to determine the space in which the mobile robots and UAVs are placed, even if an unexpected obstacle occurs, and is not displayed separately. Knowing, and using, all the space the component can be placed appropriately, the unused space is minimized and the algorithm can be executed in regard to any form of obstacle.
Figure 4 depicts various situations that occur while performing Algorithm 2: Pre-Drawn Virtual Lines Relocation. Figure 4a indicates that a virtual line is arbitrarily formed within the zone, and Figure 4b confirms that all components are rearranged on the virtual line formed. Figure 4c uses the rearranged components to form a convex hull obstacle-aware tracking barrier.
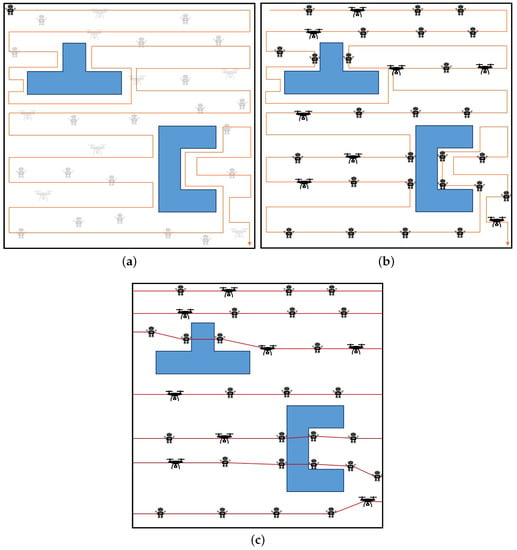
Figure 4.
The implementation status and procedure of Algorithm 2. (a) Arbitrarily form a virtual line. (b) Relocate components over virtual lines. (c) Forming a convex hull obstacle-aware tracking barrier with the rearranged components.
The pseudocode, with implementation procedures, is specified in Algorithm 2.
| Algorithm 2 Pre-Drawn-Virtual-Lines-Relocation Inputs: , Output: |
|
5. Results and Performance Analysis
In this section, the devised Algorithm 1, Pre-Filled Convex Hull-Aware Construction, and Algorithm 2, Pre-Drawn Virtual Lines Relocation, are analyzed according to the outcomes obtained after extensive simulations with various settings of theme park size, different numbers of system components, and different intervals of the random communication ranges. If we specified the system settings and execution environments, the number of system components for a group of mobile robots and a fleet of smart UAVs ranged from 100 to 250. The sizes of the theme park to be monitored were 1000 by 1000 m, 1050 by 1050, 1100 by 1100, 1150 by 1150, respectively. The intervals of the random communication ranges for the system components were considered to be from 30 to 45. Moreover, it was confirmed that all numerical outcomes as objective values of the total number of convex hull obstacle-aware tracking barriers would be an average number after 1000 experiments were implemented with different settings and parameters through an ad-hoc server, which had dual CPUs with each having 2.7 GHz, 2933 MHz and two GPUs with 48 GB for each.
For the first simulation scenario, we implemented the two different algorithms, Pre-Filled Convex Hull-Aware Construction and Pre-Drawn Virtual Lines Relocation, with number of obstacles = 2 in theme park size of , as seen in Figure 5. Note that the performance result graph consists of three axes where the X-coordinate shows the minimum communication radius of a system member, the Y-coordinate represents the total number of convex hull obstacle-aware tracking barriers, and the objective value of for Algorithms 1 and 2 is represented by the Z-coordinate. Figure 5a,b presents the output of the proposed algorithms when the number of system components n = 100 and n = 150 with the number of obstacles p = 2 in theme park area. Figure 5c,d demonstrates the outcome if n = 200 and n = 250, number of obstacles p = 2 in theme park were utilized in the simulation. As shown in Figure 5, we verified that the total number of convex hull obstacle-aware tracking barriers increased as the minimum communication range increased for both schemes. In addition, it was demonstrated that the performance of Algorithm 2, Pre-Drawn Virtual Lines Relocation, was better than that of Algorithm 1: Pre-Filled Convex Hull-Aware Construction.
