A Deep Learning Approach for Securing IoT Infrastructure with Emphasis on Smart Vertical Networks
Abstract
:1. Introduction
- A novel security framework: in this paper, we propose a comprehensive security framework that makes use of fog computing to alleviate congestion and reduce latency, thereby enhancing the responsiveness of IoT-based applications in smart cities.
- In this article, we present a method that uses artificial neural networks (ANNs) based on deep learning to detect vulnerabilities and respond to security threats within smart vertical networks (SVNs).
- Threat detection and response in real time: our approach utilizes deep learning techniques to identify and mitigate real-time threats.
- We emphasize the adaptability of our deep learning models, demonstrating their integration into existing IoT infrastructures in order to strengthen the security framework holistically.
- Detailed validation: through rigorous experimentation and case studies, we demonstrate that our proposed method is effective in strengthening the SVN component of IoT infrastructures, which is crucial for the smooth operation of smart cities.
2. Related Works
3. Database Description
3.1. ToN-IoT Dataset
3.2. InSDN Dataset
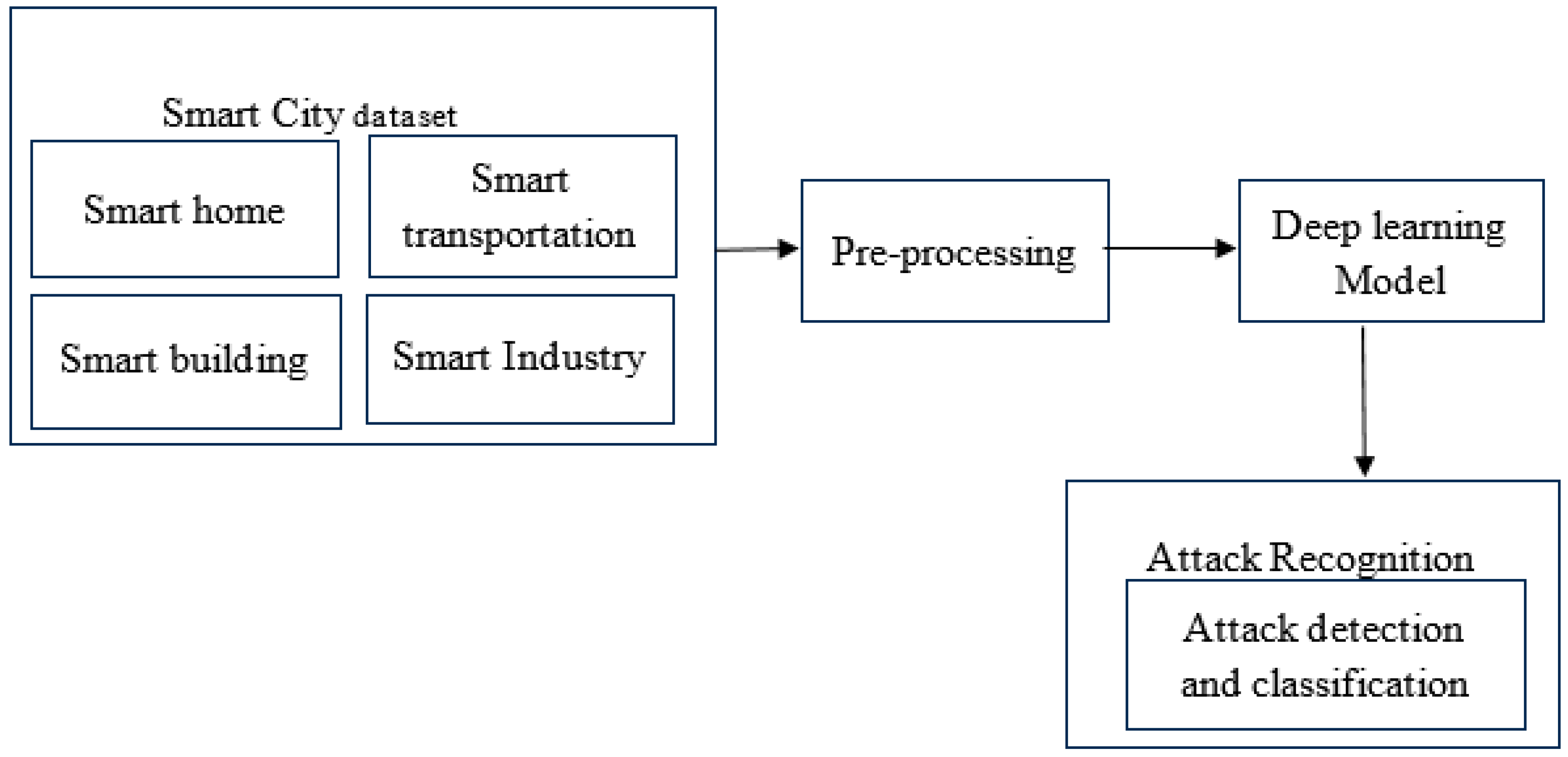
4. Proposed Methodology
Stacked Ensemble Model
- Xception CNN Model
- Entry Flow (C1–C5)
- Middle Flow (C6)
- Exit Flow (C7–C9)
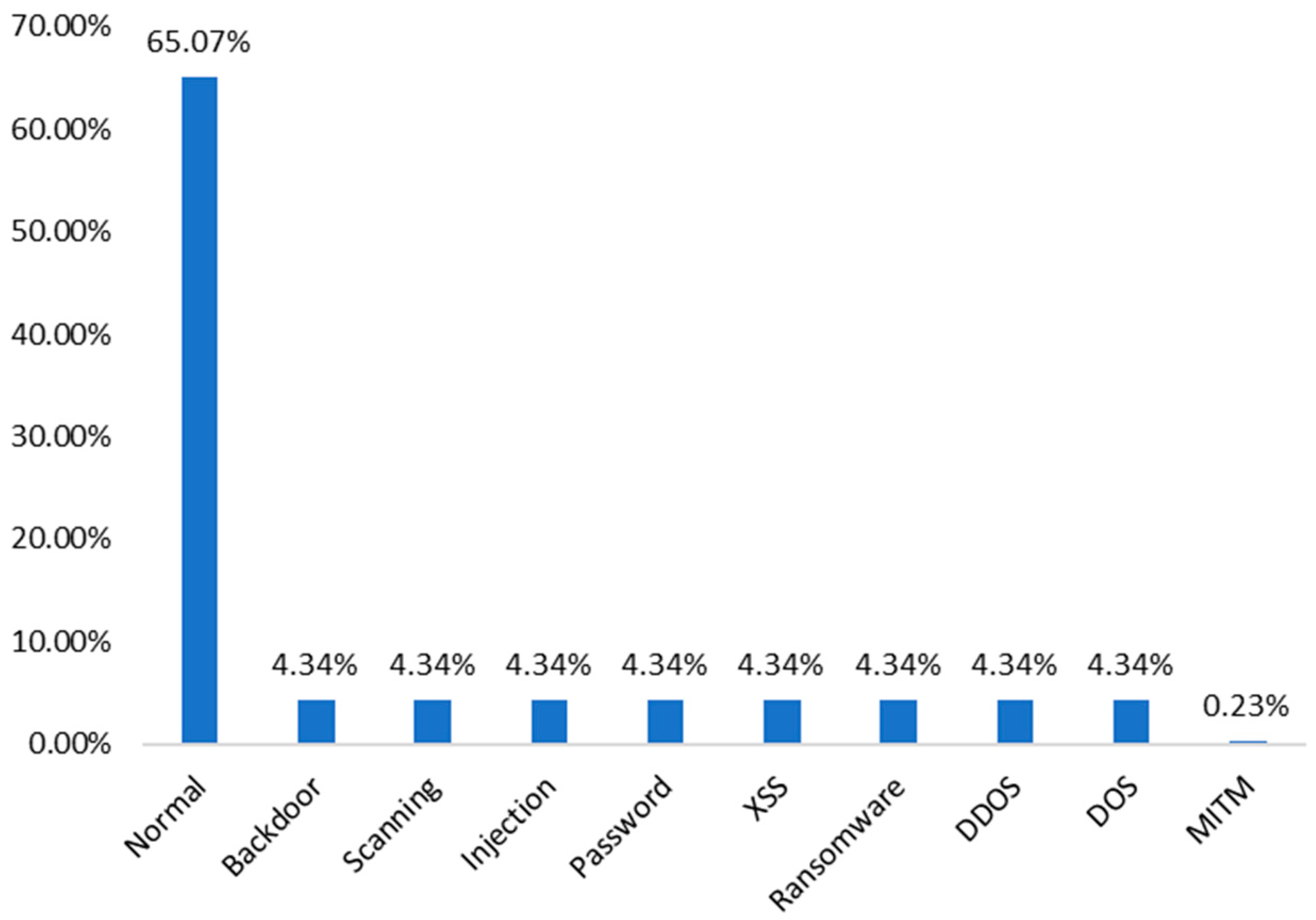
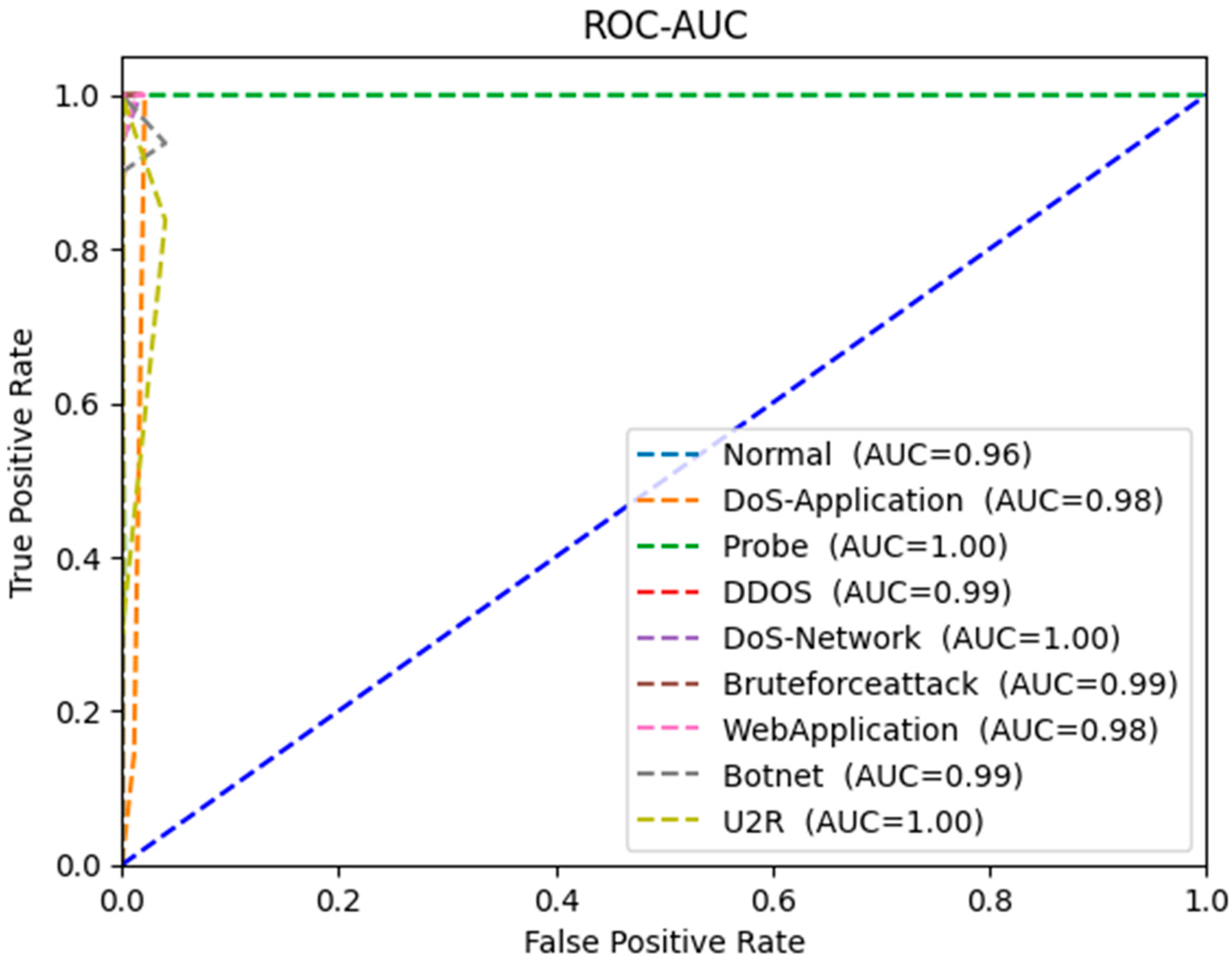
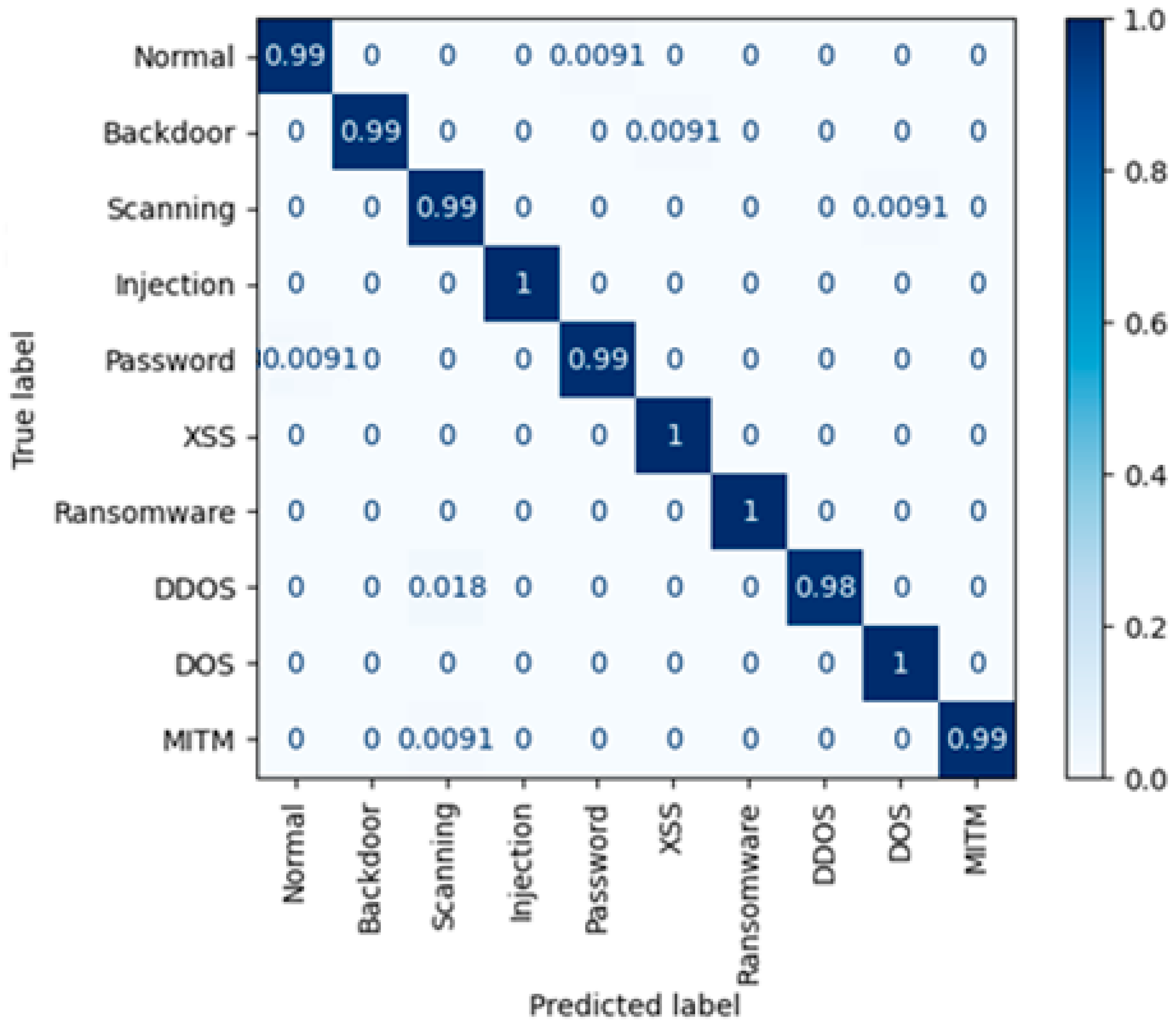
