Abstract
Sensing plays a vital role in enabling smart cities. The mobile surveillance of different sectors, the retransmission of radio signals, and package delivery are the main applications conducted by unmanned vehicles in smart cities. Multiple unmanned vehicles or miniaturized real-time flying machines with onboard sensors, whether land- or air-based, communicate with each other to form a flying sensor network. Almost all of these machines are battery-operated. Therefore, power preservation is an extremely important factor to be taken into consideration. This paper proposes a power-aware biologically inspired secure autonomous routing protocol (P-BIOSARP) that depends on enhanced ant colony optimization (eACO). eACO autonomously and securely routes the data packet, and the power awareness maintains the power consumption of the flying sensor network. The novel intelligent power-aware routing protocol was implemented in network simulator 2 to perform a number of experiments with different scenarios. The scenarios included varying numbers of total nodes and mobile nodes, different packet rates, mobile source nodes, multiple mobile routing nodes, and, on the side of security, the injection of malicious nodes. The proposed protocol is compared with BIOSARP, E-BIOSARP, and SRTLD in terms of energy consumption, the delivery ratio, and traffic overhead. The analysis shows that the P-BIOSARP remarkably reduces energy consumption compared to other well-known protocols implemented on real testbeds.
1. Introduction
Monitoring is an essential requirement in many applications, such as agriculture [1], healthcare [2,3], water surveillance systems [4], parking [5], traffic [6], tracking [7], and police and military [8,9,10], and is increasing day by day due to the handling of multiple tasks by a single person, whether on-site or remotely. In surveillance systems, numerous high-tech devices, such as digital still and video cameras (CCTVs), charge-coupled devices (CCDs), active-pixel sensors (complementary metal–oxide semiconductor (CMOS) sensors) [11], GPSs, electronic toll takers, tapping devices, walking gait, biometrics, and drones, are used. Therefore, the deployment and maintenance of these systems are very costly and also require skilled people. Some places that are out of reach or are inaccessible require devices that are disposable. These miniaturized, low-cost devices are known as wireless sensor nodes, and multiple such devices form a wireless sensor network (WSN) [12]. These wireless sensor nodes work as the internet of things (IoT) when connected directly to the internet for transferring data without a gateway. The Fourth Industrial Revolution Industry 4.0, smart agriculture, and smart cities are enabled by attaching these sensor nodes and IoT to machines to control remotely [13], as shown in Figure 1.
Figure 1.
Smart Future.
The future of connectivity is mostly wireless through the internet and sensor nodes that move, whether they are attached to some vehicle or in the form of unmanned aerial vehicles (UAVs). In mobile surveillance systems, the network scenario has changed from fixed nodes to mobile, meaning the network has a dynamic topology [14]. Some of the applications require the source nodes to be mobile, and in some, the gateway moves, as can be seen in Figure 1 for smart farming and Industry 4.0. As a result, the routing of data packets from the source node to the destination over multiple hops consumes a lot of power due to the re-establishment of routes [15]. Mobile sensor nodes that are battery-powered cannot afford fast battery depletion, which becomes a huge concern, especially in the case of disposable flying sensor nodes [16]. The efficiency of the routing protocol depends on the energy efficiency, multipath, QoS, scalability, location awareness, query, load balancing, fault tolerance, and data aggregation [17]. However, according to the application requirements, the routing protocol properties and type change [14].
In a network, when mobility is enabled, these mobile nodes affect the reliability of data transmission [18,19]. Many routing protocols address delay issues to enhance data availability [20]. Networks with a dynamic topology, where devices connect and disconnect rapidly, require a cost optimization mechanism that enables and disables features according to the data flow and device capability [21,22]. In [23], a sustainable routing protocol is introduced to provide flying sensor networks (FSNs) with better connectivity by complex free space propagation on the node to perform area detection. The nodes used in FSNs are low-cost and miniaturized with a slow processor, low memory, and small battery and are unable to handle complex algorithms in real-world scenarios [24]. The cluster-based routing protocol works well in static WSNs or IoT networks [25,26,27,28] but is unable to efficiently route data in an FSN because the node leaves and joins the network rapidly [29]. In [30], a cluster-based routing protocol for an FSN is presented that is based on the predefined static location of the sensor nodes and that of the cluster head. In terms of the mobile node, it remains in a specific area, making its movement strict. Many routing protocols to enhance the quality of secure data routing for WSNs with fixed nodes are based on simple nature-inspired optimization algorithms, such as in [31,32,33], which cannot handle mobility. Still, resource- or host-based routing support, privacy preservation, and ubiquitous support with simple AI techniques are required for future FSNs [34].
This paper proposes a power-aware ant colony optimization (ACO)-based autonomous secure routing protocol for FSNs. The ACO routing protocol is based on a probability function to calculate values by giving the maximum weight to energy and lower weights to link quality and delay parameters. The novel routing protocol helps in maintaining power consumption with secure transfer and privacy preservation, especially in network scenarios that involve massive mobile and malicious wireless nodes. The main contributions of this paper are as follows:
- A power-aware biologically inspired secure self-organized routing protocol (P-BIOSARP) for FSNs in mobile surveillance systems is proposed.
- P-BIOSARP, a biologically inspired self-organized routing protocol (BIOSARP), encryption-enabled E-BIOSARP, and secure real-time routing protocol with load distribution (SRTLD) routing protocols were implemented in network simulator 2 (NS-2).
- Experiments were conducted and results were generated to show the variation in the total number of nodes and mobile nodes with different packet rates, multiple mobile routing, and mobile source nodes, and in terms of security, malicious nodes were injected.
- The results prove that P-BIOSARP performs far better in terms of energy consumption, delivery ratio, and data packet overhead, even with a high number of flying mobile nodes and with malicious nodes.
The rest of the paper is organized as follows. The next section reviews the most relevant published literature. Section 3 explains the method and process flow of P_BIOSARP. Section 4 describes the implementation of the proposed and other routing protocols. Section 5 presents and provides a description of the experimental results. Section 6 discusses the findings. The concluding remarks and the future work are given in the last section, Section 7.
2. Related Work
This section reviews the most recent strongly justified literature related to the ACO based intelligent routing protocols particularly to secure the data and to enhance the FSNs.
