LightMAN: A Lightweight Microchained Fabric for Assurance- and Resilience-Oriented Urban Air Mobility Networks
Abstract
1. Introduction
- (1)
- A complete LightMAN system architecture is presented along with details of key components and functionalities;
- (2)
- A machine learning-based anomaly detection (MLAD) method to monitor the UAM networks in real time is proposed. To generate the source data (MAVLink message) for creating the cyber-resiliency scenario, we implemented a software-in-the-loop (SITL) simulator and associated demonstration package (pymavlink) in a python environment to emulate the message communications among UAVs;
- (3)
- A lightweight blockchain called microchain is leveraged to guarantee security and privacy requirements in UAV data access and sharing scenarios; and
- (4)
- A proof-of-concept prototype is implemented and tested on a small-scale physical network. The experimental results show that the proposed LightMAN only incurs less than two seconds of latency while committing transactions on the distributed ledger and no more than 18% overhead during access authentication.
2. Background and Related Work
2.1. Unmanned Aerial Vehicles
2.2. Blockchain Technology
2.3. Blockchain-Based UAV Networks
2.3.1. UAV Communication
2.3.2. UAV Data Integrity
2.3.3. UAV Authentication
3. Design Rationale and System Architecture
3.1. Deep Learning (DL)-Powered UAM Security
3.2. Microchain Fabric for UAM Data Sharing
- The lifetime of a committee is defined as a dynasty, and all nodes within the network use a random committee election mechanism to construct a new committee at the beginning of a new dynasty. The new committee members rely on their neighboring peers, which use a node discovery protocol to reach out to each other. Finally, all committee members maintain a fully connected consensus network, and non-committee nodes periodically synchronize states of the current dynasty. Until the current dynasty’s lifetime is ending, committee members utilize an epoch randomness generation protocol to cooperatively propose a global random seed for the next committee election.
- Given a synchronous network environment, operations of consensus processes are coordinated in sequential rounds called epochs. The block proposal leverages an efficient proof-of-credit (PoC) algorithm, which allows the consensus committee to continuously publish blocks containing transactions and extend the main chain length. The block proposal process continues running multiple rounds until the end of an epoch. Then, a voting-based chain finality protocol allows committee members to make an agreement on a checkpointing block. As a result, temporary fork chains are pruned, and these committed blocks are finalized on the unique main chain.
- The organization of on-chain and off-chain storage is illustrated by the upper right part of Figure 1. As the basic unit of on-chain data recorded on the distributed ledger, a block contains header information (e.g., previous block hash and block height) and orderly transactions. The distributed data storage (DDS), which is built on a swarm [35] network, is used as off-chain storage. The UAV data and flight logs that require heterogeneous formats and various sizes are saved on the DDS, and they can be easily addressed by their swarm hash. In an optimal manner, each transaction only contains a swarm hash as a reference pointing to its raw data on the DDS. Compared with raw data, a swarm hash has a small and fixed length (32 or 64 bytes); therefore, all transactions have almost the same data size. It is promising to improve efficiency in transaction propagation without directly padding raw data into transactions.
