UAS Traffic Management Communications: The Legacy of ADS-B, New Establishment of Remote ID, or Leverage of ADS-B-Like Systems?
Abstract
:1. Introduction
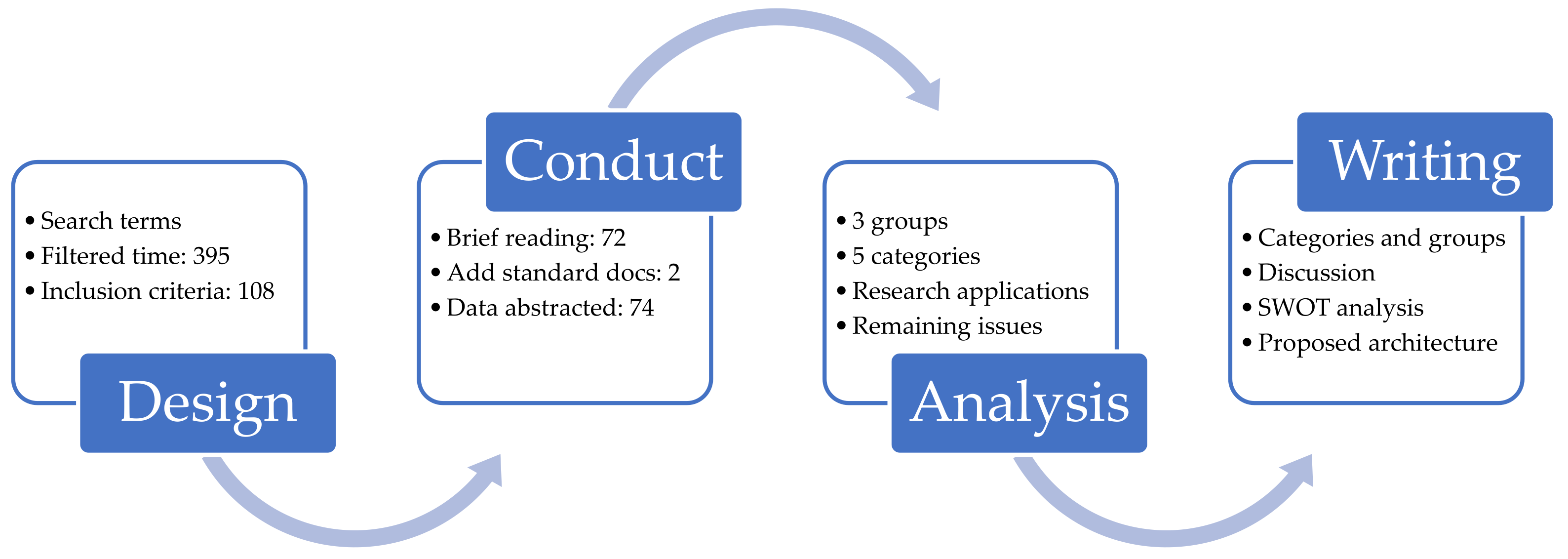
2. Review Methodology
2.1. Designing the Review
- -
- “ADS-B” and (UAS, UAV, or UTM)
- -
- “Remote ID” and (UAS, UAV, or UTM)
- -
- (UAS or UAV) and (Communication or Cellular)
2.2. Conducting the Review
2.3. Qualitative Analysis
2.4. Structure and Writing the Review
3. Result of Review
