How to Achieve Compliance with GDPR Article 17 in a Hybrid Cloud Environment
Abstract
1. Introduction
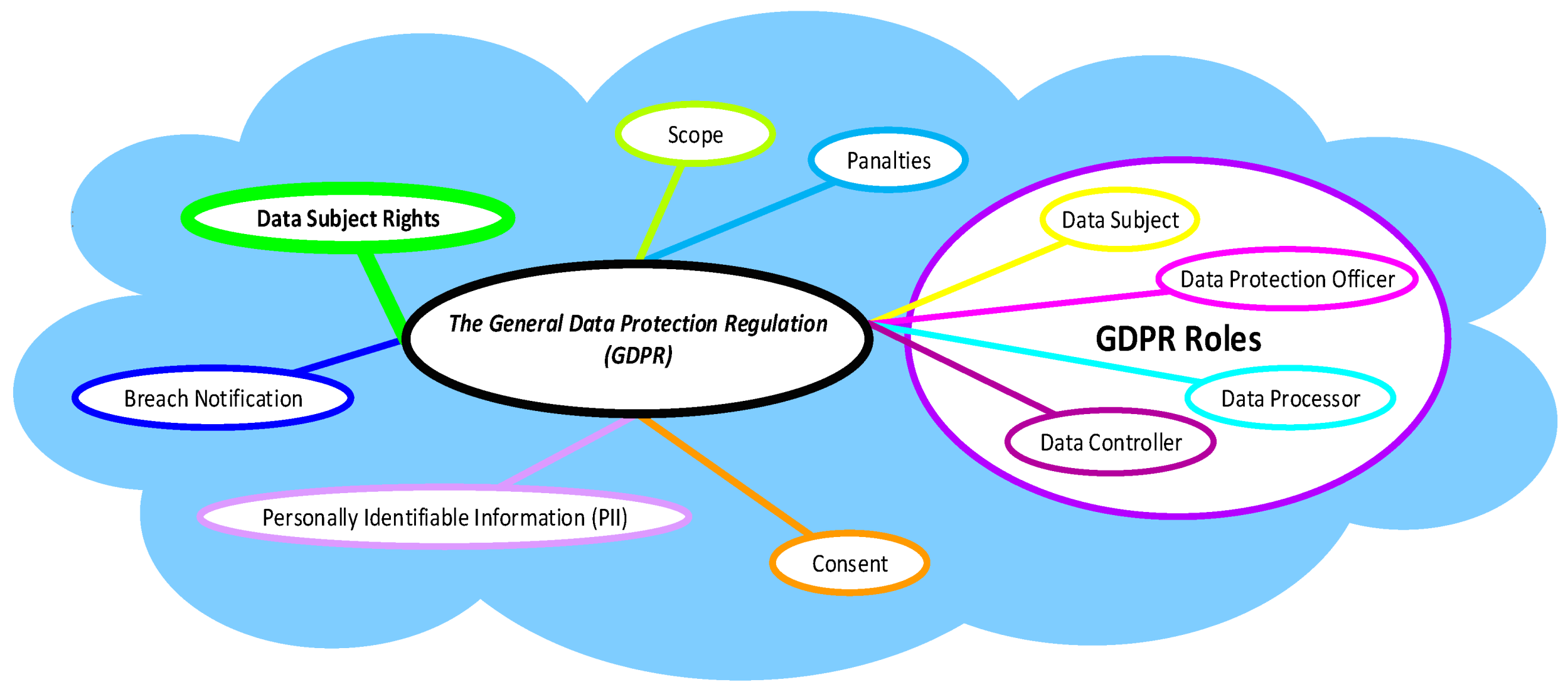
2. General Data Protection Regulation (GDPR)
- Data Subject: A data subject is a natural living person who can be identified directly or indirectly [1]. A data subject is anybody residing in the EU, not just EU citizens.
- Data Protection Officer: A Data Protection Officer (DPO) (Data Protection must have specialist skills and expertise to oversee GDPR compliance, ensuring obligations are met from the highest level of management; they are the point of contact for the supervisory authority and monitor the organisation’s compliance with the law. The DPO can either be an employee or outsourced service. Under GDPR, whilst it is mandatory for all organisations to appoint (DPO), small organisations with less than 250 employees are exempt.
- Data Processor: A data processor is an organisation that process data as per instructed by their data controller like cloud hosting providers [5]. GDPR recognising the complexity of modern-day data processing relationships identifies that data