Optimizing Group Multi-Factor Authentication for Secure and Efficient IoT Device Communications
Abstract
1. Introduction
- Comprehensive evaluation of existing IoT group authentication mechanisms, identifying critical limitations in supporting secure and efficient authentication, particularly in the context of multidevice-to-device communication scenarios.
- Design and specification of four novel protocols, HGAKA (Hybrid Group Authentication and Key Acquisition), HGA (Hybrid Group Access), SGAKA (Symmetric-Key-based Group Authentication and Key Acquisition), and SGA (Symmetric-Key-based Group Access), that extend the M2I framework to enable group-based multi-factor authentication tailored for this context.
- Comprehensive security evaluation combining the following:
- –
- Informal analysis to validate security requirements and threat resilience.
- –
- Work factor evaluation to assess the computational effort required for attacks.
- –
- Formal verification using the AVISPA (Automated Validation of Internet Security Protocols and Applications) tool, ensuring confidentiality, authentication, and robustness against a wide range of potential attacks, including replay, impersonation, and man-in-the-middle attacks.
- Detailed performance evaluation and comparative analysis of the proposed protocols against existing state-of-the-art solutions, thoroughly examining both computational and communication overhead to assess their efficiency.
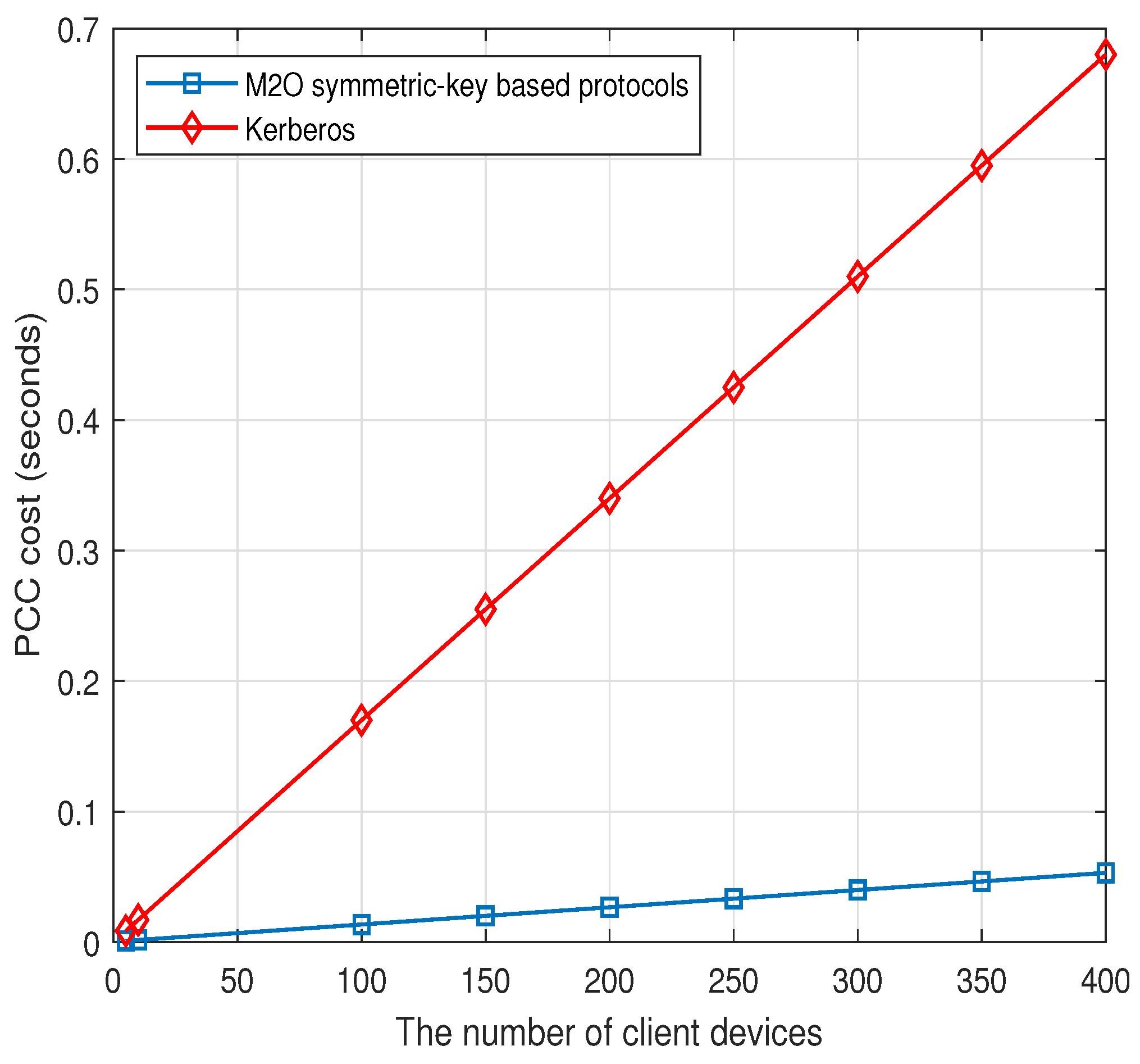
- Experimental and comparative evaluation of communication and computation costs, showing that the symmetric-key-based version of our protocols reduces these costs by 70∼74% and 89∼92%, respectively, compared to Kerberos.
2. Related Work
3. High-Level Ideas, Design Preliminaries, and Building Blocks
3.1. High-Level Ideas
- Authenticate devices according to their mode of interaction, e.g., device-to-device or multidevice-to-device interactions, to reduce the number of tokens used to facilitate identity verification.
- Use HMAC to aggregate clients’ tokens into a single group token when an authentication instance has more than one client.
- Use the Homomorphic Encryption property to reduce the number of verifications when asymmetric-key ciphers are used.
- Use a secret sharing scheme in symmetric-key-based multidevice-to-device authentication to enable clients to use their tokens (i.e., session key shares) to compute the session key.
3.2. Assumptions
- Devices have two symmetric keys.
- Devices of classes and each have an additional pair of asymmetric keys , } to support asymmetric authentication as they have higher capabilities [33].
- In the case of group authentication, client devices involved in an authentication instance can communicate with each other during the authentication process.
- One of the client devices will be selected as a group leader, and the selection can be based on the computational capabilities of the devices.
- The target device, , has a strong level of security, including the security of the long-term key () and the private key (). In other words, it is assumed that and its keys are secure as hosts a high or very high value asset, and it should be equipped with a strong level of security protection.
3.3. Performance Metrics
Theoretical Analysis:
- Communication costs are calculated based on the number and size of messages exchanged between protocol participants during execution.
- Computation costs are evaluated according to the number of cryptographic operations performed and the algorithms used to carry out these operations.
3.4. Building Blocks
3.4.1. Homomorphic Encryption
3.4.2. Shamir’s Secret Sharing
- Secrecy: Given a secret share, , it is hard to learn anything about the secret.
- Flexibility: Given a set of secret shares, S, it is easy to add or delete shares without changing the secret, as long as the .
- Recoverability: Given a subset of secret shares, , it is easy to compute the secret if .
- (i)
- Secret share construction
- Specify k (e.g., k = 3) and n (e.g., n = 5).
- Choose random numbers, e.g., 50 and 11.
- Build a polynomial of degree using Equation (1), where is the secret and to , the coefficients of the polynomial, are the random numbers chosen in the previous step.
- Construct n shares using the polynomial function, where each share is defined as . Given n points, e.g., 1 to 5, the shares are {(1, 740), (2, 823), (3, 928), (4, 1055), (5, 1204)}.
- (ii)
- Secret recovery
