Search and Rescue in a Maze-like Environment with Ant and Dijkstra Algorithms
Abstract
1. Introduction
2. Background
2.1. Indoor Search and Rescue (SAR) Operations for Swarms of Drones
2.1.1. Swarm (Multi-Agent) SAR Operations
2.1.2. UAVs in SAR Operations
2.1.3. Path Planning in Maze-like Environments
2.1.4. Communication Routing
2.1.5. Summary
2.2. Wireless Sensor Networks (WSN) in SAR for Swarms of Drones
2.2.1. Mobile Wireless Networks
2.2.2. Mobile Wireless Sensor Networks (MWSN) in SAR
2.2.3. UAVs as Nodes in Mobile Networks
2.3. Nature-Inspired Approaches to Finding the Shortest Path
2.3.1. Deterministic versus Heuristic Search
2.3.2. The Dijkstra Algorithm
- An array holding all edges costs (distance(i)) where all values are initiated to infinity except the first value (distance(source)), which is set to zero.
- An array that contains all the nodes that have been visited during the search, which, by the end, contains all nodes in the graph (denoted as visited). Then, the algorithm proceeds as follows:
- While the visited array does not contain all nodes, we take node v with the least distance(v). Initially, it will be the source because distance(source) is set to zero.
- Node v is then added to the visited array, indicating that it has been visited.
- Update distance values of adjacent nodes (u) to the node v.
- Ifthen there is a new minimal distance founded for u, so distance(u) is updated with the new minimal value. Otherwise, no changes are made to distance(u). Finally, after the algorithm has visited all nodes in the graph and the smallest distance to each node is found, distance will now contain the shortest path tree from the source node [95].
2.3.3. Ant Colony Optimization (ACO)
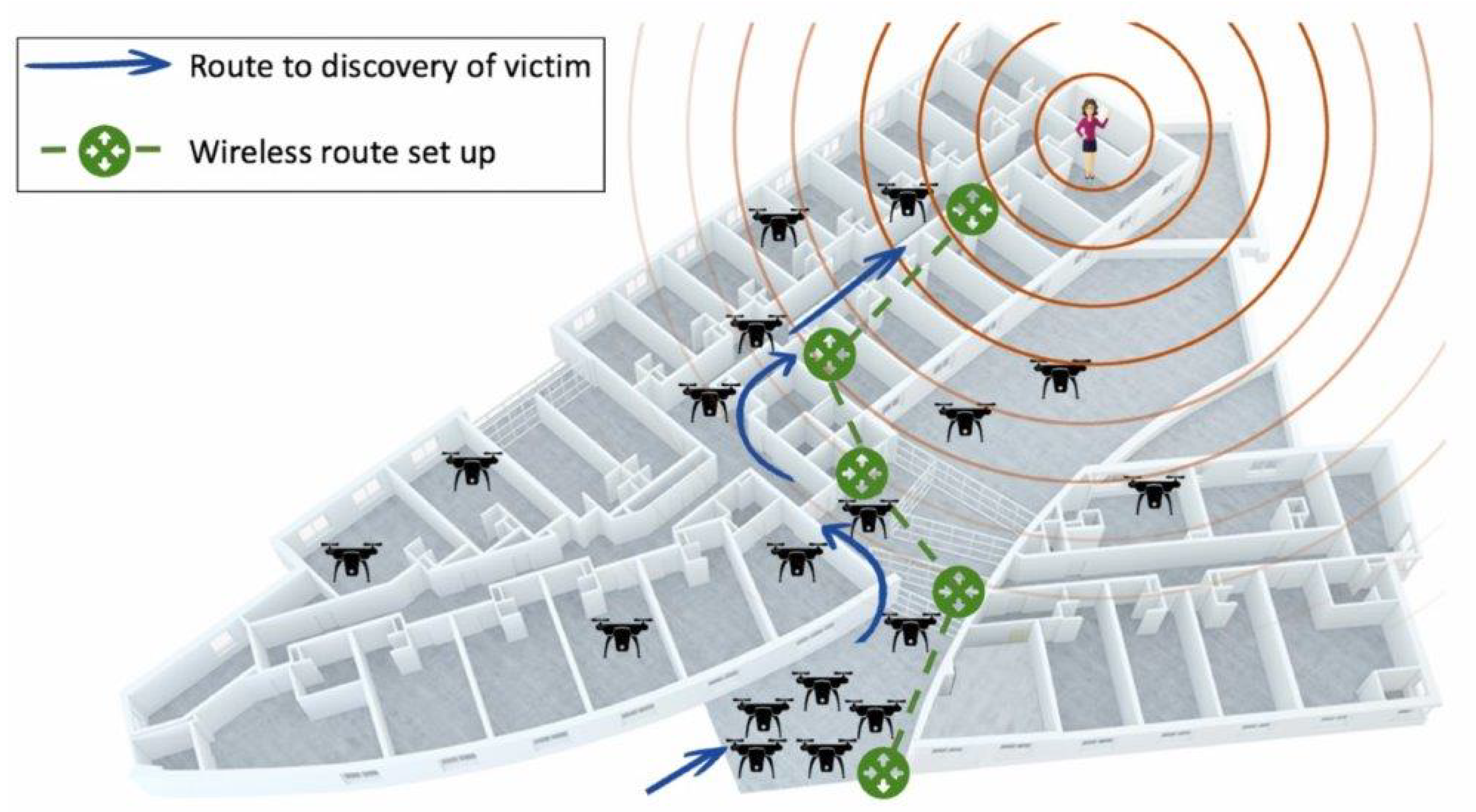
3. Search and Rescue in Maze-like Environments
3.1. Modeling the Problem
3.1.1. Indoor Search and Rescue Operations: A Maze Exploration Problem
