1. Introduction
Traffic congestion and road accidents are becoming increasingly severe with the increasing number of vehicles. It has caused great potential threats to their privacy, property, and even their lives. However, with the development of new generation mobile communication technologies, location-based services on the Internet of Vehicles (IoV) have become popular, which have alleviated the above problems to some extent and brought great convenience to people in their lives, such as carpooling [
1,
2], Ride-hailing [
3,
4,
5], navigation [
6,
7] and finding parking spaces [
8,
9]. Unfortunately, however, it still poses a certain level of security threat to people. For example, the data traffic generated during data interaction can be analyzed by hackers to get the rest of the user’s sensitive information [
10,
11,
12].
Most of the existing privacy protection schemes for the IoV generally adopt a centralized location server, which then performs location-based services via user-initiated location service queries. However, such schemes suffer from shortcomings such as single points of failure and user privacy leakage. Based on this, some scholars have tried to secure the privacy of the IoVs in other ways, and blockchain technology is a good way to do this.
Blockchain is a distributed network that can secure privacy in the IoV with hash functions and cryptography, and is not tampered with, and also supports the traceability of vehicle information. Existing blockchains can be divided into two categories, public and federated, depending on whether they require licensing authority. Where a public chain is a fully decentralized blockchain system that does not require a trusted center for maintenance, a federated chain is a partially decentralized or polycentric blockchain system. With the emergence of blockchain technology, some scholars have tried to combine blockchain technology with the IoV, and many schemes have been proposed [
13,
14,
15]. However, since the public chain-based privacy protection scheme requires a consensus mechanism for inter-node maintenance, it runs slower compared to the federation chain-based privacy protection scheme.
Another issue that needs our attention is that privacy protection schemes based on anonymous, complex cryptographic algorithms can protect the privacy and security of users, but they consume enormous resources. Can we use the existing fundamental knowledge to propose a novel privacy protection scheme for vehicular networks? For this, we invoke the privacy set intersection (PSI). PSI is a specific problem in secure multi-party computation that allows participants to input private sets and jointly compute the intersection of private sets without revealing any information beyond the intersection. PSI-based privacy protection schemes can perform location-based services while protecting user privacy [
16]. Nevertheless, it is still a great challenge to get a good application in the highly flexible and scalable vehicular networks.
1.1. Motivations
Existing privacy protection schemes for the IoV are difficult to protect users’ identity and location privacy in a privacy-secure manner. The main objective of this paper is to propose a privacy protection scheme for the IoV based on private set intersection, and to analyze the security of the proposed scheme from a theoretical point of view.
1.2. Contributions
To address the privacy and security issues in the IoV as much as possible, this paper proposes a privacy protection scheme for the IoV based on privacy set intersection. The legitimate user in the scheme completes the location-based service by initiating a query for the location-based service. In this process, no additional personal information of the user is disclosed and no large and complex cryptographic operations are required.
Below, we conclude our main contributions as follows.
- 1.
Privacy Security: This scheme can effectively protect the privacy and security of users from privacy and security threats caused by man-in-the-middle attacks.
- 2.
Dual Authentication Protocol: The dual authentication protocol based on PSI can achieve dual guarantees: First, it ensures that both communicating parties have registration certificates issued by the trusted authority (TA) and are trusted users. Second, it ensures that both communicating parties have established secure and reliable session keys in the process.
- 3.
Collaborative Recommendation of Location Services: Based on pseudorandom functions and secure one-way hash functions, we propose a privacy-secure PSI-based collaborative recommendation location service protocol. It can well protect the privacy and security of users without requiring large computational overhead and complex cryptographic algorithms.
- 4.
Distributed Storage of Transaction Information: We construct a private blockchain formed by the location service provider (LSP) and record service recommendation information in its transaction ledger to reduce LSPs’ storage costs.
1.3. Organization
The rest of this paper is organized as follows. We present the related work in
Section 2, the scheme model and design goals in
Section 3, some preparatory knowledge in
Section 4, the main location privacy protection scheme in
Section 5, the security analysis of our scheme and its comparison with existing schemes in
Section 6, the performance analysis of our scheme and its comparison with existing schemes in
Section 7, and finally a summary of the full paper in
Section 8.
2. Related Work
We divided the related work into two main categories: authentication and privacy protection on the Internet of Vehicles.
2.1. Authentication
The IoVs refer to the all-around network connection of vehicles and people, vehicles and vehicles, vehicles and roads, and vehicles and service platforms with the help of a new generation of mobile communication technology, thus providing better location-based services for people. However, there are a number of factors that threaten people’s privacy and security in this process. On the one hand, there exist certain devices that are vulnerable to attacks by malicious users, such as Road Side Units (RSU). If the RSU is attacked by a malicious user, it may tamper with the information received or sent by the vehicle, thus causing irreversible damage to the user. On the other hand, the Internet of Vehicles is highly dynamic and its devices are deployed in the open domain, which makes it vulnerable to various attacks such as surveillance and remote intrusion. To avoid the above attacks, scholars have proposed many different authentication protocols for the Internet of Vehicles. And identity authentication schemes can be traced back to the first identity-based authentication scheme proposed by Shamir in 1985 [
17]. Subsequently, scholars have proposed an increasing number of authentication schemes based on vehicular networks [
18,
19,
20,
21,
22,
23,
24,
25,
26].