4. The Many-to-One (M2O) Protocols for Multidevice-to-Device Authentication
4.1. Performance Evaluation Assumptions
- Identifiers and timestamps are 32 bits long [68].
- Nonces are 128 bits long [69].
- AES-128 is used as the symmetric-key cipher. Hence, the output size is a multiple of 128 bits [70].
- SHA-256 and HMAC-SHA256 are used for hashing, producing 256-bit message digests [71].
- RSA-3072 is used as the asymmetric-key cipher. Although the RSA block size is variable, the maximum input length of the most expensive RSA implementation is defined as the modulus (i.e., ) [72]. Hence, the input size is a multiple of 318 bytes = 2544 bits.
4.2. The M2O Hybrid Protocols
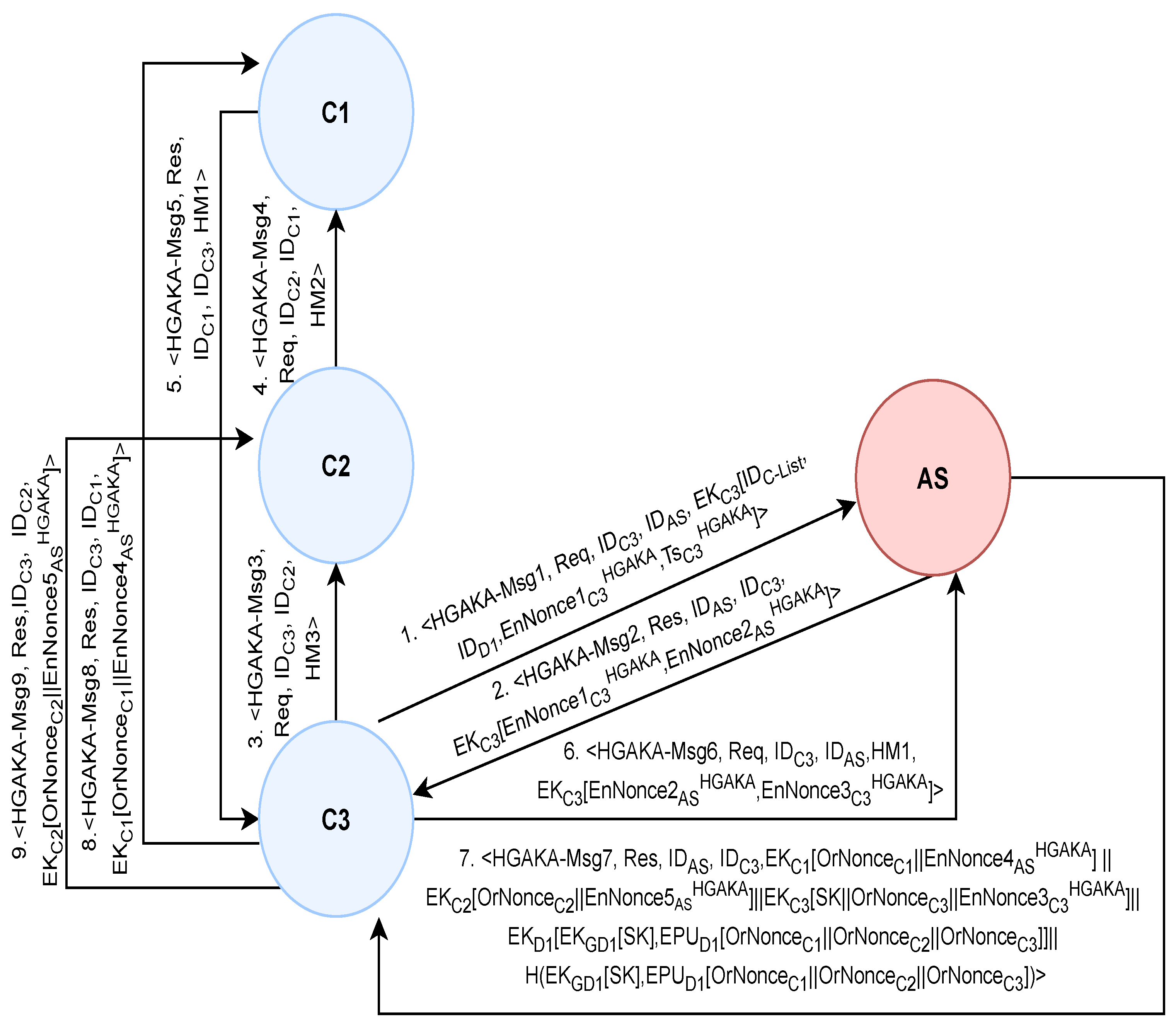
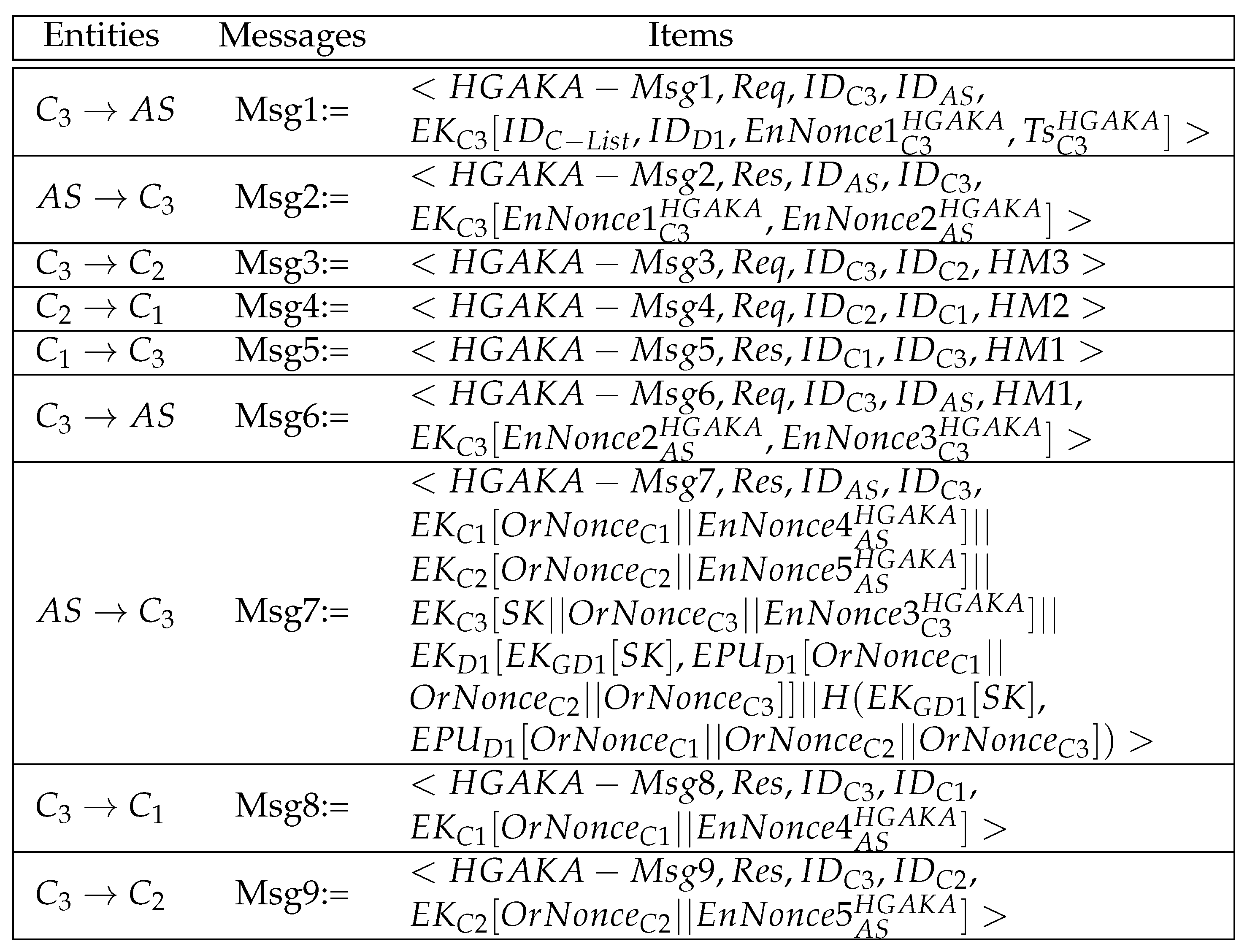
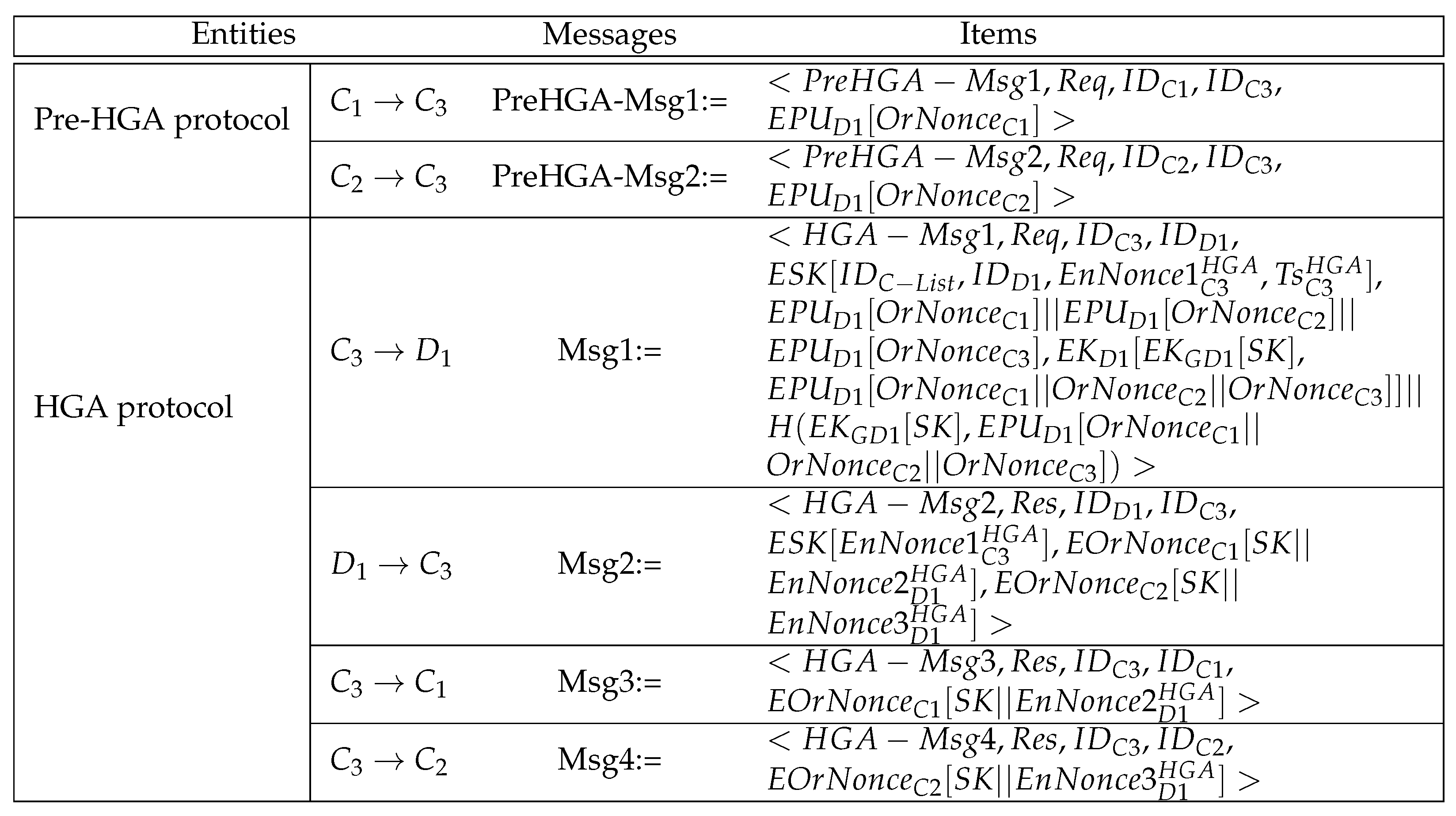
4.2.1. The Hybrid Group Authentication and Key Acquisition (HGAKA) Protocol
Messages
Operation Description
- Step1-HGAKA:
- The group leader, C3, constructs and sends , which contains a fresh timestamp and EnNonce, to the server. If no response is received within a specific amount of time, the leader resends the message or terminates the session.
- Step2-HGAKA:
- The server decrypts using to verify freshness. If fresh, the server verifies the C3 identity and then generates to construct and send to C3.
- Step3-HGAKA:
- C3 decrypts using to verify . Then, it uses as a seed to compute , where . Then, C3 sends to C2, a non-leader client.
- Step4-HGAKA:
- C2 uses the received value (i.e., ) as a seed to compute , where . , which contains , is then sent to C1, another non-leader client in the group.
- Step5-HGAKA:
- C1 uses as a seed to compute , where .
- Step6-HGAKA:
- When the last value (i.e., ) is received, C3 generatesand uses it to construct and send to the server.
- Step7-HGAKA:
- The server decrypts using to verify . Then, it verifies , and if is verified, mutual authentication is achieved between the group leader and the server. The server then generates , , n (where n is the number of clients involved), and a session key . Then, it computes an Encrypted Authorization Verification Token (where . is then sent to the group leader, C3.
- Step8-HGAKA:
- C3 decrypts using to verify . If verified, C3 obtains its OrNonce value (i.e., ) and . Then, it sends and to distribute the rest of the OrNonce values to their intended recipients. Once these messages are sent, the protocol is then terminated.
Performance Evaluation
- Communication cost
- Computation cost
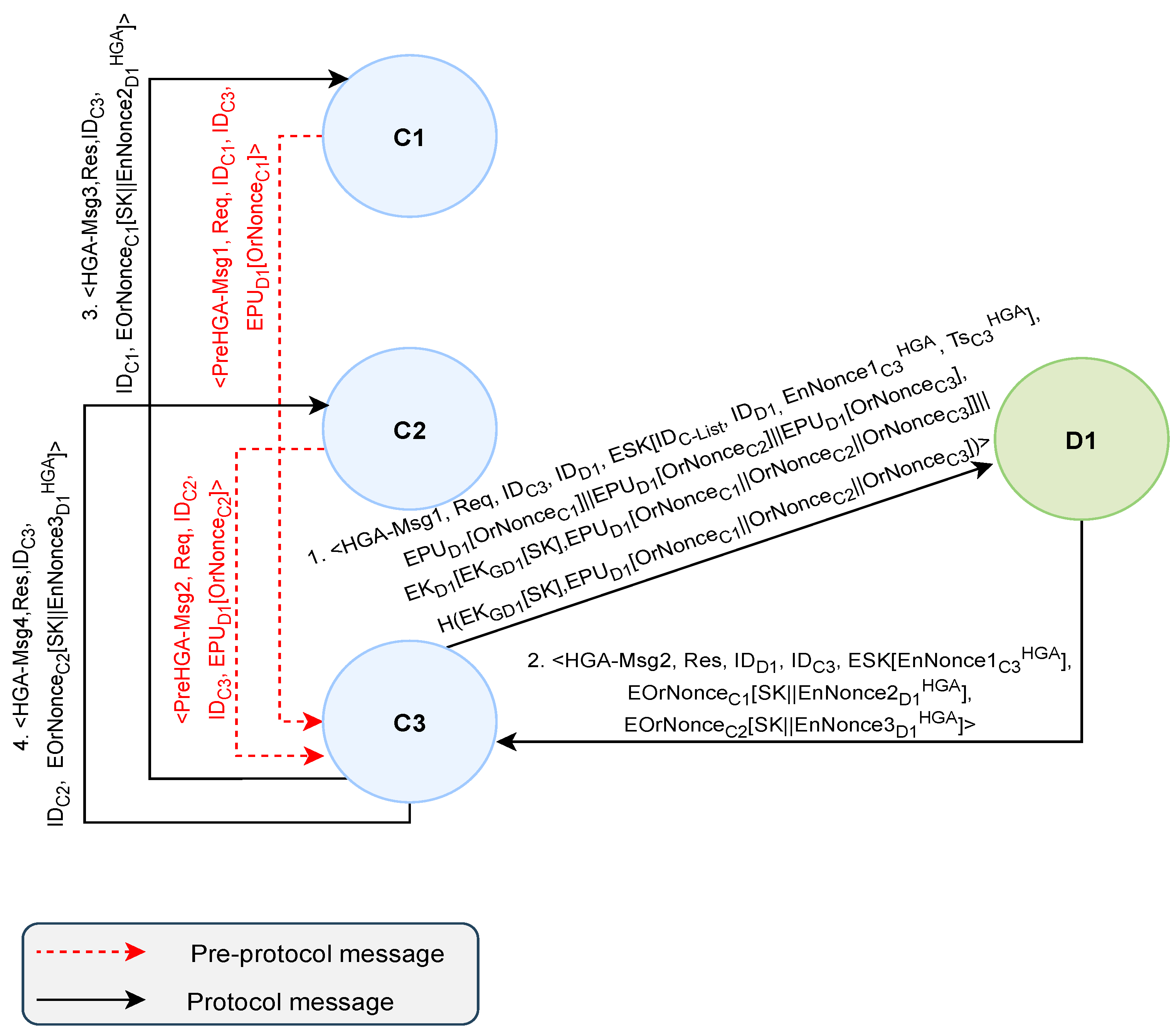
4.2.2. The Hybrid Group Access (HGA) Protocol
Messages
Operation Description
- Step1-HGA:
- Clients generate their verification tokens by encrypting their values using the target device, D1, public key (i.e., ). Once generated, each client constructs a pre-protocol message (PreHGA-Msg) and sends it to the group leader C3.
- Step2-HGA:
- Once clients’ verification tokens are all received, C3 generates its token (i.e., ) to compute the Encrypted Group Authenticator (EncGroupAuthenticator), where = . Once computed, C3 generates a fresh timestamp and EnNonce and sends to D1. If no response is received within a specific amount of time, C3 resends the message or terminates the session.
- Step3-HGA:
- D1 performs the following operations:
- It decrypts using and to obtain SK. Then, it uses SK to decrypt to verify freshness. If fresh, D1 generates a fresh value and compares it to to verify its integrity before decrypting it using its private key to obtain . This is to counter attacks since a hashing operation is much faster than RSA operations.
- If the verification is positive, D1 decrypts using to obtain , and then it computes . D1 then uses the to obtain clients’ verification tokens to compute Y, where . Then, it compares X to Y, where and to verify the integrity of the received tokens. Owing to the Homomorphic Encryption property, D1 can perform this verification without the need of accessing plaintexts of the clients’ verification tokens. If this comparison produces a positive outcome, the group authentication for D1 access is successful. As a result, D1 generates and, , and sends to achieve mutual authentication with the group leader.
- Step4-HGA:
- C3 decrypts using to verify , and upon successful verification, mutual authentication is achieved between the group leader and the target device. C3 then sends and to distribute to the clients involved. Once these messages are sent, the protocol is then terminated.