5. Result and Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Saba, T. Intrusion detection in smart city hospitals using ensemble classifiers. In Proceedings of the 13th International Conference on the Developments on eSystems Engineering (DeSE2020), Liverpool, UK, 14–17 December 2020. [Google Scholar]
- Qureshi, T.N.; Khan, Z.A.; Javaid, N.; Aldegheishem, A.; Rasheed, M.B.; Alrajeh, N. Elephant herding robustness evolution algorithm with multi-clan co-evolution against cyber attacks for scale-free internet of things in smart cities. IEEE Access 2023, 11, 79056–79072. [Google Scholar] [CrossRef]
- Prabakar, D.; Sundarrajan, M.; Manikandan, R.; Jhanjhi, N.Z.; Masud, M.; Alqhatani, A. Energy Analysis-Based Cyber Attack Detection by IoT with Artificial Intelligence in a Sustainable Smart City. Sustainability 2023, 15, 6031. [Google Scholar] [CrossRef]
- Symantec. Internet Security Threat Report; Symantec: Tempe, AZ, USA, 2020; p. 1. [Google Scholar]
- Costa, B.; Bachiega, J.; de Carvalho, L.R.; Araujo, A.P.F. Orchestration in Fog Computing: A Comprehensive Survey. ACM Comput. Surv. 2022, 55, 1–34. [Google Scholar] [CrossRef]
- Chang, V.; Golightly, L.; Modesti, P.; Xu, Q.A.; Doan, L.M.T.; Hall, K.; Boddu, S.; Kobusińska, A. A survey on intrusion detection systems for fog and cloud computing. Future Internet 2022, 14, 89. [Google Scholar] [CrossRef]
- Saba, T.; Rehman, A.; Sadad, T.; Kolivand, H.; Bahaj, S.A. Anomaly-based intrusion detection system for IoT networks through deep learning model. Comput. Electr. Eng. 2022, 99, 107810. [Google Scholar] [CrossRef]
- Yan, Z.; Yang, G.; He, R.; Yang, H.; Ci, H.; Wang, R. Ship Trajectory Clustering Based on Trajectory Resampling and Enhanced BIRCH Algorithm. J. Mar. Sci. Eng. 2023, 11, 407. [Google Scholar] [CrossRef]
