Threats, Attacks, and Cryptography Frameworks of Cybersecurity in Critical Infrastructures
Abstract
1. Introduction
- A presentation of the most recent cybersecurity attacks against CIs;
- An analysis and development of a thorough architecture that integrates the most common technologies and cryptographic mechanisms of CIs;
- The creation of a threat model, an adversary model, and an attack model based on this architecture and the structure of CIs;
- A demonstration of some published security and mitigation techniques and approaches.
2. Recent Incidents in Critical Infrastructures
2.1. Health
2.2. Energy Facilities
2.3. Intelligent Transportation Systems
2.4. Oil and Gas Facilities
2.5. Financial Services
3. Framework of Critical Infrastructures
3.1. Frameworks for Different Critical Infrastructure Systems
- Interoperability: the ability of heterogeneous devices to constantly communicate with each other via wired and wireless networks;
- Virtualization: the automation of healthcare processes by monitoring the environment;
- Decentralization: the ability of each employed component of the system to decide on their next operation based on the collected data;
- Real-time capability: the ability to quickly react to environmental changes and communicate it with the rest of the system’s components;
- Service orientation: the categorization of the system’s operations as services which are easily accessible to all related parties;
- Modularity: the scalability of the system that enables it to constantly adapt and adopt new requirements and technologies.
3.2. Differences between Frameworks
3.3. Architecture of Employed Technologies
3.3.1. SCADA Architecture
3.3.2. IoT and CPS Architectures
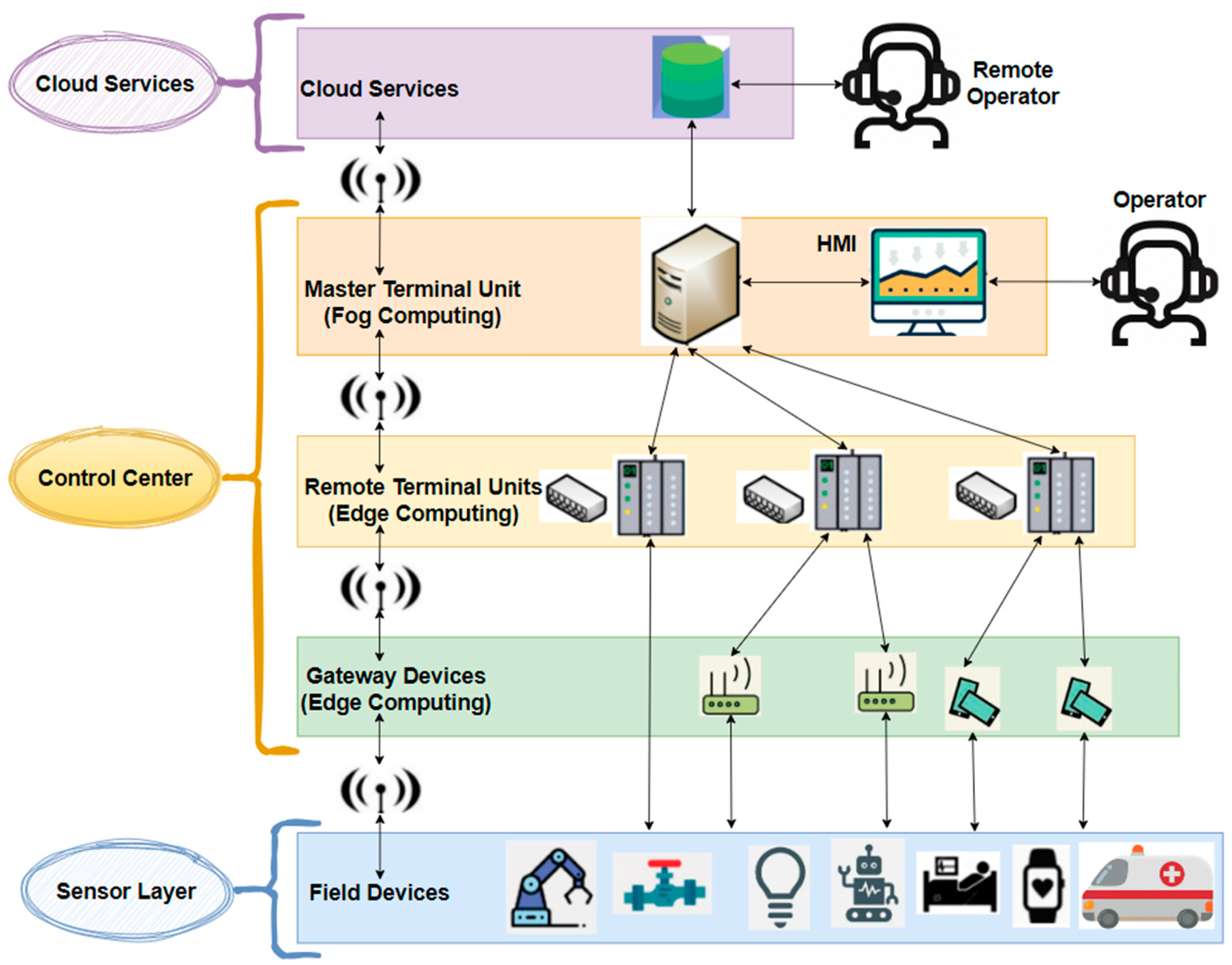
3.3.3. Unified Architecture
3.4. Cryptography in CIs
3.4.1. Cryptographic Mechanisms
3.4.2. Physical Unclonable Functions (PUFs) and Random Number Generators (RNGs)
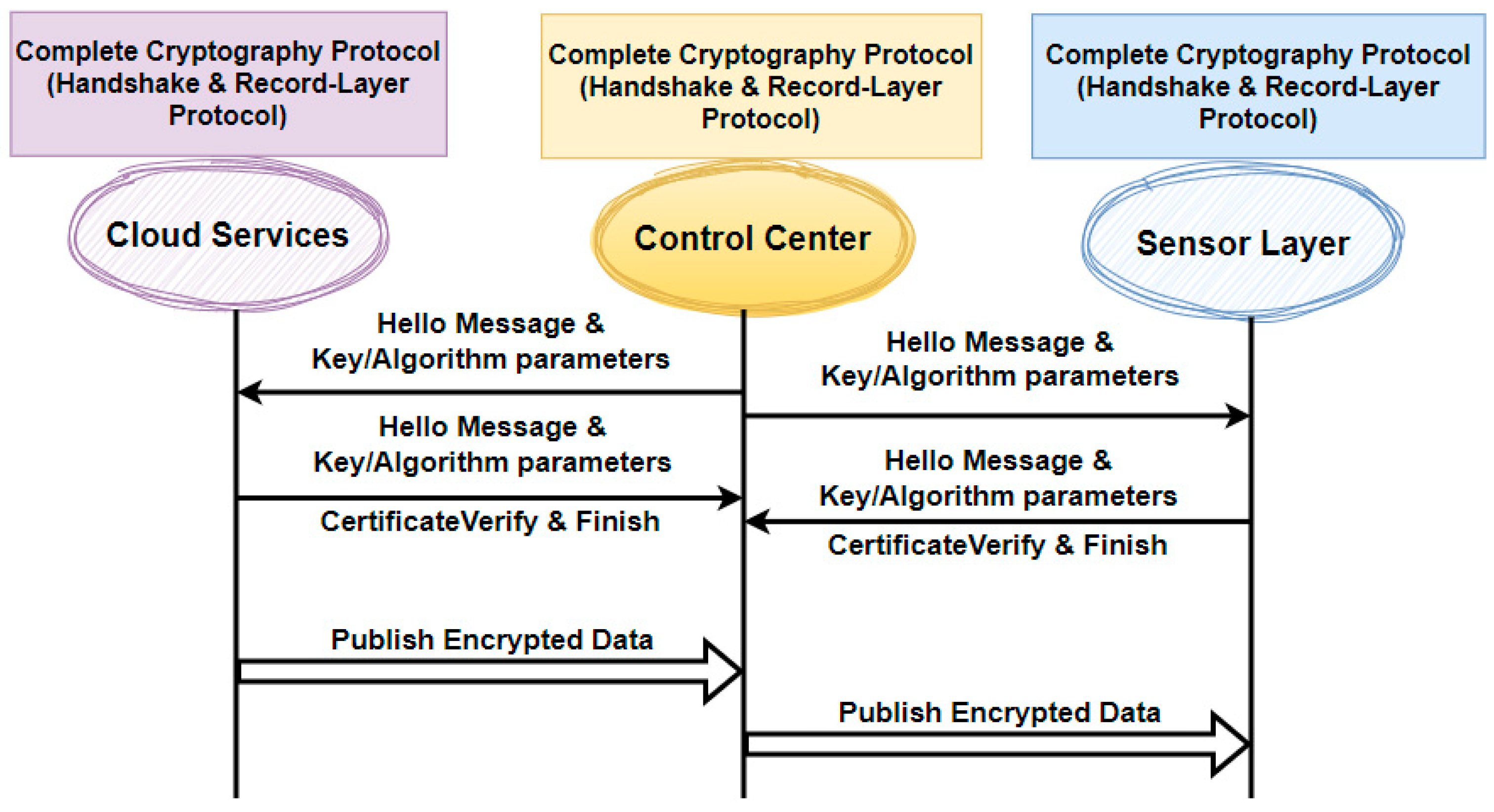
3.4.3. Cryptography Frameworks
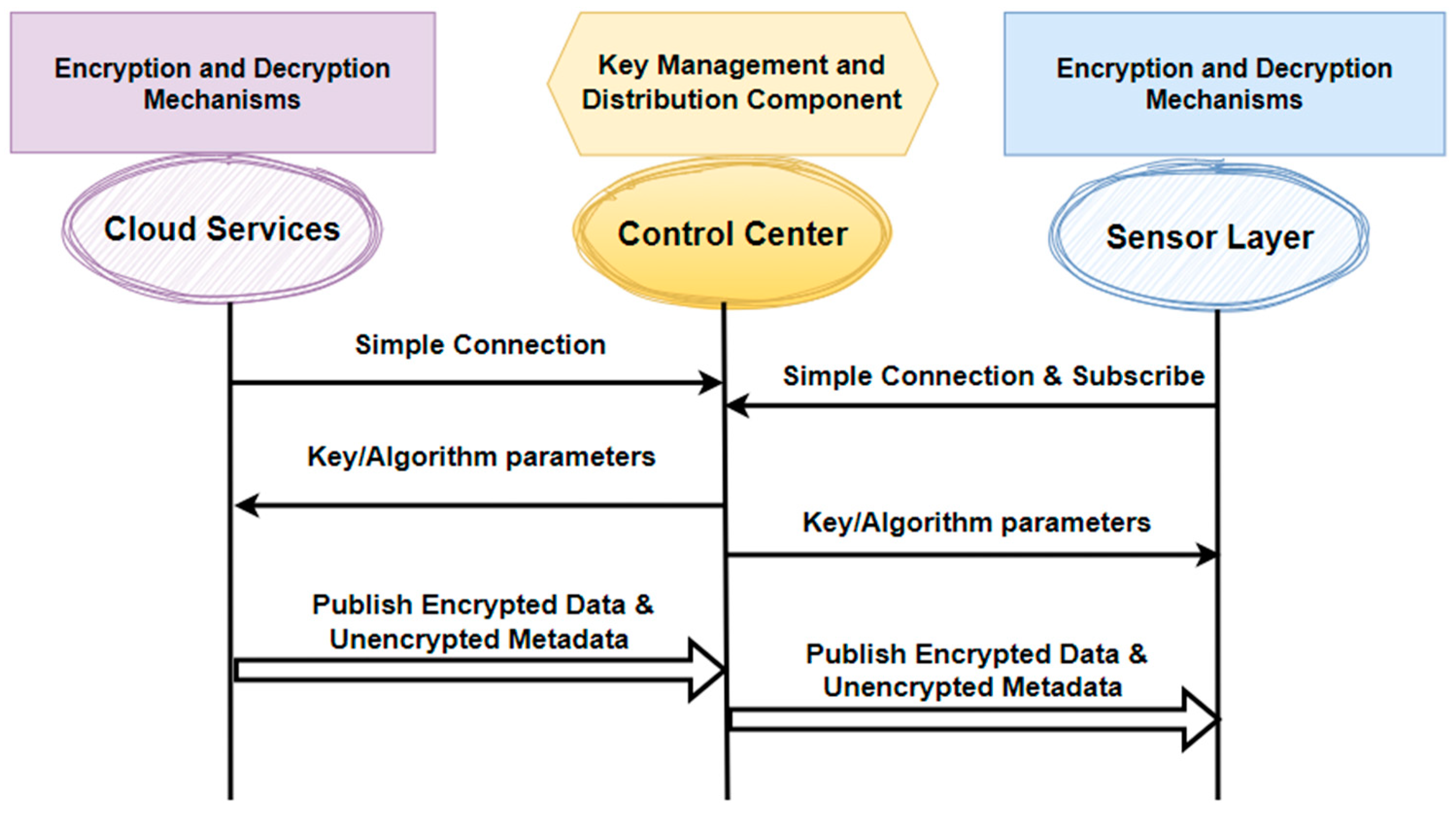
3.4.4. Cryptography of the Unified Architecture
4. Threat, Adversary, and Attack Models for Critical Infrastructures’ Architecture
4.1. Threat Modeling
4.1.1. General Threat Modeling
4.1.2. Threat Modeling in Cryptography Frameworks
4.2. Adversary Modeling
- Resources: Adversaries can be either driven by their own personal motivations, with little to no fundings and resources, or they can be funded by individuals, organizations, or even nations, thus having many access privileges and tools for more sophisticated attacks. As cryptographic primitives heavily depend on the complexity of their employed mathematic computations and their key size, the resources that are available to the adversary can play a critical role in their ability to safely encrypt the data and protect the key from brute force-based attacks. When the adversary has high computation power available, key extraction and cryptographic vulnerabilities’ exploitation is easier.
- Access: The possession of access to the system is also important to the adversary, as more types of attacks and more information can be gained by having physical access to targeted components. In the case of the described architecture of CIs, the sensor layer, which contains many resource-constrained devices, is isolated or far away from the center of the architecture. This results in being an easy target for physical attacks, such as side-channel and power analysis, microprobing, and memory flashing attacks. Moreover, some components of the control center can also execute their functionalities remotely without constant human supervision. This can also result in them being easy targets, especially in the case of insiders being adversaries. Nevertheless, even without physical access, network interfaces can also be targeted with replay or rollback attacks and grant accessibility to the system by proximity.