Performance Evaluation
- Communication cost
- Computation cost
4.3. The M2O Symmetric-Key-Based Protocols
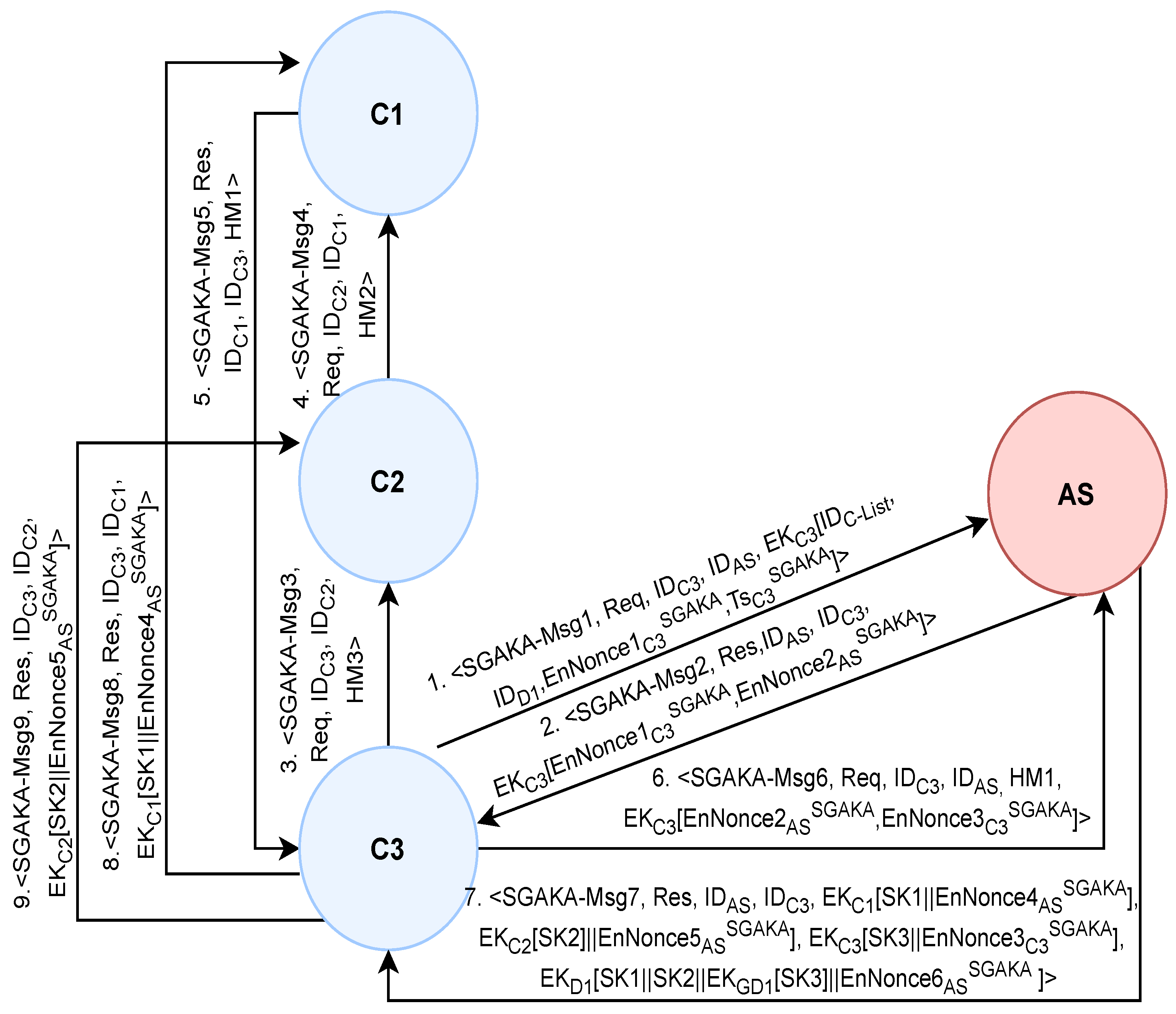
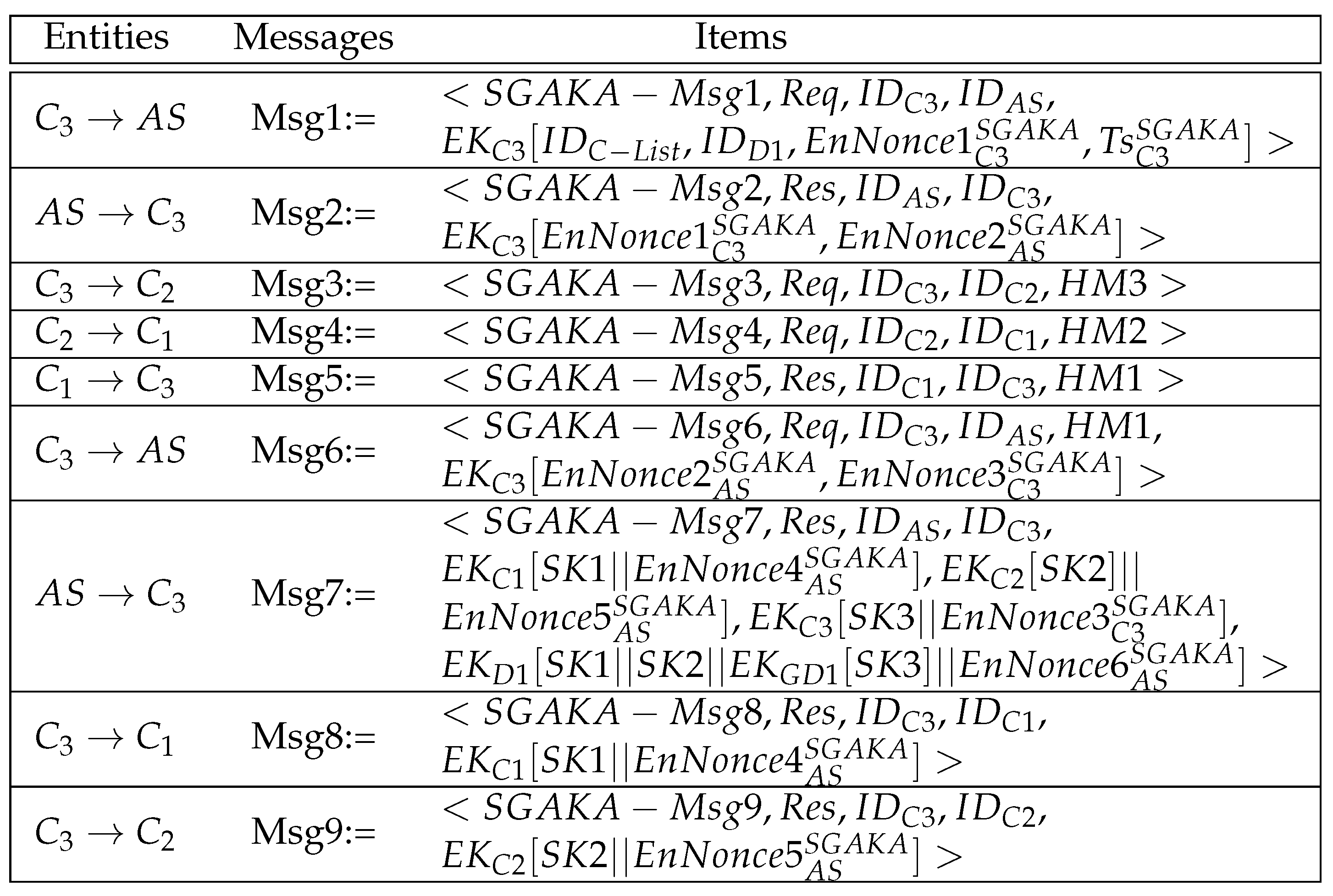
4.3.1. The Symmetric-Key-Based Group Authentication and Key Acquisition (SGAKA) Protocol
Messages
Operation Description
- Step7-SGAKA:
- The server decrypts to verify . Then, it verifies , and if is verified, the AS generates , , , n shares of the session key (i.e., , , …), and an encrypted shares token, where the . Then, it constructs and sends Msg7.
- Step8-SGAKA:
- C3 decrypts using to verify . If verified, C3 obtains its share (i.e., ). Then, it constructs and sends Msg8 and Msg9 to distribute the rest of the session key shares to their intended recipients. Once these messages are sent, the protocol is terminated.
Performance Evaluation
- Communication cost
- Computation cost
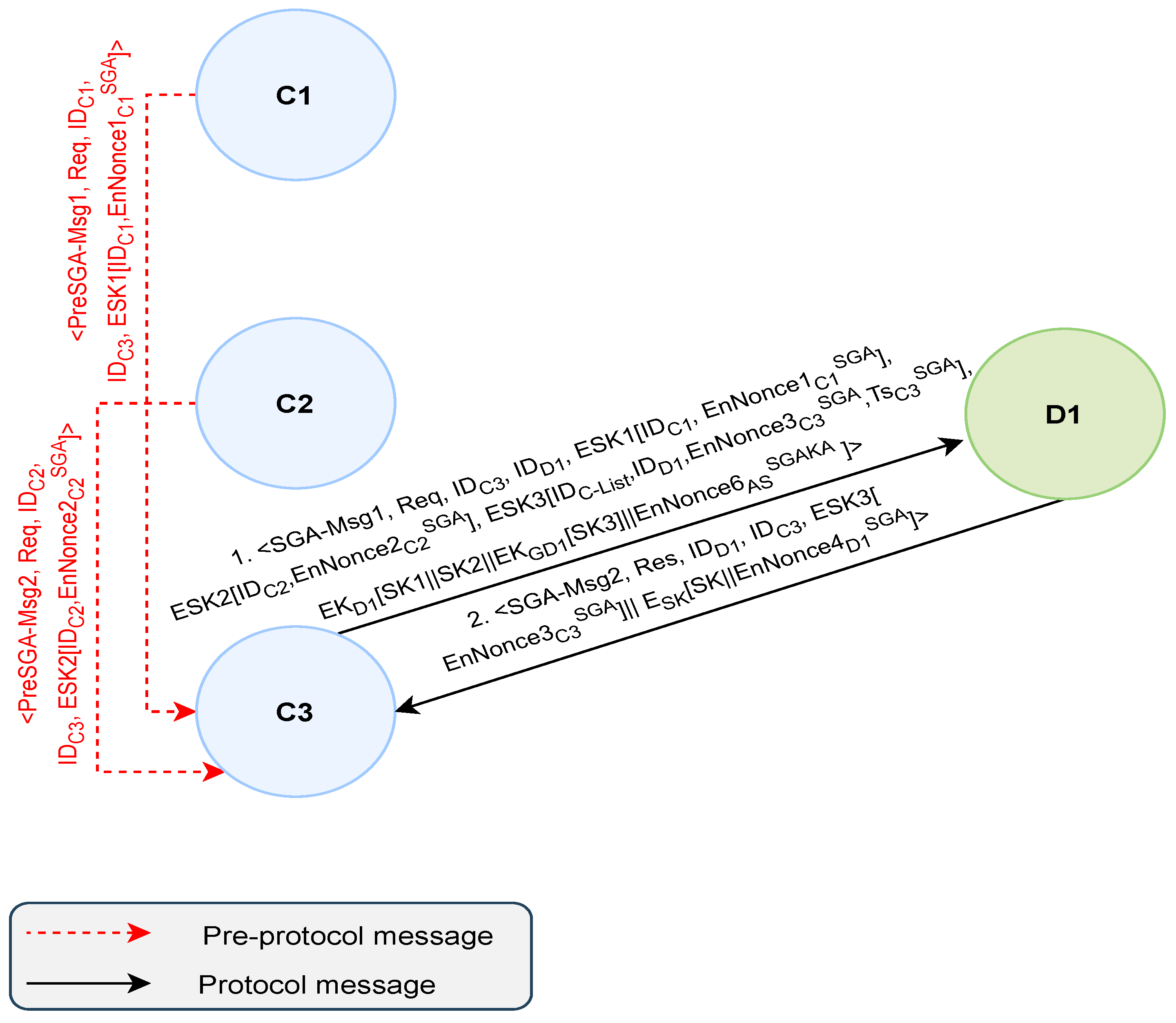
4.3.2. The Symmetric-Key-Based Group Access (SGA) Protocol
Messages
Operation Description
- Step1-SGA:
- Clients generate their verification tokens using their shares (i.e.,). Once generated, each client constructs a pre-protocol message (PreSGA-Msg) and sends it to the group leader C3.
- Step2-SGA:
- Upon the receipt of the clients’ verification tokens, C3 generates a fresh and timestamp to compute the Encrypted Group Verification Token (EncGroupVeriToken), where). Then, it constructs and sends Msg1. If no response is received within a specific amount of time, the leader resends the message or terminates the session.
- Step3-SGA:
- Upon the receipt of Msg1, D1 performs the following operations:
- It decrypts using and to obtain the session key shares. Then, it decrypts using to verify freshness.
- If fresh, D1 decrypts the clients’ verification tokens using their shares. Then, it uses these tokens with to verify their identities.
- If verified, the group authentication for D1 access is successful. Therefore, D1 computes using the session key shares. Then, it generates and sends Msg2.
- Step4-SGA:
- C3 decrypts using to verify . After verification, mutual authentication is achieved between C3 and D1. As a result, C3 collaborates with the clients involved to compute the session key. Once computed, C3 decrypts to verify the integrity of the computed SK.
Performance Evaluation
- Communication cost
- Computation cost
5. Security Analyses
5.1. Informal Analysis
5.1.1. Requirement Analysis
- R1: Mutual authentication: The challenge–response authentication method is used between a group leader and external entities, such as authentication servers or target devices, to establish mutual authentication. An invalid response results in the immediate termination of the protocol execution.
- R2: Freshness: This is verified using timestamps and random numbers.
- R3: Confidentiality: Symmetric- and asymmetric-key cryptosystems are used to protect secret message items, e.g., credentials.
- R4: Authorization: The authentication server checks the authorization status of clients involved in the GAKA protocols before issuing access credentials. Furthermore, in the HGA protocol, the target device uses the clients’ authorization tokens (i.e., ) to verify their access rights.
- R5: Availability: The protocols are designed to withstand DoS attacks. Receiving an invalid request or response will result in protocol termination, allowing the service provider to serve legitimate users.
5.1.2. Threat Analysis
- Impersonation attacks
- (i)
- Client impersonation: In the GAKA protocols, adversaries cannot compute a client value without the client’s long-term key, nor can they forge an access request without the group leader’s long-term key and the group value. In other words, forging access requests successfully requires compromising all clients. In the HGA protocol, adversaries cannot impersonate a client without knowing the client’s authorization nonce () value or forge access requests without compromising the , , and . Lastly, adversaries cannot impersonate a client in the SGA protocol without the client’s session key share or forge a successful device access request without knowing the session key shares of all clients involved and the . As a result, the protocols can withstand client impersonation attacks.
- (ii)
- Authentication server impersonation: It is not possible to impersonate the authentication server without compromising the group leader’s long-term key.
- (iii)
- Target impersonation: Adversaries cannot impersonate a target device without compromising at least two keys, e.g., the session key and the target’s private key (), in the HGA protocol. As for the SGA protocol, they will not be able to impersonate the target device without either its long-term key and group key, or its long-term key and the session key shares of all clients involved. Thus, the protocols are also resilient to target impersonation.
- Eavesdropping: As secret message components (e.g., authentication information) are always encrypted, intercepted messages cannot be used to compromise authentication.
- Replay: Replayed messages can be detected as all protocols use a combination of random numbers and timestamps to provide message freshness.
- Denial of service: An adversary cannot forge legitimate access requests to occupy clients, target devices, or the authentication server without compromising the keys involved. As a result, illegitimate access requests and messages are discarded in all protocols.
5.2. Work Factor Evaluation
5.3. Formal Security Verification
6. Performance Analysis and Comparison Study
7. Experimental Evaluation
7.1. Cryptographic Algorithms
- The AES-CBC-128 algorithm is used for symmetric encryption and decryption.
- The RSA-3072 algorithm is used for asymmetric encryption and decryption.
- The SHA-256 algorithm is utilized to compute hash values.
- The HMAC-SHA256 algorithm is used to generate HMAC values.