processors play a vital part in the protection of European citizens data and so introduced direct rules for data processors such as record keeping and reporting data breaches.
- Data Controller: The data controller is the organisation that collects, processes and stores PII and must be able to demonstrate GDPR compliance, which means the burden of proof lies with them [7].
- Data Protection Impact Assessment (DPIA): DPIA aims to identify potential risks involved the collection, processing and storage of PII, the impact on the privacy of the data subject and identify ways to mitigate those issues [8].
- Transparency: An organisation must have a granular level of transparency into their PII from consent, collection, processing and storage for the full life cycle of that data and mandatory clauses (EU, 2016).
- Data Minimization: PII can only be collected and processed where there is an identifiable reason why it is needed and should be kept no longer than is necessary for the purpose for which it was collected, and no additional data can be obtained [8].
Right to Erasure (“Right to Be Forgotten”)
- The data is no longer required for the purpose that it was originally collected.
- The data subject withdraws consent.
- The data subject objects to the processing and there are no overriding legitimate grounds.
- The PII was processed unlawfully.
- The PII must be erased for legal obligations.
- Processing of children’s PII collected via information society services.
3. Cloud Computing
Hybrid Clouds
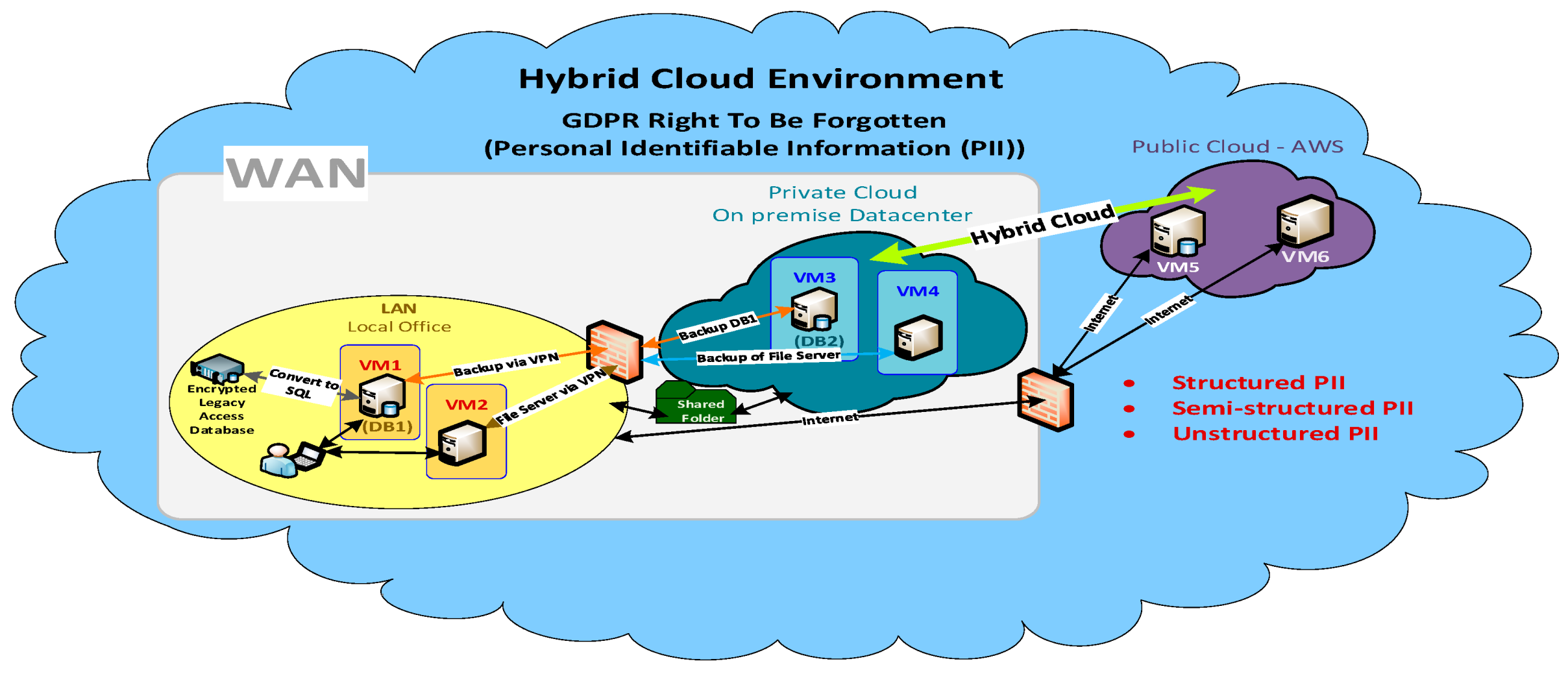
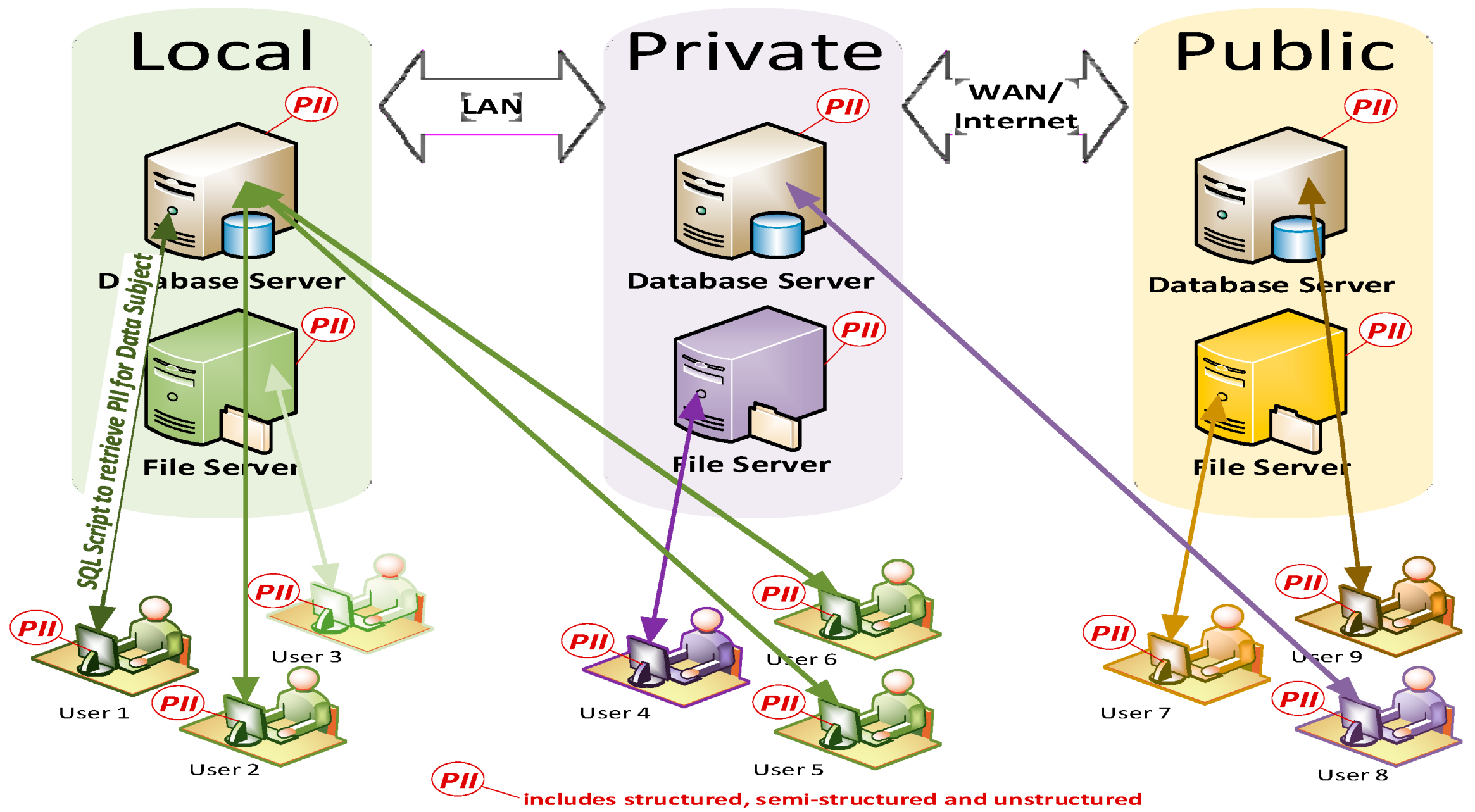
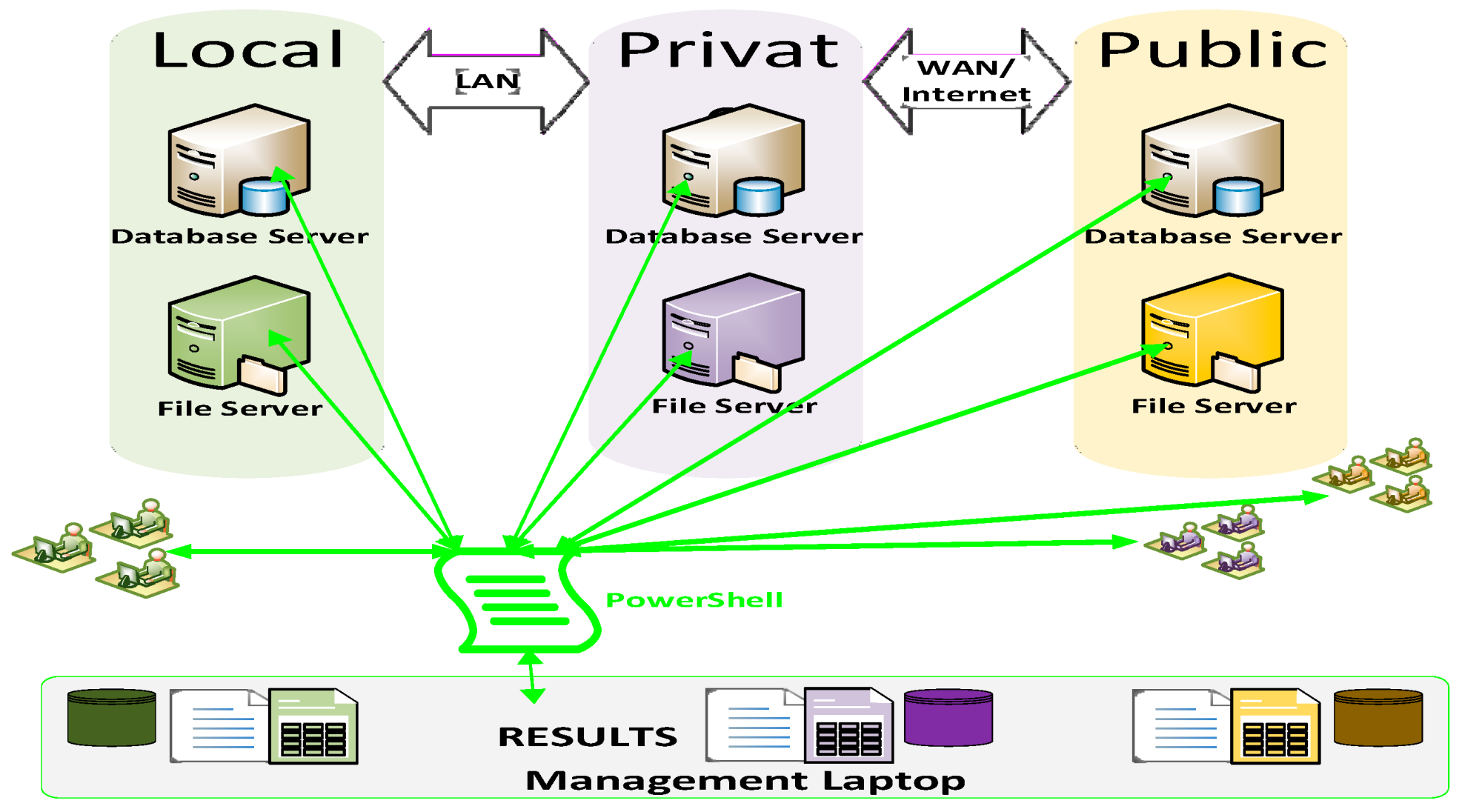
4. Hybrid Cloud Test-Bed Design
4.1. LAN, Private and Public Cloud Setup
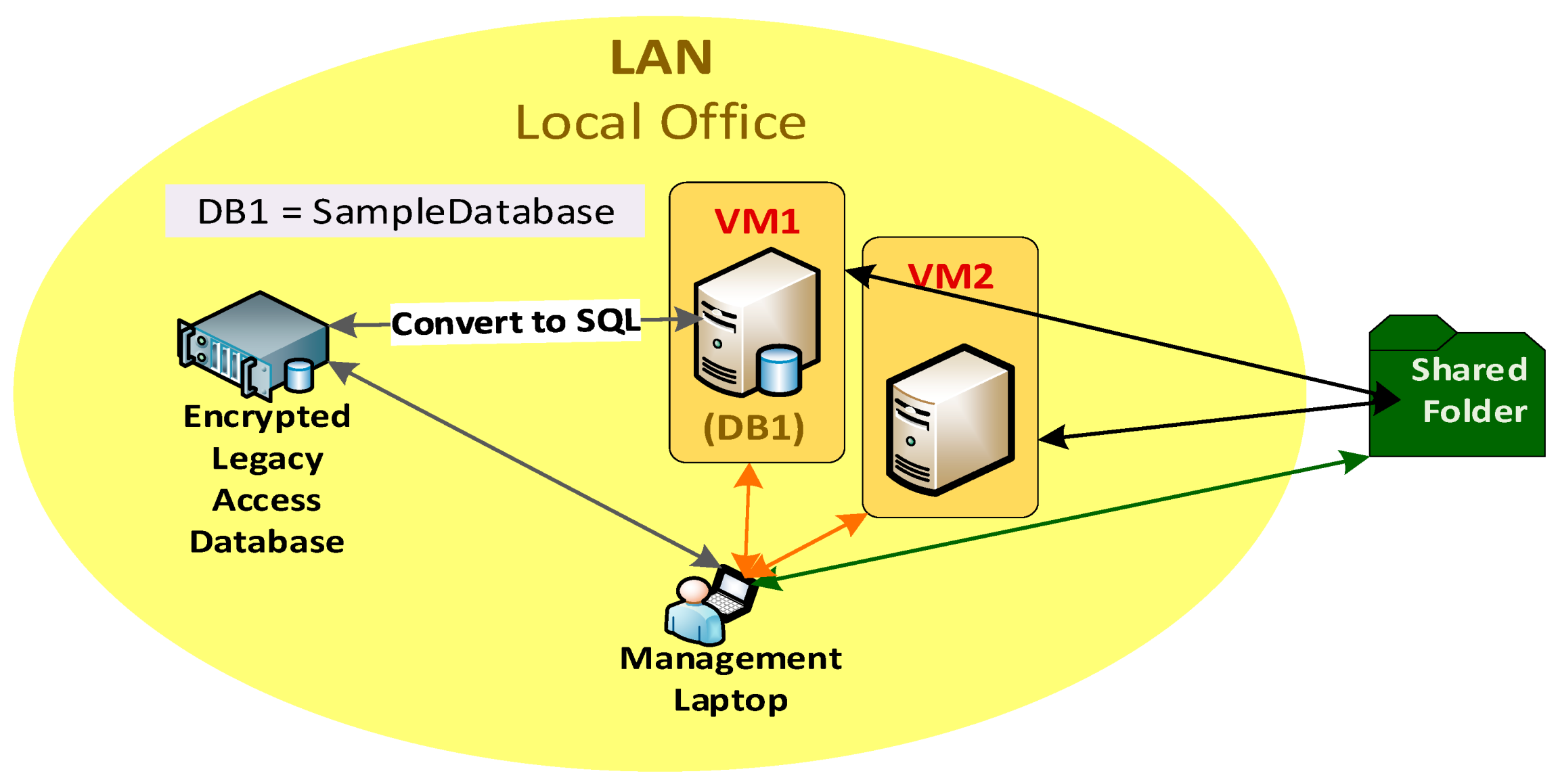
4.1.1. Local Area Network (LAN)
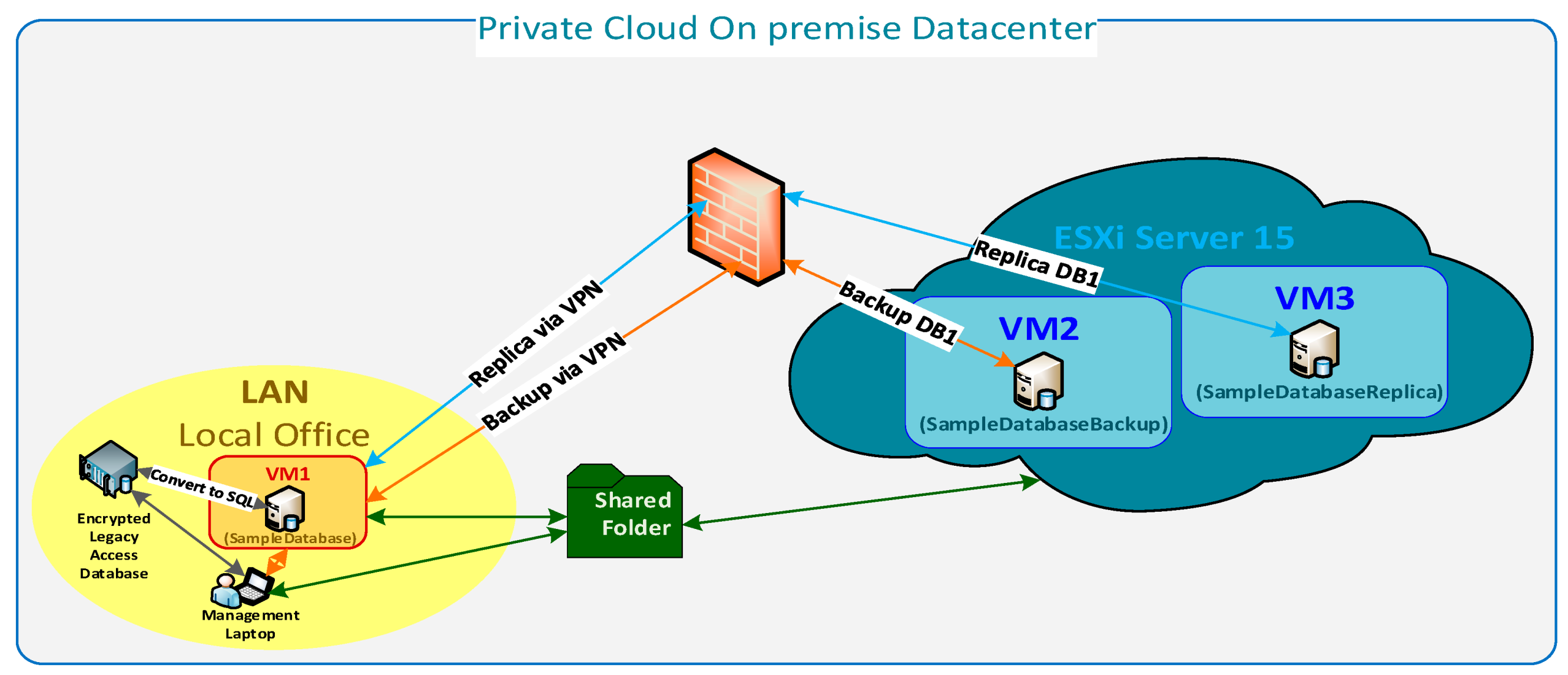
4.1.2. Private Cloud Environment
4.1.3. Public Cloud Environment
4.2. Data Discovery
- (a)
- Structured
- (b) Semi-structured
- (c) Unstructured
5. Testing
5.1. Example Scenario
- Do not have secure remote connectivity set up to access all devices on each component within the hybrid cloud; therefore, all PII cannot be identified or accessed on every device. In this example scenario, the assigned user only has access to the production database.