Ahmed in [35] developed a secure real-time with load distribution (SRTLD) routing protocol for the data forwarding with security and for distributing energy usage over the complete WSN in an efficient manner. In [36,37], the authors enhanced SRTLD with ant colony optimization (ACO) and more specifically with the probability function to make the data packet routing more intelligent that can maintain efficiency with dynamical changes in the environment named as BIOSARP. Onwards, the authors in [38] incorporate BIOSARP with cryptographic algorithm to encrypt important packet header information such as source ID, destination ID, packet ID.
The 3DRTGP in [39], the WSN routing protocol controls the number of forwarding nodes in the network and limits forwarding to a certain packet forwarding region (PFR). The network density sur-rounding every forwarding nodes is used to determine the PFR, which lowers the amount of collisions, congestion, and redundant packet transfers. In this manner 3DRTGP satisfy to maintain the real-time traffic in time-critical application. A forwarding node decides to forward a packet to meet the packet delivery delay deadline by using its characteristics of delay as processing and queuing delays, and the anticipated hop counts till destination. The explicit communication of nearby information, such as location data, is not necessary in 3DRTGP. Through thorough simulations conducted at various network densities and traffic loads, in order to provide network tuning parameters that fulfill the real-time requirements of applications, 3DRTGP is evaluated. The void node problem in 3D deployments is heuristically solved by 3DRTGP (VNP). Next, a potent heuristic approach to the VNP in 3D WSNs is given. Even in the presence of empty spaces, this strategy permits dependable functioning. In OMNeT++, the 3DRTGP is implemented, and the results are contrasted with those of ABLAR and 3D Greedy GRP.
The authors in [40], created to explicitly address the issue of node placement in a network that works in the similar way as the distribution of helium-3 (3He). 3He is on of the important components for fusion reactors, on the moon. There is considerable agreement that long-term on-site observations are required to fully comprehend the mechanisms underlying the distribution of 3He on the Moon because previous data are equivocal. The choice of the best observation locations and maximizing network longevity are the key difficulties in a multi-objective WSN installation problem. They interpret this as a constant extension of do-mains, and ant colony optimization (ACOR) includes this element. The four-directional placement (FDP) heuristic is contrasted with the procedure.
Ref. [41] presents the ACO routing protocol for mobile ad hoc networks called as AntHocNet. Given that it includes both proactive and reactive routing elements, the proposed AntOR is hybrid. It specifically merge an enhancement strategy with a proactive route management, and the reactive route construction method. The distinction while performing the diffusion process between the real and virtual pheromones is the exploration of routes. The route till destination is decided by taking into consideration the hop counts in the optimum routes, and the disjoint-link and disjoint-node routes are all important features by AntOR protocol. Along with AntOR, the authors now offer PAntOR, a parallelized variant that enables performing tasks concurrently utilizing threads. The route setup stage, connection failure notification, and route local repair procedure are all subject to this parallelization.
In [42], an improved ant colony optimization (IACO) technique was given to construct the rule of pheromone update and transfer function in each sensor node as well as to adaptively choose a data path by taking use of the network’s dynamic state, which can facilitate node mobility. With surrounding nodes, when the given protocol exchange the broadcast messages and the hops information throughout the whole network, the connection forms and renew the pheromone value in the gradient field and accordingly the route. The corresponding probability is computed by the obtained values of surrounding nodes as delay packet loss rate, data transmission, and residual energy of the node. The quickest path and the level of leftover energy are taken into account while choosing a routing strategy. Data are exchanged during the route maintenance procedure to raise the pheromone concentration. Since data packets are transported via the shortest pathways, the network as a whole uses less energy, closer to the average. A VC++ simulator is used to simulate IACO, which is then compared against CO, the Dijkstra algorithm, and data equilibrium-based algorithms (DEBA).
In [43], the communication and data compression approach for the decentralized estimation scenario is provided. It is shown the frameworks for centralized and decentralized estimates that may be seen as one unified optimization model. The authors offer a cyclic optimization approach that can manage altering the gains and phase-shifts of the sensor nodes even in challenging situations like discrete phase-shifts or sensor selection by over-parametrizing the original design problem. The developed framework has a low computing cost since each iteration combines the Gram-Schmidt process with iterations that resemble those in the power approach. creating the design challenge for a fusion center, too.
In [44], the routing protocol Ant Colony Inspired Energy efficient OLSR (AC-OLSR) was presented. Pheromone concentration was computed using a combined link quality technique that could enhance wireless network performance. Link quality and neighbor link quality, two parameters of the general ACO algorithm, were used. In order to evaluate AC-OLSR, it was simulated and compared against OLSR, EE-OLSR, and AntNet. The summary and comparison of the related work is presented in Table 1 that includes the protocol based or enhanced version of which algorithm, the parameters used for coming up with the route decision, the simulation results comparison, and the limitations of the research works.

Table 1.
Related Work Comparison.
3. Methodology
In this section, the in-depth architecture of the power-aware ant colony optimization (ACO) routing protocol (P-BIOSARP) is presented. P-BIOSARP is an extension of the enhanced E-BIOSARP, which includes an encryption mechanism. In E-BIOSARP, as discussed in Section 2, the parameters include link quality (α), delay (β), and remaining energy (δ) for deciding the most optimal node based on the probability () function, as in Equation (1), among the neighboring nodes to forward the data packet to so that it can reach the destination. On top of the optimal value calculation, the encryption is enabled to secure the packet information with a mathematical encryption function.
In P-BIOSARP, the parameter remaining energy (δ) is given the maximum w, and the other two, link quality (α) and delay (β), are given the smallest w when calculating the probability of n by Equation (2).
The process starts when the node is turned on, and the initial battery capacity that is calculated by the battery power management [45] is stored in the variable (batti) by Equation (3).
where tbc is the total battery capacity, and battce is the current energy of the battery or batteries connected to the sensor node. batti is then attached to the current time (ct), based on which the energy consumption (battec) is measured. battec is based on the average battec rate multiplied by the time taken for a single operation. battec is the result of transmitting, receiving, and processing the signals in addition to the consumption in inactive mode [46,47]. Every time any process takes place in the node, δ is updated as in Equation (3) [45].
batti = tbc − battce
δ = batti − battec
The δ parameter is mostly known as the state of charge (SoC), expressed as a percentage, where an empty battery is 0% and full is 100%. In the P-BIOSARP case, δ is retained to avoid multiple calculations and battery consumption. P-BIOSARP depends on BIOSARP, that is, an on-demand routing protocol, which means that when it is necessary to forward the data packet, the neighbor information is collected and stored in a routing table to generate the optimal n decision, as shown in the flow chart in Figure 2.