3.1.2. The Physical Accessibility
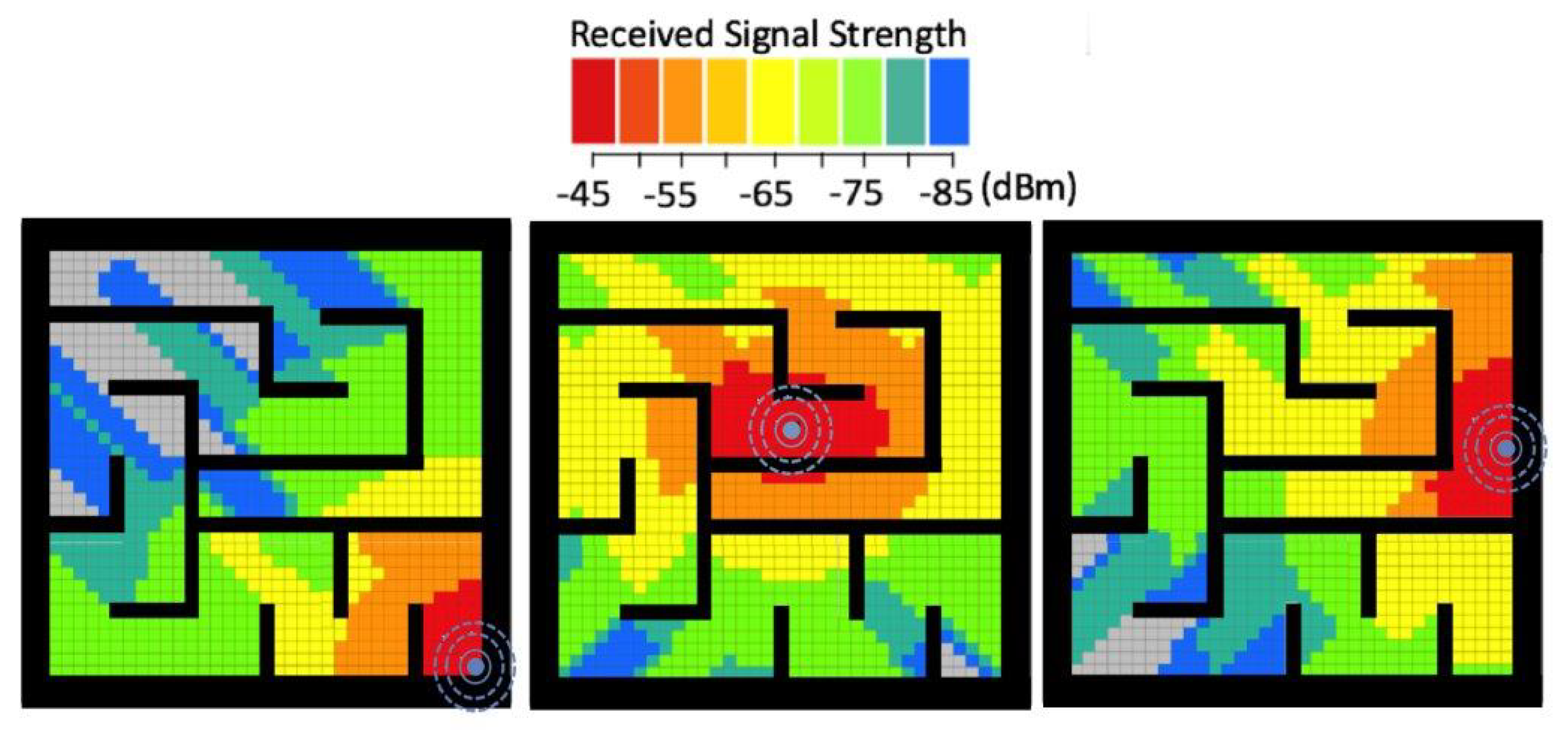
3.1.3. The Signal Accessibility
3.1.4. Modeling the Drones
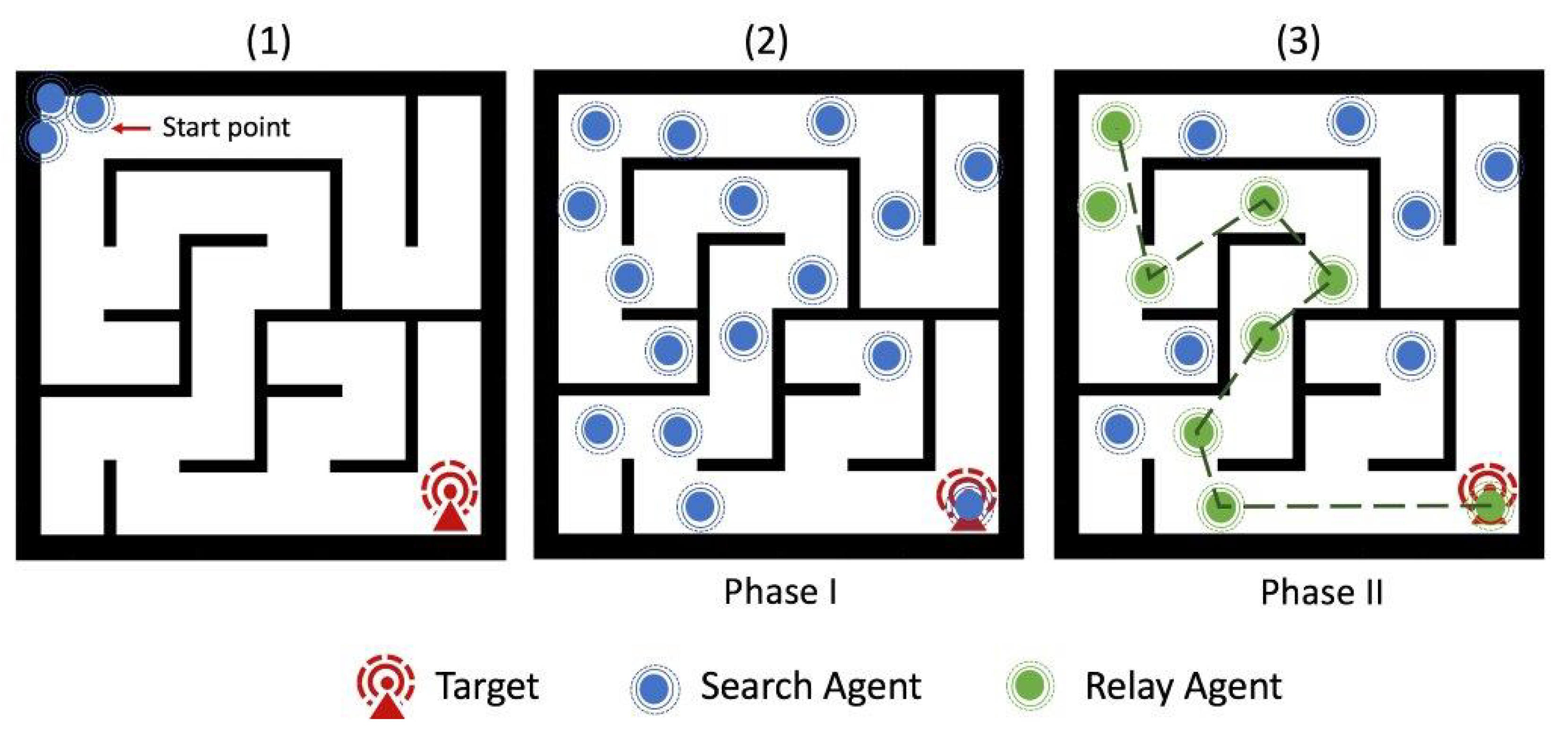
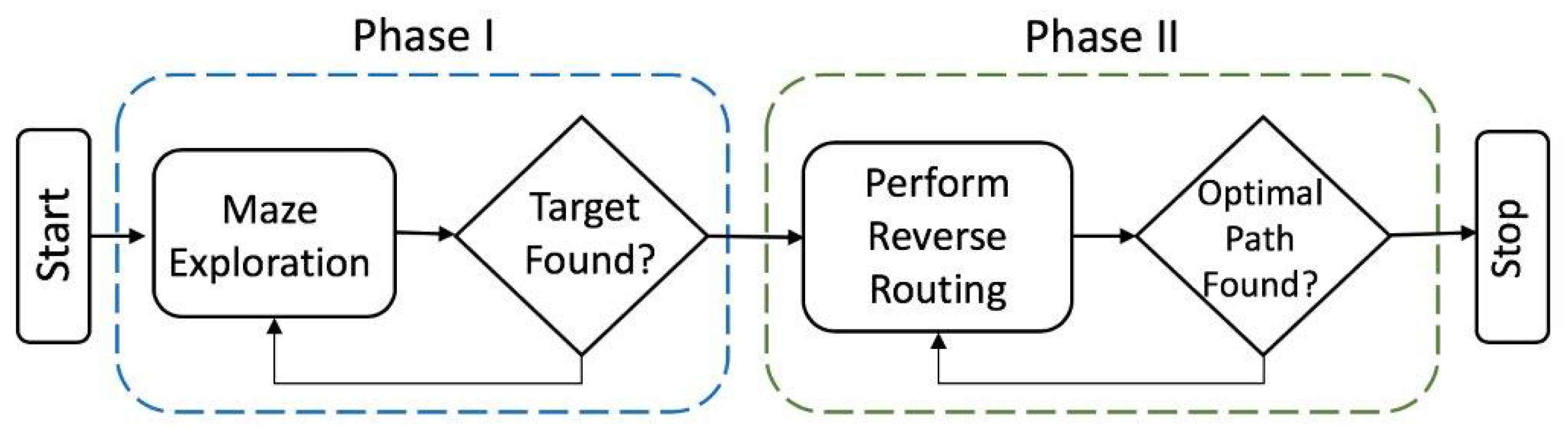
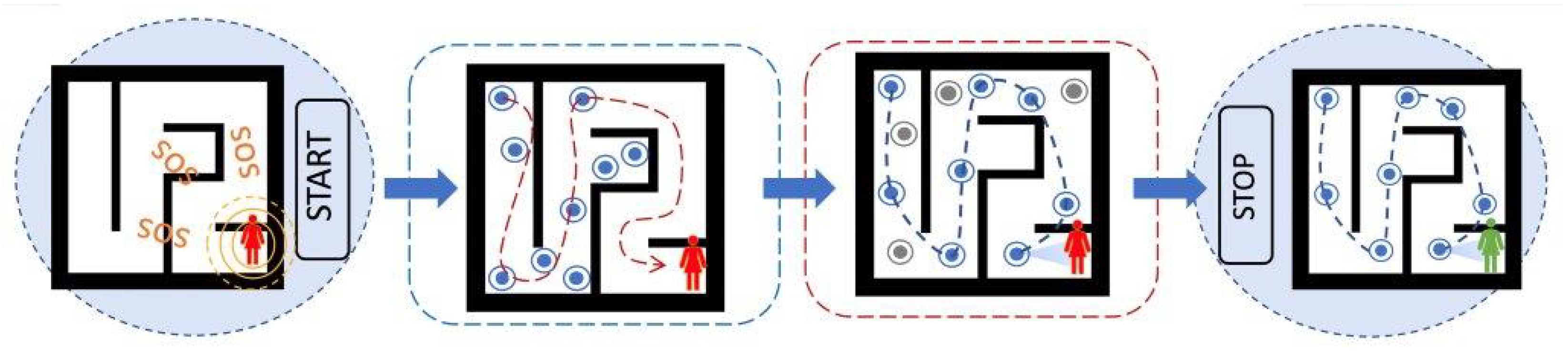
3.2. Search, and Rescue: A Problem of Two Sequential Phases
3.2.1. Phase I (Search): Maze Exploration
3.2.2. Phase II (Rescue): Signal Routing and Victim Extraction
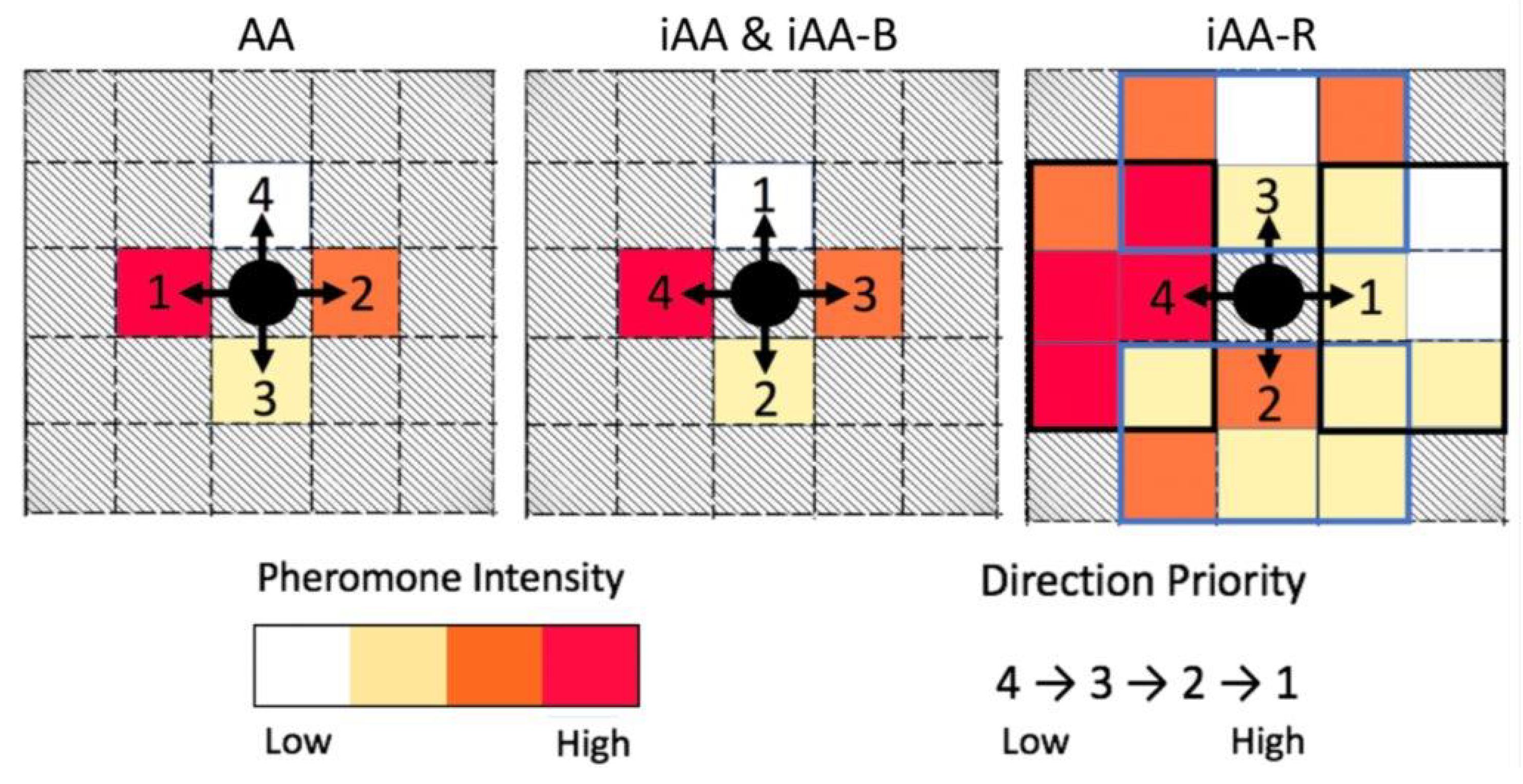
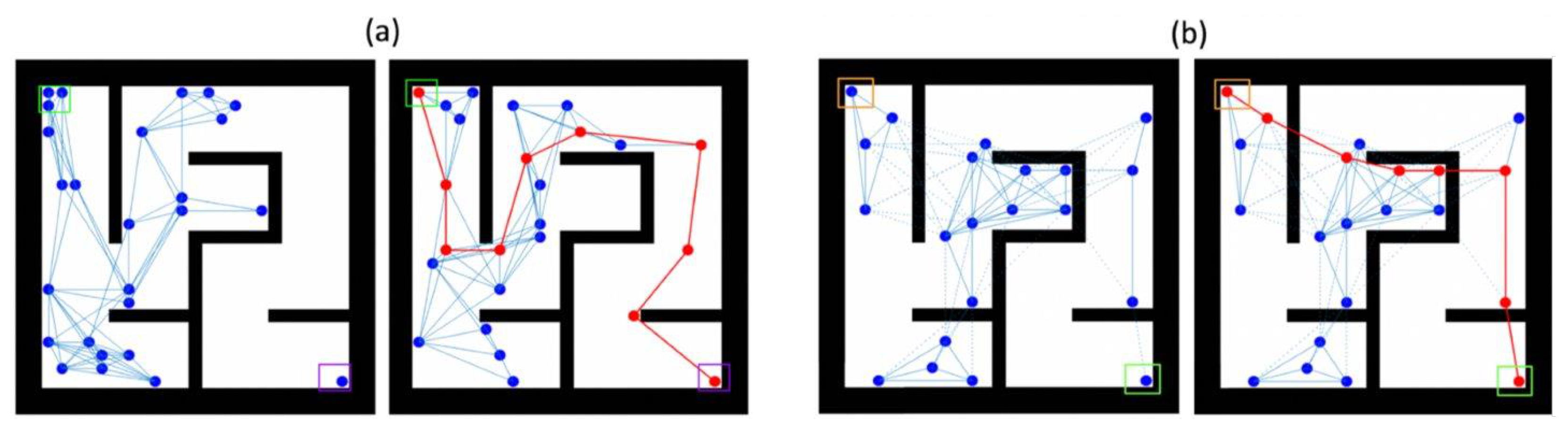
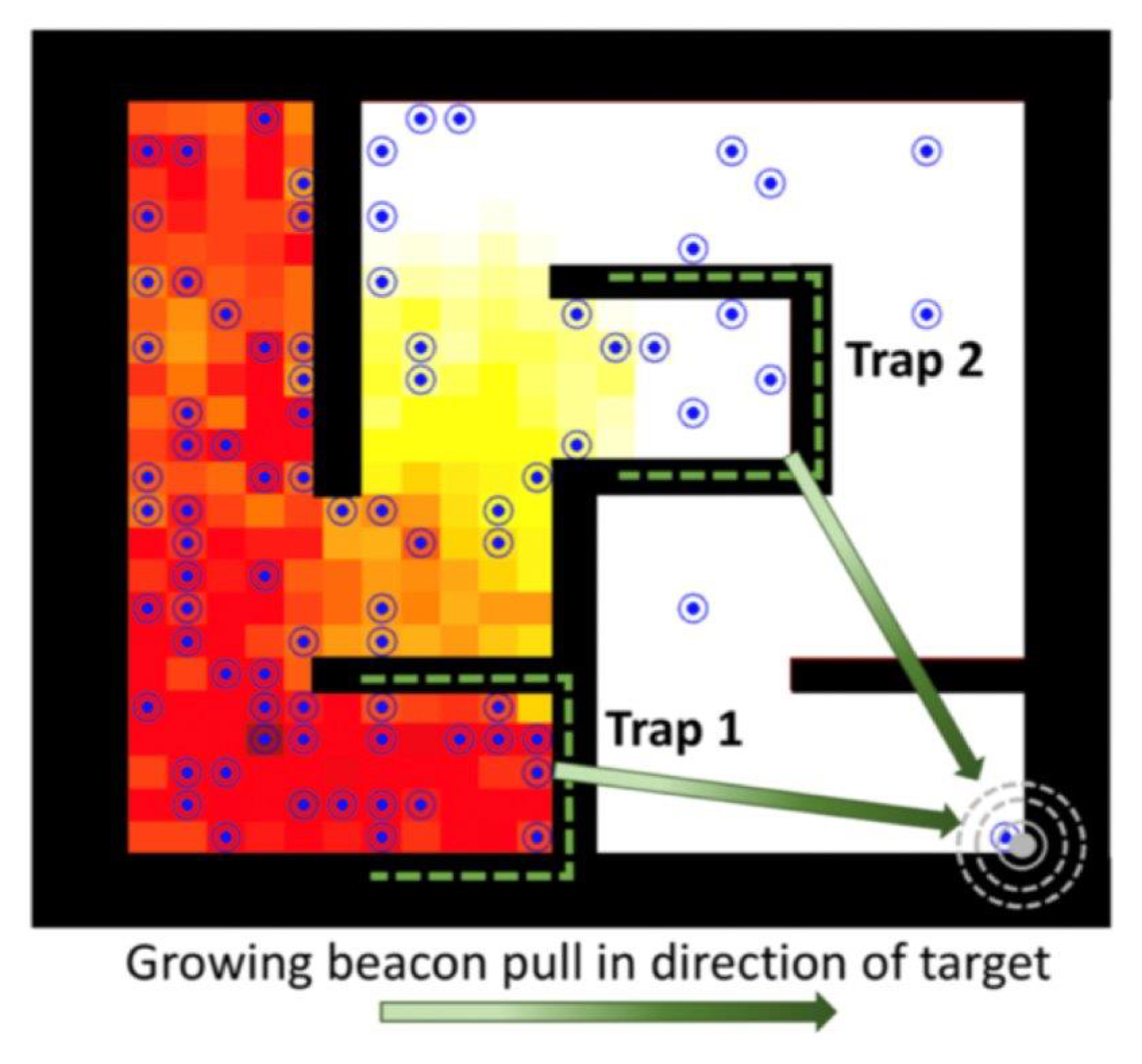
3.3. Solving Phase I (Search): Maze Exploration
3.3.1. The Approach
3.3.2. The Algorithm
|
 |
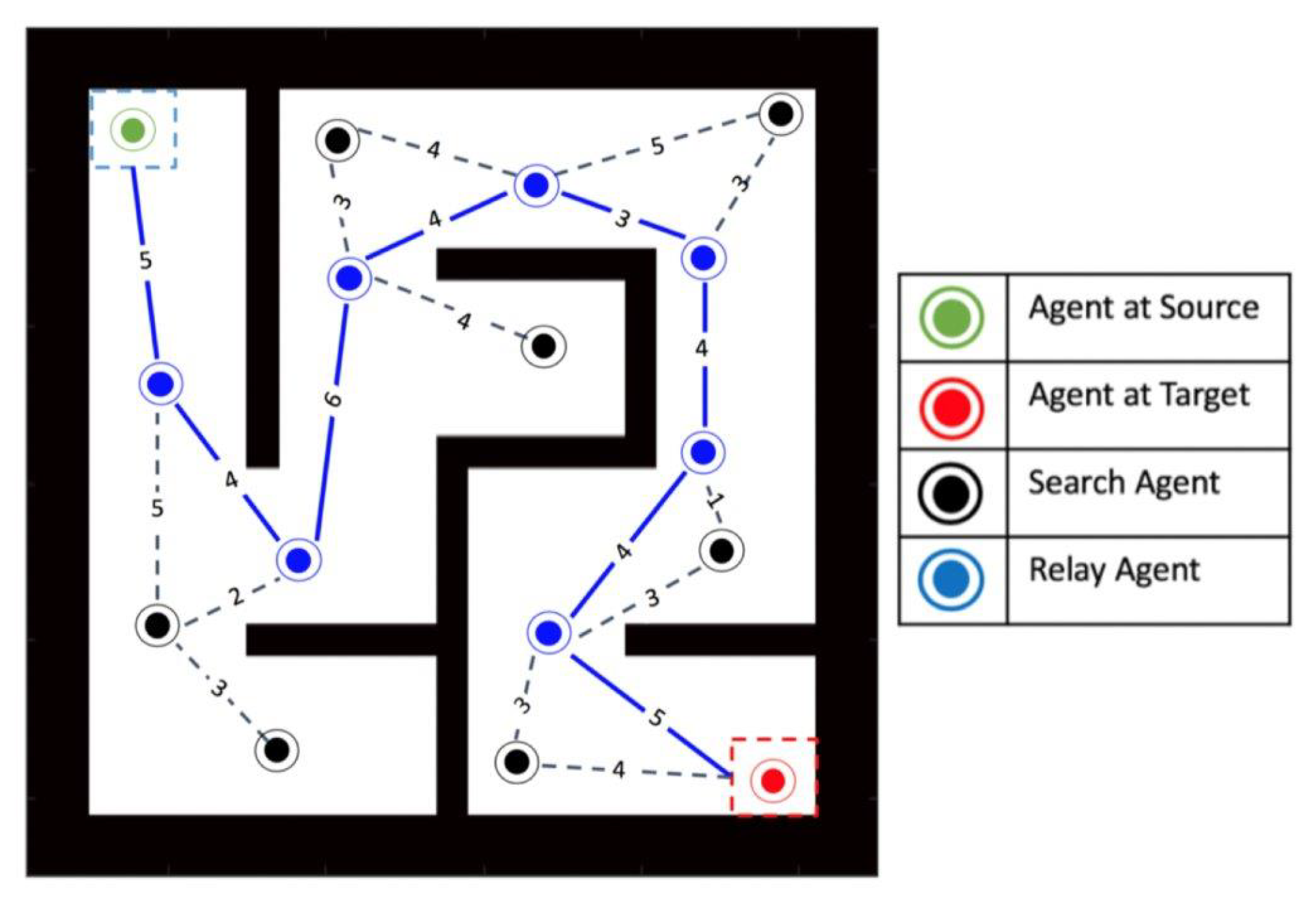
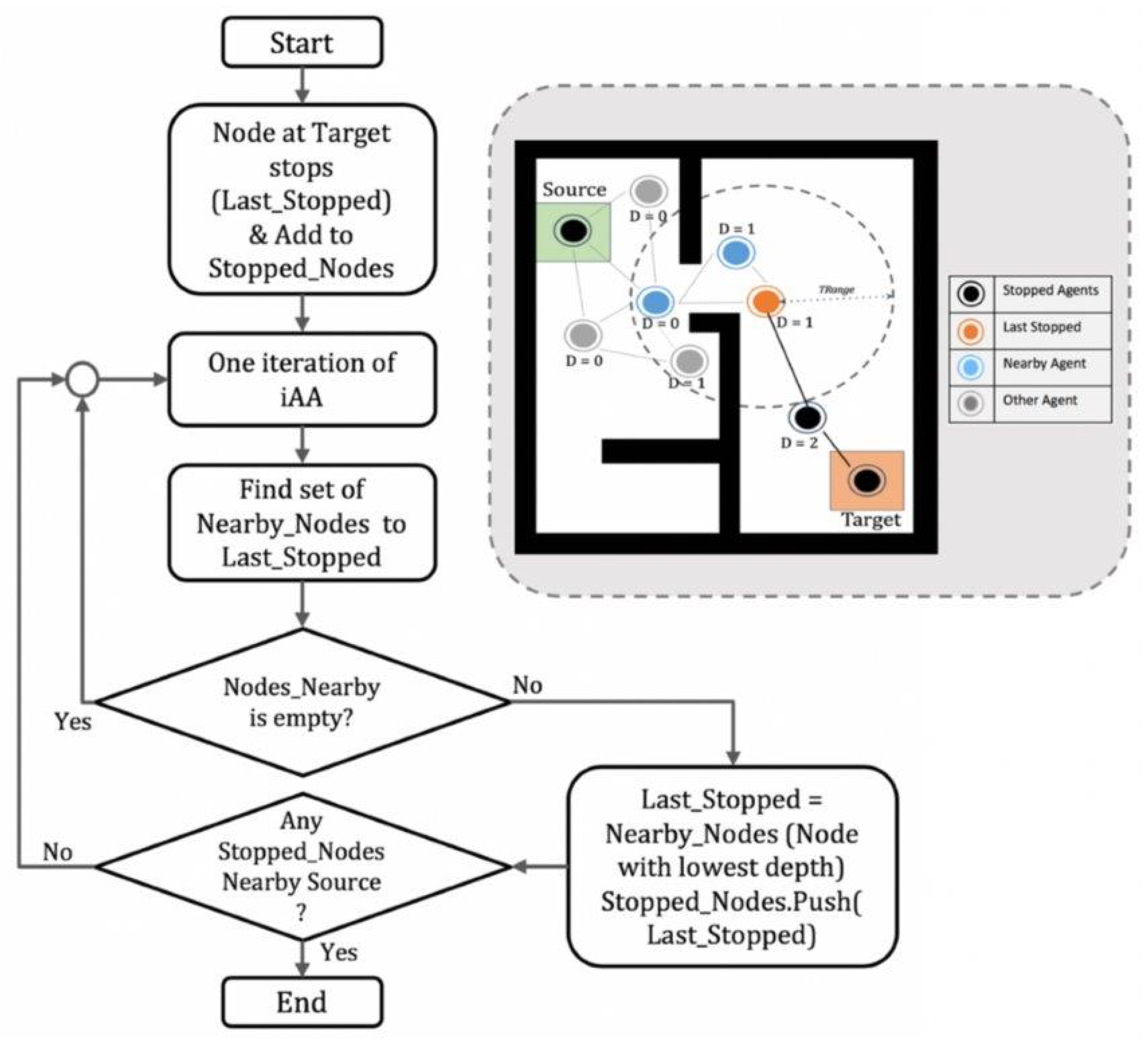
3.4. Solving Phase II (Rescue): Signal Routing and Victim Extraction
3.4.1. The Approach
3.4.2. The Algorithm
| Algorithm 2: Algorithm to find Shortest Path to Source from Target |
 |
- It is within the transmission range (TRange) of the Last_stopped Agent.