- Liu, X.; Liu, Y.; Liu, A.; Yang, L.T. Defending ON–OFF attacks using light probing messages in smart sensors for industrial communication systems. IEEE Trans. Ind. Inform. 2018, 14, 3801–3811. [Google Scholar] [CrossRef]
- Guo, Y.; Wang, Y.; Khan, F.; Al-Atawi, A.A.; Abdulwahid, A.A.; Lee, Y.; Marapelli, B. Traffic Management in IoT Backbone Networks Using GNN and MAB with SDN Orchestration. Sensors 2023, 23, 7091. [Google Scholar] [CrossRef]
- Sivaramakrishnan, R.; SenthilKumar, G. Workload Characterization in Embedded Systems Utilizing Hybrid Intelligent Gated Recurrent Unit and Extreme Learning Machines. Int. J. Intell. Syst. Appl. Eng. 2024, 12, 233–243. [Google Scholar]
- Jagadeesan, J.; Kirupanithi, D.N. An Optimized Ensemble Support Vector Machine-Based Extreme Learning Model for Real-Time Big Data Analytics and Disaster Prediction. Cogn. Comput. 2023, 1–23. [Google Scholar] [CrossRef]
- Dixit, P.; Kohli, R.; Acevedo-Duque, A.; Gonzalez-Diaz, R.R.; Jhaveri, R.H. Comparing and Analyzing Applications of Intelligent Techniques in Cyberattack Detection. Secur. Commun. Netw. 2021, 2021, 5561816. [Google Scholar] [CrossRef]
- Sriranjani, R.; Saleem, M.D.; Hemavathi, N.; Parvathy, A. Machine Learning Based Intrusion Detection Scheme to Detect Replay Attacks in Smart Grid. In Proceedings of the 2023 IEEE International Students’ Conference on Electrical, Electronics and Computer Science (SCEECS), Bhopal, India, 18–19 February 2023; pp. 1–5. [Google Scholar]