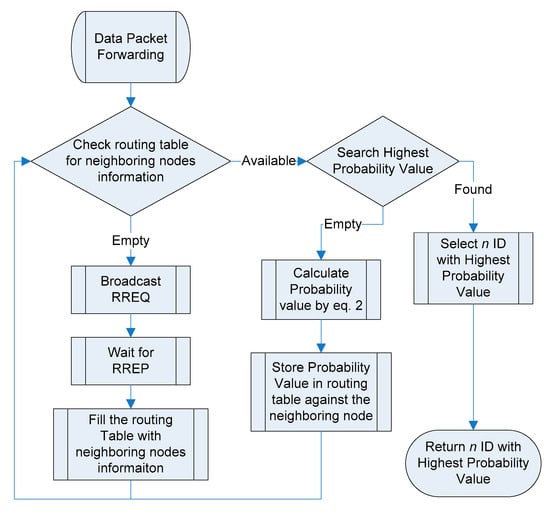
Figure 2.
P-BIOSARP process flow.
Therefore, the source node begins with the broadcasting of route request (RREQ) packets, and all of the neighboring nodes at a single hop, meaning those in the range of the source node, receive them. In response, the node receives the RREQ packet, builds the route reply (RREP) packet with its own information, and sends the RREP packet to the source node. This RREP packet of the WSN with MAC and physical layers of IEEE standard 802.15.4 includes the δ value. P-BIOSARP running at the source node decrypts and stores the information in its routing table with the n identity (ID), as shown in Figure 2.
When the route discovery procedure is completed, the source node starts calculating the probability of each n in the routing table by Equation (2). The value is also recorded in the routing table for each n. After filling all of the required fields of the routing table, the source node searches for the highest value and returns the n ID against it. The data packets in the queue are then forwarded to the selected n. In the event of rerouting or forwarding the data packet, the same process of selecting the best n is conducted, and it continues until the destination and the sink node of the WSN.
The proposed mechanism was developed with the assumption that the included mobile nodes do not move at high speed. The mobile nodes do not move out of the given region. The gateway or the sink node is a trusted body. If no neighboring node is found, the mobile node moves towards the location of the gateway. The pseudo-random function to provide the master key and the ID of the nodes is embedded in the program. The collision avoidance and the channels between devices are managed by the 802.15.4 MAC layer.
4. Implementation
A real scenario of a WSN with IEEE 802.15.4 MAC and physical layers was implemented in NS-2. The scenario TCL file was edited with the values given in Table 2. In an 8-node-based scenario, as shown in Figure 3, a one-to-one (node ID 8 as the source and node ID 0 as the destination) traffic pattern was used. The traffic pattern of 4 source nodes to 1 destination node was used in 50-node (source node IDs 25, 31, 37, and 43), as shown in Figure 4, and 121-node scenarios (source node IDs 90, 100, 110, and 120), as shown in Figure 5.

Table 2.
TCL script configuration.
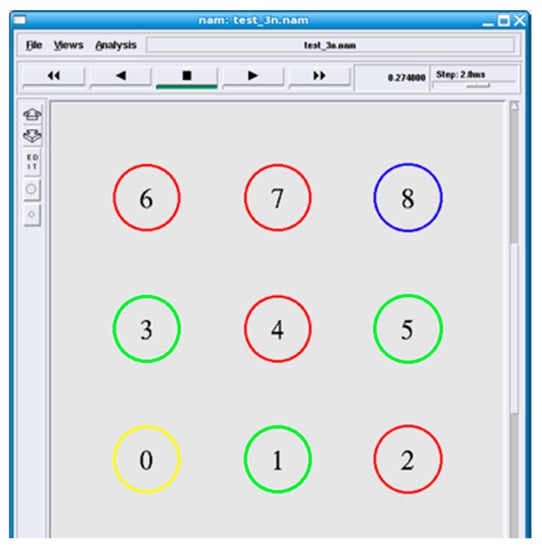
Figure 3.
Scenario with 8 nodes and 4 malicious nodes.
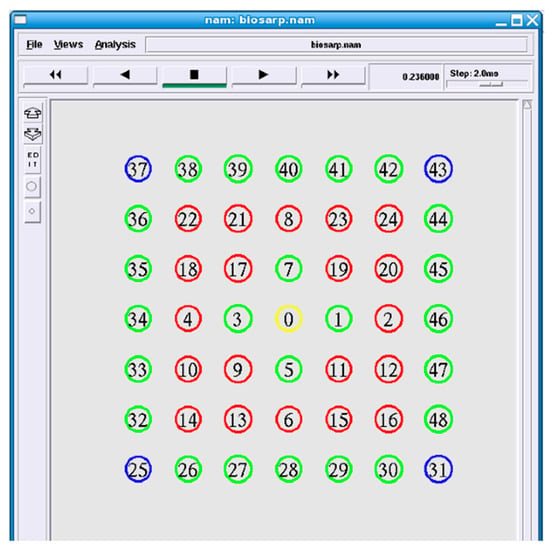
Figure 4.
Scenario with 50 nodes and 20 malicious nodes.

Figure 5.
Scenario with 121 nodes and 20 malicious nodes.
The simulation results were generated by running multiple simulations with variations in scenarios and with different routing protocols, which are E-BIOSARP, BIOSARP, SRTLD, and the novel P-BIOSARP.
The metrics for performance evaluation are battec, packet delivery ratio (PDR), and traffic overhead. First, battec is calculated based on the difference between batti and battce by Equation (5) [24,33].
battec = batti − battce
The PDR of the data packet is calculated by Equation (6) based on , the total number of packets sent by the source node or nodes, divided by , the total number of data packets received at the destination node [24,35,38].
The packet overhead (PO) is estimated by Equation (7), where total data packets received at the destination node is divided by the total control packets TCP [24,35,38].