- There are no obstacles in between it and the Last_stopped.
3.4.3. Routing
4. Materials and Methods
4.1. Modeling Choices
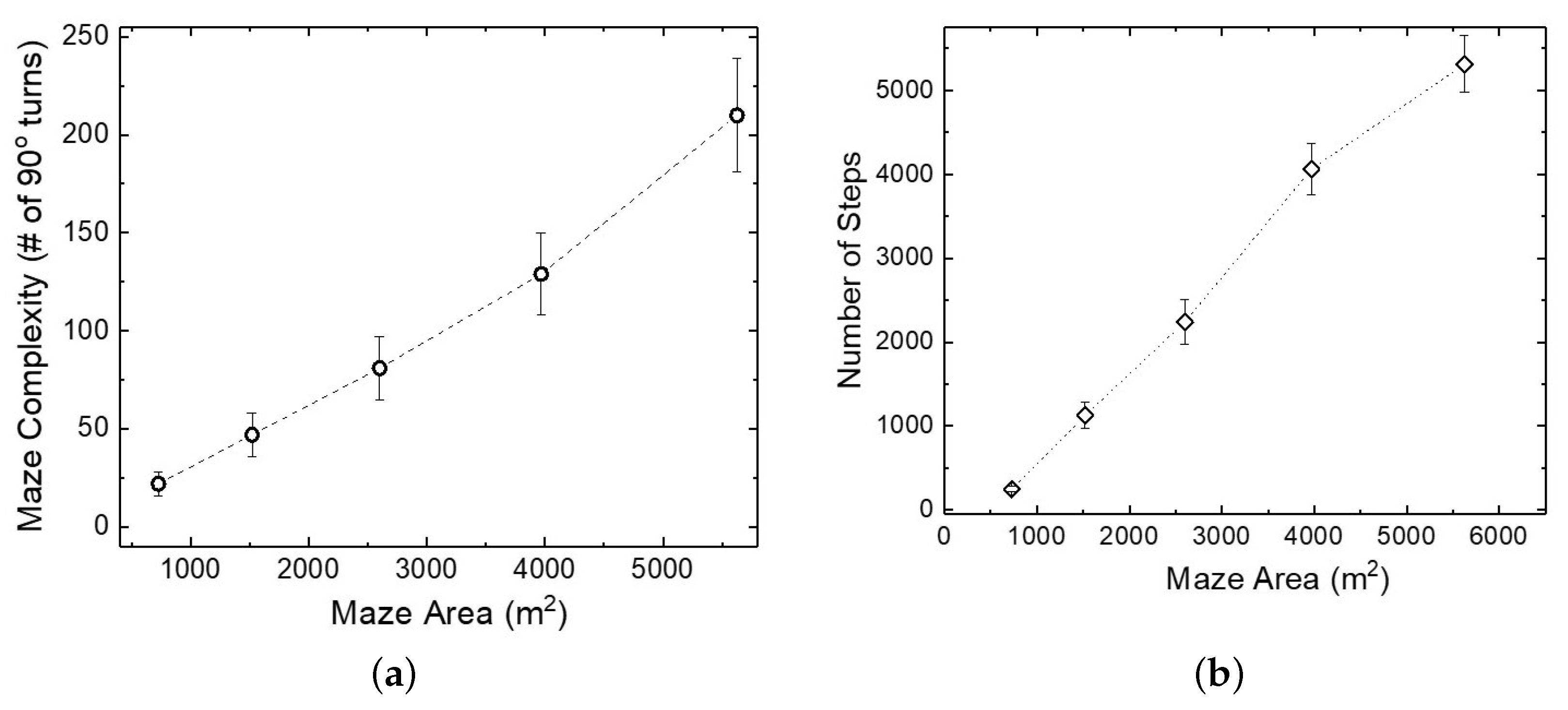
4.1.1. Maze Size and Complexity
4.1.2. Signal Progression through Obstacles
4.2. Data Collection
4.2.1. Hardware/Software Used
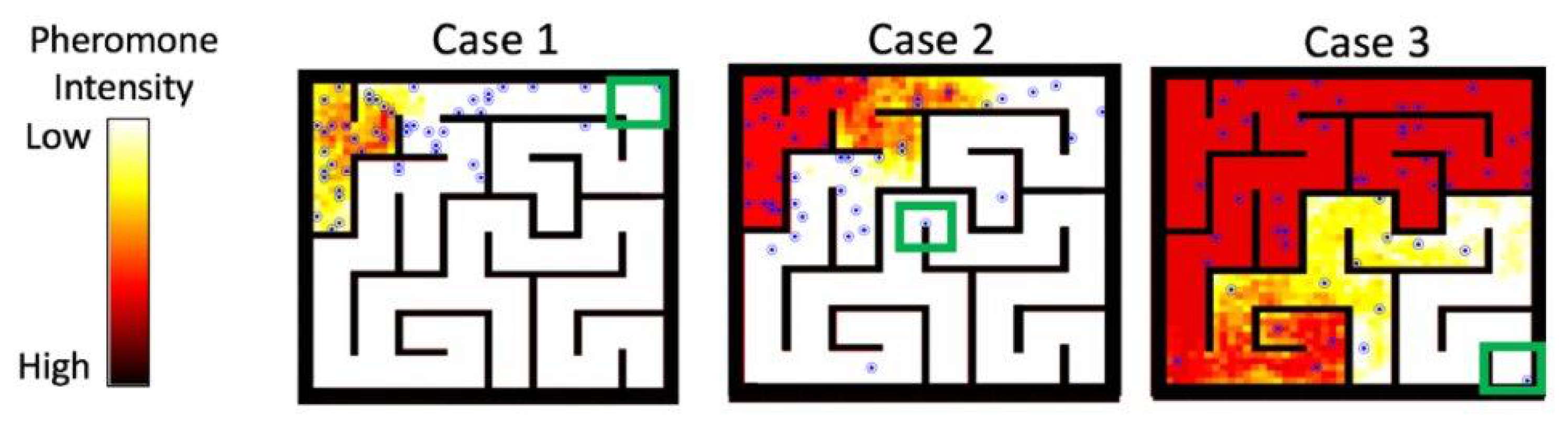
4.2.2. Maze Complexity
4.3. Comparative Evaluation of the Algorithms
4.4. Performance Measures
4.4.1. Benchmark Comparison
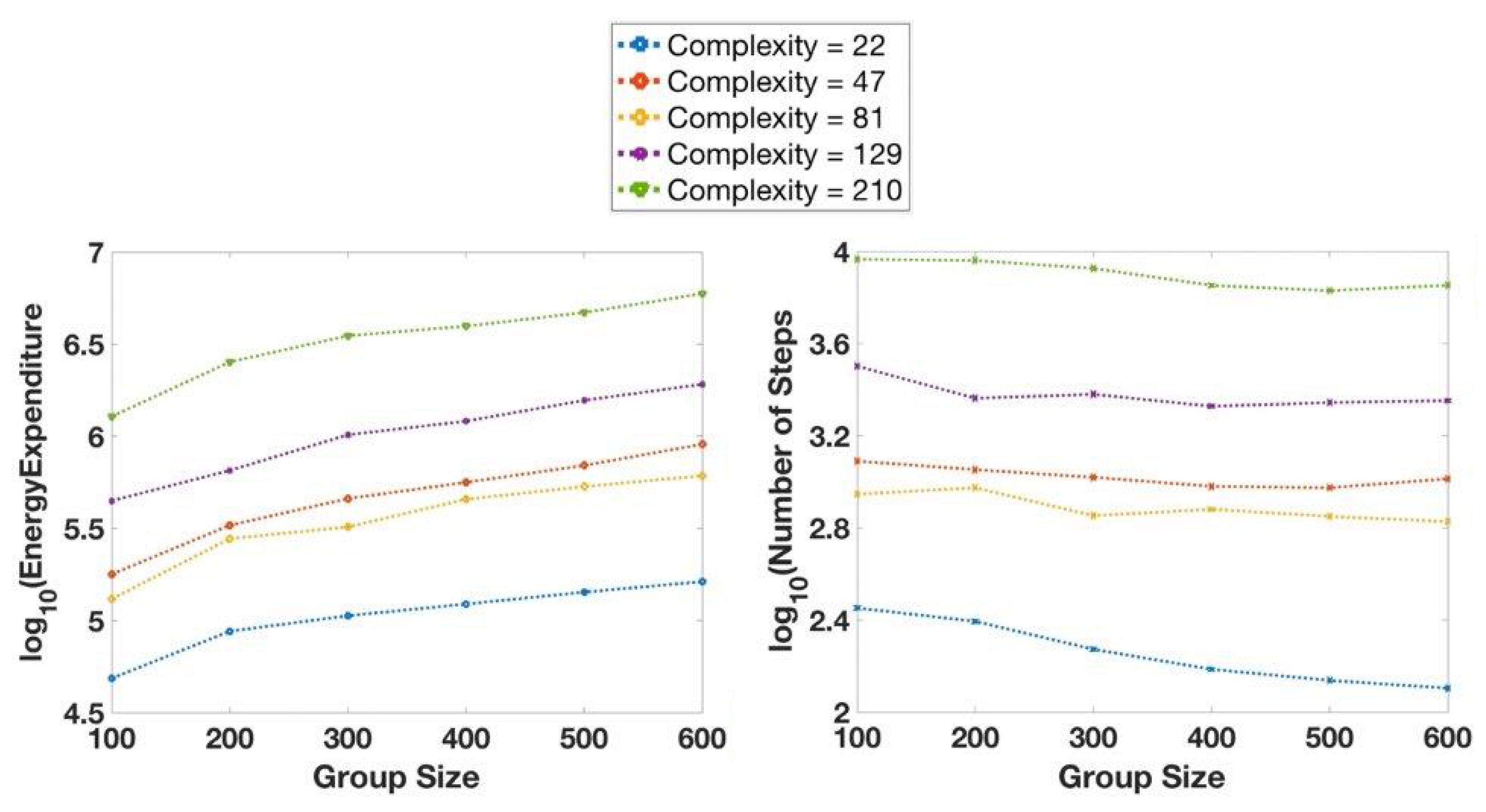
4.4.2. Cumulative Effort (Steps)
4.4.3. Estimated Energy Cost
4.4.4. Assumptions and Considerations
5. Results and Discussion
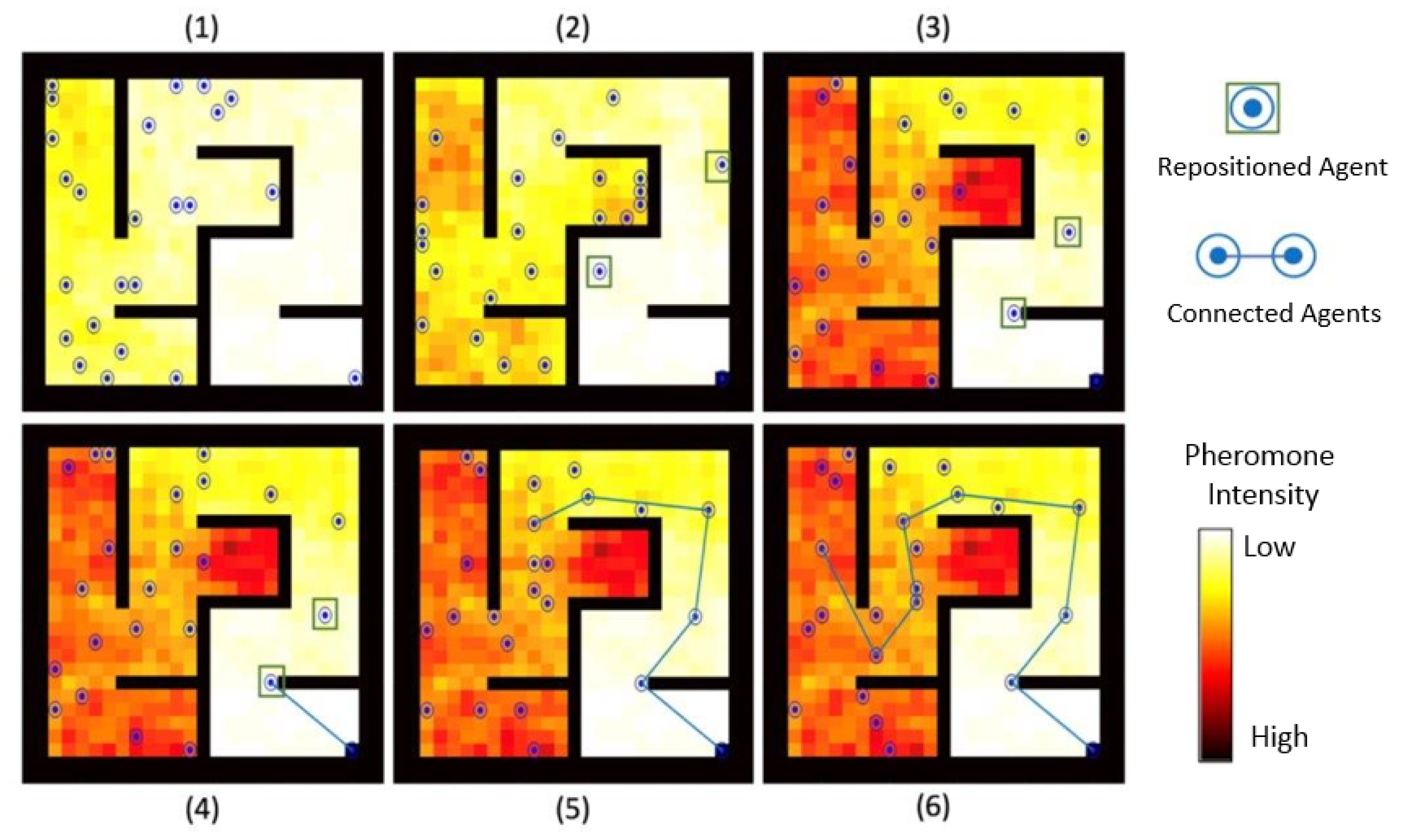
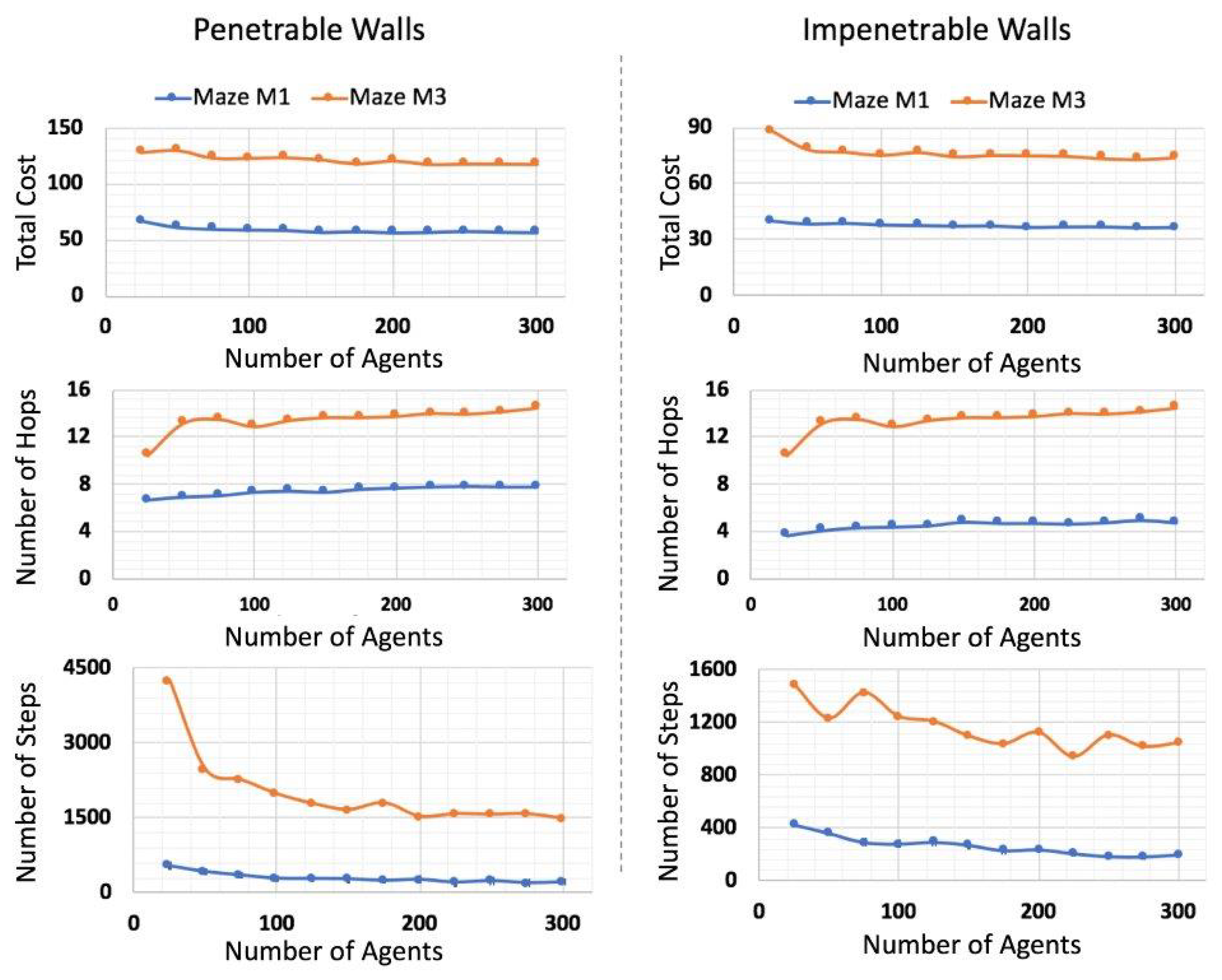
5.1. Phase I: Maze Exploration
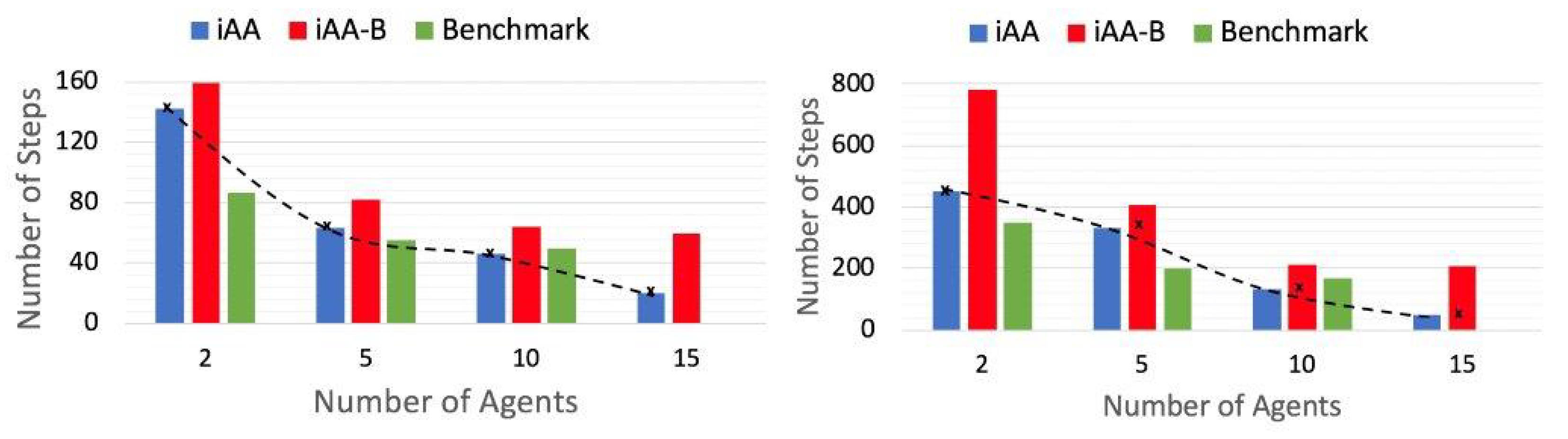
5.1.1. Benchmark Comparison
5.1.2. Cumulative Effort (Steps)
5.1.3. Estimated Energy Cost
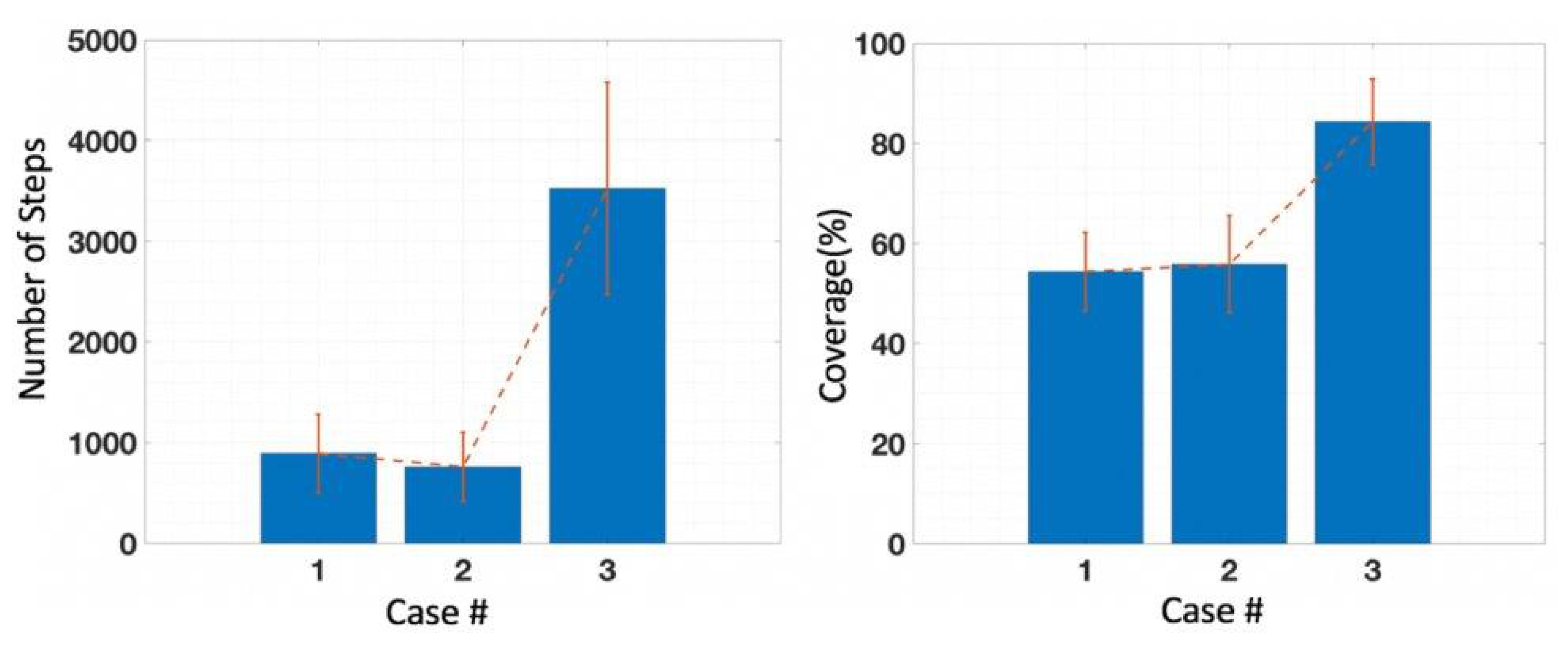
5.2. Phase II: Signal Routing and Victim Extraction
6. Conclusions and Future Work
6.1. Conclusions
6.2. Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Coopmans, C. Architecture requirements for Ethical, accurate, and resilient Unmanned Aerial Personal Remote Sensing. In Proceedings of the 2014 International Conference on Unmanned Aircraft Systems (ICUAS), Orlando, FL, USA, 27–30 May 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Marcus, M. Spectrum policy challenges of UAV/drones [Spectrum Policy and Regulatory Issues]. IEEE Wirel. Commun. 2014, 21, 8–9. [Google Scholar] [CrossRef]