4. Experimental Results and Evaluation
4.1. Prototype Implementation
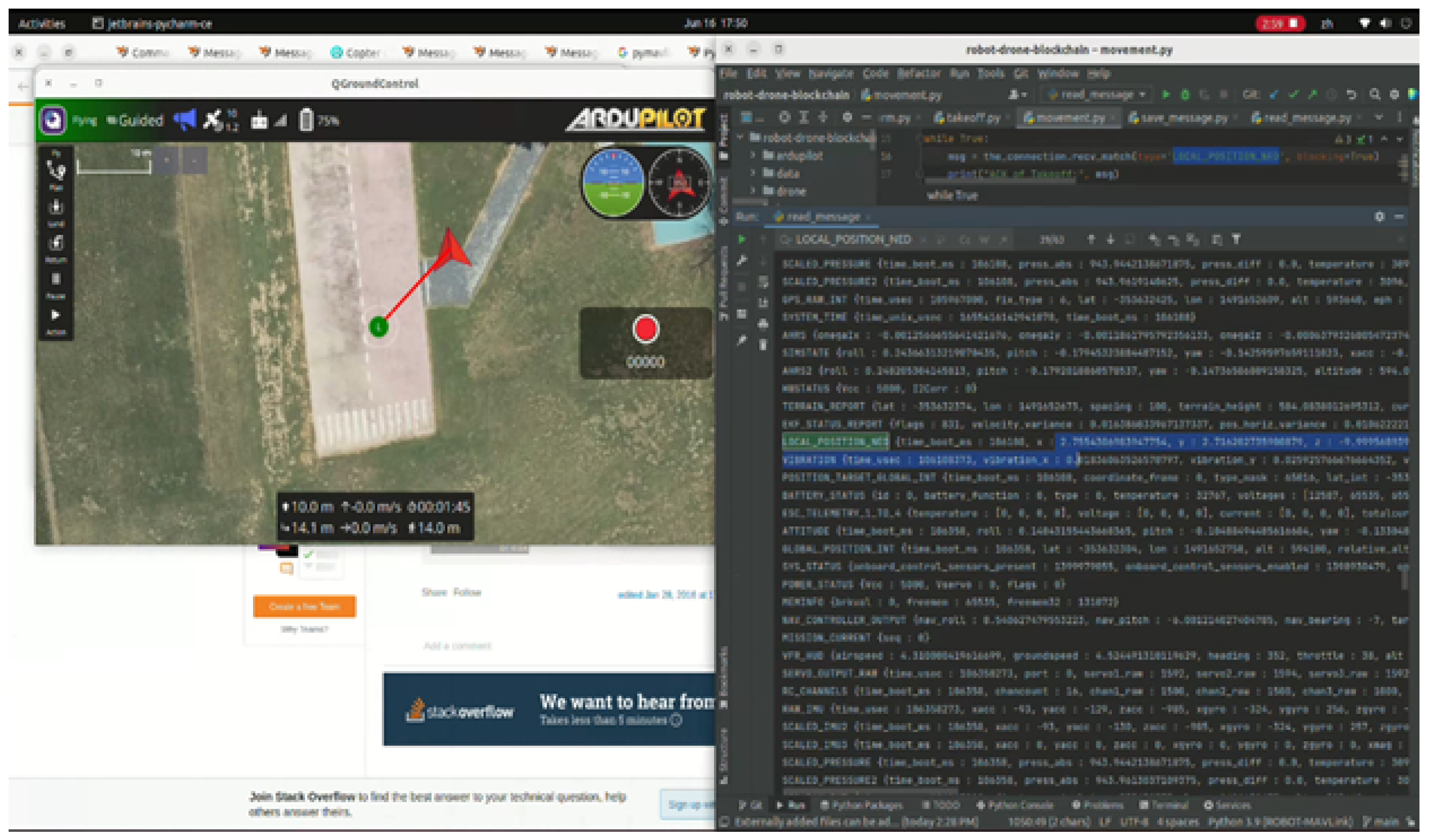
4.2. MAVLink Message Data Acquisition
4.3. Performance Evaluation
4.3.1. End-to-End Latency of Authorizing Access Tokens
4.3.2. Processing Time and Throughput in Access Authentication
4.3.3. Computation Cost by Preserving Data Privacy
4.4. Comparative Evaluation
5. Conclusions and Future Work
- (1)
- Although the microchain is promising for providing a lightweight blockchain for a small-scale UAV network such as a drone cluster, it is not suitable for a large-scale UAM system demanding scalability and dynamicity in multidomain coordination. A hierarchical integrated federated ledger infrastructure (HIFL) [41] is promising for the improvement of scalability, dynamicity, and security for multi-domain IoD applications. Thus, our ongoing efforts include validating LightMAN in a real-world UAV network and investigating the integration of microchain and HIFL to support secure inter-chain transactions in a large-scale UAM system.
- (2)
- There are still unanswered questions regarding an incentive mechanism that motivates users and drones to devote their resources (e.g., computation, storage, and networking) to participant consensus processes and gain extra profits. In our future work, we will use game theory to model incentive strategies and evaluate the effectiveness, security, and robustness of LightMAN in IoD scenarios.