5. Results
The results shown in Table 3 are the average values generated by implementing the power-aware biologically inspired self-organized routing protocol (P-BIOSARP), the encryption-enabled biologically inspired self-organized routing protocol (E-BIOSARP), the biologically inspired self-organized routing protocol (BIOSARP), and the secure real-time routing protocol with load distribution (SRTLD) in NS-2. A total of about ninety-two experiments were performed with different scenarios, which included initially varying the number of nodes, using different packet rates, increasing the node speed, using mobile nodes, and on the security side, injecting malicious nodes.

Table 3.
Experimental Results.
In addition to the results given in Table 3, the time complexity of the algorithm with the communication results is
where the difference in sending and receiving the RTR packet is 0.00325 s.
| s | 14.58793 | _8_ | RTR | --- | 41 | biosarp |
| r | 14.59118 | _7_ | RTR | --- | 41 | biosarp |
The energy comparison between P-BIOSARP and E-BIOSARP is shown in Figure 6, where the number of nodes is changed from 8 to 50 and then to 121 while keeping the packet rate at 3.6 packets per second (p/s), and the simulation was run for 300 s. In the scenario with a total of eight nodes, the number of malicious nodes is four, namely, 2, 4, 6, and 7, as shown in Figure 3. In the scenarios with 50, as shown in Figure 4, and 121 nodes, the number of malicious nodes is increased to twenty, namely, 2, 4, 6, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, and 24, as shown in Figure 5.
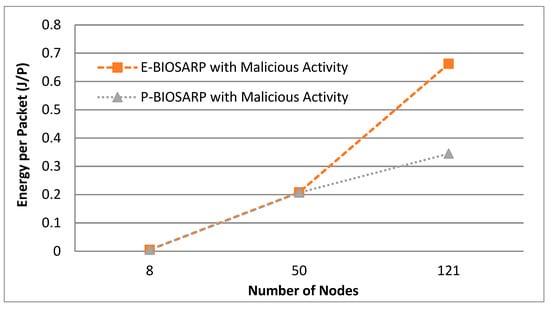
Figure 6.
battec vs. Number of Nodes Comparison between P-BIOSARP and E-BIOSARP.
Figure 7 shows the results of experimentation with the same scenario and compares the PDR between P-BIOSARP and E-BIOSARP.
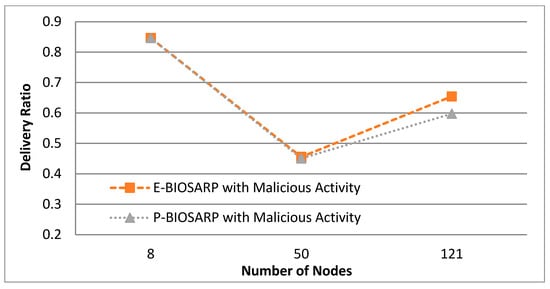
Figure 7.
PDR vs. Number of Nodes Comparison between P-BIOSARP and E-BIOSARP.
The PO, that is, the control packets required to transfer a single data packet, between P-BIOSARP and E-BIOSARP is shown in Figure 8.
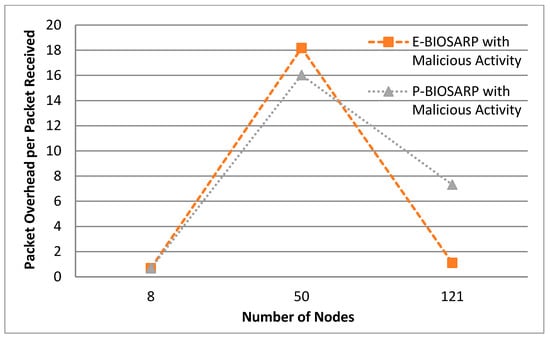
Figure 8.
PO vs. Number of Nodes Comparison between P-BIOSARP and E-BIOSARP.
In addition to varying the number of nodes in scenarios, the energy comparison between P-BIOSARP and E-BIOSARP was compared, the results of which are shown in Figure 9, by increasing malicious nodes in the network, as given in Figure 5. The number of malicious nodes was altered from 4 (malicious node IDs 22, 24, 14, and 16) to 8 (malicious node IDs 22, 24, 14, 16, 21, 23, 15, and 13), 12 (malicious node IDs 22, 24, 14, 16, 21, 23, 15, 13, 18, 10, 11, and 19), 16 (malicious node IDs 22, 24, 14, 16, 21, 23, 15, 13, 18, 10, 11, 19, 4, 8, 2, and 6), and then 20 (malicious node IDs 22, 24, 14, 16, 21, 23, 15, 13, 18, 10, 11, 19, 4, 8, 2, 6, 9, 17, 12, and 20), while the number of nodes was fixed at 121, the packet rate was fixed at 3.6 p/s, and the total time was 300 s.
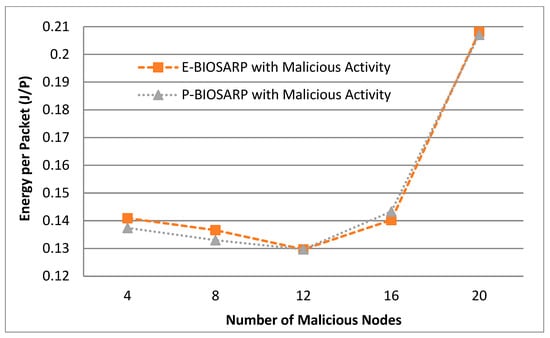
Figure 9.
battec vs. Number of Malicious Nodes Comparison between P-BIOSARP and E-BIOSARP.
Figure 10 shows the results of experimentation with the same scenario to compare the PDR between P-BIOSARP and E-BIOSARP. The PO comparison between P-BIOSARP and E-BIOSARP is shown in Figure 11.
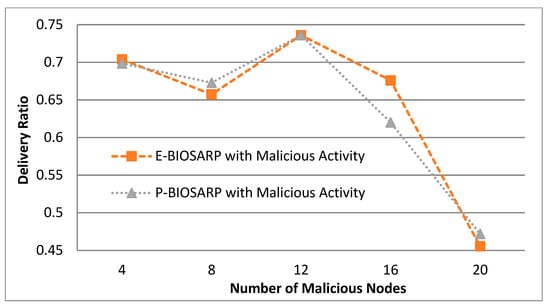
Figure 10.
PDR vs. Number of Malicious Nodes Comparison between P-BIOSARP and E-BIOSARP.