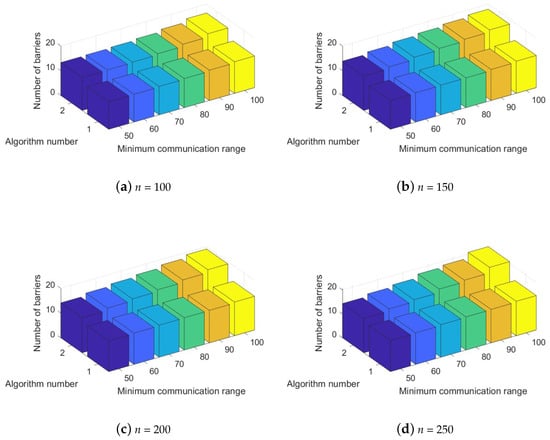
Figure 5.
Performance evaluation of different system components n of mobile robots and UAVs with the number of convex hull obstacles p = 2 in theme park size for the number of convex hull obstacle-aware tracking barriers.
In regard to the second experimental scenario, the two approaches, Pre-Filled Convex Hull-Aware Construction and Pre-Drawn Virtual Lines Relocation, were executed for theme park sizes of , , , with n = 100 and p = 2. As can be observed in Figure 6, there are three axes where the X-coordinate covers the minimum communication radius of a system member, and the Y-coordinate depicts the number of convex hull obstacle-aware tracking barriers for the two algorithms in the Z-coordinate, respectively. Figure 6a,b demonstrates the performance for the number of convex hull obstacle-aware tracking barriers when the two algorithms performed in a theme park sized and . Figure 6c,d compares Algorithms 1 and 2 implemented at and . According to Figure 6, the total number of convex hull obstacle-aware tracking barriers increased as the minimum communication radius increased for both approaches. Algorithm 2, Pre-Drawn Virtual Lines Relocation, outperformed Algorithm 1, Pre-Filled Convex Hull-Aware Construction for all applicable cases in the second group of experiments.
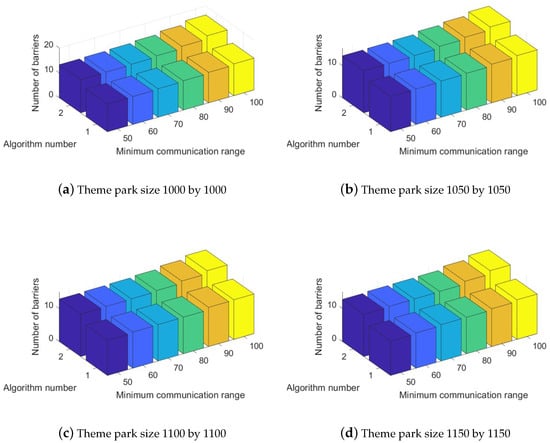
Figure 6.
Performance evaluation of different area sizes with number of system components n = 100 with the number of obstacles p = 2 for the number of convex hull obstacle-aware tracking barriers.
For the third set of simulation scenarios, the two algorithms of, Pre-Filled Convex Hull-Aware Construction and Pre-Drawn-Virtual-Lines-Relocation are achieved to resolve the MaxConvexAwareTheme problem. In this scenario, the random interval of communication range are considered as 30, 35, 40, 35, respectively. Similar to previous groups of simulations, we have three axis where X-coordinate signifies the minimum communication radius of system component and Y-coordinate describes the number of convex hull obstacle-aware tracking barriers by both algorithms in Z-coordinate with n = 100 and p = 2 as seen in Figure 7. And, Figure 7a,b express the objective value of with the random interval of communication range = 30, 35. Also, Figure 7c,d show the performance of two schemes with the random interval of communication range = 40, 45. Based on the numerical results as shown in Figure 7, it is identified that the total number of convex hull obstacle-aware tracking barriers is increasing as the minimum communication radius is increasing by both methods. As a whole, we can check that Algorithm 2: Pre-Drawn-Virtual-Lines-Relocation outperforms Algorithm 1: Pre-Filled-Convex Hull-Aware-Construction for every case in the third set of simulations consequently.
