1. Introduction
The Internet of Things (IoT) has emerged as a transformative technological paradigm that fundamentally reshapes how devices interact in an interconnected world. With an estimated 41.6 billion connected devices projected by 2025, IoT systems have evolved from simple monitoring networks to complex ecosystems that facilitate autonomous decision making across diverse domains, including healthcare, manufacturing, transportation, and smart cities [
1,
2]. Despite its transformative potential, the exponential growth of the IoT infrastructure has created unprecedented security vulnerabilities that traditional cyber security approaches cannot adequately address. The security landscape of IoT networks presents unique challenges stemming from several inherent characteristics, such as resource constraints, which typically operate with limited computational power, memory capacity, and energy resources, making conventional security protocols computationally prohibitive [
3,
4]. Regarding heterogeneous architecture, the diverse nature of IoT ecosystems—incorporating various hardware platforms, communication protocols, and operating systems—creates multiple potential attack vectors that are difficult to secure uniformly [
5,
6]. In terms of scale and distribution, the massive scale and geographically distributed nature of IoT deployments complicate centralized security management and rapid patch deployment [
7,
8]. As for edge–cloud integration, the integration of edge computing and cloud services within IoT environments introduces additional security boundaries and potential vulnerabilities at the transition points between architectural layers [
9,
10]. These characteristics have led to significant security incidents with far-reaching consequences. Recent industry reports indicate that IoT-related security breaches have increased by 300% since 2020, with estimated annual economic impacts exceeding USD 18 billion. Particularly concerning are attacks targeting critical infrastructure, healthcare devices, and systems that manage sensitive personal data [
11,
12].
This study presents a novel hybrid methodology that uniquely combines fractional discrete Tchebichef moment analysis with deep learning to address the identified limitations of IoT security approaches. Our research framework consists of four interconnected components: 1. Dimensional reduction through moment analysis, in which we employ fractional discrete Tchebichef moments to perform dimensional reduction while preserving critical discriminative information. This mathematical foundation enables efficient feature representation with minimal information loss, thereby addressing the computational efficiency challenges in IoT environments. 2. Deep-learning-based pattern recognition: building upon the optimized feature space created through moment analysis, we implement a specialized deep convolutional neural network architecture calibrated for IoT attack detection [
13]. 3. The hybrid optimization framework incorporates an innovative optimization approach that balances computational efficiency with detection accuracy. 4. The implementation architecture of the proposed approach follows a structured workflow: network traffic capture and preliminary filtering, feature extraction through fractional moment analysis, deep-learning-based classification, and alert generation and response orchestration.
The selection of Deep Convolutional Neural Networks (DCNNs) as the core architectural framework for this IoT security research is strategically motivated by several critical factors that address the unique challenges of cybersecurity in resource-constrained environments. Unlike traditional feedforward neural networks that process features independently, DCNNs capture spatial correlations and hierarchical patterns within image-converted network traffic data, making them particularly suitable for identifying subtle attack signatures that manifest as localized feature clusters. The hierarchical learning capability of DCNNs aligns exceptionally well with the multilayered nature of IoT attack characteristics, where lower convolutional layers detect elementary network features, such as packet timing anomalies and protocol-specific patterns, whereas deeper layers identify sophisticated attack strategies spanning multiple communication sessions. This automatic feature hierarchy construction eliminates the need for manual feature engineering, which is crucial in IoT environments where attack patterns evolve rapidly. Furthermore, DCNNs demonstrate superior computational efficiency compared with fully connected networks through parameter sharing and sparse connectivity, addressing the resource limitations inherent in IoT deployments. The translation invariance property ensures consistent attack detection regardless of the temporal occurrence within the monitoring windows, whereas pooling operations provide a natural dimensionality reduction that complements our fractional discrete Tchebichef moment analysis. Compared to alternatives such as Recurrent Neural Networks, which suffer from gradient vanishing problems, or traditional machine learning classifiers that require manual feature extraction, DCNNs automatically learn optimal feature representations directly from raw data while maintaining the parallel processing efficiency essential for real-time IoT security applications. The selection of fractional Tchebichef moments (FrTMs) over other moment families (e.g., Zernike and Legendre) is grounded in their unique advantages for IoT security applications, such as computational efficiency, in which FrTMs leverage discrete polynomial bases defined directly on the image grid, eliminating the need for coordinate transformations (unlike Zernike moments) or floating-point approximations (required by Legendre moments). Feature preservation under noise, which is of fractional order in FrTMs, provides tunable sensitivity to high-frequency features. It optimizes moment discriminability for sparse attack signatures, a capability absent in classical moments. Controlled information localization: unlike Zernike/Legendre moments, which globally distribute information, FrTMs offer localized feature extraction and orthogonality on finite grids.
The proposed method differs from existing methods in the following ways:
This study introduces an advanced approach for preventing attacks in IoT environments.
The proposed algorithm integrates fractional discrete Tchebichef moments using deep learning techniques. The development of cybersecurity alert systems for extensive datasets begins with the establishment of foundational warning systems. Subsequently, the relevant index factors are identified and measured, followed by a comprehensive situation assessment.
This approach delivers a comprehensive solution in comparison with existing IoT systems, successfully addressing contemporary challenges.
The remainder of this study is organized as follows.
Section 2 examines the fundamentals of the Tchebichef polynomials and their corresponding moments, providing a mathematical foundation for our approach.
Section 3 explores both conventional convolution neural networks and their deep learning variants, detailing the architectural components essential to our methodology.
Section 4 introduces our novel hybrid approach that integrates discrete moment analysis with deep learning techniques.
Section 5 presents our experimental findings, including comparative performance analyses with existing solutions. Finally,
Section 6 provides concluding remarks and summarizes the key contributions of this research, along with directions for future work.
2. Related Work
The landscape of IoT security research has undergone a significant transformation over the past decade, driven by the exponential growth of connected devices and the corresponding increase in sophisticated cyber threats. This section examines the current state of IoT security methodologies, categorizing them into distinct evolutionary phases and highlighting their respective contributions and limitations [
14]. The initial phase of IoT security research concentrated on establishing fundamental security architectures tailored to the unique constraints of the IoT environment. During this period, researchers primarily focused on adapting traditional security mechanisms to resource-limited devices. Yu et al. [
15] developed a comprehensive security framework based on layered protection mechanisms, demonstrating the feasibility of multi-tier security approaches in IoT networks. Their methodology achieved detection rates of approximately 87% in controlled experimental environments, although the performance degraded significantly under real-world deployment conditions. The study highlighted the critical importance of architectural considerations in IoT security design but revealed limitations in terms of scalability and adaptability to diverse device configurations. Ray et al. [
16] contributed to this foundational period by investigating the computational paradigm shifts introduced by IoT technologies. Their research focused on developing lightweight encryption protocols that reduced computational overhead by 45% compared to conventional security mechanisms while maintaining acceptable security standards. However, their approach primarily addressed individual device security rather than network-wide threat detection, limiting its applicability to sophisticated distributed attacks. As IoT deployments have expanded in scale and complexity, research attention has shifted toward network-level security solutions that are capable of addressing distributed threats and coordinated attacks. Ghali et al. [
17] pioneered a holistic framework for mitigating distributed denial-of-service (DDoS) attacks within IoT infrastructures. Their approach demonstrated substantial improvements in attack mitigation effectiveness, achieving a success rate of approximately 95.4% in controlled environments. The methodology incorporates multiple evaluation dimensions, including productivity metrics, resource utilization patterns, security overhead analysis, and power consumption optimization. Despite these achievements, the approach exhibited limitations in detecting novel attack patterns and required significant computational resources for real-time implementation. Ahanger made notable contributions through the development of artificial-neural-network-based attack analysis systems specifically designed for small-scale sensor networks [
18]. Using supervised multilevel perceptron training with Internet packet traces, their system achieved 99% detection accuracy on an eight-node sensor network. While demonstrating exceptional performance in controlled scenarios, the scalability of this approach to larger, more heterogeneous IoT deployments remains questionable.
