A New Code-Based Identity-Based Signature Scheme from the Ternary Large-Weight SDP
Abstract
1. Introduction
1.1. Contribution
1.2. Organization
2. Preliminaries
2.1. Notation
- General
| q | a prime number |
| a finite field of order q | |
| group of permutations | |
| the set of integers | |
| or ( a set) | the cardinal of the set |
| ( a subset of ) | is the complementary of |
- A function is called negligible if for all sufficiently large , , for all constant .
- Vectors and Matrices
| a row vector with n coordinates in | |
| a column vector which is the transpose of | |
| () | the Hamming weight: number of non-zero entries in |
| subset of vectors in of Hamming weight w | |
| component-wise product | |
| vector with only the coordinates indexed by , | |
| -matrix with entries in | |
| group of invertible square matrices of size n with entries in |
- Probability for a finite set , the notation indicates that i is assigned to be an element chosen uniformly at random from while indicates that i is assigned to be an element chosen uniformly at random using the seed . We denote the uniform distribution on by . The statistical distance between two discrete probability distributions over the same space is defined as .
2.2. Sigma Protocol and Identity-Based Identification
- : On input , where λ is a security parameter, returns a master-public and secret key pair .
- : On input and identity , it outputs a user secret key , which is assumed to be securely communicated to the user with the identity . In some cases, we allow the algorithm to output additional auxiliary information which can be shared publicly/with a verifier during the interactive protocol without compromising the secret information.
- Identification protocol: interactive protocol between a prover with inputs and a verifier with inputs . The protocol ends when outputs or .
- Experiment :
- The challenger obtains , and initializes the sets/lists into ∅, where: is the honest users set, is the corrupted users set, is the attacked user set, and is the prover’s session set.
- Phase 1: the adversary is allowed to query three different oracles, , and oracle if , otherwise, the is replaced by oracle.
- –
- if , then it returns ⊥. Otherwise, it updates the set and runs to obtain a user secret key that will be kept secret and returns 1 at the end.
- –
- if , then it returns ⊥. Otherwise, it updates the sets , , and returns .
- –
- if , then it returns ⊥. Otherwise, it returns a conversation transcript .
- –
- if , then it returns ⊥. Otherwise, if : if , it updates , then, picks a random coin ρ, sets a state for the prover and becomes . At the end it returns . Furthermore, if is the final message of the protocol, it resets back to ∅. Else if , it updates and follows exactly the procedure as in except that it does not reset back to ∅ even if is the final message of the protocol.
- Phase 2: the adversary reveals the target identity that it will impersonate. If , the challenger halts; otherwise, it updates the set . The adversary is still allowed to query the three defined oracles in the first phase (except for ).
- : on input , where λ is a security parameter, it generates a public key and secret key pair .
- : on input secret key and a message m, returns a signature σ.
- : on input public key , a message m, and the signature σ returns deterministically accept if the message was signed using the legitimate secret key, or reject otherwise.
- A signature scheme is required to satisfy the following property:
2.3. Identity-Based Signatures
- : on input , where λ is a security parameter, returns a master-public and secret key pair .
- : on input and identity , it outputs a user secret key , which is assumed to be transmitted securely to the user with the identity .
- : a randomized algorithm that takes on its input a master-public key, a user secret key, and a message, and it returns a signature σ of the message.
- : a deterministic algorithm that on input an identity, a message, a signature σ, and the returns a decision: accept if σ is a valid signature for m and , or reject otherwise.
- A third party (or a trusted authority) runs the first two algorithms. An identity-based signature scheme is required to satisfy the following property:
2.4. Code-Based Cryptography
2.5. Wave Signature Scheme
- Sampling for will result a solution to the equation that has an expected weight . Going back to , as we mentioned before, the first decoding algorithm outputs any solution to the first equation in Proposition 1 using Prange. Since the appears twice in , it is used to maximize the weight of target vector , and that by taking such that , which implies that . Hence,and since , we have which explains why the weight of the solution the output by in is hard to find without the trapdoor. We stress again that the original uses a rejection sampling in its decoding algorithm in order to achieve solutions that are close to the ones that are uniformly distributed in . Furthermore, has been proved to be EUF-CMA secure based on the two following assumptions: the first relies on the hardness of decoding random codes, and the second relies on distinguishing a random code from a normalized generalized -code.
