FPGA-Based PUF Designs: A Comprehensive Review and Comparative Analysis
Abstract
:1. Introduction
1.1. Motivations
1.2. Contributions
- Comprehensive Survey of FPGA-Based PUFs: We present a detailed survey encompassing the current and emerging methodologies for FPGA-based physical unclonable function (PUF) designs. Our focus centers on the security applications of PUFs across a wide array of product designs. To ensure the utmost relevance, we conducted a thorough analysis of more than 100 pertinent publications, encapsulating the very latest advancements in the field.
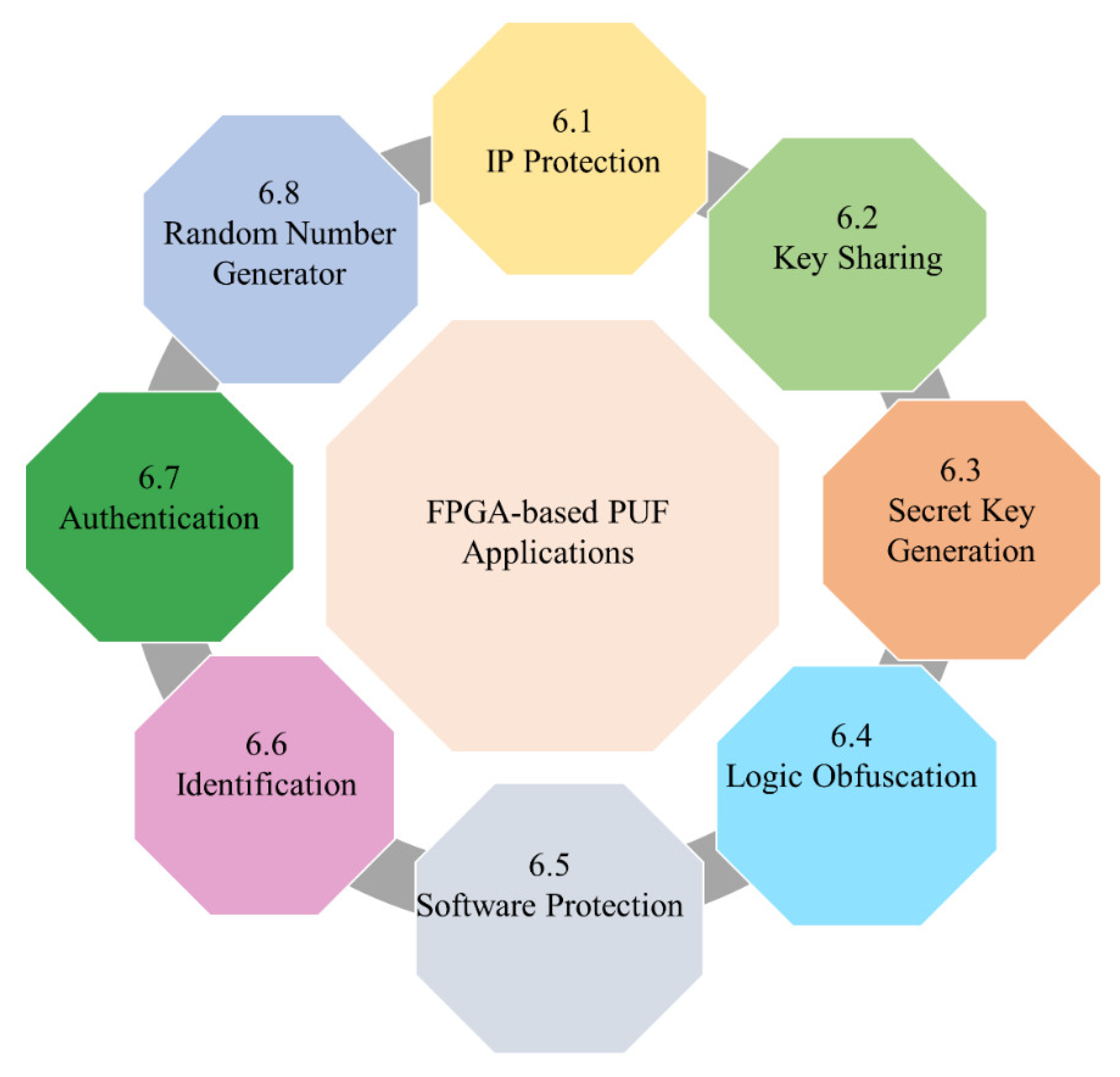
- In-Depth Categorization of PUF Applications: Our study delves deeper by categorizing research papers according to the diverse applications of FPGA-based PUFs, as illustrated in Figure 5. For each application, we place a spotlight on task-specific challenges and proffer well-informed solutions drawn from extensive literature research.
- Critical Field Assessment: In the final section of our work, we provide a critical evaluation of the current state of the field. We not only highlight critical issues but also bring attention to those that remain unresolved. Furthermore, we offer potential solutions, paving the way for further advancements in the field of FPGA-based PUFs. Our research aims to provide clarity and direction, shedding light on the path forward for this critical technology.
1.3. Paper Organization
2. Physical Unclonable Functions (PUFs)
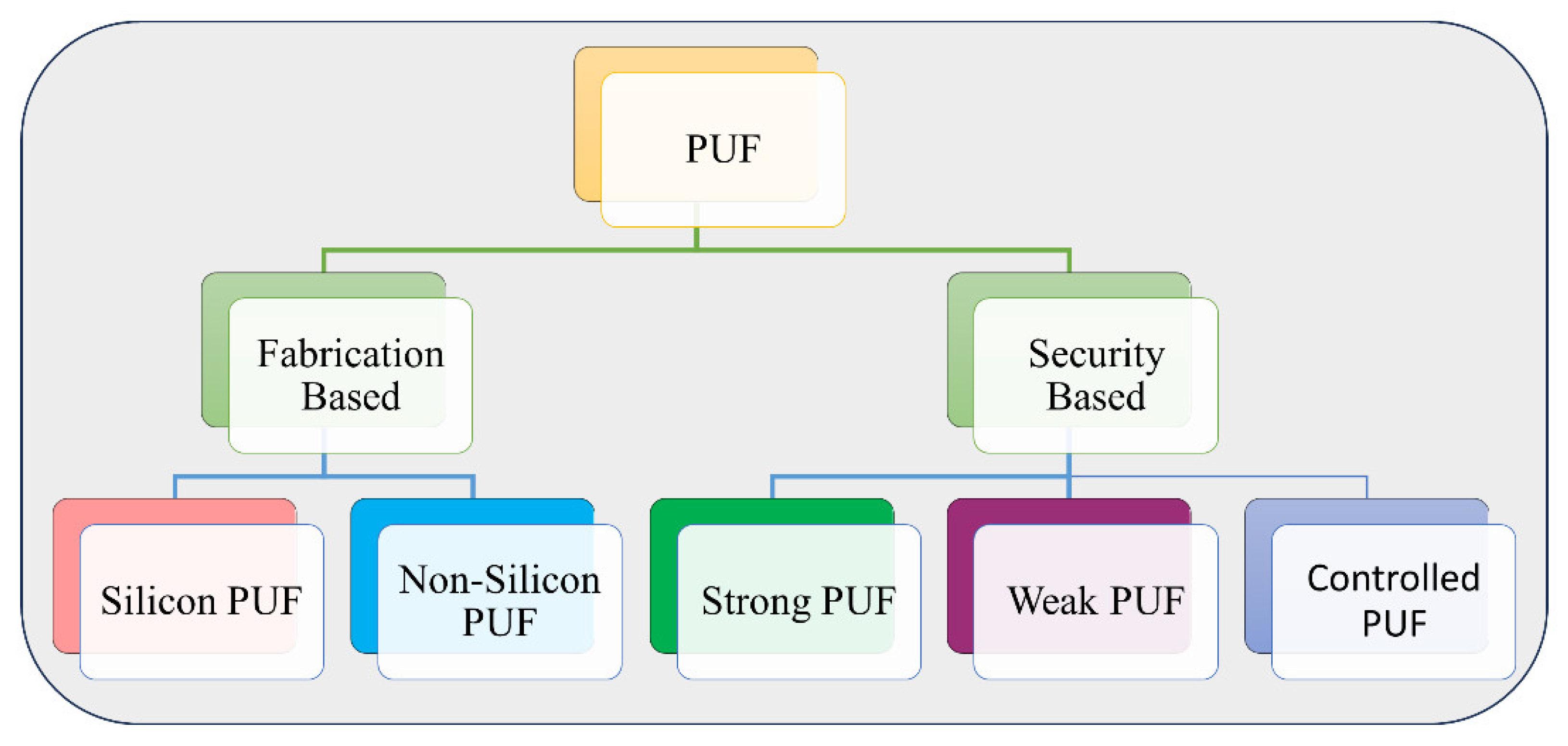
2.1. Classification of PUFs
2.1.1. Based on Fabrication
2.1.2. Based on Security
3. FPGA-Based PUF Implementations
3.1. Delay-Based PUFs
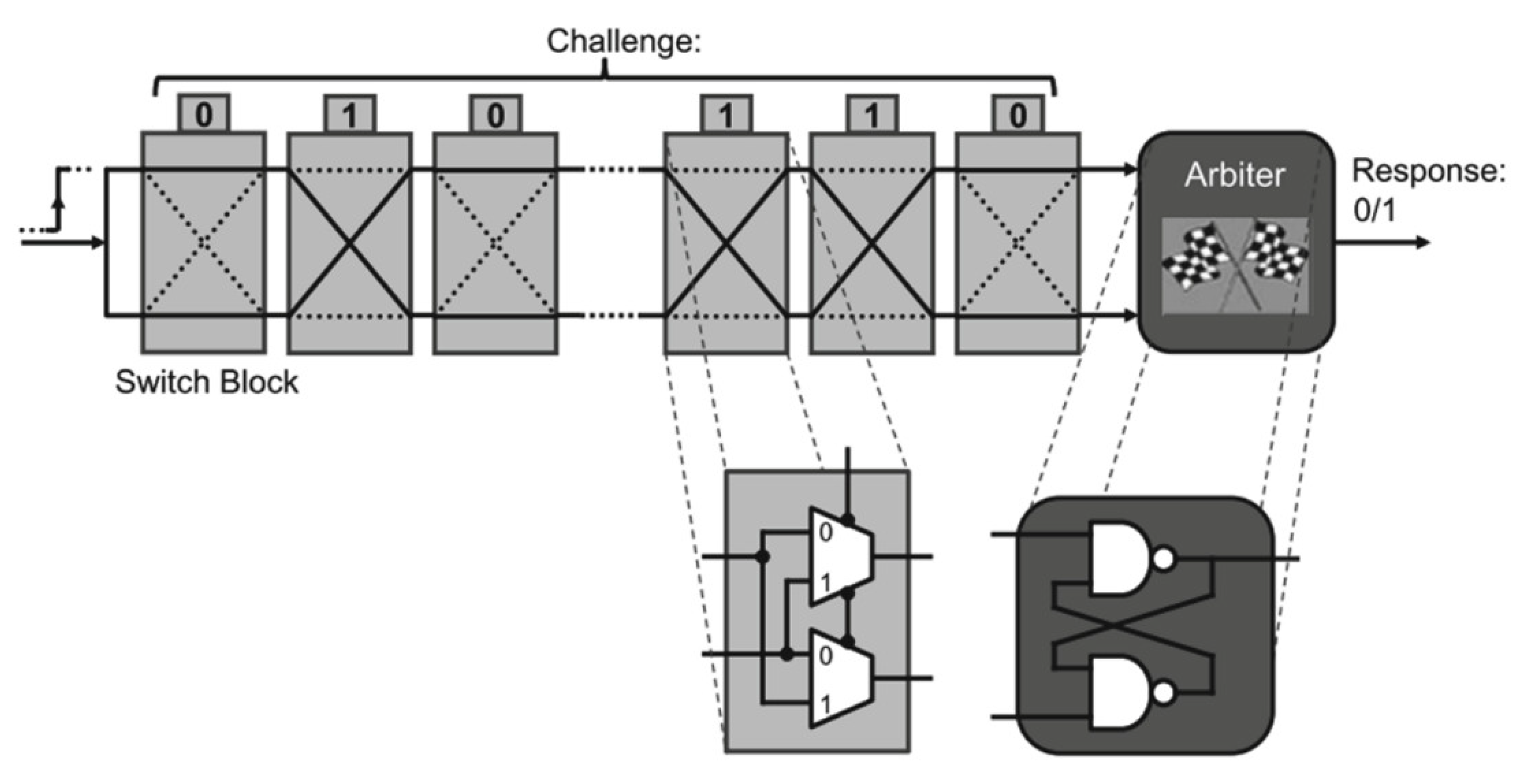
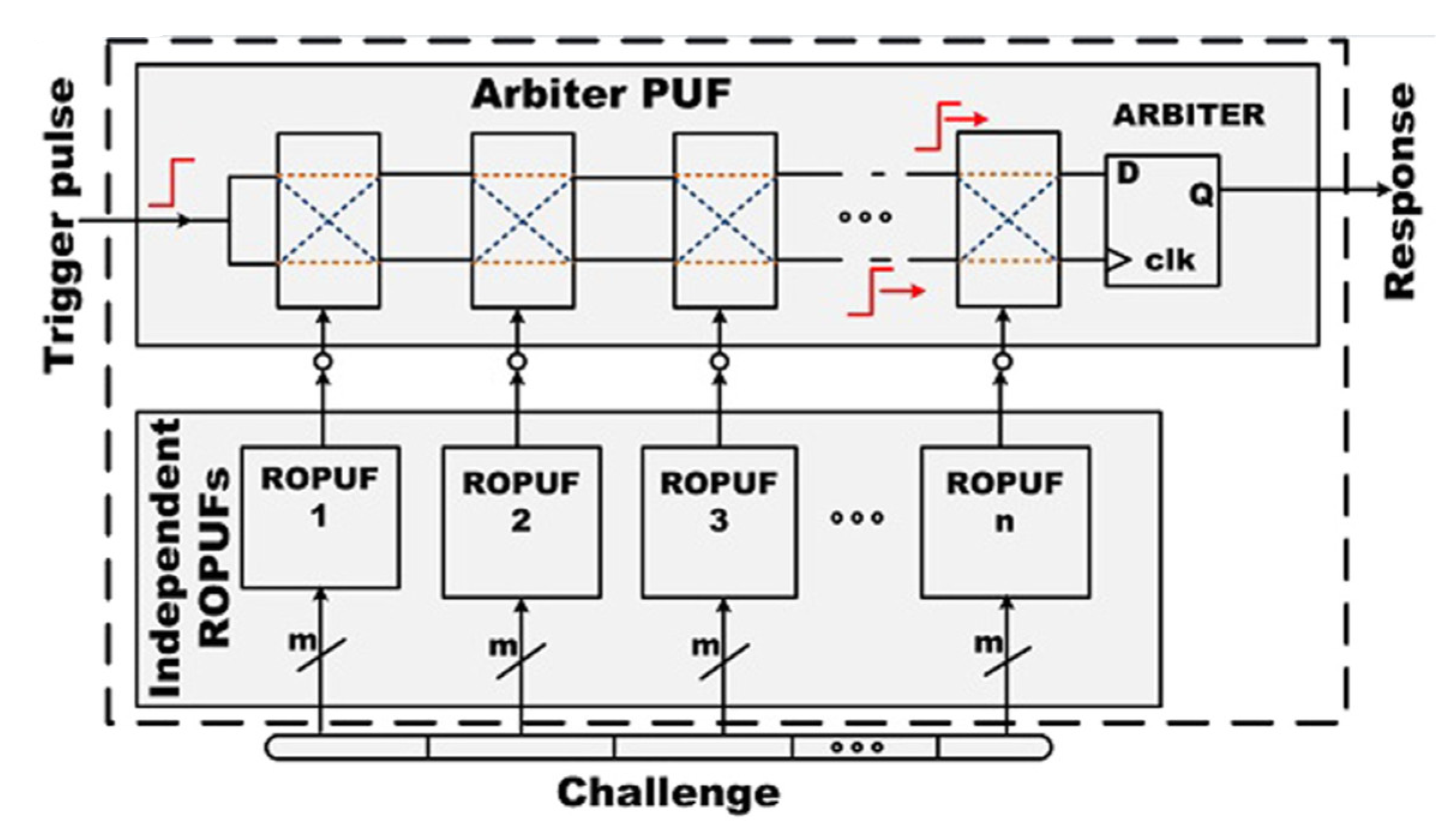
3.1.1. Arbiter PUF
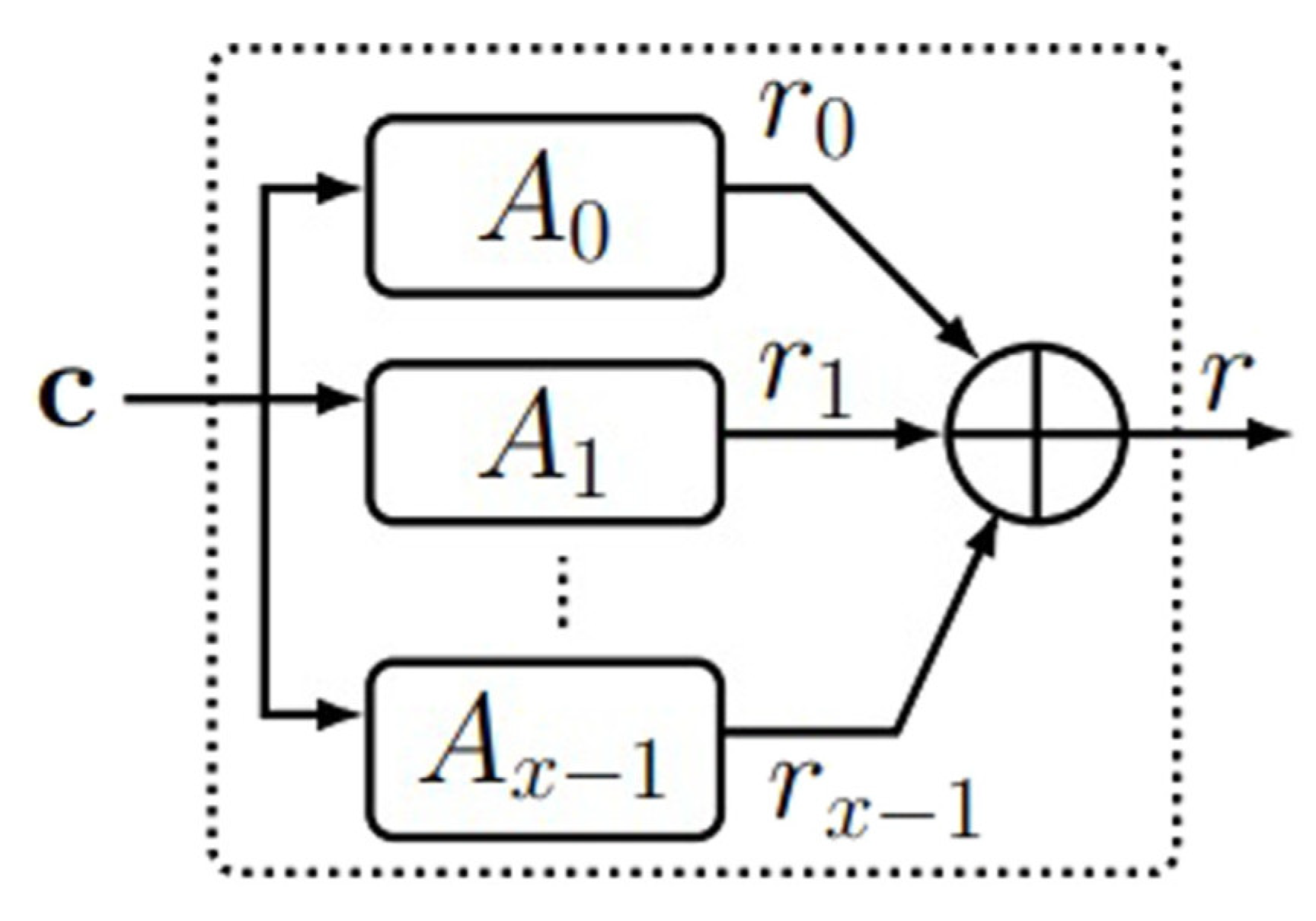
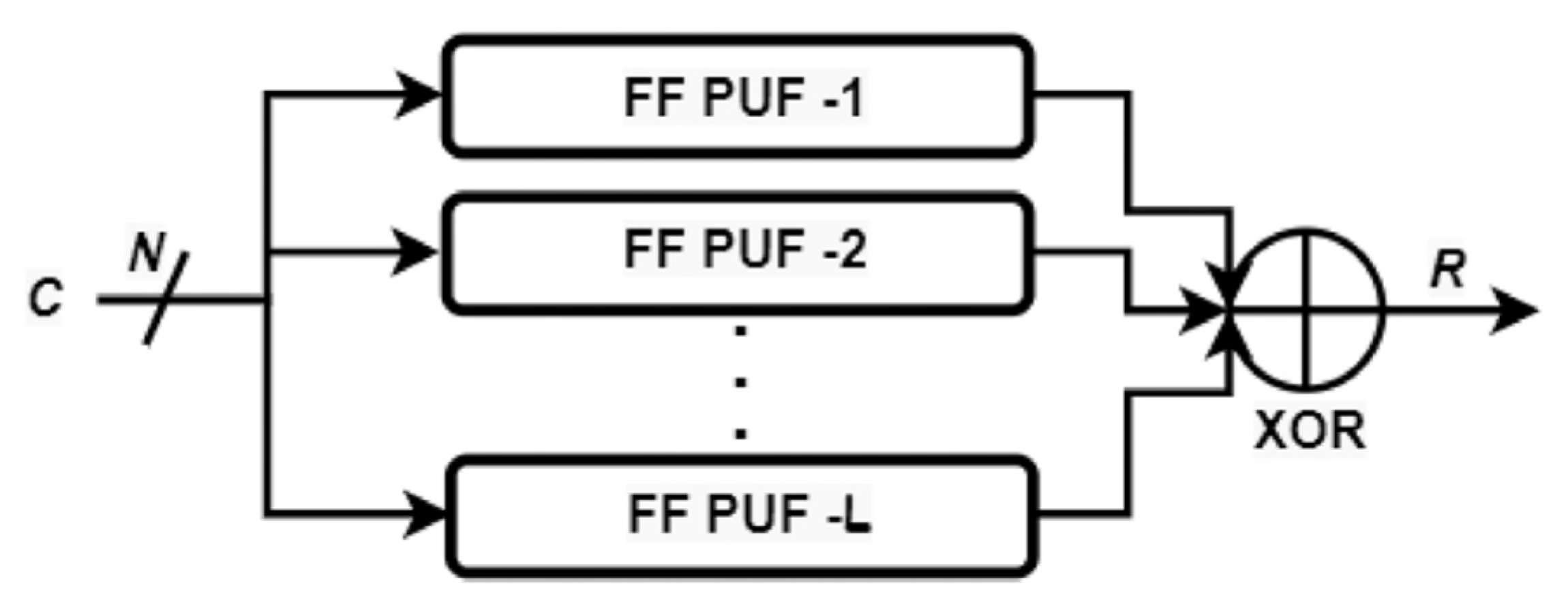
3.1.2. XOR Arbiter PUF
3.1.3. Free-Forward Arbiter PUF
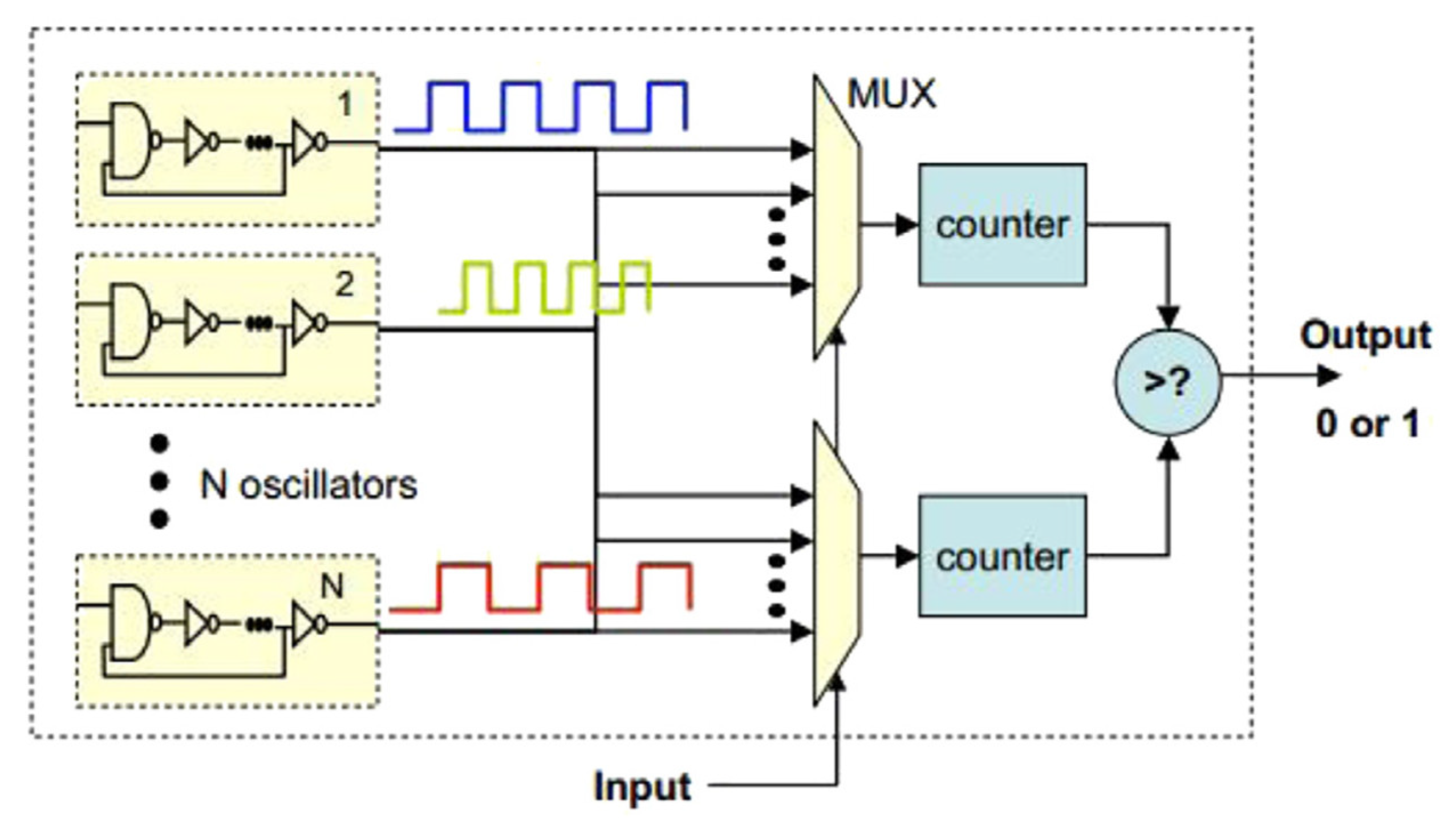
3.1.4. Ring Oscillator PUF
3.1.5. Configurable RO PUF
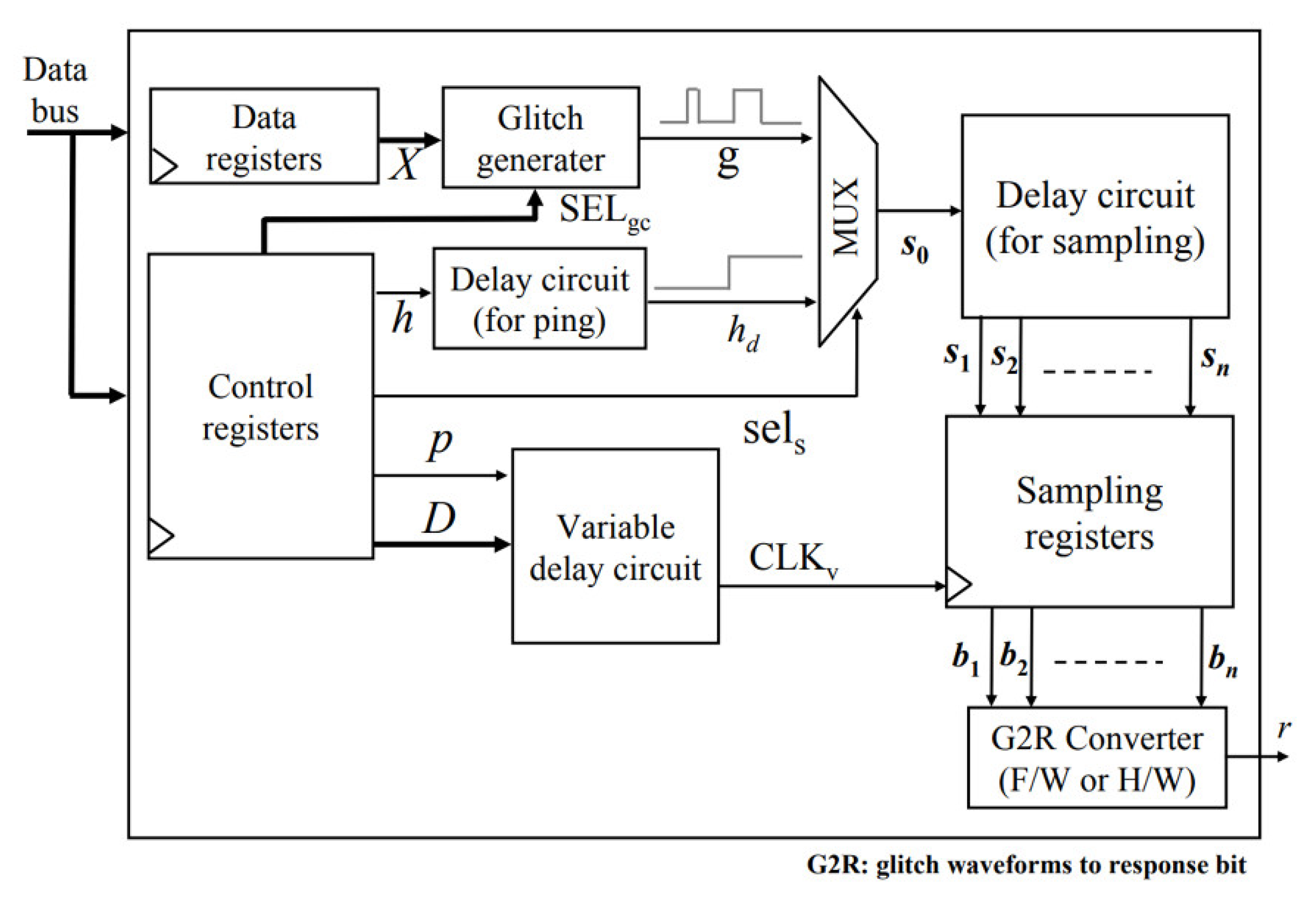
3.1.6. Glitch PUF
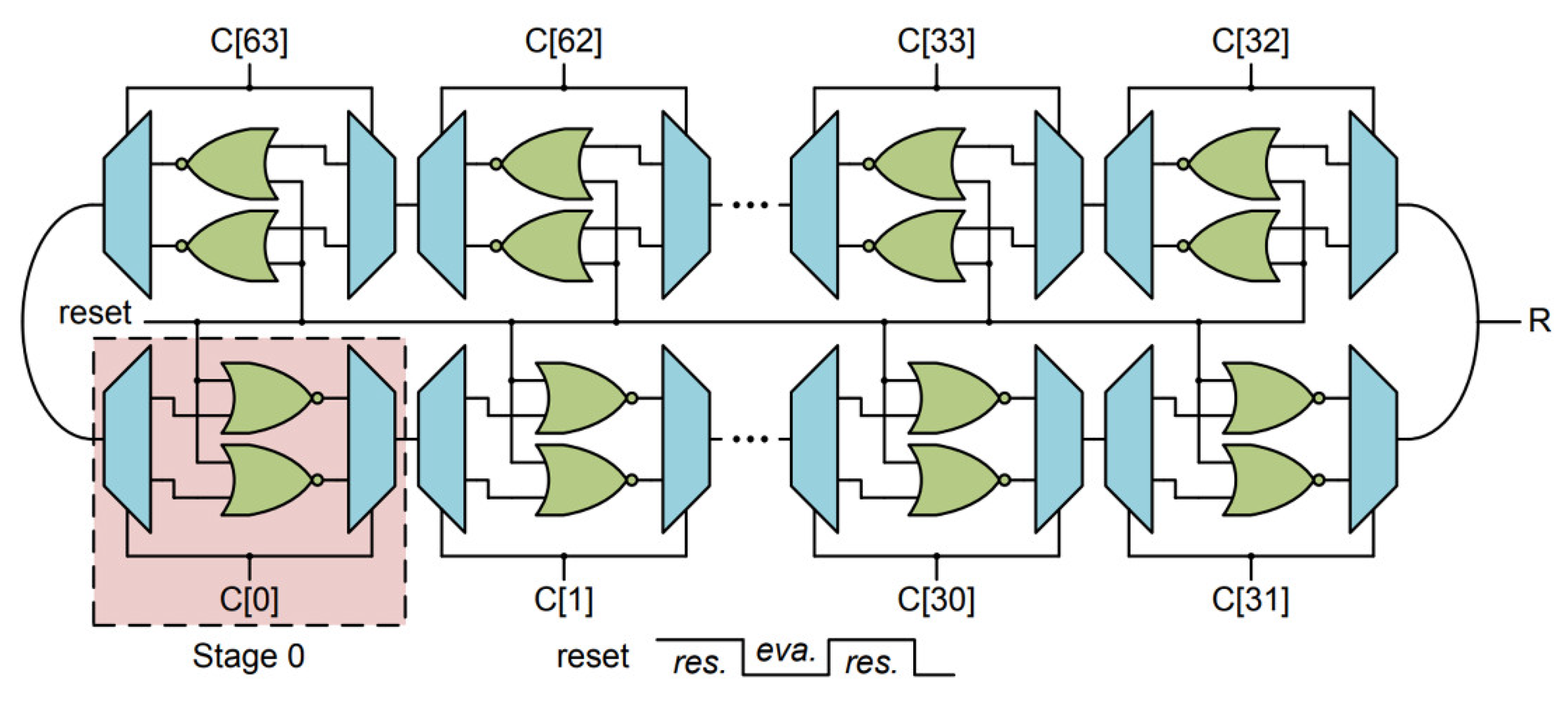
3.1.7. Bistable Ring PUF
3.1.8. PLFSR PUF
3.2. Memory-Based PUFs
3.2.1. SRAM PUF