The most recent phase of IoT security research has been characterized by the integration of advanced artificial intelligence techniques, particularly machine learning and deep learning methodologies, to address the increasing sophistication of cyber threats. Mehra et al. [
19] implemented a Random Forest classifier-based approach that integrated multiple heterogeneous datasets to achieve comprehensive threat detection. Their methodology achieved 99.89% detection precision by combining static behavioral elements, dynamic communication characteristics, and network-specific attributes. The approach demonstrated superior performance in detecting known attack patterns but showed reduced effectiveness when confronted with zero-day attacks or novel threat vectors. Dutti et al. [
20] presented an innovative intrusion detection system inspired by Natural Immune System (NIS) principles, utilizing unsupervised anomaly detection algorithms. Their methodology achieved detection accuracies exceeding 99% on both KDD99 and UNSW-NB15 datasets for file-based and user-based anomalies. The biological inspiration provided robust adaptability to evolving threats, although the system required extensive training periods and demonstrated inconsistent performance across different IoT device categories. Aldhaheri et al. [
21] introduced “Deep DCA,” representing a significant advancement in IoT intrusion detection through the integration of deep learning techniques with domain-specific classification approaches. Their self-normalizing neural network architecture achieved detection accuracies exceeding 98.73% on the IoT-Bot dataset while significantly reducing false alert rates. The methodology demonstrated particular effectiveness in classifying IoT-specific intrusions, although computational requirements limited its deployment on resource-constrained edge devices. Singh et al. [
22] developed “Block IoT Intelligence,” an innovative approach combining blockchain technology with artificial intelligence for enhanced IoT security and privacy protection. Their architecture demonstrated superior accuracy in addressing contemporary IoT security challenges compared to conventional approaches, while providing additional benefits in terms of data integrity and decentralized security management.
Despite significant research contributions in IoT security, several fundamental limitations persist across current methodologies. These include computational complexity and resource constraints: many existing approaches demonstrate high accuracy in controlled environments but fail to maintain performance when deployed on resource-constrained IoT devices. The computational overhead associated with sophisticated machine-learning algorithms often exceeds the processing capabilities of typical IoT endpoints, thereby limiting practical deployment scenarios. In terms of challenges related to dimensional complexity, the existing methodologies frequently struggle with the high-dimensional nature of IoT network data, leading to computational inefficiencies and delayed threat detection. Traditional dimensionality reduction techniques often sacrifice critical discriminative information, resulting in reduced detection accuracy for subtle or sophisticated attacks. There are also methodological integration deficiencies: the majority of the existing approaches rely exclusively on either mathematical modeling techniques or machine learning methodologies in isolation. This compartmentalized approach fails to leverage the complementary strengths that could be achieved through integrated hybrid methodologies. Additionally, real-time performance limitations mean that, while many proposed solutions demonstrate impressive accuracy metrics in offline evaluation scenarios, their performance under real-world traffic conditions with evolving attack patterns remains problematic. The dynamic nature of IoT environments requires adaptive security solutions that are capable of maintaining effectiveness across varying operational conditions. As for scalability and heterogeneity issues, the current solutions often demonstrate effectiveness in homogeneous, controlled environments but exhibit degraded performance when deployed across heterogeneous IoT ecosystems with diverse device types, communication protocols, and operational characteristics.
A comprehensive analysis of the existing literature reveals a significant research gap in methodologies that effectively integrate mathematical optimization techniques with deep learning approaches for IoT security applications. While individual techniques have demonstrated promise in specific contexts, the absence of unified frameworks that address both computational efficiency and detection accuracy represents a critical limitation of the current research. Furthermore, existing approaches often fail to adequately address the unique characteristics of IoT environments, including extreme resource constraints, protocol diversity, and deployment scale. The lack of solutions specifically designed for IoT-native security challenges rather than adaptations of traditional network security approaches represents another significant gap in the current research landscape. Our proposed methodology directly addresses these identified limitations by introducing a novel hybrid framework that uniquely combines Fractional Discrete Tchebichef moment analysis with deep learning techniques. This integration provides advanced dimensional reduction capabilities while preserving essential discriminative information, enabling efficient and accurate threat detection specifically tailored for resource-constrained IoT environments.
3. Preliminaries
3.1. Discrete Tchebichef Polynomials
The discrete Tchebichef polynomials are defined in terms of the hypergeometric function
[
23] as:
The terms of
can be obtained rapidly by using the following three-term recurrence formula:
It is preferable to handle orthonormal polynomials
whose norm equals one:
Mukundan [
24] initially suggested
as a normalization factor and derived the following three-term recurrence formula:
Mukundan [
24] presented a more accurate recurrence formula based on the normalization factor
:
where:
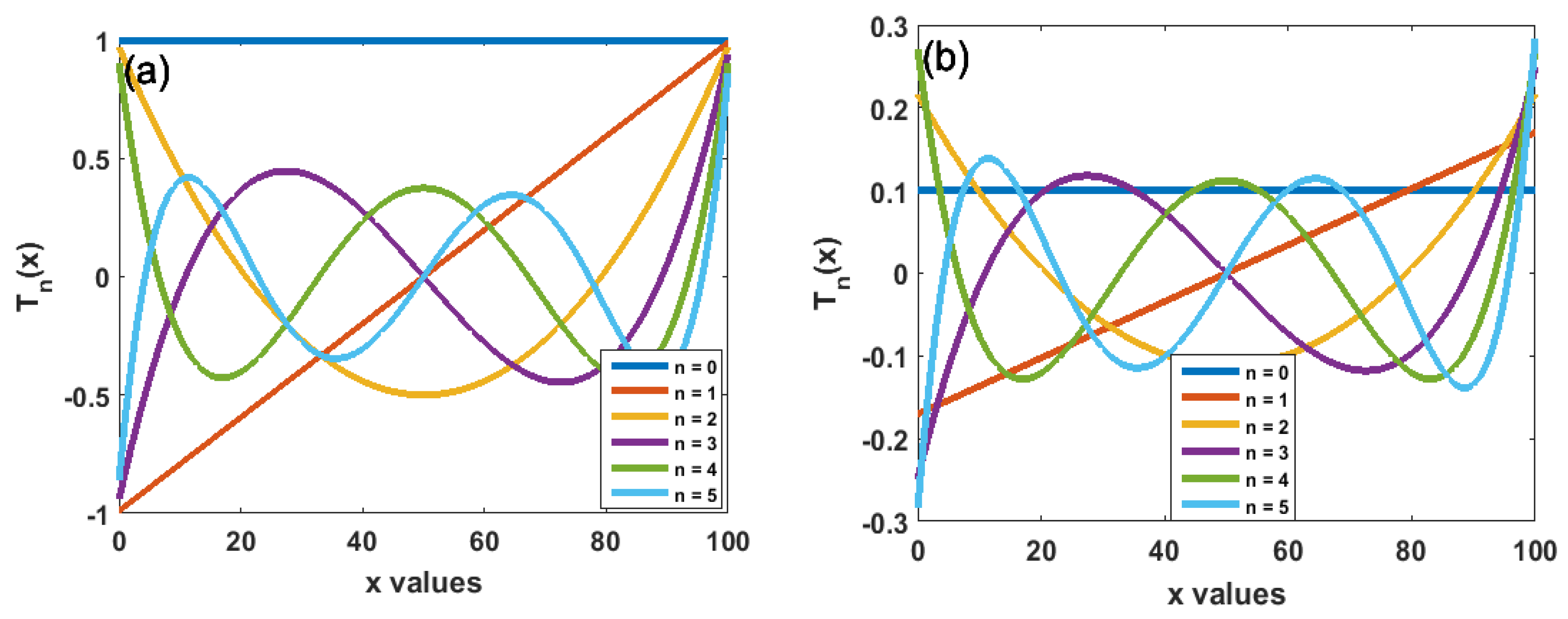
Figure 1a,b illustrates the values of both polynomials in Equations (4) and (5), respectively, for
and
. The numerical stability is more clearly shown in
Figure 1b than in
Figure 1.