- Specificity: Attackers can maliciously intend for a specific output to be produced by the CI’s control and monitoring system in order to reshape its functionality according to their own motivations. On the other hand, a specific output cannot be the target of the executed attack. Instead, the misguidance of the system to produce other kinds of outputs except the correct one can be the targeted result.
- Knowledge: An adversary can have complete or no knowledge of the system and its functionalities. The system model, parameters, and state vectors can be either already known to the attackers, because they are an insider or in contact with an insider, or because they steadily acquired access to this information by exploiting vulnerabilities of the system. The types of attacks that are executed with zero knowledge of the CI are called black-box attacks.
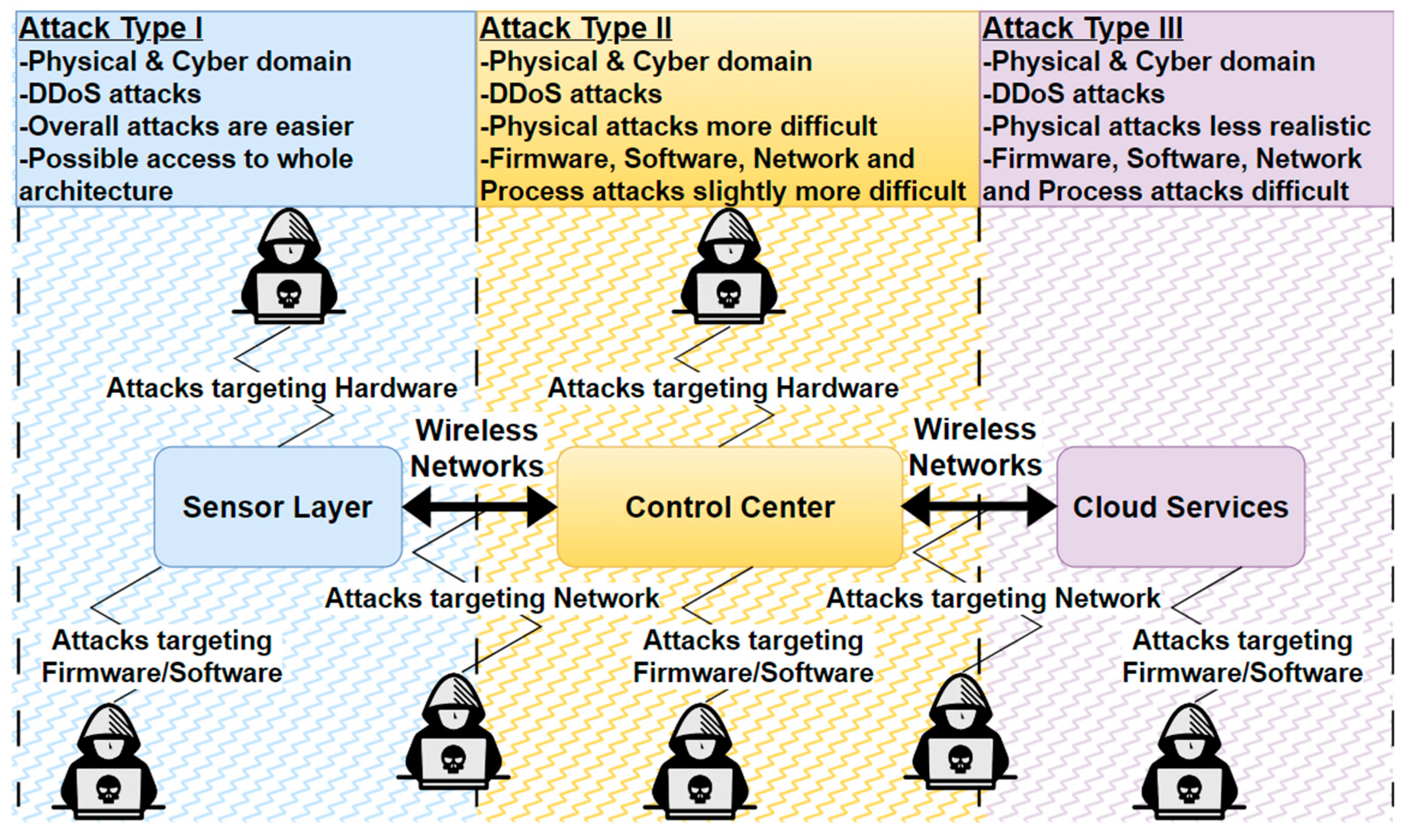
4.3. Attack Model
5. Security and Mitigation Solutions
5.1. General Security Solutions
5.2. Solutions in Cryptography
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Alcaraz, C.; Zeadally, S. Critical infrastructure protection: Requirements and challenges for the 21st century. Int. J. Crit. Infrastruct. Prot. 2015, 8, 53–66. [Google Scholar] [CrossRef]
- Al-Jaroodi, J.; Mohamed, N.; Abukhousa, E. Health 4.0: On the Way to Realizing the Healthcare of the Future. IEEE Access 2020, 8, 211189–211210. [Google Scholar] [CrossRef] [PubMed]
- Rikalovic, A.; Suzic, N.; Bajic, B.; Piuri, V. Industry 4.0 Implementation Challenges and Opportunities: A Technological Perspective. IEEE Syst. J. 2022, 16, 2797–2810. [Google Scholar] [CrossRef]
- Stergiopoulos, G.; Gritzalis, D.A.; Limnaios, E. Cyber-Attacks on the Oil & Gas Sector: A Survey on Incident Assessment and Attack Patterns. IEEE Access 2020, 8, 128440–128475. [Google Scholar]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A Survey of IoT-Enabled Cyberattacks: Assessing Attack Paths to Critical Infrastructures and Services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Tsantikidou, K.; Sklavos, N. Hardware Limitations of Lightweight Cryptographic Designs for IoT in Healthcare. Cryptography 2022, 6, 45. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Ospina, J.; Liu, X.; Konstantinou, C. Cyber-Physical Energy Systems Security: Threat Modeling, Risk Assessment, Resources, Metrics, and Case Studies. IEEE Access 2021, 9, 29775–29818. [Google Scholar] [CrossRef]
- European Commission. Communication from the Commission on a European Programme for Critical Infrastructure Protection, COM(2006) 786 Final; European Commission: Brussels, Belgium, 2006.