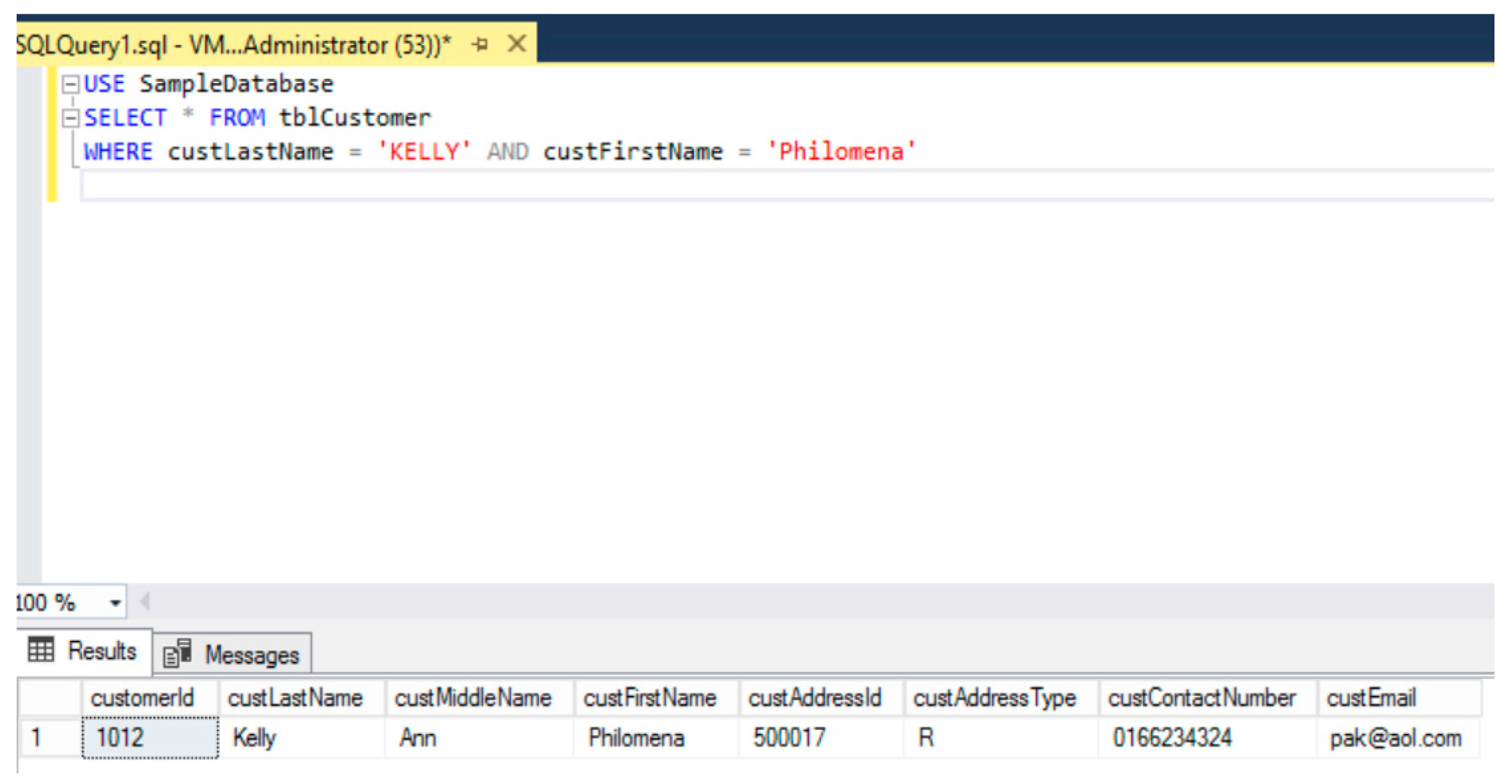
- An SQL query would be run to identify and report the location of PII in the production database, without using encryption.
- The output from the query would possibly be stored in a document/file that was not encrypted.
- Do not have audit trails in place that can be used to demonstrate reasonable measures were taken to identify, locate, report and delete PII. This example highlights there is no guarantee which user will be assigned these tasks thus making auditing and event logging harder to trace.
- Do not have authority to access all devices and the devices they have access to, they do not have authority to all PII so unable to identify, locate and report PII.
- User does not have access to some of the passwords or cryptographic keys, and therefore cannot access all PII.
- Retains expired PII.
- Retains more PII than what was/is required for the purpose, thinking they might use it in the future.
- Do not know their data landscape, nor what constitutes PII and as a result upon receipt of a valid request from a data subject to erase their PII, think deleting PII from the production database will suffice. In this example, the assigned user only checks the production database.
- PII stored in other formats were not investigated.
- An SQL query would have been run only over the Production database to locate PII, so other databases and data formats throughout the hybrid cloud environment would have been overlooked.
- Expired PII may be deactivated in some way, but unlikely to have been identified with a view to erasure.
- No automation tool or script to identify and report the location of PII for a data subject or PII that has expired.
- No access control lists or firewall rules configured to enable a user or device to access PII on every device.
- The backup process of nightly, weekly and monthly would erase the PII; however, there could be occasions where the monthly runs late, so PII would not be erased within the time limit of 30 day, which would be a PII breach.
- Backups and archives may be stored off-site and on tapes.
- PII would only have been deleted from the production database.
- No processes or procedures in place to document.
5.2. Tests
5.2.1. Structured PII Held in Databases within the Hybrid Cloud
5.2.2. Semi-Structured PII Held in Various Locations within the Hybrid Cloud
5.2.3. Unstructured PII Held in Various Locations within Hybrid Cloud
5.3. Post Implementation
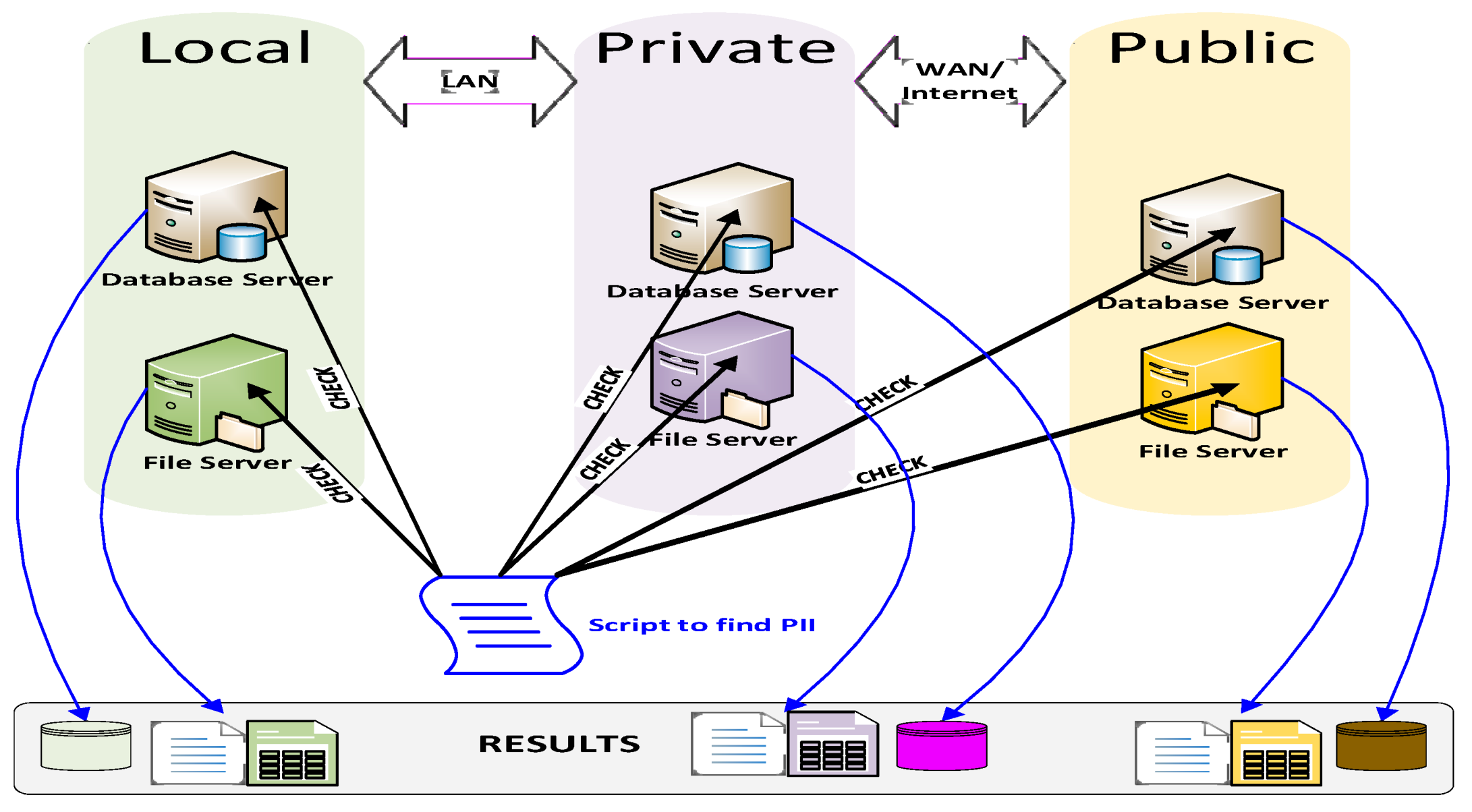
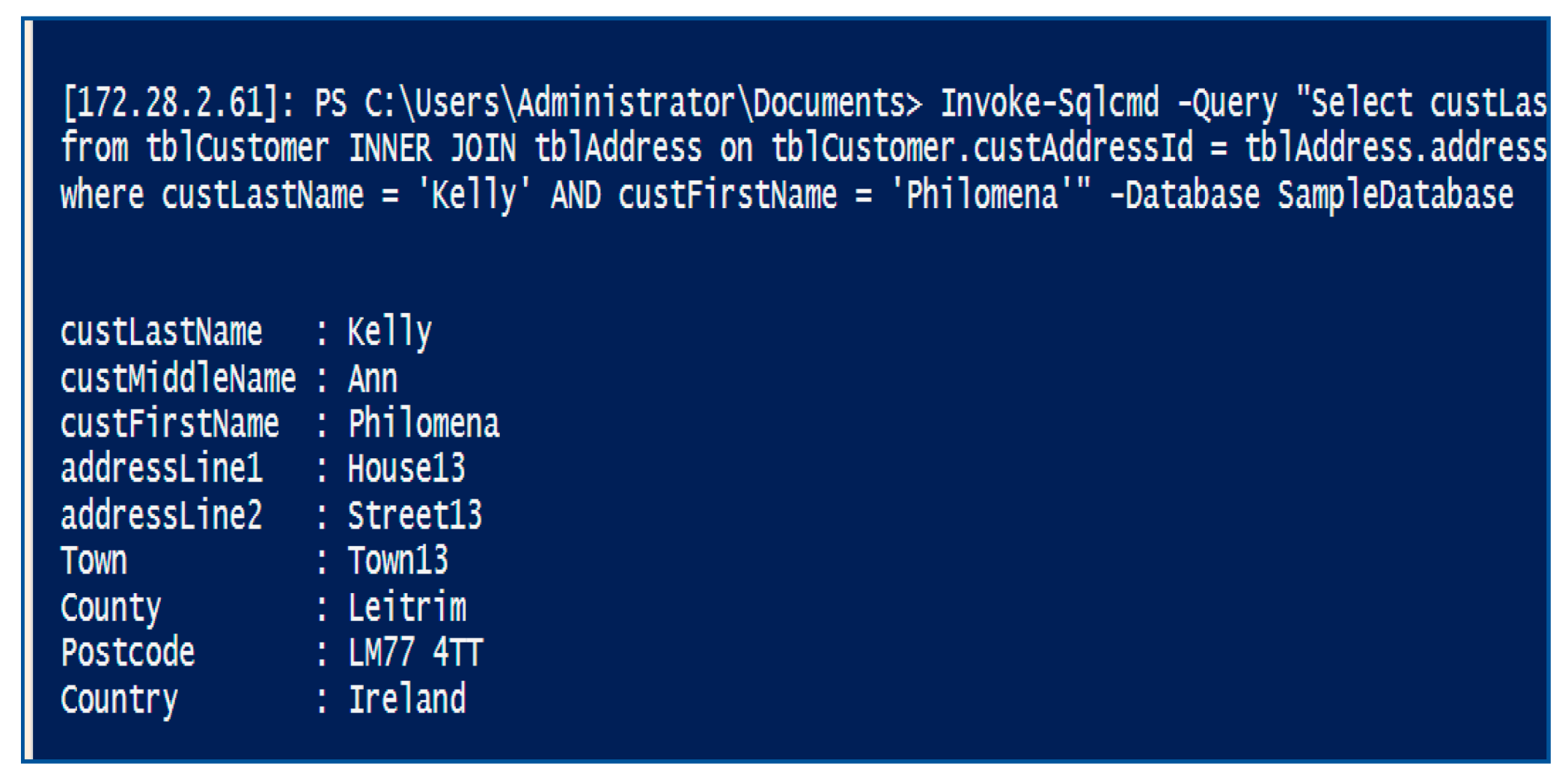
- The dedicated management laptop has a file containing all the relevant credentials encrypted. These can only be decrypted by the super user (who encrypted them) and only on this device (where they were encrypted), enabling secure non-intrusive remote connectivity to every device on each component within the hybrid cloud, enabling all PII to be identified and located.
