Open Collaborative Platform for Multi-Drones to Support Search and Rescue Operations
Abstract
:1. Introduction
2. Related Works
3. Open Collaborative Platform
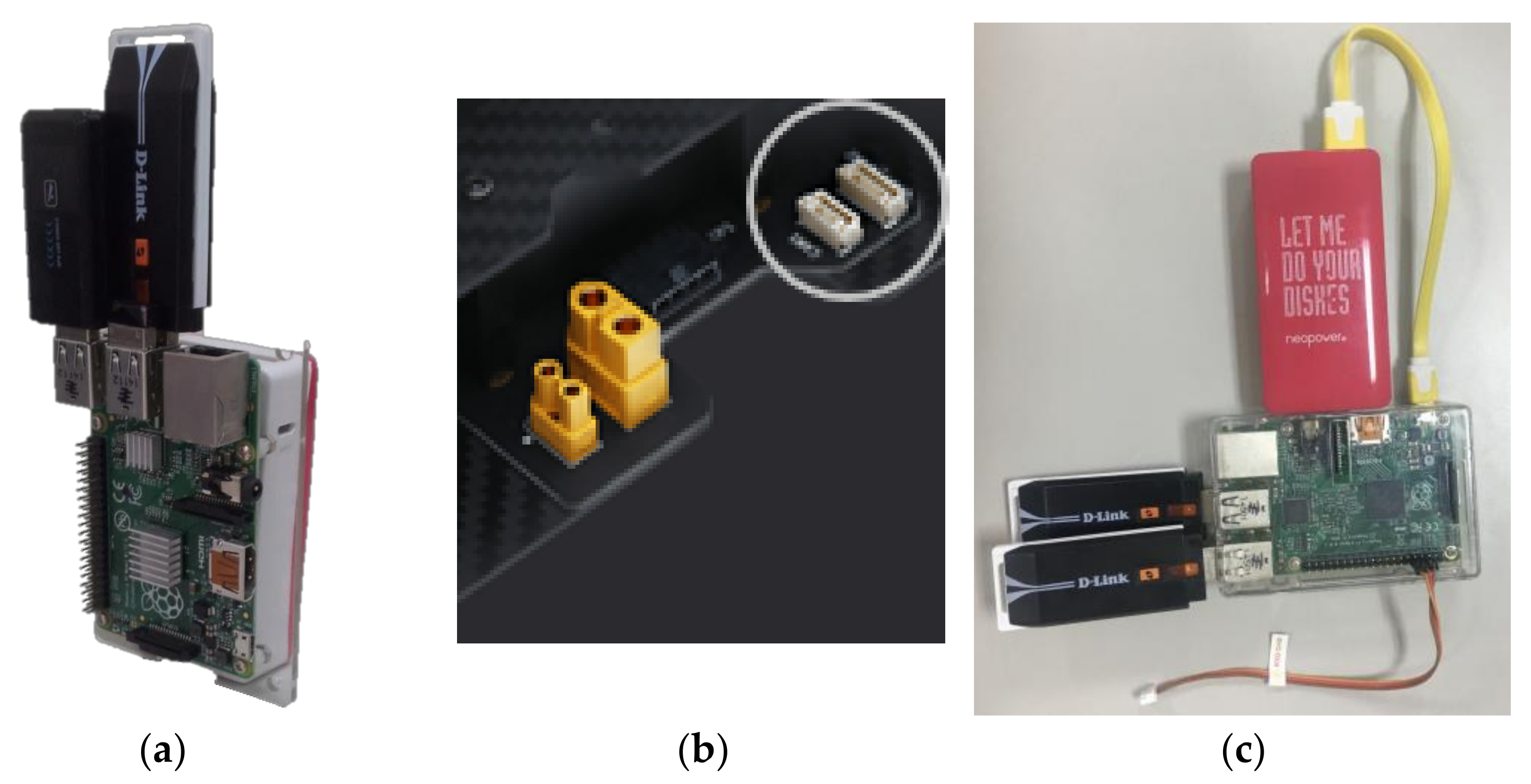
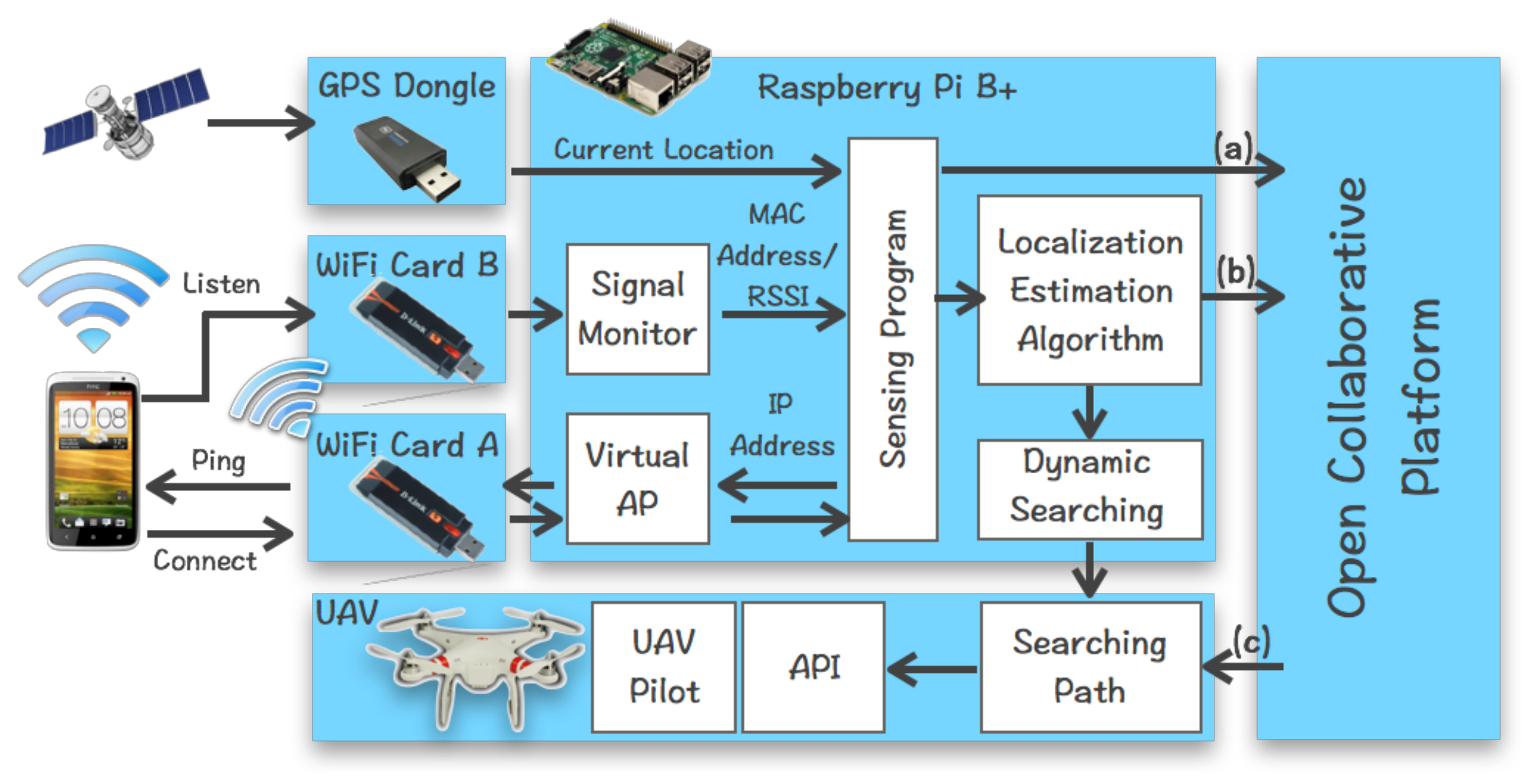
3.1. Krypto Module
3.2. Open Collaborative Platform for Multiple Drones
3.2.1. Register Drone to the Open Platform
3.2.2. Communication between Krypto and Open Platform