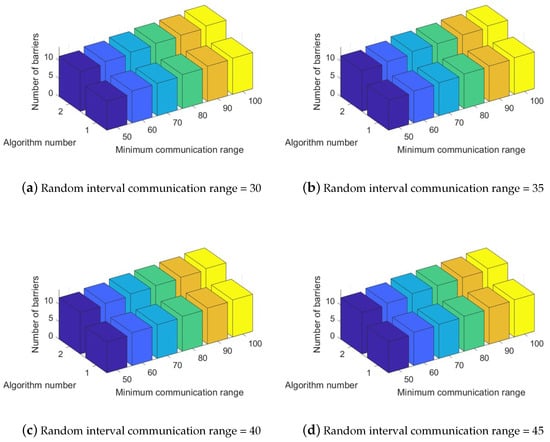
Figure 7.
Performance evaluation of different random interval communication ranges with the number of system components n = 100 and the number of obstacles p = 2 in theme park size for the number of convex hull obstacle-aware tracking barriers.
Lastly, for the fourth experimental scenario, the two schemes of Pre-Filled-Convex Hull-Aware-Construction and Pre-Drawn Virtual Lines Relocation, were used to solve the MaxConvexAwareTheme problem according to the different numbers of obstacles in the given areas. The number of convex hull obstacles p was set to 1, 2, 3, 4, respectively. To be consistent with previous scenarios, we also used three axes in the result graph. The X-coordinate presents the minimal communication range of the system component and the Y-coordinate depicts the total number of convex hull obstacle-aware tracking barriers completed by the proposed schemes in the Z-coordinate, with a total number of system components n = 100 and a given theme park area size of , as shown in Figure 8. Then, Figure 8a,b represents the objective value of with the number of convex hull obstacles p = 1, 2. Figure 8c,d displays the obtained results from the two algorithms with a random interval of communication range = 3, 4. Based on the simulation results, seen in Figure 8, we demonstrated that the total number of convex hull obstacle-aware tracking barriers increased as the minimal communication or detection range increased when Pre-Filled Convex Hull-Aware Construction and Pre-Drawn Virtual Lines Relocation were executed in the scenario. Furthermore, Algorithm 2, Pre-Drawn Virtual Lines Relocation, performed better in convex hull obstacle-aware tracking barrier construction than Algorithm 1, Pre-Filled Convex Hull-Aware Construction, for each applied case in the fourth group of simulations.
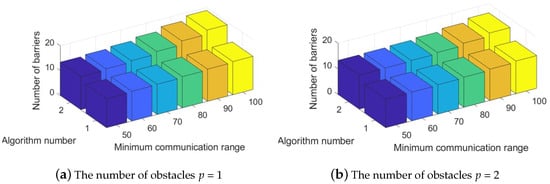
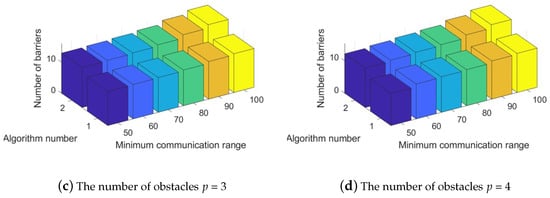
Figure 8.
Performance evaluation of different number of obstacles with the number of system components n = 100 in theme park size for the number of convex hull obstacle-aware tracking barriers.