Gupta et al. [
18] proposed a blockchain-enabled game theory-based authentication mechanism. Specially, they also proposed a three-layer multi-trusted authorization solution that supports cross-region authentication of vehicles with almost no communication delay. Wu et al. [
19] proposed an authentication protocol based on symmetric encryption and fog computing in the Internet of Vehicles. Specially, they also proposed a four-layer architecture to reduce the computational burden of cloud servers. Using bilinear mapping and a one-way hash function, Sikarwar et al. [
20] proposed an efficient and lightweight batch verification scheme. Compared with the single message verification, they claim that their scheme has better security and efficiency. Zhang et al. [
21] proposed a trust platform module (TPM)-based conditional privacy-preserving authentication protocol. In this protocol, they used bilinear mapping to accelerate the process of authentication of messages by entities in the Internet of Vehicles. Considering some resource-constrained mobile devices, Jan et al. [
22] proposed a secure and efficient lightweight, and anonymous authentication and key establishment scheme which is applicable to “Vehicle to Vehicle (V2V)” and “Vehicle to RSU (V2R)”. For forensic services on the Internet of Vehicles, it is critical to ensure data privacy of vehicles and the efficiency of data transfer between vehicles. Therefore, Zhang et al. [
23] proposed a lightweight conditional anonymous authentication scheme for forensic services in IoV. Considering the vulnerability of onboard sensors of unattended vehicles to physical attacks, Jiang et al. [
24] proposed a physically secure authentication and key exchange protocol using physical unclonable function. However, Ahmim et al. [
25] argued that the scheme of Jiang et al. [
24] has drawbacks such as a lack of message confidentiality. Based on this, Ahmim et al. [
25] proposed some solutions and improved the security of the scheme of Jiang et al. [
24]. Zhao et al. [
26] proposed a federated learning collaborative authentication protocol for shared data. It can effectively protect user privacy and prevent data leakage.
2.2. Privacy Protection
The privacy security of users plays a very important role in the development of the Internet of Vehicles. Therefore, scholars have proposed many privacy protection schemes for the Internet of Vehicles based on anonymity and cryptography technologies, among which blockchain, as a distributed technology, has been continuously applied to privacy protection schemes on the Internet of Vehicles with the needs of application scenarios.
2.2.1. Anonymity
K-anonymity is a common approach in privacy-preserving schemes for the Internet of Vehicles. K-anonymity can be traced back to the work proposed by Sweeney in 2002 [
27], but the first application to vehicular privacy protection was by Gruteser et al. [
28]. And in order to be able to satisfy the level of privacy protection required by users, Kido et al. [
29] proposed the first scheme to generate anonymous sets for users in the form of generated dummy users. However, this scheme suffers from unreliable dummy user data and the communication overhead increases as the number of dummy users increases. To solve the problem of unreliable virtual user data, scholars have proposed different K-anonymity based privacy preserving schemes for the Internet of Vehicles [
30,
31,
32,
33,
34].
Sun et al. [
30] proposed a region-of-interest division-based algorithm to preserve the location privacy of users. Specially, after considering the semantic location information, they also proposed an approach to generate dummy locations based on entropy, which can generate safe and secure dummy locations that do not contain the real location information of users. Considering frequent regions and time reachability, Liu et al. [
31] proposed frequency-aware dummy-based method to the location privacy of users, which ensures that the generated dummy locations are as safe and reasonable as possible. Niu et al. [
32] proposed a dummy-based privacy protection scheme for continuous location based services (LBSs). Especially, after considering factors such as time-sensitive side information, they proposed a dummy filtering algorithm to ensure that the dummy locations are realistic and reliable. Ni et al. [
33] proposed an anonymous entropy-based location privacy protection scheme in mobile social networks. According to the population distribution method, the scheme contains two algorithms: an anonymous region constructing algorithm based on kd-trees in densely populated regions (K-DDCA) and an anonymous region constructing algorithm based on kd-trees in sparsely populated regions (K-SDCA). To ensure the validity, uncertainty and dispersion of virtual location, Xu et al. [
34] proposed a location privacy-preservation method based on dummy locations under road restriction.
2.2.2. Cryptography
Due to the ability to provide higher quality of service and its communication overhead does not increase linearly with the number of users, cryptography-based privacy-preserving schemes for the Internet of Vehicles have numerous applications in carpooling [
35,
36] and hailing [
37,
38,
39,
40].
In view of the centralization problem existing in the traditional carpooling schemes, Li et al. [
35] proposed an efficient and privacy-preserving carpooling scheme using blockchain-assisted vehicular fog computing. Using attribute-based proxy re-encryption, Wang et al. [
36] proposed a secure ride-sharing scheme based on a consortium blockchain. All of their schemes ensure data security.
While online ride-hailing services bring a convenient way for people to travel, the privacy concern is also highly raised. Based on this, using somewhat homomorphic encryption, Yu et al. [
37] proposed an efficient and privacy-preserving ride matching scheme for Online Ride Hailing services. Specially, they also proposed an efficient exact shortest road distance computation approach over encrypted data. And by this approach, they can find the taxi with the minimum road distance to serve a rider. Using paillier cryptosystem, Huang et al. [
38] proposed a privacy-preserving online ride-sharing matching scheme. It also supports privacy-preserving ride-sharing between multiple riders. Using elliptic curve cryptosystem and digital signature technology, Wang et al. [
39] proposed a blockchain-based anonymous ride-hailing scheme for autonomous taxi network. Using somewhat homomorphic encryption, Ma et al. [
40] proposed a privacy-preserving cross-zone ride-matching scheme.