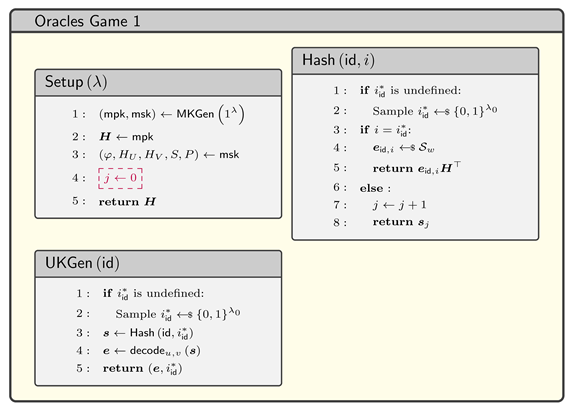
3. Identity-Based Identification from Wave
- Strategy 1: replacing with an such that , by that, a cheating prover hopes that .
- Strategy 2: replacing by an arbitrary of weight w, by that a cheating prover hopes that .
- Completeness. evident from the construction that an honest prover possessing a valid solution to of weight w always passes the verification with probability one.
- 3-Special soundness. let , , and be three valid transcripts sharing the same commitment and distinct challenges, thus, there exists at least (i)- two valid transcripts with different , and (ii)- two other valid transcripts with different with the same . From (i)- we can deduce that all the setups were generated honestly, and from (ii)- we can clearly extract the witness by computing .
- Special honest-verifier zero-knowledge. we build a simulator that can produce an indistinguishable transcript from the one obtained by honest execution of the protocol , without knowing a witness, when given , the challenge and the seed as input.
- From the seed , the simulator computes honestly .
- For , the simulator follows Strategy 1; taking any solution to and then computing and normally following the protocol. Since and are sampled uniformly at random, the generated by the simulator has the same distribution as . We havewhere and .
- For , the simulator follows Strategy 2; taking any vector and then computing and normally following the protocol. Since is sampled uniformly at random from and is negligible as ’s trapdoor one-way function is preimage sampleable on average, then it satisfies the property of the preimage sampling on average. Therefore, generated by the simulator has the same distribution as .where and .
If the commitment scheme () is hiding, then and are indistinguishable, and consequently, the two transcripts are indistinguishable as well.
- Game 0: This is the standard imp-pa game. The and oracles in this game are defined as the following,
- Game 1: This game has some differences in the , , and oracles from the previous game. These differences are specified in the following,
- Game 2: This game differs from Game 1 by making the following change to the . Instead of computing from the decoding algorithm , in Game 2 samples uniformly at random and outputs . Therefore, the difference between Game 1 and Game 2 corresponds to the statistical distance between , representing the distribution of the output of decoding and , representing the uniform distribution over . Hence, we have
- Game 3: In this game, the matrix is replaced by , in this way, the adversary is forced to find a solution to the problem. The adversary can detect the difference between this game and the previous one only if he can distinguish between : the distribution of the public key , and : the uniform distribution over . Let be the event that wins this game, then assuming the hardness of Problem 4,
- Game 4: In this game, once the adversary reveals the target identity that he intends to impersonate, the challenger checks whether has already been queried to the oracle before. If such a query has been made previously, the challenger aborts the game. Recall that is sampled uniformly at random. Therefore, by setting and , we can ensure that the challenger does not abort with probability bounded by sincehence,
- Game 5: Please note that at this point, none of the responses to the and queries depend on the secret since they have been replaced by random values. Therefore, the challenger can now respond to the conversation oracle queries on any identity by simulating the transcripts. This is indistinguishable from Game 4 due to the SHVZK property of the protocol. Let be the event that wins this game, we have ).
4. Identity-Based Signature
5. Security and Parameter Selection
- Forgery attack: in which the adversary attempts to solve the problem without the secret key.
- Key attack: in which the adversary seeks to either retrieve the secret key or solve the problem.
5.1. Optimizing the Size of Large-Weight Ternary Vectors
- Compression:
- Step 1: we replace all the non-zero coordinates of with ones, hence we obtain a binary vector that we denote in this step by . Notice that has the same large or low weight as the initial ternary vector and therefore, the size of vector can be encoded in the worst case in approximately bits using Golomb-Rice encoding. For more details, see [41,42]. (By “worst case” we mean or . A Better compression can be achieved if or .)
- Step 2: we remove all the zero entries in , and keep the rest in the same order. Let the resulting vector be denoted by . Since the multiplicative group has as its generator, i.e., , we can represent the entries in using the exponents : replace each 1 entry with exponent 0 and each with exponent 1. By doing so, the vector becomes binary and can be encoded in w bits, i.e., .
- Instead of sending , which can be encoded optimally in bits or in bits in bitsliced, we suggest sending , which can be encoded in less than bits. It is noteworthy to mention two cases in which maximum compression can be achieved:
- Case 1: if has full weight, we suggest only sending since there are no zeros in . Hence, can be encoded only in approximately n bits.
