Detecting Denial of Service Attacks (DoS) over the Internet of Drones (IoD) Based on Machine Learning
Abstract
1. Introduction
1.1. Contribution
1.2. Paper Organization
2. UAVs (Unmanned Aerial Vehicles)
2.1. UAV Security
2.2. Drone Concerns, Security, Privacy, and Safety
2.3. Existing Vulnerabilities and Cyberattacks on Drones
- Malware attacks: UAVs are mainly controlled and connected through remote devices. This technique is considered unsafe, as the automatic installation of malware over UAVs can easily be accomplished by injecting a reverse-shell TCP payload into the drone’s memory (hacking the UAV, then installing malware) [8,10].
- Spoofing/jamming attacks: These are considered sensor-based attacks that involve GPS (easiest), motion sensors, and UAV spoofing [9]. Such attacks are related to the communication methods and telemetry links transporting data to/from drones via serial ports that lack secure encryption measures. This data link vulnerability enables access and modification to the information associated with the GPS [10,11] and gives hackers full control over the targeted drones [8]. Signal congestion and signal loss methods are also used by attackers to transfer the control of a drone to a third party and spoof drones [9].
- Data interception and interference: UAV monitoring and data transfers are performed using telemetry feeds through non-secure, open transmissions. This makes the vehicles vulnerable to attacks such as malicious data injection, interception, and alteration, allowing attackers to inject infected image/video files from the UAV to the ground station [8].
- Skyjack-based attacks: A skyjack is a malicious software that the attacker installs on the targeted UAVs to detect the wireless networks within the region of the target. After that, the attacker can conduct de-authentication attacks and disable any client connected to the infected UAV through the wireless network, including the navigation controller [10,12].
3. Denial of Service (DOS)
3.1. Categories of Denial of Service Attacks
3.2. Differences in Investigating Denial of Service Attacks on Drones Compared to Other Internet of Things Devices
3.2.1. Physical Forensic Analysis
3.2.2. Type of Data Investigated
3.2.3. Physical Impact of the Attack
3.3. Denial of Service Attack on Parrot Anafi Drone
3.4. Denial of Service Attack on 3DR X8+ Drone
3.5. Denial of Service Attack on Drones in Real-Life Incidents
3.6. Big Picture of Denial of Service Attacks on Drones
4. Machine Learning Models for Detecting Denial of Service Attacks on Unmanned Aerial Vehicles
5. Related Works
Current Unmanned Aerial Vehicle Security Solutions
6. Comparisons and Results
7. Gap Analysis
8. Discussion and Future Research Directions
- Proposing an ML-based IDS model with a better accuracy rate through the implementation of continuous model training, regular collection of new high-quality data, and employing feedback from network administrators and security professionals. This contributes to the overall performance of the IDS and ensures its effectiveness in managing such attacks. Model optimization techniques should also be implemented to increase ML model scalability for identifying a different type of DoS attack.
- Developing scalable solutions, because drone platforms come with inherent resource limits. As the drone ecosystem grows, these solutions should function effectively with the limited computing and energy resources of drones.
- Lowering the cost of machine learning methods for Denial of Service (DoS) attacks. In order to reduce costs, we can develop computational resource-efficient, lightweight machine learning models that can be used in edge contexts or on devices with limited resources.
- Implementing strategies to provide better latency for the ML-IDS. Such strategies include using ML algorithms like conventional neural networks (CNNs). Another strategy can be to use cache memory techniques to store the results of operations and avoid the redundant calculation of those operations.
- Current IDS systems are missing adequate mechanisms to respond to the detected attacks. Integrating this feature enables network administrators and security personnel responsible for dealing with security to gain more control and aid in decisions regarding the recovery and later prevention of such incidents. Training the IDS to not only detect intrusions to the UAV network but also determine the appropriate responses to them based on certain factors and information the IDS collects ensures a high-quality security service that contributes to the overall safety of the UAV system and data.