6. Conclusions
In this paper, by focusing on cooperation between mobile robots and UAVs, we designed convex hull obstacle-aware tracking barriers that can be used to avoid obstacles of various shapes within a theme park area. The proposed system uses mobile robots and UAVs to create as many barriers as possible in areas with various forms of obstacles. We devised two different algorithms. Algorithm 1, Pre-Filled Convex Hull-Aware Construction, fills missing parts to make the shape of the obstacle square with minimal area. Algorithm 2, Pre-Drawn Virtual lines Relocation, pre-draws and rearranges all virtual lines representing areas where components can be arranged to avoid obstacles. The obtained simulation results showed that the proposed algorithm generated the maximum number of convex hull obstacle-aware tracking barriers, according to the given detection accuracy, the number of convex hull obstacles and the theme park size. The simulations were then performed by changing the setting or changing the components, and the performances compared to obtain a result. In future studies, we plan to investigate convex hull obstacle-aware tracking barrier generation in a three-dimensional environment, that is, 3D rather than 2D, and focus on developing further improvements in performance. The research issue of how to create optimal 3D barriers in 3D environments with numerous and variously shaped obstacles and hindrances is to be critically studied in future. We plan to find the optimal ratio between a group of mobile robots on the ground and a fleet of UAVs on the aerial side in three-dimensional theme park regions and smart complex spaces with numerous obstacles and hindrances when specific barrier construction is requested.
Author Contributions
Conceptualization, Y.C.; software, Y.C; validation, Y.C; investigation, Y.C. and H.K.; methodology, Y.C.; resources, Y.C.; data curation, Y.C.; writing–draft preparation, Y.C. and H.K.; writing–review and editing, H.K.; visualization, Y.C. and H.K.; supervision, H.K.; project administration, H.K.; funding acquisition, H.K. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Research Foundation of Korea(NRF) grant, funded by the Korea government(MSIT) (No. NRF-2021R1F1A1049213).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| UAVs | Unmanned Aerial Vehicles |
| ConvexAwareTheme | convex hull obstacle-aware tracking barriers |
References
- Geraci, G.; García-Rodríguez, A.; Azari, M.M.; Lozano, A.; Mezzavilla, M.; Chatzinotas, S.; Chen, Y.; Rangan, S.; Renzo, M.D. What will the future of UAV cellular communications be? A flight from 5G to 6G. IEEE Commun. Surv. Tutor. 2022, 24, 1304–1335. [Google Scholar] [CrossRef]
- Balkus, S.V.; Wang, H.; Cornet, B.D.; Mahabal, C.; Ngo, H.; Fang, H. A survey of collaborative machine learning using 5G vehicular communications. IEEE Commun. Surv. Tutor. 2023, 24, 1280–1303. [Google Scholar] [CrossRef]
- Xu, S.; Liu, J.; Kato, N.; Du, Y. Intelligent reflecting surface backscatter enabled multi-tier computing for 6G internet of things. IEEE J. Sel. Areas Commun. 2023, 41, 320–333. [Google Scholar] [CrossRef]
- Su, Y.; Gao, Z.; Du, X.; Guizani, M. User-centric base station clustering and resource allocation for cell-edge users in 6G ultra-dense networks. Future Gener. Comput. Syst. 2023, 141, 173–185. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Ding, M.; Pathirana, P.N.; Seneviratne, A.; Li, J.; Niyato, D.; Dobre, O.A.; Poor, H.V. 6G Internet of Things: A comprehensive survey. IEEE Internet Things J. 2022, 9, 359–383. [Google Scholar] [CrossRef]