3.2.2. Flip-Flop PUF
3.2.3. Butterfly PUF
3.3. Combined PUFs
3.3.1. Hybrid PUF
3.3.2. Composite PUF
3.3.3. Double Arbiter PUF
3.4. FPGA-Based PUF Advantages and Challenges
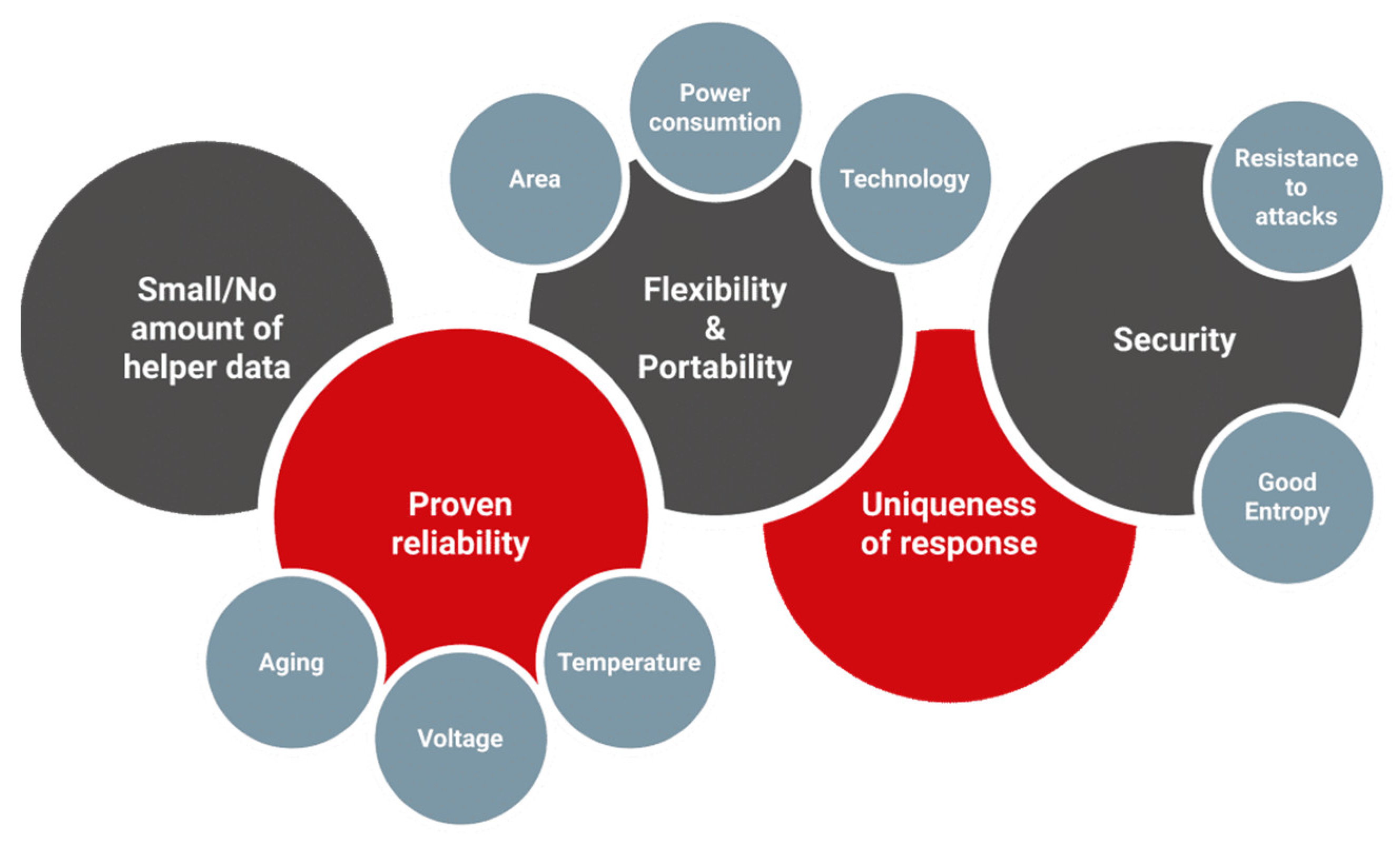
4. PUF Quality Metrics
5. Performance Evaluation and Comparative Analysis
| Types | Design | Uniqueness | Reliability | Uniformity | Bit-Alias | Area (Total Slices) | Res. Bit Length | Target FPGA | Attack-Resistant | Year | |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Ideal Value | 50% | 100% | 50% | 50% | |||||||
| Delay based PUFs | Arbiter PUF | Naveenkumar et al. [92] | 49.88 | 99.20 | 48.74% | - | - | 64 | Artix-7 | ML-based-modeling attack | 2022 |
| Sahoo et al. [101] | 45.25 | 95.93 | 48.30 | - | - | 90 | Spartan-3 | - | 2015 | ||
| Maiti et al. [91] | 7.20 | 99.76 | 55.69 | 19.57 | - | 128 | Virtex-5 | - | 2013 | ||
| Machida et al. [81] | 4.70 | 99.32 | 54.78 | - | 177 | 128 | Virtex-5 | - | 2015 | ||
| Anandakumar et al. [32] | 44.30 | 96.00 | 48.45 | - | 234 | 256 | Spartan-6 | - | 2017 | ||
| Hori et al. [102] | 36.75 | 98.48 | 42.34 | - | - | 128 | Virtex-5 | - | 2010 | ||
| Mahalat et al. [94] | 51.34 | 97.57 | 57.64 | 132 | 64 | Artix-7 | ML-based-modeling attack | 2021 | |||
| Anandakumar et al. [49] | 48.69 | 99.41 | 50.73 | - | 279 | 64 | Artix-7 | ML-based-modeling attack | 2022 | ||
| RO-PUF | Maiti et al. [91] | 47.24 | 99.14 | 50.56 | 50.56 | - | 511 | Spartan-3E | - | 2013 | |
| Anandakumar et al. [32] | 47.13 | 99.16 | 50.61 | - | 82 | 256 | Spartan-6 | - | 2017 | ||
| Merli et al. [97] | 48.51 | 98.28 | - | - | 512 | 128 | Spartan-3E | - | 2010 | ||
| Anandakumar et al. [93] | 48.91 | 97.91 | 49.55 | 49.55 | 107 | 256 | Artix-7 | ML-based-modeling attack | 2022 | ||
| Habib et al. [103] | 48.30 | 97.88 | 50.13 | 51.80 | 747 | 283 | Spartan-3E | - | 2013 | ||
| Yu et al. [104] | 47 | - | - | - | 420 | 64 | Spartan-3E | - | 2012 | ||
| Lee et al. [98] | 50.1 | - | 49.4 | - | - | 64 | Artix-7 | - | 2018 | ||
| Dang et al. [96] | 50.23 | 95.92 | 52.64 | - | - | 32 | Artix-7 | - | 2022 | ||
| Zhang et al. [105] | 49.33 | 95.45 | 49.50 | - | 186 | 136 | Virtex-5 | ML-based-modeling attack | 2018 | ||