7.2. Experimental Setup and Iteration Count
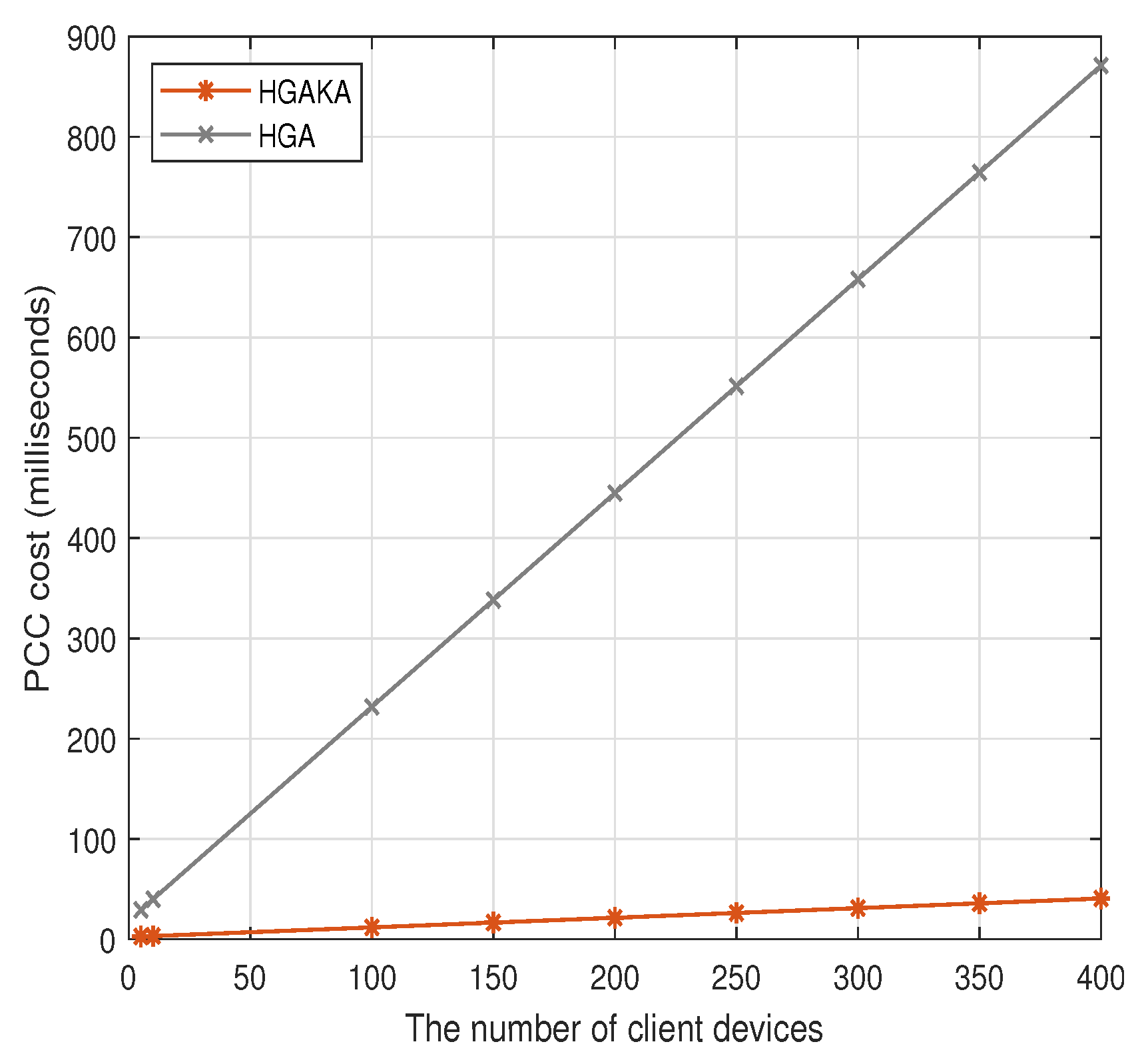
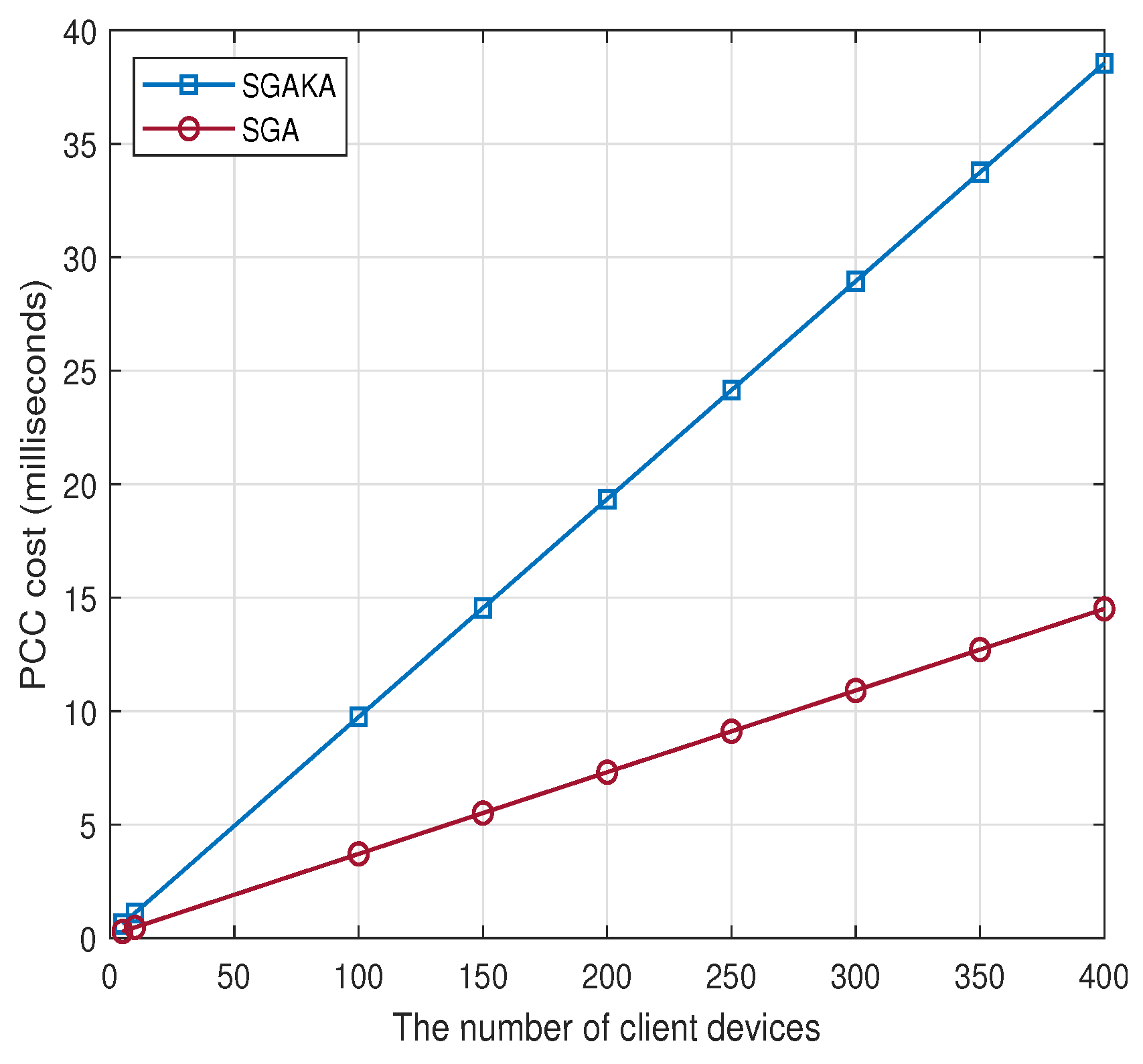
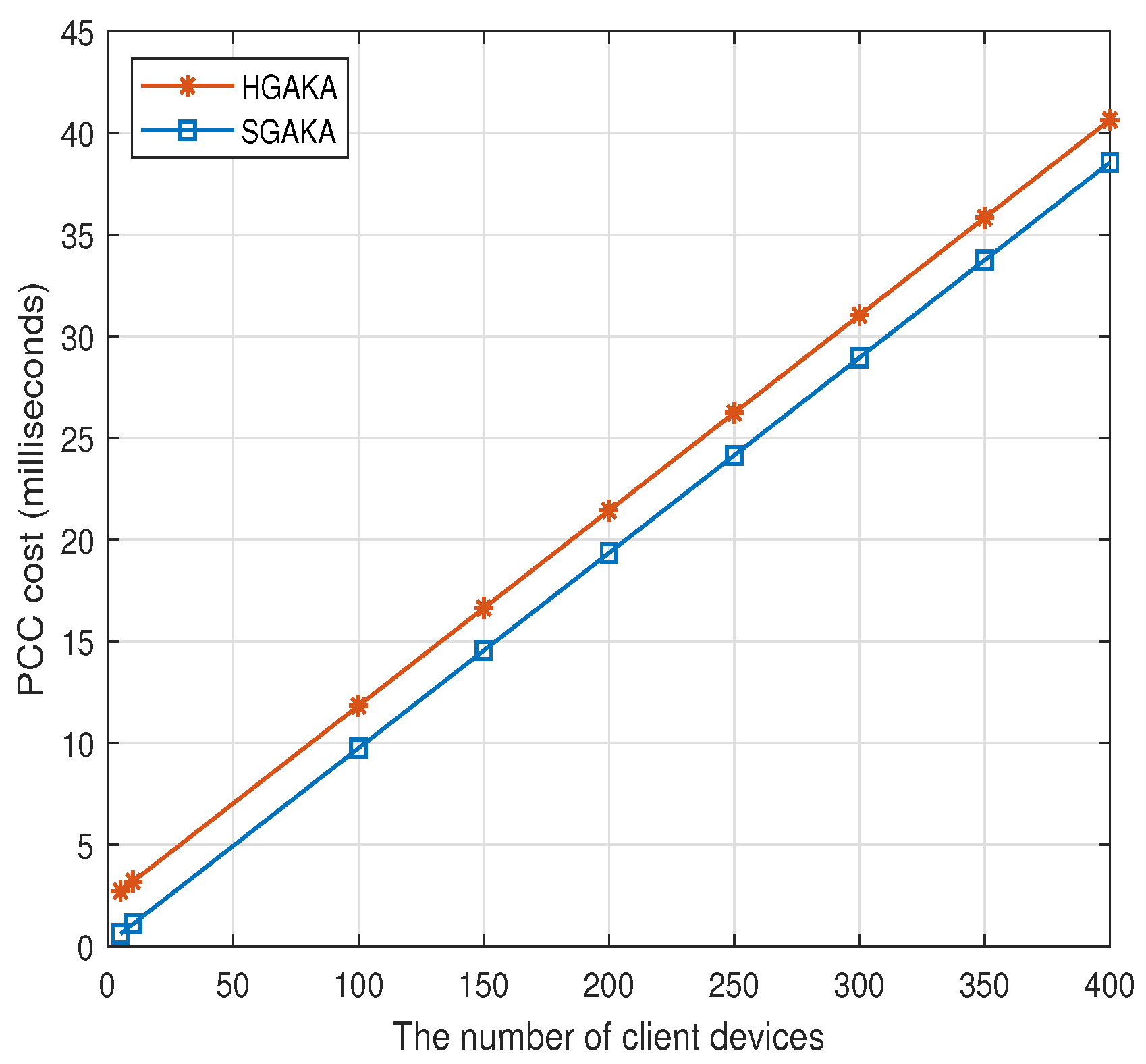
7.3. Experiment Results
8. The M2O Protocols Versus a Benchmark Solution
8.1. Kerberos
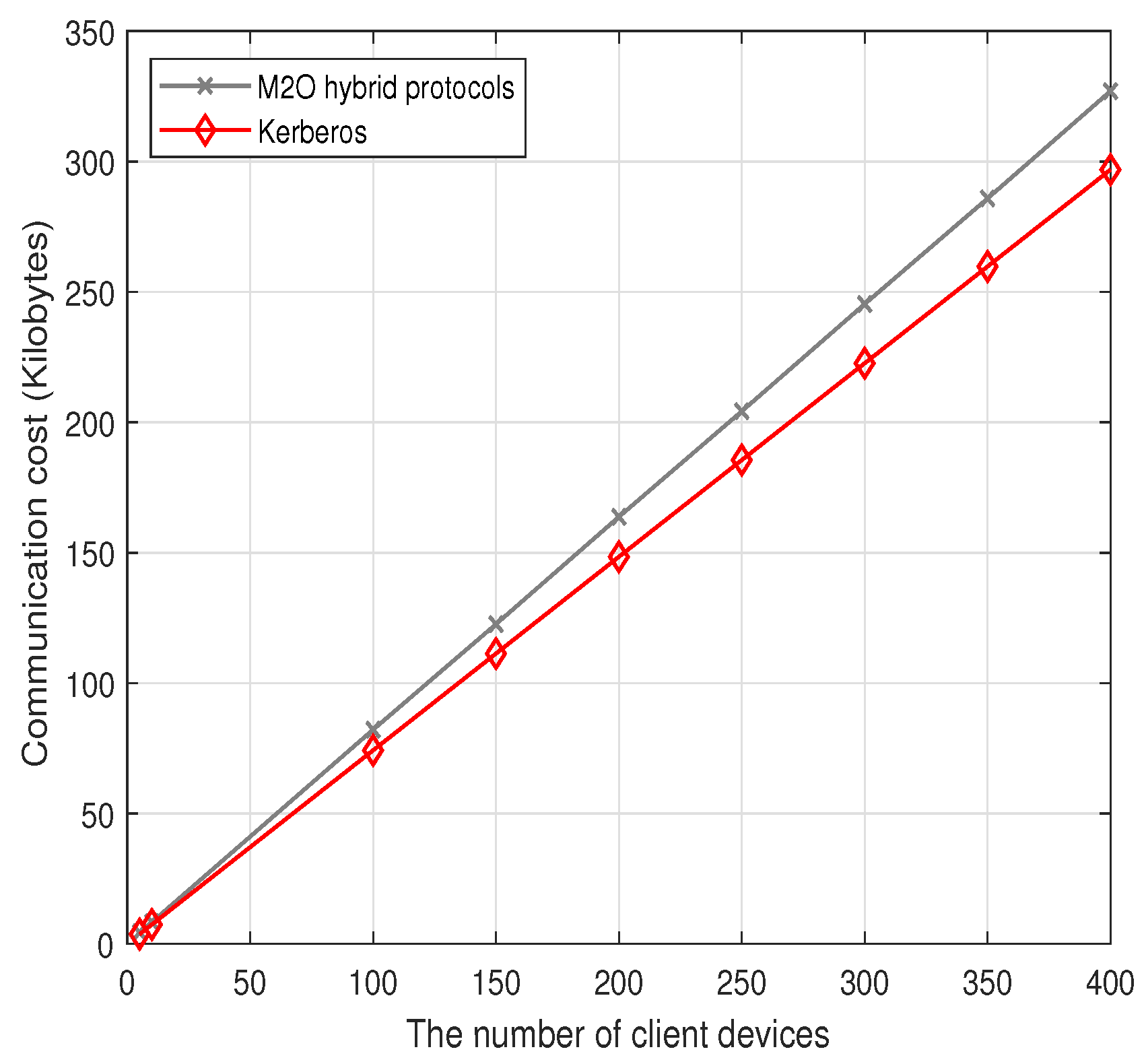
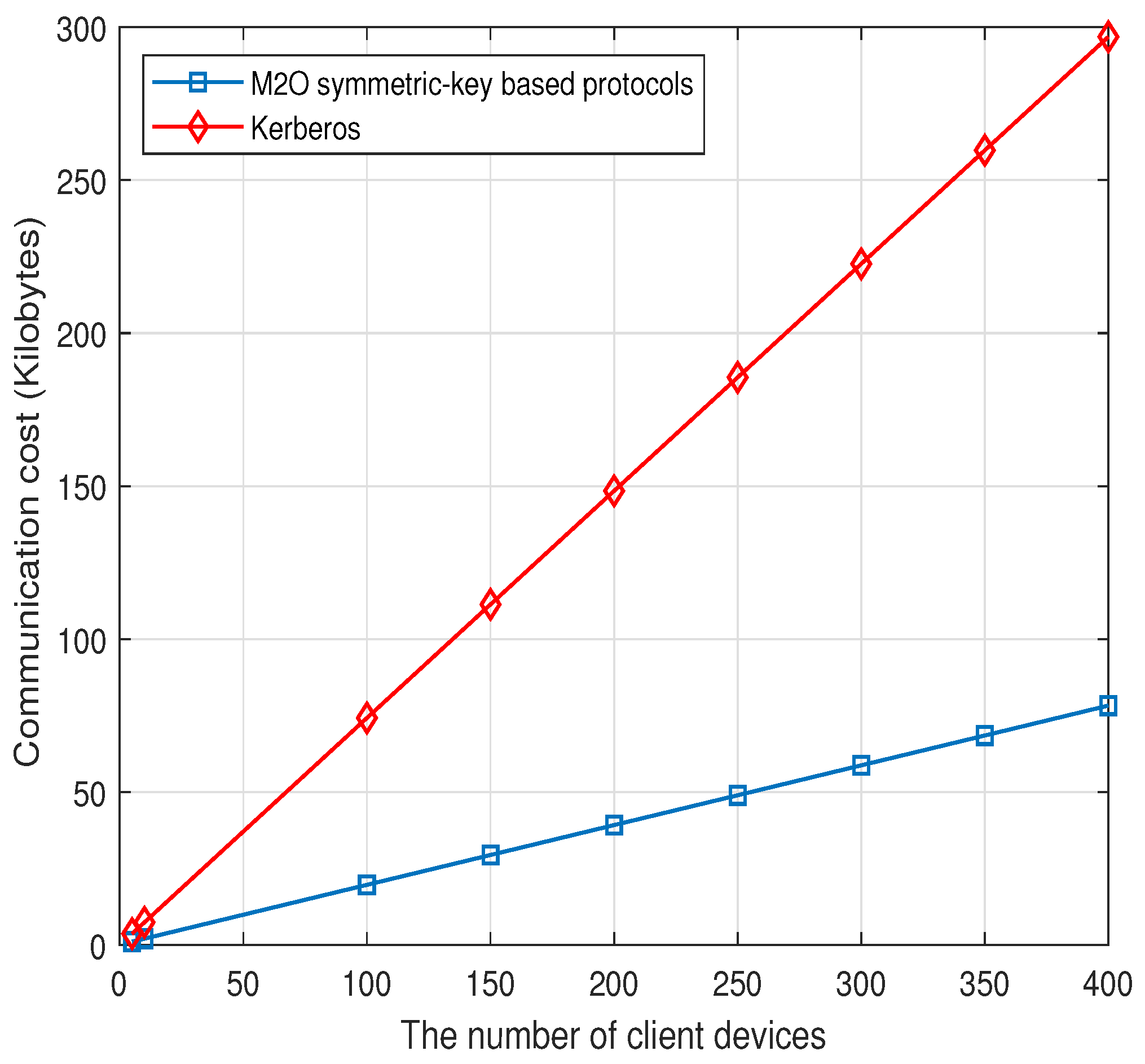
8.2. Communication Costs
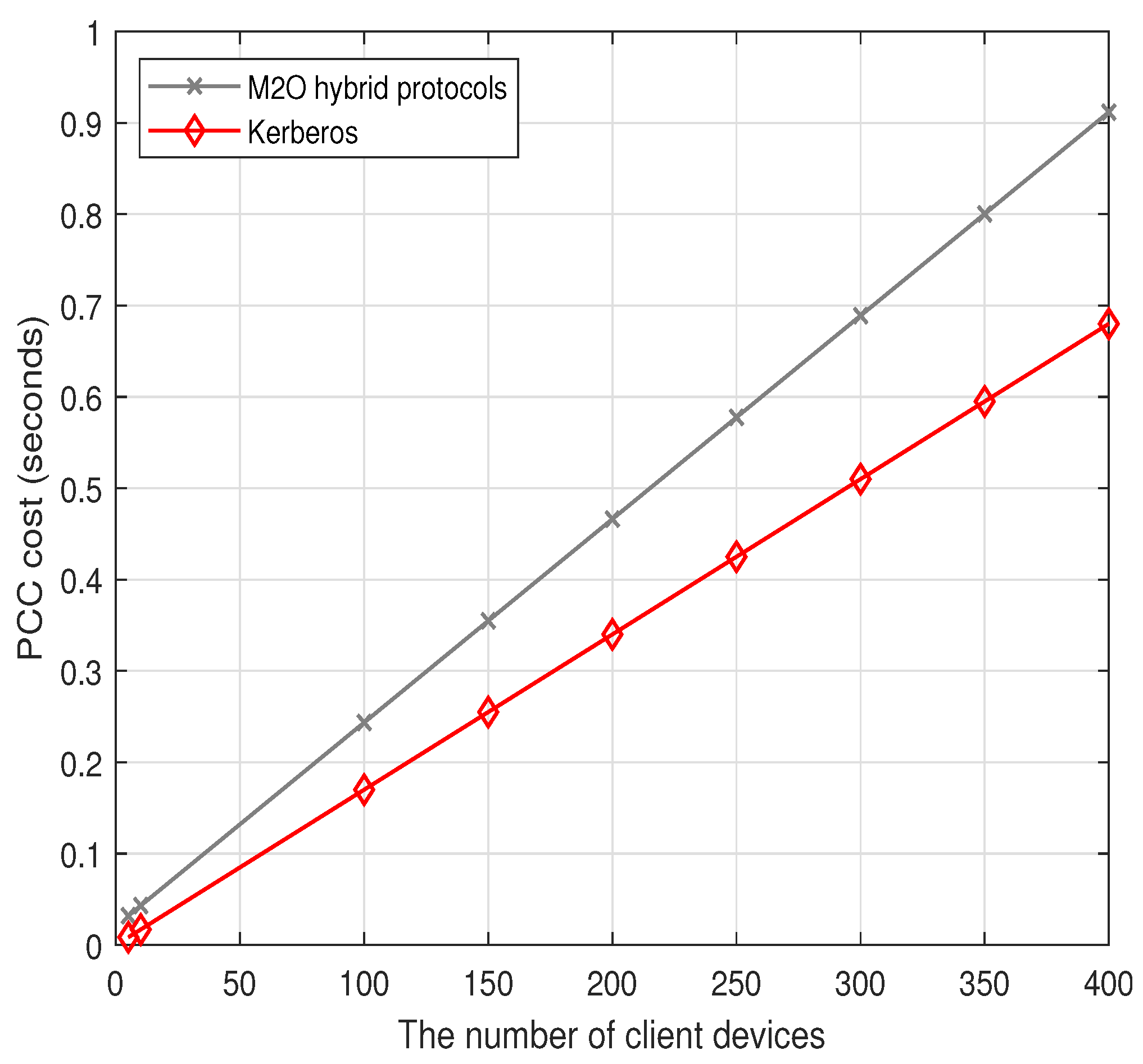
8.3. Computation Costs
9. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Notations
| encryption with key ; | |
| nonce used for verification; | |
| client device x identity; | |
| target device x identity; | |
| client device x symmetric key; | |
| target device x symmetric key; | |
| shared key used by the authentication server and devices in group ; | |
| message size is a multiple of S bits; | |
| number of clients; | |
| nonce used for authorization; | |
| target device x private key; | |
| target device x public key; | |
| execution time of asymmetric encryption; | |
| execution time of asymmetric decryption; | |
| execution time of symmetric encryption/decryption; | |
| execution time of symmetric encryption in Kerberos; | |
| execution time of symmetric decryption in Kerberos; | |
| time to generate a hashed message authentication code; | |
| time to generate a message digest; | |
| time to generate a random number; | |
| execution time of Chebyshev mapping; | |
| execution time of multiplication over elliptic curve; | |
| execution time of a modulus operation; | |
| execution time of a bitwise exclusive OR (XOR) operation; | |
| current time; | |
| Kerberos time settings; | |
| timestamp; | |
| time window for the allowable transmission delay. |
References
- Gulati, K.; Boddu, R.S.K.; Kapila, D.; Bangare, S.L.; Chnani, N.; Saravanan, G. A Review Paper on Wireless Sensor Network Techniques in Internet of Things (IoT). Mater. Today 2022, 51, 161–165. [Google Scholar] [CrossRef]
- Rani, J.; Dhingra, A.; Sindhu, V. A Detailed Review of the IoT with Detection of Sinkhole Attacks in RPL based Network. In Proceedings of the 2022 IEEE International Conference on Communication, Computing and Internet of Things (IC3IoT), Chennai, India, 10–11 March 2022. [Google Scholar]
- Sharma, V.; Tripathi, A.K. A Systematic Review of Meta-Heuristic Algorithms in IoT based Application. Array 2022, 14, 100164. [Google Scholar] [CrossRef]
- Tay, S.W.; Zhang, N.; AlJanah, S. A Problem Analysis of Smart Home Automation: Toward Secure and Usable Communication-Based Authorization. IEEE Access 2024, 12, 18103–18121. [Google Scholar] [CrossRef]
- AlJanah, S. An Interaction based Multi-Factor Multi-Level Authentication Framework for IoT Environments. Ph.D. Dissertation, The University of Manchester, Manchester, UK, 2022. [Google Scholar]
- Tewari, A.; Gupta, B.B. Cryptanalysis of a Novel Ultra-Lightweight Mutual Authentication Protocol for IoT Devices Using RFID Tags. J. Supercomput. 2017, 73, 1085–1102. [Google Scholar] [CrossRef]
- Fan, K.; Song, P.; Yang, Y. ULMAP: Ultralightweight NFC Mutual Authentication Protocol with Pseudonyms in the Tag for IoT in 5G. Mob. Inf. Syst. 2017, 2017, 2349149. [Google Scholar] [CrossRef]
- Ovilla-Martinez, B.; Bossuet, L. Restoration Protocol: Lightweight and Secure Devices Authentication based on PUF. In Proceedings of the 2017 IFIP/IEEE International Conference on Very Large Scale Integration (VLSI-SoC), Abu Dhabi, United Arab Emirates, 23–25 October 2017. [Google Scholar]
- Gu, C.; Chang, C.H.; Liu, W.; Yu, S.; Wang, Y.; O’Neill, M. A Modeling Attack Resistant Deception Technique for Securing Lightweight-PUF based Authentication. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2020, 40, 1183–1196. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. A Robust and Anonymous Patient Monitoring System Using Wireless Medical Sensor Networks. Future Gener. Comput. Syst. 2018, 80, 483–495. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Sangaiah, A.K.; Xu, L.; Kumari, S.; Wu, L.; Shen, J. A Lightweight and Robust Two-Factor Authentication Scheme for Personalized Healthcare Systems Using Wireless Medical Sensor Networks. Future Gener. Comput. Syst. 2018, 82, 727–737. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Vasilakos, A.V. Authenticated Key Management Protocol for Cloud-Assisted Body Area Sensor Networks. J. Netw. Comput. Appl. 2018, 123, 112–126. [Google Scholar] [CrossRef]
- Fotouhi, M.; Bayat, M.; Das, A.K.; Far, H.A.; Pournaghi, S.M.; Doostari, M.A. A Lightweight and Secure Two-Factor Authentication Scheme for Wireless Body Area Networks in Health-Care IoT. Comput. Netw. 2020, 177, 107333. [Google Scholar] [CrossRef]
- Liu, Z.; Guo, C.; Wang, B. A Physically Secure, Lightweight Three-Factor and Anonymous User Authentication Protocol for IoT. IEEE Access 2020, 8, 195914–195928. [Google Scholar] [CrossRef]
- Gope, P.; Amin, R.; Islam, S.H.; Kumar, N.; Bhalla, V.K. Lightweight and Privacy-Preserving RFID Authentication Scheme for Distributed IoT Infrastructure with Secure Localization Services for Smart City Environment. Future Gener. Comput. Syst. 2018, 83, 629–637. [Google Scholar] [CrossRef]