- Ogan, R. Integration of manned and unmanned aircraft systems into U.S. airspace. In Proceedings of the IEEE SOUTHEASTCON 2014, Lexington, KY, USA, 13–16 March 2014; pp. 1–4. [Google Scholar] [CrossRef]
- Schneider, D. Open season on drones? IEEE Spectrum 2014, 51, 32–33. [Google Scholar] [CrossRef]
- Broad, W.J. The U.S. Flight from Pilotless Planes. Science 1981, 213, 188–190. [Google Scholar] [CrossRef] [PubMed]
- Paredes, J.A.; Álvarez, F.J.; Hansard, M.; Rajab, K.Z. A Gaussian Process model for UAV localization using millimetre wave radar. Expert Syst. Appl. 2021, 185, 115563. [Google Scholar] [CrossRef]
- Ismail, H.; Roy, R.; Sheu, L.J.; Chieng, W.H.; Tang, L.C. Exploration-Based SLAM (e-SLAM) for the Indoor Mobile Robot Using Lidar. Sensors 2022, 22, 1689. [Google Scholar] [CrossRef] [PubMed]
- Gupta, A.; Fernando, X. Simultaneous Localization and Mapping (SLAM) and Data Fusion in Unmanned Aerial Vehicles: Recent Advances and Challenges. Drones 2022, 6, 85. [Google Scholar] [CrossRef]
- Hildmann, H.; Kovacs, E. Review: Using Unmanned Aerial Vehicles (UAVs) as Mobile Sensing Platforms (MSPs) for Disaster Response, Civil Security and Public Safety. Drones 2019, 3, 59. [Google Scholar] [CrossRef]
- American Red Cross. Drones for Disaster Response and Relief Operations. Report, Measure (32 Advisors Company). 2015. Available online: www.issuelab.org/resources/21683/21683.pdf (accessed on 1 August 2022).