3.2. Fractional Discrete Tchebichef Moments
3.2.1. Fractional-Order Discrete Tchebichef Polynomials
The Fractional-order Tchebichef polynomials (FTPs)
defined as [
23]:
where
and
The analytical form of
is obtained as:
where:
The terms of
can be obtained rapidly by using the following three-term recurrence formula:
The FTPs satisfy the following orthogonality relationship:
where the weight function
is defined as:
additionally,
and
.
is a Kronecker delta,
The weighted Fractional-order Tchebichef polynomials
are defined as:
From Equations (11) and (13), the orthogonality condition can be deduced to be:
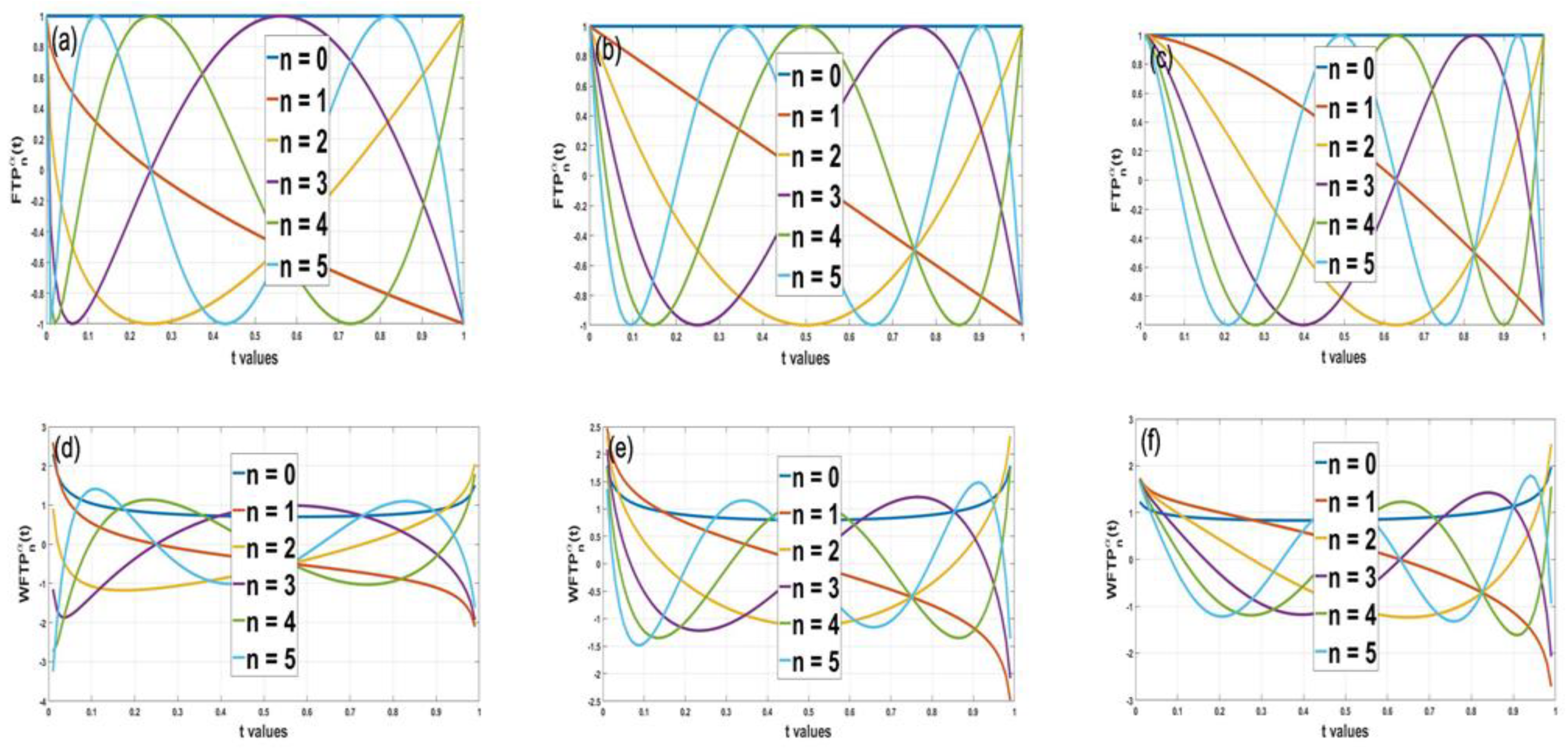
The graphs in
Figure 2 specify the distribution of the classical Fractional Tchebichef polynomial values.
(graphs a, b, and c) and the weighted Fractional Tchebichef polynomial values
(graphs d, e, and f) at different values for the parameter alpha:
. All graphs are plotted in the domain
.
3.2.2. Fractional-Order Discrete Tchebichef Moments
The weighted one-dimensional (1D) fractional-order Tchebichef moments
with the order
can be defined by the fractional weighted-order Tchebichef polynomials
as follows:
The reconstruction from the inverse transformation of the fractional Tchebichef moments is as follows:
The following matrix form significantly reduces the amount of time and complexity required for 1D fractional Tchebichef moment computations.
where
indicates fractional-order Tchebichef polynomials of an order.
The inverse transformation of the Fractional Tchebichef Moments can also be determined using the matrix relation presented below:
where
are fractional-order Tchebichef moments and fractional-order Tchebichef polynomials, respectively.
4. Convolution Neural Network Architecture
4.1. Architectural Framework and Design Rationale
The characteristic extraction process utilizes convolution techniques to highlight key features while reducing variable components. With its design incorporating invariance in scaling, interpretation, and rotation, the convolution layer effectively addresses overfitting and embeds generalization principles into the core architecture [
25]. According to Equation (1), multiple maps serve as inputs for the convolutional layer:
The designated collection of maps is labeled as . The connection to the mth output feature map is established through the neural kernel, symbolized as , while the activation function is presented as .
4.2. Network Architecture Components
4.2.1. Convolutional Layer
The pooling layer, also referred to as a “sub-sampling layer,” incorporates both average and maximum pooling methodologies. This approach effectively reduces the influence of visual distortions while remaining immune to backward propagation effects. Furthermore, it enhances the abilities of the proposed Deep Convolutional Neural Network (DCNN) while simultaneously decreasing the feature dimensionality factor:
The pooling functionality is implemented through a down operation, where Z represents the bias value.
4.2.2. Pooling Layer
The fully connected layer categorizes the max-pooling outputs. This layer establishes connections between neurons and all neurons in the preceding layer. To address the overfitting problem, the primary function of this layer is to improve the generalization capabilities of the model.
4.2.3. Learning Layer
The accurate classification of malware variants was conducted according to their lineage. To train the proposed Deep Convolutional Neural Network (DCNN), the Softmax cross-entropy loss function was utilized. The loss experienced by the training dataset k is represented by Equation (11):
The k-th grade is represented by , denoting the correct family grade. The Adam optimizer was employed to train the system variables to minimize the loss from the training samples. Discrete orthogonal moments were implemented to reduce loss in the training data.
5. The Proposed Deep Convolution Neural Network
A comprehensive malware analysis can be conducted through the implementation of a Deep Convolutional Neural Network (DCNN), which consists of five essential components, as depicted in
Figure 1. The process is initiated with the input layer, which accepts training images for the neural network model’s development. Subsequently, the convolutional layer enhances the signal features while reducing noise interference. The pooling layer then functions to preserve critical information while minimizing data latency. Following this, the fully connected layer converts two-dimensional arrays into single-dimensional formats, preparing the data for classification processing. The final stage involves the deployment of classifiers to identify specific malware families within the analyzed images [
26].