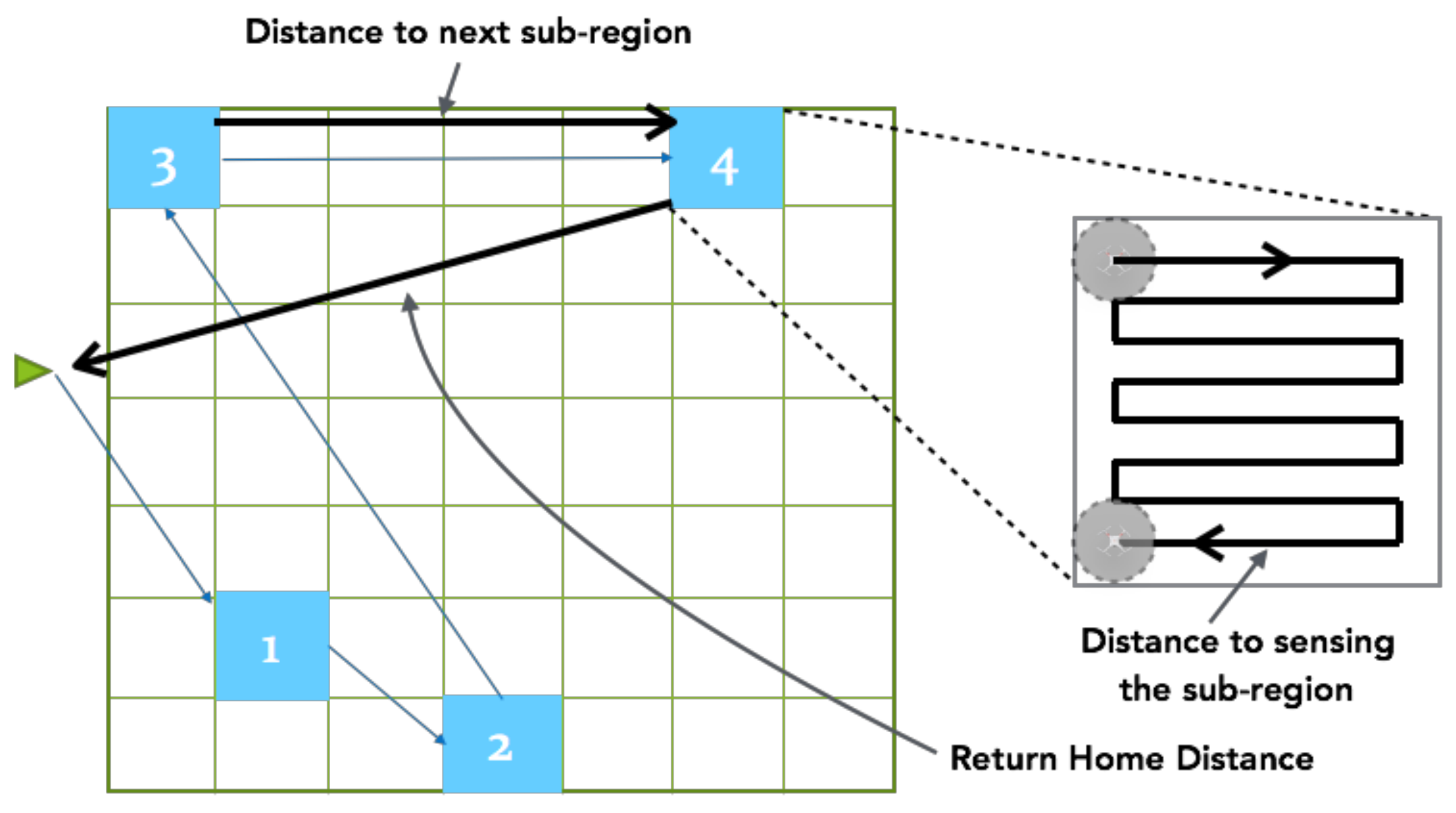
3.3. Collaborative Searching Path Planning
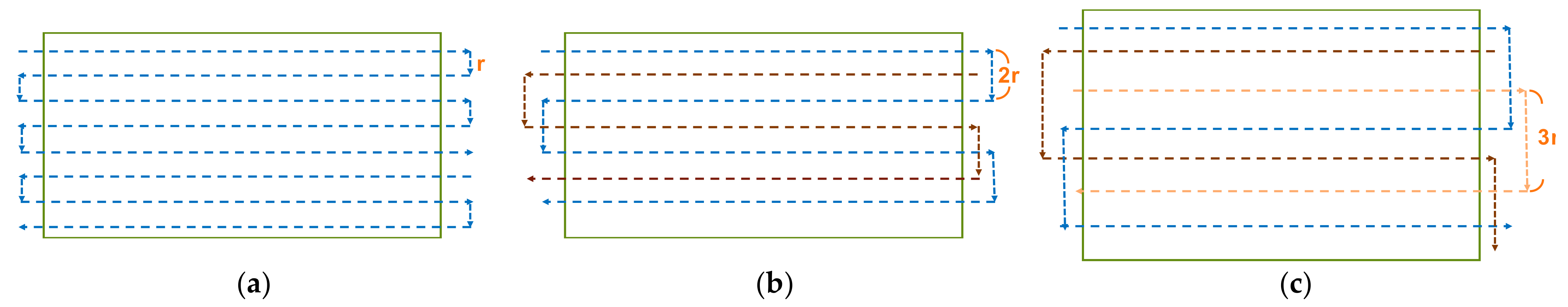
3.3.1. Searching Path Planning
3.3.2. Join or Rejoin SAR Operation
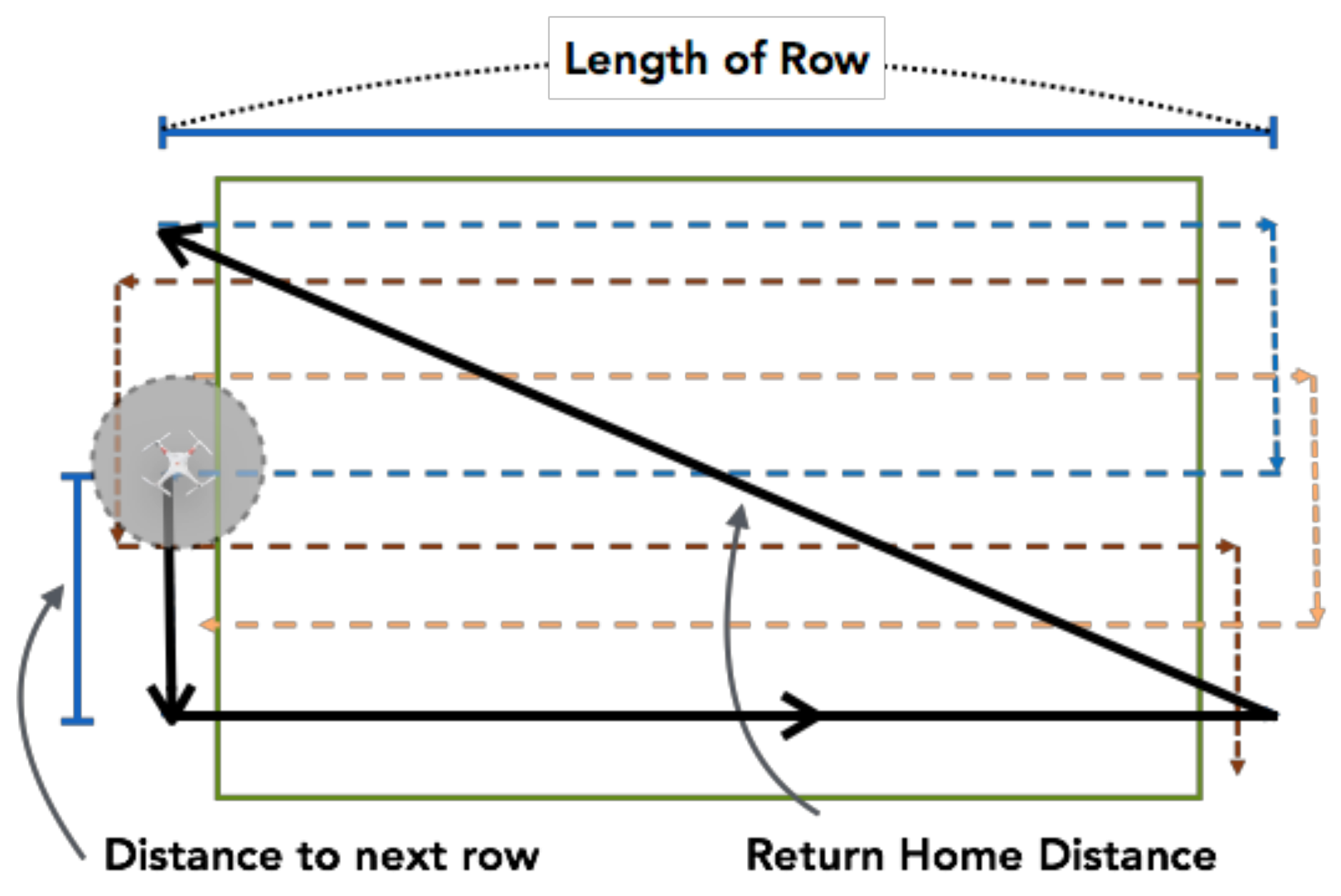
3.3.3. Return-to-Home
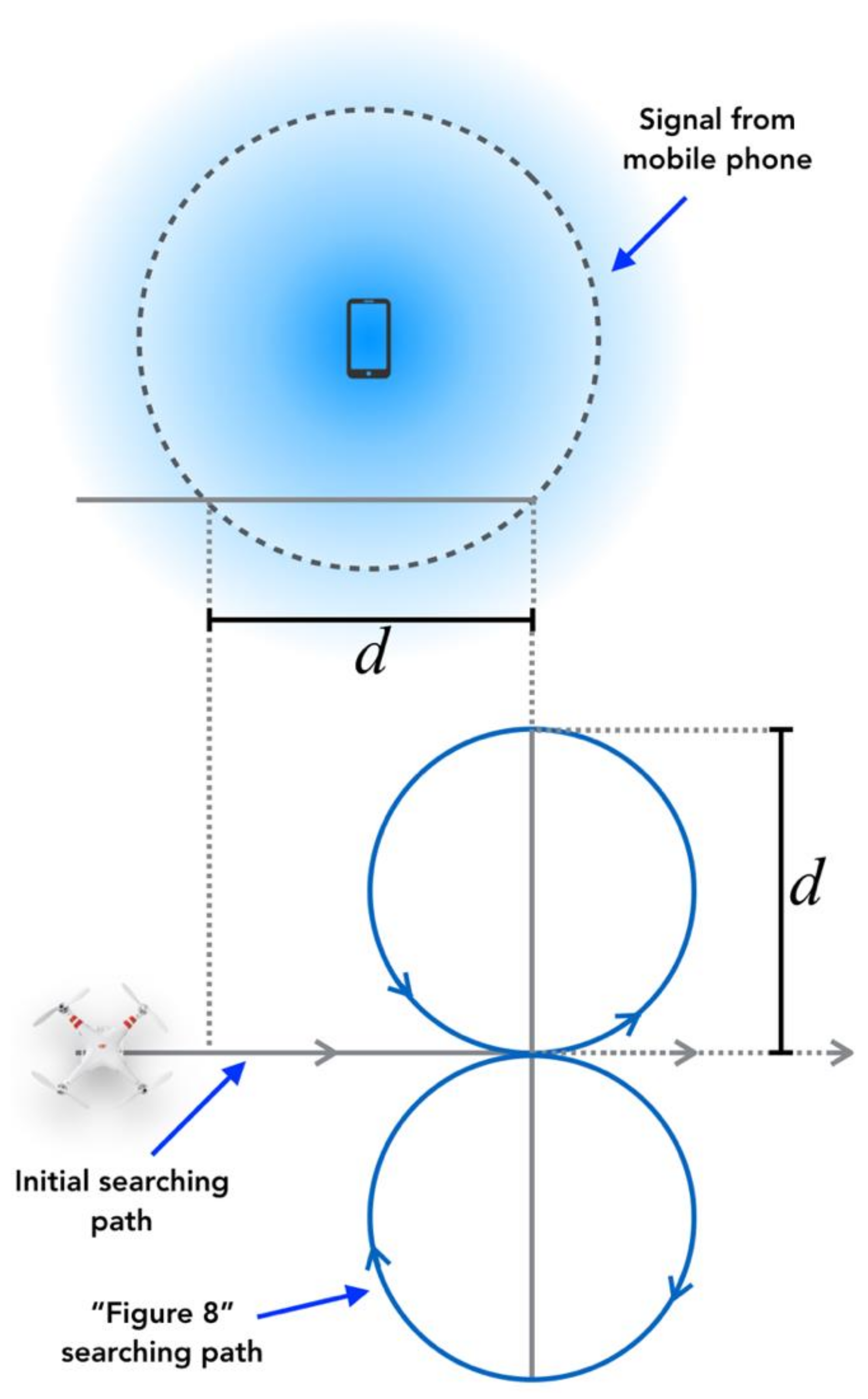
3.3.4. Dynamic Searching Path
4. Performance Evaluation
4.1. Field Experiments
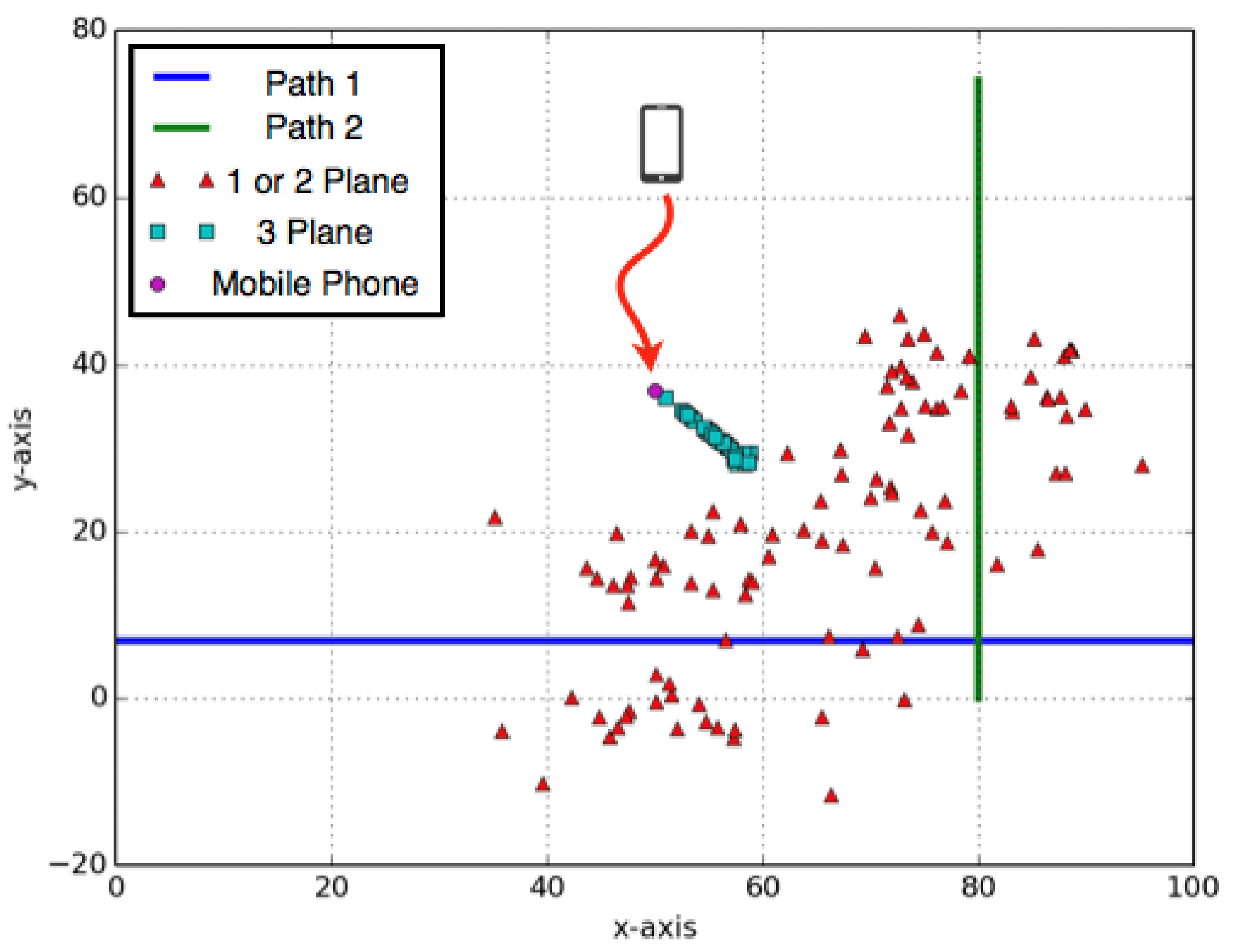
4.1.1. Verify Settings for Location Estimation
4.1.2. Effect on Accuracy of Location Estimation with Dynamic Searching Path
4.2. Simulation Study
4.2.1. Settings
4.2.2. Implemented Schemes
- In the Random approach, all drones moved in a random waypoint mobility model in which a random destination was selected. The drone moved to the selected destination before another random destination was selected.
- In the Centralized approach, all drones followed an assigned searching path (i.e., a sweeping curve that staggered with each other) from the Open Collaborative Platform.
- In the Distributed approach, each drone randomly selected a sub-region and searched the selected sub-region using a sweeping curve. Each sub-region was 200 m by 200 m. When a drone finished searching the selected sub-region, it randomly selected another sub-region and searched the subsequently selected sub-region.
- In the Hybrid approach, all drones can exchange information about searched sub-regions by themselves or with other drones. Two drones can exchange information when they were within 50 m of each other. With the exchanged information, drones avoided selecting those already searched sub-regions.