- Deep, S.; Zheng, X.; Jolfaei, A.; Yu, D.; Ostovari, P.; Kashif Bashir, A. A survey of security and privacy issues in the Internet of Things from the layered context. Trans. Emerg. Telecommun. Technol. 2022, 33, e3935. [Google Scholar] [CrossRef]
- Patel, O.; Patel, H. To Use an Ethereum-Based Public Blockchain Network to Provide Confidentiality, Integrity, and Access Control to IoT-Based Medical Healthcare Data. J. Pharm. Negat. Results 2022, 13, 4400–4413. [Google Scholar]
- Li, Z.; He, Y.; Yu, H.; Kang, J.; Li, X.; Xu, Z.; Niyato, D. Data heterogeneity-robust federated learning via group client selection in industrial IoT. IEEE Internet Things J. 2022, 9, 17844–17857. [Google Scholar] [CrossRef]
- Rao, P.M.; Deebak, B.D. Security and privacy issues in smart cities/industries: Technologies, applications, and challenges. J. Ambient Intell. Humaniz. Comput. 2022, 14, 10517–10553. [Google Scholar] [CrossRef]
- Anand, P.; Singh, Y.; Selwal, A.; Singh, P.K.; Felseghi, R.A.; Raboaca, M.S. IoVT: Internet of Vulnerable Things? Threat Architecture, Attack Surfaces, and Vulnerabilities in Internet of Things and Its Applications towards Smart Grids. Energies 2020, 13, 4813. [Google Scholar] [CrossRef]
- Malhotra, P.; Singh, Y.; Anand, P.; Bangotra, D.K.; Singh, P.K.; Hong, W.-C. Internet of Things: Evolution, Concerns and Security Challenges. Sensors 2021, 21, 1809. [Google Scholar] [CrossRef]
- Kumar, P.; Prabhat, G.P.; Tripathi, R.G. An ensemble learning and fog-cloud architecture-driven cyber-attack detection framework for IoMT networks. Comput. Commun. 2021, 166, 110–124. [Google Scholar] [CrossRef]