- Abouaomar, A.; Taïk, A.; Filali, A.; Cherkaoui, S. Federated deep reinforcement learning for open RAN slicing in 6G networks. IEEE Internet Things J. 2023, 61, 126–132. [Google Scholar] [CrossRef]
- Taha, A.M.; Elabd, A. IoT for certified sustainability in smart buildings. IEEE Netw. 2023, 35, 241–247. [Google Scholar] [CrossRef]
- Xiu, H.; Gao, Z.; Liao, A.; Mei, Y.; Zheng, D.; Tan, S.; Renzo, M.D.; Hanzo, L. Joint activity detection and channel estimation for massive IoT access based on millimeter-wave/terahertz multi-panel massive MIMO. IEEE Trans. Veh. Technol. 2022, 72, 1349–1354. [Google Scholar] [CrossRef]
- Bugshan, N.; Khalil, I.; Rahman, M.S.; Atiquzzaman, M.; Yi, X.; Badsha, S. Toward trustworthy and privacy-preserving federated deep learning service framework for industrial internet of things. IEEE Trans. Ind. Inform. 2023, 19, 1535–1547. [Google Scholar] [CrossRef]
- Zhao, Y.; Liu, W.; Li, B.; Zhou, X.; Ning, Z.; Qiu, T.; Atiquzzaman, M. Entity and sociality trust-aware model for content distribution in social internet of vehicles. IEEE Trans. Veh. Technol. 2022, 71, 12511–12522. [Google Scholar] [CrossRef]
- Zhang, Q.; Wu, J.; Zanella, M.; Yang, W.; Bashir, A.K.; Fornaciari, W. Sema-IIoVT: Emergent semantic-based trustworthy information-centric fog system and testbed for intelligent internet of vehicles. IEEE Consum. Electron. Mag. 2023, 12, 70–79. [Google Scholar] [CrossRef]
- Hamdaoui, B.; Alkalbani, M.; Rayes, A.; Zorba, N. IoTShare: A blockchain-enabled IoT resource sharing on-demand protocol for smart city situation-awareness applications. IEEE Internet Things J. 2020, 7, 10548–10561. [Google Scholar] [CrossRef]
- Solmaz, G.; Turgut, D. Optimizing event coverage in theme parks. Wirel. Netw. 2014, 20, 1445–1459. [Google Scholar] [CrossRef]
- Solmaz, G.; Turgut, D. Pedestrian mobility in theme park disasters. IEEE Commun. Mag. 2015, 53, 172–177. [Google Scholar] [CrossRef]
- Filali, A.; Mlika, Z.; Cherkaoui, S.; Kobbane, A. Dynamic SDN-based radio access network slicing with deep reinforcement learning for URLLC and eMBB Services. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2174–2187. [Google Scholar] [CrossRef]
- Raja, G.; Senthivel, S.G.; Balaganesh, S.; Rajakumar, B.R.; Ravichandran, V.; Guizani, M. MLB-IoD: Multi Layered Blockchain Assisted 6G Internet of Drones Ecosystem. IEEE Trans. Veh. Technol. 2023, 72, 2511–2520. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Miridakis, N.I.; Michalas, A.; Skondras, E.; Vergados, D.J.; Vergados, D.V. Energy optimization in massive MIMO UAV-aided MEC-enabled vehicular networks. IEEE Access 2021, 9, 117388–117403. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Maliatsos, K.; Skoutas, D.N.; Vouyioukas, D.; Skianis, C. Secure UAV-aided mobile edge computing for IoT: A review. IEEE Access 2022, 10, 86353–86383. [Google Scholar] [CrossRef]
- Nomikos, N.; Michailidis, E.T.; Nomikos, N.; Trakadas, P.; Vouyioukas, D.; Karl, H.; Martrat, J.; Zahariadis, T.B.; Papadopoulos, K.; Voliotis, S. A UAV-based moving 5G RAN for massive connectivity of mobile users and IoT devices. Veh. Commun. 2020, 25, 100250. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Bithas, P.S.; Nomikos, N.; Vouyioukas, D.; Kanatas, A.G. Outage probability analysis in multi-user FSO/RF and UAV-enabled MIMO communication networks. Phys. Commun. 2021, 49, 101475. [Google Scholar] [CrossRef]