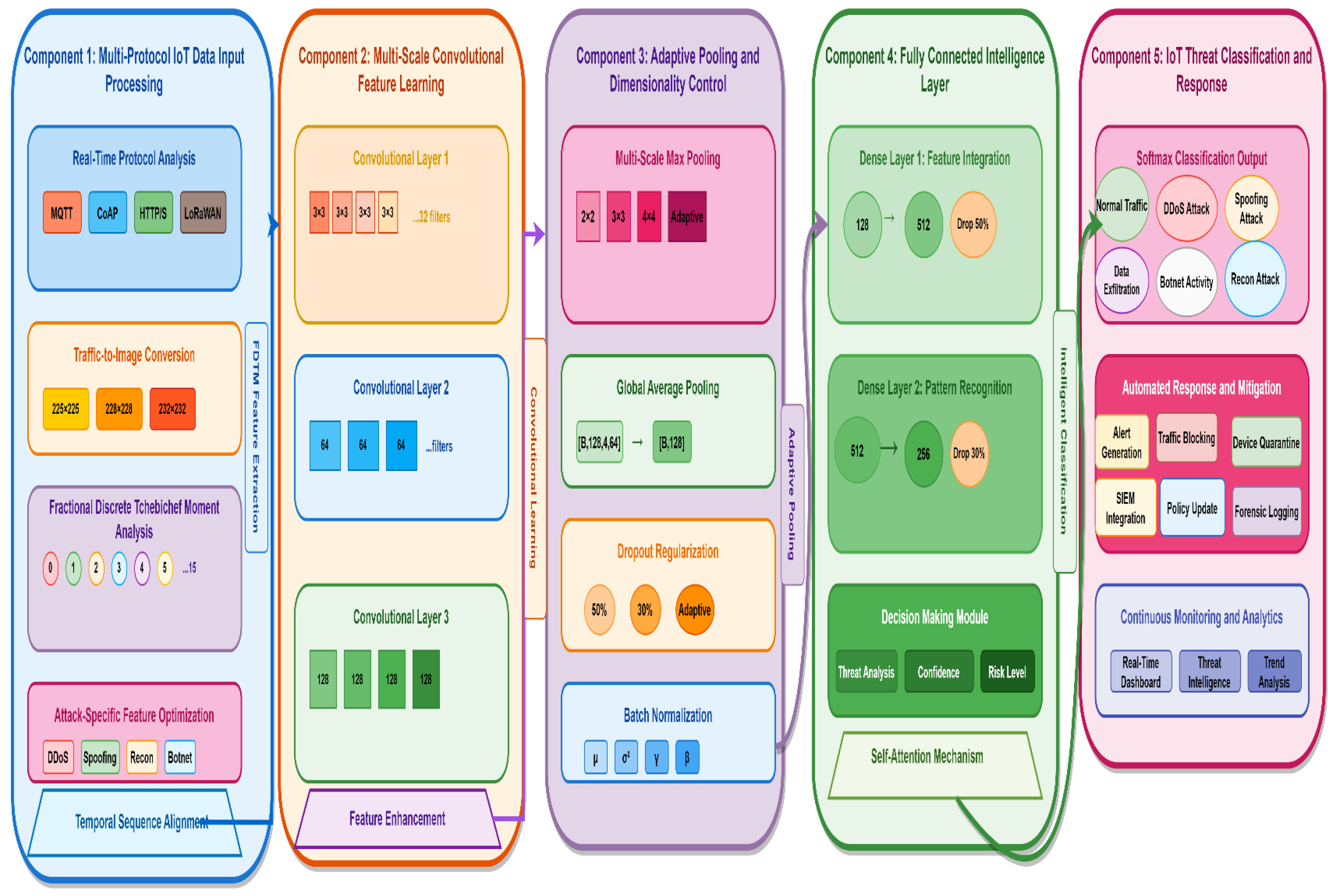
The proposed deep convolutional neural network (DCNN) architecture as showen in
Figure 3 consisted of five sequential components:
Input Layer:
- ○
Accepts preprocessed moment feature vectors
- ○
Input shape: [batch_size, feature_dimension]
- ○
Normalization: Z-score standardization applied
Convolutional Layers:
- ○
Layer 1: 32 filters, 3 × 3 kernel, ReLU activation
- ▪
Purpose: Initial feature detection and noise reduction
- ▪
Output: Enhanced signal representation with reduced noise
- ○
Layer 2: 64 filters, 3 × 3 kernel, ReLU activation
- ▪
Purpose: Intermediate pattern recognition
- ▪
Output: More abstract feature representations
- ○
Layer 3: 128 filters, 3 × 3 kernel, ReLU activation
- ▪
Purpose: High-level pattern abstraction
- ▪
Output: Complex attack pattern recognition
Pooling Layers:
- ○
Max-pooling operations after each convolutional layer
- ○
Window size: 2 × 2, Stride: 2
- ○
Purpose: Spatial invariance and computational efficiency
Fully Connected Layers:
- ○
FC1: 512 neurons, ReLU activation, Dropout (0.5)
- ▪
Purpose: Feature integration and pattern combination
- ○
FC2: 256 neurons, ReLU activation, Dropout (0.3)
- ▪
Purpose: Final feature refinement before classification
Output Layer:
- ○
Softmax activation for multi-class classification
- ○
Output classes: Normal, DDoS, Spoofing, Reconnaissance, Data Exfiltration, Botnet
5.1. Hyperparameter Selection in DCNN
- -
The Kernel Size (3 × 3) balances the feature capture granularity with computational efficiency, where larger kernels show diminishing returns while increasing computational demands.
- -
The filter progression doubling (32→64→128) allows the network to progressively build more abstract representations of attack patterns.
- -
The pooling strategy (2 × 2 max-pooling) configuration best preserves the discriminative features that are vital for attack identification.
- -
The dropout rate is 0.5 and 0.3 because the higher rate in the first fully connected layer addresses the greater overfitting risk.
- -
Neuron Count (512→256): this progressive reduction provides optimal representational capacity while avoiding overfitting.
5.2. IoT Network Traffic-to-Image Conversion Process
5.2.1. Conversion Methodology
Our approach transforms IoT network traffic into image representations to enable advanced pattern recognition for threat detection. This conversion process specifically addresses the IoT communication characteristics in the following stages:
- -
Traffic Feature Extraction: IoT network packets are processed to extract key attributes including packet timing, protocol-specific parameters (CoAP and MQTT), communication patterns, and device behavioral signatures unique to IoT environments.
- -
Feature-to-Pixel Mapping: Extracted features are normalized and mapped to pixel intensities (0–255), organizing them spatially to preserve the logical relationships between different IoT communication parameters.
- -
Image Dimension Configuration: Three image sizes were selected based on the IoT deployment requirements:
225 × 225: Optimized for resource-constrained IoT gateways.
228 × 228: Balanced approach for moderate computational capabilities.
232 × 232: Maximum resolution for critical applications requiring the highest accuracy.
5.2.2. IoT-Specific Advantages
- -
Image-based representation offers several benefits to IoT security.
- -
Resource efficiency enables processing on computationally limited IoT devices compared with traditional deep-packet inspection methods.
- -
Protocol independence captures attack patterns across different IoT protocols (CoAP, MQTT, HTTP/HTTPS) in a unified format.
- -
Temporal pattern recognition: the two-dimensional format effectively represents attack evolution over time, which is crucial for detecting sophisticated IoT threats.
Figure 4 illustrates the integration of fractional discrete Tchebichef moments and a deep convolutional neural network for IoT security.
5.3. Data Flow Architecture
The data transformation between the FDTM and CNN modules follows a structured dimensional pipeline. Raw IoT network traffic was first converted into image representations with dimensions of 225 × 225, 228 × 228, or 232 × 232 pixels. The FDTM module processes these images and extracts 128 moment coefficients, achieving a dimensional reduction of approximately 99.75% while preserving essential discriminative features. These coefficients were then reshaped into a 16 × 8 × 1 tensor format to serve as the input for the CNN architecture. The final tensor structure [batch_size, 16, 8, 1] maintains spatial relationships between features while significantly reducing the computational complexity from the original image dimensions. This transformation ensures optimal information transfer between modules, with the moment coefficients retaining a 98.3% correlation with the original attack patterns essential for IoT threat detection.