3. Problem Statement
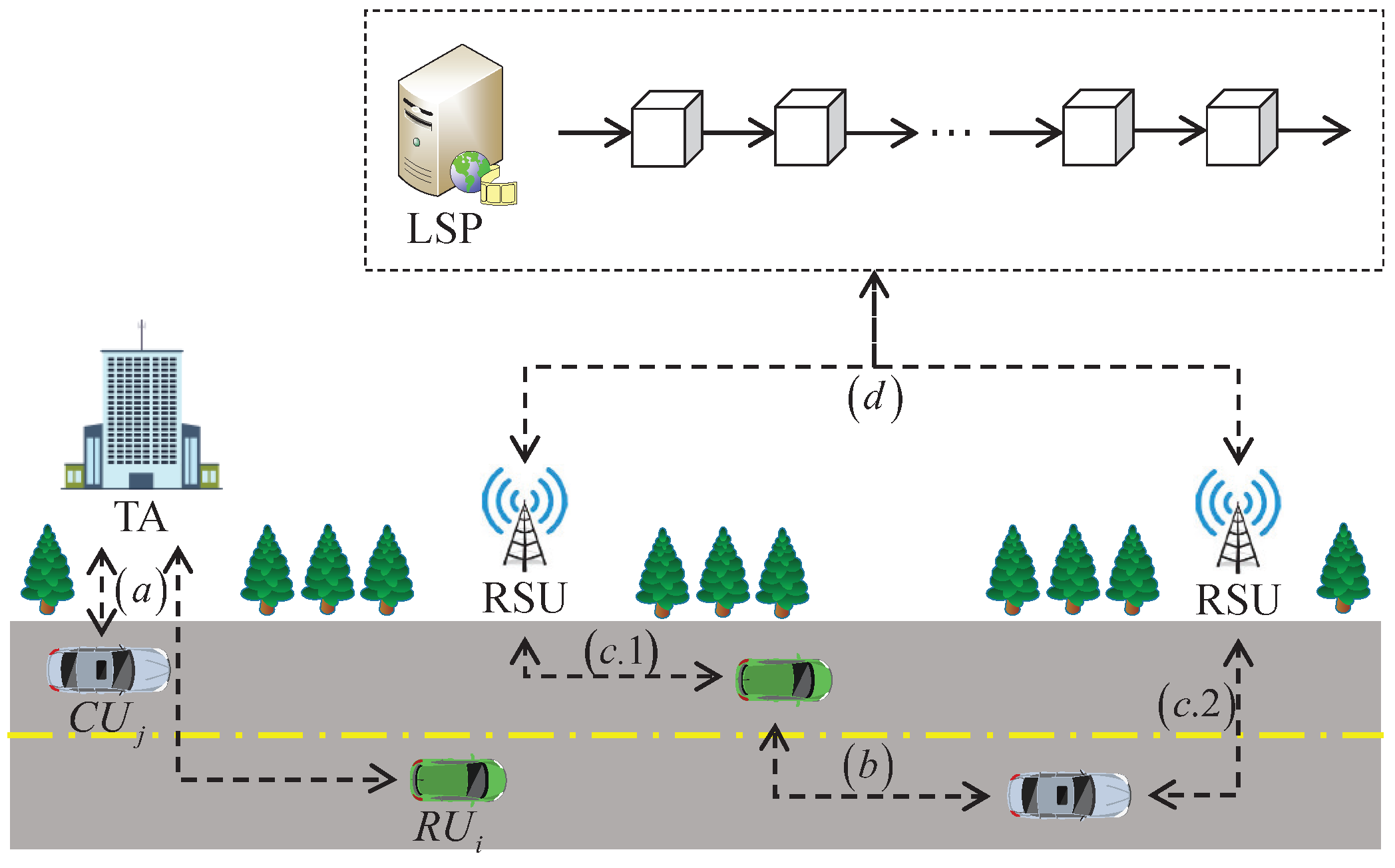
3.1. System Model
The system model of this scheme consists of trusted authority (TA), road side unit (RSU), requesting users (
), collaborating users (
), and location service provider (LSP) which are depicted in
Figure 1.
- 1.
TA: A trust center, mainly responsible for user registration, generation of system private key , system public key and system parameters .
- 2.
LSP: A location service provider, which is the core component of this paper, is primarily responsible for the maintenance of the blockchain.
- 3.
RSU: A roadside infrastructure is installed on both sides of the road with some computing and storage capacity, mainly responsible for message forwarding, functional verification, and PSI operations.
- 4.
: Users who initiate location service queries.
- 5.
: Users who respond to a location service query.
The key notations are listed in
Table 1.
3.2. Threat Model
The main security threats to this scheme originate from the following components.
- 1.
Most of the requesting users are honest and trustworthy, and will send real and reliable location service queries. However, a small percentage of requesting users will upload false location service queries or repeatedly initiate queries multiple times within a short period of time, thus reducing system security and query efficiency.
- 2.
Most of the collaborative users are honest and trustworthy, and will generate true and reliable location service responses based on their historical experience, background knowledge. However, there exists a small percentage of collaborative users who will generate false service responses, thus reducing service efficiency.
- 3.
A typical vulnerable attack during the communication between two parties is the man-in-the-middle attack, where a malicious user can perform acts such as wiretapping and forging messages during the communication between two parties.