- PowerShell can encrypt and decrypt so files containing PII will be encrypted in transit as well as at rest.
- Credentials are stored encrypted and only the super user can decrypt these when required.
- Files can be encrypted using an Advanced Encryption Standard (AES) algorithm, so the data retrieved using the script may be encrypted. The use of specified trusted hosts adds to securing access.
- Only one super user will carry out this task; therefore, audit trails and event logs can be used to check the activity of this user and demonstrate that reasonable measures were taken to identify, locate, report and delete PII.
- The super user has the appropriate authority to access all devices and access all PII on these devices so PII can be identified and the location reported for all PII within the hybrid cloud environment.
- The super user will have access to all passwords, cryptographic keys, names and IP addresses of all devices within the hybrid cloud enabling administrative access to all devices.
- Expired PII is no longer retained as PowerShell can identify and retrieve the location of all PII within the hybrid environment and so can be deleted.
- Whilst identifying all the PII that is currently retained, extra PII may be identified and dealt with, but data minimisation would be carried out under GDPR Article 5 “Principles relating to processing of personal data”.
- The data landscape is clear so now all areas containing all formats of PII can be identified and located within the hybrid cloud environment.
- The super user has administrative authority to all PII on every device within the hybrid environment and because of this, the process cannot be fully automated. A manual log on is required to every device and each script run separately. All PII can now be identified for a data subject and PII where the contract has expired.
- With all devices configured, PowerShell can be run to locate and retrieve the location of PII for both a data subject and expired PII.
- Access control lists and firewall rules are configured to only allow the dedicated management machine and super user access to PII on every device.
- The backup process of nightly, weekly and monthly would erase the PII; therefore, procedures are put in place to ensure that the monthly is run on 28th day or nearest weekend to 28th day of the month.
- Backups and archives may be stored off-site and on tapes. These must all be encrypted and stored in a secure environment and where feasible erased.
- All PII would be securely deleted from every device within the hybrid cloud.
- Steps undertaken would be documented so they can be used to demonstrate that reasonable measures were taken to be compliant with GDPR Article 17, “Right to Erasure”.