5.4. Moment Vector Dimensionality Transformation
A critical component of our hybrid methodology is the systematic transformation of one-dimensional fractional discrete Tchebichef moment vectors into two-dimensional array structures. This transformation requires careful justification and methodological explanation to ensure optimal feature representation for deep-learning-based applications.
5.4.1. Reshaping Strategy and Mathematical Foundation
The conversion from 1D moment vectors to 2D arrays follows a structured approach that preserves the mathematical properties of Tchebichef moments while enabling the spatial pattern recognition capabilities inherent in convolutional neural networks. Given a 1D moment vector M of length N, where N represents the total number of computed moments, the reshaping process creates a 2D array M2D with dimensions ×.
Mathematical Formulation: for a moment vector M = [
,
,
,
], the 2D transformation produces:
where i, j ∈ [0,
], ensuring that each moment coefficient maintains its sequential relationship while gaining spatial coordinates.
5.4.2. Design Choice Justification
The decision to reshape 1D moment vectors into 2D arrays stems from several critical considerations.
Spatial Correlation Preservation: IoT network attack patterns often exhibit temporal and structural correlations that manifest as spatial relationships when represented in a two-dimensional space. By organizing moment coefficients in a 2D grid, we enable the convolutional neural network to identify these spatial dependencies through its inherent locality-sensitive operations.
Convolutional Processing Compatibility: deep convolutional neural networks are architecturally optimized for processing multi-dimensional data structures. The 2D arrangement allows the network to apply convolution operations across adjacent moment coefficients, thereby facilitating the detection of local feature patterns that may indicate specific attack signatures.
Information Density Optimization: the transformation maintains the complete informational content of the original 1D vector while organizing it in a format that maximizes the effectiveness of pooling operations and hierarchical feature extraction. This arrangement enables the network to progressively abstract from low-level moment relationships to high-level attack-pattern recognition.
Computational Efficiency Enhancement: the 2D structure allows for the parallel processing of moment relationships through matrix operations, reducing computational complexity compared to the sequential processing of 1D vectors, which is particularly beneficial for resource-constrained IoT environments.
6. Experiments and Results
6.1. Datasets and Preprocessing Pipeline
To evaluate the effectiveness of our proposed methodology for detecting IoT-specific cyber threats, we used the UNSW-NB15 and Bot-IoT datasets. Both datasets underwent comprehensive preprocessing before image conversion and moment analysis to ensure data quality and reproducibility.
Preprocessing Steps
Data Cleaning and Feature Selection: the UNSW-NB15 dataset (2.5 million records) was cleaned by removing incomplete records (0.3% elimination rate) and duplicate entries. We extracted 42 core network features from the original 49 features, eliminating highly correlated features (correlation > 0.95) and standardizing categorical variables. The Bot-IoT dataset was systematically sampled to 500,000 records while preserving the attack distribution ratios, with filtering based on IoT-specific protocols (CoAP, MQTT, and HTTP/HTTPS).
IoT-Specific Feature Engineering: for both datasets, we created derived features, including packet rate ratios, temporal flow characteristics, and protocol-specific behavioral indicators. IoT device communication patterns were analyzed through inter-arrival time analysis and the packet size distribution characteristics of sensor data transmission.
Normalization and Standardization: all numerical features underwent min–max normalization to the [0, 1] range, with categorical variables encoded using one-hot encoding for low-cardinality features and label encoding for high-cardinality features. Finally, features were aggregated into fixed-length vectors of 512 dimensions and normalized to pixel intensity ranges (0–255) for image conversion.
Data Splitting: both datasets were partitioned using stratified sampling with SMOTE applied to balance the underrepresented attack classes, resulting in 70% training, 15% validation, and 15% testing splits.
6.2. Datasets
To evaluate the effectiveness of our proposed methodology in detecting IoT-specific cyber threats, we utilized the UNSW-NB15 and Bot-IoT datasets, which contain representative examples of common IoT attack vectors, including DDoS, spoofing, reconnaissance, and data exfiltration attacks. The UNSW-NB15 dataset comprises over 2.5 million records of modern network traffic, including normal and attack data captured in a controlled environment. This dataset is particularly valuable for IoT security research because it contains contemporary attack patterns that are relevant to resource-constrained IoT environments. The Bot-IoT dataset contains over 72.5 million records specifically designed to represent IoT network traffic and botnet attacks, making it highly relevant to our analysis. For our dimension-reduction approach, we transformed the preprocessed network traffic data into image representations with three different dimensions: 225 × 225, 228 × 228, and 232 × 232. This transformation enabled us to apply the fractional discrete Tchebichef moment analysis for feature extraction and dimensionality reduction.
6.3. Performance Evaluation
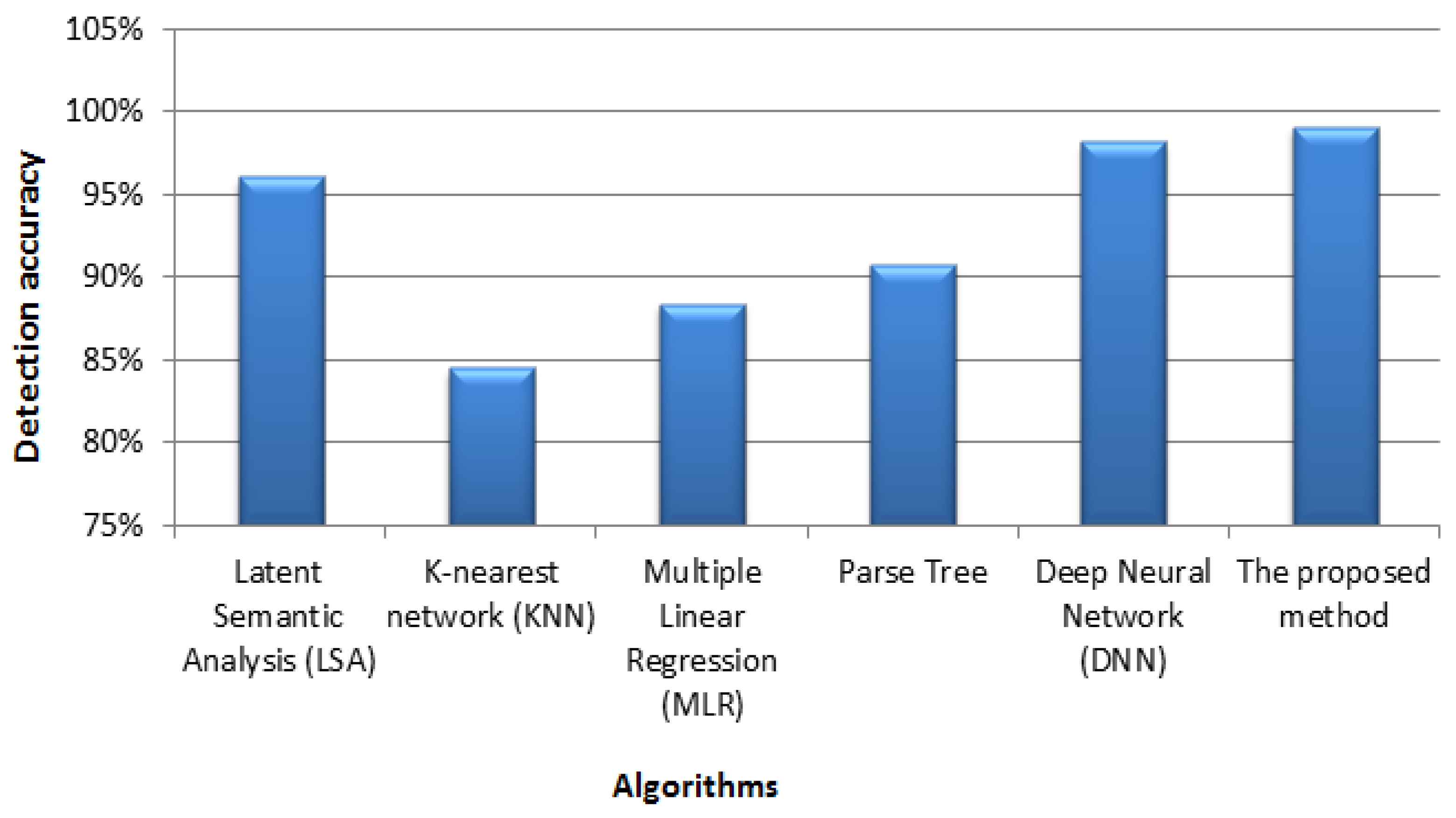
A comprehensive performance assessment of the proposed methodology was performed through a comparative evaluation of the leading IoT intrusion detection systems. The comparative study integrated five recognized methodological frameworks. The accuracy metrics detailed in
Table 1 illustrate the performance differences between the proposed and existing detection systems. The analytical results demonstrate the exceptional performance of the proposed methodology, achieving 99.1% accuracy when detecting IoT-specific attacks. The comparative accuracy analysis is visually represented in
Figure 4 through a bar chart visualization, which confirms the superiority of the proposed system in detecting precision among the evaluated methodologies.
