A Fractional Computer Virus Propagation Model with Saturation Effect
Abstract
1. Introduction
2. Notations and Terminologies
- (C1)
- f is continuous in the region .
- (C2)
- f is globally Lipschitz continuous with respect to x, i.e., there exists a positive constant C such that the following is true:
- (A1)
- Suppose all meet . Then, the origin is locally asymptotically stable.
- (A2)
- Suppose there exists such that . Then, the origin is unstable.
3. A Fractional Computer Virus Propagation Model
- ()
- External computers are physically connected to the network at constant rate (entrance rate).
- ()
- Every internal computer is physically disconnected from the network at constant rate (exit rate).
- ()
- When contacting with latent computers, susceptible internal computers become infected, do not perform virus-induced destructive operations, and hence become latent at time t at rate . Here, the constant is referred to as the infection force, while the constant is referred to as the saturation index.
- ()
- When contacting with bursting computers, susceptible internal computers become infected, perform virus-induced destructive operations, and hence become bursting at time t at rate .
- ()
- Due to transition from latency to burst, every latent computer becomes bursting at rate (burst rate).
- ()
- Due to recovery from burst, every bursting computer becomes susceptible at rate (recovery rate).
- ()
- Let denote the order of the Caputo derivative used in the subsequent modeling. Assume .
4. Basic Properties
5. Basic Reproduction Number
6. Virus–Endemic Equilibria
- (D1)
- is referred to as 0+ if , .
- (D2)
- is referred to as +0 if , .
- (D3)
- is referred to as ++ if , .
- (A1)
- Model (28) admits no +0 virus–endemic equilibrium.
- (A2)