- Lara, E.; Aguilar, L.; Sanchez, M.A.; García, J.A. Lightweight Authentication Protocol for M2M Communications of Resource-Constrained Devices in Industrial Internet of Things. Sensors 2020, 20, 501. [Google Scholar] [CrossRef] [PubMed]
- Mahalat, M.H.; Saha, S.; Mondal, A.; Sen, B. A PUF based Light Weight Protocol For Secure WiFi Authentication of IoT Devices. In Proceedings of the 8th IEEE International Symposium on Embedded Computing and System Design (ISED), Cochin, India, 13–15 December 2018. [Google Scholar]
- Roy, S.; Das, D.; Mondal, A.; Mahalat, M.H.; Roy, S.; Sen, B. PUF Based Lightweight Authentication and Key Exchange Protocol for IoT. In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), Online, 6–8 July 2021. [Google Scholar]
- Roy, S.; Das, D.; Mondal, A.; Mahalat, M.H.; Sen, B.; Sikdar, B. PLAKE: PUF Based Secure Lightweight Authentication and Key Exchange Protocol for IoT. IEEE Internet Things J. 2022, 10, 8547–8559. [Google Scholar] [CrossRef]
- Roy, S.; Das, D.; Sen, B. Secure and Lightweight Authentication Protocol Using PUF for the IoT-Based Wireless Sensor Network. ACM J. Emerg. Technol. Comput. Syst. 2023, 20, 1–17. [Google Scholar] [CrossRef]
- Liang, W.; Xie, S.; Long, J.; Li, K.C.; Zhang, D.; Li, K. A Double PUF-Based RFID Identity Authentication Protocol in Service-Centric Internet of Things Environments. Inf. Sci. 2019, 503, 129–147. [Google Scholar] [CrossRef]
- Fan, K.; Luo, Q.; Zhang, K.; Yang, Y. Cloud-Based Lightweight Secure RFID Mutual Authentication Protocol in IoT. Inf. Sci. 2020, 527, 329–340. [Google Scholar] [CrossRef]
- Lai, C.; Lu, R.; Zheng, D.; Li, H.; Shen, X.S. GLARM: Group-Based Lightweight Authentication Scheme for Resource-Constrained Machine to Machine Communications. Comput. Netw. 2016, 99, 66–81. [Google Scholar] [CrossRef]
- Modiri, M.; Mohajeri, J.; Salmasizadeh, M. A Novel Group-Based Secure Lightweight Authentication and Key Agreement Protocol for Machine-Type Communication. Sci. Iran. 2021, 29, 3273–3287. [Google Scholar]
- Chen, Y.; López, L.; Martínez, J.F.; Castillejo, P. A Lightweight Privacy Protection User Authentication and Key Agreement Scheme Tailored for the Internet of Things Environment: LightPriAuth. J. Sens. 2018, 2018, 7574238. [Google Scholar] [CrossRef]
- Nikravan, M.; Reza, A. A Multi-Factor User Authentication and Key Agreement Protocol Based on Bilinear Pairing for the Internet of Things. Wirel. Pers. Commun. 2020, 111, 463–494. [Google Scholar] [CrossRef]
- Chatterjee, U.; Chakraborty, R.S.; Mukhopadhyay, D. A PUF-Based Secure Communication Protocol for IoT. ACM Trans. Embed. Comput. Syst. (TECS) 2017, 16, 1–25. [Google Scholar] [CrossRef]
- Braeken, A. PUF Based Authentication Protocol for IoT. Symmetry 2018, 10, 352. [Google Scholar] [CrossRef]
- Naeem, M.; Chaudhry, S.A.; Mahmood, K.; Karuppiah, M.; Kumari, S. A Scalable and Secure RFID Mutual Authentication Protocol Using ECC for Internet of Things. Int. J. Commun. Syst. 2020, 33, e3906. [Google Scholar] [CrossRef]
- Izza, S.; Benssalah, M.; Drouiche, K. An Enhanced Scalable and Secure RFID Authentication Protocol for WBAN within an IoT Environment. J. Inf. Secur. Appl. 2021, 58, 102705. [Google Scholar] [CrossRef]
- Shen, J.; Chang, S.; Shen, J.; Liu, Q.; Sun, X. A Lightweight Multi-Layer Authentication Protocol for Wireless Body Area Networks. Future Gener. Comput. Syst. 2018, 78, 956–963. [Google Scholar] [CrossRef]
- Liu, X.; Jin, C.; Li, F. An Improved Two-Layer Authentication Scheme for Wireless Body Area Networks. J. Med. Syst. 2018, 42, 143. [Google Scholar] [CrossRef]
- AlJanah, S.; Zhang, N.; Tay, S.W. A Survey on Smart Home Authentication: Toward Secure, Multi-Level And Interaction-Based Identification. IEEE Access 2021, 9, 130914–130927. [Google Scholar] [CrossRef]
- AlJanah, S.; Zhang, N.; Tay, S. A Multifactor Multilevel and Interaction Based (M2I) Authentication Framework for Internet of Things (IoT) Applications. IEEE Access 2022, 10, 47965–47996. [Google Scholar] [CrossRef]
- Chuang, Y.H.; Lo, N.W.; Yang, C.Y.; Tang, S.W. A Lightweight Continuous Authentication Protocol for the Internet of Things. Sensors 2018, 18, 1104. [Google Scholar] [CrossRef]
- Shah, S.W.; Syed, N.F.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. LCDA: Lightweight Continuous Device-to-Device Authentication for a Zero Trust Architecture (ZTA). Comput. Secur. 2021, 108, 102351. [Google Scholar] [CrossRef]
- Adeli, M.; Bagheri, N.; Sadeghi, S.; Kumari, S. χPERBP: A Cloud-Based Lightweight Mutual Authentication Protocol. Cryptol. ePrint Arch. 2021, 16, 1785–1802. [Google Scholar]
- Barker, E.; Chen, L.; Roginsky, A.; Vassilev, A.; Davis, R. Recommendation for Pair-Wise-Key Establishment Schemes Using Discrete Logarithm Cryptography. National Institute of Standards and Technology (NIST). 2018. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-56Ar3.pdf (accessed on 1 February 2025).