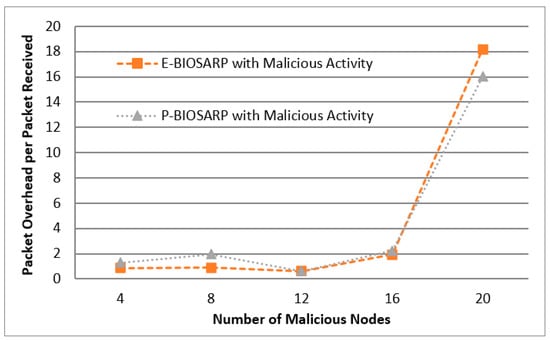
Figure 11.
PO vs. Number of Malicious Nodes Comparison between P-BIOSARP and E-BIOSARP.
Furthermore, the scenarios were varied with different packet rates, starting with 0.33 per second, followed by 0.7/s, 1.5/s, 2.2/s, and 3.6/s. In these scenarios, the number of total nodes was fixed to 121, of which 20 were malicious nodes (IDs 22, 24, 14, 16, 21, 23, 15, 13, 18, 10, 11, 19, 4, 8, 2, 6, 9, 17, 12, and 20), as shown in Figure 5, and the simulation was run for 300 s. The energy comparison between P-BIOSARP, E-BIOSARP, BIOSARP, and SRTLD is shown in Figure 12.
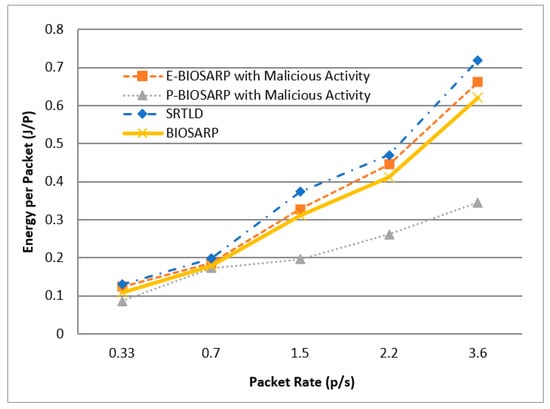
Figure 12.
battec vs. Packet Rate Comparison between P-BIOSARP, E-BIOSARP, SRTLD, and BI-OSARP.
The results of experimentation with the same scenario to compare the PDR between P-BIOSARP, E-BIOSARP, BIOSARP, and SRTLD are shown in Figure 13. The PO comparison between P-BIOSARP, E-BIOSARP, BIOSARP, and SRTLD is shown in Figure 14.
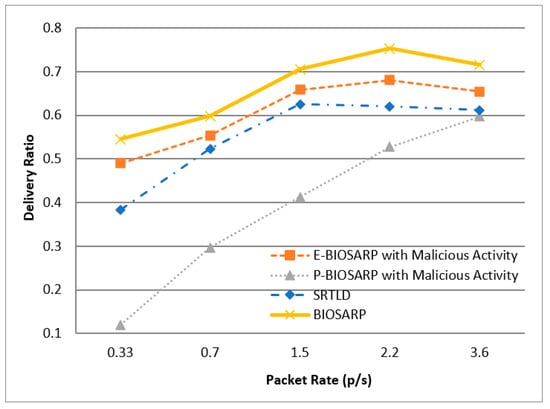
Figure 13.
PDR vs. Packet Rate Comparison between P-BIOSARP, E-BIOSARP, SRTLD, and BI-OSARP.
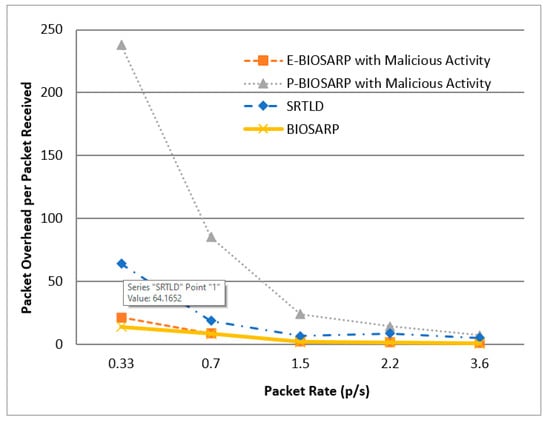
Figure 14.
PO vs. Packet Rate Comparison between P-BIOSARP, E-BIOSARP, SRTLD, and BIOSARP.
P-BIOSARP and E-BIOSARP were further tested under full load with a scenario that included 20 malicious nodes (IDs 22, 24, 14, 16, 21, 23, 15, 13, 18, 10, 11, 19, 4, 8, 2, 6, 9, 17, 12, and 20) and 12 mobile nodes, where 4 are source nodes that generate the data. The results were obtained with different packet rates, starting with 0.33 per second, followed by 1.5/s, 2.2/s, and 3.6/s. In these scenarios, the number of total nodes was fixed to 121, as shown in Figure 5, and the simulation was run for 300 s. The energy comparison between P-BIOSARP and E-BIOSARP is shown in Figure 15.
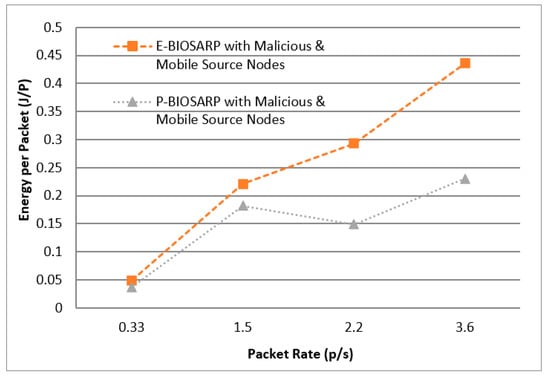
Figure 15.
battec vs. Packet Rate Comparison between P-BIOSARP, E- BIOSARP with Malicious Nodes and with Mobility.
The results of experimentation with the same scenario to compare the PDR between P-BIOSARP and E-BIOSARP are shown in Figure 16. The PO comparison between P P-BIOSARP and E-BIOSARP is shown in Figure 17.