- Model (28) admits a 0+ virus–endemic equilibrium if and only if . In this case, model (28) admits the following unique virus–endemic equilibrium:
- (A3)
- Model (28) admits a ++ virus–endemic equilibrium if and only if , . In this case, model (28) admits the following unique virus–endemic equilibrium:
7. Asymptotic Stability of the Equilibrium
- (A1)
- If , then is locally asymptotically stable.
- (A2)
- If , then is unstable.
8. Asymptotic Stability of the Equilibrium
- (A1)
- If , then is locally asymptotically stable.
- (A2)
- If , then is unstable.
9. Asymptotic Stability of the Equilibrium
- (A1)
- If , , then is locally asymptotically stable.
- (A2)
- If or , then is unstable.
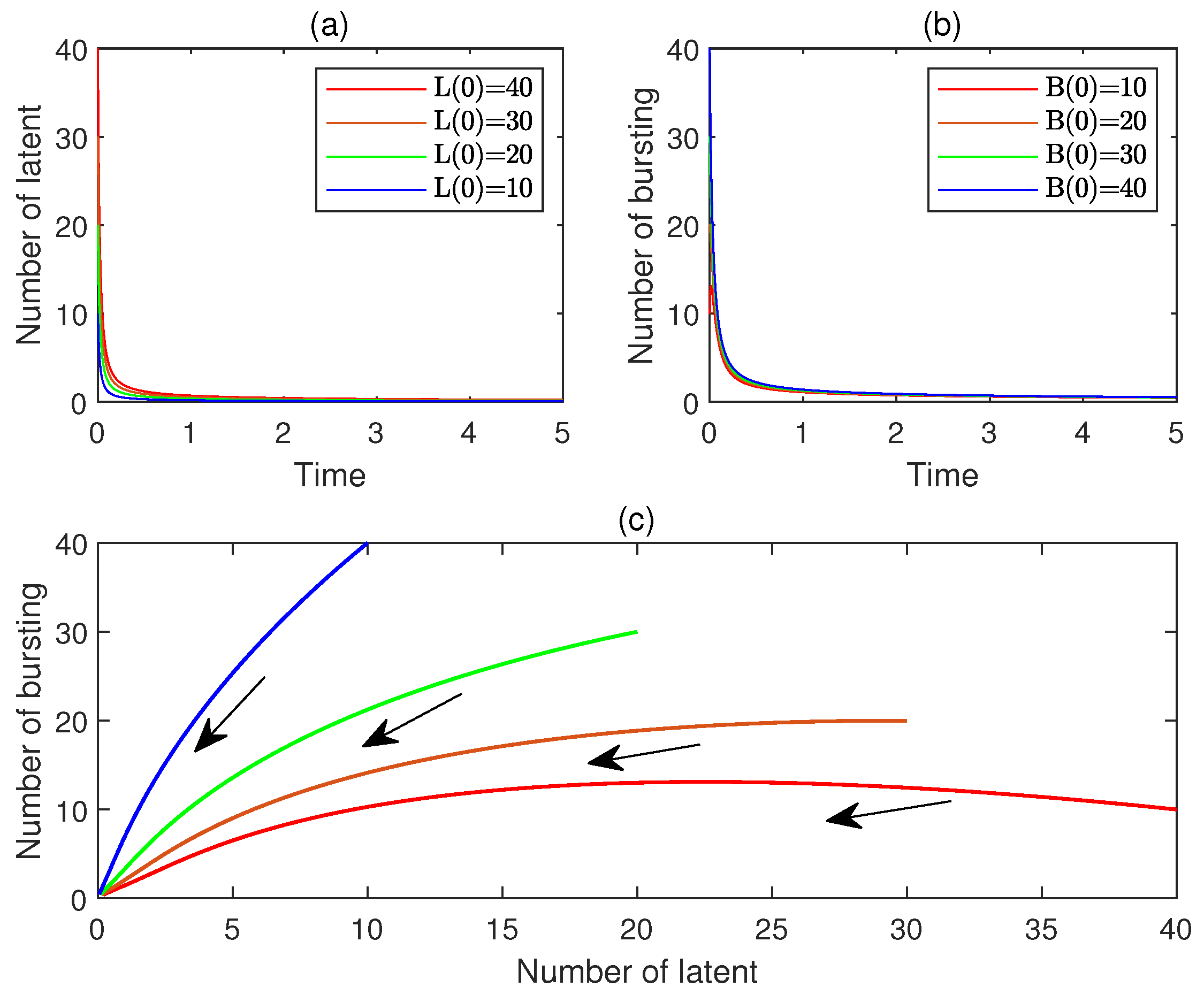
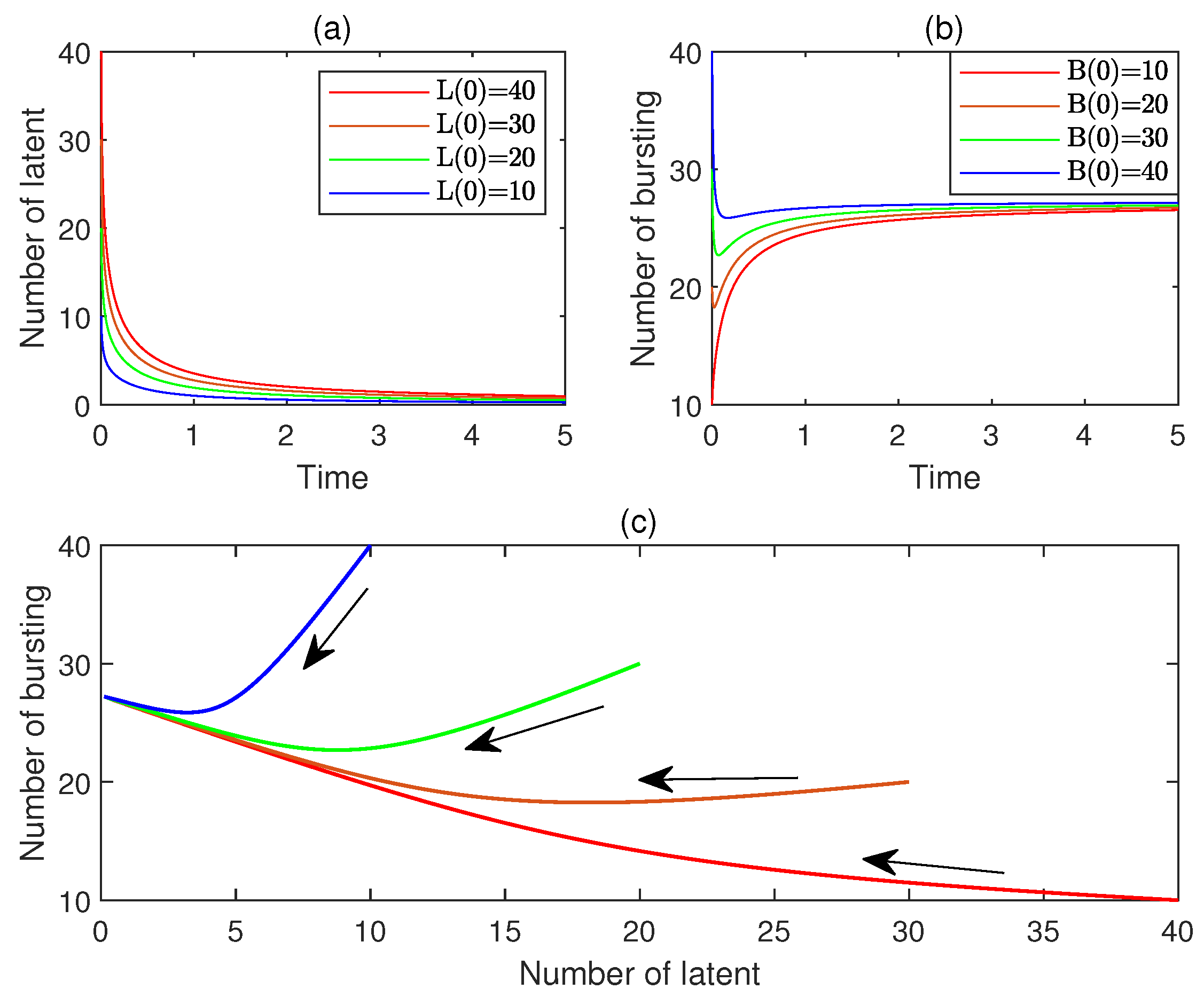
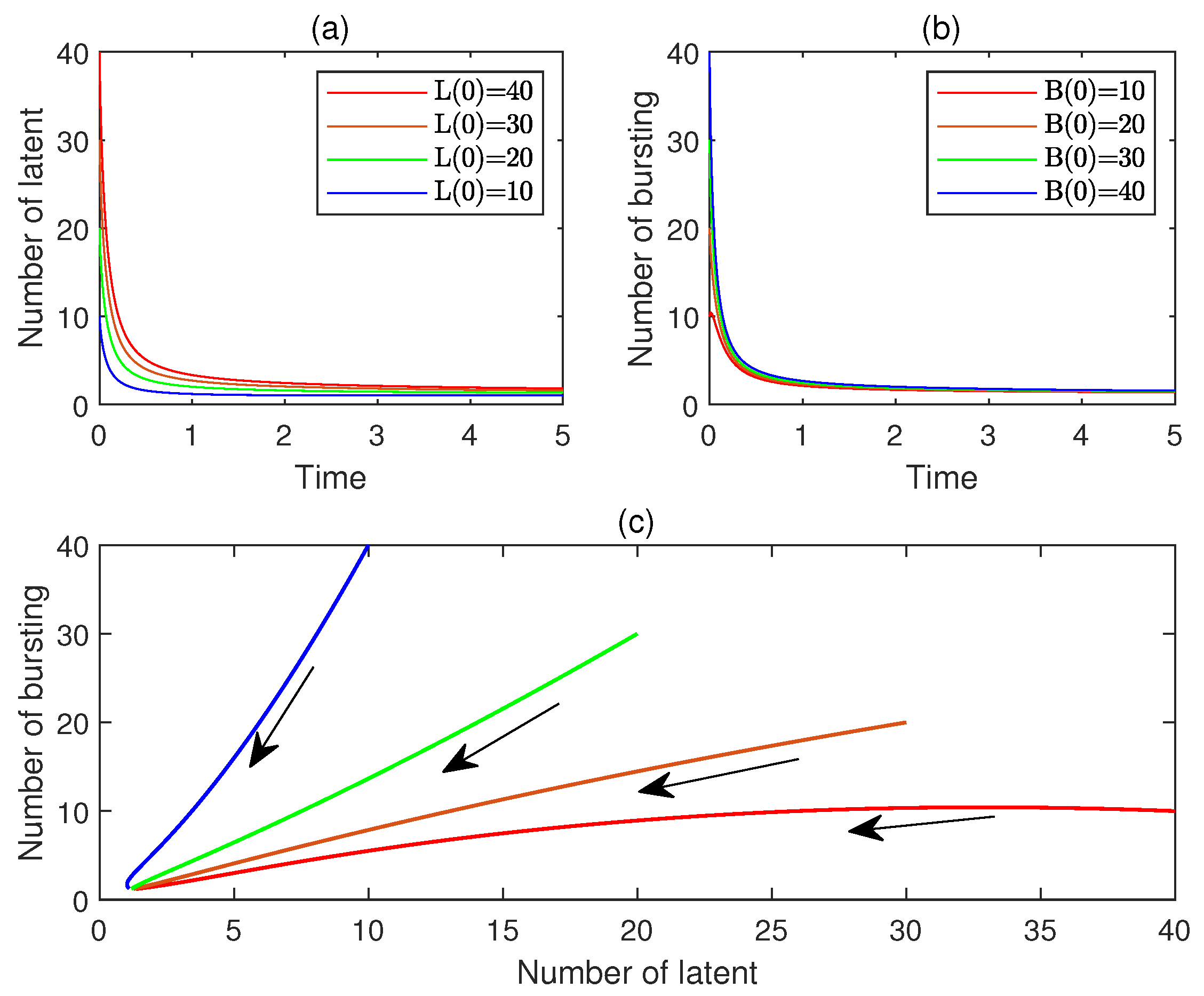
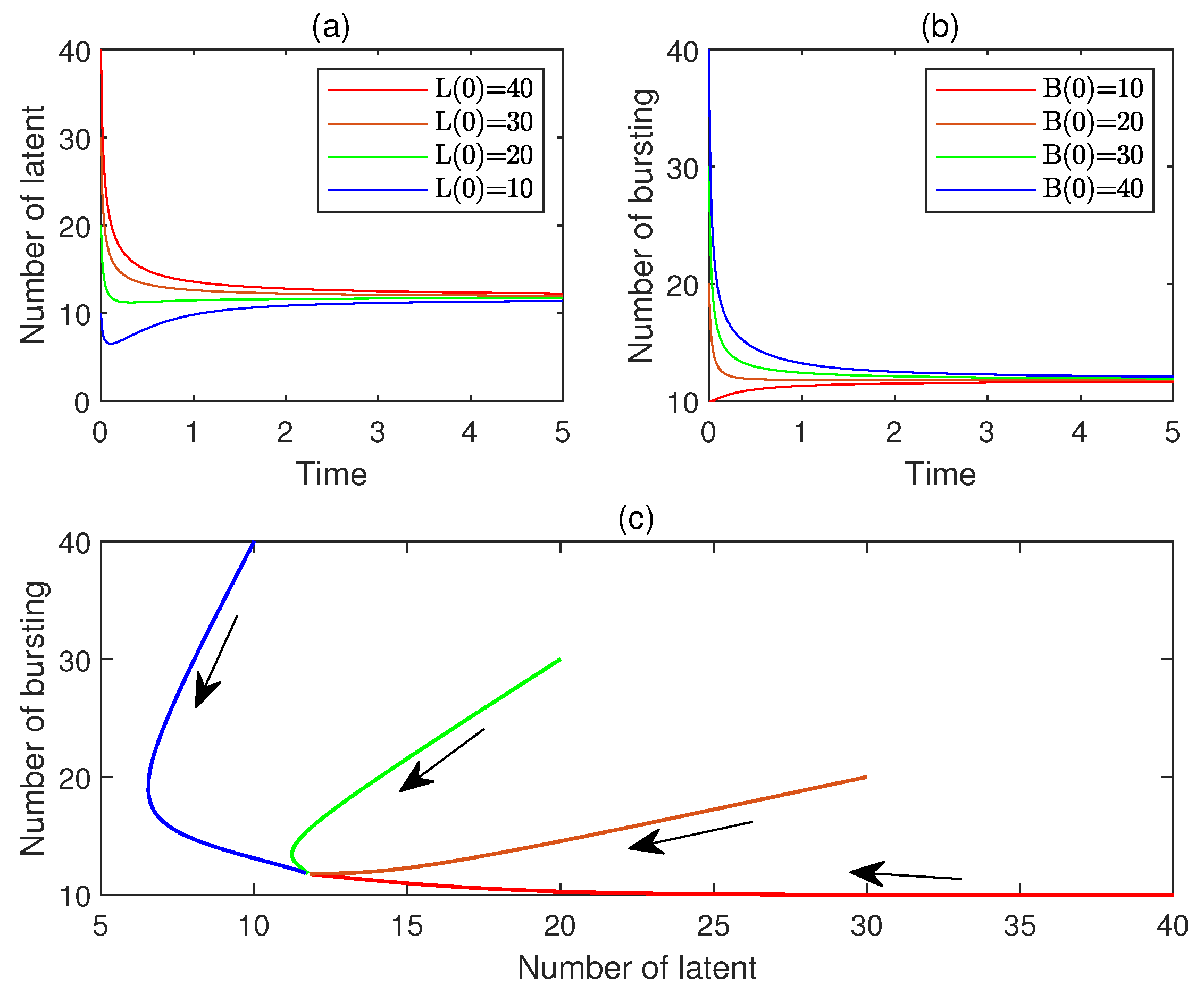
10. Numerical Simulations
11. Further Discussions
11.1. Sensitivity Analysis
- (A1)
- .