- (3)
- The third important milestone is an in-field validation of LightMAN in the context of practical applications. Once all the functional blocks and integrated systems are successfully tested in the lab environment, a small-scale drone network will be created with drones that are designed by the team. The completely customized drones will allow us to mount the LightMAN system on top of multiple application-determined sensing blocks, such as smart surveillance cameras or motion sensors. Specifically, to better validate the effectiveness of LightMAN, we plan to test our implementation with a hardware-in-the-loop (HITL) design in a hierarchical practical environment. We will deploy our validator devices on the hardware drones and establish a small-scale decentralized platform. Each drone will function as an individual node with communication protocols (e.g., MAVLink, TCP/IP) within LightMAN. Some typical communication-related anomalies (e.g., GPS spoofing, and channel access attacks) will be crafted to perform a practical injection attack onto the device sensors. In the future study, we will also build multiple clients and servers onboard to stream the shared data (e.g., MAVLink messages) and process the UAM monitoring among UAVs in real time.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ABI | Application Binary Interfaces |
| AC | Access Control |
| ADS-B | Automatic Dependent Surveillance Broadcast |
| AI | Artificial Intelligence |
| ATS | Air Traffic Service |
| CAN | Controller Area Network |
| CapAC | Capability-based Access Control |
| DApp | Decentralized App |
| DDS | Distributed Data Storage |
| DDoS | Distributed Denial-of-Service |
| DL | Deep Learning |
| DLT | Distributed Ledger Technology |
| IoD | Internet of Drones |
| IoT | Internet of Things |
| MC | Master Controller |
| MEC | Multi-Access Edge Computing |
| ML | Machine Learning |
| PBN | Performance Bottleneck |
| PoC | Proof-of-Credit |
| PoT | Proof-of-Traffic |
| PoW | Proof-of-Work |
| PKI | Public Key Infrastructure |
| QoE | Quality-of-Experience |
| QoS | Quality-of-Service |
| RL | Reinforcement Learning |
| SAW | Situational Awareness |
| SC | Smart Contract |
| SDN | Software-defined Networking |
| SITL | Software-In-The-Loop |
| SPF | Single Point of Failure |
| UAM | Urban Air Mobility |
| UAV | Unmanned Aerial Vehicle |
References
- Xu, R.; Nikouei, S.Y.; Nagothu, D.; Fitwi, A.; Chen, Y. Blendsps: A blockchain-enabled decentralized smart public safety system. Smart Cities 2020, 3, 928–951. [Google Scholar] [CrossRef]
- Xu, R.; Lin, X.; Dong, Q.; Chen, Y. Constructing trustworthy and safe communities on a blockchain-enabled social credits system. In Proceedings of the 15th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, New York, NY, USA, 5–7 November 2018; pp. 449–453. [Google Scholar]
- Alladi, T.; Chamola, V.; Sahu, N.; Guizani, M. Applications of blockchain in unmanned aerial vehicles: A review. Veh. Commun. 2020, 23, 100249. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Agrawal, A.; Goyal, A.; Luong, N.C.; Niyato, D.; Yu, F.R.; Guizani, M. Fast, reliable, and secure drone communication: A comprehensive survey. IEEE Commun. Surv. Tutor. 2021, 23, 2802–2832. [Google Scholar] [CrossRef]
- Chen, N.; Chen, Y.; Blasch, E.; Ling, H.; You, Y.; Ye, X. Enabling smart urban surveillance at the edge. In Proceedings of the 2017 IEEE International Conference on Smart Cloud (SmartCloud), New York, NY, USA, 3–5 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 109–119. [Google Scholar]