4.2.3. Results on Number of Drones vs. Coverage Area
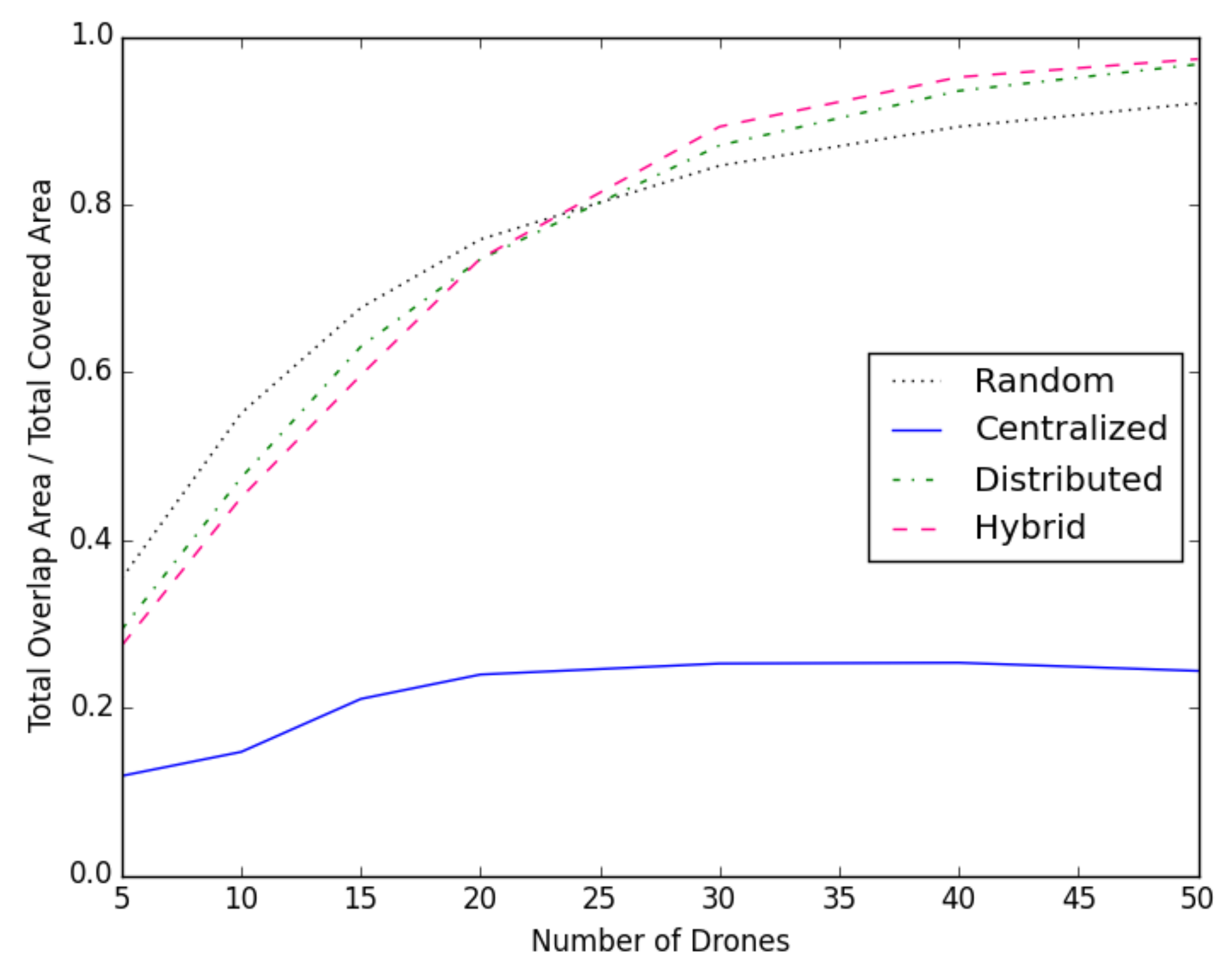
4.2.4. Results on Number of Drone vs. Overlapping Area
4.2.5. Effectiveness of Each Approach vs. Number of Drones
4.2.6. Results on Average Searching Time
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Centre for Research on the Epidemiology of Disasters, “Disaster Year in Review 2020”. Available online: https://cred.be/sites/default/files/CredCrunch65.pdf (accessed on 12 April 2022).
- World Health Organization (WHO). Wildfires. Available online: https://www.who.int/health-topics/wildfires#tab=tab_1 (accessed on 12 April 2022).
- National Science Foundation (NSF). Hurricane Katrina Small, Unmanned Aircraft Search for Survivors in Katrina Wreckage. 2005. Available online: http://www.nsf.gov/news/news_summ.jsp?cntn_id=104453 (accessed on 12 April 2022).
- Ho, Y.-H.; Chen, Y.-R.; Chen, L.-J. Krypto: Assisting Search and Rescue Operations using Wi-Fi Signal with UAV. In ACM International Workshop on Micro Aerial Vehicle Networks, Systems, and Applications for Civilian Use; DroNet: Florence, Italy, 2015. [Google Scholar]
- Ho, Y.-H.; Chen, Y.-R. Krypto Source Code. Available online: https://github.com/NTNUNSL/WIFILocatedDrone (accessed on 12 April 2022).
- DJI Onboard SDK. Available online: https://developer.dji.com/onboard-sdk/documentation/ (accessed on 15 May 2021).