- (A2)
- .
- (A3)
- .
- (A4)
- or 0 according as or .
- (A5)
- or 0 according as or .
- (A6)
- .
- (i)
- The entrance rate has a significant positive impact on .
- (ii)
- The exit rate has a significant negative impact on . Furthermore, the strength of the impact strengthens with the increase in .
- (iii)
- The infection force has a significant positive impact on .
- (iv)
- In the case where , the burst rate has a significant negative impact on . Furthermore, the strength of the impact strengthens with the increase in .
- (v)
- In the case where , the burst rate has no impact on .
- (vi)
- In the case where , the recovery rate has a significant negative impact on . Furthermore, the strength of the impact strengthens with the increase in .
- (vii)
- In the case where , the recovery rate has no impact on .
- (viii)
- The saturation index has no impact on .
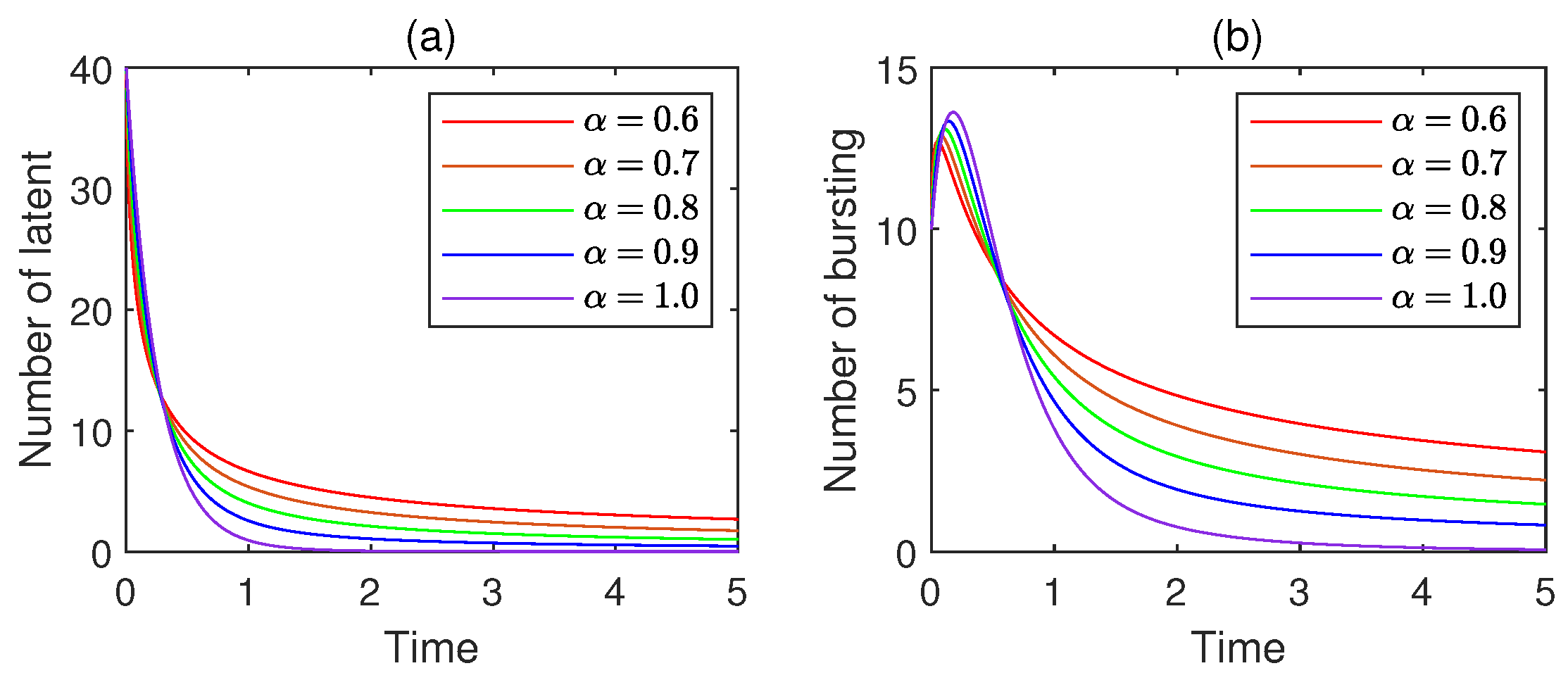
11.2. Impact of the Fractional Order
- (i)
- Compared with the corresponding integer-order model, a fractional-order SLBS model shows a slower spread rate of virus. Furthermore, the smaller the fractional order, the lower the virus propagation rate would be. This reflects the memory effect of the virus and the cumulative impact of historical infection information.
- (ii)
- The virus does not disappear completely after a long time, maintaining a low-level residual state. This is in line with the actual situation where the latent virus persists in the network.
- (iii)
- With the change in fractional order, the equilibrium point of virus prevalence can be adjusted flexibly, showing a complex dynamic transition process between different states.