- Developing robust defense mechanisms capable of identifying and mitigating adversarial attempts aimed at circumventing machine learning-based security systems.
- Adapting anomaly detection methodologies to accommodate diverse environmental conditions and operational contexts within drone networks for ensuring the sustained effectiveness of detection mechanisms across varied scenarios.
- Applying chaos engineering methods to evaluate the robustness of drone swarms. Chaos engineering is an emerging technology that tests the versatility of an interconnected system by arbitrarily causing unexpected events. In this way, the robustness of a swarm of drones can be tested for arbitrary attacks.
- Considering timestamps to detect different types of DoS attacks in real-time networks.
- Subsequent investigations ought to concentrate on collaborative UAV tactics, optimizing latency and incorporating more extensive spectrum-sharing protocols. These developments would support the creation of more robust and flexible UAV anti-jamming technologies.
9. Conclusions and Future Work
Funding
Conflicts of Interest
References
- Zeng, Y.; Wu, Q.; Zhang, R. Accessing from the Sky: A Tutorial on UAV Communications for 5G and beyond. Proc. IEEE 2019, 107, 2327–2375. [Google Scholar] [CrossRef]
- Jamil, S.; Rahman, M.; Fawad. A Comprehensive Survey of Digital Twins and Federated Learning for Industrial Internet of Things (IIoT), Internet of Vehicles (IoV) and Internet of Drones (IoD). Appl. Syst. Innov. 2022, 5, 56. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Agrawal, A.; Goyal, A.; Luong, N.C.; Niyato, D.; Yu, F.R.; Guizani, M. Fast, Reliable, and Secure Drone Communication: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2021, 23, 2802–2832. [Google Scholar] [CrossRef]
- IEEE Computer Society. Technical Council on Test Technology, IEEE Solid-State Circuits Society, International Federation for Information Processing, and EDA Association. In Proceedings of the 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 25–29 March 2019. [Google Scholar]
- Tsao, K.-Y.; Girdler, T.; Vassilakis, V.G. A survey of cyber security threats and solutions for UAV communications and flying ad- hoc networks. Ad Hoc Netw. 2022, 133, 102894. [Google Scholar] [CrossRef]
- Prasad, R.; Rohokale, V.; Prasad, R.; Rohokale, V. Artificial intelligence and machine learning in cyber security. In Cyber Security: The Lifeline of Information and Communication Technology; Springer: Cham, Switzerland, 2020; pp. 231–247. [Google Scholar]
- Ramadan, R.A.; Emara, A.-H.M.; Al-Sarem, M.; Elhamahmy, M. Internet of Drones Intrusion Detection Using Deep Learning. Electronics 2021, 10, 2633. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Majeed, R.; Abdullah, N.A.; Mushtaq, M.F.; Kazmi, R. Drone Security: Issues and Challenges. Available online: www.ijacsa.thesai.org (accessed on 2 February 2024).