| Choudhury et al. [99] | 47.40 | - | 49.20 | 49.10 | - | 124 | Artix-7 | - | 2017 | ||
| Rabiei et al. [95] | 48.49 | 99.55 | 50.99 | - | 210 | 256 | Spartan-6 | Modeling and MITM attack | 2022 | ||
| Karmakar et al. [106] | 49 | 85.95 | 50 | - | 626 (LUT) | 8 | Artix-7 | - | 2023 | ||
| Huang et al. [54] | 48.74 | 98.91 | 49.3 | 49.2 | 12 (LUT) | 128 | Virtex-7 | - | 2023 | ||
| Butterfly PUF | Kumar et al. [72] | 43.16 | 96.20 | - | - | 130 | 50 | Virtex-5 | - | 2008 | |
| Memory based PUFs | Latch PUF | Anandakumar et al. [32] | 48.10 | 99.19 | 50.20 | - | 54 | 256 | Spartan-6 | - | 2017 |
| Ardakani et al. [107] | 49.32 | 98.80 | 44.65 | 44.65 | 128 | 127 | Spartan-3 | - | 2018 | ||
| Anandakumar et al. [93] | 49.47 | 98.29 | 51.02 | 51.02 | 101 | 256 | Artix-7 | ML-based-modeling attack | 2022 | ||
| Habib et al. [108] | 49.24 | 98.87 | - | - | 324 | 256 | Spartan-6 | - | 2015 | ||
| Stanciu et al. [109] | 34.73 | 92.00 | - | - | - | - | Spartan-6 | - | 2016 | ||
| SRAM PUF | Guajardo et al. [19] | 49.97 | 88.00 | - | - | - | 128 | - | - | 2007 | |
| DFF PUF | Khan et al. [110] | 50.2 | 97.89 | - | 49.613 | - | 128 | Artix-7 | - | 2020 | |
| Combined PUFs | Hybrid PUF | Vega et al. [111] | 48.59 | 97.89 | 50.97 | - | - | 1024 | Artix-7 | ML-based-modeling attack | 2023 |
| Khoshroo et al. [77] | 39.63 | 93.63 | 48.30 | 25.20 | - | 128 | Virtex-2 | - | 2013 | ||
| Anandakumar et al. [33] | 49.41 | 99.22 | 50.09 | 50.09 | 257 | 256 | Spartan-6 | ML-based-modeling attack | 2020 | ||
| Tanamoto et al. [112] | 32.52 | 96.96 | 55.66 | - | - | 256 | Spartan-6 | - | 2017 | ||
| Composite PUF | Sahoo et al. [90] | 36.87 | 98.85 | 54.76 | - | - | 64 | Spartan-3 | ML-based-modeling attack | 2015 | |
| Sahoo et al. [80] | 49.04 | 97.48 | 50.07 | - | 1051 | - | Spartan-3 | Chosen-challenge attack | 2014 | ||
| Multi-PUF | Ma et al. [113] | 40.60 | - | 30.03 | - | - | 32 | Artix-7 | ML-based-modeling attack | 2018 | |
| DAPUF | Machida et al. [81] | 50.24 | 88.20 | 53.94 | - | 436 | 128 | Virtex-5 | ML-based-modeling attack | 2015 | |
| FF-APUF | Gu et al. [114] | 41.53 | 95.50 | - | - | 2816 | 64 | Artix-7 | ML-based-modeling attack | 2021 | |