- 4.
Security threats due to physical factors are not considered.
3.3. Design Goals
The design goals of this scheme have the following main parts.
- 1.
Identity Privacy: The user’s identity information is anonymous to other users, RSUs and LSPs during the registration, authentication and service query process.
- 2.
Location Privacy: Users’ location information must be protected from remaining malicious users who may obtain it in an undisclosed manner and derive the rest of the user’s sensitive information from it.
- 3.
Route Privacy: The user’s route information is known only to him/herself, and it is difficult for the rest of the users to infer the user’s route from the available information.
- 4.
Non-Repudiation: No user can repudiate the act of sending a message and the content of the message. TA can reveal the identity of users who have malicious behavior.
- 5.
Anti-Man-in-the-Middle Attack: No man-in-the-middle attacks from malicious users during the communication between the two parties.
4. Preliminaries
In this section, we briefly revisit elemental techniques that are used to support the construction of the proposed scheme. These include bilinear pairing, the problem of collusion attack algorithm with k traitors (k-CAA), and private set intersection.
4.1. Bilinear Pairing
Assume are cyclic groups of prime order p, where is a generator in . Let be a bilinear pairing if the following conditions are satisfied.
- 1.
Bilinearity: for all and , .
- 2.
Non-degeneracy: .
- 3.
Computability: for all and , is efficiently computable.
4.2. k-CAA Problem
For any integer k and , , given , compute , where and .
4.3. Private Set Intersection
PSI means that the participants input the private set and jointly compute the intersection of the private set without revealing any information other than the intersection. And the most popular PSI scheme is the PSI scheme based on oblivious pseudo-random functions (OPRF-Based PSI), as shown in
Figure 2.
- 1.
Sender holds the set , Receiver holds the set , is Sender’s private key, and F is an oblivious pseudo-random function.
- 2.
Receiver sends to OPRF. Then OPRF generates and and sends them to Sender and Receiver respectively.
- 3.
When receiving , Sender computes and sends it to the Receiver.
- 4.
When receiving from Sender, Receiver contrasts with , and then generates the PSI results for Sender and Receiver.
In
Section 5.4, we construct a dual authentication protocol using PSI techniques and define a notation, i.e.,
, which indicates that the PSI result of the set
X and
Y is
. For this, we make the following rules.
If Sender and Receiver have the same set, i.e., , then we make ; otherwise we make .
5. The Proposed Scheme
5.1. Overview
The scheme consists of the following parts: system initialization, user registration, dual authentication, service query (response), service recommendations and service transactions. The flow of the scheme is shown in
Figure 3. Specifically, In (i), each user (requesting user and collaborating user) registers with the TA and generates the corresponding public-private key pair. In (ii), each user to be communicated authenticates with each other and generates a temporary session key. In (iii), the requesting user initiates a service request (and the collaborating user generates a service response) and sends it to the RSU. In (iv), the RSU performs signature verification of the requesting user (or collaborating user) and generates the corresponding service recommendation for the requesting user. Finally, in (v), the requesting user and the collaborating user establish a communication channel to complete the service recommendation.
5.2. System Initialization
Given a security parameter , the TA generates two cyclic groups of prime order and chooses a bilinear pairing , where is a generator in , and . The TA chooses three hash functions , , , and . Next, the TA chooses , computes and generates a user’s certificate of registration . Finally, the public key is , the private key is , and the public parameters is .
5.3. User Registration
Each user ( and ) must register with the TA and generate their own public-private key pair, specifically.
- 1.
The user chooses , computes and sends to TA via a public channel.
- 2.
When receiving from user , TA performs the following operations.
Compute .
Choose , and compute .
Finally, send to user via a secure channel.
5.4. Dual Authentication
In this part, and verify each other and agree on a temporary session key.
- 1.
randomly chooses a security parameter
for pseudorandom function (PRF) and a number
.
computes
Then sends to via public channel.
- 2.
When receiving
from
,
verifies
If the verification is correct,
chooses a number
and computes
Then sends to via public channel.
- 3.
When receiving
from
,
verifies
If the verification is correct, computes , and performs a intersection operation on . If , i.e., , this indicates that and have the same registration certificate issued by TA and generate a secure and reliable session key , and indicates that is a reliable user. Then sends to via public channel; otherwise, interrupt process.
- 4.
When receiving from , performs a intersection operation on . If , i.e., , this indicates that and have the same registration certificate issued by TA and generate a secure and reliable session key , and indicates that is a reliable user; otherwise, interrupt process.
The proof of correctness of the Equations (
3) and (
5) are demonstrated as shown below.
5.5. Service Query (Response)
In the service query (response) part, initiates a service query ( generates a service response) and sends it to the RSU for service recommendations, specifically.
- 1.
The user chooses numbers and computes .
- 2.
The user computes , and , where is the service query contents of (or the service response contents of ).
- 3.
Finally, the user sends to the RSU via public channel.
5.6. Service Recommendations
When receiving from different users ( or ), the RSU performs the following operations:
- 1.
Compute , and and then verify the validity of , and . If it is not valid, drop the corresponding query (response); otherwise, continue.
- 2.
For two different users ( and ) of , compute and send it to the
- 3.
Write into the transaction and send it to the blockchain network.
The proof of correctness of the equations
, and
are demonstrated as shown below.