- Yıldız, H.; Cenk, M.; Onur, E. PLGAKD: A PUF-Based Lightweight Group Authentication and Key Distribution Protocol. IEEE Internet Things J. 2021, 8, 5682–5696. [Google Scholar] [CrossRef]
- Chien, H.Y. Group Authentication with Multiple Trials and Multiple Authentications. Secur. Commun. Netw. 2017, 2017, 3109624. [Google Scholar] [CrossRef]
- Aydin, Y.; Kurt, G.K.; Ozdemir, E.; Yanikomeroglu, H. A Flexible and Lightweight Group Authentication Scheme. IEEE Internet Things J. 2020, 7, 10277–10287. [Google Scholar] [CrossRef]
- Xu, R.; Wang, X.; Morozov, K. Group Authentication for Cloud-to-Things Computing: Review and Improvement. Comput. Netw. 2021, 198, 108374. [Google Scholar] [CrossRef]
- Xia, Z.; Liu, Y.; Hsu, C.F.; Chang, C.C. Cryptanalysis and Improvement of a Group Authentication Scheme with Multiple Trials and Multiple Authentications. Secur. Commun. Netw. 2020, 2020, 6183861. [Google Scholar] [CrossRef]
- Shamir, A. How to Share a Secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Jiang, R.; Lai, C.; Luo, J.; Wang, X.; Wang, H. EAP-Based Group Authentication and Key Agreement Protocol for Machine-Type Communications. Int. J. Distrib. Sens. Netw. 2013, 9, 304601. [Google Scholar] [CrossRef]
- Mobarhan, M.A.; Salamah, M. REPS-AKA3: A Secure Authentication and Re-authentication Protocol for LTE Networks. J. Netw. Comput. Appl. 2022, 9, 304601. [Google Scholar] [CrossRef]
- Choi, D.; Choi, H.K.; Lee, S.Y. A Group-Based Security Protocol for Machine-Type Communications in LTE-Advanced. Wirel. Netw. 2015, 21, 405–419. [Google Scholar] [CrossRef]
- Ashkejanpahlouie, F.K.; Talouki, M.A.; Ghahfarokhi, B.S. A Secure Group-Based Authentication Protocol for Machine-Type Communication in LTE/LTE-A Networks. In Proceedings of the ACM International Conference on Smart Cities and Internet of Things, Mashhad, Iran, 26–27 September 2018. [Google Scholar]
- Fu, A.; Song, J.; Li, S.; Zhang, G.; Zhang, Y. A Privacy-Preserving Group Authentication Protocol for Machine-Type Communication in LTE/LTE-A Networks. Secur. Commun. Netw. 2016, 9, 2002–2014. [Google Scholar] [CrossRef]
- Parne, B.L.; Gupta, S.; Chaudhari, N.S. SEGB: Security Enhanced Group Based AKA Protocol for M2M Communication in an IoT Enabled LTE/LTE-A Network. IEEE Access 2018, 6, 3668–3684. [Google Scholar] [CrossRef]
- Singh, G.; Shrimankar, D.D. Dynamic Group Based Efficient Access Authentication and Key Agreement Protocol for MTC in LTE-A Networks. Wirel. Pers. Commun. 2018, 101, 829–856. [Google Scholar] [CrossRef]
- Gupta, S.; Pradhan, A.K.; Chaudhari, N.S.; Singh, A. LS-AKA: A Lightweight and Secure Authentication and Key Agreement Scheme for Enhanced Machine Type Communication Devices in 5G Smart Environment. Sustain. Energy Technol. Assess. 2023, 60, 103448. [Google Scholar] [CrossRef]
- Ouaissa, M.; Houmer, M.; Ouaissa, M. An Enhanced Authentication Protocol Based Group for Vehicular Communications over 5G Networks. In Proceedings of the 3rd IEEE International Conference on Advanced Communication Technologies and Networking (CommNet), Marrakech, Morocco, 4–6 September 2020. [Google Scholar]
- Gharsallah, I.; Smaoui, S.; Zarai, F. An Efficient Authentication and Key Agreement Protocol for a Group of Vehicles Devices in 5G Cellular Networks. IET Inf. Secur. 2020, 14, 21–29. [Google Scholar] [CrossRef]
- Miao, J.; Wang, Z.; Miao, X.; Xing, L. A Secure and Efficient Lightweight Vehicle Group Authentication Protocol in 5G Networks. Wirel. Commun. Mob. Comput. 2021, 2021, 4079092. [Google Scholar] [CrossRef]
- Security Architecture and Procedures for 5G System, 3GPP. The European Telecommunications Standards Institute (ETSI) Publication 15.4.0 Release 15. 2019. Available online: https://www.etsi.org/deliver/etsi_ts/133500_133599/133501/15.04.00_60/ts_133501v150400p.pdf (accessed on 1 January 2025).
- Singh, G. GBEAKA: Group-Based Efficient Authentication and Key Agreement Protocol for LPIoMT Using 5G. Internet Things 2023, 22, 100688. [Google Scholar] [CrossRef]
- Zhang, S.; Lee, J.H. A Group Signature and Authentication Scheme for Blockchain-Based Mobile-Edge Computing. IEEE Internet Things J. 2019, 7, 4557–4565. [Google Scholar] [CrossRef]
- Khalid, U.; Asim, M.; Baker, T.; Hung, P.C.; Tariq, M.A.; Rafferty, L. A Decentralized Lightweight Blockchain-Based Authentication Mechanism for IoT Systems. Clust. Comput. 2020, 23, 2067–2087. [Google Scholar] [CrossRef]
- Kumar, R.; Sharma, R. Leveraging Blockchain for Ensuring Trust in IoT: A Survey. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 8599–8622. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Park, Y. Blockchain-Envisioned Secure Authentication Approach in AIoT: Applications, Challenges, and Future Research. Wirel. Commun. Mob. Comput. 2021, 2021, 3866006. [Google Scholar] [CrossRef]
- Ren, W.; Tong, X.; Du, J.; Wang, N.; Li, S.C.; Min, G.; Zhao, Z.; Bashir, A.K. Privacy-Preserving Using Homomorphic Encryption in Mobile IoT Systems. Comput. Commun. 2021, 165, 105–111. [Google Scholar] [CrossRef]
- Li, S.; Zhao, S.; Min, G.; Qi, L.; Liu, G. Lightweight Privacy-Preserving Scheme using Homomorphic Encryption in Industrial Internet of Things. IEEE Internet Things J. 2021, 9, 14542–14550. [Google Scholar] [CrossRef]
- Sadi, M. Homomorphic Encryption. In Emerging Topics in Hardware Security; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Acar, A.; Aksu, H.; Uluagac, A.S.; Conti, M. A Survey on Homomorphic Encryption Schemes: Theory and Implementation. ACM Comput. Surv. 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Gabriel, B. A Multi-Level Access Control Framework for Data Access in a Healthcare Cloud; The University of Manchester: Manchester, UK, 2018. [Google Scholar]
- Lambers, J.; Mooney, A.; Montiforte, V. Explorations in Numerical Analysis: Python Edition; World Scientific Publishing Company: Hackensack, NJ, USA, 2021. [Google Scholar]
- Dammak, M.; Boudia, O.R.M.; Messous, M.A.; Senouci, S.M.; Gransart, C. Token-Based Lightweight Authentication to Secure IoT Networks. In Proceedings of the 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019. [Google Scholar]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of Secure User Authenticated Key Management Protocol for Generic IoT Networks. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Zhang, Q.; Ding, Q. Digital Image Encryption Based on Advanced Encryption Standard (AES). In Proceedings of the Fifth IEEE International Conference on Instrumentation and Measurement, Computer, Communication and Control (IMCCC), Qinhuangdao, China, 18–20 September 2015. [Google Scholar]
- Mohamed, K.S. New Frontiers in Cryptography: Quantum, Blockchain, Lightweight, Chaotic and DNA; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Moriarty, K.; Kaliski, B.; Jonsson, J.; Rusch, A. PKCS# 1: RSA Cryptography Specifications Version 2.2; Internet Engineering Task Force: Wilmington, DE, USA, 2016. [Google Scholar]
- Chapple, M.; Stewart, J.M.; Gibson, D. (ISC) 2 CISSP Certified Information Systems Security Professional Official Study Guide; John Wiley & Sons: Hoboken, NJ, USA, 2018. [Google Scholar]
- Barker, E. Recommendation for Key Management. National Institute of Standards and Technology (NIST) Special Publication 800-57. 2020. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-57pt1r5.pdf (accessed on 1 March 2025).
- Belfaik, Y.; Lotfi, Y.; Sadqi, Y.; Safi, S. A Comparative Study of Protocols Security Verification Tools: Avispa, Scyther, ProVerif, and Tamarin; Springer: Berlin/Heidelberg, Germany, 2024. [Google Scholar]
- Han, K.; Ma, M.; Li, X.; Feng, Z.; Hao, J. An Efficient Handover Authentication Mechanism for 5G Wireless Network. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019. [Google Scholar]
- Singh, M.; Ranganathan, M. NIST Technical Note 2123: Formal Verification of Bootstrapping Remote Secure Key Infrastructures (BRSKI) Protocol Using AVISPA; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2020.
- Mahmoud, D.F.; Moussa, S.M.; Badr, N.L. The Spatiotemporal Data Reduction (STDR): An Adaptive IoT-Based Data Reduction Approach. In Proceedings of the IEEE International Conference on Intelligent Computing and Information Systems (ICICIS), Cairo, Egypt, 5–7 December 2021. [Google Scholar]
- Qiu, J.; Tian, Z.; Du, C.; Zuo, Q.; Su, S.; Fang, B. A Survey on Access Control in the Age of Internet of Things. IEEE Internet Things J. 2020, 7, 4682–4696. [Google Scholar] [CrossRef]
- Saqib, M.; Moon, A.H. A Systematic Security Assessment and Review of Internet of Things in the Context of Authentication. Comput. Secur. 2023, 125, 103053. [Google Scholar] [CrossRef]
- Sönmez Turan, M.; McKay, K.; Chang, D.; Kang, J.; Kelsey, J. Ascon-Based Lightweight Cryptography Standards for Constrained Devices. National Institute of Standards and Technology (NIST). 2024. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-232.ipd.pdf (accessed on 1 March 2025).
