Privacy in Quantum Estimation †
Abstract
:1. Introduction
2. Private Quantum Estimation
3. Application to Two-Qubit Unitaries
- (i)
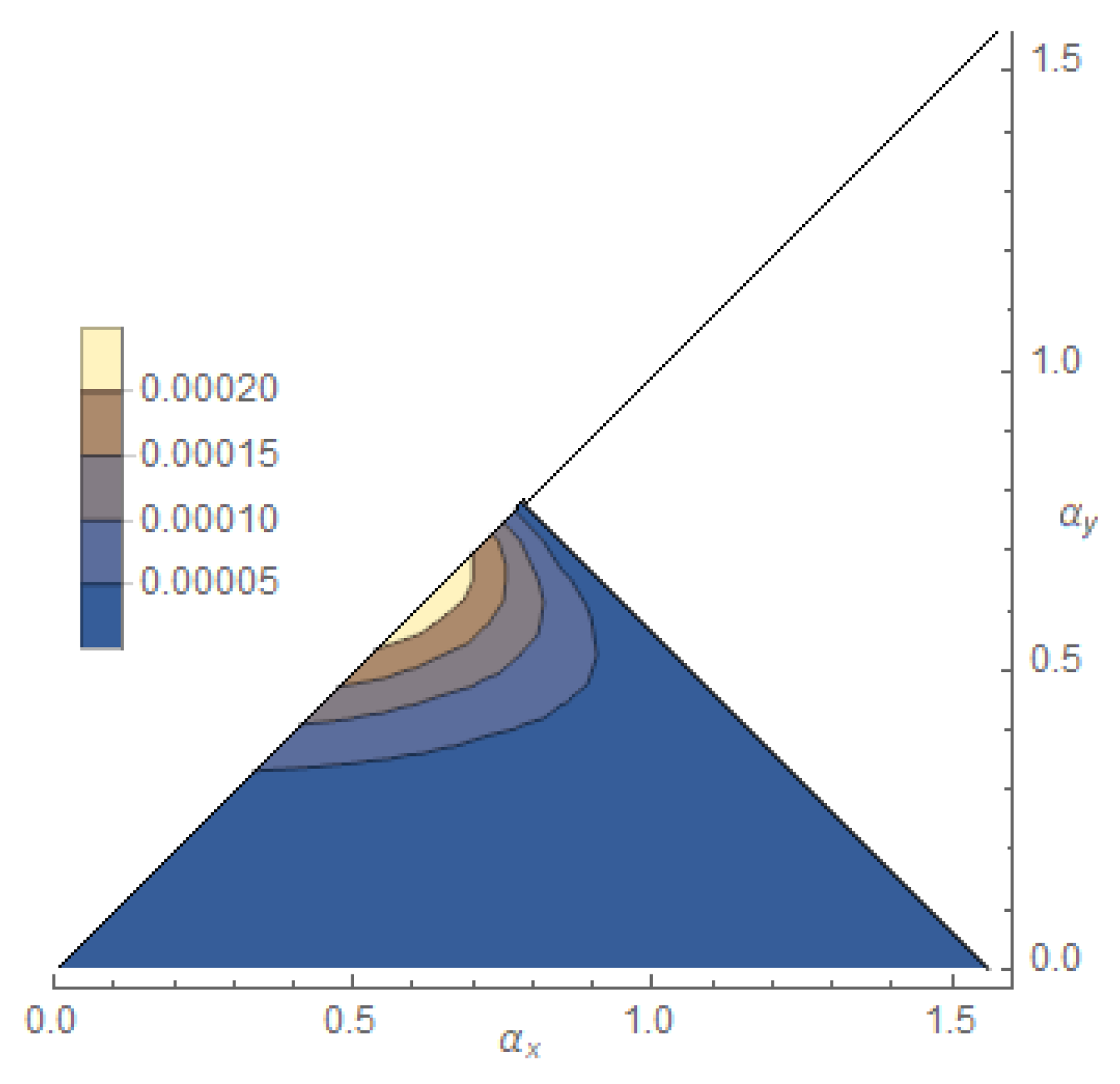
- Estimation of . We took 325 points in the region and for each point we estimated through and independently through . This is done by also optimizing the privacy (5) over the probe’s state, i.e., by consideringwhose contour plot is reported in Figure 1.On the line we have and this divides the region into two triangles. Only in the lower one the estimation is private (in the upper one results smaller than ). Furthermore there is a specific and small region where the privacy increases with respect to the background.