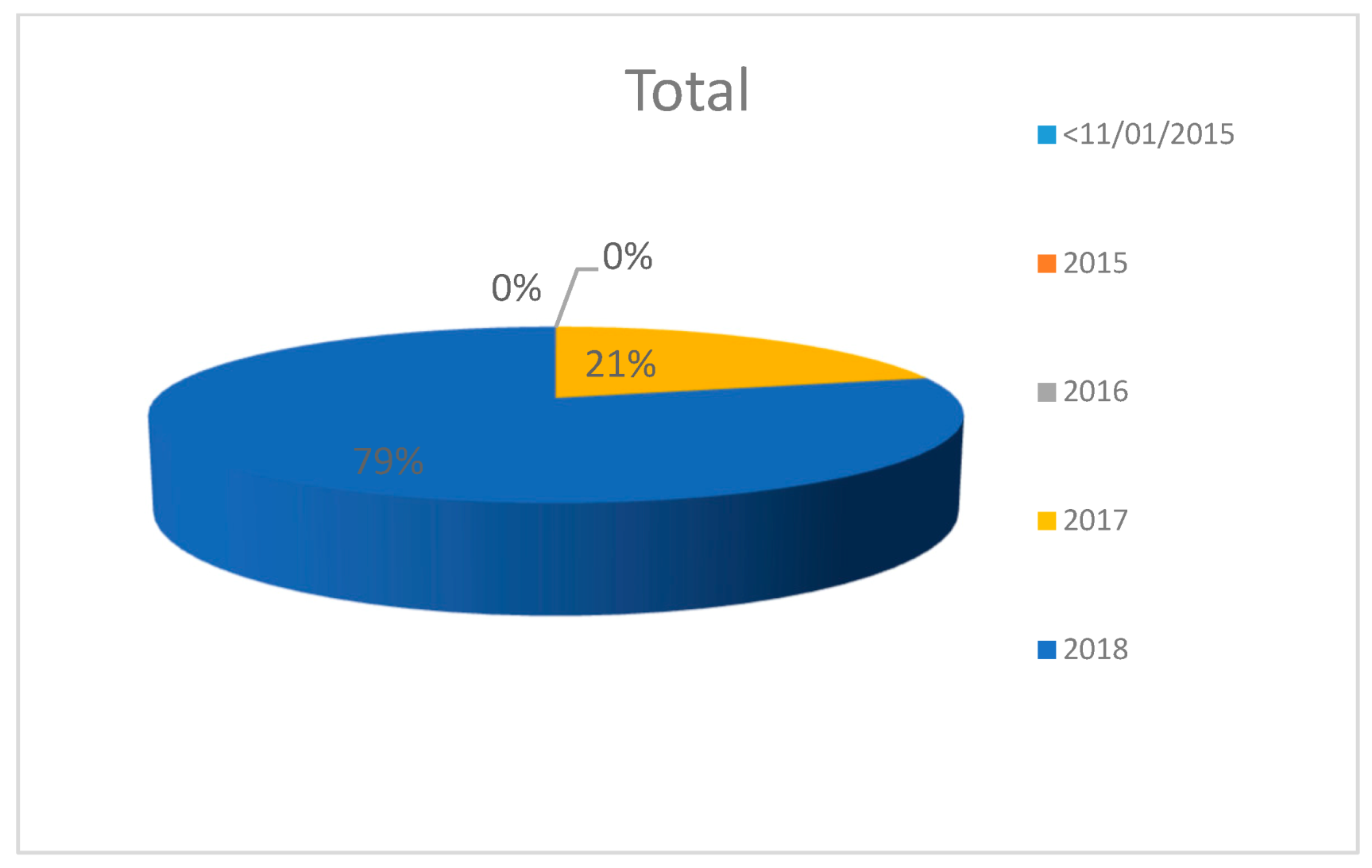
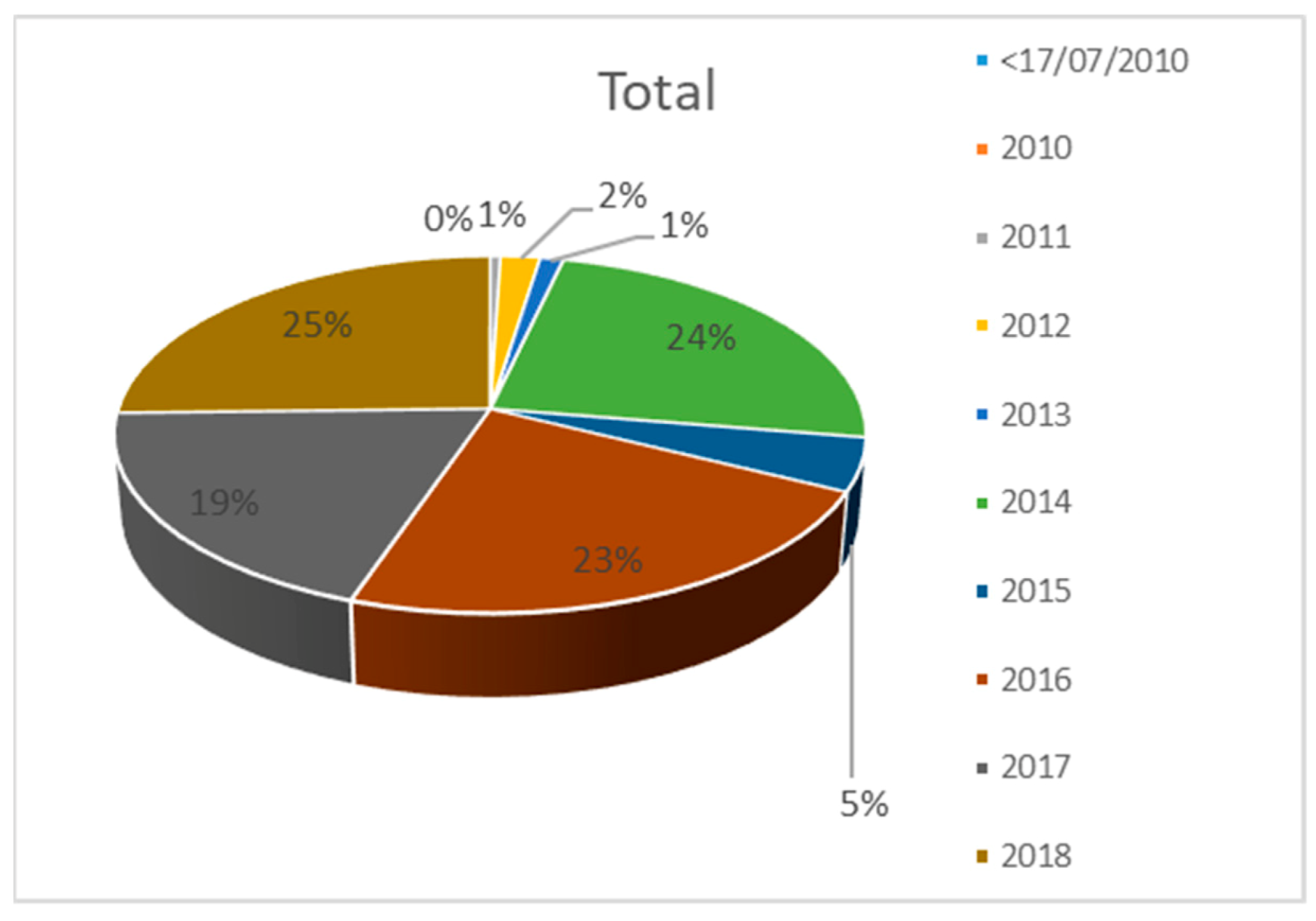
6. Evaluation
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Silicon Republic. Interview with Ireland’s Data Protection Commissioner, Helen Dixon. 2017. Available online: https://www.youtube.com/watch?v=nV7isMbAS7s (accessed on 11 January 2018).
- Singh, S. Hybrid Cloud Market. 2018. Available online: https://www.marketsandmarkets.com/PressReleases/hybrid-cloud.asp (accessed on 30 August 2018).
- Charles, J. The Most Effective Ways to Protect Your Small Business from Cyber Attacks. Small Business Trends. 2017. Available online: https://smallbiztrends.com/2017/01/how-to-protect-your-small-business-against-a-cyber-attack.html (accessed on 30 August 2018).
- Bradley, N. The Threat is Coming from Inside the Network: Insider Threats Outrank External Attacks. 2015. Available online: https://securityintelligence.com/the-threat-is-coming-from-inside-the-network/ (accessed on 30 August 2018).
- European Commission. What Is a Data Controller or a Data Processor; European Commission: Brussels, Belgium, 2018; Available online: https://ec.europa.eu/info/law/law-topic/data-protection/reform/rules-business-and-organisations/obligations/controller-processor/what-data-controller-or-data-processor_en (accessed on 22 August 2018).
- Villers, V.; Vonner, F. GDPR: The Legal Issues in Jargon-Free English. 2016. Available online: https://www.pwc.lu/en/general-data-protection/docs/pwc-gdpr-legal-issues-in-jargon-free-english.pdf (accessed on 31 March 2020).
- General Data Protection Regulation (GDPR)—Final Text Neatly Arranged. 2018. Available online: https://gdpr-info.eu/ (accessed on 22 August 2018).