- DJI Mobile SDK. Available online: https://developer.dji.com/mobile-sdk/documentation/ (accessed on 15 May 2021).
- Federal Aviation Administration “Drones by the Numbers”. Available online: https://www.faa.gov/uas/resources/by_the_numbers/ (accessed on 12 April 2022).
- National Association for Search and Rescue. Available online: http://nasar.org (accessed on 12 April 2022).
- Life Locator Geophysical Survey Systems. Available online: https://www.geophysical.com/products/lifelocator-trx (accessed on 19 May 2022).
- LEADER Search and Rescue Equipment. Available online: http://www.leadernorthamerica.com (accessed on 19 May 2022).
- Cisco Annual Internet Report (2018–2023) White Paper. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html (accessed on 12 April 2022).
- Ni, L.M.; Liu, Y.; Lau, Y.C.; Patil, A.P. LANDMARC: Indoor location sensing using active RFID. Wirel. Netw. 2004, 10, 701–710. [Google Scholar] [CrossRef]
- Niculescu, D.; Nath, B. VOR base stations for indoor 802.11 positioning. In Proceedings of the 10th Annual International Conference on Mobile Computing and Networking, Philadelphia, PA, USA, 26 September 2004; pp. 58–69. [Google Scholar]
- Priyantha, N.B.; Chakraborty, A.; Balakrishnan, H. The cricket location-support system. In Proceedings of the ACM MobiCom, Boston, MA, USA, 1 August 2000; pp. 32–43. [Google Scholar]
- Want, R.; Hopper, A.; Falcão, V.; Gibbons, J. The active badge location system. ACM Trans. Inf. Syst. (TOIS) 1992, 10, 91–102. [Google Scholar] [CrossRef]
- Youssef, M.; Youssef, A.; Rieger, C.; Shankar, U.; Agrawala, A. Pinpoint: An asynchronous time-based location determination system. In Proceedings of the ACM MobiSys, Uppsala, Sweden, 19 June 2006; pp. 165–176. [Google Scholar]
- Azizyan, M.; Constandache, I.; Roy Choudhury, R. Surroundsense: Mobile phone localization via ambience fingerprinting. In Proceedings of the 15th Annual International Conference on Mobile Computing and Networking, Uppsala, Sweden, 20 September 2009; pp. 261–272. [Google Scholar]
- Bahl, P.; Padmanabhan, V.N. RADAR: An in- building RF-based user location and tracking system. In Proceedings of the IEEE INFOCOM, Tel Aviv, Israel, 26–30 March 2000; Volume 2, pp. 775–784. [Google Scholar]
- Bhasker, E.S.; Brown, S.W.; Griswold, W.G. Employing User Feedback for Fast, Accurate, Low- Maintenance Geolocationing. In Proceedings of the IEEE PerCom, Los Alamitos, CA, USA, 17 March 2004; pp. 111–120. [Google Scholar]
- Cheng, Y.C.; Chawathe, Y.; LaMarca, A.; Krumm, J. Accuracy characterization for metropolitan-scale Wi-Fi localization. In Proceedings of the ACM MobiSys, Seattle, WA, USA, 6 June 2005; pp. 233–245. [Google Scholar]
- Griswold, W.G.; Shanahan, P.; Brown, S.W.; Boyer, R.; Ratto, M.; Shapiro, R.B.; Truong, T.M. ActiveCampus: Experiments in community-oriented ubiquitous computing. Computer 2004, 37, 73–81. [Google Scholar] [CrossRef]
- Park, J.; Charrow, B.; Curtis, D.; Battat, J.; Minkov, E.; Hicks, J.; Teller, S.; Ledlie, J. Growing an organic indoor location system. In Proceedings of the ACM MobiSys, San Francisco, CA, USA, 15 June 2010; pp. 271–284. [Google Scholar]
- Varshavsky, A.; de Lara, E.; Hightower, J.; LaMarca, A.; Otsason, V. GSM indoor localization. Pervasive Mob. Comput. 2007, 3, 698–720. [Google Scholar] [CrossRef] [Green Version]
- Youssef, M.; Agrawala, A. The Horus WLAN location determination system. Wirel. Netw. 2008, 14, 357–374. [Google Scholar] [CrossRef]
- Chintalapudi, K.; Padmanabha Iyer, A.; Padmanabhan, V.N. Indoor localization without the pain. In Proceedings of the ACM MobiCom, Chicago, IL, USA, 20–24 September 2010; pp. 173–184. [Google Scholar]
- Ji, Y.; Biaz, S.; Pandey, S.; Agrawal, P. ARIADNE: A dynamic indoor signal map construction and localization system. In Proceedings of the ACM MobiSys, Uppsala, Sweden, 19–22 June 2006; pp. 151–164. [Google Scholar]
- Jiang, J.; Han, G.; Xu, H.; Shu, L.; Guizani, M. LMAT: Localization with a Mobile Anchor Node Based on Trilateration in Wireless Sensor Networks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM), Houston, TX, USA, 5–9 December 2011. [Google Scholar]
- Lim, H.; Kung, L.C.; Hou, J.C.; Luo, H. Zero- configuration indoor localization over IEEE 802.11 wireless infrastructure. Wirel. Netw. 2010, 16, 405–420. [Google Scholar] [CrossRef]