- (ii)
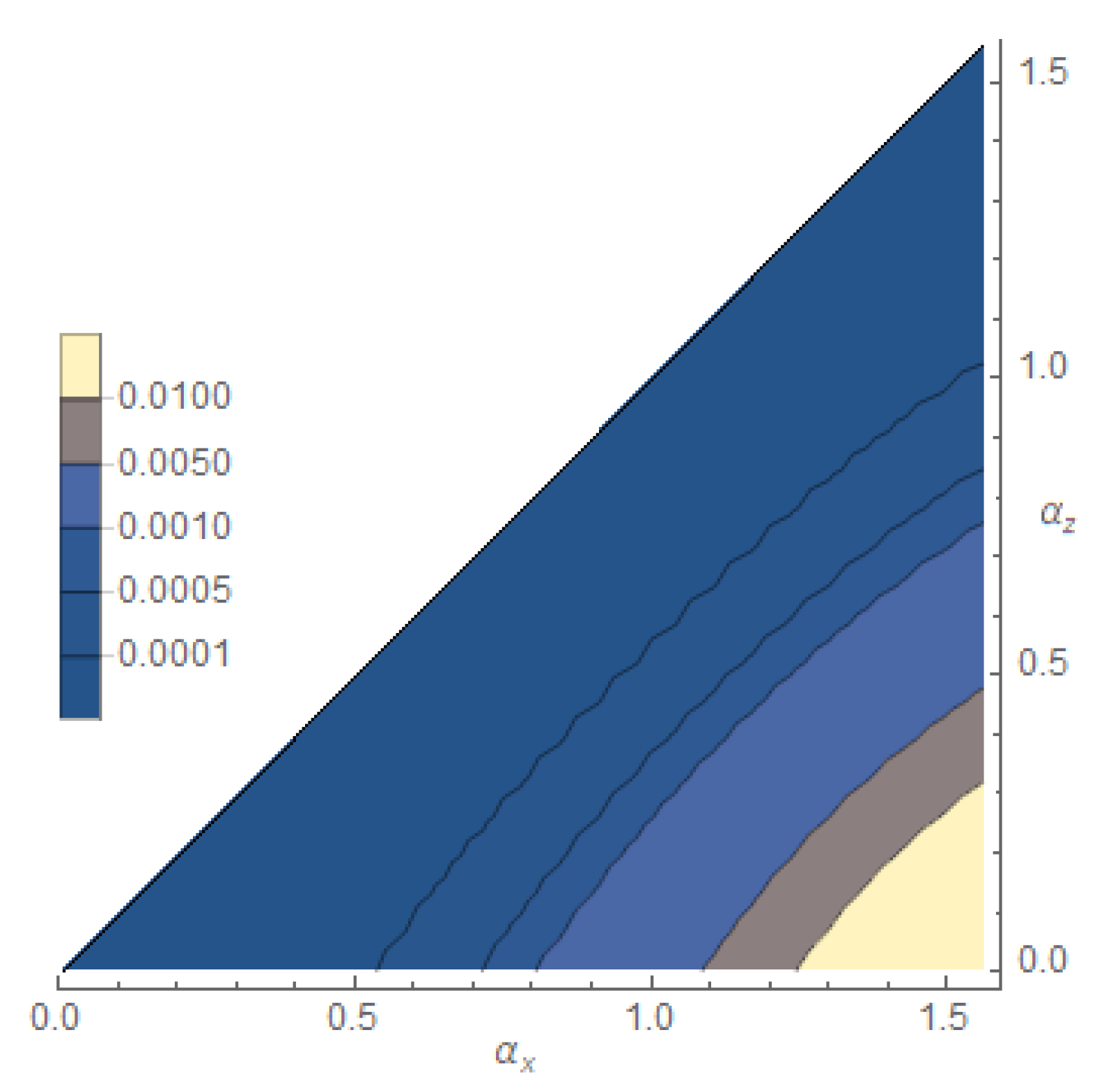
- Estimation of . In this case we took 325 points in the region , and for each point we estimated through and independently through likewise the previous case. Then we evaluated the privacywhose contour plot is reported in Figure 2. Notice that although can be made zero by choosing 1, this does not give the maximum privacy since in such a case also turns out to be zero. The maximum privacy is obtained when decrease to 0 and increase to .