- International Society of Automation, ISA/IEC 62443 Series of Standards. Available online: https://www.isa.org/standards-and-publications/isa-standards/isa-iec-62443-series-of-standards (accessed on 19 February 2024).
- Stouffer, K.; Pease, M.; Tang, C.; Zimmerman, T.; Pillitteri, V.; Lightman, S.; Hahn, A.; Saravia, S.; Sherule, A.; Thompson, M. NIST Special Publication: NIST SP 800-82r3 Guide to Operational Technology (OT) Security; NIST: Gaithersburg, MD, USA, 2023.
- Knapp, E.D.; Langill, J.T. Industrial Network Security: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems, 2nd ed.; Syngress: St. Rockland, MA, USA, 2015. [Google Scholar]
- Staddon, E.; Loscri, V.; Mitton, N. Attack Categorisation for IoT Applications in Critical Infrastructures, a Survey. Appl. Sci. 2021, 11, 7228. [Google Scholar] [CrossRef]
- Makrakis, G.M.; Kolias, C.; Kambourakis, G.; Rieger, C.; Benjamin, J. Industrial and Critical Infrastructure Security: Technical Analysis of Real-Life Security Incidents. IEEE Access 2021, 9, 165295–165325. [Google Scholar] [CrossRef]
- Lehto, M. Cyber-Attacks Against Critical Infrastructure. In Cyber Security. Computational Methods in Applied Sciences; Springer: Cham, Switzerland, 2022; p. 56. [Google Scholar]
- Abir, S.M.A.A.; Anwar, A.; Choi, J.; Kayes, A.S.M. IoT-Enabled Smart Energy Grid: Applications and Challenges. IEEE Access 2021, 9, 50961–50981. [Google Scholar] [CrossRef]
- Rahouti, M.; Xiong, K.; Xin, Y. Secure Software-Defined Networking Communication Systems for Smart Cities: Current Status, Challenges, and Trends. IEEE Access 2021, 9, 12083–12113. [Google Scholar] [CrossRef]
- Pliatsios, D.; Sarigiannidis, P.; Lagkas, T.; Sarigiannidis, A.G. A Survey on SCADA Systems: Secure Protocols, Incidents, Threats and Tactics. IEEE Commun. Surv. Tutor. 2020, 22, 1942–1976. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of Threats to the Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1636–1675. [Google Scholar] [CrossRef]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of Threats? A Survey of Practical Security Vulnerabilities in Real IoT Devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Khurshid, A.; Alsaaidi, R.; Aslam, M.; Raza, S. EU Cybersecurity Act and IoT Certification: Landscape, Perspective and a Proposed Template Scheme. IEEE Access 2022, 10, 129932–129948. [Google Scholar] [CrossRef]
- McKay, K.A.; Bassham, L.; Turan, M.S.; Mouha, N. NISTIR 8114. Report on Lightweight Cryptography; NIST: Gaithersburg, MD, USA, 2017.
- Chen, L.; Jordan, S.; Liu, Y.; Moody, D.; Peralta, R.; Perlner, R.; Smith-Tone, D. NISTIR 8105. Report on Post-Quantum Cryptography; NIST: Gaithersburg, MD, USA, 2016.
- European Union Agency for Cybersecurity (ENISA). ENISA Threat Landscape 2023; ENISA: Athens, Greece, 2023.
- Medtronic Recalls MiniMed Insulin Pumps as FDA Warns about Hacking Risk. CNN. Available online: https://edition.cnn.com/2019/06/27/health/medtronic-insulin-pump-recall-cybersecurity-fda-bn/index.html. (accessed on 4 December 2023).