- Abro, G.E.M.; Zulkifli, S.A.B.M.; Masood, R.J.; Asirvadam, V.S.; Laouti, A. Comprehensive Review of UAV Detection, Security, and Communication Advancements to Prevent Threats. Drones 2022, 6, 284. [Google Scholar] [CrossRef]
- Baig, Z.; Syed, N.; Mohammad, N. Securing the Smart City Airspace: Drone Cyber Attack Detection through Machine Learning. Future Internet 2022, 14, 205. [Google Scholar] [CrossRef]
- Yahuza, M.; Idris, M.Y.I.; Bin Ahmedy, I.; Wahab, A.W.B.A.; Nandy, T.; Noor, N.M.; Bala, A. Internet of Drones Security and Privacy Issues: Taxonomy and Open Challenges. IEEE Access 2021, 9, 57243–57270. [Google Scholar] [CrossRef]
- Hsu, W.C. Lightweight Cyberattack Intrusion Detection System for Unmanned Aerial Vehicles Using Recurrent Neural Networks. Master’s Thesis, Purdue University, West Lafayette, IN, USA, 2021. [Google Scholar]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on Internet-scale IoT exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Renduchintala, A.; Jahan, F.; Khanna, R.; Javaid, A.Y. A comprehensive micro unmanned aerial vehicle (UAV/Drone) forensic framework. Digit. Investig. 2019, 30, 52–72. [Google Scholar] [CrossRef]
- Ahn, H. Deep Learning Based Anomaly Detection for a Vehicle in Swarm Drone System. In Proceedings of the 2020 International Conference on Unmanned Aircraft Systems (ICUAS), Athens, Greece, 1–4 September 2020. [Google Scholar]
- Kulp, P.; Mei, N. A Framework for Sensing Radio Frequency Spectrum Attacks on Medical Delivery Drones. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics, Toronto, ON, Canada, 11–14 October 2020; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2020; pp. 408–413. [Google Scholar] [CrossRef]
- Guo, R.; Tian, J.; Wang, B.; Shang, F. Cyber-Physical Attack Threats Analysis for UAVs from CPS Perspective. In Proceedings of the 2020 International Conference on Computer Engineering and Application, ICCEA 2020, Guangzhou, China, 18–20 March 2020; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2020; pp. 259–263. [Google Scholar] [CrossRef]
- Feng, J.; Tornert, J. Denial-of-Service Attacks against the Parrot ANAFI Drone; KTH Royal Institute of Technology: Stockholm, Sweden, 2021. [Google Scholar]
- Kwon, Y.M.; Yu, J.; Cho, B.M.; Eun, Y.; Park, K.J. Empirical Analysis of MAVLink Protocol Vulnerability for Attacking Unmanned Aerial Vehicles. IEEE Access 2018, 6, 43203–43212. [Google Scholar] [CrossRef]
- Elkhider, S.M.; El-Ferik, S.; Saif, A.W.A. Containment Control of Multiagent Systems Subject to Denial of Service Attacks. IEEE Access 2022, 10, 48102–48111. [Google Scholar] [CrossRef]
- Virupakshar, K.B.; Asundi, M.; Channal, K.; Shettar, P.; Patil, S.; Narayan, D.G. Distributed Denial of Service (DDoS) Attacks Detection System for OpenStack-based Private Cloud. Procedia Comput. Sci. 2020, 167, 2297–2307. [Google Scholar] [CrossRef]