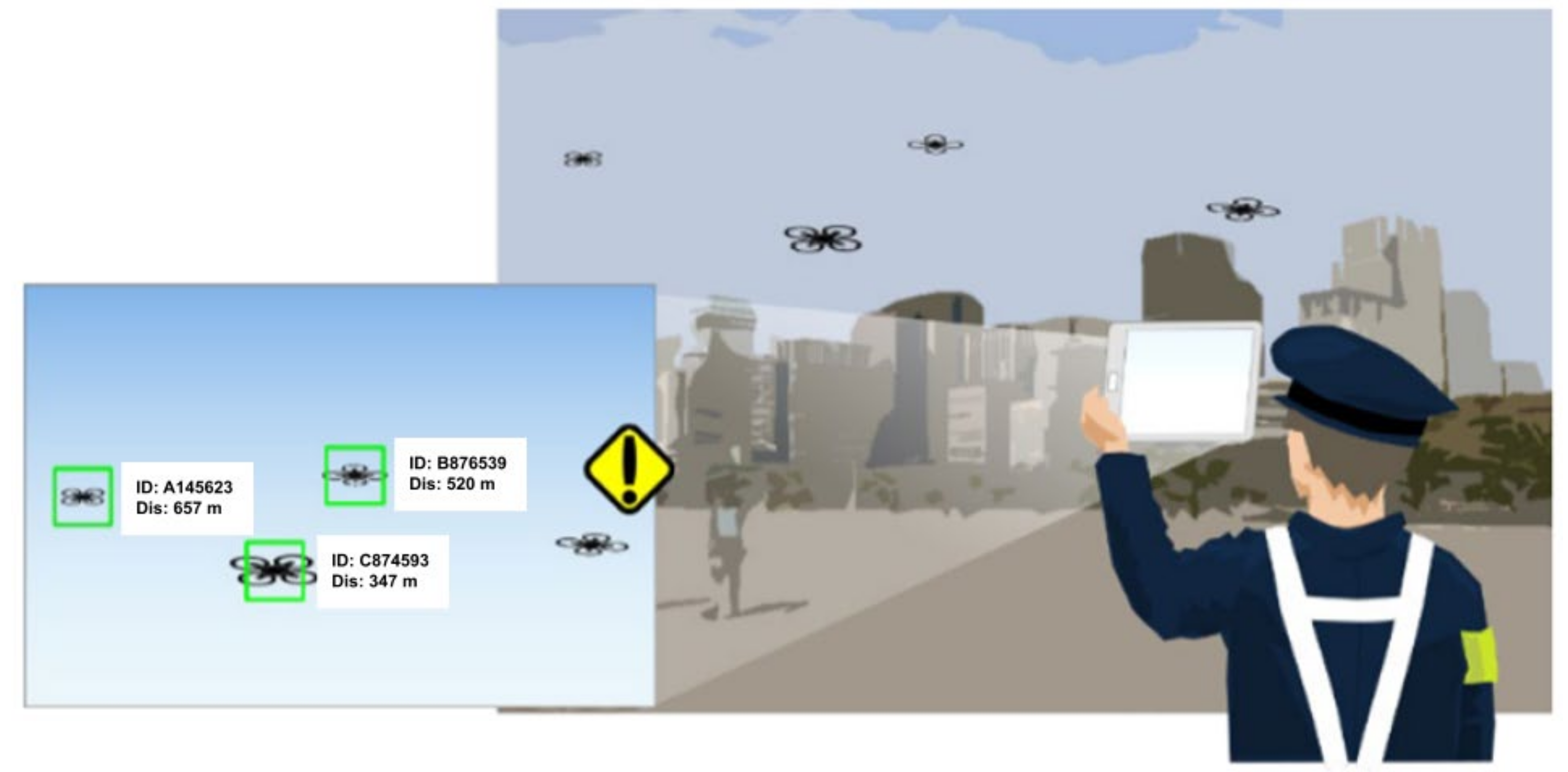
3.1. Definition
3.2. Data Format
- -
- UAS owner identification and its contact.
- -
- Properties of the vehicle including aircraft type, such as fixed-wing, quadcopter, etc.
- -
- Current flight plan, vehicle heading, speed, and future operations.
- -
- UTM status of the current flight plan, such as rogue, non-conforming, etc.
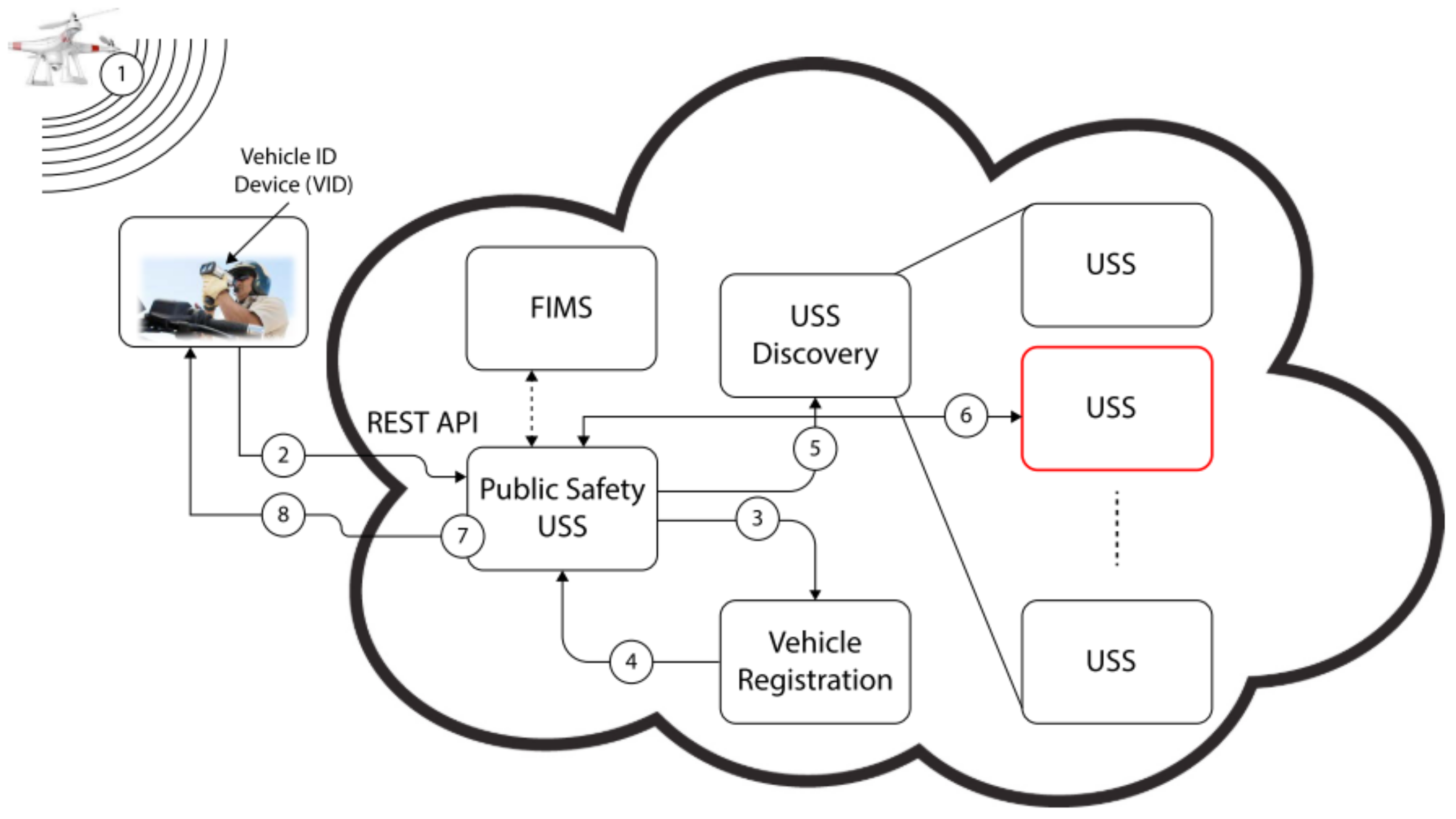
3.3. Technology
3.4. Research Applications
3.4.1. ADS-B Research
3.4.2. ADS-B-Like Research