- Madigan, D.; Einahrawy, E.; Martin, R.P.; Ju, W.H.; Krishnan, P.; Krishnakumar, A.S. Bayesian indoor positioning systems. In Proceedings of the IEEE INFOCOM, Miami, FL, USA, 13–17 March 2005; Volume 2, pp. 1217–1227. [Google Scholar]
- Sahu, P.K.; Wu, E.H.-K.; Sahoo, J. DuRT: Dual RSSI trend based localization for wireless sensor networks. IEEE Sens. J. 2013, 13, 3115–3123. [Google Scholar] [CrossRef]
- Hara, S.; Anzai, D.; Yabu, T.; Kyesan, L.; Derham, T.; Zemek, R. A Perturbation Analysis on the Performance of TOA and TDOA Localization in Mixed LOS/NLOS Environments. IEEE Transl. Commun. 2013, 6, 679–680. [Google Scholar] [CrossRef]
- Kotwal, S.B.; Verma, S.; Sharma, A. Region based collaborative Angle of Arrival localization for wireless sensor networks with maximum range information. In Proceedings of the Computational Intelligence and Communication Networks (CICN), Bhopal, India, 26–28 November 2010. [Google Scholar]
- Weiss, A.J.; Picard, J.S. Maximum likelihood localization of wireless networks using biased range measurements. In Proceedings of the IEEE International Symposium on Communications and Information Technologies (ISCIT), Sydney, NSW, Australia, 17–19 October 2007. [Google Scholar]
- Will, H.; Hillebrandt, T.; Yuan, Y.; Yubin, Z.; Kyas, M. The Membership Degree Min-Max Localization Algorithm. In Proceedings of the IEEE Ubiquitous Positioning, Indoor Navigation and Location Based Service (UPINLBS), Helsinki, Finland, 3–4 October 2012. [Google Scholar]
- DJI Flight Planning Unlock. Available online: http://www.dji.com/zh-tw/flysafe/custom-unlock (accessed on 15 May 2021).
- Arce, G.R. Nonlinear Signal Processing: A Statistical Approach; Wiley: Hoboken, NJ, USA, 2005. [Google Scholar]
- DJI Ground Station. Available online: http://www.dji.com/product/pc-ground-station/feature (accessed on 15 May 2021).
- Buchin, K. Organizing Point Set. Ph.D. Thesis, Fachbereich Mathematik und Informatik der Freien Universitat, Berlin, Germany, 2007. Available online: http://www.mi.fu-berlin.de/inf/groups/ag-ti/theses/phd_finished/buchin_kevin/index.html (accessed on 12 April 2022).
- Araujo, J.F.; Sujit, P.B.; Sousa, J.B. Multiple UAV area decomposition and coverage. In Proceedings of the Symposium on Computational Intelligence for Security and Defense Applications (CISDA), Singapore, 16–19 April 2013. [Google Scholar]
- Maza, I.; Ollero, A. Multiple UAV cooperative searching operation using polygon area decomposition and efficient coverage algorithms. In Distributed Autonomous Robotic Systems 6; Springer: Tokyo, Japan, 2007; pp. 221–230. [Google Scholar]
- Mehdizade, M. A Decomposition Strategy for Optimal Coverage of an Area of Interest Using Heterogeneous Team of UAVs. Master’s Thesis, Concordia University, Montreal, QC, Canada, 2012; pp. 77–100. [Google Scholar]
- Chen, L.-J.; Huang, J.-H.; Chen, Y.-Y.; Tung, L.-P. Using Known Vectors to Improve Data Dissemination in Opportunistic Networks. Int. J. Ad Hoc Ubiquitous Comput. Indersci. 2014, 17, 59–69. [Google Scholar]
- Ho, Y.-H.; Ho, A.-H.; Hua, K.A. Routing Protocols for Inter-Vehicular Networks: A Comparative Study in High-Mobility and Large Obstacles Environments. Comput. Commun. J. 2008, 31, 2767–2780. [Google Scholar] [CrossRef]
- Huang, Y.-T.; Ho, Y.-H.; Chu, H.-H.; Chen, L.-J. Adaptive Drone Sensing with Always Return-To-Home Guaranteed. In Proceedings of the 1st International Workshop on Experiences with the Design and Implementation of Smart Objects, Paris, France, 7 September 2015. [Google Scholar]















Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ho, Y.-H.; Tsai, Y.-J. Open Collaborative Platform for Multi-Drones to Support Search and Rescue Operations. Drones 2022, 6, 132. https://doi.org/10.3390/drones6050132
Ho Y-H, Tsai Y-J. Open Collaborative Platform for Multi-Drones to Support Search and Rescue Operations. Drones. 2022; 6(5):132. https://doi.org/10.3390/drones6050132
Chicago/Turabian StyleHo, Yao-Hua, and Yu-Jung Tsai. 2022. "Open Collaborative Platform for Multi-Drones to Support Search and Rescue Operations" Drones 6, no. 5: 132. https://doi.org/10.3390/drones6050132
APA StyleHo, Y.-H., & Tsai, Y.-J. (2022). Open Collaborative Platform for Multi-Drones to Support Search and Rescue Operations. Drones, 6(5), 132. https://doi.org/10.3390/drones6050132