- Bithas, P.S.; Nikolaidis, V.; Kanatas, A.G.; Karagiannidis, G.K. UAV-to-Ground Communications: Channel Modeling and UAV Selection. IEEE Trans. Commun. 2020, 68, 5135–5144. [Google Scholar] [CrossRef]
- Armeniakos, C.K.; Bithas, P.S.; Kanatas, A.G. Finite point processes in a truncated octahedron-based 3D UAV network. IEEE Trans. Veh. Technol. 2022, 71, 7230–7243. [Google Scholar] [CrossRef]
- Liu, L.; Xiong, K.; Cao, J.; Lu, Y.; Fan, P.; Letaief, K.B. Average AoI minimization in UAV-assisted data collection with RF wireless power transfer: A deep reinforcement learning scheme. IEEE Internet Things J. 2022, 9, 5216–5228. [Google Scholar] [CrossRef]
- Hu, H.; Xiong, K.; Qu, G.; Ni, Q.; Fan, P.; Letaief, K.B. AoI-minimal trajectory planning and data collection in UAV-assisted wireless powered IoT networks. IEEE Internet Things J. 2021, 8, 1211–1223. [Google Scholar] [CrossRef]
- Inthizami, N.S.; Ma’sum, M.A.; Alhamidi, M.R.; Gamal, A.; Ardhianto, R.; Kurnianingsih; Jatmiko, W. Flood video segmentation on remotely sensed UAV using improved efficient neural network. ICT Express 2022, 8, 347–351. [Google Scholar] [CrossRef]
- Garcia, A.J.; Aouto, A.; Lee, J.-M.; Kim, D.-S. CNN-32DC: An improved radar-based drone recognition system based on convolutional neural network. ICT Express 2022, 8, 606–610. [Google Scholar] [CrossRef]
- Morocho-Cayamcela, M.E.; Lim, W.; Maier, M. An optimal location strategy for multiple drone base stations in massive MIMO. ICT Express 2022, 8, 230–234. [Google Scholar] [CrossRef]
- Zhang, S.; Liu, W.; Ansari, N. Joint wireless charging and data collection for UAV-enabled internet of things network. IEEE Internet Things J. 2022, 9, 23852–23859. [Google Scholar] [CrossRef]
- Hossain, M.A.; Hossain, A.R.; Ansari, N. Numerology-capable UAV-MEC for future generation massive IoT networks. IEEE Internet Things J. 2022, 9, 23860–23868. [Google Scholar] [CrossRef]
- Wang, X.; Yang, L.T.; Meng, D.; Dong, M.; Ota, K.; Wang, H. Multi-UAV cooperative localization for marine targets based on weighted subspace fitting in SAGIN environment. IEEE Internet Things J. 2022, 9, 5708–5718. [Google Scholar] [CrossRef]
- Zhang, T.; Zhu, K.; Zheng, S.; Niyato, D.; Luong, N.C. Trajectory design and power control for joint radar and communication enabled multi-UAV cooperative detection systems. IEEE Trans. Commun. 2023, 71, 158–172. [Google Scholar] [CrossRef]
- Wang, F.; Li, B.; Li, B. Quality-oriented federated learning on the fly. IEEE Netw. 2022, 36, 152–159. [Google Scholar] [CrossRef]
- Kim, H.; Ben-Othman, J.; Hwang, K.; Choi, B. Intelligent aerial-ground surveillance and epidemic prevention with discriminative public and private services. IEEE Netw. 2022, 36, 40–46. [Google Scholar] [CrossRef]
- Kim, H.; Ben-Othman, J.; Mokdad, L.; Son, J.; Li, C. Research challenges and security threats to AI-driven 5G virtual emotion applications using autonomous vehicles, drones, and smart devices. IEEE Netw. 2020, 34, 288–294. [Google Scholar] [CrossRef]
- Lee, S.; Lee, S.; Kim, H. Differential security barriers for virtual emotion detection in maritime transportation stations with cooperative mobile robots and UAVs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2461–2471. [Google Scholar] [CrossRef]
- Zhao, M.; Adib, F.; Katabi, D. Emotion recognition using wireless signals. Commun. ACM 2018, 61, 91–100. [Google Scholar] [CrossRef]
- Taha, A.M.; Ali, N.A. Monitoring a crowd’s affective state: Status quo and future outlook. IEEE Commun. Mag. 2019, 57, 26–32. [Google Scholar] [CrossRef]