3.4.3. Remote ID Research
3.5. Remaining Issues
3.5.1. Security
3.5.2. Safety
3.5.3. Communication
3.5.4. Surveillance
4. Discussion
4.1. SWOT Analysis
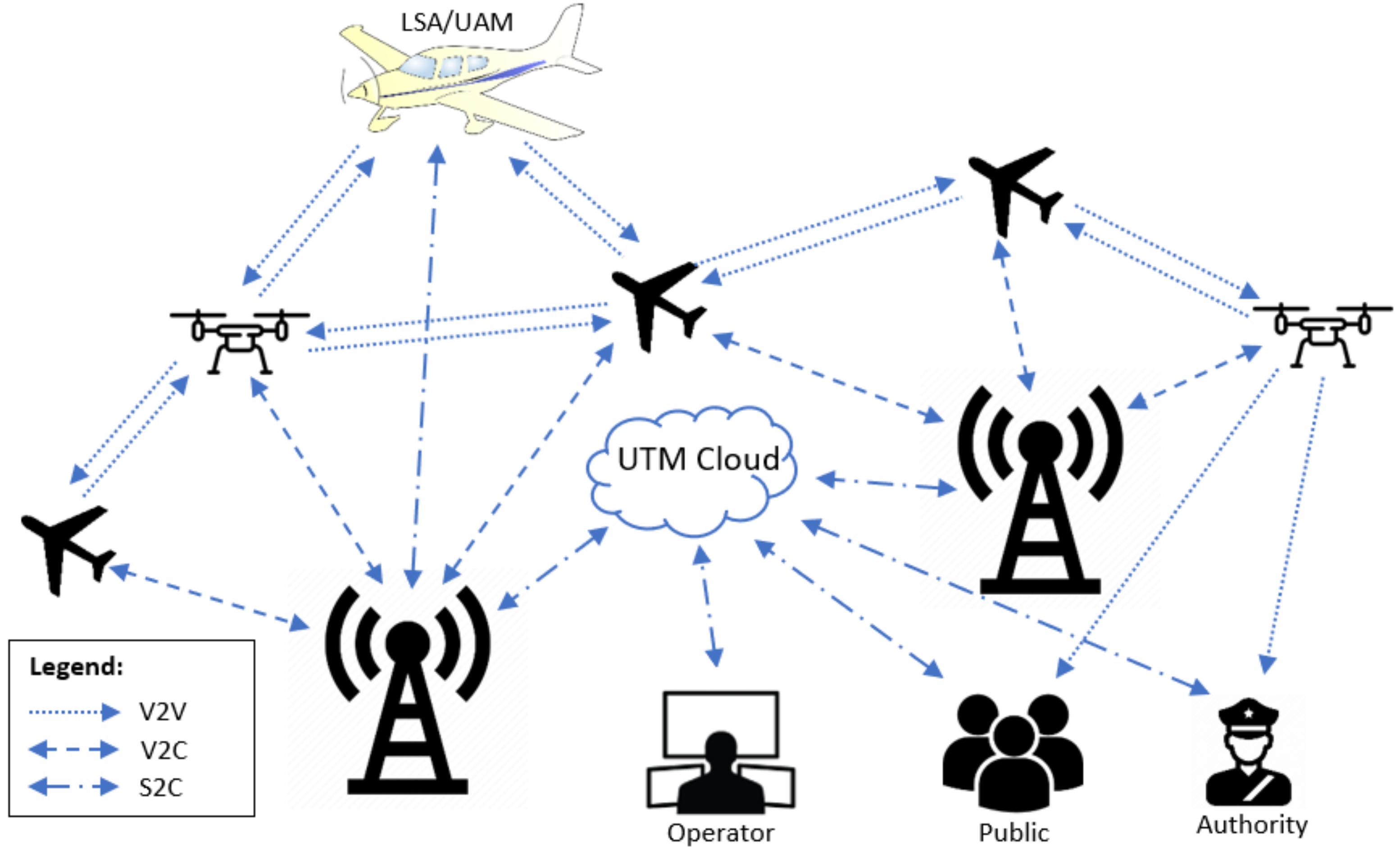
4.2. UTM Multi-Channels Communication
5. Conclusions and Recommendation
Author Contributions
Funding
Conflicts of Interest
References
- Constantine, D. The Future of the Drone Economy. 2020. Available online: https://levitatecap.com/levitate/wp-content/uploads/2020/12/White-Paper-v4.pdf (accessed on 8 July 2021).