- Valente, J.a.; Sanz, D.; Barrientos, A.; Cerro, J.d.; Ribeiro, A.; Rossi, C. An Air-Ground Wireless Sensor Network for Crop Monitoring. Sensors 2011, 11, 6088–6108. [Google Scholar] [CrossRef]
- Chen, M.; Hu, Q.; Mackin, C.; Fisac, J.F.; Tomlin, C.J. Safe platooning of unmanned aerial vehicles via reachability. In Proceedings of the 2015 54th IEEE Conference on Decision and Control (CDC), Osaka, Japan, 15–18 December 2015; pp. 4695–4701. [Google Scholar] [CrossRef]
- Giyenko, A.; Cho, Y.I. Intelligent Unmanned Aerial Vehicle Platform for Smart Cities. In Proceedings of the 2016 Joint 8th International Conference on Soft Computing and Intelligent Systems (SCIS) and 17th International Symposium on Advanced Intelligent Systems (ISIS), Sapporo, Japan, 25–28 August 2016; pp. 729–733. [Google Scholar] [CrossRef]
- Nakata, R.; Clemens, S.; Lee, A.; Lubecke, V. RF techniques for motion compensation of an Unmanned Aerial Vehicle for remote radar life sensing. In Proceedings of the 2016 IEEE MTT-S International Microwave Symposium (IMS), San Francisco, CA, USA, 22–27 May 2016; pp. 1–4. [Google Scholar] [CrossRef]
- Hildmann, H.; Eledlebi, K.; Saffre, F.; Isakovic, A.F. Chapter The swarm is more than the sum of its drones—A swarming behaviour analysis for the deployment of drone-based wireless access networks in GPS-denied environments and under model communication noise. In Studies in Systems, Decision and Control; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Steenbeek, A.; Nex, F. CNN-Based Dense Monocular Visual SLAM for Real-Time UAV Exploration in Emergency Conditions. Drones 2022, 6, 79. [Google Scholar] [CrossRef]
- Pauner, C.; Kamara, I.; Viguri, J. Drones. Current challenges and standardisation solutions in the field of privacy and data protection. In Proceedings of the 2015 ITU Kaleidoscope: Trust in the Information Society (K-2015), Barcelona, Spain, 9–11 December 2015; pp. 1–7. [Google Scholar] [CrossRef]
- Erdelj, M.; Natalizio, E.; Chowdhury, K.R.; Akyildiz, I.F. Help from the Sky: Leveraging UAVs for Disaster Management. IEEE Pervasive Comput. 2017, 16, 24–32. [Google Scholar] [CrossRef]
- Boubeta-Puig, J.; Moguel, E.; Sánchez-Figueroa, F.; Hernández, J.; Preciado, J.C. An Autonomous UAV Architecture for Remote Sensing and Intelligent Decision-making. IEEE Internet Comput. 2018, 22, 6–15. [Google Scholar] [CrossRef]
- Apvrille, L.; Tanzi, T.; Dugelay, J.L. Autonomous drones for assisting rescue services within the context of natural disasters. In Proceedings of the 2014 XXXIth IEEE URSI General Assembly and Scientific Symposium (URSI GASS), Beijing, China, 16–23 August 2014; pp. 1–4. [Google Scholar]
- Nazib, R.A.; Moh, S. Routing Protocols for Unmanned Aerial Vehicle-Aided Vehicular Ad Hoc Networks: A Survey. IEEE Access 2020, 8, 77535–77560. [Google Scholar] [CrossRef]
- Deaconu, A.M.; Udroiu, R.; Nanau, C.Ş. Algorithms for Delivery of Data by Drones in an Isolated Area Divided into Squares. Sensors 2021, 21, 5472. [Google Scholar] [CrossRef]
- Giyenko, A.; Cho, Y.I. Intelligent UAV in smart cities using IoT. In Proceedings of the 2016 16th International Conference on Control, Automation and Systems (ICCAS), Gyeongju, Korea, 16–19 October 2016; pp. 207–210. [Google Scholar] [CrossRef]
- Hildmann, H.; Kovacs, E.; Saffre, F.; Isakovic, A.F. Nature-Inspired Drone Swarming for Real-Time Aerial Data-Collection Under Dynamic Operational Constraints. Drones 2019, 3, 71. [Google Scholar] [CrossRef]
- Eldemiry, A.; Zou, Y.; Li, Y.; Wen, C.Y.; Chen, W. Autonomous Exploration of Unknown Indoor Environments for High-Quality Mapping Using Feature-Based RGB-D SLAM. Sensors 2022, 22, 5117. [Google Scholar] [CrossRef] [PubMed]
- Li, J.; Tinka, A.; Kiesel, S.; Durham, J.W.; Kumar, T.K.S.; Koenig, S. Lifelong Multi-Agent Path Finding in Large-Scale Warehouses. In Proceedings of the 19th International Conference on Autonomous Agents and MultiAgent Systems, Auckland, New Zealand, 9–13 May 2020; International Foundation for Autonomous Agents and Multiagent Systems: Richland, SC, USA, 2020; pp. 1898–1900. [Google Scholar]
- Li, J.; Sun, K.; Ma, H.; Felner, A.; Kumar, T.K.S.; Koenig, S. Moving Agents in Formation in Congested Environments. In Proceedings of the 19th International Conference on Autonomous Agents and MultiAgent Systems, Auckland, New Zealand, 9–13 May 2020; International Foundation for Autonomous Agents and Multiagent Systems: Richland, SC, USA, 2020; pp. 726–734. [Google Scholar]
- Hussein, A.; Adel, M.; Bakr, M.; Shehata, O.M.; Khamis, A. Multi-robot Task Allocation for Search and Rescue Missions. J. Phys. Conf. Ser. 2014, 570, 052006. [Google Scholar] [CrossRef]
- Saffre, F.; Hildmann, H. Adaptive Behaviour for a Self-Organising Video Surveillance System Using a Genetic Algorithm. Algorithms 2021, 14, 74. [Google Scholar] [CrossRef]
- Aljehani, M.; Inoue, M. Communication and autonomous control of multi-UAV system in disaster response tasks. In Proceedings of the KES International Symposium on Agent and Multi-Agent Systems: Technologies and Applications, Vilamoura, Portugal, 21–23 June 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 123–132. [Google Scholar]
- Spezzano, G. Editorial: Special Issue “Swarm Robotics”. Appl. Sci. 2019, 9, 1474. [Google Scholar] [CrossRef]
- Gainer, J.J., Jr.; Dawkins, J.J.; DeVries, L.D.; Kutzer, M.D.M. Persistent Multi-Agent Search and Tracking with Flight Endurance Constraints. Robotics 2018, 8, 2. [Google Scholar] [CrossRef]
- Shakhatreh, H.; Sawalmeh, A.H.; Al-Fuqaha, A.I.; Dou, Z.; Almaita, E.K.; Khalil, I.M.; Othman, N.S.; Khreishah, A.; Guizani, M. Unmanned Aerial Vehicles (UAVs): A Survey on Civil Applications and Key Research Challenges. IEEE Access 2019, 7, 48572–48634. [Google Scholar] [CrossRef]
- Khuwaja, A.A.; Chen, Y.; Zhao, N.; Alouini, M.; Dobbins, P. A Survey of Channel Modeling for UAV Communications. IEEE Commun. Surv. Tutor. 2018, 20, 2804–2821. [Google Scholar] [CrossRef]
- Bupe, P.; Haddad, R.; Rios-Gutierrez, F. Relief and emergency communication network based on an autonomous decentralized UAV clustering network. In Proceedings of the SoutheastCon 2015, Fort Lauderdale, FL, USA, 9–12 April 2015; pp. 1–8. [Google Scholar] [CrossRef]
- Wang, J.; Shake, T.; Deutsch, P.; Coyle, A.; Cheng, B.N. Topology management algorithms for large-scale aerial high capacity directional networks. In Proceedings of the MILCOM 2016—2016 IEEE Military Communications Conference, Baltimore, MD, USA, 1–3 November 2016; pp. 343–348. [Google Scholar] [CrossRef]
- Won, J.; Seo, S.H.; Bertino, E. A Secure Communication Protocol for Drones and Smart Objects. In Proceedings of the 10th ACM Symposium on Information, Computer and Communications Security (ASIA CCS ’15), Singapore, 14–17 April 2015; ACM: New York, NY, USA, 2015; pp. 249–260. [Google Scholar] [CrossRef]
- Lee, K.S.; Ovinis, M.; Nagarajan, T.; Seulin, R.; Morel, O. Autonomous patrol and surveillance system using unmanned aerial vehicles. In Proceedings of the 2015 IEEE 15th International Conference on Environment and Electrical Engineering (EEEIC), Rome, Italy, 23 July 2015; pp. 1291–1297. [Google Scholar] [CrossRef]
- Trivedi, A.; Srinivasan, D.; Sanyal, K.; Ghosh, A. A Survey of Multiobjective Evolutionary Algorithms Based on Decomposition. IEEE Trans. Evol. Comput. 2017, 21, 440–462. [Google Scholar] [CrossRef]
- Tjiharjadi, S.; Setiawan, E. Design and Implementation of a Path Finding Robot Using Flood Fill Algorithm. Int. J. Mech. Eng. Robot. Res. 2016, 5, 180–185. [Google Scholar] [CrossRef]
- Rivera, G. Path Planning for General Mazes. Master’s Thesis, Missouri University of Science and Technology, Rolla, MO, USA, 2012. [Google Scholar]
- Mac, T.T.; Copot, C.; Tran, D.T.; De Keyser, R. Heuristic approaches in robot path planning: A survey. Robot. Auton. Syst. 2016, 86, 13–28. [Google Scholar] [CrossRef]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of Important Issues in UAV Communication Networks. IEEE Commun. Surv. Tutor. 2016, 18, 1123–1152. [Google Scholar] [CrossRef]
- Li, Y.; Cai, L. UAV-Assisted Dynamic Coverage in a Heterogeneous Cellular System. IEEE Netw. 2017, 31, 56–61. [Google Scholar] [CrossRef]