| Cascaded PUF | CaPUF | Nassar et al. [115] | 55.63 | 92.54 | 50.06 | - | 5723 (LUT) | 16 | Virtex-7 | ML-based-modeling attack | 2022 |
| Configurable PUF | CT-PUF | Zhang et al. [100] | ~49 | ~99 | ~48 | - | 731 (LUT) | 64 | Zedboard | ML-based-modeling attack | 2022 |
| CRO-PUF | Jeeru et al. [116] | 35.78 | 99.21 | 49.86 | 45 | - | 128 | Spartan-3E | - | 2019 | |
| Feedback-based Lightweight PUF | FLAM-PUF | Wu et al. [117] | 49.85 | 96.58 | 49.99 | - | (1955) Gate Equivalent | 128 | - | ML-based-modeling attack | 2022 |
6. FPGA Based PUF Applications
6.1. IP Protection
6.2. Key Sharing
6.3. Secret Key Generation
6.4. Logic Obfuscation
6.5. Software Protection
6.6. Identification
6.7. Authentication
6.8. Random Number Generator
7. Challenges and Future Directions
7.1. Challenges in FPGA-Based PUF Designs
7.2. Variability and Aging
7.3. Response Stability
7.4. Resource Utilization
7.5. Randomness Assurance
7.6. Secure Key Storage
7.7. Testability
7.8. Configuration Management
Future Directions
7.9. Improved Reliability and Stability
7.10. Enhanced Security against Modeling Attacks
7.11. Resource-Efficient Designs
7.12. Post-Quantum Security
7.13. Standardization
8. Conclusions
- Environmental variables including temperature, voltage, and electromagnetic interference can influence PUF reactions, making them less dependable under difficult circumstances.
- Due to manufacturing irregularities, FPGA-based PUFs may display exceptions in their responses, which may affect their dependability and consistency.
- It can be difficult to choose the best design for a given application due to the diversity of available FPGA-based PUF designs, which can prevent standardization.
- PUFs on FPGAs can increase the overall cost of a device or system, which makes them less cost-effective for particular applications.
- When integrating PUFs into already-existing FPGA designs, compatibility, design changes, and potential interaction with other functions may need to be carefully taken into account.
- Some FPGA-based PUF designs could be difficult to scale in order to support applications that demand large numbers of PUF instances.