- Said Elsayed, M.; Le-Khac, N.A.; Dev, S.; Jurcut, A.D. Network anomaly detection using LSTM based autoencoder. In Proceedings of the 16th ACM Symposium on QoS and Security for Wireless and Mobile Networks (2020), Alicante, Spain, 16–20 November 2020; pp. 37–45. [Google Scholar]
- Elsayed, M.S.; Jahromi, H.Z.; Nazir, M.M.; Jurcut, A.D. The role of CNN for intrusion detection systems: An improved CNN learning approach for SDNs. In Future Access Enablers for Ubiquitous and Intelligent Infrastructures, Proceedings of the 5th EAI International Conference, FABULOUS 2021, Virtual Event, 6–7 May 2021; Springer: Cham, Switzerland, 2021; pp. 91–104. [Google Scholar]
- Rondon, L.P.; Babun, L.; Aris, A.; Akkaya, K.; Uluagac, A.S. Survey on enterprise Internet-of-Things systems (E-IoT): A security perspective. Ad Hoc Netw. 2022, 125, 102728. [Google Scholar] [CrossRef]
- Alajanbi, M.; Mohd Arfian Ismail, R.A.H.; Sulaiman, J. Intrusion Detection: A Review. Mesopotamian J. Cybersecur. 2021, 2021, 4. [Google Scholar]
- Safara, F.; Souri, A.; Serrizadeh, M. Improved intrusion detection method for communication networks using association rule mining and artificial neural networks. IET Commun. 2020, 14, 1192–1197. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Moustafa, N.; Hawash, H.; Ding, W. Deep Learning Techniques for IoT Security and Privacy; Springer: New York, NY, USA, 2022; Volume 997. [Google Scholar]
- An, G.H.; Cho, T.H. Improving Sinkhole Attack Detection Rate through Knowledge-Based Specification Rule for a Sinkhole Attack Intrusion Detection Technique of IoT. Int. J. Comput. Netw. Appl. IJCNA 2022, 9, 169–178. [Google Scholar] [CrossRef]