- Han, T.; Ribeiro, I.D.L.; Magaia, N.; Preto, J.; Segundo, A.H.F.N.; de Macêdo, A.R.L.; Muhammad, K.; de Albuquerque, V.H.C. Emerging drone trends for blockchain-based 5G networks: Open issues and future perspectives. IEEE Netw. 2021, 35, 38–43. [Google Scholar] [CrossRef]
- Aloqaily, M.; Bouachir, O.; Boukerche, A.; Al Ridhawi, I. Design guidelines for blockchain-assisted 5G-UAV networks. IEEE Netw. 2021, 35, 64–71. [Google Scholar] [CrossRef]
- Blasch, E.; Xu, R.; Chen, Y.; Chen, G.; Shen, D. Blockchain methods for trusted avionics systems. In Proceedings of the 2019 IEEE National Aerospace and Electronics Conference (NAECON), Dayton, OH, USA, 15–19 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 192–199. [Google Scholar]
- Xu, R.; Zhai, Z.; Chen, Y.; Lum, J.K. BIT: A blockchain integrated time banking system for community exchange economy. In Proceedings of the 2020 IEEE International Smart Cities Conference (ISC2), Piscataway, NJ, USA, 28 September–1 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–8. [Google Scholar]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. Exploration of blockchain-enabled decentralized capability-based access control strategy for space situation awareness. Opt. Eng. 2019, 58, 041609. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. Blendcac: A smart contract enabled decentralized capability-based access control mechanism for the iot. Computers 2018, 7, 39. [Google Scholar] [CrossRef]
- Nikouei, S.Y.; Xu, R.; Nagothu, D.; Chen, Y.; Aved, A.; Blasch, E. Real-time index authentication for event-oriented surveillance video query using blockchain. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–8. [Google Scholar]
- Sharma, V.; You, I.; Jayakody, D.N.K.; Reina, D.G.; Choo, K.K.R. Neural-blockchain-based ultrareliable caching for edge-enabled UAV networks. IEEE Trans. Ind. Inform. 2019, 15, 5723–5736. [Google Scholar] [CrossRef]
- Wang, J.; Liu, Y.; Niu, S.; Song, H. Lightweight blockchain assisted secure routing of swarm UAS networking. Comput. Commun. 2021, 165, 131–140. [Google Scholar] [CrossRef]
- Chang, Z.; Guo, W.; Guo, X.; Chen, T.; Min, G.; Abualnaja, K.M.; Mumtaz, S. Blockchain-empowered drone networks: Architecture, features, and future. IEEE Netw. 2021, 35, 86–93. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Karimipour, H.; Srivastava, G.; Aledhari, M. Enabling drones in the internet of things with decentralized blockchain-based security. IEEE Internet Things J. 2020, 8, 6406–6415. [Google Scholar] [CrossRef]
- Feng, C.; Liu, B.; Guo, Z.; Yu, K.; Qin, Z.; Choo, K.K.R. Blockchain-based cross-domain authentication for intelligent 5G-enabled internet of drones. IEEE Internet Things J. 2021, 9, 6224–6238. [Google Scholar] [CrossRef]
- Aggarwal, S.; Shojafar, M.; Kumar, N.; Conti, M. A new secure data dissemination model in internet of drones. In Proceedings of the 2019 IEEE International Conference on Communications (ICC 2019), Shangai, China, 20–24 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Liang, X.; Zhao, J.; Shetty, S.; Li, D. Towards data assurance and resilience in IoT using blockchain. In Proceedings of the 2017 IEEE Military Communications Conference (MILCOM 2017), Baltimore, MD, USA, 23–25 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 261–266. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Business Review. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 20 October 2022).
- Welcome to Ethereum. Available online: https://ethereum.org/en/ (accessed on 30 August 2022).
- Hyperledger Fabric. Available online: https://hyperledger-fabric.readthedocs.io/en/latest/ (accessed on 30 July 2022).