Author Contributions
Funding
Conflicts of Interest
References
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, Privacy and Trust in Internet of Things: The Road Ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Radomirovic, S. Towards a Model for Security and Privacy in the Internet of Things. In Proceedings of the First International Workshop on the Security of the Internet of Things, Tokyo, Japan, 29 November 2010. [Google Scholar]
- Wurm, J.; Hoang, K.; Arias, O.; Sadeghi, A.-R.; Jin, Y. Security Analysis on Consumer and Industrial IoT Devices. In Proceedings of the 2016 21st Asia and South Pacific Design Automation Conference (ASP-DAC), Macao, China, 25–28 January 2016; pp. 519–524. [Google Scholar]
- Shrouf, F.; Ordieres, J.; Miragliotta, G. Smart Factories in Industry 4.0: A Review of the Concept and of Energy Management Approached in Production Based on the Internet of Things Paradigm. In Proceedings of the 2014 IEEE International Conference on Industrial Engineering and Engineering Management, Selangor, Malaysia, 9–12 December 2014; pp. 697–701. [Google Scholar]
- Zerrouki, F.; Ouchani, S.; Bouarfa, H. A Survey on Silicon PUFs. J. Syst. Archit. 2022, 127, 102514. [Google Scholar] [CrossRef]
- Pappu, R.; Recht, B.; Taylor, J.; Gershenfeld, N. Physical One-Way Functions. Science 2002, 297, 2026–2030. [Google Scholar] [CrossRef] [PubMed]
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Silicon Physical Random Functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; Association for Computing Machinery: New York, NY, USA, 2002; pp. 148–160. [Google Scholar]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF Based Authentication and Key Exchange Protocol for IoT Without Explicit CRPs in Verifier Database. IEEE Trans. Dependable Secur. Comput. 2019, 16, 424–437. [Google Scholar] [CrossRef]
- Suh, G.E.; Devadas, S. Physical Unclonable Functions for Device Authentication and Secret Key Generation. In Proceedings of the 44th Annual Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; Association for Computing Machinery: New York, NY, USA, 2007; pp. 9–14. [Google Scholar]
- Qureshi, M.A.; Munir, A. PUF-RAKE: A PUF-Based Robust and Lightweight Authentication and Key Establishment Protocol. IEEE Trans. Dependable Secur. Comput. 2021, 19, 2457–2475. [Google Scholar] [CrossRef]
- Usmani, M.A.; Keshavarz, S.; Matthews, E.; Shannon, L.; Tessier, R.; Holcomb, D.E. Efficient PUF-Based Key Generation in FPGAs Using Per-Device Configuration. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 364–375. [Google Scholar] [CrossRef]
- Assaf, T.; Al-Dweik, A.; Iraqi, Y.; Jangsher, S.; Pandey, A.; Giacalone, J.-P.; Abulibdeh, E.E.; Saleh, H.; Mohammad, B. High-Rate Secret Key Generation Using Physical Layer Security and Physical Unclonable Functions. IEEE Open J. Commun. Soc. 2023, 4, 209–225. [Google Scholar] [CrossRef]
- Maes, R.; Van Herrewege, A.; Verbauwhede, I. PUFKY: A Fully Functional PUF-Based Cryptographic Key Generator. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2012, Leuven, Belgium, 9–12 September 2012; Prouff, E., Schaumont, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 302–319. [Google Scholar]
- Anchana, U.K.; Mogireddy, M.; Kadavergu, E.; Singh, S. Design of PUF Based Chaotic Random Number Generator. In Proceedings of the 2023 Second International Conference on Electrical, Electronics, Information and Communication Technologies (ICEEICT), Trichirappalli, India, 5–7 April 2023; pp. 1–7. [Google Scholar]
- Dheeraj, A.; Das, P.; Kumar, K.; Kalanadhabhatta, S.; Acharyya, A. Modeling Attacks Resilient Multiple PUF-CPRNG Architecture Design Methodology. In Proceedings of the 2022 IEEE 35th International System-on-Chip Conference (SOCC), Belfast, UK, 5–8 September 2022; pp. 1–6. [Google Scholar]
- Kalanadhabhatta, S.; Kumar, D.; Anumandla, K.K.; Reddy, S.A.; Acharyya, A. PUF-Based Secure Chaotic Random Number Generator Design Methodology. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2020, 28, 1740–1744. [Google Scholar] [CrossRef]
- Sutar, S.; Raha, A.; Kulkarni, D.; Shorey, R.; Tew, J.; Raghunathan, V. D-PUF: An Intrinsically Reconfigurable DRAM PUF for Device Authentication and Random Number Generation. ACM Trans. Embed. Comput. Syst. 2017, 17, 17. [Google Scholar] [CrossRef]
- Roy, D.B.; Bhasin, S.; Nikolić, I.; Mukhopadhyay, D. Combining PUF with RLUTs: A Two-Party Pay-per-Device IP Licensing Scheme on FPGAs. ACM Trans. Embed. Comput. Syst. 2019, 18, 1–22. [Google Scholar] [CrossRef]
- Guajardo, J.; Kumar, S.S.; Schrijen, G.-J.; Tuyls, P. FPGA Intrinsic PUFs and Their Use for IP Protection. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2007, Vienna, Austria, 10–13 September 2007; Paillier, P., Verbauwhede, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 63–80. [Google Scholar]
- Suragani, R.; Nazarenko, E.; Anagnostopoulos, N.A.; Mexis, N.; Kavun, E.B. Identification and Classification of Corrupted PUF Responses via Machine Learning. In Proceedings of the 2022 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 27–30 June 2022; pp. 137–140. [Google Scholar]
- Rostami, M.; Majzoobi, M.; Koushanfar, F.; Wallach, D.S.; Devadas, S. Robust and Reverse-Engineering Resilient PUF Authentication and Key-Exchange by Substring Matching. IEEE Trans. Emerg. Top. Comput. 2014, 2, 37–49. [Google Scholar] [CrossRef]
- Roy, S.; Das, D.; Mondal, A.; Mahalat, M.H.; Sen, B.; Sikdar, B. PLAKE: PUF-Based Secure Lightweight Authentication and Key Exchange Protocol for IoT. IEEE Internet Things J. 2023, 10, 8547–8559. [Google Scholar] [CrossRef]
- Sun, D.-Z.; Gao, Y.-N.; Tian, Y. On the Security of a PUF-Based Authentication and Key Exchange Protocol for IoT Devices. Sensors 2023, 23, 6559. [Google Scholar] [CrossRef] [PubMed]
- Yang, K.; Forte, D.; Tehranipoor, M.M. CDTA: A Comprehensive Solution for Counterfeit Detection, Traceability, and Authentication in the IoT Supply Chain. ACM Trans. Des. Autom. Electron. Syst. 2017, 22, 1–31. [Google Scholar] [CrossRef]
- Shamsoshoara, A.; Korenda, A.; Afghah, F.; Zeadally, S. A Survey on Physical Unclonable Function (PUF)-Based Security Solutions for Internet of Things. Comput. Netw. 2020, 183, 107593. [Google Scholar] [CrossRef]
- Yalli, J.S.; Hasan, M.H. A Unique PUF Authentication Protocol Based Fuzzy Logic Categorization for Internet of Things (IOT) Devices. In Proceedings of the 2023 12th International Conference on Software and Computer Applications, Kuantan, Malaysia, 23–25 February 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 246–252. [Google Scholar]
- Babaei, A.; Schiele, G. Physical Unclonable Functions in the Internet of Things: State of the Art and Open Challenges. Sensors 2019, 19, 3208. [Google Scholar] [CrossRef]
- Al-Meer, A.; Al-Kuwari, S. Physical Unclonable Functions (PUF) for IoT Devices. ACM Comput. Surv. 2023, 55, 314. [Google Scholar] [CrossRef]
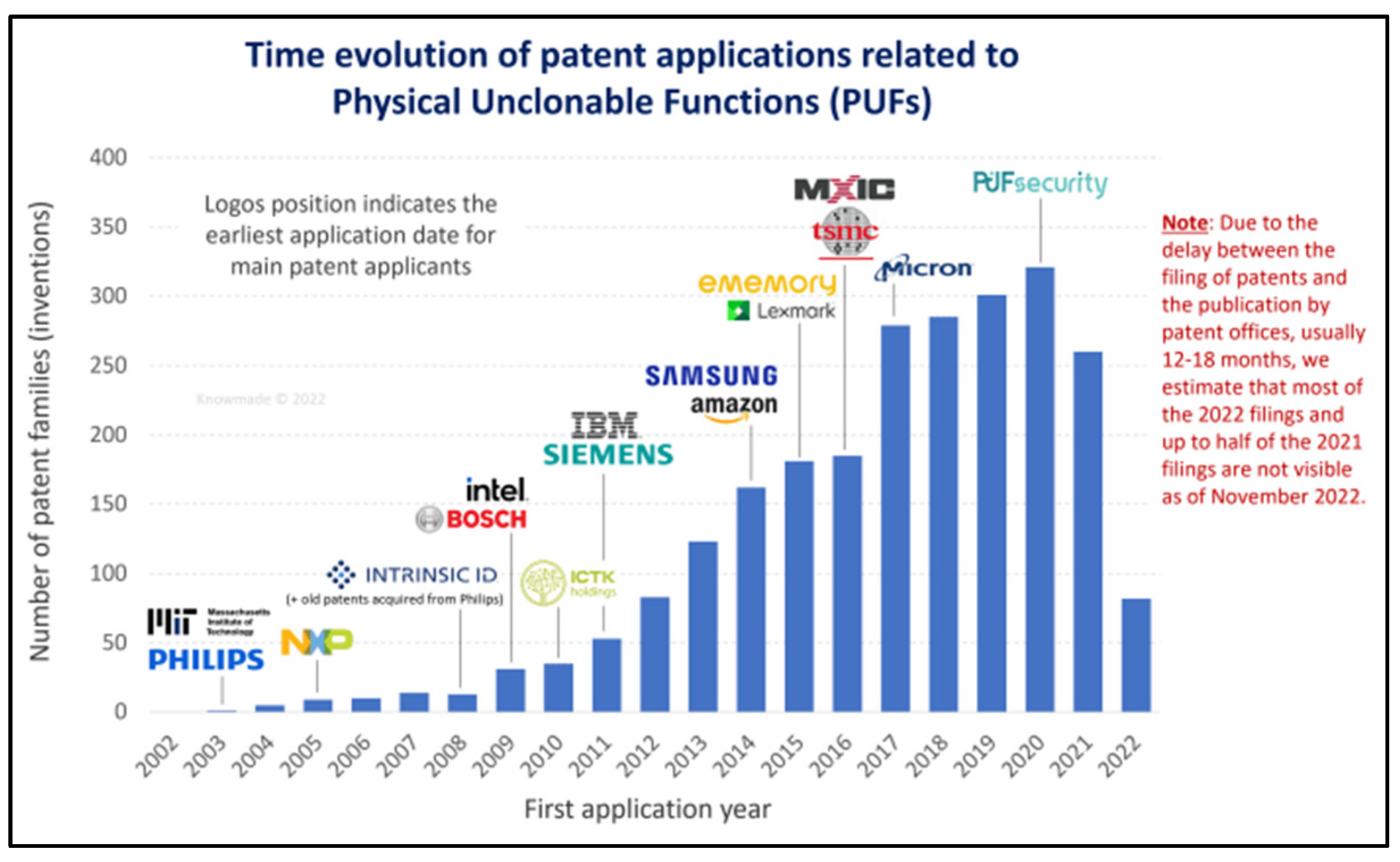
- Knowmade Physical Unclonable Functions for Securing Our Digital World. Available online: https://www.knowmade.com/technology-news/semiconductor-news/memory-news/physical-unclonable-functions-pufs-a-short-review-of-innovators-who-are-making-the-digital-revolution-more-secure/ (accessed on 31 July 2023).
- Physically Unclonable Function—PUF Solution. Available online: https://www.secure-ic.com/products/issp/security-ip/key-management/puf-ip/ (accessed on 12 August 2023).
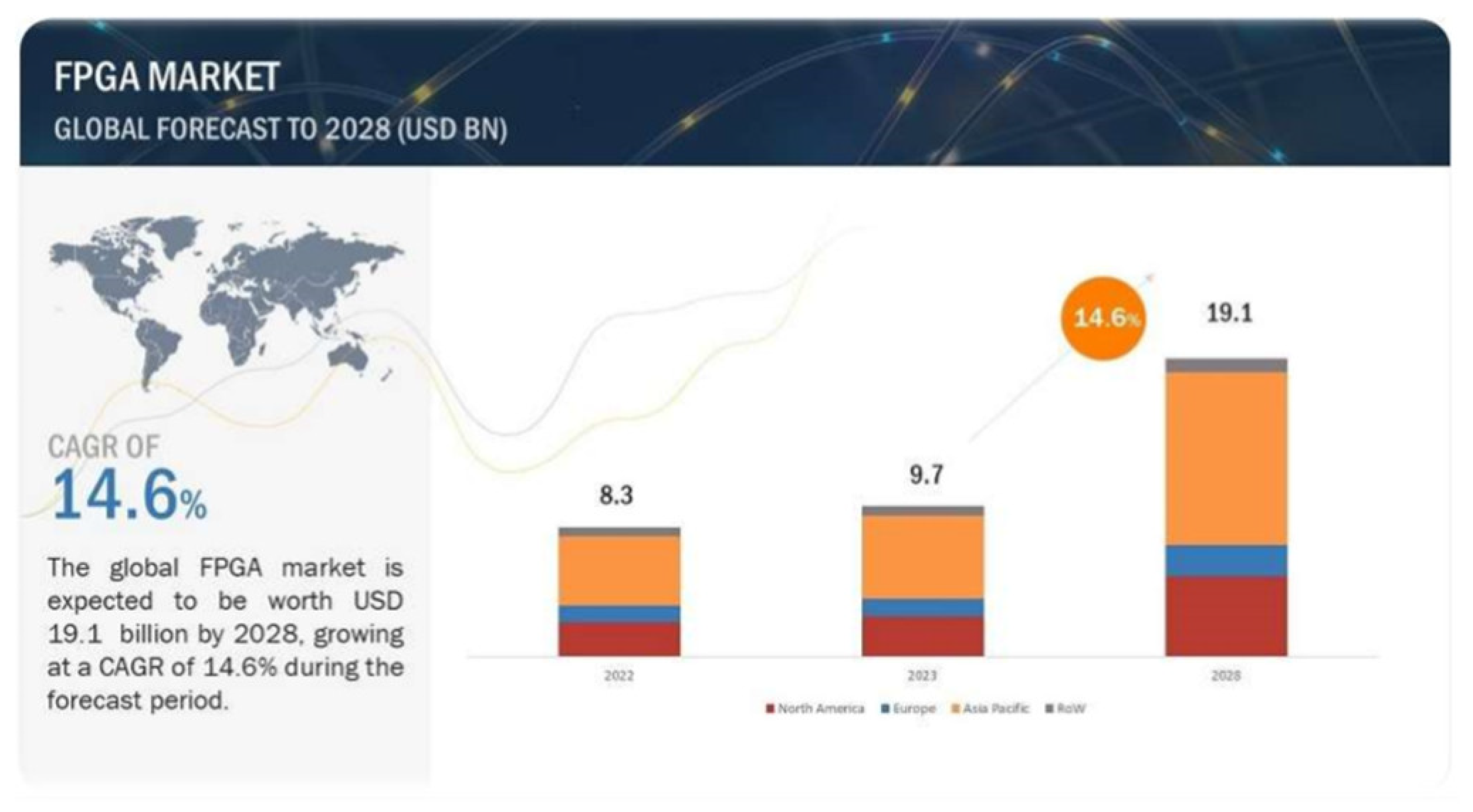
- FPGA Industry Worth $19.1 Billion by 2028. Available online: https://www.marketsandmarkets.com/PressReleases/fpga.asp (accessed on 17 August 2023).