- Haider, W.; Moustafa, N.; Keshk, M.; Fernandez, A.; Choo, K.-K.-R.; Wahab, A. FGMCHADS: Fuzzy Gaussian mixture-based correntropy models for detecting zero-day attacks from linux systems. Comput. Secur. 2020, 96, 101906. [Google Scholar] [CrossRef]






| Ref. | Authors and Year | Main Contribution | Advantages | Disadvantages | Applicability to IoT Security |
|---|---|---|---|---|---|
| [7] | Saba et al., 2022 | Anomaly-based IDS for IoT networks via DL | High detection accuracy, adaptability to new threats | Requires substantial training data, may have longer training times | Highly applicable for network security |
| [10] | Guo et al., 2023 | Traffic management in IoT networks with SDN orchestration | Efficient traffic handling, enhanced through GNN and MAB | Complexity in deployment and maintenance, possible overhead | Applicable for managing network traffic |
| [16] | Patel and Patel, 2022 | Blockchain for IoT healthcare data confidentiality | Enhanced data integrity and access control | Blockchain complexity, scalability issues | Applicable for secure healthcare data |
| [22] | Elsayed et al., 2020 | Network anomaly detection using LSTM-based autoencoder | Effective for sequential data, captures temporal dependencies | Can be computationally intensive, challenging to tune | Applicable for continuous data streams |
| [23] | Elsayed M et al., 2020 | Improved CNN for IDS in SDNs | Higher accuracy in detection with an improved learning approach | Specific to SDNs, may not generalize to other network types | Applicable for intrusion detection in SDNs |
| [14] | Sriranjani et al., 2023 | Machine learning for detecting replay attacks in smart grid | Effective in identifying specific replay attack patterns | Limited to smart grid environments | Applicable for smart grid security |