- Masys, A.J. Advanced Sciences and Technologies for Security Applications. 2021. Available online: http://www.springer.com/series/5540 (accessed on 30 January 2024).
- Dey, V.; Pudi, V.; Chattopadhyay, A.; Elovici, Y. Security Vulnerabilities of Unmanned Aerial Vehicles and Countermeasures: An Experimental Study. In Proceedings of the IEEE International Conference on VLSI Design, Pune, India, 6–10 January 2018; IEEE Computer Society: Washington, DC, USA, 2019; pp. 398–403. [Google Scholar] [CrossRef]
- Rahman, K.; Aziz, M.A.; Usman, N.; Kiren, T.; Cheema, T.A.; Shoukat, H.; Bhatia, T.K.; Abdollahi, A.; Sajid, A. Cognitive Lightweight Logistic Regression-Based IDS for IoT-Enabled FANET to Detect Cyberattacks. Mob. Inf. Syst. 2023, 2023, 7690322. [Google Scholar] [CrossRef]
- Majeed, R.; Abdullah, N.A.; Mushtaq, M.F.; Umer, M.; Nappi, M. Intelligent cyber-security system for iot-aided drones using voting classifier. Electronics 2021, 10, 2926. [Google Scholar] [CrossRef]
- Mihoub, A.; Fredj, O.B.; Cheikhrouhou, O.; Derhab, A.; Krichen, M. Denial of service attack detection and mitigation for internet of things using looking-back-enabled machine learning techniques. Comput. Electr. Eng. 2022, 98, 107716. [Google Scholar] [CrossRef]
- Fredj, O.B.; Mihoub, A.; Krichen, M.; Cheikhrouhou, O.; Derhab, A. CyberSecurity Attack Prediction: A Deep Learning Approach. In Proceedings of the SIN 2020: 13th International Conference on Security of Information and Networks, Merkez, Turkey, 4–7 November 2020; ACM International Conference Proceeding Series. Association for Computing Machinery: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Mihoub, A.; Snoun, H.; Krichen, M.; Kahia, M.; Salah, R.B.H.; Predicting, R.B.H.S. Predicting COVID-19 Spread Level using Socio-Economic Indicators and Machine Learning Techniques. In Proceedings of the 2020 First International Conference of Smart Systems and Emerging Technologies (SMARTTECH), Riyadh, Saudi Arabia, 3–5 November 2020. [Google Scholar] [CrossRef]
- Qaisar, S.M.; Alyamani, N.; Waqar, A.; Krichen, M. Machine Learning with Adaptive Rate Processing for Power Quality Disturbances Identification. SN Comput. Sci. 2022, 3, 14. [Google Scholar] [CrossRef]
- Abdulghani, A.M.; Abdulghani, M.M.; Walters, W.L.; Abed, K.H. Improving Intrusion Detection in UAV Communication Using an LSTM-SMOTE Classification Method. J. Cyber Secur. 2022, 4, 287–298. [Google Scholar] [CrossRef]
- Rezaeenour, J.; Ahmadi, M.; Jelodar, H.; Shahrooei, R. Systematic review of content analysis algorithms based on deep neural networks. Multimed. Tools Appl. 2023, 82, 17879–17903. [Google Scholar] [CrossRef]