- ResearchAndMarkets.com. Global UAS Traffic Management (UTM) System Market 2021–2031: System Architecture, Use Cases, Enabling Technologies and Country-Wise UTM Concepts. Business Wire. 2021. Available online: https://www.businesswire.com (accessed on 8 July 2021).
- Snyder, H. Literature review as a research methodology: An overview and guidelines. J. Bus. Res. 2019, 104, 333–339. [Google Scholar] [CrossRef]
- Carrio, A.; Lin, Y.; Saripalli, S.; Campoy, P. Obstacle Detection System for Small UAVs using ADS-B and Thermal Imaging. J. Intell. Robot. Syst. 2017, 88, 583–595. [Google Scholar] [CrossRef]
- Kim, Y.; Jo, J.-Y.; Lee, S. ADS-B vulnerabilities and a security solution with a timestamp. IEEE Aerosp. Electron. Syst. Mag. 2017, 32, 52–61. [Google Scholar] [CrossRef]
- Pan, Y.; Li, S.; Li, B.; Bhargav, B.; Ning, Z.; Han, Q.; Zhu, T. When UAVs coexist with manned airplanes: Large-scale aerial network management using ADS-B. Trans. Emerg. Telecommun. Technol. 2019, 30, e3714. [Google Scholar] [CrossRef]
- Languell, Z.P.; Gu, Q. Securing ADS-B with Multi-Point Distance-Bounding for UAV Collision Avoidance. In Proceedings of the 2019 IEEE 16th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Monterey, CA, USA, 4–7 November 2019; pp. 145–153. [Google Scholar]
- Orrell, G.L.; Chen, A.; Reynolds, C.J. Small unmanned aircraft system (SUAS) automatic dependent surveillance-broadcast (ADS-B) like surveillance concept of operations: A path forward for small UAS surveillance. In Proceedings of the 2017 IEEE/AIAA 36th Digital Avionics Systems Conference (DASC), St. Petersburg, FL, USA, 17–21 September 2017; Volume 2017. [Google Scholar] [CrossRef]
- Azari, M.M.; Geraci, G.; Garcia-Rodriguez, A.; Pollin, S. Cellular UAV-to-UAV Communications. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; Volume 2019. [Google Scholar] [CrossRef] [Green Version]
- Hosseini, N.; Jamal, H.; Haque, J.; Magesacher, T.; Matolak, D.W. UAV Command and Control, Navigation and Surveillance: A Review of Potential 5G and Satellite Systems. In Proceedings of the 2019 IEEE Aerospace Conference, Big Sky, MT, USA, 2–9 March 2019; Volume 2019, pp. 1–10. [Google Scholar] [CrossRef] [Green Version]
- Minucci, F.; Vinogradov, E.; Pollin, S. Avoiding Collisions at Any (Low) Cost: ADS-B Like Position Broadcast for UAVs. IEEE Access 2020, 8, 121843–121857. [Google Scholar] [CrossRef]
- Ghubaish, A.; Salman, T.; Jain, R. Experiments with a LoRaWAN-Based Remote ID System for Locating Unmanned Aerial Vehicles (UAVs). Wirel. Commun. Mob. Comput. 2019, 2019, 1–11. [Google Scholar] [CrossRef] [Green Version]
- Murrell, E.; Walker, Z.; King, E.; Namuduri, K. Remote ID and Vehicle-to-Vehicle Communications for Unmanned Aircraft System Traffic Management. Res. Adv. Technol. Digit. Libr. 2020, 12574, 194–202. [Google Scholar] [CrossRef]
- Kubo, D.; Osedo, A.; Yasui, I. Low Altitude Situational Awareness Enhancement using Remote ID Broadcasted from small UAS. In AIAA AVIATION 2020 FORUM; American Institute of Aeronautics and Astronautics: Reston, VA, USA, 2020; Volume 1, pp. 6–13. [Google Scholar]
- International Civil Aviation Organisation. ADS-B Implementation and Operations Guidance Document; International Civil Aviation Organisation: Montreal, QC, Canada, 2020; Volume 13. [Google Scholar]
- An ADS-B Like Communication for UTM. In Proceedings of the 2019 Integrated Communications, Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 9–11 April 2019; Volume 2019, pp. 1–12. [CrossRef]
- Lin, Y.-H.; Lin, C.E.; Chen, H.-C. ADS-B Like UTM Surveillance Using APRS Infrastructure. Aerospace 2020, 7, 100. [Google Scholar] [CrossRef]
- ASTM F3411-19; Standard Specification for Remote ID and Tracking; ASTM International: West Conshohocken, PA, USA, 2020.