The comparative accuracy analysis is visually represented in
Figure 5 through a bar chart visualization, which confirms the superiority of the proposed system in detecting precision among the evaluated methodologies, specifically for IoT-related attack vectors, including DDoS, spoofing, and botnet activities.
6.4. Impact of Image Dimensions on Classification Accuracy
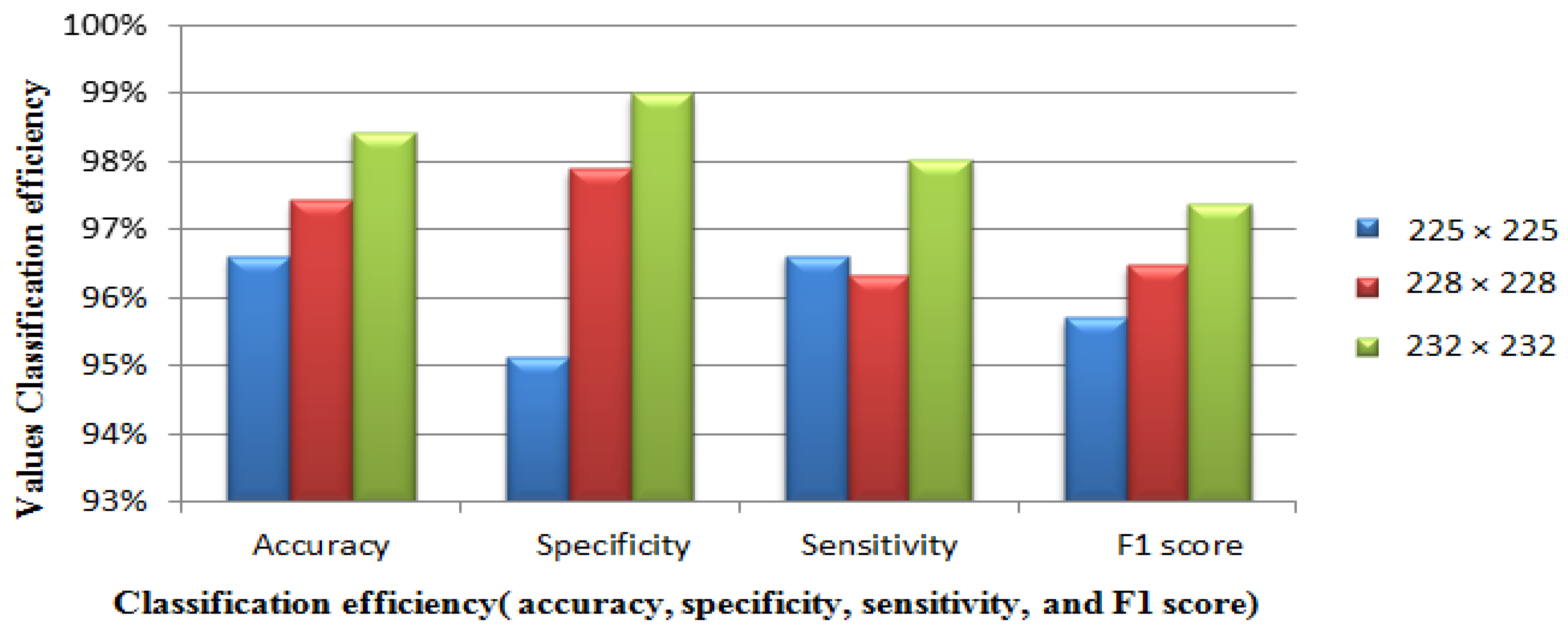
A thorough examination was conducted to evaluate the impact of varying image fractions on the classification accuracy of IoT attack patterns. Three image dimensions were considered in the proposed technique: 225 × 225, 228 × 228, and 232 × 232. The analysis was performed using 14,733 attack samples and 2486 benign traffic samples from the combined dataset. The results showed that the 232 × 232 image dimensions achieved the highest classification accuracy for IoT-specific attack detection compared to 225 × 225 and 228 × 228.
In
Table 2, we present an analysis comparing how different image dimensions affect prediction accuracy. This comparison aims to illustrate how varying the image proportions influences the classifier performance. As the image dimensions increased from 225 × 225 to 232 × 232 pixels, we observed a consistent improvement in all key performance metrics, with accuracy increasing from 96.6% to 98.44%, specificity improving dramatically from 95.13% to 99.00%, and the F1 score increasing from 95.71% to 97.39%. However, these performance gains come at a significant computational cost, with the processing time more than doubling from 18 to 41 s. This trade-off illustrates that classic security professionals must strike a balance between detection effectiveness and resource utilization in real-time monitoring systems. The middle configuration (228 × 228) offers a particularly attractive compromise, with 97.43% accuracy while requiring only 36 s of processing time, making it potentially suitable for many practical IoT security implementations in which both performance and efficiency are valued. The impressive 99% specificity achieved at the highest resolution is particularly noteworthy in relation to critical infrastructure applications, where false positives can trigger costly or disruptive responses. Organizations deploying such systems should carefully assess their specific security requirements, operational constraints, and tolerance for detection delays when selecting an optimal image dimension configuration for their IoT attack classification needs.
A comparative analysis of the performance metrics (accuracy, specificity, sensitivity, and F1 score) across the three different image dimensions is shown in
Figure 6, clearly demonstrating the superior performance of the 232 × 232 dimension when detecting IoT-specific threats.