| [18] | Rao and Deebak, 2022 | Security and privacy in smart cities/industries | Comprehensive review of technologies and applications | No new model or algorithm proposed | Provides a framework for addressing smart city security challenges |
| [21] | Kumar et al., 2021 | Cyberattack detection for IoMT networks | Uses ensemble learning and fog–cloud architecture for efficiency | Requires specific infrastructure setup | Highly applicable for IoMT security |
| LSTM Layers | Hidden Layers | Accuracy | ROC | Precision | Recall | F1-Score |
|---|---|---|---|---|---|---|
| 1 | 100 | 98.2% | 0.95 | 0.92 | 0.89 | 0.905 |
| 1 | 200 | 97.6% | 0.94 | 0.91 | 0.87 | 0.89 |
| 1 | 300 | 98.0% | 0.95 | 0.92 | 0.88 | 0.9 |
| 1 | 400 | 97.4% | 0.94 | 0.90 | 0.86 | 0.88 |
| 2 | 100 | 98.4% | 0.96 | 0.93 | 0.90 | 0.915 |
| 2 | 200 | 98.6% | 0.97 | 0.94 | 0.91 | 0.925 |
| 2 | 300 | 98.8% | 0.97 | 0.95 | 0.92 | 0.935 |
| 2 | 400 | 98.7% | 0.97 | 0.94 | 0.91 | 0.925 |
| 3 | 100 | 99.0% | 0.98 | 0.95 | 0.93 | 0.94 |
| 3 | 200 | 99.1% | 0.98 | 0.96 | 0.93 | 0.945 |
| 3 | 300 | 99.8% | 0.99 | 0.98 | 0.97 | 0.975 |
| 3 | 400 | 99.5% | 0.98 | 0.97 | 0.95 | 0.96 |
| 4 | 100 | 98.8% | 0.97 | 0.94 | 0.92 | 0.93 |
| 4 | 200 | 98.9% | 0.97 | 0.95 | 0.92 | 0.935 |
| 4 | 300 | 99.6% | 0.98 | 0.97 | 0.96 | 0.965 |
| 4 | 400 | 99.2% | 0.98 | 0.96 | 0.94 | 0.95 |
| LSTM Layers | Hidden Layers | Accuracy | ROC AUC | Precision | Recall | F1-Score |
|---|---|---|---|---|---|---|
| 1 | 100 | 95.2% | 0.951 | 0.942 | 0.962 | 0.952 |