- Ishihara, A.K.; Rios, J.; Venkatesan, P. Remote UAS ID for Rapid Assessment of Flight and Vehicle Information. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019. [Google Scholar] [CrossRef] [Green Version]
- Duffield, M.; McLain, T.W. A Well Clear Recommendation for Small UAS in High-Density, ADS-B-Enabled Airspace. In Proceedings of the AIAA Information Systems-AIAA Infotech@Aerospace, Grapevine, TX, USA, 9–13 January 2017. [Google Scholar] [CrossRef] [Green Version]
- Sherman, T.; Elemy, T.; Retherford, M.; Cady, T.; Bhandari, S. Collision Avoidance System for Fixed-Wing UAVs using Ping-2020 ADS-B Transreceivers. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019; American Institute of Aeronautics and Astronautics (AIAA): Reston, VA, USA, 2019; pp. 1–9. [Google Scholar]
- Bhandari, S.; Curtis-Brown, N.; Guzman, I.; Sherman, T.; Tellez, J.; Gomez, E. UAV Collision Detection and Avoidance using ADS-B Sensor and Custom ADS-B Like Solution. In Proceedings of the AIAA Information Systems-AIAA Infotech@Aerospace, Grapevine, TX, USA, 9–13 January 2017; pp. 1–12. [Google Scholar] [CrossRef]
- Mozaffari, M.; Lin, X.; Hayes, S. Toward 6G with Connected Sky: UAVs and Beyond. IEEE Commun. Mag. 2021, 59, 74–80. [Google Scholar] [CrossRef]
- Tang, X.-M.; Chen, J.-D.; Li, T. Unmanned aerial vehicle trajectory data fusion based on an active and passive feedback system. Proc. Inst. Mech. Eng. Part G J. Aerosp. Eng. 2019, 234, 887–895. [Google Scholar] [CrossRef]
- Zhang, H.; Yan, Y.; Li, S.; Hu, Y.; Liu, H. UAV Behavior-Intention Estimation Method Based on 4-D Flight-Trajectory Prediction. Sustainability 2021, 13, 12528. [Google Scholar] [CrossRef]
- Lum, C.W.; Rotta, H.; Patel, R.; Kuni, H.; Patana-Anake, T.; Longhurst, J.; Chen, K. UAS Operation and Navigation in GPS-Denied Environments Using Multilateration of Aviation Transponders. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019. [Google Scholar] [CrossRef]
- Duffy, B.; Glaab, L. Variable-power ADS-B for UAS. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Palenska, M.; Brazdilova, S.L.; Casek, P.; Korenciak, L. Low-Power ADS-B for GA Operating in Low Altitude Airspace. In Proceedings of the 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), San Antonio, TX, USA, 11–15 October 2020; pp. 1–10. [Google Scholar] [CrossRef]
- Sallouha, H.; Chiumento, A.; Pollin, S. Aerial Vehicles Tracking Using Noncoherent Crowdsourced Wireless Networks. IEEE Trans. Veh. Technol. 2021, 70, 10780–10791. [Google Scholar] [CrossRef]
- Sidibe, A.; Loubet, G.; Takacs, A.; Ferré, G.; Ghiotto, A. Miniature drone antenna design for the detection of airliners. Int. J. Microw. Wirel. Technol. 2021, 13, 21–27. [Google Scholar] [CrossRef]
- Goossen, J.; Kim, J.; van der Hoeven, S. Development of a versatile ADS-B communications system. In Proceedings of the 2018 Texas Symposium on Wireless and Microwave Circuits and Systems (WMCS), Waco, TX, USA, 5–6 April 2018; pp. 1–4. [Google Scholar]
- Zhu, Y.; Shi, X.; Kang, K. UAV-Based Flight Inspection System. In Proceedings of the International Flight Inspection Symposium, Monterey, CA, USA, 16–20 April 2018; pp. 16–20. [Google Scholar]
- Alarcón, V.; García, M.; Alarcón, F.; Viguria, A.; Martínez, Á.; Janisch, D.; Acevedo, J.J.; Maza, I.; Ollero, A. Procedures for the Integration of Drones into the Airspace Based on U-Space Services. Aerospace 2020, 7, 128. [Google Scholar] [CrossRef]
- Berdonosov, V.; Zivotova, A.; Naing, Z.H.; Zhuravlev, D.O. Speed Approach for UAV Collision Avoidance. J. Phys. Conf. Ser. 2018, 1015, 052002. [Google Scholar] [CrossRef]
- Languell, Z.P.; Gu, Q. A Multi-Point Distance-Bounding Protocol for Securing Automatic Dependent Surveillance-Broadcast in Unmanned Aerial Vehicle Applications. J. Comput. Sci. Technol. 2020, 35, 825–842. [Google Scholar] [CrossRef]
- Lee, Z.; Kumar, R.; Radmanesh, R.; Kumar, M.; Cohen, K. Application of fuzzy logic for developing sense and avoid techniques for uav flight operations in national airspace. In Dynamic Systems and Control Conference; American Society of Mechanical Engineers: New York, NY, USA, 2020; Volume 2. [Google Scholar] [CrossRef]