- Anandakumar, N.N.; Hashmi, M.S.; Sanadhya, S.K. Compact Implementations of FPGA-Based PUFs with Enhanced Performance. In Proceedings of the 2017 30th International Conference on VLSI Design and 2017 16th International Conference on Embedded Systems (VLSID), Hyderabad, India, 7–11 January 2017; pp. 161–166. [Google Scholar]
- Anandakumar, N.N.; Hashmi, M.S.; Sanadhya, S.K. Efficient and Lightweight FPGA-Based Hybrid PUFs with Improved Performance. Microprocess. Microsyst. 2020, 77, 103180. [Google Scholar] [CrossRef]
- Nalla Anandakumar, N.; Sanadhya, S.K.; Hashmi, M.S. FPGA-Based True Random Number Generation Using Programmable Delays in Oscillator-Rings. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 570–574. [Google Scholar] [CrossRef]
- Joshi, S.; Mohanty, S.P.; Kougianos, E. Everything You Wanted to Know About PUFs. IEEE Potentials 2017, 36, 38–46. [Google Scholar] [CrossRef]
- Zhang, J.-L.; Qu, G.; Lv, Y.-Q.; Zhou, Q. A Survey on Silicon PUFs and Recent Advances in Ring Oscillator PUFs. J. Comput. Sci. Technol. 2014, 29, 664–678. [Google Scholar] [CrossRef]
- Strong PUFs: Models, Constructions, and Security Proofs|SpringerLink. Available online: https://link.springer.com/chapter/10.1007/978-3-642-14452-3_4 (accessed on 23 October 2023).
- Mukhopadhyay, D. PUFs as Promising Tools for Security in Internet of Things. IEEE Des. Test 2016, 33, 103–115. [Google Scholar] [CrossRef]
- Yehoshuva, C.; Raja Adhithan, R.; Nalla Anandakumar, N. A Survey of Security Attacks on Silicon Based Weak PUF Architectures. In Proceedings of the Security in Computing and Communications, Chennai, India, 14–17 October 2020; Thampi, S.M., Wang, G., Rawat, D.B., Ko, R., Fan, C.-I., Eds.; Springer: Singapore, 2021; pp. 107–122. [Google Scholar]
- Wachsmann, C.; Sadeghi, A.-R. Physically Unclonable Functions (PUFs): Applications, Models, and Future Directions; Synthesis Lectures on Information Security, Privacy, and Trust; Springer International Publishing: Cham, Switzerland, 2015; ISBN 978-3-031-01216-7. [Google Scholar]
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Controlled Physical Unknown Functions: Applications to Secure Smartcards and Certified Execution. Available online: https://api.semanticscholar.org/CorpusID:9153005 (accessed on 23 October 2023).
- Morozov, S.; Maiti, A.; Schaumont, P. An Analysis of Delay Based PUF Implementations on FPGA. In Proceedings of the Reconfigurable Computing: Architectures, Tools and Applications, Bangkok, Thailand, 17–19 March 2010; Sirisuk, P., Morgan, F., El-Ghazawi, T., Amano, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 382–387. [Google Scholar]
- Morozov, S.; Maiti, A.; Schaumont, P. A Comparative Analysis of Delay Based PUF Implementations on FPGA. 2009. Available online: https://eprint.iacr.org/2009/629 (accessed on 23 October 2023).
- Zhang, J.; Wu, Q.; Lyu, Y.; Zhou, Q.; Cai, Y.; Lin, Y.; Qu, G. Design and Implementation of a Delay-Based PUF for FPGA IP Protection. In Proceedings of the 2013 International Conference on Computer-Aided Design and Computer Graphics, Guangzhou, China, 16–18 November 2013; ISBN 978-1-4799-2576-6. [Google Scholar]
- Lee, J.W.; Lim, D.; Gassend, B.; Suh, G.E.; van Dijk, M.; Devadas, S. A Technique to Build a Secret Key in Integrated Circuits for Identification and Authentication Applications. In Proceedings of the 2004 Symposium on VLSI Circuits. Digest of Technical Papers (IEEE Cat. No.04CH37525), Honolulu, HI, USA, 17–19 June 2004; pp. 176–179. [Google Scholar]
- Hemavathy, S.; Bhaaskaran, V.S.K. Arbiter PUF—A Review of Design, Composition, and Security Aspects. IEEE Access 2023, 11, 33979–34004. [Google Scholar] [CrossRef]
- Kulkarni, S.; Vani, R.M.; Hunagund, P.V. Designing of Arbiter PUF for Securing IP and IoT Devices. In Proceedings of the Data Intelligence and Cognitive Informatics, Tirunelveli, India, 8–9 July 2020; Jeena Jacob, I., Kolandapalayam Shanmugam, S., Piramuthu, S., Falkowski-Gilski, P., Eds.; Springer: Singapore, 2021; pp. 131–138. [Google Scholar]
- Shariffuddin, S.k.; Sivamangai, N.M.; Napolean, A.; Naveenkumar, R.; Kamalnath, S.; Saranya, G. Review on Arbiter Physical Unclonable Function and Its Implementation in FPGA for IoT Security Applications. In Proceedings of the 2022 6th International Conference on Devices, Circuits and Systems (ICDCS), Coimbatore, India, 21–22 April 2022; pp. 369–374. [Google Scholar]
- Anandakumar, N.N.; Hashmi, M.S.; Chaudhary, M.A. Implementation of Efficient XOR Arbiter PUF on FPGA With Enhanced Uniqueness and Security. IEEE Access 2022, 10, 129832–129842. [Google Scholar] [CrossRef]
- Becker, G.T. The Gap Between Promise and Reality: On the Insecurity of XOR Arbiter PUFs. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2015, Saint-Malo, France, 13–16 September 2015; Güneysu, T., Handschuh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 535–555. [Google Scholar]
- Avvaru, S.V.S.; Parhi, K.K. Feed-Forward XOR PUFs: Reliability and Attack-Resistance Analysis. In Proceedings of the 2019 on Great Lakes Symposium on VLSI, Tysons Corner, VA, USA, 9–11 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 287–290. [Google Scholar]
- Avvaru, S.V.S.; Zeng, Z.; Parhi, K.K. Homogeneous and Heterogeneous Feed-Forward XOR Physical Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2485–2498. [Google Scholar] [CrossRef]
- Maiti, A.; Casarona, J.; McHale, L.; Schaumont, P. A Large Scale Characterization of RO-PUF. In Proceedings of the 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Anaheim, CA, USA, 13–14 June 2010; pp. 94–99. [Google Scholar]
- Huang, Z.; Bian, J.; Lin, Y.; Liang, H.; Ni, T. Design Guidelines and Feedback Structure of Ring Oscillator PUF for Performance Improvement. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2023. Early Access. [Google Scholar] [CrossRef]
- Martínez-Rodríguez, M.C.; Rojas-Muñoz, L.F.; Camacho-Ruiz, E.; Sánchez-Solano, S.; Brox, P. Efficient RO-PUF for Generation of Identifiers and Keys in Resource-Constrained Embedded Systems. Cryptography 2022, 6, 51. [Google Scholar] [CrossRef]
- Maiti, A.; Schaumont, P. Improved Ring Oscillator PUF: An FPGA-Friendly Secure Primitive. J. Cryptol. 2011, 24, 375–397. [Google Scholar] [CrossRef]
- Gao, M.; Lai, K.; Qu, G. A Highly Flexible Ring Oscillator PUF. In Proceedings of the 51st Annual Design Automation Conference, San Francisco, CA, USA, 1–5 June 2014; Association for Computing Machinery: New York, NY, USA, 2014; pp. 1–6. [Google Scholar]
- Suzuki, D.; Shimizu, K. The Glitch PUF: A New Delay-PUF Architecture Exploiting Glitch Shapes. In Proceedings of the Cryptographic Hardware and Embedded Systems, CHES 2010, Santa Barbara, CA, USA, 17–20 August 2010; Mangard, S., Standaert, F.-X., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 366–382. [Google Scholar]
- Glitch PUF: Extracting Information from Usually Unwanted Glitches. Available online: https://www.jstage.jst.go.jp/article/transfun/E95.A/1/E95.A_1_223/_article (accessed on 23 October 2023).
- Nozaki, Y.; Takemoto, S.; Ikezaki, Y.; Yoshikawa, M. Performance Evaluation of Unrolled Cipher Based Glitch PUF Implemented on Virtex-7. In Proceedings of the 2021 International Symposium on Devices, Circuits and Systems (ISDCS), Higashihiroshima, Japan, 21 March 2021; pp. 1–4. [Google Scholar]
- Chen, Q.; Csaba, G.; Lugli, P.; Schlichtmann, U.; Rührmair, U. The Bistable Ring PUF: A New Architecture for Strong Physical Unclonable Functions. In Proceedings of the 2011 IEEE International Symposium on Hardware-Oriented Security and Trust, San Diego, CA, USA, 5–6 June 2011; Available online: https://ieeexplore.ieee.org/document/5955011 (accessed on 27 September 2023).
- Yamamoto, D.; Takenaka, M.; Sakiyama, K.; Torii, N. Security Evaluation of Bistable Ring PUFs on FPGAs Using Differential and Linear Analysis. In Proceedings of the 2014 Federated Conference on Computer Science and Information Systems, Warsaw, Poland, 7–10 September 2014; pp. 911–918. [Google Scholar]
- Chen, Q.; Csaba, G.; Lugli, P.; Schlichtmann, U.; Rührmair, U. Characterization of the Bistable Ring PUF. In Proceedings of the 2012 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 12–16 March 2012; pp. 1459–1462. [Google Scholar]
- Xu, X.; Rührmair, U.; Holcomb, D.E.; Burleson, W. Security Evaluation and Enhancement of Bistable Ring PUFs. In Proceedings of the Radio Frequency Identification, New York, NY, USA, 23–24 June 2015; Mangard, S., Schaumont, P., Eds.; Springer International Publishing: Cham, Switzerland, 2015; pp. 3–16. [Google Scholar]
- Hori, Y.; Kang, H.; Katashita, T.; Satoh, A. Pseudo-LFSR PUF: A Compact, Efficient and Reliable Physical Unclonable Function. In Proceedings of the 2011 International Conference on Reconfigurable Computing and FPGAs, Cancun, Mexico, 30 November–2 December 2011; pp. 223–228. [Google Scholar]
- Ogasahara, Y.; Hori, Y.; Katashita, T.; Iizuka, T.; Awano, H.; Ikeda, M.; Koike, H. Implementation of Pseudo-Linear Feedback Shift Register-Based Physical Unclonable Functions on Silicon and Sufficient Challenge–Response Pair Acquisition Using Built-In Self-Test before Shipping. Integration 2020, 71, 144–153. [Google Scholar] [CrossRef]
- Zhou, T.; Ji, Y.; Chen, M.; Li, Y. PL-MRO PUF: High Speed Pseudo-LFSR PUF Based on Multiple Ring Oscillators. In Proceedings of the 2020 IEEE International Symposium on Circuits and Systems (ISCAS), Seville, Spain, 12–14 October 2020; pp. 1–5. [Google Scholar]
- Bautista Adames, I.A.; Das, J.; Bhanja, S. Survey of Emerging Technology Based Physical Unclonable Funtions. In Proceedings of the 26th Edition on Great Lakes Symposium on VLSI, Boston, MA, USA, 18–20 May 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 317–322. [Google Scholar]
- Physically Unclonable Functions: A Study on the State of the Art and Future Research Directions|SpringerLink. Available online: https://link.springer.com/chapter/10.1007/978-3-642-14452-3_1 (accessed on 27 September 2023).
- Maes, R.; Tuyls, P.; Verbauwhede, I. Intrinsic PUFs from Flip-Flops on Reconfigurable Devices. In Proceedings of the 3rd Benelux Workshop on Information and System Security (WIS-Sec2008), Eindhoven, The Netherlands, 13–14 November 2008. [Google Scholar]
- Improved Reliability of FPGA-Based PUF Identification Generator Design|ACM Transactions on Reconfigurable Technology and Systems. Available online: https://dl.acm.org/doi/abs/10.1145/3053681 (accessed on 27 September 2023).