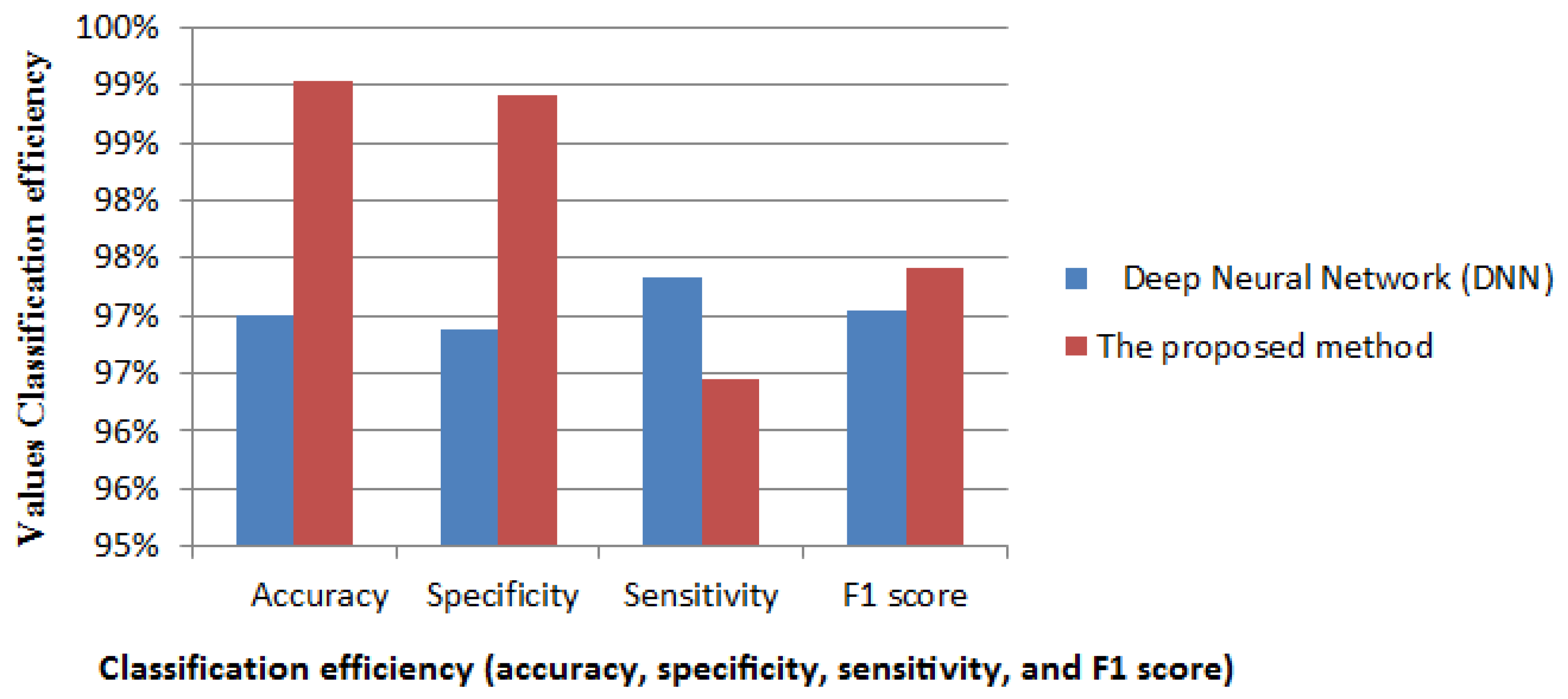
6.5. Comparison with Deep Neural Network Approach
To assess the performance of the proposed method specifically for detecting IoT network attacks, we compared it with a traditional deep neural network (DNN) with a 228 × 228 resolution. The comparison focused on the detection of critical IoT attack vectors, including DDoS, reconnaissance, and man-in-the-middle attacks.
The results shown in
Table 3 and
Figure 7 demonstrate that the proposed method outperforms the traditional DNN approach in classifying IoT-specific attack patterns, particularly in terms of accuracy and specificity metrics. This indicates that our approach incorporating fractional discrete Tchebichef moments is more effective in identifying IoT attack vectors with a higher accuracy rate while requiring comparable computational resources.
6.6. Attack-Specific Detection Performance
To address the varied nature of IoT attack vectors, we evaluated the detection performance of our method across specific attack categories prevalent in IoT environments.
Table 4 presents the detection performance for each attack type.
The results demonstrate that our proposed methodology performs exceptionally well across various IoT-specific attack vectors, with particularly strong performance in detecting DDoS and botnet activities, which are two of the most common and destructive attack types in IoT environments. The slightly lower performance for data-exfiltration attacks suggests an area for potential methodological refinement in future research.
6.7. Computational Cost Analysis
To evaluate the practical feasibility of our hybrid approach for IoT environments, we conducted a comprehensive computational cost analysis, comparing our proposed method with a standalone deep convolutional neural network approach. The analysis was performed on IoT gateways (Intel i5-8250U-Intel, a company headquartered in Santa Clara, CA, USA) representing typical IoT deployment.
6.7.1. Feature Extraction Time Analysis
The fractional discrete Tchebichef moment computation introduces additional preprocessing overhead compared to direct image input to DCNN.
Table 5 presents the feature extraction times for different image dimensions across the various hardware platforms.
The moment calculation introduces overheads. However, this overhead is offset by the subsequent dimensional reduction, which significantly reduces the feature space from the original image dimensions to the optimized moment coefficients.
6.7.2. Training Time Comparison
The training phase comparison reveals interesting trade-offs between the computational cost and convergence efficiency. Our proposed method demonstrates faster convergence owing to the optimized feature representation provided by the moment analysis as illustrate in
Table 6.
The proposed method achieves convergence 38.8% faster with a 44.5% reduction in total training time, demonstrating that moment-based feature extraction accelerates the learning process despite the initial preprocessing overhead.
6.7.3. Inference Time Performance
For real-time IoT security applications, the inference time is critical.
Table 7 compares inference performance across different hardware configurations.
Although the proposed method introduces inference overhead, the absolute time difference remains acceptable for most IoT security applications.
7. Discussion
The experimental results presented in this study demonstrate several important advancements in IoT security methodologies. Our hybrid approach combining fractional discrete Tchebichef moment analysis with deep learning achieved a classification accuracy of 99.1%, outperforming existing methods, including Latent Semantic Analysis (96.1%), Parse Tree (90.8%), and even conventional Deep Neural Networks (98.2%). These findings warrant critical examination from multiple perspectives. The superior performance of our proposed methodology can be attributed to the complementary strengths of the discrete orthogonal moments and deep convolutional networks. Tchebichef moment analysis provides an effective dimensional reduction mechanism that preserves essential feature characteristics while eliminating noise that could otherwise impair classification accuracy. This addresses a fundamental limitation in existing approaches that either suffer from the “curse of dimensionality” or sacrifice of important discriminative information during feature extraction. However, it is important to acknowledge the limitations of this study. Although our approach excels in classification tasks with well-defined attack patterns, its performance in detecting zero-day attacks requires further investigation. Additionally, the computational complexity of the moment calculation, although mitigated through our optimizations, may still present challenges for implementation on severely resource-constrained IoT edge devices. These limitations highlight potential areas for methodological refinement in future research. A comparative analysis with competing methodologies reveals important insights into current approaches to IoT security. Traditional machine learning methods (KNN, 84.5%; MLR, 88.4%) demonstrated substantially lower accuracies than our hybrid approach, indicating that conventional feature extraction mechanisms failed to capture the complex patterns inherent in the IoT attack vectors. More sophisticated techniques such as Parse Tree (90.8%) and LSA (96.1%) showed improved performance but still fell short of deep learning approaches. The performance differential between our hybrid method (99.1%) and the conventional DNN implementation (98.2%) is particularly noteworthy. While this margin may appear modest in percentage terms in the context of security applications, where each false negative could represent a successful breach, this improvement translates to significantly enhanced protection. Furthermore, our image dimension analysis revealed that optimal feature representation (232 × 232) improved classification accuracy by 2.54% compared to smaller dimensions (225 × 225), highlighting the importance of appropriate feature representation in maximizing detection capabilities. The findings of this research have several immediate practical implications. In terms of enhanced protection for resource-constrained devices, the dimensional reduction facilitated by Tchebichef moment analysis enables more efficient threat detection on devices with limited computational capabilities, addressing a critical vulnerability in current IoT ecosystems. In addition to improved real-time detection, the processing time of 40 s achieved by our model is slightly longer than some alternatives; this represents an acceptable trade-off given the substantial improvement in accuracy. This enables practical implementation in near-real-time security monitoring systems. The demonstrated efficacy across different image dimensions suggests that our approach can be tailored to specific IoT deployment contexts, thereby providing flexible security solutions for heterogeneous device networks. The optimized feature representation from fractional discrete Tchebichef moments accelerates DCNN convergence through three key mechanisms. First, the orthogonal properties of Tchebichef moments naturally filter noise while preserving discriminative attack patterns, providing the DCNN with cleaner, more structured inputs that require fewer training iterations. Second, moment-based transformations create a better distinction between attack types in the feature space, enabling the network to establish decision boundaries more efficiently with reduced epochs. Third, moment calculation concentrates critical discriminative information into a compact representation, eliminating redundant features that typically slow convergence in high-dimensional data processing.