5.7. Service Transactions
In the service transactions part, the and will complete the relevant service recommendations via the personal channel. Specifically, the encrypts the relevant service response content, i.e., , using the temporary session key and finally sends it to the . And the completes the location-based service query by computing .
6. Privacy and Security Analysis
In this section, we analyze the privacy and security of the proposed scheme, which mainly includes identity privacy, location privacy, route privacy, non-repudiation, and anti-man-in-the-middle attacks.
6.1. Identity Privacy
In our scheme, we protect the privacy of the user’s identity. During the user registration process, each user must register with the TA to obtain the corresponding private key and registration certificate . And in this process, all users are registered using the hash of their identity, i.e., , without revealing the user’s identity information. In the dual authentication process, each user proves that he or she is secure and trustworthy via a registration certificate obtained at the time of registration, while maintaining the user’s anonymity. In the service query (response) process, the user’s identity information is secure because the user’s identity (in this case, anonymous identity) is not involved. In summary, the user’s identity information is anonymous to the rest of the users, RSUs and LSPs. However, the user’s identity privacy is conditionally secure for the TA. This is because the user’s private key is issued by the TA. If the TA is compromised, the user’s identity will be revealed.
6.2. Location Privacy
In the service query (response) process, we use a secure pseudo-random function and a one-way hash function to process the user’s location data, i.e., . And during the service transaction, we process the user’s location data by its constructed session key, i.e. . The location data processed in both ways will become indistinguishable, thus ensuring the privacy and security of the user’s location.
6.3. Route Privacy
When
initiates a service query (
generates a service response), it is known from
Section 6.2 that the user’s location privacy is security. Moreover, the user uses a pseudo-random function and a hash function for its message content
M, i.e.,
, which prevents the adversary from determining that
E and
are generated by the same
M. Finally, in the service transaction phase, we claim the following two facts. (1)
cannot infer the routing information of
from the location service sent by
. For example, there are three routes available for driving from A to B.
only knows that
took one of the three routes, and does not know which one was taken. (2)
also cannot infer the next routing information of
from the location service it sends. On the one hand, the path selection of
has a large uncertainty, and on the other hand,
cannot know whether
accepts the location service it sends.
6.4. Non-Repudiation
When there exists some malicious users who endanger the privacy and security of the rest of the users by means of message replay and forgery, TA can compute to obtain the private key of the malicious user and its corresponding identity.
The proof of correctness of the equations
is demonstrated as shown below.
6.5. Anti-Man-in-the-Middle Attack
We have mainly considered man-in-the-middle attack resistance in the dual authentication phase. Specifically, under the random oracle and k-CAA assumptions, we prove by Theorem 1 that the proposed signature technique is resistant to existential forgery in the dual authentication phase. This ensures that the dual authentication protocol proposed in this paper is resistant to man-in-the-middle attacks.
Theorem 1. The proposed scheme is existentially unforgeable in the random oracle model under the k-CAA assumption.
Proof of Theorem 1. We assume that there exists an attacker who adaptively selects messages and identities can break the scheme proposed in this paper with a non-negligible advantage after performing times of queries, times of private key extraction queries and times of signature queries within the time t. Then there exists a challenger who can solve the problem with a non-negligible advantage in time .
We assume that given a challenge to , i.e., given , , , the goal of is to output a solution of the problem, where .
- 1.
Setup. runs the system initialization algorithm, then chooses , and computes . constructs a list containing the array , and finally sends the public parameter to .
- 2.
Queries. In response to the query of , maintains list to track the query, query, private key extraction query and signature query of . The list is empty at the beginning. We assume that for each , has queried the value of before performing query, private key extraction query and signature query for simplicity.
query. maintains a list containing the array . Specifically, for , prepares a response and adds it to the . When makes a query to , recovers from and sends it to .
query. maintains a list containing the array . When makes a query to , recovers from and chooses a number , so that . Then adds to and sends to .
Private key extraction query. When makes a private key extraction query to , recovers from and then verifies . If , output “⊥” (“⊥” means failure). Otherwise there is (i.e., there is such that ), then computes . Finally, adds to and sends to .
Signature query. When makes signature query to , recovers from and verifies . If , outputs “⊥”. Otherwise, computes and sends it to .
- 3.
outputs a message signature pair
about the
, and the signature satisfies the following equation.
verifies
. If
, output “⊥”. Otherwise, we have that equation (
12) holds. Therefore,
can compute
and thus output the array
as a solution to the
problem, where
. And this contradicts the k-CAA assumption that it is a difficult problem.
□
We compare this scheme with existing work in
Table 2 in terms of privacy and security. Only the proposed scheme can satisfy all the conditions. Generally speaking, some smart parking, carpooling and ride hailing schemes [
1,
2,
4,
8,
41] based on location services can protect users’ location privacy to a certain extent, but they can still lead to location and route information leakage due to malicious compromise by attackers.
7. Performance Analysis
To instantiate our proposed scheme, we compare the proposed scheme with other existing schemes in terms of computational and communication overheads. The experimental performance verifies the efficiency and effectiveness of our scheme.
7.1. Experiment Setting
The experiments in our scheme were all conducted on a computer (Intel®Core™ i5-3470S CPU @ 2.90 GHz × 2, 3.8 GiB RAM) running Ubuntu 20.04.3 LTS 64-bit OS. We made use of modules such as hashlib and cryptography in Python. We first evaluate the time cost of the exponential operation , hash operation , and bilinear operation , where the time cost of each operation is the average time after running 1000 times. Specifically, the time cost of each operation is ms, ms, ms. Next, we instantiated 100 users on a computer and compared the performance of our scheme with other schemes in terms of computation and communication overhead.