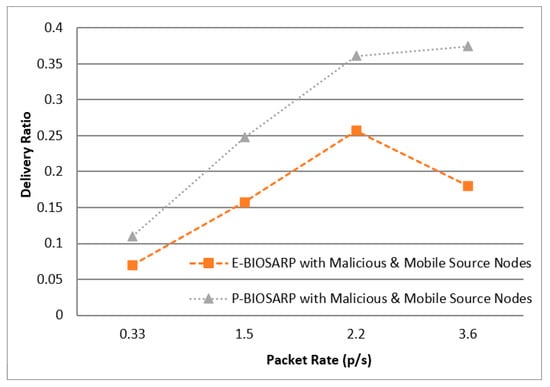
Figure 16.
PDR vs. Packet Rate Comparison between P-BIOSARP, E- BIOSARP with Malicious Nodes and with Mobility.
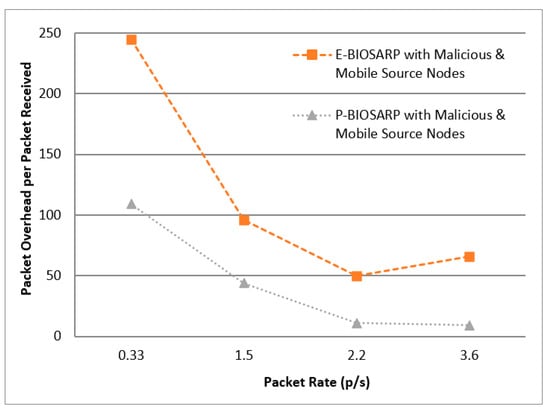
Figure 17.
PO vs. Packet Rate Comparison between P-BIOSARP and E-BIOSARP with Malicious Nodes and with Mobility.
6. Discussion
The results in figures and also in tabular form in Table 3 demonstrate that the power consumption is reduced when using P-BIOSARP because, as described in the methodology (Section 3), the maximum weight is given to the energy parameter when calculating and making decisions with the most optimal node. The best node is selected from the neighboring nodes, with the node with the highest remaining battery chosen over the rest.
In Figure 6, the battec of P-BIOSARP is far better than E-BIOSARP when the simulation was run with 121 nodes for 300 s. This shows that if the network is increased with more nodes and needs to be deployed for a longer period, battec will become increasingly better. In addition, the PDR is a bit lower in Figure 7, and the traffic overhead is higher in Figure 8, which is a shortcoming of giving a large rise to a single property, and it eventually depends on the application requirements.
Furthermore, in the scenario where the malicious nodes are increased from 4 to 20, on average, battec, as shown in Figure 9, is less required with P-BIOSARP than with E-BIOSARP. However, the PDR in Figure 10 and traffic overhead in Figure 11 are a little bit higher. This shows that when a high level of security is required, parameters that can raise the quality of traffic all need to be enabled.
In the scenario with a maximum of 121 nodes in an 80 m2 area and run for 300 s where the packet rate increases from 0.33/s to 3.6/s, Figure 12 shows that there is a significant difference in battec, which is an average of 17% less with P-BIOSARP compared to the E-BIOSARP, BIOSARP, and SRTLD routing protocols. The PDR is lower, as shown in Figure 13, and PO is high, as shown in Figure 14, with P-BIOSARP. Analyzing the trends in Figure 12, Figure 13, and Figure 14 shows that with more traffic in the network, P-BIOSARP performs much better in all aspects, whether battec, PDR, or PO is considered.
In the case where the scenario is configured with 20 malicious nodes and 12 mobile nodes with source nodes, meaning with a full load on the network routing protocols to establish and route the data packets, the P-BIOSARP results are far better than those of the other routing protocols in terms of battec, as shown in Figure 15, PDR, as shown in Figure 16, and PO, as shown in Figure 17. Hence, the results prove that when the network is heavily loaded and needs to save energy, P-BIOSARP should be employed. Otherwise, when high quality is required for data routing, parameters related to reliability should be considered when making the optimal decision. P-BIOSARP is able to secure the FSN from spoofing, HELLO flood attacks, Sybil attacks, eavesdropping, selective forwarding, acknowledgment spoofing, brute-force or exhaustive key search, replaying or altering of routing information, data-tampering attacks, and cloning, as it is the enhanced version of [38].
7. Conclusions
This paper proposes a power-aware ant colony optimization (ACO)-based autonomous secure routing protocol for FSNs in mobile surveillance systems. The decision of the next hop to the destination is based on a probability value that is calculated based on three parameters. The remaining battery power is given the maximum weight in P-BIOSARP, and a lower weight is assigned to the link quality and the packet delay. As a result, the optimal choice of the neighboring flying sensor node is mainly related to the remaining battery power, but the link quality and delay are also taken under consideration with less priority. P-BIOSARP transfers data packets securely by encrypting important header information to preserve privacy. FSN scenarios were configured with variations in the number of mobile nodes and malicious nodes. The experimental analysis supports that P-BIOSARP consumes 17% less energy with a better delivery ratio and with less data packet overhead compared to the E-BIOSARP, BIOSARP, and SRTLD routing protocols. Moreover, the results show that P-BIOSARP performance rises with the increase in time, nodes, and the packet rate.
In the future, P-BIOSARP will be tested on real flying sensor nodes by varying the parameter weights. Furthermore, additional testing will be performed based on the distribution function.
Author Contributions
Conceptualization, I.A. and K.S.; methodology, K.S.; software, K.S.; validation, I.A. and K.S.; formal analysis, K.S.; investigation, K.S.; resources, I.A. and K.S.; writing—original draft preparation, K.S.; writing—review and editing, I.A. and K.S.; visualization, I.A. and K.S.; supervision, I.A. and K.S.; project administration, I.A. and K.S.; funding acquisition, I.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research work was funded by Institutional Fund Projects under grant no. IFPIP-1254-611-1442. Therefore, the authors gratefully acknowledge technical and financial support from the Ministry of Education and King Abdulaziz University, DSR, Jeddah, Saudi Arabia.
Data Availability Statement
Not applicable.