| 1 | 200 | 96.5% | 0.965 | 0.954 | 0.974 | 0.964 |
| 1 | 300 | 97.1% | 0.971 | 0.962 | 0.978 | 0.970 |
| 1 | 400 | 96.8% | 0.968 | 0.957 | 0.975 | 0.966 |
| 2 | 100 | 97.5% | 0.975 | 0.968 | 0.978 | 0.973 |
| 2 | 200 | 98.3% | 0.983 | 0.978 | 0.983 | 0.980 |
| 2 | 300 | 98.7% | 0.987 | 0.982 | 0.987 | 0.985 |
| 2 | 400 | 98.5% | 0.985 | 0.980 | 0.988 | 0.984 |
| 3 | 100 | 98.8% | 0.988 | 0.983 | 0.989 | 0.986 |
| 3 | 200 | 99.1% | 0.991 | 0.986 | 0.992 | 0.989 |
| 3 | 300 | 99.8% | 0.998 | 0.996 | 0.998 | 0.997 |
| 3 | 400 | 99.5% | 0.995 | 0.994 | 0.995 | 0.995 |
| 4 | 100 | 99.0% | 0.990 | 0.988 | 0.991 | 0.989 |
| 4 | 200 | 99.2% | 0.992 | 0.990 | 0.993 | 0.992 |
| 4 | 300 | 99.6% | 0.996 | 0.995 | 0.997 | 0.996 |
| 4 | 400 | 99.3% | 0.993 | 0.992 | 0.994 | 0.993 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kolhar, M.; Aldossary, S.M. A Deep Learning Approach for Securing IoT Infrastructure with Emphasis on Smart Vertical Networks. Designs 2023, 7, 139. https://doi.org/10.3390/designs7060139
Kolhar M, Aldossary SM. A Deep Learning Approach for Securing IoT Infrastructure with Emphasis on Smart Vertical Networks. Designs. 2023; 7(6):139. https://doi.org/10.3390/designs7060139
Chicago/Turabian StyleKolhar, Manjur, and Sultan Mesfer Aldossary. 2023. "A Deep Learning Approach for Securing IoT Infrastructure with Emphasis on Smart Vertical Networks" Designs 7, no. 6: 139. https://doi.org/10.3390/designs7060139
APA StyleKolhar, M., & Aldossary, S. M. (2023). A Deep Learning Approach for Securing IoT Infrastructure with Emphasis on Smart Vertical Networks. Designs, 7(6), 139. https://doi.org/10.3390/designs7060139