- Sethuraman, S.C.; Vijayakumar, V.; Walczak, S. Cyber Attacks on Healthcare Devices Using Unmanned Aerial Vehicles. J. Med. Syst. 2020, 44, 29. [Google Scholar] [CrossRef]
- Sterle, L.; Bhunia, S. On SolarWinds Orion Platform Security Breach. In Proceedings of the 2021 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/IOP/SCI), Atlanta, GA, USA, 18–21 October 2021. [Google Scholar]
- Rajkumar, V.S.; Ştefanov, A.; Presekal, A.; Palensky, P.; Torres, J.L.R. Cyber Attacks on Power Grids: Causes and Propagation of Cascading Failures. IEEE Access 2023, 11, 103154–103176. [Google Scholar] [CrossRef]
- Understanding Cyber Threats in Transport. European Union Agency for Cybersecurity (ENISA). Available online: https://www.enisa.europa.eu/news/understanding-cyber-threats-in-transport. (accessed on 4 December 2023).
- Timeline of Cyber Incidents Involving Financial Institutions. Carnegie. Available online: https://carnegieendowment.org/specialprojects/protectingfinancialstability/timeline. (accessed on 4 December 2023).
- Hu, F. Security and Privacy in Internet of Things (IoTs): Models, Algorithms, and Implementations; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Greer, C.; Burns, M.; Wollman, D.; Griffor, E. Cyber-Physical Systems and Internet of Things, Special Publication (NIST SP); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019.
- Duo, W.; Zhou, M.; Abusorrah, A. A Survey of Cyber Attacks on Cyber Physical Systems: Recent Advances and Challenges. IEEE/CAA J. Autom. Sin. 2022, 9, 784–800. [Google Scholar] [CrossRef]
- Falco, G.; Caldera, C.; Shrobe, H. IIoT Cybersecurity Risk Modeling for SCADA Systems. IEEE Internet Things J. 2018, 5, 4486–4495. [Google Scholar] [CrossRef]
- Alanazi, M.; Mahmood, A.; Chowdhury, M.J.M. SCADA vulnerabilities and attacks: A review of the state-of-the-art and open issues. Comput. Secur. 2023, 125, 103028. [Google Scholar] [CrossRef]
- Fan, C.; Shie, C.; Tseng, Y.; Huang, H. An Efficient Data Protection Scheme Based on Hierarchical ID-Based Encryption for MQTT. ACM Trans. Sens. Netw. 2023, 19, 61. [Google Scholar] [CrossRef]
- Li, P.; Su, J.; Wang, X. iTLS: Lightweight Transport-Layer Security Protocol for IoT With Minimal Latency and Perfect Forward Secrecy. IEEE Internet Things J. 2020, 7, 6828–6841. [Google Scholar] [CrossRef]
- Della Sala, R.; Scotti, G. A Novel FPGA Implementation of the NAND-PUF with Minimal Resource Usage and High Reliability. Cryptography 2023, 7, 18. [Google Scholar] [CrossRef]
- Mall, P.; Amin, R.; Das, A.K.; Leung, M.T.; Choo, K.-K.R. PUF-Based Authentication and Key Agreement Protocols for IoT, WSNs, and Smart Grids: A Comprehensive Survey. IEEE Internet Things J. 2022, 9, 8205–8228. [Google Scholar] [CrossRef]
- Garcia-Bosque, M.; Pérez-Resa, A.; Sánchez-Azqueta, C.; Aldea, C.; Celma, S. Chaos-Based Bitwise Dynamical Pseudorandom Number Generator On FPGA. IEEE Trans. Instrum. Meas. 2019, 68, 291–293. [Google Scholar] [CrossRef]
- Della Sala, R.; Bellizia, D.; Scotti, G. A Novel Ultra-Compact FPGA-Compatible TRNG Architecture Exploiting Latched Ring Oscillators. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 1672–1676. [Google Scholar] [CrossRef]
- Zhou, W.; Cao, C.; Huo, D.; Cheng, K.; Zhang, L.; Guan, L.; Liu, T.; Jia, Y.; Zheng, Y.; Zhang, Y.; et al. Reviewing IoT Security via Logic Bugs in IoT Platforms and Systems. IEEE Internet Things J. 2021, 8, 11621–11639. [Google Scholar] [CrossRef]
- Arafin, M.T.; Stanley, A.; Sharma, P. Hardware-based anti-counterfeiting techniques for safeguarding supply chain integrity. In Proceedings of the 2017 IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, USA, 28–31 May 2017. [Google Scholar]
- Utyamishev, D.; Partin-Vaisband, I. Real-Time Detection of Power Analysis Attacks by Machine Learning of Power Supply Variations On-Chip. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2020, 39, 45–55. [Google Scholar] [CrossRef]