- Case 2: if has low weight, can be encoded in approximately bits.
- Decompression: is simplified in the following.
- For the parameters proposed for [6] submitted to the NIST’s second call for additional digital signatures, and , applying Section 5.1 led to a signature of size B instead of 822B.
5.2. Key Sizes
- The master-public key is a matrix over . This matrix can be encoded in bits, using an efficient encoding achieved through a compact representation that requires only bits per trit (or 5 trits per byte), which is indeed close to the entropy limit . For more details about this encoding, we advise the reader to check [6] (Appendix C.1).
- The user-secret key is defined as , where replaces the earlier pair , as explained above. Here, i is a -bit salt, , is generated from a seed of bits, and has a seed of bits and a ternary vector of length .Consequently, the total size of is approximately less than bits.
5.3. Signature Size
- of - is of size
- signature output by is of size
- ℓ is a commitment of size bits.
- is a seed of size bits.
- commitment of size bits.
- seeds of size bits.
- is of size: bits.
- As a result, by taking , we obtain a signature of size:
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. BGKM-SIG1

References
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Advances in Cryptology. CRYPTO’84; Blakley, G.R., Chaum, D., Eds.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 1984; Volume 196, pp. 47–53. [Google Scholar]
- Galindo, D.; Herranz, J.; Kiltz, E. On the Generic Construction of Identity-Based Signatures with Additional Properties. In Advances in Cryptology—ASIACRYPT 2006. ASIACRYPT 2006; Lai, X., Chen, K., Eds.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2006; Volume 4284, pp. 178–193. [Google Scholar] [CrossRef]
- Bellare, M.; Namprempre, C.; Neven, G. Security proofs for identity-based identification and signature schemes. J. Cryptol. 2009, 22, 1–61. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Barenghi, A.; Biasse, J.F.; Ngo, T.; Persichetti, E.; Santini, P. Advanced signature functionalities from the code equivalence problem. Int. J. Comput. Math. Comput. Syst. Theory 2022, 7, 112–128. [Google Scholar] [CrossRef]
- Banegas, G.; Carrier, K.; Chailloux, A.; Couvreur, A.; Debris-Alazard, T.; Gaborit, P.; Karpman, P.; Loyer, J.; Niederhagen, R.; Sendrier, N.; et al. Wave: Round 1 Submission. 2023. Available online: https://tdalazard.io/wave_documentation.pdf (accessed on 10 June 2025).
- Bidoux, L.; Gaborit, P.; Kulkarni, M.; Mateu, V. Code-based signatures from new proofs of knowledge for the syndrome decoding problem. Des. Codes Cryptogr. 2023, 91, 497–544. [Google Scholar] [CrossRef]
- Courtois, N.; Finiasz, M.; Sendrier, N. How to Achieve a McEliece-Based Digital Signature Scheme. In Advances in Cryptology—ASIACRYPT 2001; Boyd, C., Ed.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2001; Volume 2248, pp. 157–174. [Google Scholar] [CrossRef]
- Stern, J. A New Identification Scheme Based on Syndrome Decoding. In Advances in Cryptology—CRYPTO’ 93; Stinson, D.R., Ed.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 1994; Volume 773, pp. 13–21. [Google Scholar] [CrossRef]
- Niederreiter, H. Knapsack-type cryptosystems and algebraic coding theory. Prob. Contr. Inform. Theory 1986, 15, 157–166. [Google Scholar]
- Faugere, J.C.; Gauthier-Umana, V.; Otmani, A.; Perret, L.; Tillich, J.P. A distinguisher for high-rate McEliece cryptosystems. IEEE Trans. Inf. Theory 2013, 59, 6830–6844. [Google Scholar] [CrossRef]
- Cayrel, P.L.; Gaborit, P.; Girault, M. Identity-based identification and signature schemes using correcting codes. In Proceedings of the International Workshop on Coding and Cryptography, WCC, Versailles, France, 16–20 April 2007; pp. 69–78. [Google Scholar]
- El Yousfi Alaoui, S.M.; Cayrel, P.L.; Mohammed, M. Improved identity-based identification and signature schemes using Quasi-Dyadic Goppa codes. In Proceedings of the Information Security and Assurance: International Conference, ISA 2011, Brno, Czech Republic, 15–17 August 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 146–155. [Google Scholar]
- Barreto, P.S.; Cayrel, P.L.; Misoczki, R.; Niebuhr, R. Quasi-dyadic CFS signatures. In Proceedings of the International Conference on Information Security and Cryptology, Kunming, China, 14–16 December 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 336–349. [Google Scholar]
- Faugere, J.C.; Otmani, A.; Perret, L.; Tillich, J.P. Algebraic cryptanalysis of McEliece variants with compact keys. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Madrid, Spain, 30 May–3 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 279–298. [Google Scholar]