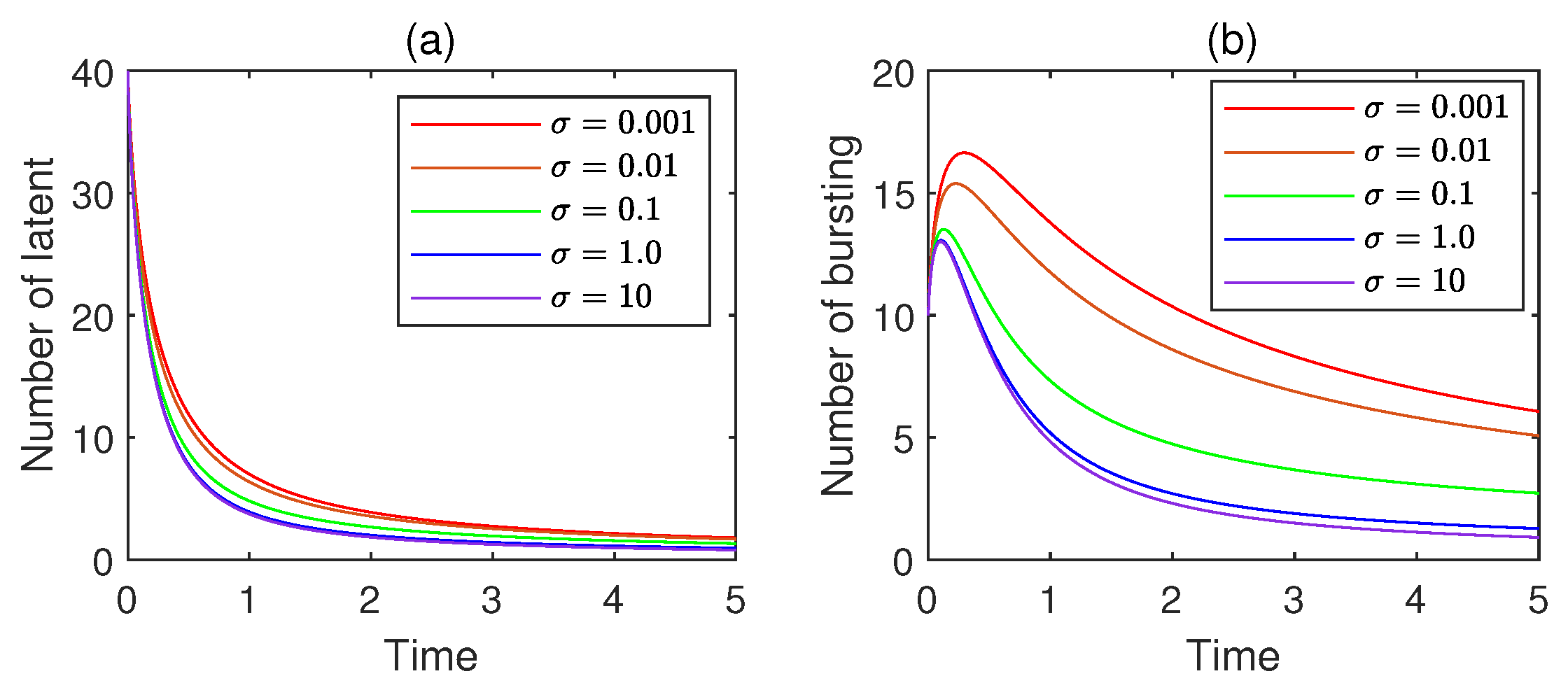
11.3. Impact of the Saturation Index
- (i)
- Saturation introduces a natural limit, reflecting real-world constraints like finite vulnerable devices, limited network bandwidth, or activated antivirus measures that slow spread as more devices become infected. Without saturation, the infection rate might grow indefinitely, leading to an implausible scenario where all susceptible devices become infected instantly.
- (ii)
- The virus spreads rapidly in the early stage when there are many susceptible devices and few barriers. However, as the number of infected devices increases, the infection rate plateaus due to saturation, causing the spread to decelerate. This results in a more realistic sigmoid curve, where the spread eventually stabilizes rather than exploding exponentially.
- (iii)
- By capturing the diminishing return of virus transmission, where each new infection becomes harder to achieve, this nonlinear saturation aligns the real-world behavior, making predictions of virus prevalence and spread dynamics more reliable.