Acknowledgments
This research work was funded by Institutional Fund Projects under grant no. (IFPIP-1254-611-1442). Therefore, the authors gratefully acknowledge technical and financial support from the Ministry of Education and King Abdulaziz University, DSR, Jeddah, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Akhtar, M.N.; Shaikh, A.J.; Khan, A.; Awais, H.; Bakar, E.A.; Othman, A.R. Smart Sensing with Edge Computing in Precision Agriculture for Soil Assessment and Heavy Metal Monitoring: A Review. Agriculture 2021, 11, 475. [Google Scholar] [CrossRef]
- BinDhim, N.F.; Althumiri, N.A.; Basyouni, M.H.; Alageel, A.A.; Alghnam, S.; Al-Qunaibet, A.M.; Almubarak, R.A.; Aldhukair, S.; Ad-Dab’bagh, Y. Saudi Arabia Mental Health Surveillance System (MHSS): Mental health trends amid COVID-19 and comparison with pre-COVID-19 trends. Eur. J. Psychotraumatol. 2021, 12, 1875642. [Google Scholar] [CrossRef] [PubMed]
- Ullah, I.; Alomari, A.; Ul Amin, N.; Khan, M.A.; Khattak, H. An Energy Efficient and Formally Secured Certificate-Based Signcryption for Wireless Body Area Networks with the Internet of Things. Electronics 2019, 8, 1171. [Google Scholar] [CrossRef]
- Keshaviah, A.; Hu, X.C.; Henry, M. Developing a Flexible National Wastewater Surveillance System for COVID-19 and Beyond. Environ. Health Perspect. 2021, 129, 045002. [Google Scholar] [CrossRef] [PubMed]
- Ke, R.; Zhuang, Y.; Pu, Z.; Wang, Y. A Smart, Efficient, and Reliable Parking Surveillance System With Edge Artificial Intelligence on IoT Devices. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4962–4974. [Google Scholar] [CrossRef]
- Pramanik, A.; Sarkar, S.; Maiti, J. A real-time video surveillance system for traffic pre-events detection. Accid. Anal. Prev. 2021, 154, 106019. [Google Scholar] [CrossRef]
- Jha, S.; Seo, C.; Yang, E.; Joshi, G.P. Real time object detection and trackingsystem for video surveillance system. Multimed. Tools Appl. 2021, 80, 3981–3996. [Google Scholar] [CrossRef]
- Janbandhu, A.C.; Sharma, S.; Ansari, I.A.; Bajaj, V. Drone-based vision system: Surveillance during calamities. In Computational Intelligence Based Solutions for Vision Systems; IOP Publishing Ltd.: Bristol, UK, 2022. [Google Scholar]
- Srivastava, A.; Badal, T.; Garg, A.; Vidyarthi, A.; Singh, R. Recognizing human violent action using drone surveillance within real-time proximity. J. Real-Time Image Process. 2021, 18, 1851–1863. [Google Scholar] [CrossRef]
- Santamaria, A.F.; Raimondo, P.; Tropea, M.; De Rango, F.; Aiello, C. An IoT Surveillance System Based on a Decentralised Architecture. Sensors 2019, 19, 1469. [Google Scholar] [CrossRef]
- Sukhavasi, S.B.; Sukhavasi, S.B.; Elleithy, K.; Abuzneid, S.; Elleithy, A. CMOS Image Sensors in Surveillance System Applications. Sensors 2021, 21, 488. [Google Scholar] [CrossRef]
- Ouni, R.; Saleem, K. Framework for Sustainable Wireless Sensor Network Based Environmental Monitoring. Sustainability 2022, 14, 8356. [Google Scholar] [CrossRef]
- Amiri-Zarandi, M.; Hazrati Fard, M.; Yousefinaghani, S.; Kaviani, M.; Dara, R. A Platform Approach to Smart Farm Information Processing. Agriculture 2022, 12, 838. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Żywiołek, J.; Ullah, I. Swarm of UAVs for Network Management in 6G: A Technical Review. IEEE Trans. Netw. Serv. Manag. 2022, 1-1. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G. Routing Protocols in Wireless Sensor Networks. In Computational Intelligence in Sensor Networks; Mishra, B.B., Dehuri, S., Panigrahi, B.K., Nayak, A.K., Mishra, B.S.P., Das, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; pp. 215–248. [Google Scholar]
- Mohamed, R.E.; Saleh, A.I.; Abdelrazzak, M.; Samra, A.S. Survey on Wireless Sensor Network Applications and Energy Efficient Routing Protocols. Wirel. Pers. Commun. 2018, 101, 1019–1055. [Google Scholar] [CrossRef]
- Guleria, K.; Verma, A.K. Comprehensive review for energy efficient hierarchical routing protocols on wireless sensor networks. Wirel. Netw. 2019, 25, 1159–1183. [Google Scholar] [CrossRef]
- Yue, Y.-G.; He, P. A comprehensive survey on the reliability of mobile wireless sensor networks: Taxonomy, challenges, and future directions. Inf. Fusion 2018, 44, 188–204. [Google Scholar] [CrossRef]
- Rady, A.; El-Rabaie, E.L.-S.M.; Shokair, M.; Abdel-Salam, N. Comprehensive survey of routing protocols for Mobile Wireless Sensor Networks. Int. J. Commun. Syst. 2021, 34, e4942. [Google Scholar] [CrossRef]
- Kumaran, K.M.; Chinnadurai, M. A Competent Ad-hoc Sensor Routing Protocol for Energy Efficiency in Mobile Wireless Sensor Networks. Wirel. Pers. Commun. 2021, 116, 829–844. [Google Scholar] [CrossRef]
- Del-Valle-Soto, C.; Mex-Perera, C.; Nolazco-Flores, J.A.; Velázquez, R.; Rossa-Sierra, A. Wireless Sensor Network Energy Model and Its Use in the Optimization of Routing Protocols. Energies 2020, 13, 728. [Google Scholar] [CrossRef]
- Sara, G.S.; Sridharan, D. Routing in mobile wireless sensor network: A survey. Telecommun. Syst. 2014, 57, 51–79. [Google Scholar] [CrossRef]
- Khan, M.A.; Qureshi, I.M.; Khanzada, F. A Hybrid Communication Scheme for Efficient and Low-Cost Deployment of Future Flying Ad-Hoc Network (FANET). Drones 2019, 3, 16. [Google Scholar] [CrossRef]