- Faugère, J.C.; Otmani, A.; Perret, L.; de Portzamparc, F.; Tillich, J.P. Folding alternant and Goppa Codes with non-trivial automorphism groups. IEEE Trans. Inf. Theory 2015, 62, 184–198. [Google Scholar] [CrossRef]
- Yang, G.; Tan, C.H.; Mu, Y.; Susilo, W.; Wong, D.S. Identity based identification from algebraic coding theory. Theor. Comput. Sci. 2014, 520, 51–61. [Google Scholar] [CrossRef]
- Song, B.; Zhao, Y. Provably secure identity-based identification and signature schemes from code assumptions. PLoS ONE 2017, 12, e0182894. [Google Scholar] [CrossRef] [PubMed]
- Cramer, R.; Damgård, I.; Schoenmakers, B. Proofs of Partial Knowledge and Simplified Design of Witness Hiding Protocols. In Advances in Cryptology—CRYPTO ’94; Desmedt, Y., Ed.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 1994; Volume 839, pp. 174–187. [Google Scholar] [CrossRef]
- Preetha Mathew, K.; Vasant, S.; Rangan, C.P. On provably secure code-based signature and signcryption scheme. IACR Cryptol. EPrint Arch. 2012, 2012, 585. [Google Scholar]
- Biasse, J.F.; Micheli, G.; Persichetti, E.; Santini, P. LESS is more: Code-based signatures without syndromes. In Proceedings of the International Conference on Cryptology in Africa, Cairo, Egypt, 20–22 July 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 45–65. [Google Scholar]
- Fiat, A.; Shamir, A. How to Prove Yourself: Practical Solutions to Identification and Signature Problems. In Advances in Cryptology—CRYPTO’ 86; Odlyzko, A.M., Ed.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 1987; Volume 263, pp. 186–194. [Google Scholar] [CrossRef]
- Debris-Alazard, T.; Sendrier, N.; Tillich, J.P. Wave: A New Family of Trapdoor One-Way Preimage Sampleable Functions Based on Codes. In Advances in Cryptology—ASIACRYPT 2019; Galbraith, S.D., Moriai, S., Eds.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2019; Volume 11921, pp. 21–51. [Google Scholar] [CrossRef]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for hard lattices and new cryptographic constructions. In Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008; pp. 197–206. [Google Scholar]
- Sendrier, N. Decoding one out of many. In Proceedings of the International Workshop on Post-Quantum Cryptography, Taipei, Taiwan, 29 November–2 December 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 51–67. [Google Scholar]
- Bricout, R.; Chailloux, A.; Debris-Alazard, T.; Lequesne, M. Ternary syndrome decoding with large weight. In Proceedings of the Selected Areas in Cryptography–SAC 2019: 26th International Conference, Waterloo, ON, Canada, 12–16 August 2019; Revised Selected Papers 26. Springer: Berlin/Heidelberg, Germany, 2020; pp. 437–466. [Google Scholar]
- Cho, J.; No, J.S.; Lee, Y.; Koo, Z.; Kim, Y.S. Enhanced pqsigRM: Code-based digital signature scheme with short signature and fast verification for post-quantum cryptography. Cryptol. Eprint Arch. 2022. [Google Scholar]
- Ritterhoff, S.; Maringer, G.; Bitzer, S.; Weger, V.; Karl, P.; Schamberger, T.; Schupp, J.; Wachter-Zeh, A. FuLeeca: A Lee-based signature scheme. In Proceedings of the Code-Based Cryptography Workshop, Lyon, France, 22–23 April 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 56–83. [Google Scholar]
- Debris-Alazard, T.; Loisel, P.; Vasseur, V. Exploiting signature leakages: Breaking Enhanced pqsigRM. In Proceedings of the 2024 IEEE International Symposium on Information Theory (ISIT), Athens, Greece, 7–12 July 2024; pp. 2903–2908. [Google Scholar]
- Hörmann, F.; van Woerden, W. FuLeakage: Breaking FuLeeca by learning attacks. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2024; Springer: Berlin/Heidelberg, Germany, 2024; pp. 253–286. [Google Scholar]
- Attema, T.; Fehr, S. Parallel repetition of (k 1, …, k μ)-special-sound multi-round interactive proofs. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 13–18 August 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 415–443. [Google Scholar]
- Kurosawa, K.; Heng, S.H. Identity-based identification without random oracles. In Proceedings of the Computational Science and Its Applications–ICCSA 2005: International Conference, Singapore, 9–12 May 2005; Springer: Berlin/Heidelberg, Germany, 2005. Part II 5. pp. 603–613. [Google Scholar]
- Fujioka, A.; Saito, T.; Xagawa, K. Security enhancement of identity-based identification with reversibility. In Proceedings of the Information and Communications Security: 14th International Conference, ICICS 2012, Hong Kong, China, 29–31 October 2012; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2012; pp. 202–213. [Google Scholar]
- NIST. Post-Quantum Cryptography: Digital Signature Schemes. Available online: https://csrc.nist.gov/projects/pqc-dig-sig (accessed on 10 June 2025).