7.2. Computational Overhead
We experimentally evaluate the computational overhead of our scheme in the user registration, signature and signature verification phases and compare it with PiSim [
7], SRPP [
8], and ASAP [
41], as shown in
Figure 4.
In user registration, we only use exponential and hash operations with low computational overhead, making the computational overhead of this paper only 0.1586 ms, which is much smaller than [
7,
8,
41]. In signature, we use only 5 exponential operations and 2 hash operations, and its computational overhead is 0.2741 ms. Compared with [
7,
8,
41], our scheme has a slight advantage. And in signature verification, although we use bilinear operations with high computational overhead, we can still have some advantages in this paper compared with [
7,
8,
41].
7.3. Communication Overhead
Next, we analyze the communication overhead of the user’s location service query during transmission.
In PPCS [
30], the user generates a service query
, where
is the user’s identity,
are the location data,
R is the the radius of the user’s query scope,
C is the service query content. Therefore, the total communication overhead is expressed as
KBytes.
In RR-DLS [
34], the user generates a service query
, where
is the service query content at location
,
V is the degree of privacy protection. Therefore, the total communication overhead is expressed as
KBytes.
In DK-A [
45], the user generates a service request
and sends it to a trusted server for encryption. After the server receives
n service requests
, it saves
and generates two matrices
about the service requests. Finally, it outputs
as the user’s service query, where
is the user ID,
is the location data,
is the service query content. Therefore, the total communication overhead is expressed as
KBytes.
In our scheme, the user generates a service query , then its total communication overhead is expressed as KBytes. Specifically, since the number of occupied bits of is fixed, and the number of bits of E is related to the hash function . In the case that is deterministic, the number of bits of E is also fixed and does not change with the number of users. Therefore, the communication overhead of the service query of the users in our scheme is constant 0.10 KBytes.
The results of the communication overhead comparison for each scheme are shown in
Figure 5. Through our analysis, we found that the service queries of [
30,
34,
45] are constructed based on anonymity sets, which makes their communication overhead increase linearly with the increase of anonymity sets. Although the increase of anonymity set can further improve the security of user’s location privacy, its higher communication overhead is not tolerable for us. In contrast, this paper reduces the communication overhead to a constant 0.10 while guaranteeing user privacy security. Obviously, our paper has a greater advantage in terms of communication overhead compared to [
30,
34,
45].
8. Conclusions
To better protect users’ privacy and security, this paper proposes a privacy protection scheme for the Internet of Vehicles based on privacy set intersection. Specifically, we propose two privacy-secure protocols: a dual authentication protocol and a service recommendation protocol. The dual authentication protocol based on privacy set intersection has dual security guarantees. One can ensure that both sides of the authenticated communication are secure and trusted, and the other ensures that the session keys established by both sides in the process are secure and reliable. While in the service recommendation protocol, users are blinded to their location information by a pseudorandom function and a one-way hash function, making the user’s location information available and invisible. Compared with existing schemes, our scheme is more security, achieving identity privacy, location privacy, routing privacy, non-repudiation, and anti-man-in-the-middle attack. Also, it is experimentally shown that our scheme is significantly better than the existing schemes in terms of computation overhead and communication overhead.
In the future, we will design a more fully functional privacy protection scheme, such as migrating the PSI operation in the service recommendation protocol to the smart contract of the blockchain. Thus, we can avoid the privacy leakage of users due to the excessive authority of RSU.
Author Contributions
Conceptualization, Q.Z. and Z.Z.; methodology, Z.Z.; formal analysis, Q.Z., K.W. and M.C.; writing—original draft preparation, Z.Z.; writing—review and editing, Q.Z. and Z.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Key Research and Development Program of China grant number 2021YFA1000600 and by the National Natural Science Foundation of China grant number 12171114.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Baza, M.; Lasla, N.; Mahmoud, M.M.E.A.; Srivastava, G.; Abdallah, M. B-Ride: Ride Sharing with Privacy-preservation, Trust and Fair Payment Atop Public Blockchain. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1214–1229. [Google Scholar] [CrossRef]