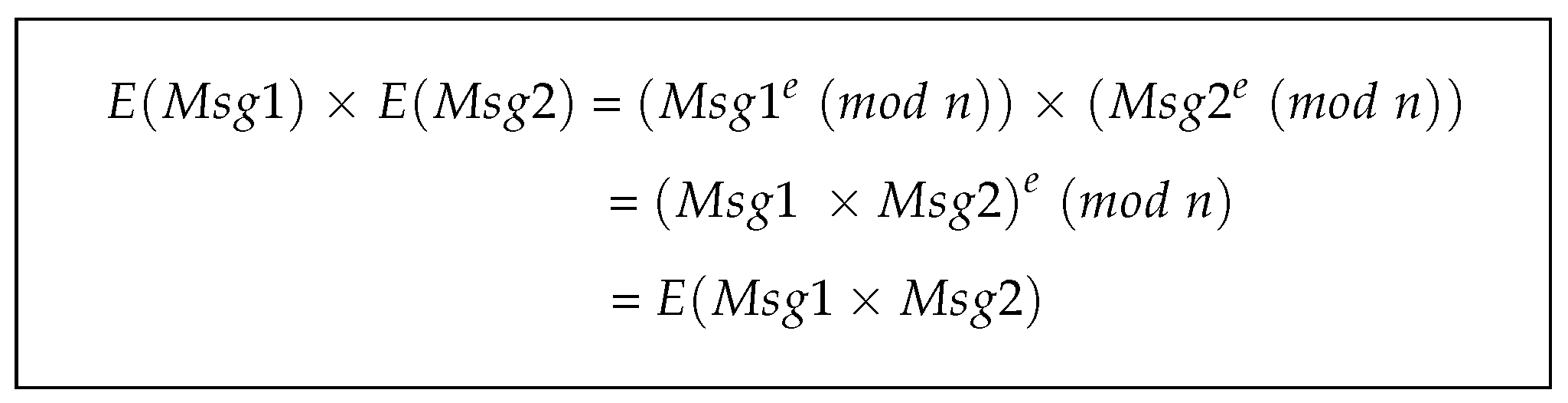
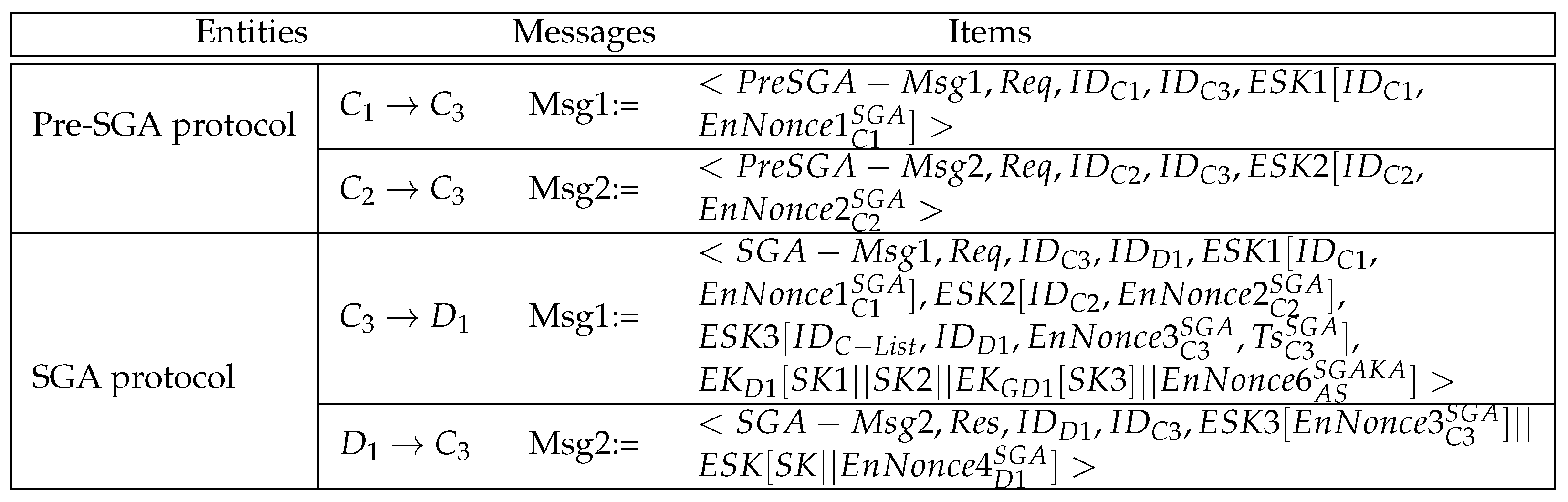
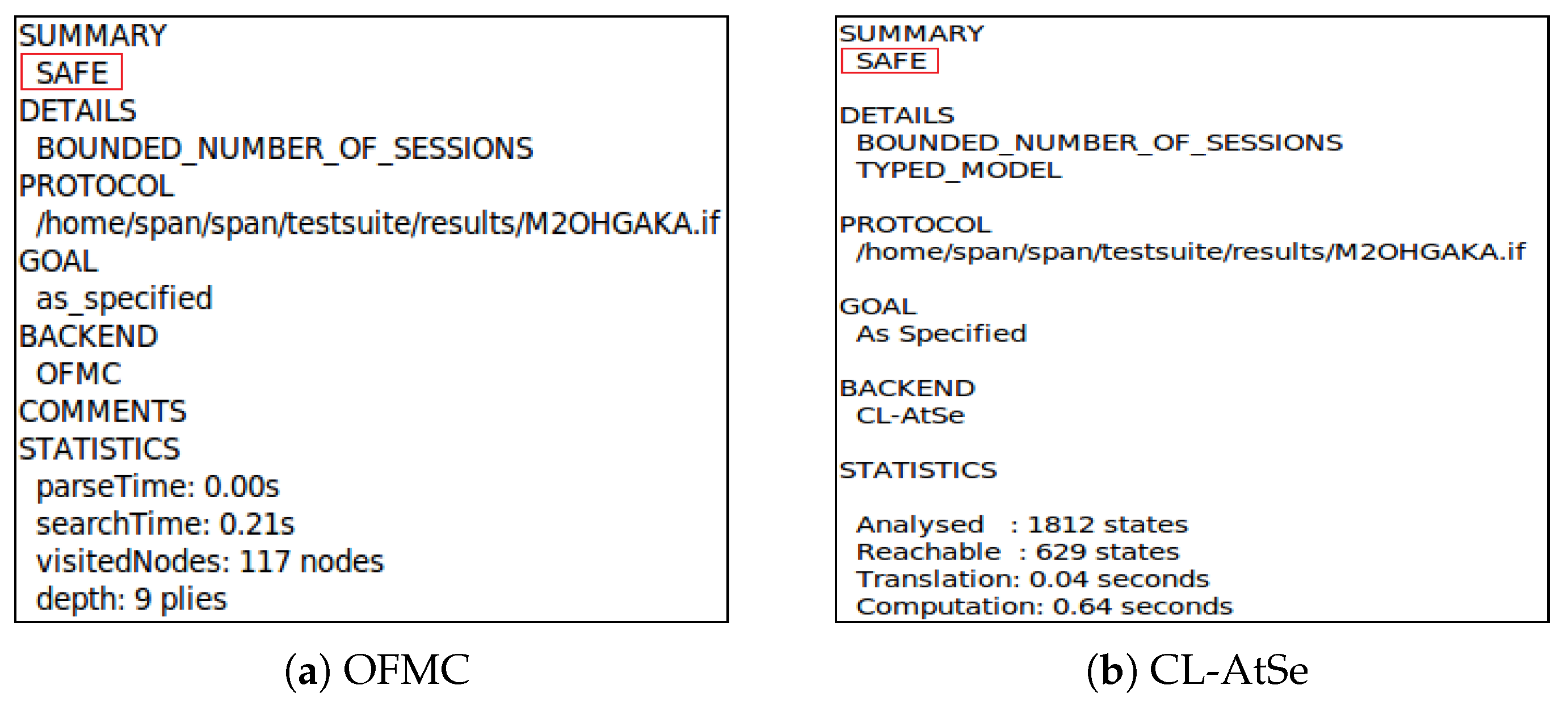
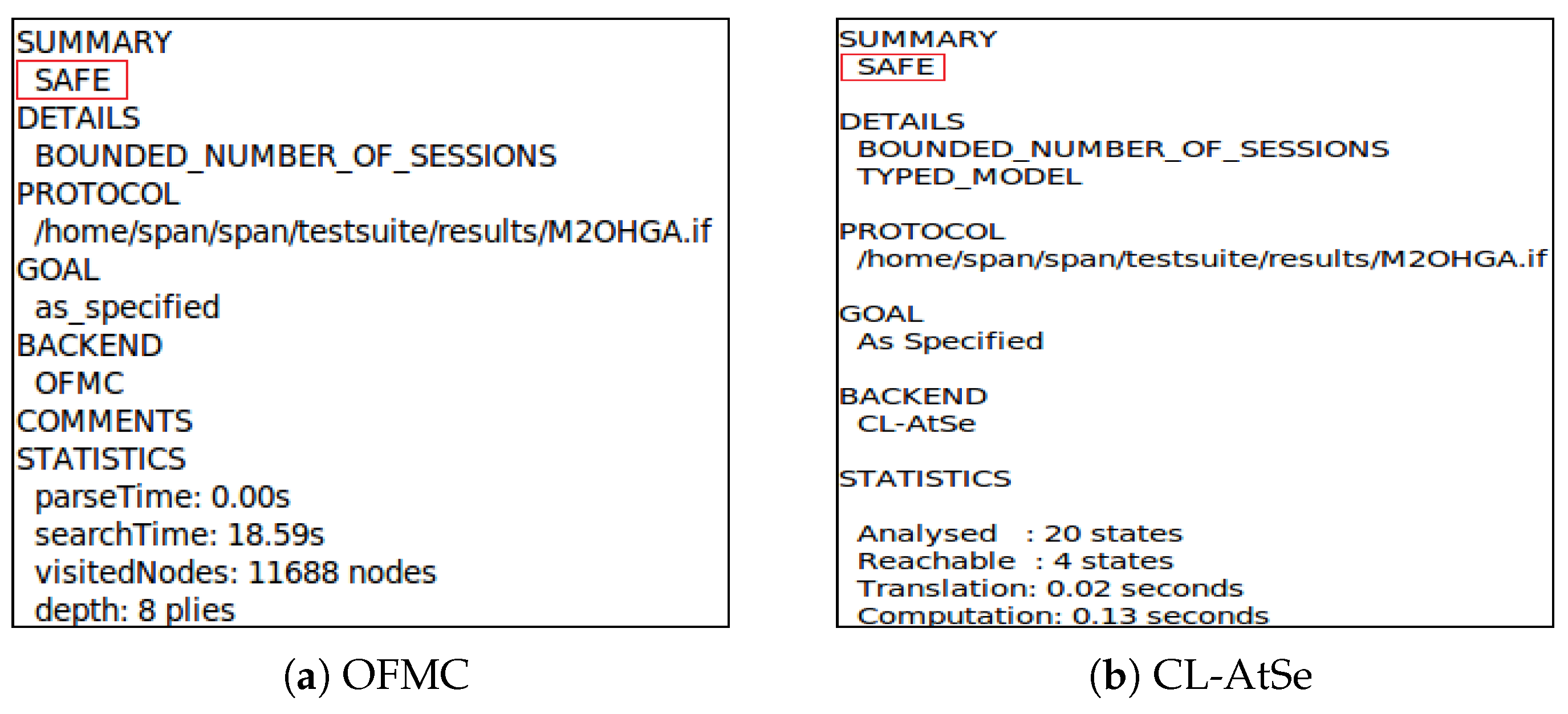
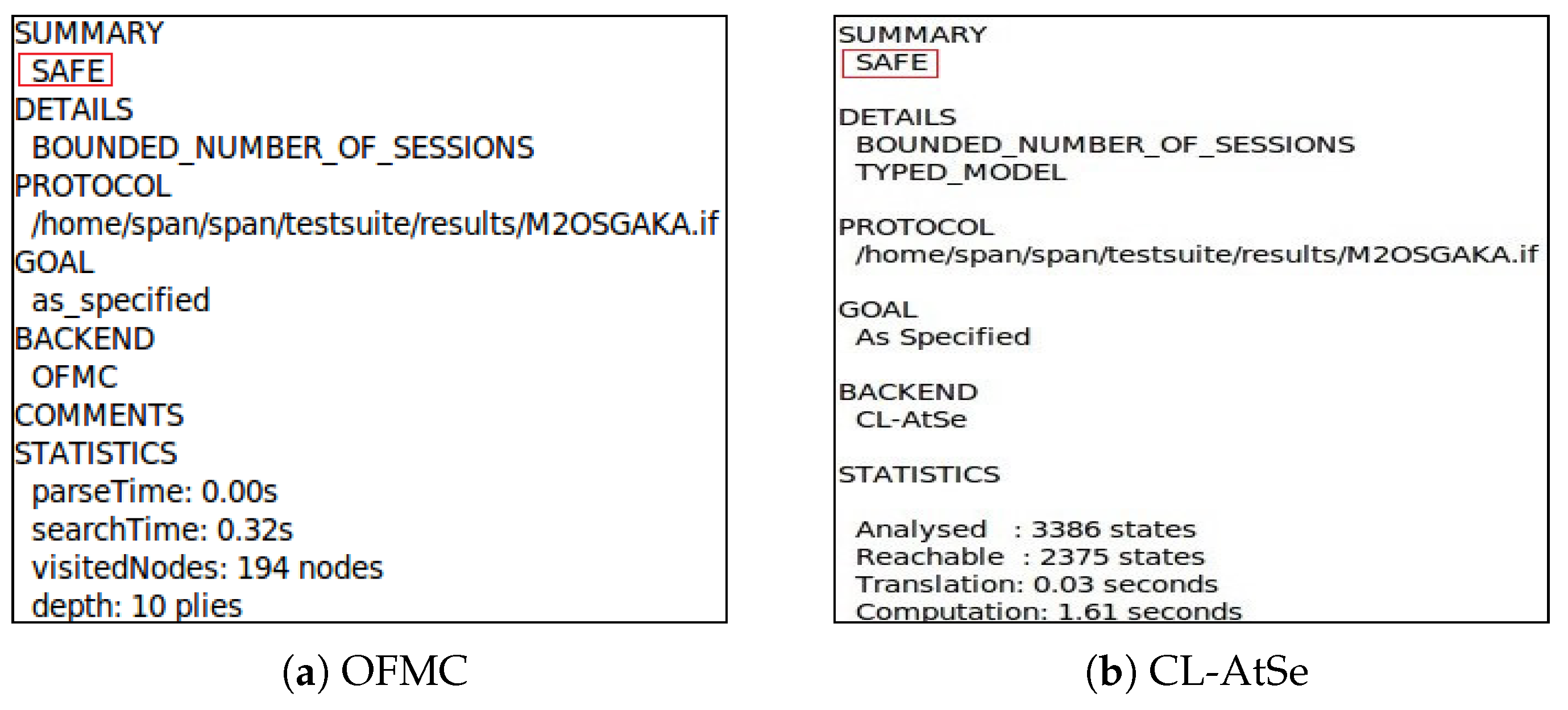
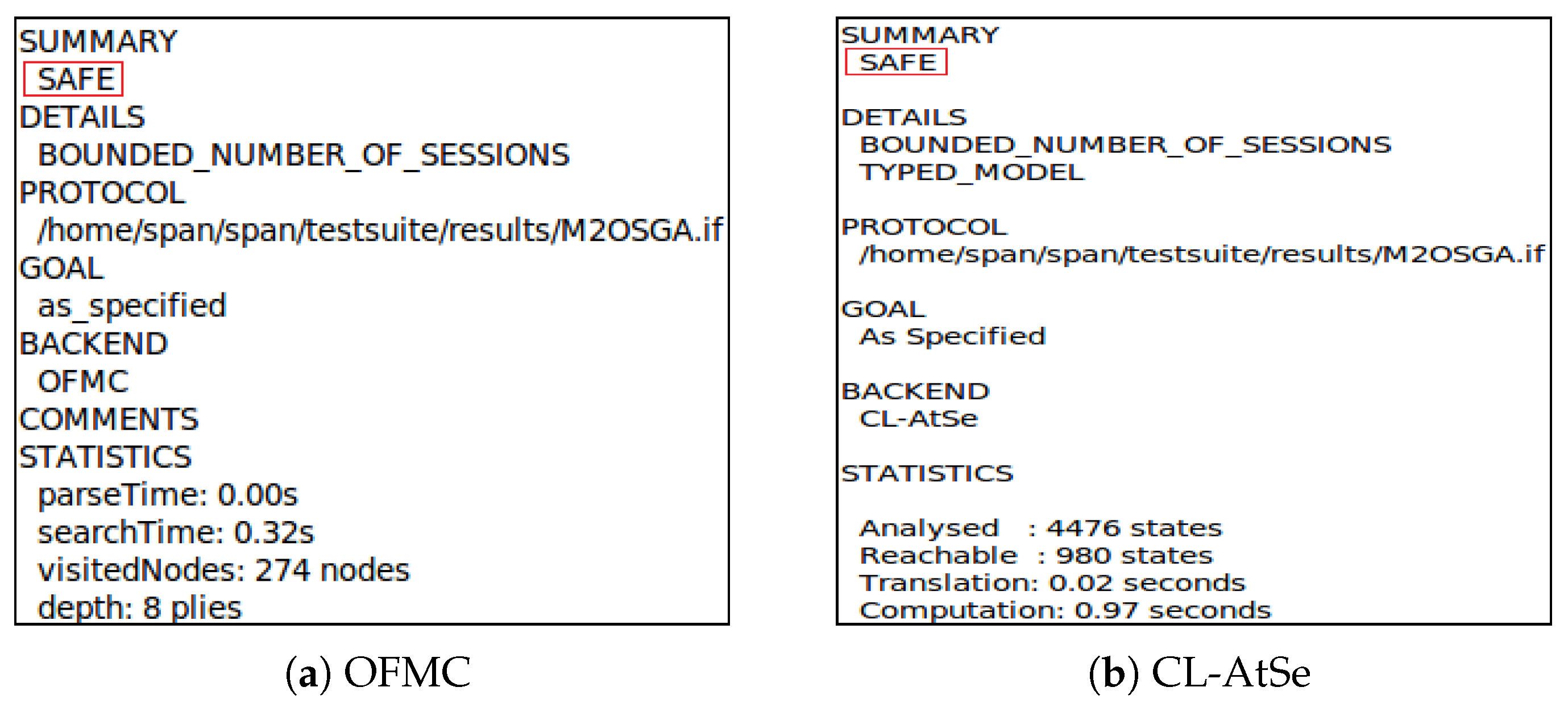
| Entities | Messages | Items | Length (bits) |
|---|---|---|---|
| Client devices leader | Msg1 | ||
| AS | Msg2 | 256 | |
| Client device | Msg3 | ||
| Client devices leader | Msg4 | 512 | |
| AS | Msg5 | ||
| Client devices leader | Msg6 | ||
| Communication cost |
| Protocol | Entities | Total Cost | ||
|---|---|---|---|---|
| Client Devices | AS | |||
| Leader | Non-Leader | |||
| HGAKA | ||||
| Entities | Messages | Items | Length (bits) |
|---|---|---|---|
| Non-leader client device | PreHGA-Msgi | ||
| Client device leader | Msg1 | ||
| Target device | Msg2 | 128 | |
| Client device leader | Msg3 | ||
| Communication cost | |||
| Protocol | Entities | Total Cost | ||
|---|---|---|---|---|
| Client Devices | Target Device | |||
| Leader | Non-Leader | |||
| HGA | ||||
| Entities | Messages | Items | Length (bits) |
|---|---|---|---|
| Client device leader | Msg1 | ||
| AS | Msg2 | 256 | |
| Client device | Msg3 | ||
| Client device leader | Msg4 | 512 | |
| AS | Msg5 | ||
| Client device leader | Msg6 | ||
| Communication cost | |||
| Protocol | Entities | Total Cost | ||
|---|---|---|---|---|
| Client Devices | AS | |||
| Leader | Non-Leader | |||
| SGAKA | + | + | ||
| Entities | Messages | Items | Length (bits) |
|---|---|---|---|
| Non-leader client device | PreSGA- Msgi | ||
| Client device leader | Msg1 | ||
| Target device | Msg2 | 384 | |
| Communication cost | |||
| Protocol | Entities | Total Cost | ||
|---|---|---|---|---|
| Client Devices | Target Device | |||
| Leader | Non-Leader | |||
| SGA | ||||
| Protocol | Work Factor |
|---|---|
| HGAKA | |
| HGA | |
| SGAKA | |
| SGA |
| IoT Group Authentication Solutions | R1 | R2 | R3 | R4 | R5 | MA |
|---|---|---|---|---|---|---|
| Yildiz et al. [39] | ✓ | ✓ | ✓ | x | ✓ | x |
| Chien [40] | o | ✓ | o | x | x | x |
| Aydin et al. [41] | o | x | ✓ | x | x | x |
| Zhang et al. [58] | ✓ | o | ✓ | x | ✓ | x |
| Khalid et al. [59] | ✓ | ✓ | ✓ | ✓ | o | x |
| Jiang et al. [45] | ✓ | ✓ | o | x | x | x |
| Choi et al. [47] | ✓ | x | o | x | x | x |
| Fu et al. [49] | ✓ | o | ✓ | x | x | x |
| Singh and Shrimankar [51] | ✓ | ✓ | ✓ | x | ✓ | x |
| Parne et al. [50] | ✓ | ✓ | ✓ | x | x | x |
| 5G-AKA [56] | ✓ | x | ✓ | ✓ | o | x |
| Ouaissa et al. [53] | ✓ | o | ✓ | x | x | x |
| Gharsallah et al. [54] | ✓ | x | o | x | x | x |
| Miao et al. [55] | ✓ | ✓ | ✓ | x | ✓ | x |
| The M2O hybrid protocols | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| The M2O symmetric-key-based protocols | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| IoT Group Authentication Solutions | Communication Cost (bits) |