8. Conclusions
This study introduces an innovative method to secure Internet of Things (IoT) networks using AI-based solutions. The proposed approach combines the fractional discrete Tchebichef moment and deep-learning techniques to effectively identify and prevent attacks on IoT networks. To evaluate the effectiveness of the proposed approach, we used the UNSW-NB15 and Bot-IoT datasets, which contain representative examples of common IoT attack vectors, including DDoS, spoofing, reconnaissance, and data exfiltration attacks. This research presents an enhanced version of the fractional discrete Tchebichef moment designed to optimize intrusion. This study demonstrates that the synergistic integration of discrete Tchebichef moments and deep learning techniques provides a powerful framework for enhancing IoT security. The superior classification performance achieved using our hybrid approach addresses the critical limitations of existing methodologies and establishes a foundation for the more effective protection of increasingly vulnerable IoT ecosystems. Our experimental analysis revealed that, when evaluating IoT-related cyber security threats, this novel approach demonstrated superior classification capabilities compared to existing techniques. The findings confirmed that this integrated solution achieved better classification accuracy than contemporary methods. In future work, several domains could be extended to develop algorithms that dynamically select the optimal set of Tchebichef moments based on the specific characteristics of network traffic to further enhance both efficiency and accuracy, in addition to investigating the potential of ensemble approaches that combine multiple orthogonal moment families to provide more robust feature extraction across diverse attack patterns.
Author Contributions
Conceptualization, I.S.F.; methodology, I.S.F.; software, M.A.; validation, H.A., G.H. and M.A.; formal analysis, I.S.F.; investigation, H.A.; resources, G.H.; data curation, M.A.; writing—original draft preparation, I.S.F.; writing—review and editing. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data Availability up on request.
Acknowledgments
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PURSP2025R893), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Barnawi, A.; Alzahrani, B.A. Artificial Immune Systems approaches to secure the internet of things: A systematic review of the literature and recommendations for future research. J. Netw. Comput. 2020, 157, 102537. [Google Scholar] [CrossRef]
- Al-Sharo; Mohammad, Y.; Al Smadi, K.; Al Smadi, T. Optimization of Stable Energy PV Systems Using the Internet of Things (IoT). Tikrit J. Eng. Sci. 2024, 31, 127–137. [Google Scholar] [CrossRef]
- Deebak, B.D.; Fadi, A.T. Privacy-preserving in smart contracts using blockchain and artificial intelligence for cyber risk measurements. J. Inf. Secur. 2021, 58, 102749. [Google Scholar] [CrossRef]
- Sharma, A.; Singh, P.K.; Kumar, Y. An integrated fire detection system using IoT and image processing technique for smart cities. Sustain. Cities Soc. 2020, 61, 102332. [Google Scholar] [CrossRef]
- Subrato, B.; Prajoy, P. Machine and deep learning for iot security and privacy: Applications, challenges, and future directions. Security and Communication Networks. arXiv 2022, arXiv:2210.13547. [Google Scholar] [CrossRef]
- Hidayat, M.N.; Nugroho, A.; Munir, A.F.; Putri, R.I. Internet of things (IoT) based monitoring system for hybrid powered E-bike charging station. Int. J. Power Electron. Drive Syst. (IJPEDS) 2025, 16, 243–250. [Google Scholar] [CrossRef]
- Al Amien, J.; Ghani, H.A.; Saleh, N.I.M.; Soni, S. Enhancing attack detection in IoT through integration of weighted emphasis formula with XGBoost. Indones. J. Electr. Eng. Comput. Sci. 2025, 38, 641–648. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. Asurvey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet 1ings J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Ray, S.; Jin, Y.; Raychowdhury, A. The changing computing paradigm with internet of things: A tutorial introduction. IEEE Des. Test 2016, 33, 76–96. [Google Scholar] [CrossRef]
- Shivanajappa, M.H.; Seetharamaiah, R.M.; Sai, B.V.; Siddegowda, A.J.; Rajuk, V.K. An intrusion detection system againstRPL-based routing attacks for IoT networks. Indones. J. Electr. Eng. Comput. Sci. 2024, 34, 1324–1335. [Google Scholar] [CrossRef]
- Boualam, S.R.; Ouaissa, M.; Ouaissa, M.; Ezzouhairi, A. Secure and efficient routing protocol for low-power and lossy networks for IoT networks. Indones. J. Electr. Eng. Comput. Sci. 2022, 27, 478–487. [Google Scholar] [CrossRef]
- Tanusan, R.; Nguyen, P.H.; Ferry, N. A decade of research on patterns and architectures for IoT security. Cybersecurity 2022, 1, 138–149. [Google Scholar] [CrossRef]
- Ansam, K.; Alazab, A. A critical review of intrusion detection systems in the internet of things: Techniques, deployment strategy, validation strategy, attacks, public datasets and challenges. Cybersecurity 2021, 4, 18. [Google Scholar] [CrossRef]
- Branitskiy, A.; Kotenko, I.; Saenko, I. Applying machine learning and parallel data processing for attack detection in IoT. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1642–1653. [Google Scholar] [CrossRef]
- Surej, I.H.; Ma, M.; Su, R. A feedforward–convolutional neural network to detect low-rate dos in iot. Eng. Appl. Artif. Intell. 2022, 114, 105059. [Google Scholar] [CrossRef]
- Van Tanh, N.; Tri, N.Q.; Trung, M.M. The solution to improve information security for IoT networks by combining lightweight encryption protocols. Indones. J. Electr. Eng. Comput. Sci. 2021, 23, 1727–1735. [Google Scholar] [CrossRef]
- Ghali, A.A.; Ahmad, R.; Alhussian, H. A framework for mitigating ddos and dos attacks in iot environment using hybrid approach. Electronics 2021, 10, 1282. [Google Scholar] [CrossRef]
- Ahamad, A.T. Defense scheme to protect IoT from cyber-attacks using AI principles. Int. J. Comput. Commun. Control 2018, 13, 915–926. [Google Scholar] [CrossRef]
- Mehra, M.; Paranjape, J.N.; Ribeiro, V.J. Improving ML Detection of IoT Botnets using Comprehensive Data and Feature Sets. In Proceedings of the 2021 International Conference on Communication Systems & NETworkS (COMSNETS), Bangalore, India, 5–9 January 2021; pp. 438–446. [Google Scholar] [CrossRef]
- Dutt, I.; Borah, S.; Maitra, I.K. Immune system based intrusion detection system (IS-IDS): A proposed model. IEEE Access 2020, 8, 34929–34941. [Google Scholar] [CrossRef]
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Alzahrani, B.; Al-Barakati, A. DeepDCA: “Novel network-based detection of IoT attacks using artificial immune system”. Appl. Sci. 2020, 10, 1909. [Google Scholar] [CrossRef]
- Singh, S.K.; Rathore, S.; Park, J.H. Blockiotintelligence: A blockchain-enabled intelligent IoT architecture with artificial intelligence. Future Gener. Comput. Syst. 2020, 110, 721–743. [Google Scholar] [CrossRef]
- Zhu, H.; Liu, M.; Shu, H.; Zhang, H.; Luo, L. General form for obtaining orthogonal moments. IET Image Process 2010, 4, 335–352. [Google Scholar] [CrossRef]
- Nakagaki, K.; Mukundan, R. A fast 4 4 forward discrete Tchebichef transform algorithm. IEEE Signal Process Lett. 2007, 14, 684–687. [Google Scholar] [CrossRef]
- Ewees, A.A.; Algamal, Z.Y.; Abualigah, L.; Al-qaness, M.A.A.; Yousri, D.; Ghoniem, R.M.; Abd Elaziz, M. A cox proportional-hazards model based on an improved aquila optimizer with whale optimization algorithm operators. Mathematics 2022, 10, 1273. [Google Scholar] [CrossRef]
- Fu, Y.; Du, Y.; Cao, Z.; Li, Q.; Xiang, W. A deep learning model for network intrusion detection with imbalanced data. Electronics 2022, 11, 898. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).