- Data Protection. Data Protection Acts 1988 and 2003: Informal Consolidation. 2018. Available online: https://www.dataprotection.ie/documents/legal/CompendiumAct.pdf (accessed on 22 August 2018).
- TechNet. What is Volume Shadow Copy Service? Data Recovery. 2008. Available online: https://technet.microsoft.com/pt-pt/library/cc757854(v=ws.10).aspx (accessed on 17 September 2018).
- ICO. Deleting Your Data from Computers, Laptops and Other Devices. 2018. Available online: https://ico.org.uk/your-data-matters/online/deleting-your-data/ (accessed on 18 September 2018).
- Citizensinformation.ie. Your Rights under the GDPR. 2018. Available online: http://www.citizensinformation.ie/en/government_in_ireland/data_protection/rights_under_general_data_protection_regulation.html (accessed on 22 August 2018).
- Stevestein. Download SQL Server PowerShell Module. 2018. Available online: https://docs.microsoft.com/en-us/sql/powershell/download-sql-server-ps-module (accessed on 22 September 2018).
- Hughes, T.J.; Saverice-Rohan, A. IAPP-EY Annual Privacy Governance Report 2017. Available online: https://iapp.org/media/pdf/resource_center/IAPP-EY-Governance-Report-2017.pdf (accessed on 23 August 2018).
- Mantelero, A. The EU Proposal for a General Data Protection Regulation and the roots of the “right to be forgotten”. Comput. Law Secur. Rev. 2013, 29, 229–235. [Google Scholar] [CrossRef]
- Dulong de Rosnay, M.; Guadamuz, A. Memory Hole or Right to Delist? Implications of the Right to be Forgotten for Web Archiving. RESET 2017, 1, 3. [Google Scholar] [CrossRef]
- Carter, E.L. The Right to Be Forgotten; Oxford Research Encyclopedia of Communication: Oxford, UK, 2016; Available online: http://communication.oxfordre.com/view/10.1093/acrefore/9780190228613.001.0001/acrefore-9780190228613-e-189 (accessed on 23 August 2018).
- ColumbiaLearn. MOOC FOE1x; 5.6.1 The Liability of Search Engines; FOE in the Digital Age—Part I. 2018. Available online: https://www.youtube.com/watch?v=KExWhmJm1NM&index=40&list=PLSuwqsAnJMtwD9UjukMljQDRefFCp0cIm (accessed on 11 January 2018).
- Vollmer, N. Article 10 EU General Data Protection Regulation (EU-GDPR). 2018. Available online: http://www.privacy-regulation.eu/en/article-10-processing-of-personal-data-relating-to-criminal-convictions-and-offences-GDPR.htm (accessed on 23 August 2018).
- Ahmed, F.U. Right to be forgotten: A critique of the post-Costeja Gonzalez paradigm. Comp. Telecommun. Law Rev. 2015, 21, 175–185. [Google Scholar]
- Hoffman, C. Why Deleted Files Can Be Recovered, and How You Can Prevent it. How-To Geek. 2018. Available online: https://www.howtogeek.com/125521/htg-explains-why-deleted-files-can-be-recovered-and-how-you-can-prevent-it/ (accessed on 14 September 2018).
- Gottlieb, C. Right to Erasure. The GDPR Guy. 2018. Available online: https://thegdprguy.com/right-to-erasure/ (accessed on 17 September 2018).
- Jayaram, P. Recover Deleted Data from SQL Table Using Transaction Log and LSNs—DZone Database. 2018. Available online: https://dzone.com/articles/recover-deleted-data-from-sql-table-using-transact (accessed on 17 September 2018).
- Anderson, M. Why Data Erasure Matters for GDPR. The Ontrack UK Blog. 2018. Available online: https://www.ontrack.com/uk/blog/the-world-of-data/why-data-erasure-matters-for-gdpr/ (accessed on 17 September 2018).
- Anuradha, P.; Kumar, T.R.; Sobhana, N.V. Recovering deleted browsing artifacts from web browser log files in Linux environment. In Proceedings of the 2016 Symposium on Colossal Data Analysis and Networking (CDAN), Indore, India, 18–19 March 2016; pp. 1–4. [Google Scholar]
- CSO Online. What is Personally Identifiable Information (PII)? How to Protect it under GDPR. 2018. Available online: https://www.csoonline.com/article/3215864/privacy/how-to-protect-personally-identifiable-information-pii-under-gdpr.html (accessed on 17 March 2018).
- Bavota, G. Mining Unstructured Data in Software Repositories: Current and Future Trends. In Proceedings of the 2016 IEEE 23rd International Conference on Software Analysis, Evolution, and Reengineering (SANER), Suita, Japan, 14–18 March 2016; pp. 1–12. [Google Scholar]
- Simms, D.; Ghernaouti, S. Structured and Unstructured Data in the Cloud: A Swiss Perspective on Readiness and Internal Controls. In Proceedings of the 27th International Conference on Advanced Information Networking and Applications Workshops, Barcelona, Spain, 25–28 March 2013; pp. 643–648. [Google Scholar] [CrossRef]