- Kumar, S.; Lai, T.H.; Posner, M.E.; Sinha, P. Maximizing the lifetime of a barrier of wireless sensors. IEEE Trans. Mob. Comput. 2010, 9, 1161–1172. [Google Scholar] [CrossRef]
- Wang, Z.; Chen, H.; Cao, Q.; Qi, H.; Wang, Z.; Wang, Q. Achieving location error tolerant barrier coverage for wireless sensor networks. Comput. Netw. 2017, 112, 314–328. [Google Scholar] [CrossRef]
- Li, L.; Zhang, B.; Shen, X.; Zheng, J.; Yao, Z. A study on the weak barrier coverage problem in wireless sensor networks. Comput. Netw. 2011, 55, 711–721. [Google Scholar] [CrossRef]
- Malek, M.S.; Sadik, B.; Rahman, M.M. On balanced k-coverage in visual sensor networks. J. Netw. Comput. Appl. 2016, 72, 72–86. [Google Scholar] [CrossRef]
- Carrabs, F.; Cerulli, R.; D’Ambrosio, C.; Raiconi, A. A hybrid exact approach for maximizing lifetime in sensor networks with complete and partial coverage constraints. J. Netw. Comput. Appl. 2015, 58, 12–22. [Google Scholar] [CrossRef]
- Chen, A.; Zhu, Y.; Li, Z.; Lai, T.H.; Liu, C. Is one-way barrier coverage achievable using comprehensive sensors? Comput. Commun. 2015, 57, 100–114. [Google Scholar] [CrossRef]
- Li, W.; Zhang, W. Coverage hole and boundary nodes detection in wireless sensor networks. J. Netw. Comput. Appl. 2015, 48, 819–827. [Google Scholar] [CrossRef]
- Vecchio, M.; Lopez-Valcarce, R. Improving area coverage of wireless sensor networks via controllable mobile nodes: A greedy approach. J. Netw. Comput. Appl. 2015, 48, 1–13. [Google Scholar] [CrossRef]
- Kim, H.; Ben-Othman, J. FAMU: Fault-tolerant mutual assisted virtual emotion barrier system using intelligent smart UAVs. IEEE Trans. Veh. Technol. 2021, 70, 10845–10852. [Google Scholar] [CrossRef]
- Kloder, S.; Hutchinson, S. Barrier coverage for variable bounded-range line-of sight guard. In Proceedings of the IEEE International Conference on Robotics and Automation, Rome, Italy, 10–14 April 2007; pp. 391–396. [Google Scholar]
- Bhattacharya, B.; Burmester, M.; Hu, Y.; Kranakis, E.; Shi, Q.; Wiese, A. Optimal movement of mobile sensors for barrier coverage of a planar region. Theor. Comput. Sci. 2009, 410, 5515–5528. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Li, X.; Shen, X.; Sun, Y. Cost-effective barrier coverage by mobile sensor networks. In Proceedings of the IEEE Annual International Conference on Computer Communications (INFOCOM), Orlando, FL, USA, 25–30 March 2012; pp. 819–827. [Google Scholar]
- Shen, J.; Wang, Z.; Wang, Z. Fault tolerant line-based barrier coverage formation in mobile wireless sensor networks. Int. J. Distrib. Sens. Netw. 2015. [Google Scholar] [CrossRef]
- Saipulla, A.; Liu, B.; Xing, G.; Fu, X.; Wang, J. Barrier coverage with sensors of limited mobility. In Proceedings of the ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc), Chicago, IL, USA, 20–24 September 2010; pp. 201–210. [Google Scholar]
- Kong, L.; Liu, X.; Li, Z.; Wu, M. Automatic barrier coverage formation with mobile sensor networks. In Proceedings of the ACM IEEE International Conference on Communications (ICC), Cape Town, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar]
- Dobrev, S.; Durocher, S.; Eftekhari, M.; Georgiou, K.; Kranakis, E.; Krizanc, D.; Narayanan, L.; Opatrny, J.; Shende, S.; Urrutia, J. Complexity of barrier coverage with relocatable sensors in the plane. Theor. Comput. Sci. 2015, 579, 64–73. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).