- Saleem, K.; Fisal, N.; Al-Muhtadi, J. Empirical Studies of Bio-Inspired Self-Organized Secure Autonomous Routing Protocol. IEEE Sens. J. 2014, 14, 2232–2239. [Google Scholar] [CrossRef]
- Hosen, A.S.M.S.; Cho, G.H. An Energy Centric Cluster-Based Routing Protocol for Wireless Sensor Networks. Sensors 2018, 18, 1520. [Google Scholar] [CrossRef]
- Liu, Y.; Wu, Q.; Zhao, T.; Tie, Y.; Bai, F.; Jin, M. An Improved Energy-Efficient Routing Protocol for Wireless Sensor Networks. Sensors 2019, 19, 4579. [Google Scholar] [CrossRef] [PubMed]
- Behera, T.M.; Mohapatra, S.K.; Samal, U.C.; Khan, M.S.; Daneshmand, M.; Gandomi, A.H. Residual Energy-Based Cluster-Head Selection in WSNs for IoT Application. IEEE Internet Things J. 2019, 6, 5132–5139. [Google Scholar] [CrossRef]
- Rodríguez, A.; Del-Valle-Soto, C.; Velázquez, R. Energy-Efficient Clustering Routing Protocol for Wireless Sensor Networks Based on Yellow Saddle Goatfish Algorithm. Mathematics 2020, 8, 1515. [Google Scholar] [CrossRef]
- Fanian, F.; Kuchaki Rafsanjani, M. Cluster-based routing protocols in wireless sensor networks: A survey based on methodology. J. Netw. Comput. Appl. 2019, 142, 111–142. [Google Scholar] [CrossRef]
- Zafar, S.; Bashir, A.; Chaudhry, S.A. Mobility-Aware Hierarchical Clustering in Mobile Wireless Sensor Networks. IEEE Access 2019, 7, 20394–20403. [Google Scholar] [CrossRef]
- Saleem, K.; Chaudhry, J.; Orgun, M.A.; Al-Muhtadi, J. A bio-inspired secure IPv6 communication protocol for Internet of Things. In Proceedings of the 2017 Eleventh International Conference on Sensing Technology (ICST), Sydney, Australia, 4–6 December 2017; pp. 1–6. [Google Scholar]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.-J. An Improved Routing Schema with Special Clustering Using PSO Algorithm for Heterogeneous Wireless Sensor Network. Sensors 2019, 19, 671. [Google Scholar] [CrossRef]
- Rathee, M.; Kumar, S.; Gandomi, A.H.; Dilip, K.; Balusamy, B.; Patan, R. Ant Colony Optimization Based Quality of Service Aware Energy Balancing Secure Routing Algorithm for Wireless Sensor Networks. IEEE Trans. Eng. Manag. 2021, 68, 170–182. [Google Scholar] [CrossRef]
- Wheeb, A.H.; Nordin, R.; Samah, A.A.; Alsharif, M.H.; Khan, M.A. Topology-Based Routing Protocols and Mobility Models for Flying Ad Hoc Networks: A Contemporary Review and Future Research Directions. Drones 2022, 6, 9. [Google Scholar] [CrossRef]
- Ahmed, A.A.; Fisal, N.F. Secure real-time routing protocol with load distribution in wireless sensor networks. Secur. Commun. Netw. 2011, 4, 839–869. [Google Scholar] [CrossRef]
- Saleem, K.; Fisal, N.; Baharudin, M.A.; Ahmed, A.A.; Hafizah, S.; Kamilah, S. Ant colony inspired self-optimized routing protocol based on cross layer architecture for wireless sensor networks. WSEAS Trans. Commun. 2010, 9, 669–678. [Google Scholar]
- Saleem, K.; Fisal, N.; Hafizah, S.; Rashid, R.A. An Intelligent Information Security Mechanism for the Network Layer of WSN: BIOSARP; Springer: Berlin/Heidelberg, Germany, 2011; pp. 118–126. [Google Scholar]
- Saleem, K.; Derhab, A.; Orgun, M.A.; Al-Muhtadi, J.; Rodrigues, J.J.P.C.; Khalil, M.S.; Ali Ahmed, A. Cost-Effective Encryption-Based Autonomous Routing Protocol for Efficient and Secure Wireless Sensor Networks. Sensors 2016, 16, 460. [Google Scholar] [CrossRef] [PubMed]
- Rubeaai, S.F.A.; Abd, M.A.; Singh, B.K.; Tepe, K.E. 3D Real-Time Routing Protocol With Tunable Parameters for Wireless Sensor Networks. IEEE Sens. J. 2016, 16, 843–853. [Google Scholar] [CrossRef]
- López-Matencio, P. An ACOR-Based Multi-Objective WSN Deployment Example for Lunar Surveying. Sensors 2016, 16, 209. [Google Scholar] [CrossRef]
- Rupérez Cañas, D.; Sandoval Orozco, A.L.; García Villalba, L.J.; Kim, T.-h. A Family of ACO Routing Protocols for Mobile Ad Hoc Networks. Sensors 2017, 17, 1179. [Google Scholar] [CrossRef]
- Zou, Z.; Qian, Y. Wireless sensor network routing method based on improved ant colony algorithm. J. Ambient Intell. Humaniz. Comput. 2019, 10, 991–998. [Google Scholar] [CrossRef]
- Khobahi, S.; Soltanalian, M.; Jiang, F.; Swindlehurst, A.L. Optimized Transmission for Parameter Estimation in Wireless Sensor Networks. IEEE Trans. Signal Inf. Processing Over Netw. 2020, 6, 35–47. [Google Scholar] [CrossRef]
- Jain, R. Ant Colony Inspired Energy Efficient OLSR (AC-OLSR) Routing Protocol in MANETS. Wirel. Pers. Commun. 2022, 124, 3307–3320. [Google Scholar] [CrossRef]
- Mokrenko, O.; Vergara-Gallego, M.; Lombardi, W.; Lesecq, S.; Albea, C. WSN power management with battery capacity estimation. In Proceedings of the 2015 IEEE 13th International New Circuits and Systems Conference (NEWCAS), Grenoble, France, 7–10 June 2015; pp. 1–4. [Google Scholar]
- Chen, S.; Yao, J.; Wu, Y. Analysis of the Power Consumption for Wireless Sensor Network Node Based on Zigbee. Procedia Eng. 2012, 29, 1994–1998. [Google Scholar] [CrossRef]
- Du, W.; Mieyeville, F.; Navarro, D. Modeling Energy Consumption of Wireless Sensor Networks by SystemC. In Proceedings of the 2010 Fifth International Conference on Systems and Networks Communications, Nice, France, 22–27 August 2010; pp. 94–98. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).