- Nabil, M.; Sherif, A.; Mahmoud, M.; Alsharif, A.; Abdallah, M. Efficient and Privacy-preserving Ridesharing Organization for Transferable and Non-transferable Services. IEEE Trans. Dependable Secur. Comput. 2021, 18, 1291–1306. [Google Scholar] [CrossRef]
- Zhao, Q.; Zuo, C.; Pellegrino, G.; Lin, Z. Geo-locating Drivers: A Study of Sensitive Data Leakage in Ride-hailing Services. In Proceedings of the 26th Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Yu, H.; Shu, J.; Jia, X.; Zhang, H.; Yu, X. Lpride: Lightweight and Privacy-preserving Ride Matching over Road Networks in Online Ride Hailing Systems. IEEE Trans. Veh. Technol. 2019, 68, 10418–10428. [Google Scholar] [CrossRef]
- Yu, H.; Zhang, H.; Yu, X.; Du, X.; Guizani, M. Pgride: Privacy-preserving Group Ridesharing Matching in Online Ride Hailing Services. IEEE Internet Things J. 2021, 8, 5722–5735. [Google Scholar] [CrossRef]
- Baruah, B.; Dhal, S. An Intelligent Privacy Preserving Vehicle Navigation System. In Proceedings of the 2019 IEEE Region 10 Symposium (TENSYMP), Kolkata, India, 7–9 June 2019; pp. 727–732. [Google Scholar]
- Li, M.; Chen, Y.; Zheng, S.; Hu, D.; Lal, C.; Conti, M. Privacy-preserving Navigation Supporting Similar Queries in Vehicular Networks. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1133–1148. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhang, L.; Kang, B.; Ma, Y.; Chen, T. Secure and Reliable Parking Protocol Based on Blockchain for Vanets. In Proceedings of the 2021 IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021; pp. 1–6. [Google Scholar]
- Wang, L.; Lin, X.; Zima, E.; Ma, C. Towards Airbnb-like Privacy-enhanced Private Parking Spot Sharing Based on Blockchain. IEEE Trans. Veh. Technol. 2020, 69, 2411–2423. [Google Scholar] [CrossRef]
- Jiang, S.; Zhu, X.; Wang, L. An Efficient Anonymous Batch Authentication Scheme Based on HMAC for Vanets. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2193–2204. [Google Scholar] [CrossRef]
- Arif, M.; Wang, G.; Bhuiyan, M.; Wang, T.; Chen, J. A Survey on Security Attacks in VANETs: Communication, applications and challenges. Veh. Commun. 2019, 19, 100179. [Google Scholar] [CrossRef]
- Chen, J.; He, K.; Yuan, Q.; Chen, M.; Du, R.; Xiang, Y. Blind Filtering at Third Parties: An Efficient Privacy-preserving Framework for Location-based Services. IEEE Trans. Mob. Comput. 2018, 17, 2524–2535. [Google Scholar] [CrossRef]
- Karim, H.; Rawat, D.B. Tollsonly Please—Homomorphic Encryption for Toll Transponder Privacy in Internet of Vehicles. IEEE Internet Things J. 2022, 9, 2627–2636. [Google Scholar] [CrossRef]
- Li, B.; Liang, R.; Zhou, W.; Yin, H.; Gao, H.; Cai, K. LBS Meets Blockchain: An Efficient Method with Security Preserving Trust in SAGIN. IEEE Internet Things J. 2022, 9, 5932–5942. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Shahzad, L.; Abdelmaboud, A.; Elfadil Eisa, T.A.; Alamri, B.; Javed, I.T.; Al-Dhaqm, A.; Crespi, N. A Blockchain-based Efficient, Secure and Anonymous Conditional Privacy-preserving and Authentication Scheme for the Internet of Vehicles. Appl. Sci. 2022, 12, 476. [Google Scholar] [CrossRef]
- Li, Z.; Alazab, M.; Garg, S.; Hossain, M.S. Priparkrec: Privacy-preserving Decentralized Parking Recommendation Service. IEEE Trans. Veh. Technol. 2021, 70, 4037–4050. [Google Scholar] [CrossRef]
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Proceedings of CRYPTO 84 on Advances in Cryptology; Springer: Berlin/Heidelberg, Germany, 1985; Volume 196, pp. 47–53. [Google Scholar]
- Gupta, M.; Kumar, R.; Shekhar, S.; Sharma, B.; Patel, R.B.; Jain, S.; Dhaou, I.B.; Iwendi, C. Game Theory-based Authentication Framework to Secure Internet of Vehicles with Blockchain. Sensors 2022, 22, 5119. [Google Scholar] [CrossRef]
- Wu, T.-Y.; Guo, X.; Chen, Y.-C.; Kumari, S.; Chen, C.-M. SGXAP: Sgx-based Authentication Protocol in Iov-enabled Fog Computing. Symmetry 2022, 14, 1393. [Google Scholar] [CrossRef]
- Sikarwar, H.; Das, D. Towards Lightweight Authentication and Batch Verification Scheme in Iov. IEEE Trans. Dependable Secur. Comput. 2022, 19, 3244–3256. [Google Scholar] [CrossRef]
- Zhang, M.; Zhu, B.; Li, Y.; Wang, Y. Tpm-based Conditional Privacy-preserving Authentication Protocol in Vanets. Symmetry 2022, 14, 1123. [Google Scholar] [CrossRef]
- Jan, S.A.; Amin, N.U.; Shuja, J.; Abbas, A.; Maray, M.; Ali, M. SELWAK: A Secure and Efficient Lightweight and Anonymous Authentication and Key Establishment Scheme for Iot Based Vehicular Ad Hoc Networks. Sensors 2022, 22, 4019. [Google Scholar] [CrossRef]