- Radmanesh, M.; Kumar, M.; Sarim, M. Grey wolf optimization based sense and avoid algorithm in a Bayesian framework for multiple UAV path planning in an uncertain environment. Aerosp. Sci. Technol. 2018, 77, 168–179. [Google Scholar] [CrossRef]
- Pierpaoli, P.; Rahmani, A. UAV collision avoidance exploitation for noncooperative trajectory modification. Aerosp. Sci. Technol. 2018, 73, 173–183. [Google Scholar] [CrossRef]
- Berdonosov, V.; Zivotova, A.; Zhuravlev, D.; Naing, Z.H. Implementation of the Speed Approach for UAV Collision Avoidance in Dynamic Environment. In Proceedings of the 2018 International Multi-Conference on Industrial Engineering and Modern Technologies (FarEastCon), Vladivostok, Russia, 3–4 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Burke, P.J. Small Unmanned Aircraft Systems (SUAS) and Manned Traffic near John Wayne Airport (KSNA) Spot Check of the SUAS Facility Map: Towards a New Paradigm for Drone Safety Near Airports. Drones 2019, 3, 84. [Google Scholar] [CrossRef] [Green Version]
- Wallace, R.J.; Kiernan, K.W.; Haritos, T.; Robbins, J.; D’souza, G.V. Evaluating small UAS near midair collision risk using Aero Scope and ADS-B. Int. J. Aviat. Aeronaut. Aerosp. 2018, 5, 2. [Google Scholar] [CrossRef]
- Aweiss, A.; Homola, J.; Rios, J.; Jung, J.; Johnson, M.; Mercer, J.; Modi, H.; Torres, E.; Ishihara, A. Flight Demonstration of Unmanned Aircraft System (UAS) Traffic Management (UTM) at Technical Capability Level 3. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Mott, J.H.; Marshall, Z.A.; Vandehey, M.A.; May, M.; Bullock, D.M. Detection of Conflicts Between ADS-B-Equipped Aircraft and Unmanned Aerial Systems. Transp. Res. Rec. J. Transp. Res. Board 2020, 2674, 197–204. [Google Scholar] [CrossRef]
- Jacob, J.; Mitchell, T.; Loffi, J.; Vance, M.; Wallace, R. Airborne visual detection of small unmanned aircraft systems with and without ADS-B. In Proceedings of the 2018 IEEE/ION Position, Location and Navigation Symposium (PLANS), Monterey, CA, USA, 23–26 April 2018; pp. 749–756. [Google Scholar]
- Meer, I.A.; Ozger, M.; Lundmark, M.; Sung, K.W.; Cavdar, C. Ground Based Sense and Avoid System for Air Traffic Management. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Arpaio, M.J.; Paolini, G.; Fuschini, F.; Costanzo, A.; Masotti, D. An All-in-One Dual Band Blade Antenna for ADS-B and 5G Communications in UAV Assisted Wireless Networks. Sensors 2021, 21, 5734. [Google Scholar] [CrossRef] [PubMed]
- Siewert, S.; Sampigethaya, K.; Buchholz, J.; Rizor, S. Fail-Safe, Fail-Secure Experiments for Small UAS and UAM Traffic in Urban Airspace. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Svanstrom, F.; Englund, C.; Alonso-Fernandez, F. Real-Time Drone Detection and Tracking with Visible, Thermal and Acoustic Sensors. In Proceedings of the 2020 25th International Conference on Pattern Recognition (ICPR), Milan, Italy, 10–15 January 2020; pp. 7265–7272. [Google Scholar]
- Grzybowski, J.; Latos, K.; Czyba, R. Low-Cost Autonomous UAV-Based Solutions to Package Delivery Logistics. In Advanced, Contemporary Control; Springer: Berlin/Heidelberg, Germany, 2020; pp. 500–507. [Google Scholar]
- Shaikh, E.; Mohammad, N.; Muhammad, S. Model Checking Based Unmanned Aerial Vehicle (UAV) Security Analysis. In Proceedings of the 2020 International Conference on Communications, Signal Processing, and their Applications (ICCSPA), Sharjah, United Arab Emirates, 16–18 March 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, J.; Song, D.; Liang, R.; Han, P. ADS-B and UAV Signal Monitoring System Design Based on Spectrum Sensing. In Proceedings of the 2019 IEEE 8th Joint International Information Technology and Artificial Intelligence Conference (ITAIC), Chongqing, China, 24–26 May 2019; pp. 422–426. [Google Scholar] [CrossRef]
- Wu, Y.; Dai, H.-N.; Wang, H.; Choo, K.-K.R. Blockchain-Based Privacy Preservation for 5G-Enabled Drone Communications. IEEE Netw. 2021, 35, 50–56. [Google Scholar] [CrossRef]
- Bateman, A.J.; Burkholder, J.; Summers, T.; Richards, N.D. Incorporating RF Coverage Analysis in Mission Planning for Future Airspace Operations. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019. [Google Scholar] [CrossRef]