|---|---|
| Jiang et al. [45] | |
| Choi et al. [47] | |
| Fu et al. [49] | |
| Singh and Shrimankar [51] | |
| Parne et al. [50] | |
| 5G-AKA [56] | |
| Ouaissa et al. [53] | |
| Gharsallah et al. [54] | |
| Miao et al. [55] | |
| M2O hybrid protocols | |
| M2O symmetric-key-based protocols | + |
| IoT Group Authentication Solutions | Computation Cost |
|---|---|
| Jiang et al. [45] | |
| Choi et al. [47] | |
| Fu et al. [49] | |
| Singh and Shrimankar [51] | |
| Parne et al. [50] | |
| 5G-AKA [56] | |
| Ouaissa et al. [53] | |
| Gharsallah et al. [54] | |
| Miao et al. [55] | |
| M2O hybrid protocols | |
| M2O symmetric-key-based protocols |
| Cryptographic Operation | Average Execution Time (Milliseconds) |
|---|---|
| SHA256 | 0.0096 |
| HMAC- SHA256 | 0.0300 |
| AES-CBC-128 encryption | 0.0181 |
| AES-CBC-128 decryption | 0.0184 |
| AES-CTS-128 encryption | 0.055 |
| AES-CTS-128 decryption | 0.080 |
| RSA-3072 encryption | 2.096 |
| RSA-3072 decryption | 16.459 |
| Authentication Type | Two-Factor | ||
|---|---|---|---|
| Protocol | M2O Hybrid | Kerberos | |
| HGAKA | HGA | ||
| Communication cost (bits) | 1536 | ||
| Authentication Type | Two-Factor | ||
|---|---|---|---|
| Protocol | M2O Symmetric-Key-Based | Kerberos | |
| SGAKA | SGA | ||
| Communication cost (bits) | 768 | ||
| Authentication Type | Two-Factor | ||
|---|---|---|---|
| Protocol | M2O Hybrid | Kerberos | |
| HGAKA | HGA | ||
| Cryptographic operations | |||
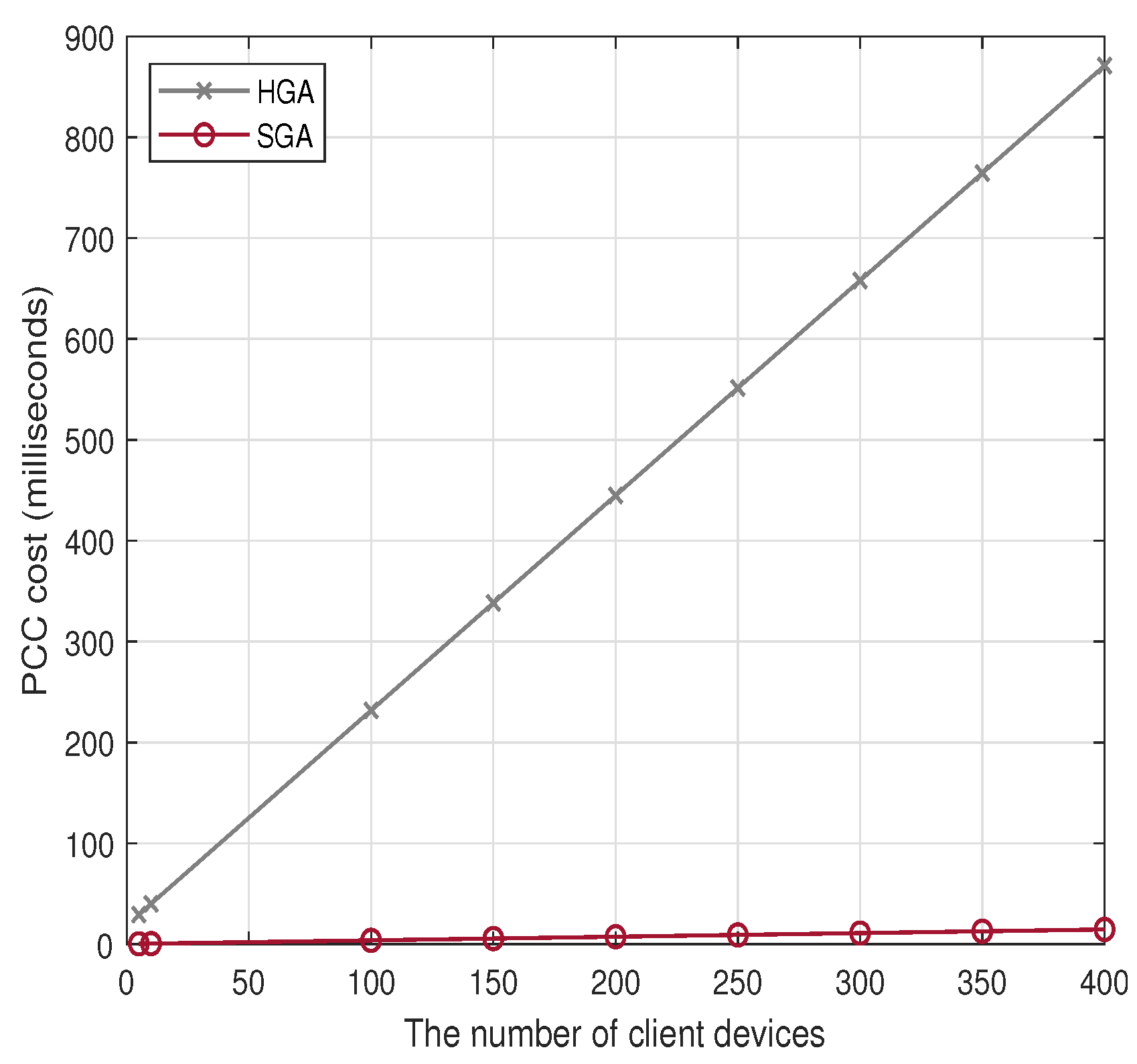
| PCC cost (ms) | + | + | |
| Authentication Type | Two-Factor | ||
|---|---|---|---|
| Protocol | M2O Symmetric-Key-Based | Kerberos | |
| SGAKA | SGA | ||
| Cryptographic operations | |||
| PCC cost (ms) | + | + | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
AlJanah, S.; Zhang, N.; Tay, S.W. Optimizing Group Multi-Factor Authentication for Secure and Efficient IoT Device Communications. Cryptography 2025, 9, 35. https://doi.org/10.3390/cryptography9020035
AlJanah S, Zhang N, Tay SW. Optimizing Group Multi-Factor Authentication for Secure and Efficient IoT Device Communications. Cryptography. 2025; 9(2):35. https://doi.org/10.3390/cryptography9020035
Chicago/Turabian StyleAlJanah, Salem, Ning Zhang, and Siok Wah Tay. 2025. "Optimizing Group Multi-Factor Authentication for Secure and Efficient IoT Device Communications" Cryptography 9, no. 2: 35. https://doi.org/10.3390/cryptography9020035
APA StyleAlJanah, S., Zhang, N., & Tay, S. W. (2025). Optimizing Group Multi-Factor Authentication for Secure and Efficient IoT Device Communications. Cryptography, 9(2), 35. https://doi.org/10.3390/cryptography9020035