- (iii)
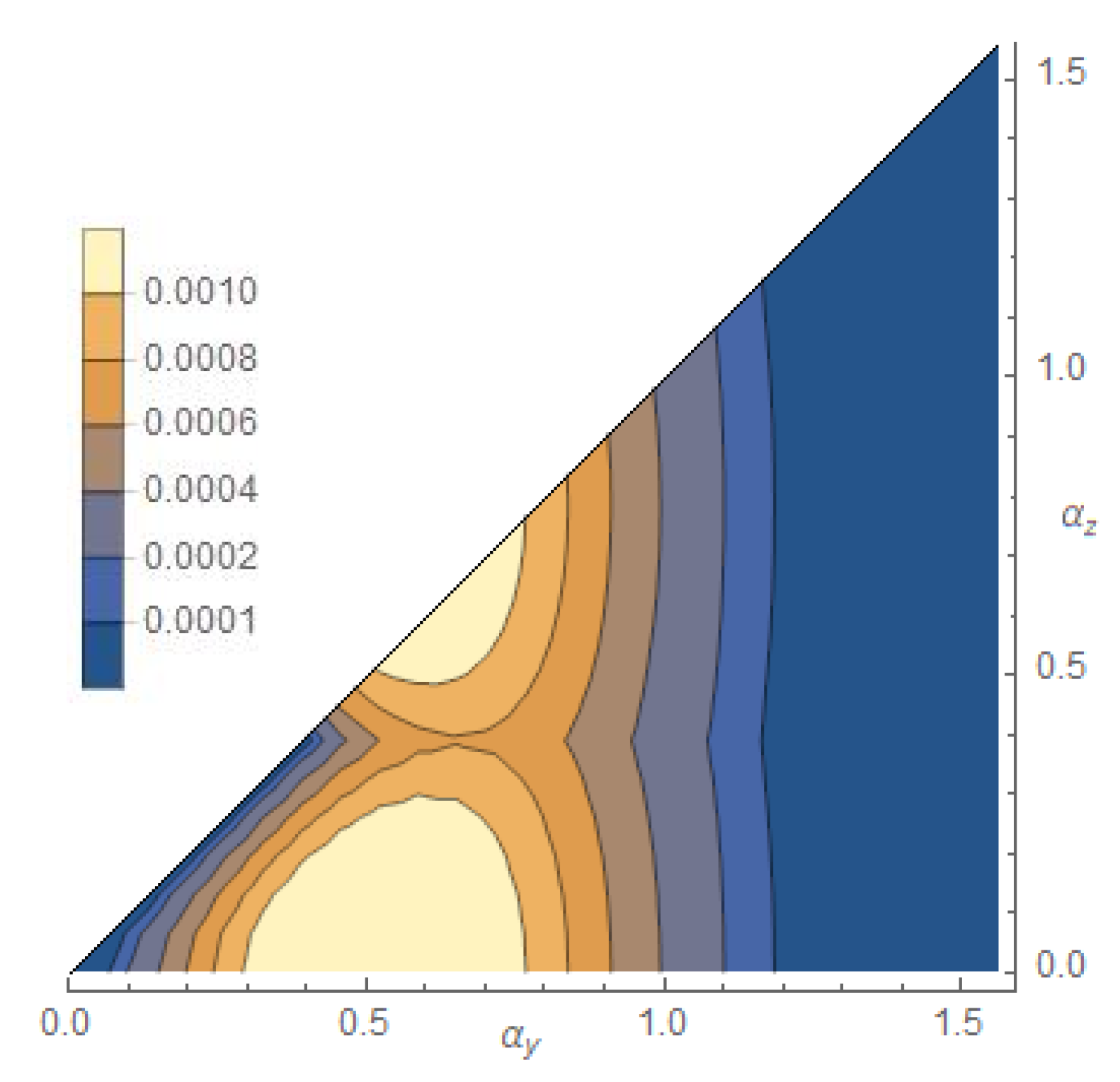
- Estimation of . In this last case we took 325 points in the region and for each point we estimated through and independently through . We actually computedwhose contour plot is shown in Figure 3.
4. Conclusion
Author Contributions
Funding
Conflicts of Interest
References
- Wilde, M.M. Quantum Information Theory; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Stinespring, W.F. Positive functions on C*-algebras. Proc. Am. Math. Soc. 1955, 6, 211. [Google Scholar]
- Cai, N.; Winter, A.; Yeung, R.W. Quantum privacy and quantum wiretap channels. Problems of Information Transmission. 2004, 40, 318, Devetak, I. The private classical capacity and quantum capacity of a quantum channel. IEEE Trans. Inf. Theory 2005, 51, 44. [Google Scholar] [CrossRef]
- Personick, S.D. Application of quantum estimation theory to analog communication over quantum channels. IEEE Trans. Inf. Theory 1971, 17, 240. [Google Scholar] [CrossRef]
- Rexiti, M; Mancini, S. Estimation of two-qubit interactions through channels with environment assistance. Int. J. Quantum Inf. 2017, 15, 1750053. [Google Scholar] [CrossRef]
- Rexiti, M.; Mancini, S. Adversarial versus cooperative quantum estimation. Quantum Inf. Processing 2019, 18, 102. [Google Scholar] [CrossRef]
| 1 | This choice by virtue of (7) forces to be exactly determined. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rexiti, M.; Mancini, S. Privacy in Quantum Estimation. Proceedings 2019, 12, 13. https://doi.org/10.3390/proceedings2019012013
Rexiti M, Mancini S. Privacy in Quantum Estimation. Proceedings. 2019; 12(1):13. https://doi.org/10.3390/proceedings2019012013
Chicago/Turabian StyleRexiti, Milajiguli, and Stefano Mancini. 2019. "Privacy in Quantum Estimation" Proceedings 12, no. 1: 13. https://doi.org/10.3390/proceedings2019012013
APA StyleRexiti, M., & Mancini, S. (2019). Privacy in Quantum Estimation. Proceedings, 12(1), 13. https://doi.org/10.3390/proceedings2019012013