- Andryeyev, O.; Mitschele-Thiel, A. Increasing the Cellular Network Capacity Using Self-Organized Aerial Base Stations. In Proceedings of the 3rd Workshop on Micro Aerial Vehicle Networks, Systems, and Applications, Niagara Falls, NY, USA, 23 June 2017; pp. 37–42. [Google Scholar]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of Things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Mainetti, L.; Patrono, L.; Vilei, A. Evolution of Wireless Sensor Networks towards the Internet of Things: A survey. In Proceedings of the 2011 IEEE 19th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 15–17 September 2011; pp. 1–6. [Google Scholar]
- Eledlebi, K.; Hildmann, H.; Ruta, D.; Isakovic, A.F. A Hybrid Voronoi Tessellation/Genetic Algorithm Approach for the Deployment of Drone-Based Nodes of a Self-Organizing Wireless Sensor Network (WSN) in Unknown and GPS Denied Environments. Drones 2020, 4, 33. [Google Scholar] [CrossRef]
- Hayat, S.; Yanmaz, E.; Muzaffar, R. Survey on Unmanned Aerial Vehicle Networks for Civil Applications: A Communications Viewpoint. IEEE Commun. Surv. Tutor. 2016, 18, 2624–2661. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.; Debbah, M. A Tutorial on UAVs for Wireless Networks: Applications, Challenges, and Open Problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef]
- Hossein Motlagh, N.; Taleb, T.; Arouk, O. Low-Altitude Unmanned Aerial Vehicles-Based Internet of Things Services: Comprehensive Survey and Future Perspectives. IEEE Internet Things J. 2016, 3, 899–922. [Google Scholar] [CrossRef]
- Guevara, K.; Rodriguez, M.; Gallo, N.; Velasco, G.; Vasudeva, K.; Guvenc, I. UAV-based GSM network for public safety communications. In Proceedings of the SoutheastCon 2015, Fort Lauderdale, FL, USA, 9–12 April 2015; pp. 1–2. [Google Scholar] [CrossRef]
- Sharma, B.; Srivastava, G.; Lin, J. A bidirectional congestion control transport protocol for the internet of drones. Comput. Commun. 2020, 153, 102–116. [Google Scholar] [CrossRef]
- Bhargava, A.; Verma, S. KATE: Kalman Trust Estimator for Internet of Drones. Comput. Commun. 2020, 160, 388–401. [Google Scholar] [CrossRef]
- Chang, Y.S. An enhanced rerouting cost estimation algorithm towards internet of drone. J. Supercomput. 2020, 76, 10036–10049. [Google Scholar] [CrossRef]
- Giannini, C.; Shaaban, A.A.; Buratti, C.; Verdone, R. Delay Tolerant Networking for smart city through drones. In Proceedings of the 2016 International Symposium on Wireless Communication Systems (ISWCS), Poznan, Poland, 20–23 September 2016; pp. 603–607. [Google Scholar] [CrossRef]
- Faiçal, B.S.; Pessin, G.; Filho, G.P.R.; Carvalho, A.C.P.L.F.; Furquim, G.; Ueyama, J. Fine-Tuning of UAV Control Rules for Spraying Pesticides on Crop Fields. In Proceedings of the 2014 IEEE 26th International Conference on Tools with Artificial Intelligence, Limassol, Cyprus, 10–12 November 2014; pp. 527–533. [Google Scholar] [CrossRef]
- de Albuquerque, J.C.; de Lucena, S.C.; Campos, C.A.V. Evaluating data communications in natural disaster scenarios using opportunistic networks with Unmanned Aerial Vehicles. In Proceedings of the 2016 IEEE 19th International Conference on Intelligent Transportation Systems (ITSC), Rio de Janeiro, Brazil, 1–4 November 2016; pp. 1452–1457. [Google Scholar] [CrossRef]
- Anand, D.G.; Giriprasad, M.N. Energy Efficient Coverage Problems In Wireless Ad Hoc Sensor Networks. Zenodo 2018. [Google Scholar] [CrossRef]
- Valente, J.; Almeida, R.; Kooistra, L. A Comprehensive Study of the Potential Application of Flying Ethylene-Sensitive Sensors for Ripeness Detection in Apple Orchards. Sensors 2019, 19, 372. [Google Scholar] [CrossRef]
- Valente, J.; Roldán, J.; Garzón, M.; Barrientos, A. Towards Airborne Thermography via Low-Cost Thermopile Infrared Sensors. Drones 2019, 3, 30. [Google Scholar] [CrossRef]
- Aftab, F.; Khan, A.; Zhang, Z. Bio-inspired clustering scheme for Internet of Drones application in industrial wireless sensor network. Int. J. Distrib. Sens. Netw. 2019, 15, 155014771988990. [Google Scholar] [CrossRef]
- Camazine, S.; Deneubourg, J.L.; Franks, N.R.; Sneyd, J.; Theraulaz, G.; Bonabeau, E. Self-Organization in Biological Systems; Princeton Univ Press: Princeton, NJ, USA, 2001. [Google Scholar]
- Mugler, A.; Aimee, G.B.; Takahashi, K.; Rein ten Wolde, P. Membrane Clustering and the Role of Rebinding in Biochemical Signaling. Biophys. J. 2012, 102, 1069–1078. [Google Scholar] [CrossRef]
- Navlakha, S.; Bar-Joseph, Z. Algorithms in nature: The convergence of systems biology and computational thinking. Mol. Syst. Biol. 2011, 7, 546. [Google Scholar] [CrossRef]
- Bonabeau, E.; Dorigo, M.; Theraulaz, G. Inspiration for optimization from social insect behaviour. Nature 2000, 406, 39–42. [Google Scholar] [CrossRef]
- Berdahl, A.; Torney, C.J.; Ioannou, C.C.; Faria, J.J.; Couzin, I.D. Emergent Sensing of Complex Environments by Mobile Animal Groups. Science 2013, 339, 574–576. [Google Scholar] [CrossRef]
- Lim, S.; Rus, D. Stochastic distributed multi-agent planning and applications to traffic. In Proceedings of the IEEE ICRA, Saint Paul, MN, USA, 14–18 May 2012; pp. 2873–2879. [Google Scholar]
- Sleegers, J.; Olij, R.; van Horn, G.; van den Berg, D. Where the really hard problems aren’t. Oper. Res. Perspect. 2020, 7, 100160. [Google Scholar] [CrossRef]
- Pearl, J. Heuristics: Intelligent Search Strategies for Computer Problem Solving; The Addison-Wesley Series in Artificial Intelligence; Addison-Wesley: Boston, MA, USA, 1984. [Google Scholar]
- Brownlee, J. Clever Algorithms: Nature-Inspired Programming Recipes; Lulu.com: Morrisville, NC, USA, 2011. [Google Scholar]
- Yang, X.S. Firefly algorithms for multimodal optimization. Stoch. Algorithms Funct. Appl. (SAGA) 2009, 5792, 169–178. [Google Scholar]
- Leena, N.; Saju, K. A survey on path planning techniques for autonomous mobile robots. IOSR J. Mech. Civ. Eng. (IOSR-JMCE) 2014, 8, 76–79. [Google Scholar]
- Bounini, F.; Gingras, D.; Pollart, H.; Gruyer, D. Modified Artificial Potential Field method for online path planning applications. In Proceedings of the 2017 IEEE Intelligent Vehicles Symposium (IV), Los Angeles, CA, USA, 11–14 June 2017; pp. 180–185. [Google Scholar]
- Khatib, O. Real-time obstacle avoidance for manipulators and mobile robots. In Autonomous Robot Vehicles; Cox, I.J., Wilfong, G., Eds.; Springer: New York, NY, USA, 1986; pp. 396–404. [Google Scholar]
- Sutantyo, D.K.; Kernbach, S.; Levi, P.; Nepomnyashchikh, V.A. Multi-robot searching algorithm using Lévy flight and artificial potential field. In Proceedings of the 2010 IEEE International Workshop on Safety Security and Rescue Robotics (SSRR), Bremen, Germany, 26–30 July 2010; pp. 1–6. [Google Scholar]
- Hanafi, D.; Abueejela, Y.M.; Zakaria, M.F. Wall follower autonomous robot development applying fuzzy incremental controller. Intell. Control. Autom. 2013, 4, 18. [Google Scholar] [CrossRef]
- Wang, L.; Luo, C.; Li, M.; Cai, J. Trajectory Planning of an Autonomous Mobile Robot by Evolving Ant Colony System. Int. J. Robot. Autom. 2017, 32, 1500–1515. [Google Scholar] [CrossRef]
- Malone, N.; Chiang, H.T.; Lesser, K.; Oishi, M.; Tapia, L. Hybrid dynamic moving obstacle avoidance using a stochastic reachable set-based potential field. IEEE Trans. Robot. 2017, 33, 1124–1138. [Google Scholar] [CrossRef]
- Atten, C.; Channouf, L.; Danoy, G.; Bouvry, P. UAV fleet mobility model with multiple pheromones for tracking moving observation targets. In Proceedings of the 19th European Conference on the Applications of Evolutionary Computation, Porto, Portugal, 30 March–1 April 2016; pp. 332–347. [Google Scholar]
- Cao, J. Robot Global Path Planning Based on an Improved Ant Colony Algorithm. J. Comput. Commun. 2016, 4, 11–19. [Google Scholar] [CrossRef]
- Krentz, T.; Greenhagen, C.; Roggow, A.; Desmond, D.; Khorbotly, S. A modified Ant Colony Optimization algorithm for implementation on multi-core robots. In Proceedings of the IEEE Swarm/Human Blended Intelligence Workshop (SHBI), Cleveland, OH, USA, 28–29 September 2015; pp. 1–6. [Google Scholar]
- Fossum, F.; Montanier, J.M.; Haddow, P.C. Repellent pheromones for effective swarm robot search in unknown environments. In Proceedings of the 2014 IEEE Symposium on Swarm Intelligence (SIS), Orlando, FL, USA, 9–12 December 2014; pp. 1–8. [Google Scholar]
- Deepak, B.; Parhi, D.R.; Raju, B. Advance particle swarm optimization-based navigational controller for mobile robot. Arab. J. Sci. Eng. 2014, 39, 6477–6487. [Google Scholar] [CrossRef]
- Wang, Z.W.R. Robot Path Planning for Mobile Robot Based on Improved Ant Colony Algorithm. Appl. Mech. Mater. 2013, 385–386, 717–720. [Google Scholar]