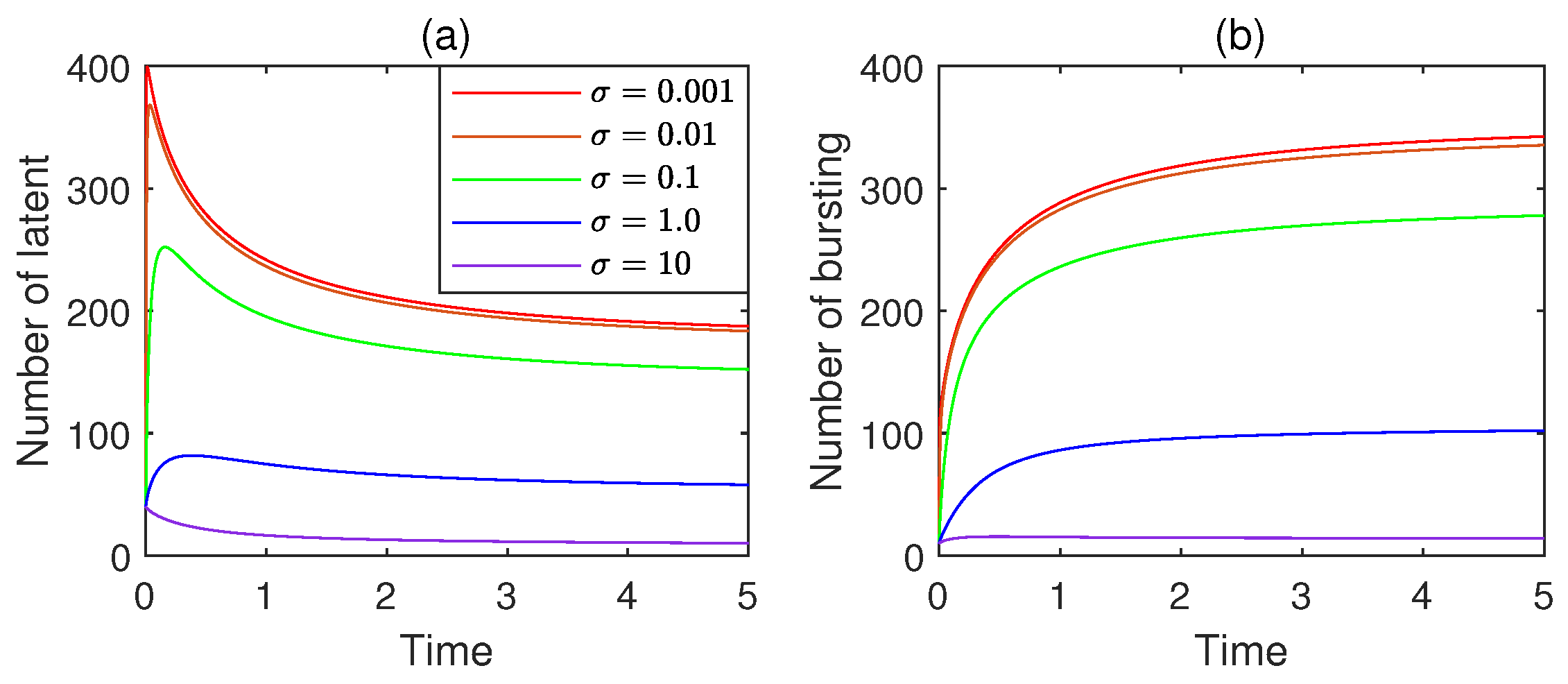
11.4. Coupling Effect of the Fractional Order and the Saturation Index
- (i)
- The coupling with saturation effects manifests as a dynamic interplay where the memory-dependent, non-local propagation characteristics of the fractional-order framework interact with the saturation mechanism, where the propagation rate slows or plateaus as the number of infected nodes approaches a system capacity (e.g., due to limited network resources, enhanced defense responses, or reduced susceptible nodes).
- (ii)
- The coupling leads to more realistic propagation dynamics, whereby the fractional-order component captures the historical influence and gradual rate changes, while the nonlinear saturation effect constrains excessive spread, reflecting real-world scenarios where propagation is limited by factors like protective measures, network load, or finite susceptible populations. Together, they yield a more accurate depiction of how viruses spread—balancing historical dependencies with the self-limiting nature of large-scale outbreaks.
12. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Proof of Lemma 7
References
- Szor, P. The Art of Computer Virus Research and Defense; Addison-Wesley Professional: Boston, MA, USA, 2005. [Google Scholar]
- Blancaflor, E.; Bauson, V.L.; Cruz, A.L.; Escandor, M. Medusa ransomware against data Privacy: A comprehensive study of ransomware attacks across various organizations and strategic recommendations for future prevention. In Proceedings of the 2024 7th International Conference on Information Science and Systems, New York, NY, USA, 31 January 2025; pp. 28–34. [Google Scholar]
- Britton, N.F. Essential Mathematical Biology; Springer: Heidelberg/Berlin, Germany, 2003. [Google Scholar]
- Kephart, J.O.; White, S.R. Directed epidemiological models of computer viruses. In Proceedings of the 1999 IEEE Computer Society Symposium on Research in Security and Privacy, Los Alamitos, CA, USA, 20–22 May 1991; pp. 343–359. [Google Scholar]
- Kephart, J.O.; White, S.R. Measuring and modeling computer virus prevalence. In Proceedings of the 1999 IEEE Computer Society Symposium on Research in Security and Privacy, Los Alamitos, CA, USA, 24–26 May 1993; pp. 2–15. [Google Scholar]
- Prakash, O.; Kumar, A.; Bharti, S.K. Computer virus propagation models: A mathematical review. J. Inf. Optim. Sci. 2023, 44, 1043–1055. [Google Scholar] [CrossRef]
- Zhang, W.; Yang, X.; Yang, L. A delayed malware propagation model under a distributed patching mechanism: Stability analysis. Mathematics 2025, 13, 2266. [Google Scholar] [CrossRef]
- Upadhyay, R.K.; Kumari, S. Bifurcation analysis of an e-epidemic model in wireless sensor network. Int. J. Comput. Math. 2018, 95, 1775–1805. [Google Scholar] [CrossRef]
- Yang, F.; Zhang, Z. Dynamics of a nonlinear SIQRS computer virus spreading model with two delays. AIMS Math. 2021, 6, 4083–4104. [Google Scholar] [CrossRef]
- Upadhyay, R.K.; Kumari, S.; Misra, A.K. Modeling the virus dynamics in computer network with SVEIR model and nonlinear incident rate. J. Appl. Math. Comput. 2017, 54, 485–509. [Google Scholar] [CrossRef]
- Zhao, T.; Zhang, Z.; Upadhyay, R.K. Delay-induced Hopf bifurcation of an SVEIR computer virus model with nonlinear incidence rate. Adv. Differ. Equ. 2018, 2018, 256. [Google Scholar] [CrossRef]
- Chu, Y.; Xia, W.; Wang, Z. A delayed computer virus model with nonlinear incidence rate. Syst. Sci. Control Eng. 2019, 7, 389–406. [Google Scholar] [CrossRef]
- Yu, X.; Zeb, A.; Zhang, Z. Mathematical analysis of a delayed malware propagation model on mobile wireless sensor network. Fractals 2022, 30, 2240160. [Google Scholar] [CrossRef]
- Liu, J.; Saeed, I.; Zeb, A. Delay effect of an e-epidemic SEIRS malware propagation model with a generalized non-monotone incidence rate. Results Phys. 2022, 39, 105672. [Google Scholar] [CrossRef]
- Zhang, Z.; Madhusudanan, V.; Murthy, B.S.N. Effect of delay in SMS worm propagation in mobile network with saturated incidence rate. Wirel. Pers. Commun. 2023, 131, 659–678. [Google Scholar] [CrossRef]
- Yao, Y.; Fu, Q.; Yang, W.; Wang, Y.; Sheng, C. An epidemic model of computer worms with time delay and variable infection rate. Secur. Commun. Netw. 2018, 2018, 9756982. [Google Scholar] [CrossRef]