- Susanto; Stiawan, D.; Arifin, M.A.S.; Idris, M.Y.; Budiarto, R. IoT botnet malware classification using weka tool and scikit-learn machine learning. In Proceedings of the International Conference on Electrical Engineering, Computer Science and Informatics (EECSI), Institute of Advanced Engineering and Science, Yogyakarta, Indonesia, 1–2 October 2020; pp. 15–20. [Google Scholar] [CrossRef]
- Mohammed, A.B.; Fourati, L.C.; Fakhrudeen, A.M. A Comparative Study of Attribute Selection Algorithms on Intrusion Detection System in UAVs: A Case Study of UKM-IDS20 Dataset. Lect. Notes Comput. Sci. (Incl. Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinform.) 2023, 13857, 34–46. [Google Scholar] [CrossRef]
- Karimibiuki, M.; Aibin, M.; Lai, Y.; Khan, R.; Norfield, R.; Hunter, A. Drones’ Face off: Authentication by Machine Learning in Autonomous IoT Systems. In Proceedings of the 2019 IEEE 10th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference, UEMCON 2019, New York, NY, USA, 10–12 October 2019; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2019; pp. 0329–0333. [Google Scholar] [CrossRef]
- Ribeiro, A.A.; Sachine, M. On the optimal separating hyperplane for arbitrary sets: A generalization of the SVM formulation and a convex hull approach. Optimization 2022, 71, 213–226. [Google Scholar] [CrossRef]
- Shrestha, R.; Omidkar, A.; Roudi, S.A.; Abbas, R.; Kim, S. Machine-learning-enabled intrusion detection system for cellular connected uav networks. Electronics 2021, 10, 1549. [Google Scholar] [CrossRef]
- Aldaej, A.; Ahanger, T.A.; Atiquzzaman, M.; Ullah, I.; Yousufudin, M. Smart Cybersecurity Framework for IoT-Empowered Drones: Machine Learning Perspective. Sensors 2022, 22, 2630. [Google Scholar] [CrossRef]
- Ouiazzane, S.; Addou, M.; Barramou, F. DoS and DDoS Cyberthreats Detection in Drone Networks. In Advances in Intelligent System and Smart Technologies; Lecture Notes in Networks and Systems; Springer: Cham, Switzerland, 2024; pp. 109–119. [Google Scholar] [CrossRef]
- Tan, X.; Su, S.; Zuo, Z.; Guo, X.; Sun, X. Intrusion Detection of UAVs Based on the Deep Belief Network Optimized by PSO. Sensors 2019, 19, 5529. [Google Scholar] [CrossRef]
- Ch, R.; Srivastava, G.; Gadekallu, T.R.; Maddikunta, P.K.R.; Bhattacharya, S. Security and privacy of UAV data using blockchain technology. J. Inf. Secur. Appl. 2020, 55, 102670. [Google Scholar] [CrossRef]
- Abualsauod, E.H. A hybrid blockchain method in internet of things for privacy and security in unmanned aerial vehicles network. Comput. Electr. Eng. 2022, 99, 107847. [Google Scholar] [CrossRef]
- Javeed, D.; Gao, T.; Saeed, M.S.; Kumar, P. An Intrusion Detection System for Edge-Envisioned Smart Agriculture in Extreme Environment. IEEE Internet Things J. 2024, 11, 26866–26876. [Google Scholar] [CrossRef]
- Attique, D.; Hao, W.; Ping, W.; Javeed, D.; Kumar, P. Explainable and Data-Efficient Deep Learning for Enhanced Attack Detection in IIoT Ecosystem. IEEE Internet Things J. 2024, 1, 1. [Google Scholar] [CrossRef]