- Xu, R.; Chen, Y.; Blasch, E. Microchain: A Light Hierarchical Consensus Protocol for IoT Systems. In Blockchain Applications in IoT Ecosystem; Springer: Cham, Switzerland, 2021; pp. 129–149. [Google Scholar]
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV cellular communications: Practical aspects, standardization advancements, regulation, and security challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3417–3442. [Google Scholar] [CrossRef]
- Blasch, E.; Sabatini, R.; Roy, A.; Kramer, K.A.; Andrew, G.; Schmidt, G.T.; Insaurralde, C.C.; Fasano, G. Cyber awareness trends in avionics. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–8. [Google Scholar]
- Xu, R.; Nagothu, D.; Chen, Y. Decentralized video input authentication as an edge service for smart cities. IEEE Consum. Electron. Mag. 2021, 10, 76–82. [Google Scholar] [CrossRef]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine generals problem. ACM Trans. Program. Lang. Syst. 1982, 4, 382–401. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2018, 6, 2188–2204. [Google Scholar] [CrossRef]
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Hu, N.; Tian, Z.; Sun, Y.; Yin, L.; Zhao, B.; Du, X.; Guizani, N. Building agile and resilient UAV networks based on SDN and blockchain. IEEE Netw. 2021, 35, 57–63. [Google Scholar] [CrossRef]
- Blasch, E.; Raz, A.K.; Sabatini, R.; Insaurralde, C.C. Information Fusion as an Autonomy enabler for UAS Traffic Management (UTM). In Proceedings of the AIAA Scitech Forum 2021, Virtual Event, 11–15 January 2021; pp. 1–12. [Google Scholar]
- Mnih, V.; Kavukcuoglu, K.; Silver, D.; Graves, A.; Antonoglou, I.; Wierstra, D.; Riedmiller, M.A. Playing Atari with Deep Reinforcement Learning. arXiv 2013, arXiv:1312.5602. [Google Scholar]
- Li, J.; Sun, A.; Han, J.; Li, C. A Survey on Deep Learning for Named Entity Recognition. IEEE Trans. Knowl. Data Eng. 2020, 34, 50–70. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y. μDFL: A Secure Microchained Decentralized Federated Learning Fabric atop IoT Networks. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2677–2688. [Google Scholar] [CrossRef]
- Swarm. Available online: https://ethersphere.github.io/swarm-home/ (accessed on 30 September 2022).