- Liu, Y.; Shan, G.; Liu, Y.; Alghamdi, A.; Alam, I.; Biswas, S. Blockchain Bridges Critical National Infrastructures: E-Healthcare Data Migration Perspective. IEEE Access 2022, 10, 28509–28519. [Google Scholar] [CrossRef]
- Chaudhry, J.A.; Saleem, K.; Alazab, M.; Zeeshan, H.M.A.; Al-Muhtadi, J.; Rodrigues, J.J.P.C. Data Security Through Zero-Knowledge Proof and Statistical Fingerprinting in Vehicle-to-Healthcare Everything (V2HX) Communications. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3869–3879. [Google Scholar] [CrossRef]
- Katulić, F.; Sumina, D.; Groš, S.; Erceg, I. Protecting Modbus/TCP-Based Industrial Automation and Control Systems Using Message Authentication Codes. IEEE Access 2023, 11, 47007–47023. [Google Scholar] [CrossRef]
- Geng, Y.; Chen, Y.; Ma, R.; Wei, Q.; Pan, J.; Wang, J.; Cheng, P.; Wang, Q. Defending Cyber–Physical Systems Through Reverse-Engineering-Based Memory Sanity Check. IEEE Internet Things J. 2023, 10, 8331–8347. [Google Scholar] [CrossRef]
- Tan, B.; Elnaggar, R.; Fung, J.M.; Karri, R.; Chakrabarty, K. Toward Hardware-Based IP Vulnerability Detection and Post-Deployment Patching in Systems-on-Chip. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2021, 40, 1158–1171. [Google Scholar] [CrossRef]
- Gourisetti, S.N.G.; Mylrea, M.; Patangia, H. Cybersecurity Vulnerability Mitigation Framework Through Empirical Paradigm (CyFEr): Prioritized Gap Analysis. IEEE Syst. J. 2020, 14, 1897–1908. [Google Scholar] [CrossRef]
- Zhu, Q.; Qin, Y.; Zhou, C.; Fei, L. Hierarchical Flow Model-Based Impact Assessment of Cyberattacks for Critical Infrastructures. IEEE Syst. J. 2019, 13, 3944–3955. [Google Scholar] [CrossRef]
- Dedousis, P.; Stergiopoulos, G.; Arampatzis, G.; Gritzalis, D. A Security-Aware Framework for Designing Industrial Engineering Processes. IEEE Access 2021, 9, 163065–163085. [Google Scholar] [CrossRef]
- Dedousis, P.; Stergiopoulos, G.; Arampatzis, G.; Gritzalis, D. Enhancing Operational Resilience of Critical Infrastructure Processes Through Chaos Engineering. IEEE Access 2023, 11, 106172–106189. [Google Scholar] [CrossRef]
- Ashley, T.D.; Kwon, R.; Gourisetti, S.N.G.; Katsis, C.; Bonebrake, C.A.; Boyd, P.A. Gamification of Cybersecurity for Workforce Development in Critical Infrastructure. IEEE Access 2022, 10, 112487–112501. [Google Scholar] [CrossRef]
- Moreira, F.R.; Da Silva Filho, D.A.; Nze, G.D.A.; de Sousa Júnior, R.T.; Nunes, R.R. Evaluating the Performance of NIST’s Framework Cybersecurity Controls Through a Constructivist Multicriteria Methodology. IEEE Access 2021, 9, 129605–129618. [Google Scholar] [CrossRef]
- Feijoo-Martínez, J.R.; Guerrero-Curieses, A.; Gimeno-Blanes, F.; Castro-Fernández, M.; Rojo-Álvarez, J.L. Cybersecurity Alert Prioritization in a Critical High Power Grid With Latent Spaces. IEEE Access 2023, 11, 23754–23770. [Google Scholar] [CrossRef]
- Ferdowsi, A.; Eldosouky, A.; Saad, W. Interdependence-Aware Game-Theoretic Framework for Secure Intelligent Transportation Systems. IEEE Internet Things J. 2021, 8, 16395–16405. [Google Scholar] [CrossRef]
- Sowjanya, K.; Dasgupta, M.; Ray, S. A lightweight key management scheme for key-escrow-free ECC-based CP-ABE for IoT healthcare systems. J. Syst. Archit. 2021, 117, 102108. [Google Scholar] [CrossRef]
- Das, S.; Namasudra, S. Multiauthority CP-ABE-based Access Control Model for IoT-enabled Healthcare Infrastructure. IEEE Trans. Ind. Inform. 2023, 19, 821–829. [Google Scholar] [CrossRef]
- Ar-Reyouchi, E.M.; Ghoumid, K.; Ar-Reyouchi, D.; Rattal, S.; Yahiaoui, R.; Elmazria, O. Protocol Wireless Medical Sensor Networks in IoT for the Efficiency of Healthcare. IEEE Internet Things J. 2022, 9, 10693–10704. [Google Scholar] [CrossRef]
- Hamad, M.; Finkenzeller, A.; Liu, H.; Lauinger, J.; Prevelakis, V.; Steinhorst, S. SEEMQTT: Secure End-to-End MQTT-Based Communication for Mobile IoT Systems Using Secret Sharing and Trust Delegation. IEEE Internet Things J. 2023, 10, 3384–3406. [Google Scholar] [CrossRef]