- Zhang, M.; Zhou, J.; Cong, P.; Zhang, G.; Zhuo, C.; Hu, S. LIAS: A Lightweight Incentive Authentication Scheme for Forensic Services in Iov. IEEE Trans. Autom. Sci. Eng. 2022, 1–16. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, X.; Zhang, N.; Tian, Y.; Ma, X.; Ma, J. Three-factor authentication protocol using physical unclonable function for IoV. Comput. Commun. 2021, 173, 45–55. [Google Scholar] [CrossRef]
- Ahmim, I.; Ghoualmi-Zine, N.; Ahmim, A.; Ahmim, M. Security Analysis on “three-factor Authentication Protocol Using Physical Unclonable Function for Iov”. Int. J. Inf. Secur. 2022, 21, 1019–1026. [Google Scholar] [CrossRef]
- Zhao, P.; Huang, Y.; Gao, J.; Xing, L.; Wu, H.; Ma, H. Federated Learning-based Collaborative Authentication Protocol for Shared Data in Social Iov. IEEE Sens. J. 2022, 22, 7385–7398. [Google Scholar] [CrossRef]
- Sweeney, L. K-Anonymity: A Model for Protecting Privacy. Int. J. Uncertain. Fuzziness Knowl.-Based Syst. 2002, 10, 557–570. [Google Scholar] [CrossRef]
- Gruteser, M.; Grunwald, D. Anonymous Usage of Location-Based Services Through Spatial and Temporal Cloaking. In MobiSys ’03, Proceedings of the 1st International Conference on Mobile Systems, Applications and Services, San Francisco, CA, USA, 5–8 May 2003; Association for Computing Machinery: New York, NY, USA, 2003; pp. 31–42. [Google Scholar]
- Kido, H.; Yanagisawa, Y.; Satoh, T. An Anonymous Communication Technique Using Dummies for Location-Based Services. In Proceedings of the International Conference on Pervasive Services, Santorini, Greece, 11–14 July 2005; pp. 88–97. [Google Scholar]
- Sun, G.; Cai, S.; Yu, H.; Maharjan, S.; Chang, V.; Du, X.; Guizani, M. Location Privacy Preservation for Mobile Users in Location-based Services. IEEE Access 2019, 7, 87425–87438. [Google Scholar] [CrossRef]
- Liu, J.; Jiang, X.; Zhang, S.; Wang, H.; Dou, W. FADBM: Frequency-aware Dummy-based Method in Long-term Location Privacy Protection. In Proceedings of the 2019 IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), Tianjin, China, 4–6 December 2019; pp. 384–391. [Google Scholar]
- Niu, J.; Zhu, X.; Shi, L.; Ma, J. Time-aware Dummy-based Privacy Protection for Continuous LBSs. In Proceedings of the 2019 International Conference on Networking and Network Applications (NaNA), Daegu, Republic of Korea, 10–13 October 2019; pp. 15–20. [Google Scholar]
- Ni, L.; Tian, F.; Ni, Q.; Yan, Y.; Zhang, J. An Anonymous Entropy-based Location Privacy Protection Scheme in Mobile Social Networks. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 1–19. [Google Scholar] [CrossRef]
- Xu, X.; Chen, H.; Xie, L. A Location Privacy Preservation Method Based on Dummy Locations in Internet of Vehicles. Appl. Sci. 2021, 11, 4594. [Google Scholar] [CrossRef]
- Li, M.; Zhu, L.; Lin, X. Efficient and Privacy-preserving Carpooling Using Blockchain-assisted Vehicular Fog Computing. IEEE Internet Things J. 2019, 6, 4573–4584. [Google Scholar] [CrossRef]
- Wang, D.; Zhang, X. Secure Ride-sharing Services Based on a Consortium Blockchain. IEEE Internet Things J. 2021, 8, 2976–2991. [Google Scholar] [CrossRef]
- Yu, H.; Jia, X.; Zhang, H.; Shu, J. Efficient and Privacy-preserving Ride Matching Using Exact Road Distance in Online Ride Hailing Services. IEEE Trans. Serv. Comput. 2022, 15, 1841–1854. [Google Scholar] [CrossRef]
- Huang, J.; Luo, Y.; Xu, M.; Hu, B.; Long, J. Pshare: Privacy-preserving Ride-sharing System with Minimum-detouring Route. Appl. Sci. 2022, 12, 842. [Google Scholar] [CrossRef]
- Wang, K.; Liu, M.; Wang, J.; Wu, M.; Zhao, F. BBARHS: Blockchain-Based Anonymous Ride-Hailing Scheme for Autonomous Taxi Network. Secur. Commun. Netw. 2022, 2022, 8296608. [Google Scholar] [CrossRef]
- Ma, H.; Ping, Y.; Zhang, Y. Privacy-Preserving Cross-Zone Ride-Matching for Online Ride-Hailing Service. Math. Probl. Eng. 2022, 2022, 5040766. [Google Scholar] [CrossRef]
- Zhu, L.; Li, M.; Zhang, Z.; Qin, Z. ASAP: An Anonymous Smart-parking and Payment Scheme in Vehicular Networks. IEEE Trans. Dependable Secur. Comput. 2020, 17, 703–715. [Google Scholar] [CrossRef]
- Kou, B.; Cao, S.; Lv, J. A Privacy Protection Scheme for Carpooling Service Using Fog Computing. J. Phys. Conf. Ser. 2020, 1601, 032019. [Google Scholar] [CrossRef]
- Zhou, X.; He, D.; Khan, M.K.; Wu, W.; Choo, K.-K.R. An Efficient Blockchain-based Conditional Privacy-preserving Authentication Protocol for Vanets. IEEE Trans. Veh. Technol. 2022, 1–12. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Huang, X.; Kumar, N.; Choo, K.-K.R. BCPPA: A Blockchain-based Conditional Privacy-preserving Authentication Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2021, 22, 7408–7420. [Google Scholar] [CrossRef]
- Xing, L.; Jia, X.; Gao, J.; Wu, H. A Location Privacy Protection Algorithm Based on Double K-anonymity in the Social Internet of Vehicles. IEEE Commun. Lett. 2021, 25, 3199–3203. [Google Scholar] [CrossRef]
| Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).