- Kunze, S.; Weinberger, A. Concept for a Geo-Awareness-System for Civilian Unmanned Aerial Systems. In Proceedings of the 2021 31st International Conference Radioelektronika (RADIOELEKTRONIKA), Brno, Czech Republic, 19–21 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Yue, X.; Liu, Y.; Wang, J.; Song, H.; Cao, H. Software Defined Radio and Wireless Acoustic Networking for Amateur Drone Surveillance. IEEE Commun. Mag. 2018, 56, 90–97. [Google Scholar] [CrossRef]
- Lin, C.E.; Shao, P.-C.; Lin, Y.-Y. System Operation of Regional UTM in Taiwan. Aerospace 2020, 7, 65. [Google Scholar] [CrossRef]
- Baek, H.; Lim, J. Design of Future UAV-Relay Tactical Data Link for Reliable UAV Control and Situational Awareness. IEEE Commun. Mag. 2018, 56, 144–150. [Google Scholar] [CrossRef]
- Minucci, F.; Vinogradov, E.; Sallouha, H.; Pollin, S. UAV Location Broadcasting with Wi-Fi SSID. In Proceedings of the 2019 Wireless Days (WD), Manchester, UK, 24–26 April 2019. [Google Scholar] [CrossRef]
- Vinogradov, E.; Minucci, F.; Pollin, S. Wireless Communication for Safe UAVs: From Long-Range Deconfliction to Short-Range Collision Avoidance. IEEE Veh. Technol. Mag. 2020, 15, 88–95. [Google Scholar] [CrossRef] [Green Version]
- Shao, P.-C. Risk Assessment for UAS Logistic Delivery under UAS Traffic Management Environment. Aerospace 2020, 7, 140. [Google Scholar] [CrossRef]
- Perez, E.; Winger, A.; Tran, A.; Garcia-Paredes, C.; Run, N.; Keti, N.; Bhandari, S.; Raheja, A. Autonomous Collision Avoidance System for a Multicopter using Stereoscopic Vision. In Proceedings of the 2018 International Conference on Unmanned Aircraft Systems (ICUAS), Dallas, TX, USA, 12–15 June 2018; Volume 91768, pp. 579–588. [Google Scholar] [CrossRef]
- Abdel-Malek, M.A.; Akkaya, K.; Bhuyan, A.; Cebe, M.; Ibrahim, A.S. Enabling Second Factor Authentication for Drones in 5G using Network Slicing. In Proceedings of the 2020 IEEE Globecom Workshops (GC Wkshps), Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Kuroda, V.; Egorov, M.; Munn, S.; Evans, A. Unlicensed Technology Assessment for Uas Communications. In Proceedings of the 2020 Integrated Communications Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 8–10 September 2020; pp. 1–12. [Google Scholar] [CrossRef]
- Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. ARID: Anonymous Remote IDentification of Unmanned Aerial Vehicles. In Proceedings of the Annual Computer Security Applications Conference, Association for Computing Machinery (ACM). New York, NY, USA, 6–10 December 2021; pp. 207–218. [Google Scholar]
- Alkadi, R.; Shoufan, A. Unmanned Aerial Vehicles Traffic Management Solution Using Crowd-sensing and Blockchain. IEEE Trans. Netw. Serv. Manag. 2021, 1–14. [Google Scholar]
- Alsoliman, A.; Bin Rabiah, A.; Levorato, M. Privacy-Preserving Authentication Framework for UAS Traffic Management Systems. In Proceedings of the 2020 4th Cyber Security in Networking Conference (CSNet), Lausanne, Switzerland, 21–23 October 2020. [Google Scholar]
- Shoufan, A.; Yeun, C.Y.; Taha, B. eSIM-Based Authentication Protocol for UAV Remote Identification. In Security and Privacy in the Internet of Things; Wiley: New York, NY, USA, 2021; pp. 91–122. [Google Scholar] [CrossRef]
- Rios, J.L.; Aweiss, A.S.; Jung, J.; Homola, J.; Johnson, M.; Johnson, R. Flight Demonstration of Unmanned Aircraft System (UAS) Traffic Management (UTM) at Technical Capability Level. In Proceedings of the AIAA AVIATION 2020 Forum, Virtual, 15–19 June 2020. [Google Scholar]
- Service-Oriented Separation Assurance for Small UAS Traffic Management. In Proceedings of the 2019 Integrated Communications, Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 9–11 April 2019; Volume 27. [CrossRef]
- Marques, M.; Brum, A.; Antunes, S.; Mota, J.G. Sense and Avoid Implementation in a Small Unmanned Aerial Vehicle. In Proceedings of the 2018 13th APCA International Conference on Control and Soft Computing (CONTROLO), Ponta Delgada, Portugal, 4–6 June 2018; pp. 395–400. [Google Scholar]
- Perner, C.; Schmitt, C. Security Concept for Unoccupied Aerial Systems. In Proceedings of the 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), San Antonio, TX, USA, 11–15 October 2020. [Google Scholar] [CrossRef]
- Shelley, A. Drone Registration Will Not Prevent Another Gatwick. SSRN Electron. J. 2019, 1–14. [Google Scholar] [CrossRef]