- Flask: A Pyhon Microframework. Available online: https://flask.palletsprojects.com/ (accessed on 30 September 2022).
- Pyca/Cryptography Documentation. Available online: https://cryptography.io/ (accessed on 30 September 2022).
- MAVLink Developer Guide. Available online: https://mavlink.io/en/ (accessed on 30 September 2022).
- ArduPilot Project. Available online: https://github.com/ArduPilot/ardupilot (accessed on 30 September 2022).
- Taylor, M.; Chen, H.; Qin, F.; Stewart, C. Avis: In-Situ Model Checking for Unmanned Aerial Vehicles. In Proceedings of the 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Taipei, Taiwan, 21–24 June 2021. [Google Scholar]
- Xu, R.; Chen, Y.; Li, X.; Blasch, E. A Secure Dynamic Edge Resource Federation Architecture for Cross-Domain IoT Systems. In Proceedings of the 2022 International Conference on Computer Communications and Networks (ICCCN), Waikiki Beach, Honolulu, HI, USA, 25–27 July 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–8. [Google Scholar]





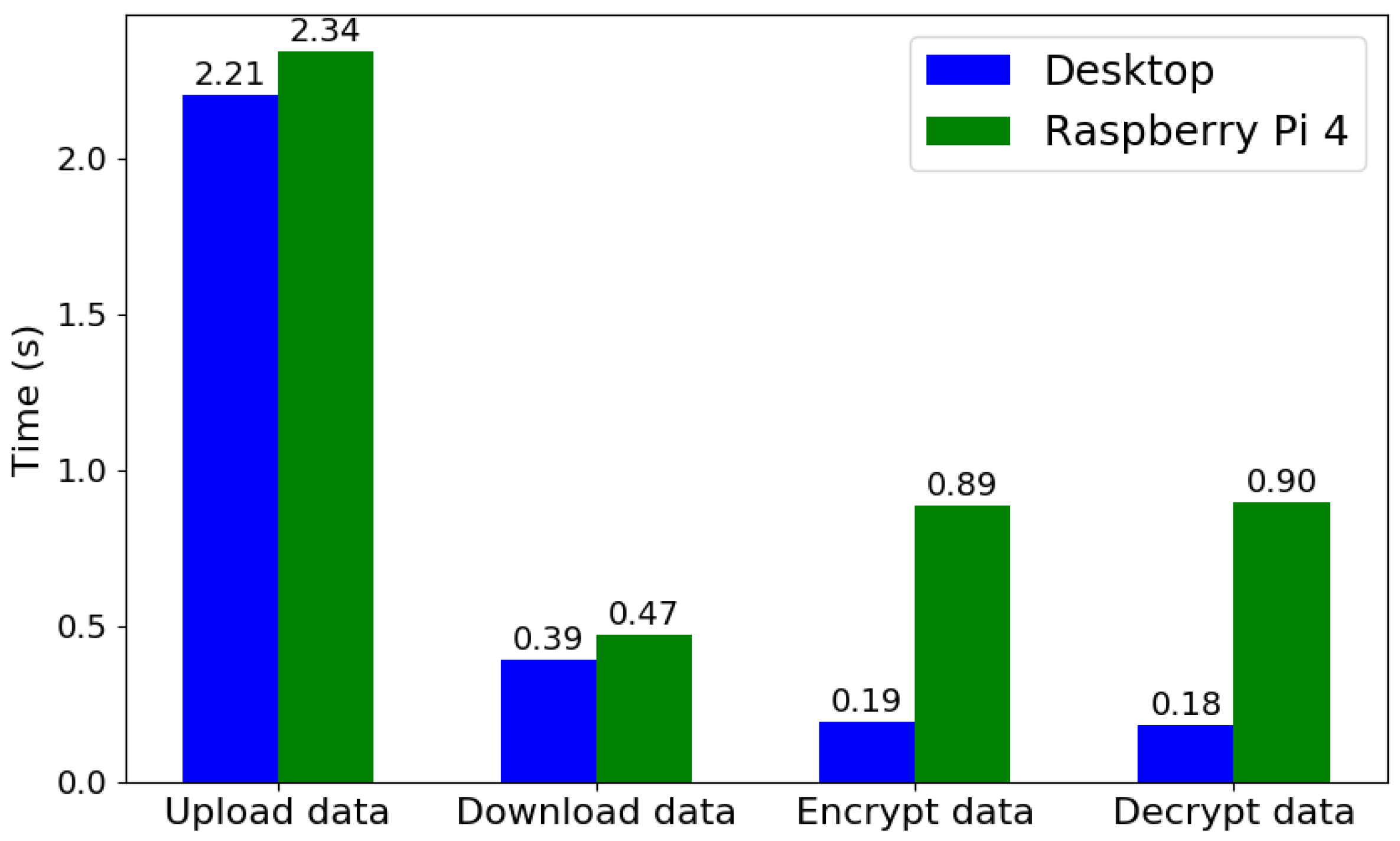
| Device | Redbarn HPC | Raspberry Pi 4 Model B |
|---|---|---|
| CPU | 3.4 GHz, Core i7-2600K (8 cores) | 1.5 GHz, Quad core Cortex-A72 (ARM v8) |
| Memory | 16 GB DDR3 | 4 GB SDRAM |
| Storage | 500 GB HHD | 64 GB (microSD card) |
| OS | Ubuntu 18.04 | Raspbian GNU/Linux (Jessie) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, R.; Wei, S.; Chen, Y.; Chen, G.; Pham, K. LightMAN: A Lightweight Microchained Fabric for Assurance- and Resilience-Oriented Urban Air Mobility Networks. Drones 2022, 6, 421. https://doi.org/10.3390/drones6120421
Xu R, Wei S, Chen Y, Chen G, Pham K. LightMAN: A Lightweight Microchained Fabric for Assurance- and Resilience-Oriented Urban Air Mobility Networks. Drones. 2022; 6(12):421. https://doi.org/10.3390/drones6120421
Chicago/Turabian StyleXu, Ronghua, Sixiao Wei, Yu Chen, Genshe Chen, and Khanh Pham. 2022. "LightMAN: A Lightweight Microchained Fabric for Assurance- and Resilience-Oriented Urban Air Mobility Networks" Drones 6, no. 12: 421. https://doi.org/10.3390/drones6120421
APA StyleXu, R., Wei, S., Chen, Y., Chen, G., & Pham, K. (2022). LightMAN: A Lightweight Microchained Fabric for Assurance- and Resilience-Oriented Urban Air Mobility Networks. Drones, 6(12), 421. https://doi.org/10.3390/drones6120421