- Podlubny, I. Fractional Differential Equations; Academic Press: Cambridge, MA, USA, 1999. [Google Scholar]
- Zarin, R.; Khaliq, H.; Khan, A.; Khan, D.; Akgul, A.; Humphries, U.W. Deterministic and fractional modeling of a computer virus propagation. Results Phys. 2022, 33, 105130. [Google Scholar] [CrossRef]
- Sabir, Z.; Raja, M.A.Z.; Mumtaz, N.; Fathurrochman, I.; Sadat, R.; Ali, M.R. An investigation through stochastic procedures for solving the fractional order computer virus propagation mathematical model with kill signals. Neural Process. Lett. 2023, 55, 1783–1797. [Google Scholar] [CrossRef]
- Zhou, Y.; Liu, B.; Zhou, K.; Shen, S. Malware propagation model of fractional order, optimal control strategy and simulations. Front. Phys. 2023, 11, 1201053. [Google Scholar] [CrossRef]
- Yang, L.; Song, Q.; Liu, Y. Dynamics analysis of a new fractional-order SVEIR-KS model for computer virus propagation: Stability and Hopf bifurcation. Neurocomputing 2024, 598, 128075. [Google Scholar] [CrossRef]
- Shi, X.; Luo, A.; Chen, X.; Huang, Y.; Huang, C.; Yin, X. The dynamical behaviors of a fractional-order malware propagation model in information networks. Mathematics 2024, 12, 3814. [Google Scholar] [CrossRef]
- Yang, L.X.; Yang, X.; Zhu, Q.; Wen, L. A computer virus model with graded cure rates. Nonlinear Anal. Real World Appl. 2013, 14, 414–422. [Google Scholar] [CrossRef]
- Yang, L.X.; Yang, X. A new epidemic model of computer viruses. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 1935–1944. [Google Scholar] [CrossRef]
- Yang, L.X.; Yang, X. The impact of nonlinear infection rate on the spread of computer virus. Nonlinear Dyn. 2015, 82, 85–95. [Google Scholar] [CrossRef]
- Ren, J.; Xu, Y. Stability and bifurcation of a computer virus propagation model with delay and incomplete antivirus ability. Math. Probl. Eng. 2014, 2014, 475934. [Google Scholar] [CrossRef]
- Zhao, T.; Wei, S.; Bi, D. Hopf bifurcation of a computer virus propagation model with two delays and infectivity in latent period. Syst. Sci. Control Eng. 2018, 6, 90–101. [Google Scholar] [CrossRef]
- Zhang, Z.; Kumari, S.; Upadhyay, R.K. A delayed e-epidemic SLBS model for computer virus. Adv. Differ. Equ. 2019, 2019, 414. [Google Scholar] [CrossRef]
- Li, C.; Liao, X. The impact of hybrid quarantine strategies and delay factor on viral prevalence in computer networks. Math. Model. Nat. Phenom. 2016, 11, 105–119. [Google Scholar] [CrossRef]
- Zhang, Z.; Upadhyay, R.K.; Bi, D.; Wei, R. Stability and Hopf bifurcation of a delayed epidemic model of computer virus with impact of antivirus software. Discret. Dyn. Nat. Soc. 2018, 2018, 8239823. [Google Scholar] [CrossRef]
- Ding, J.; Gul, N.; Liu, G.; Saeed, T. Dynamical aspects of a delayed computer viruses model with horizontal and vertical dissemination over internet. Fractals 2023, 31, 2340092. [Google Scholar] [CrossRef]
- Angstmann, C.N.; Henry, B.I.; McGann, A.V. A fractional-order infectivity SIR model. Phys. A 2016, 452, 8239823. [Google Scholar] [CrossRef]
- Angstmann, C.N.; Erickson, A.M.; Henry, B.I.; McGann, A.V.; Murray, J.M.; Nichols, J.A. A general framework for fractional order compartment models. SIAM Rev. 2021, 63, 375–392. [Google Scholar] [CrossRef]
- Xiao, D.; Ruan, S. Global analysis of an epidemic model with nonmonotone incidence rate. Math. Biosci. 2007, 208, 86–93. [Google Scholar] [CrossRef]
- Buonomo, B.; Rionero, S. On the Lyapunov stability for SIRS epidemic models with general nonlinear incidence rate. Appl. Math. Comput. 2010, 217, 4010–4016. [Google Scholar] [CrossRef]
- Diekmann, O.; Heesterbeek, J.A.P.; Metz, J.A.J. On the definition and the computation of the basic reproduction ratio R0 in models for infectious diseases in heterogeneous populations. J. Math. Biol. 1990, 28, 365–382. [Google Scholar] [CrossRef]
- van den Driessche, P.; Watmough, J. Reproduction numbers and sub-threshold endemic equilibria for compartmental models of disease transmission. Math. Biosci. 2002, 180, 29–48. [Google Scholar] [CrossRef] [PubMed]
- Robinson, R. An Introduction to Dynamical Systems: Continuous and Discrete; Pearson Education, Inc.: London, UK, 2005. [Google Scholar]
- Diethelm, K.; Neville, J.; Ford, N.J.; Freed, A.D. A predictor-correction approach approach for the numerical solution of fractional differential equations. Nonlinear Dyn. 2002, 29, 3–22. [Google Scholar] [CrossRef]