- Athavale, J.; Baldovin, A.; Mo, S.; Paulitsch, M. Chip-Level Considerations to Enable Dependability for eVTOL and Urban Air Mobility Systems. In Proceedings of the 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), San Antonio, TX, USA, 11–15 October 2020; pp. 1–6. [Google Scholar]
- Bauranov, A.; Rakas, J. Designing airspace for urban air mobility: A review of concepts and approaches. Prog. Aerosp. Sci. 2021, 125, 100726. [Google Scholar] [CrossRef]
- Zhi, Y.; Fu, Z.; Sun, X.; Yu, J. Security and Privacy Issues of UAV: A Survey. Mob. Netw. Appl. 2020, 25, 95–101. [Google Scholar] [CrossRef]
- Wuerll, R.; Robert, J.; Heuberger, A. An overview of current and proposed communication standards for large deployment of Unmanned Aircraft Systems. In Proceedings of the 2019 IEEE Aerospace Conference, Big Sky, MT, USA, 2–9 March 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Benzaghta, M.A.; Elwalda, A.; Mousa, M.; Erkan, I.; Rahman, M. SWOT analysis applications: An integrative literature review. J. Glob. Bus. Insights 2021, 6, 55–73. [Google Scholar] [CrossRef]
- Khoshbakht, M.; Gou, Z.; Dupre, K. Cost-benefit Prediction of Green Buildings: SWOT Analysis of Research Methods and Recent Applications. Procedia Eng. 2017, 180, 167–178. [Google Scholar] [CrossRef] [Green Version]



| No | Category | ADS-B | ADS-B-Like | Remote ID |
|---|---|---|---|---|
| 1 | Definition | [4,5,6,7] | [8,9,10,11] | [12,13,14] |
| 2 | Data format | [5,7,15] | [8,16,17] | [13,18,19] |
| 3 | Technology | [5,6,7,15,20,21] | [8,9,10,11,16,17,22,23] | [12,13,14,18,19] |
| 4 | Research application | [4,5,6,20,21,22,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52] | [8,11,16,17,22,41,43,45,53,54,55,56,57,58,59,60,61,62] | [12,13,14,19,42,63,64,65,66,67,68] |
| 5 | Remaining issues | [69,70,71,72,73,74] | [10,69,70,73,74,75,76] | [70,72,73,74] |
| No | Research Application | ADS-B | ADS-B-Like | Remote ID |
|---|---|---|---|---|
| 1 | Surveillance | [24,25,26,27,28,29,30,31,32,33] | [8,11,16,17,53,54,55,56,57] | - |
| 2 | Detect and avoid | [4,21,22,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49] | [22,41,43,58,59,60] | [12,13,14] |
| 3 | Capacity estimation | [6,20] | - | [63] |
| 4 | Communication | - | [45,61] | [19,64] |
| 5 | Command and control | - | [53,57] | - |
| 6 | Security | [5,50,51,52] | [62] | [42,65,66,67,68] |
| No | Remaining Issues | ADS-B | ADS-B-Like | Remote ID |
|---|---|---|---|---|
| 1 | Security | [69,70,71,72] | [70,71,72,73,74,75] | [72,73,74] |
| 2 | Safety | [69,70,71] | [70,73] | [12,13,14] |
| 3 | Communication | - | [69,73,74,76] | - |
| 4 | Surveillance | [73,74] | [10,69] | [70] |
| SWOT | ADS-B | Remote ID | ADS-B-Like |
|---|---|---|---|
| Strength | Mature standard and technology, surveillance purpose | Mainly for security, Established standard | Two ways of communication, many options in wireless technology |
| Weakness | No security feature, predicted capacity congestion | Short coverage, not supporting surveillance | No standard established, variety in quality |
| Opportunity | Compulsory in manned flights by civil aviation authorities | Endorsed by FAA | Wireless technology development will favor the application for UAV |
| Threat | Other systems have a lower price | Usage by security officers | New ground accessory required |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ruseno, N.; Lin, C.-Y.; Chang, S.-C. UAS Traffic Management Communications: The Legacy of ADS-B, New Establishment of Remote ID, or Leverage of ADS-B-Like Systems? Drones 2022, 6, 57. https://doi.org/10.3390/drones6030057
Ruseno N, Lin C-Y, Chang S-C. UAS Traffic Management Communications: The Legacy of ADS-B, New Establishment of Remote ID, or Leverage of ADS-B-Like Systems? Drones. 2022; 6(3):57. https://doi.org/10.3390/drones6030057
Chicago/Turabian StyleRuseno, Neno, Chung-Yan Lin, and Shih-Cheng Chang. 2022. "UAS Traffic Management Communications: The Legacy of ADS-B, New Establishment of Remote ID, or Leverage of ADS-B-Like Systems?" Drones 6, no. 3: 57. https://doi.org/10.3390/drones6030057
APA StyleRuseno, N., Lin, C.-Y., & Chang, S.-C. (2022). UAS Traffic Management Communications: The Legacy of ADS-B, New Establishment of Remote ID, or Leverage of ADS-B-Like Systems? Drones, 6(3), 57. https://doi.org/10.3390/drones6030057