- Aurangzeb, M.; Lewis, F.L.; Huber, M. Efficient, swarm-based path finding in unknown graphs using Reinforcement Learning. In Proceedings of the 2013 10th IEEE International Conference on Control and Automation (ICCA), Hangzhou, China, 12–14 June 2013; pp. 870–877. [Google Scholar]
- Buniyamin, N.; Ngah, W.; Sariff, N.; Mohamad, Z. A simple local path planning algorithm for autonomous mobile robots. Int. J. Syst. Appl. Eng. Dev. 2011, 5, 151–159. [Google Scholar]
- Wang, H.; Yu, Y.; Yuan, Q. Application of Dijkstra algorithm in robot path-planning. In Proceedings of the 2011 IEEE Second International Conference on Mechanic Automation and Control Engineering (MACE), Inner Mongolia, China, 15–17 July 2011; pp. 1067–1069. [Google Scholar]
- Ahuja, M. Fuzzy Counter Ant Algorithm for Maze Problem. Master’s Thesis, University of Cincinnati, Cincinnati, OH, USA, 2010. [Google Scholar]
- Gong, D.; Lu, L.; Li, M. Robot path planning in uncertain environments based on particle swarm optimization. In Proceedings of the IEEE Congress on Evolutionary Computation (CEC’09), Wellington, New Zealand, 10–13 June 2009; pp. 2127–2134. [Google Scholar]
- Sauter, J.A.; Matthews, R.; Parunak, H.V.D.; Brueckner, S.A. Performance of digital pheromones for swarming vehicle control. In Proceedings of the Fourth International Joint Conference on Autonomous Agents and Multiagent Systems, Utrecht, The Netherlands, 25–29 July 2005; pp. 903–910. [Google Scholar]
- Nagatani, K.; Kiribayashi, S.; Okada, Y.; Tadokoro, S.; Nishimura, T.; Yoshida, T.; Koyanagi, E.; Hada, Y. Redesign of rescue mobile robot Quince. In Proceedings of the 2011 IEEE International Symposium on Safety, Security, and Rescue Robotics (SSRR), Kyoto, Japan, 1–5 November 2011; pp. 13–18. [Google Scholar]
- Ma, X.; Mao, R. Path planning for coal mine robot to avoid obstacle in gas distribution area. Int. J. Adv. Robot. Syst. 2018, 15, 1729881417751505. [Google Scholar] [CrossRef]
- Xiaowei, F.; Xiaoguang, G. Multi-UAVs cooperative control in communication relay. In Proceedings of the 2016 IEEE International Conference on Signal Processing, Communications and Computing (ICSPCC), Hong Kong, China, 5–8 August 2016; pp. 1–5. [Google Scholar]
- Mondada, F.; Floreano, D.; Guignard, A.; Deneubourg, J.L.; Gambardella, L.; Nolfi, S.; Dorigo, M. Search for Rescue: An Application for the SWARM-BOT Self-Assembling Robot Concept; Technical Report, LSA2-I2S-STI; Swiss Federal Institute of Technology: Lausanne, Switzerland, 2002. [Google Scholar]
- Fawzy, A.E.; Shokair, M.; Saad, W. Balanced and energy-efficient multi-hop techniques for routing in wireless sensor networks. IET Netw. 2017, 7, 33–43. [Google Scholar] [CrossRef]
- Gupta, N.; Mangla, K.; Jha, A.K.; Umar, M. Applying Dijkstra’s Algorithm in Routing Process. Int. J. New Technol. Res 2016, 2, 122–124. [Google Scholar]
- Fadzli, S.A.; Abdulkadir, S.I.; Makhtar, M.; Jamal, A.A. Robotic Indoor Path Planning Using Dijkstra. In Proceedings of the 2015 2nd IEEE International Conference on Information Science and Security (ICISS), Seoul, Korea, 10–12 January 2015; pp. 1–4. [Google Scholar]
- Liu, H.; Stoll, N.; Junginger, S.; Thurow, K. A Floyd-Dijkstra hybrid application for mobile robot path planning in life science automation. In Proceedings of the 2012 IEEE International Conference on Automation Science and Engineering (CASE), Seoul, Korea, 20–24 August 2012; pp. 279–284. [Google Scholar]
- Rai, R.; Chinghtam, T.S. A Hybrid Framework for Robot Path Planning and Navigation using ACO and Dijkstra’s Algorithm. In Proceedings of the International Symposium on Devices MEMS, Intelligent Systems & Communication (ISDMISC), Gangtok, India, 19–24 October 2011. [Google Scholar]
- Yazici, A.; Sipahioglu, A.; Parlaktuna, O.; Gurel, U. A heuristic-based route planning approach for a homogeneous multi-robot team. In Proceedings of the Computer Aided Control System Design, 2006 IEEE International Conference on Control Applications, 2006 IEEE International Symposium on Intelligent Control, Munich, Germany, 4–6 October 2006; pp. 1237–1242. [Google Scholar]
- Dorigo, M.; Stützle, T. Ant Colony Optimization; Bradford Company: Scituate, MA, USA, 2004. [Google Scholar]
- Zhangqi, A.; Xiaoguang, Z.; Qingyao, H. Mobile robot path planning based on parameter optimization ant colony algorithm. Procedia Eng. 2011, 15, 2738–2741. [Google Scholar] [CrossRef]
- Diestel, R. Graph Theory, 5th ed.; Springer Graduate Texts in Mathematic; Springer-Verlag, © Reinhard Diestel: Berlin, Germany, 2017. [Google Scholar]
- Engelbrecht, A.P. Fundamentals of Computational Swarm Intelligence; John Wiley & Sons: New York, NY, USA, 2006. [Google Scholar]
- West, D.B. Introduction to Graph Theory; Prentice Hall: Upper Saddle River, NJ, USA, 2001; Volume 2, ISBN 978-0130144003. [Google Scholar]
- Giannopoulou, A.C. Tree-Depth of Graphs: Characterisations and Obstructions. Ph.D. Thesis, National and Kapodistrian University of Athens, Zografou, Greece, 2009. [Google Scholar]
- Rappaport, T.S. Wireless Communications: Principles and Practice; Rentice Hall: Upper Saddle River, NJ, USA, 1996; Volume 2, ISBN 9780133755367. [Google Scholar]
- Wilson, R. Propagation Losses through Common Building Materials 2.4 GHz vs 5 GHz; Magis Networks Inc.: San Diego, CA, USA, 2002. [Google Scholar]
- Atzmon, D.; Stern, R.; Felner, A.; Sturtevant, N.R.; Koenig, S. Probabilistic Robust Multi-Agent Path Finding. In Proceedings of the 30th International Conference on Automated Planning and Scheduling (ICAPS), Nancy, France, 14–19 June 2020; pp. 37–39. [Google Scholar]
- Li, J.; Gange, G.; Harabor, D.; Stuckey, P.J.; Ma, H.; Koenig, S. New Techniques for Pairwise Symmetry Breaking in Multi-Agent Path Finding. In Proceedings of the 30th International Conference on Automated Planning and Scheduling (ICAPS), Nancy, France, 14–19 June 2020; pp. 193–201. [Google Scholar]
- Eledlebi, K.; Ruta, D.; Hildmann, H.; Saffre, F.; Alhammadi, Y.; Isakovic, A.F. Coverage and Energy Analysis of Mobile Sensor Nodes in Obstructed Noisy Indoor Environment: A Voronoi-Approach. IEEE Trans. Mob. Comput. 2020, 21, 2745–2760. [Google Scholar] [CrossRef]
- Berlinger, F.; Gauci, M.; Nagpal, R. Implicit coordination for 3D underwater collective behaviors in a fish-inspired robot swarm. Sci. Robot. 2021, 6, eabd8668. [Google Scholar] [CrossRef]



| Ref | LP | HT | Algorithm Used |
|---|---|---|---|
| [78] | ✓ | Improved ACO | |
| [79] | ✓ | Artificial Potential Field Method | |
| [80] | ✓ | ✓ | Multi Pheromones for tracking targets |
| [81] | ✓ | ✓ | Improved ACO Heuristic Function |
| [82] | ✓ | Simple ACO | |
| [83] | ✓ | ✓ | Repellent Pheromone for coverage |
| [84] | ✓ | ✓ | Advanced PSO |
| [85] | ✓ | Genetic Algorithm with ACO | |
| [86] | ✓ | Hybrid ACO w. Random- + RL based-Search | |
| [87] | ✓ | Point Bug Algorithm | |
| [88] | ✓ | Dijkstra Algorithm | |
| [89] | ✓ | ✓ | Fuzzy Logic with Counter ACO |
| [90] | ✓ | PSO in partially known environments | |
| [91] | ✓ | ✓ | Combination of multiple pheromones |
| Reference | Cost Function | Alg. | |
|---|---|---|---|
| ✓ | [93] | Distance, Gas Concentration | D, ACO |
| [96] | Energy | D | |
| [97] | Distance | D | |
| ✓ | [98] | Energy, Difficulty, Distance | D |
| ✓ | [99] | Distance | FD |
| ✓ | [100] | Distance | D, ACO |
| ✓ | [101] | Distance | D + others |
| Dimensions | Complexity | |
|---|---|---|
| Maze 1 (M1) | 27 × 27 | 22 |
| Maze 2 (M2) | 39 × 39 | 47 |
| Maze 3 (M3) | 51 × 51 | 81 |
| Maze 4 (M4) | 63 × 63 | 129 |
| Maze 5 (M5) | 75 × 75 | 210 |
| Direction | Cost |
|---|---|
| Hover | 0.5 |
| Forward | 1 |
| 90 turn | 1.5 |
| Backward | 2 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Husain, Z.; Al Zaabi, A.; Hildmann, H.; Saffre, F.; Ruta, D.; Isakovic, A.F. Search and Rescue in a Maze-like Environment with Ant and Dijkstra Algorithms. Drones 2022, 6, 273. https://doi.org/10.3390/drones6100273
Husain Z, Al Zaabi A, Hildmann H, Saffre F, Ruta D, Isakovic AF. Search and Rescue in a Maze-like Environment with Ant and Dijkstra Algorithms. Drones. 2022; 6(10):273. https://doi.org/10.3390/drones6100273
Chicago/Turabian StyleHusain, Zainab, Amna Al Zaabi, Hanno Hildmann, Fabrice Saffre, Dymitr Ruta, and A. F. Isakovic. 2022. "Search and Rescue in a Maze-like Environment with Ant and Dijkstra Algorithms" Drones 6, no. 10: 273. https://doi.org/10.3390/drones6100273
APA StyleHusain, Z., Al Zaabi, A., Hildmann, H., Saffre, F., Ruta, D., & Isakovic, A. F. (2022). Search and Rescue in a Maze-like Environment with Ant and Dijkstra Algorithms. Drones, 6(10), 273. https://doi.org/10.3390/drones6100273