- Kumar, S.S.; Guajardo, J.; Maes, R.; Schrijen, G.-J.; Tuyls, P. Extended Abstract: The Butterfly PUF Protecting IP on Every FPGA. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, CA, USA, 9 June 2008; pp. 67–70. [Google Scholar]
- Xu, X.; Liang, H.; Huang, Z.; Jiang, C.; Ouyang, Y.; Fang, X.; Ni, T.; Yi, M. A Highly Reliable Butterfly PUF in SRAM-Based FPGAs. IEICE Electron. Express 2017, 14, 20170551. [Google Scholar] [CrossRef]
- Design of Hybrid Strong PUF Circuit against Machine Learning Attacks. Available online: https://journal.ecust.edu.cn/article/doi/10.14135/j.cnki.1006-3080.20221009003?pageType=en (accessed on 23 October 2023).
- Cao, R.; Mei, N. A Fpga Hybrid Cro Puf Based on Three-State Gate for Improving Reliability and Hardware Overhead. Arab. Econ. Bus. J. 2014, 1–6. [Google Scholar] [CrossRef]
- Devika, K.N.; Bhakthavatchalu, R. FPGA Implementation of Programmable Hybrid PUF Using Butterfly and Arbiter PUF Concepts. J. Phys. Conf. Ser. 2022, 2312, 012033. [Google Scholar] [CrossRef]
- Khoshroo, S. Design and Evaluation of FPGA-Based Hybrid Physically Unclonable Functions. In Electronic Thesis and Dissertation Repository; University of Western Ontario: London, ON, Canada, 2013. [Google Scholar]
- Sahoo, D.P.; Mukhopadhyay, D.; Chakraborty, R.S. Design of Low Area-Overhead Ring Oscillator PUF with Large Challenge Space. In Proceedings of the 2013 International Conference on Reconfigurable Computing and FPGAs (ReConFig), Cancun, Mexico, 9–11 December 2013; Available online: https://ieeexplore.ieee.org/document/6732277 (accessed on 27 September 2023).
- Wu, Z.; Patel, H.; Sachdev, M.; Tripunitara, M.V. Strengthening PUFs Using Composition. In Proceedings of the 2019 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Westminster, CO, USA, 4–7 November 2019; pp. 1–8. [Google Scholar]
- Sahoo, D.P.; Saha, S.; Mukhopadhyay, D.; Chakraborty, R.S.; Kapoor, H. Composite PUF: A New Design Paradigm for Physically Unclonable Functions on FPGA. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014; pp. 50–55. [Google Scholar]
- Machida, T.; Yamamoto, D.; Iwamoto, M.; Sakiyama, K. A New Arbiter PUF for Enhancing Unpredictability on FPGA. Sci. World J. 2015, 2015, e864812. [Google Scholar] [CrossRef] [PubMed]
- Alamro, M.A.; Zhuang, Y.; Aseeri, A.O.; Alkatheiri, M.S. Examination of Double Arbiter PUFs on Security against Machine Learning Attacks. In Proceedings of the 2019 IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019; pp. 3165–3171. [Google Scholar]
- Alamro, M.A.; Mursi, K.T.; Zhuang, Y.; Alkatheiri, M.S.; Aseeri, A.O. Does Sophisticating Double Arbiter PUF Design Ensure Its Security? Performance and Security Assessments on 5-1 DAPUF. In Proceedings of the 2020 IEEE International Conference on Big Data (Big Data), Atlanta, GA, USA, 10–13 December 2020; pp. 1788–1795. [Google Scholar]
- Hou, S.; Ma, Y.; Deng, D.; Wang, Z.; Ren, G. Modeling and Physical Attack Resistant Authentication Protocol with Double PUFs. J. Inf. Secur. Appl. 2023, 76, 103543. [Google Scholar] [CrossRef]
- Papakonstantinou, I.; Sklavos, N. Physical Unclonable Functions (PUFs) Design Technologies: Advantages and Trade Offs. In Computer and Network Security Essentials; Daimi, K., Ed.; Springer International Publishing: Cham, Switzerland, 2018; pp. 427–442. ISBN 978-3-319-58424-9. [Google Scholar]
- Xin, X.; Kaps, J.P.; Gaj, K. A Configurable Ring-Oscillator-Based PUF for Xilinx FPGAs. In Proceedings of the 2011 14th Euromicro Conference on Digital System Design, Oulu, Finland, 31 August–2 September 2011; Available online: https://ieeexplore.ieee.org/abstract/document/6037472 (accessed on 24 October 2023).
- Sklavos, N.; Chaves, R.; Di Natale, G.; Regazzoni, F. (Eds.) Hardware Security and Trust; Springer International Publishing: Cham, Switzerland, 2017; ISBN 978-3-319-44316-4. [Google Scholar]
- Nam, J.-W.; Ahn, J.-H.; Hong, J.-P. Compact SRAM-Based PUF Chip Employing Body Voltage Control Technique. IEEE Access 2022, 10, 22311–22319. [Google Scholar] [CrossRef]
- Miskelly, J.; Gu, C.; Ma, Q.; Cui, Y.; Liu, W.; O’Neill, M. Modelling Attack Analysis of Configurable Ring Oscillator (CRO) PUF Designs. In Proceedings of the 2018 IEEE 23rd International Conference on Digital Signal Processing (DSP), Shanghai, China, 19–21 November 2018; Available online: https://ieeexplore.ieee.org/abstract/document/8631638 (accessed on 24 October 2023).
- Sahoo, D.P.; Nguyen, P.H.; Mukhopadhyay, D.; Chakraborty, R.S. A Case of Lightweight PUF Constructions: Cryptanalysis and Machine Learning Attacks. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2015, 34, 1334–1343. [Google Scholar] [CrossRef]
- Maiti, A.; Gunreddy, V.; Schaumont, P. A Systematic Method to Evaluate and Compare the Performance of Physical Unclonable Functions. In Embedded Systems Design with FPGAs; Athanas, P., Pnevmatikatos, D., Sklavos, N., Eds.; Springer: New York, NY, USA, 2013; pp. 245–267. ISBN 978-1-4614-1362-2. [Google Scholar]
- Naveenkumar, R.; Sivamangai, N.M.; Napolean, A.; Priya, S.S.S. Design and Evaluation of XOR Arbiter Physical Unclonable Function and Its Implementation on FPGA in Hardware Security Applications. J. Electron. Test 2022, 38, 653–666. [Google Scholar] [CrossRef]
- Anandakumar, N.N.; Hashmi, M.S.; Sanadhya, S.K. Design and Analysis of FPGA-Based PUFs with Enhanced Performance for Hardware-Oriented Security. J. Emerg. Technol. Comput. Syst. 2022, 18, 72. [Google Scholar] [CrossRef]
- Mahalat, M.H.; Mandal, S.; Mondal, A.; Sen, B.; Chakraborty, R.S. Implementation, Characterization and Application of Path Changing Switch Based Arbiter PUF on FPGA as a Lightweight Security Primitive for IoT. ACM Trans. Des. Autom. Electron. Syst. 2021, 27, 26. [Google Scholar] [CrossRef]
- Rabiei, H.; Kaveh, M.; Mosavi, M.; Martín, D. MCRO-PUF: A Novel Modified Crossover RO-PUF with an Ultra-Expanded CRP Space. CMC 2022, 74, 4831–4845. [Google Scholar] [CrossRef]
- Dang, T.-K.; Serrano, R.; Hoang, T.-T.; Pham, C.-K. A Novel Ring Oscillator PUF for FPGA Based on Feedforward Ring Oscillators. In Proceedings of the 2022 19th International SoC Design Conference (ISOCC), Gangneung-si, Republic of Korea, 19–22 October 2022; pp. 87–88. [Google Scholar]
- Merli, D.; Stumpf, F.; Eckert, C. Improving the Quality of Ring Oscillator PUFs on FPGAs. In Proceedings of the 5th Workshop on Embedded Systems Security, Scottsdale, Arizona, 24 October 2010; Association for Computing Machinery: New York, NY, USA, 2010; pp. 1–9. [Google Scholar]
- Lee, S.; Oh, M.-K.; Kang, Y.; Choi, D. Implementing a Phase Detection Ring Oscillator PUF on FPGA. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 17–19 October 2018; pp. 845–847. [Google Scholar]
- Choudhury, M.; Pundir, N.; Niamat, M.; Mustapa, M. Analysis of a Novel Stage Configurable ROPUF Design. In Proceedings of the 2017 IEEE 60th International Midwest Symposium on Circuits and Systems (MWSCAS), Boston, MA, USA, 6–9 August 2017; pp. 942–945. [Google Scholar]
- Zhang, J.; Shen, C.; Guo, Z.; Wu, Q.; Chang, W. CT PUF: Configurable Tristate PUF Against Machine Learning Attacks for IoT Security. IEEE Internet Things J. 2022, 9, 14452–14462. [Google Scholar] [CrossRef]
- Sahoo, D.P.; Chakraborty, R.S.; Mukhopadhyay, D. Towards Ideal Arbiter PUF Design on Xilinx FPGA: A Practitioner’s Perspective. In Proceedings of the 2015 Euromicro Conference on Digital System Design, Madeira, Portugal, 26–28 August 2015; Available online: https://ieeexplore.ieee.org/abstract/document/7302326/ (accessed on 25 September 2023).
- Hori, Y.; Yoshida, T.; Katashita, T.; Satoh, A. Quantitative and Statistical Performance Evaluation of Arbiter Physical Unclonable Functions on FPGAs. In Proceedings of the 2010 International Conference on Reconfigurable Computing and FPGAs, Cancun, Mexico, 13–15 December 2010; pp. 298–303. [Google Scholar]
- Habib, B.; Gaj, K.; Kaps, J.-P. FPGA PUF Based on Programmable LUT Delays. In Proceedings of the 2013 Euromicro Conference on Digital System Design, Los Alamitos, CA, USA, 4–6 September 2013; pp. 697–704. [Google Scholar]
- Yu, H.; Leong, P.H.; Xu, Q. An FPGA Chip Identification Generator Using Configurable Ring Oscillators. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2011, 20, 2198–2207. [Google Scholar] [CrossRef]
- Zhang, J.; Tan, X.; Zhang, Y.; Wang, W.; Qin, Z. Frequency Offset-Based Ring Oscillator Physical Unclonable Function. IEEE Trans. Multi-Scale Comput. Syst. 2018, 4, 711–721. [Google Scholar] [CrossRef]
- Karmakar, M.; Naz, S.F.; Shah, A.P. Fault-Tolerant Reversible Logic Gate-Based RO-PUF Design. Mem. Mater. Devices Circuits Syst. 2023, 4, 100055. [Google Scholar] [CrossRef]
- Ardakani, A.; Shokouhi, S.B.; Reyhani-Masoleh, A. Improving Performance of FPGA-Based SR-Latch PUF Using Transient Effect Ring Oscillator and Programmable Delay Lines. Integration 2018, 62, 371–381. [Google Scholar] [CrossRef]
- Habib, B.; Kaps, J.-P.; Gaj, K. Efficient SR-Latch PUF. In Proceedings of the Applied Reconfigurable Computing, Bochum, Germany, 13–17 April 2015; Sano, K., Soudris, D., Hübner, M., Diniz, P.C., Eds.; Springer International Publishing: Cham, Switzerland, 2015; pp. 205–216. [Google Scholar]
- Stanciu, A.; Cirstea, M.N.; Moldoveanu, F.D. Analysis and Evaluation of PUF-Based SoC Designs for Security Applications. IEEE Trans. Ind. Electron. 2016, 63, 5699–5708. [Google Scholar] [CrossRef]
- Khan, S.; Shah, A.P.; Chouhan, S.S.; Gupta, N.; Pandey, J.G.; Vishvakarma, S.K. A Symmetric D Flip-Flop Based PUF with Improved Uniqueness. Microelectron. Reliab. 2020, 106, 113595. [Google Scholar] [CrossRef]
- FLEX PUF: A Flexible Physical Unclonable Function Design Using Configurable Templates. Available online: https://www.researchsquare.com (accessed on 26 September 2023).