- Sriraghav, K.; Jayanthi, S.; Vidya, N.; Enigo, V.S.F. ScrAnViz—A tool to scrap, analyze and visualize unstructured-data using attribute-based opinion mining algorithm. In Proceedings of the 2017 Innovations in Power and Advanced Computing Technologies (i-PACT), Vellore, India, 21–22 April 2017; pp. 1–5. [Google Scholar]
- Zhang, Q.; Cheng, L.; Cheng, R. Cloud Computing: State-of-the-Art and Research Challenges. 2010. Available online: https://link.springer.com/content/pdf/10.1007/s13174-010-0007-6.pdf (accessed on 31 March 2020).
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2011; p. 7.

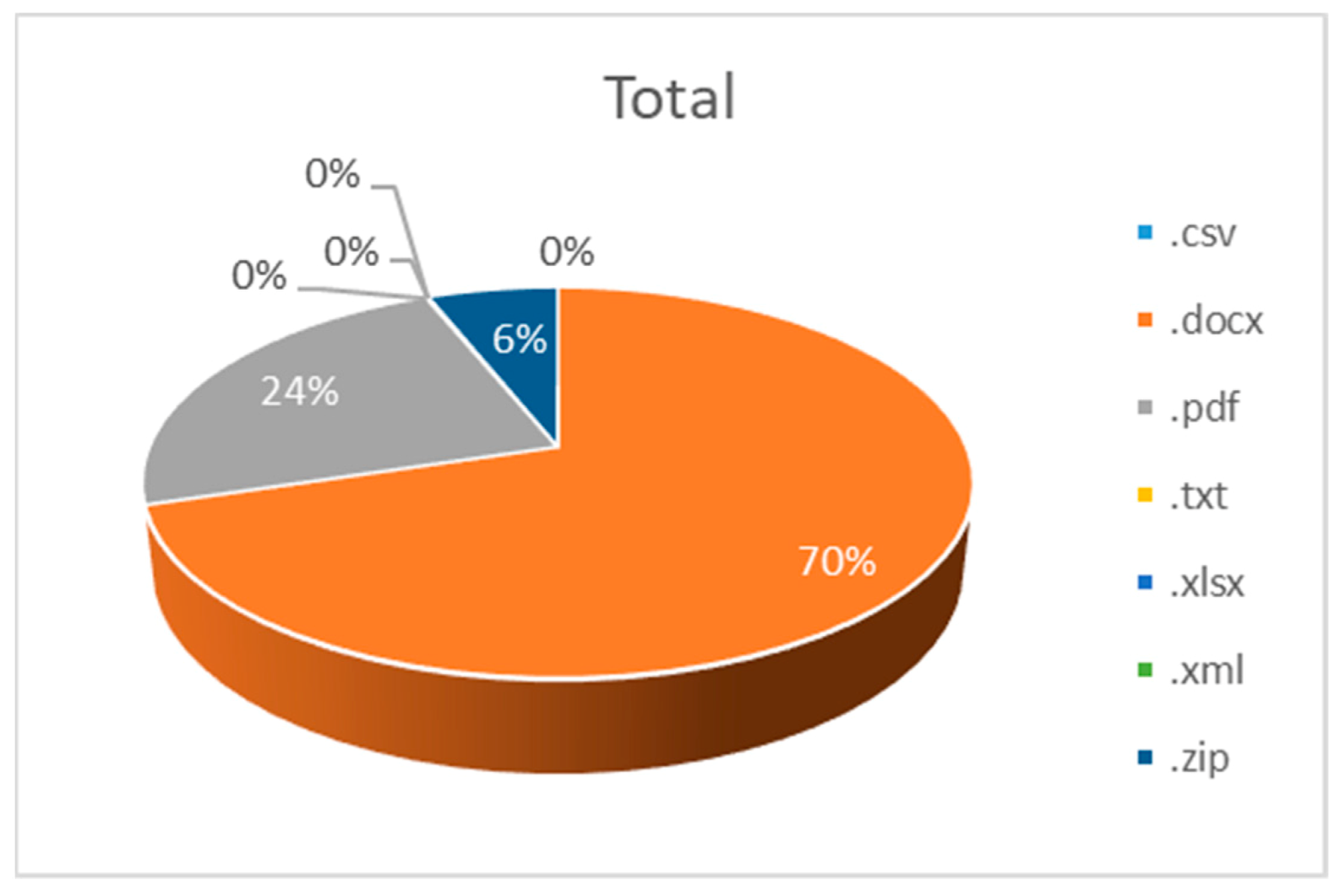

| Employee | Customer | Payment |
|---|---|---|
| employeeId | customerId | PaymentId |
| empLastName, empMiddleName & empFirstName | custLastName, custMiddleName & custFirstName | cardNumber, sortCode & accountNumber |
| empAddressId | custAddressId | |
| empContactNumber | custContactNumber | |
| empEmail | custEmail |
| Recommendations to be Implemented | Before Using Recommendations | After Using Recommendations |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| PII for Data Subject | |||
|---|---|---|---|
| Data Subject | LAN | PRIVATE | PUBLIC |
| Structured | Yes | Yes | Yes |
| Semi-Structured | Yes | Yes | Yes |
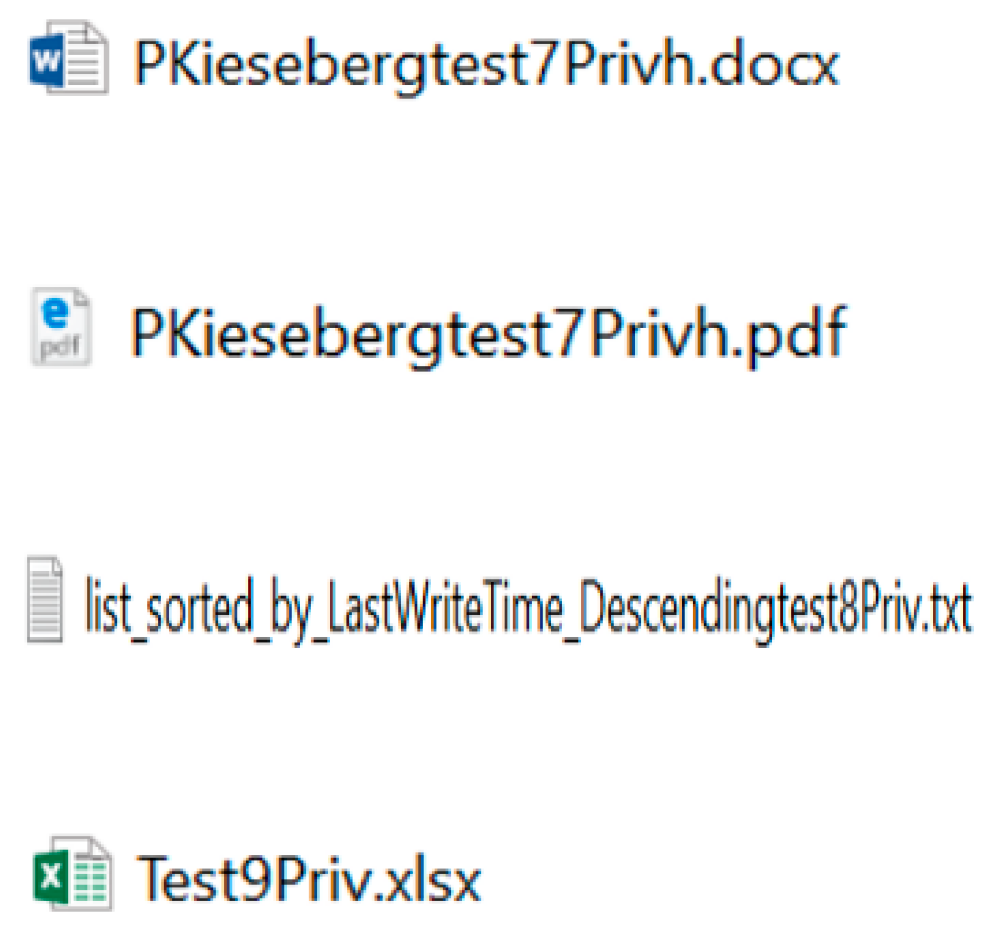
| Unstructured | Yes (.txt) No (.docx, .pdf, .xlsx) | Yes (.txt) No (.docx, .pdf, .xlsx) | Yes (.txt) No (.docx, .pdf, .xlsx) |
| Encrypted | Yes (access database) No (.zip) | n/a | n/a |
| PII That Has Expired | |||
|---|---|---|---|
| Expiration Date | LAN | PRIVATE | PUBLIC |
| Structured | Yes | Yes | Yes |
| Semi-Structured | Yes | Yes | Yes |
| Unstructured | Yes (.docx, .pdf, .txt) No (.xlsx) | Yes (.docx, .pdf, .txt) No (.xlsx) | Yes (.docx, .pdf, .txt) No (.xlsx) |
| Encrypted | Yes (access database) No (.zip) | n/a | n/a |
| Top 14 Recommendations to Become Compliant with GDPR Article 17 Right to Erasure (“Right to be Forgotten”) | |
|---|---|
| Dedicated Management Laptop: | |
| 1 | Allocate a dedicated management machine configured with trusted hosts, file containing encrypted username and passwords, to connect securely with all devices. |
| Encryption | |
| 2 | Ensure PII is encrypted both at rest and in transit. |
| 3 | Ensure event logs and audit trails are in place, to demonstrate reasonable measures were taken to ensure the Right to Erasure (“Right to be Forgotten”). |
| Super User: Access and Authority | |
| 4 | Create a super user account with administrative authority enabling full access to all PII on every device (physical and virtual) within the hybrid environment. |
| 5 | Have access to passwords, cryptographic keys etc. |
| 6 | Have access to the names and IP addresses of all devices in the hybrid cloud. |
| Personally Identifiable Information (PII): | |
| 7 | Identify all the PII that is currently retained. |
| 8 | Create scripts to identify and locate PII for a data subject and where PII is due to expire, incorporating encryption. |
| Task Automation and Configuration Management Tool | |
| 9 | Use an appropriate tool. (If using PowerShell, as in this instance, ensure it has been configured on each device). |
| Security: Firewalls | |
| 10 | Make sure the Firewall has been configured with the relevant Inbound and Outbound rules for specific ports and IP addresses and Access Control Lists (ACLs) are up and running. |
| Erasure: | |
| 11 | Securely delete relevant PII records (remember to empty recycle bins, clear history and remove from backups and archives, which may be stored off-site and on tape, if feasible). |
| 14 | Document steps carried out. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kelly, M.; Furey, E.; Curran, K. How to Achieve Compliance with GDPR Article 17 in a Hybrid Cloud Environment. Sci 2021, 3, 3. https://doi.org/10.3390/sci3010003
Kelly M, Furey E, Curran K. How to Achieve Compliance with GDPR Article 17 in a Hybrid Cloud Environment. Sci. 2021; 3(1):3. https://doi.org/10.3390/sci3010003
Chicago/Turabian StyleKelly, Miriam, Eoghan Furey, and Kevin Curran. 2021. "How to Achieve Compliance with GDPR Article 17 in a Hybrid Cloud Environment" Sci 3, no. 1: 3. https://doi.org/10.3390/sci3010003
APA StyleKelly, M., Furey, E., & Curran, K. (2021). How to Achieve Compliance with GDPR Article 17 in a Hybrid Cloud Environment. Sci, 3(1), 3. https://doi.org/10.3390/sci3010003