- Fouque, P.A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Prest, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z.; et al. Falcon: Fast-Fourier lattice-based compact signatures over NTRU. Submiss. NIST’s Post-Quantum Cryptogr. Stand. Process 2018, 36, 1–75. [Google Scholar]
- Prange, E. The use of information sets in decoding cyclic codes. IRE Trans. Inf. Theory 1962, 8, 5–9. [Google Scholar] [CrossRef]
- Goldreich, O.; Kahan, A. How to construct constant-round zero-knowledge proof systems for NP. J. Cryptol. 1996, 9, 167–189. [Google Scholar] [CrossRef]
- Beullens, W. Sigma Protocols for MQ, PKP and SIS, and Fishy Signature Schemes. In Advances in Cryptology—EUROCRYPT 2020; Canteaut, A., Ishai, Y., Eds.; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2020; Part III; Volume 12107, pp. 183–211. [Google Scholar] [CrossRef]
- Sendrier, N. Wave parameter selection. In Proceedings of the International Conference on Post-Quantum Cryptography, College Park, MD, USA, 16–18 August 2023; pp. 91–110. [Google Scholar]
- Loyer, J. Quantum Security Analysis of Wave. Cryptol. Eprint Arch. 2023. Available online: https://eprint.iacr.org/2023/1263.pdf (accessed on 10 June 2025).
- Kiely, A. Selecting the Golomb parameter in Rice coding. IPN Prog. Rep. 2004, 42, 159. [Google Scholar]
- Rice, R.F. Some Practical Universal Noiseless Coding Techniques; Technical Report; National Aeronautics and Space Administration (NASA): Washington, DC, USA, 1979.
- Rissanen, J.; Langdon, G.G. Arithmetic coding. IBM J. Res. Dev. 1979, 23, 149–162. [Google Scholar] [CrossRef]
- Sayood, K. Introduction to Data Compression; Morgan Kaufmann: San Francisco, CA, USA, 2017. [Google Scholar]
- Banegas, G.; Debris-Alazard, T.; Nedeljković, M.; Smith, B. Wavelet: Code-based postquantum signatures with fast verification on microcontrollers. arXiv 2021, arXiv:2110.13488. [Google Scholar] [CrossRef]





| Scheme | Signature | Security | ||
|---|---|---|---|---|
| - [18] | 30 MB | 240 bit | 35 MB | |
| - [5] | MB | KB | KB | |
| - (this work) | MB | KB | 22 KB |
| n | k | w | M | |||
|---|---|---|---|---|---|---|
| 128 | 8576 | 4288 | 7668 | - | - | |
| - | 128 | 518 | 186 | 518 | 256 | 128 |
| Instance | Signature Size | + Our Technique Signature Size | Compression % |
|---|---|---|---|
| -I | 822B | B | |
| -III | 1249B | B | |
| -V | 1644B | B |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Challi, S.; Kulkarni, M.; Serraj, T. A New Code-Based Identity-Based Signature Scheme from the Ternary Large-Weight SDP. Cryptography 2025, 9, 53. https://doi.org/10.3390/cryptography9030053
Challi S, Kulkarni M, Serraj T. A New Code-Based Identity-Based Signature Scheme from the Ternary Large-Weight SDP. Cryptography. 2025; 9(3):53. https://doi.org/10.3390/cryptography9030053
Chicago/Turabian StyleChalli, Sana, Mukul Kulkarni, and Taoufik Serraj. 2025. "A New Code-Based Identity-Based Signature Scheme from the Ternary Large-Weight SDP" Cryptography 9, no. 3: 53. https://doi.org/10.3390/cryptography9030053
APA StyleChalli, S., Kulkarni, M., & Serraj, T. (2025). A New Code-Based Identity-Based Signature Scheme from the Ternary Large-Weight SDP. Cryptography, 9(3), 53. https://doi.org/10.3390/cryptography9030053