- Tanamoto, T.; Yasuda, S.; Takaya, S.; Fujita, S. Physically Unclonable Function Using an Initial Waveform of Ring Oscillators. IEEE Trans. Circuits Syst. II Express Briefs 2017, 64, 827–831. [Google Scholar] [CrossRef]
- Ma, Q.; Gu, C.; Hanley, N.; Wang, C.; Liu, W.; O’Neill, M. A Machine Learning Attack Resistant Multi-PUF Design on FPGA. In Proceedings of the 2018 23rd Asia and South Pacific Design Automation Conference (ASP-DAC), Jeju, Republic of Korea, 22–25 January 2018; pp. 97–104. [Google Scholar]
- Gu, C.; Liu, W.; Cui, Y.; Hanley, N.; O’Neill, M.; Lombardi, F. A Flip-Flop Based Arbiter Physical Unclonable Function (APUF) Design with High Entropy and Uniqueness for FPGA Implementation. IEEE Trans. Emerg. Top. Comput. 2021, 9, 1853–1866. [Google Scholar] [CrossRef]
- Nassar, H.; Bauer, L.; Henkel, J. CaPUF: Cascaded PUF Structure for Machine Learning Resiliency. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2022, 41, 4349–4360. [Google Scholar] [CrossRef]
- Reddy Jeeru, D.; Panduranga Vittal, K.; Anikethan, H.V.U.; Kumar, A.S. Implementation of Enhanced Parallel Port Interface for Frequency Analysis in a Configurable Ring Oscillator PUF Circuits on Xilinx Spartan 3E Architecture. In Proceedings of the 2019 IEEE International Conference on Electronics, Computing and Communication Technologies (CONECCT), Bangalore, India, 26–27 July 2019; pp. 1–7. [Google Scholar]
- Wu, L.; Hu, Y.; Zhang, K.; Li, W.; Xu, X.; Chang, W. FLAM-PUF: A Response–Feedback-Based Lightweight Anti-Machine-Learning-Attack PUF. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2022, 41, 4433–4444. [Google Scholar] [CrossRef]
- Yang, S.-H.; Liu, T.-T. A Highly Stable Physically Unclonable Function Using Algorithm-Based Mismatch Hardening Technique in 28-Nm CMOS. IEEE Trans. Circuits Syst. I Regul. Pap. 2023, 70, 280–289. [Google Scholar] [CrossRef]
- Gao, Y.; Su, Y.; Yang, W.; Chen, S.; Nepal, S.; Ranasinghe, D.C. Building Secure SRAM PUF Key Generators on Resource Constrained Devices. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 912–917. [Google Scholar]
- Delvaux, J.; Gu, D.; Schellekens, D.; Verbauwhede, I. Helper Data Algorithms for PUF-Based Key Generation: Overview and Analysis. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2015, 34, 889–902. [Google Scholar] [CrossRef]
- Ali Pour, A.; Afghah, F.; Hély, D.; Beroulle, V.; Natale, G.D.; Korenda, A.R.; Cambou, B. Helper Data Masking for Physically Unclonable Function-Based Key Generation Algorithms. IEEE Access 2022, 10, 40150–40164. [Google Scholar] [CrossRef]
- Zhang, J.; Ding, L.; Chen, Z.; Li, W.; Qu, G. DA PUF: Dual-State Analog PUF. In Proceedings of the 59th ACM/IEEE Design Automation Conference, San Francisco, CA, USA, 10–14 July 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 73–78. [Google Scholar]
- Liu, Y.; Li, J.; Qu, T.; Dai, Z. CBDC-PUF: A Novel Physical Unclonable Function Design Framework Utilizing Configurable Butterfly Delay Chain Against Modeling Attack. ACM Trans. Des. Autom. Electron. Syst. 2023, 28, 78. [Google Scholar] [CrossRef]
- Sahoo, D.P.; Mukhopadhyay, D.; Chakraborty, R.S.; Nguyen, P.H. A Multiplexer-Based Arbiter PUF Composition with Enhanced Reliability and Security. IEEE Trans. Comput. 2018, 67, 403–417. [Google Scholar] [CrossRef]
- Shi, J.; Lu, Y.; Zhang, J. Approximation Attacks on Strong PUFs. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2020, 39, 2138–2151. [Google Scholar] [CrossRef]
- Zhang, J.; Shen, C. Set-Based Obfuscation for Strong PUFs against Machine Learning Attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 288–300. [Google Scholar] [CrossRef]
- Zhang, J.; Lin, Y.; Lyu, Y.; Qu, G. A PUF-FSM Binding Scheme for FPGA IP Protection and Pay-Per-Device Licensing. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1137–1150. [Google Scholar] [CrossRef]
- Zheng, J.X.; Potkonjak, M. A Digital PUF-Based IP Protection Architecture for Network Embedded Systems. In Proceedings of the Tenth ACM/IEEE Symposium on Architectures for Networking and Communications Systems, Los Angeles, CA, USA, 20–21 October 2014; Association for Computing Machinery: New York, NY, USA, 2014; pp. 255–256. [Google Scholar]
- Guo, Q.; Ye, J.; Gong, Y.; Hu, Y.; Li, X. PUF Based Pay-Per-Device Scheme for IP Protection of CNN Model. In Proceedings of the 2018 IEEE 27th Asian Test Symposium (ATS), Hefei, China, 15–18 October 2018; pp. 115–120. [Google Scholar]
- Zhang, J.; Qu, G. Physical Unclonable Function-Based Key Sharing via Machine Learning for IoT Security. IEEE Trans. Ind. Electron. 2020, 67, 7025–7033. [Google Scholar] [CrossRef]
- Tehranipoor, F.; Karimian, N.; Yan, W.; Chandy, J.A. DRAM-Based Intrinsic Physically Unclonable Functions for System-Level Security and Authentication. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 1085–1097. [Google Scholar] [CrossRef]
- Suresh, V.; Manimegalai, R. SPIC-SRAM PUF Intergrated Chip Based Software Licensing Model. In Proceedings of the Security in Computing and Communications, Bangalore, India, 19–22 September 2018; Thampi, S.M., Madria, S., Wang, G., Rawat, D.B., Alcaraz Calero, J.M., Eds.; Springer: Singapore, 2019; pp. 377–388. [Google Scholar]
- Chhabra, S.; Lata, K. Hardware Obfuscation of AES IP Core Using PUFs and PRNG: A Secure Cryptographic Key Generation Solution for Internet-of-Things Applications. SN Comput. Sci. 2022, 3, 303. [Google Scholar] [CrossRef]
- Enamul Quadir, M.S.; Chandy, J.A. Key Generation for Hardware Obfuscation Using Strong PUFs. Cryptography 2019, 3, 17. [Google Scholar] [CrossRef]
- Zhang, J. A Practical Logic Obfuscation Technique for Hardware Security. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2016, 24, 1193–1197. [Google Scholar] [CrossRef]
- Gora, M.A.; Maiti, A.; Schaumont, P. A Flexible Design Flow for Software IP Binding in FPGA. IEEE Trans. Ind. Inform. 2010, 6, 719–728. [Google Scholar] [CrossRef]
- Barbareschi, M.; Di Natale, G.; Torres, L.; Mazzeo, A. A Ring Oscillator-Based Identification Mechanism Immune to Aging and External Working Conditions. IEEE Trans. Circuits Syst. I Regul. Pap. 2017, 65, 700–711. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, Q. A PUF-Based Unified Identity Verification Framework for Secure IoT Hardware via Device Authentication. World Wide Web 2020, 23, 1057–1088. [Google Scholar] [CrossRef]
- Gope, P.; Millwood, O.; Sikdar, B. A Scalable Protocol Level Approach to Prevent Machine Learning Attacks on Physically Unclonable Function Based Authentication Mechanisms for Internet of Medical Things. IEEE Trans. Ind. Inform. 2022, 18, 1971–1980. [Google Scholar] [CrossRef]
- Lounis, K.; Zulkernine, M. Lessons Learned: Analysis of PUF-Based Authentication Protocols for IoT. Digit. Threat. 2022, 4, 19. [Google Scholar] [CrossRef]
- Aysu, A.; Gulcan, E.; Moriyama, D.; Schaumont, P.; Yung, M. End-To-End Design of a PUF-Based Privacy Preserving Authentication Protocol. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2015, Saint-Malo, France, 13–16 September 2015; Güneysu, T., Handschuh, H., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 556–576. [Google Scholar]
- Li, D.; Lu, Z.; Zou, X.; Liu, Z. PUFKEY: A High-Security and High-Throughput Hardware True Random Number Generator for Sensor Networks. Sensors 2015, 15, 26251–26266. [Google Scholar] [CrossRef]
- Van der Leest, V.; van der Sluis, E.; Schrijen, G.-J.; Tuyls, P.; Handschuh, H. Efficient Implementation of True Random Number Generator Based on SRAM PUFs. In Cryptography and Security: From Theory to Applications: Essays Dedicated to Jean-Jacques Quisquater on the Occasion of His 65th Birthday; Naccache, D., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2012; pp. 300–318. ISBN 978-3-642-28368-0. [Google Scholar]
- Chen, S.; Li, B.; Zhou, C. FPGA Implementation of SRAM PUFs Based Cryptographically Secure Pseudo-Random Number Generator. Microprocess. Microsyst. 2018, 59, 57–68. [Google Scholar] [CrossRef]






| Types | Design | Ref. | Advantages | Challenges |
|---|---|---|---|---|
| Delay based PUFs | Arbiter PUF | Morozov et al. [43] | Identical instantiation of building blocks may not be necessary. | Requires symmetric routing in a building block. |
| Papakonstantinou et al. [85] | - | Pair of multiplexers in an APUF needs to be identical. | ||
| RO-PUF | Morozov et al. [43] | Does not require symmetric routing in a building block. | Building blocks require identical instantiation. | |
| Xin et al. [86] | - | RO PUFs is that they require one pair of ring oscillators per bit of output. Therefore, in order to collect enough output bits for a safe security level, a large number of ring oscillators is needed. | ||
| Papakonstantinou et al. [85] | Easier evaluation of entropy and higher reliability than a simple arbiter PUF. | It has slower response, though, it requires larger area and consumes more power. | ||
| Butterfly PUF | Morozov et al. [43] | Identical instantiation of building blocks may not be necessary. | Requires symmetric routing in a building block. | |
| Papakonstantinou et al. [85] | Choosing a settling time for the CRPs makes the design of a BR-PUF easier since the symmetry of the layout will not be so necessary. | Pair of latches in a BPUF cell needs to be identical. | ||
| Since the difference between intra and inter-chip variation increases with longer settling times, the identification and authentication become more efficient. | Experimental results show that there is a trade-off between reliability and uniqueness. Choosing a short settling time favors reliability whereas longer settling times favor uniqueness. | |||
| Memory based PUFs | Latch PUF | - | LPUF has some RS latches that generate inconsistent (random) numbers (i.e., “random latches”). This randomness causes a problem in that the reliability of the response is reduced. | |
| - | The response bits become lower as the number of random latches increases, which reduces the variety and entropy of responses. | |||
| SRAM PUF | Sklavos et al. [87] | SRAM PUFs require less area and they are easily implemented to FPGAs. | - | |
| Already existing SRAM of the device can be used for its construction. | - | |||
| Nam et al. [88] | SRAM PUF has the advantages of a rapid response and a small area. | There is a disadvantage related to the number of CRPs required for authentication of an entity. | ||
| Combined PUFs | Hybrid PUF | Devika et al. [76] | Combines the advantages of both Arbiter PUF and Butterfly PUF. | Since delay arising out of manufacturing variations are beyond the control it can be exploited to generate keys that are more unique than those produced by normal arbiter PUF designs. |
| Composite PUF | Sahoo et al. [80] | Utilizes smaller PUFs as design building blocks to create a “Composite PUF” with larger challenge-space and superior performance at reasonable resource overhead. | The composition is useful if at least one of the component PUFs possesses an unbiased response. | |
| CRO-PUF | Miskelly et al. [89] | Main advantage of CRO over RO is that it is much more efficient in terms of space and component usage. | Traditional CRO architecture is vulnerable to ML attacks. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lata, K.; Cenkeramaddi, L.R. FPGA-Based PUF Designs: A Comprehensive Review and Comparative Analysis. Cryptography 2023, 7, 55. https://doi.org/10.3390/cryptography7040055
Lata K, Cenkeramaddi LR. FPGA-Based PUF Designs: A Comprehensive Review and Comparative Analysis. Cryptography. 2023; 7(4):55. https://doi.org/10.3390/cryptography7040055
Chicago/Turabian StyleLata, Kusum, and Linga Reddy Cenkeramaddi. 2023. "FPGA-Based PUF Designs: A Comprehensive Review and Comparative Analysis" Cryptography 7, no. 4: 55. https://doi.org/10.3390/cryptography7040055
APA StyleLata, K., & Cenkeramaddi, L. R. (2023). FPGA-Based PUF Designs: A Comprehensive Review and Comparative Analysis. Cryptography, 7(4), 55. https://doi.org/10.3390/cryptography7040055