- Wu, G.; Zhang, Y.; Zhang, H.; Yu, S.; Yu, S.; Shen, S. SIHQR model with time delay for worm spread analysis in IIoT-enabled PLC network. Ad Hoc Netw. 2024, 160, 103504. [Google Scholar] [CrossRef]
- Nithya, D.; Madhusudanan, V.; Murthy, B.S.N.; Geetha, R.; Mung, N.X.; Dao, N.; Cho, S. Delayed dynamics analysis of SEI2RS malware propagation models in cyber–Physical systems. Comput. Netw. 2024, 248, 110481. [Google Scholar] [CrossRef]
- Wang, J.; Chang, X. A SEIQRS computer virus propagation model and impulse control with two delays. Math. Methods Appl. Sci. 2025, 48, 6851–6865. [Google Scholar] [CrossRef]
- Hanif, A.; Butt, A.I.K.; Ahmad, W. Numerical approach to solve Caputo-Fabrizio-fractional model of corona pandemic with optimal control design and analysis. Math. Methods Appl. Sci. 2023, 46, 9751–9782. [Google Scholar] [CrossRef]
- Butt, A.I.K.; Imran, M.; Azeem, K.; Ismaeel, T.; McKinney, B.A. Analyzing HIV/AIDS dynamics with a novel Caputo-Fabrizio fractional order model and optimal control measures. PLoS ONE 2024, 19, e0315850. [Google Scholar] [CrossRef]
- Imran, M.; Butt, A.I.K.; McKinney, B.A.; Al Nuwairan, M.; Al Mukahal, F.H.H.; Batool, S. A comparative analysis of different fractional optimal control strategies to eradicate Bayoud disease in date palm trees. Fractal Fract. 2025, 9, 260. [Google Scholar] [CrossRef]
- Ye, M.; Jiang, H. Bifurcation control for a fractional-order delayed SEIR rumor spreading model with incommensurate orders. Acta Math. Sci. 2023, 43B, 2662–2682. [Google Scholar] [CrossRef]
- Wei, C.; Fu, C.; Yang, X.; Qin, Y.; Yang, L. Stability analysis of a rumor-spreading model with two time delays and saturation effect. Mathematics 2025, 13, 1729. [Google Scholar] [CrossRef]
- Sheng, T.; Fu, C.; Yang, X.; Qin, Y.; Yang, L. Asymptotic stability of a rumor spreading model with three time delays and two saturation functions. Mathematics 2025, 13, 2015. [Google Scholar] [CrossRef]
- Jafar, M.T.; Yang, L.X.; Li, G.; Zhu, Q.; Gan, C. Minimizing malware propagation in Internet of Things networks: An optimal control using feedback loop approach. IEEE Trans. Inf. Forensics Secur. 2024, 19, 9682–9697. [Google Scholar] [CrossRef]
- Liu, G.; Fu, C.; Yang, X.; Yang, L.; Feng, Y.; Qin, Y. Study of the antivirus patch testing problem through optimal control modeling. PLoS ONE 2025, 20, e0319916. [Google Scholar] [CrossRef] [PubMed]
- Atangana, A. Fractal-fractional differentiation and integration: Connecting fractal calculus and fractional calculus to predict complex system. Chaos Solitons Fractals 2017, 102, 396–406. [Google Scholar] [CrossRef]
- Atangana, A.; Akgul, A.; Owolabi, K.M. Analysis of fractal fractional differential equations. Alex. Eng. J. 2020, 59, 1117–1134. [Google Scholar] [CrossRef]
- Akgul, A.; Fatima, U.; Iqbal, M.S.; Ahmed, N.; Raza, A.; Iqbal, Z.; Rafiq, M. A fractal fractional model for computer virus dynamics. Chaos Solitons Fractals 2021, 147, 110947. [Google Scholar] [CrossRef]
- Razi, N.; Bano, A.; Ishtiaq, U.; Kamran, T.; Garayev, M.; Popa, I.-L. Probing malware propagation model with variable infection rates under integer, fractional, and fractal–fractional orders. Fractal Fract. 2025, 9, 90. [Google Scholar] [CrossRef]
- Althubyani, M.; Saber, S. Hyers–Ulam stability of fractal–fractional computer virus models with the Atangana–Baleanu Operator. Fractal Fract. 2025, 9, 158. [Google Scholar] [CrossRef]





Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Z.; Yang, X.; Yang, L. A Fractional Computer Virus Propagation Model with Saturation Effect. Fractal Fract. 2025, 9, 587. https://doi.org/10.3390/fractalfract9090587
Liu Z, Yang X, Yang L. A Fractional Computer Virus Propagation Model with Saturation Effect. Fractal and Fractional. 2025; 9(9):587. https://doi.org/10.3390/fractalfract9090587
Chicago/Turabian StyleLiu, Zijie, Xiaofan Yang, and Luxing Yang. 2025. "A Fractional Computer Virus Propagation Model with Saturation Effect" Fractal and Fractional 9, no. 9: 587. https://doi.org/10.3390/fractalfract9090587
APA StyleLiu, Z., Yang, X., & Yang, L. (2025). A Fractional Computer Virus Propagation Model with Saturation Effect. Fractal and Fractional, 9(9), 587. https://doi.org/10.3390/fractalfract9090587