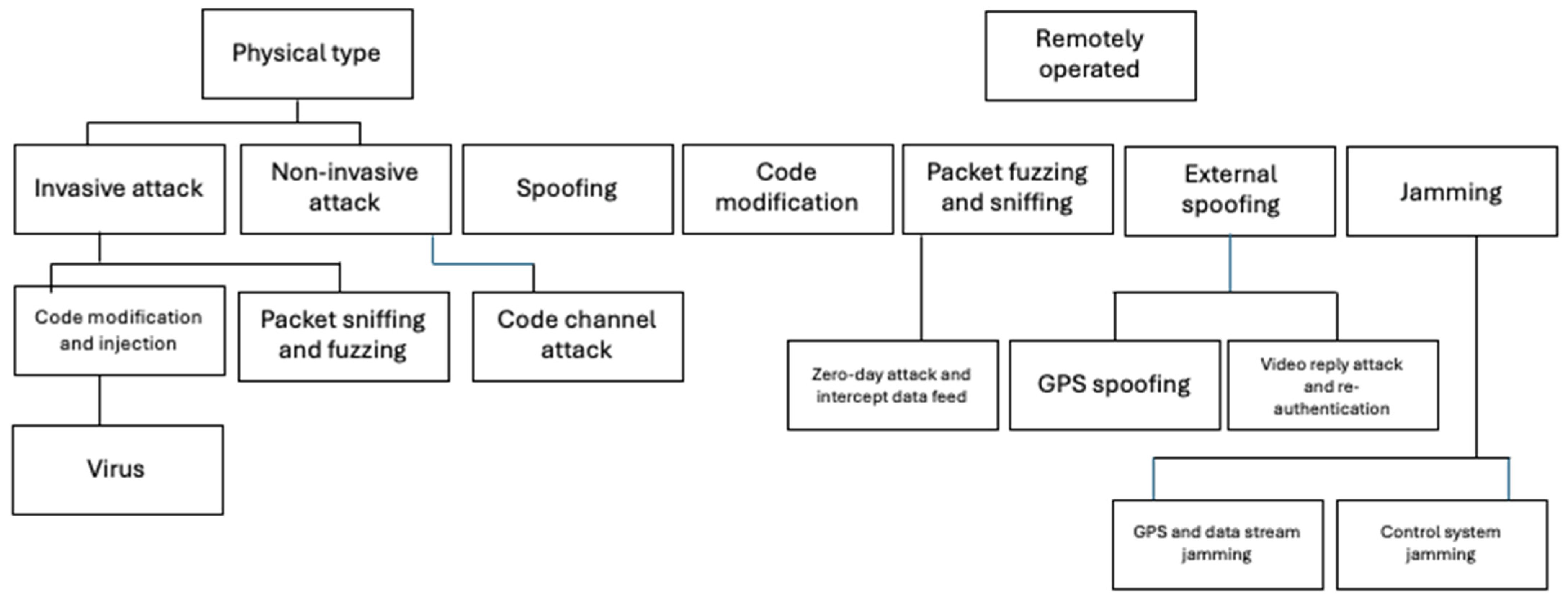
| Security Target | Attack Type | Attack Nature |
|---|---|---|
| Confidentiality |
|
|
| Privacy |
|
|
| Integrity |
|
|
| Availability |
|
|
| Authentication |
|
|
| Ref. | ML Algorithms | Accuracy | Precision | Recall | F1 | Open Issue |
|---|---|---|---|---|---|---|
| [25] | LR | 82.54% | NM | NM | NM | Has problems with relations effects among variables |
| [31,32] | LSTM-SMOTE | 99.71% Benign 99.83% Attack | 99.95% Benign 97.95% Attack | 99.44% Benign 99.79% Attack | 99.89% Benign 98.96% Attack | Work on increasing the efficiency of the model is much needed |
| [33] | RF | 99.09% | NM | NM | NM | Work on decreasing the latency is needed |
| [34] | MLP | 99.93% | The efficient detection of a variety of vulnerable drones can be worked upon in the future | |||
| [35,36] | SVM | 99.07% | 95.6% | 96% | 95.8% | Need to improve the inconsistent results |
| [37] | DT | 99.99% | 1 | 1 | 1 | Lack of real-time adaption, scalability issue |
| [37] | KNN | 99.94% | 0.999 | 1 | 0.999 | Scalability issue, sensitive to noise. |
| [37] | K-M | 37.67% | 0.331 | 0.982 | 0.496 | Needs an improvement in terms of accuracy |
| [38] | LR&RF | 98.58% | 0.9768 | 0.9859 | 0.9901 | High cost |
| [39] | Tree Ensemble | 99.98% | 0.997 | 0.995 | NM | NM |
| [40] | ANN | 90.79% | 0.9961 | NM | NM | prone to overfitting |
| [40] | DNN | 91.36% | 0.9960 | NM | NM | need a big amount of training data to learn the complex patterns and features in the data |
| [40] | PSO-DBN | 92.44% | 0.9982 | NM | NM | NM |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alsumayt, A.; Nagy, N.; Alsharyofi, S.; Al Ibrahim, N.; Al-Rabie, R.; Alahmadi, R.; Alesse, R.A.; Alahmadi, A.A. Detecting Denial of Service Attacks (DoS) over the Internet of Drones (IoD) Based on Machine Learning. Sci 2024, 6, 56. https://doi.org/10.3390/sci6030056
Alsumayt A, Nagy N, Alsharyofi S, Al Ibrahim N, Al-Rabie R, Alahmadi R, Alesse RA, Alahmadi AA. Detecting Denial of Service Attacks (DoS) over the Internet of Drones (IoD) Based on Machine Learning. Sci. 2024; 6(3):56. https://doi.org/10.3390/sci6030056
Chicago/Turabian StyleAlsumayt, Albandari, Naya Nagy, Shatha Alsharyofi, Noor Al Ibrahim, Renad Al-Rabie, Resal Alahmadi, Roaa Ali Alesse, and Amal A. Alahmadi. 2024. "Detecting Denial of Service Attacks (DoS) over the Internet of Drones (IoD) Based on Machine Learning" Sci 6, no. 3: 56. https://doi.org/10.3390/sci6030056
APA StyleAlsumayt, A., Nagy, N., Alsharyofi, S., Al Ibrahim, N., Al-Rabie, R., Alahmadi, R., Alesse, R. A., & Alahmadi, A. A. (2024). Detecting Denial of Service Attacks (DoS) over the Internet of Drones (IoD) Based on Machine Learning. Sci, 6(3), 56. https://doi.org/10.3390/sci6030056