- Pérez, S.; Hernández-Ramos, J.L.; Raza, S.; Skarmeta, A. Application Layer Key Establishment for End-to-End Security in IoT. IEEE Internet Things J. 2020, 7, 2117–2128. [Google Scholar] [CrossRef]
- Gu, C.; Chang, C.H.; Liu, W.; Hanley, N.; Miskelly, J.; O’Neill, M. A large-scale comprehensive evaluation of single-slice ring oscillator and PicoPUF bit cells on 28-nm Xilinx FPGAs. J. Cryptogr. Eng. 2021, 11, 227–238. [Google Scholar] [CrossRef]
- Habib, B.; Kaps, J.P.; Gaj, K. Efficient SR-Latch PUF. Applied Reconfigurable Computing, ARC 2015. In Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2015; pp. 205–216. [Google Scholar]
- Madani, M.; Tanougast, C. FPGA Implementation of an Enhanced Chaotic-KASUMI Block Cipher. Microprocess. Microsyst. 2021, 80, 103644. [Google Scholar] [CrossRef]
- Yang, B.; Rožic, V.; Grujic, M.; Mentens, N.; Verbauwhede, I. ES-TRNG: A high-throughput, low-area true random number generator based on edge sampling. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 3, 267–292. [Google Scholar] [CrossRef]
- Addabbo, T.; Fort, A.; Moretti, R.; Mugnaini, M.; Takaloo, H.; Vignoli, V. A New Class of Digital Circuits for the Design of Entropy Sources in Programmable Logic. IEEE Trans. Circuits Syst. I Regul. Pap. 2020, 67, 2419–2430. [Google Scholar] [CrossRef]
- Baturone, I.; Román, R.; Corbacho, Á. A unified multibit PUF and TRNG based on ring oscillators for secure IoT devices. IEEE Internet Things J. 2023, 10, 6182–6192. [Google Scholar] [CrossRef]
- Wang, Y.; Liang, H.; Wang, Y.; Yao, L.; Yi, M.; Huang, Z.; Lu, Y. A reconfigurable PUF structure with dual working modes based on entropy separation model. Microelectron. J. 2022, 124, 105445. [Google Scholar] [CrossRef]
- Tsantikidou, K.; Boufeas, D.; Sklavos, N. Area-Delay Efficient Security Scheme for Smart Hospital Systems. In Proceedings of the 2023 IEEE International Conference on Cyber Security and Resilience (CSR), Venice, Italy, 31 July–2 August 2023. [Google Scholar]
- Tsantikidou, K.; Sklavos, N. Minimal Resource Required E-Health System with End-to-End Authenticated Encryption Mechanism. In Proceedings of the 2023 12th International Conference on Modern Circuits and Systems Technologies (MOCAST), Athens, Greece, 28–30 June 2023. [Google Scholar]
- Yang, G.; Shi, Z.; Chen, C.; Xiong, H.; Li, F.; Hu, H.; Wan, Z. Hardware Optimizations of Fruit-80 Stream Cipher: Smaller than Grain. ACM Trans. Reconfigurable Technol. Syst. 2023, 16, 22. [Google Scholar] [CrossRef]
- Bahadori, M.; Järvinen, K.; Niemi, V. FPGA Implementations of 256-Bit SNOW Stream Ciphers for Postquantum Mobile Security. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 29, 1943–1954. [Google Scholar] [CrossRef]
- Pu, C.; Wall, A.; Choo, K.-K.R.; Ahmed, I.; Lim, S. A Lightweight and Privacy-Preserving Mutual Authentication and Key Agreement Protocol for Internet of Drones Environment. IEEE Internet Things J. 2022, 9, 9918–9933. [Google Scholar] [CrossRef]
- Sun, C.; Liu, J.; Xu, X.; Ma, J. A Privacy-Preserving Mutual Authentication Resisting DoS Attacks in VANETs. IEEE Access 2017, 5, 24012–24022. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tsantikidou, K.; Sklavos, N. Threats, Attacks, and Cryptography Frameworks of Cybersecurity in Critical Infrastructures. Cryptography 2024, 8, 7. https://doi.org/10.3390/cryptography8010007
Tsantikidou K, Sklavos N. Threats, Attacks, and Cryptography Frameworks of Cybersecurity in Critical Infrastructures. Cryptography. 2024; 8(1):7. https://doi.org/10.3390/cryptography8010007
Chicago/Turabian StyleTsantikidou, Kyriaki, and Nicolas Sklavos. 2024. "Threats, Attacks, and Cryptography Frameworks of Cybersecurity in Critical Infrastructures" Cryptography 8, no. 1: 7. https://doi.org/10.3390/cryptography8010007
APA StyleTsantikidou, K., & Sklavos, N. (2024). Threats, Attacks, and Cryptography Frameworks of Cybersecurity in Critical Infrastructures. Cryptography, 8(1), 7. https://doi.org/10.3390/cryptography8010007






