Multi-Wavelength Quantum Key Distribution Emulation with Physical Unclonable Function
Abstract
:1. Background Information
1.1. Motivation
1.2. QKD Overview
Security Based on Quantum Mechanics
1.3. QKD Protocols
1.3.1. BB84
Eavesdropper Detection
Practical Implementation, Attacks, and Decoy States
1.3.2. B92, SARG04, SSP99, and QKD Protocols after BB84
1.3.3. E91
2. Multi-Wavelength QKD with a PUF
2.1. Multi-Wavelength QKD
2.1.1. Ternary Protocol
Problems and Improvements to the Ternary Protocol
2.1.2. Quaternary Protocol
2.2. QKD with PUF
2.2.1. PUF Background
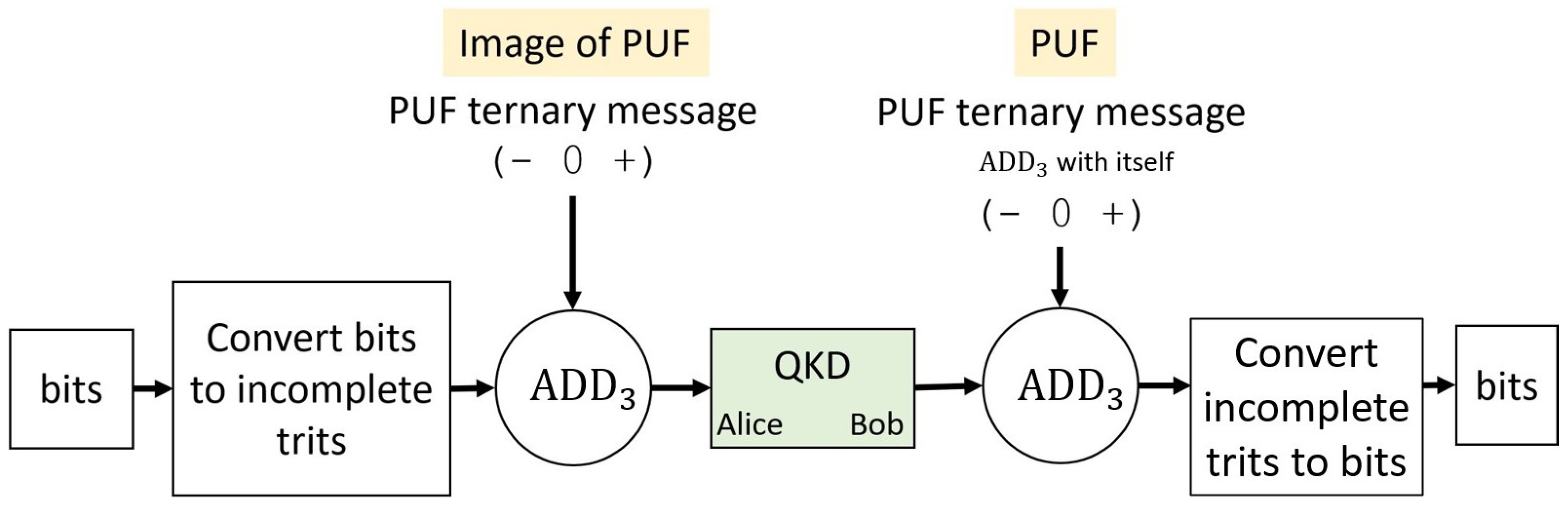
2.2.2. Ternary Protocol with a PUF
2.2.3. Obscuring and Unobscuring Bitstreams with Addition
2.2.4. Quaternary Protocol with a PUF
3. Bitwise Transform
3.1. TAPKI System
3.2. Ternary Transform
3.3. Quaternary Transform
3.4. Octal Transform
3.5. Restricting States
3.6. Alternative Mask Options
- 1.
- Shift mask before re-use.
- 2.
- Hash mask before re-use.
- 3.
- Generate a new mask for random addresses.
- 4.
- Generate a new mask using the same addresses, but different parameters (e.g., combinations of current and temperature for memristor PUFs).
- 5.
- Generate key as demonstrated, then recursively “XOR-AND-Tumble” the key and mask, feeding the outputs back into the system and repeating a defined, or random, number of times. To illustrate this novel XOR-AND-Tumble sequence in a manner that is easy to follow, we have labeled the initial inputs , and the corresponding outputs , indexed in the order in which they first appear:
3.7. Relationships of Expansion
4. Building a QKD Emulation System to Test Protocols
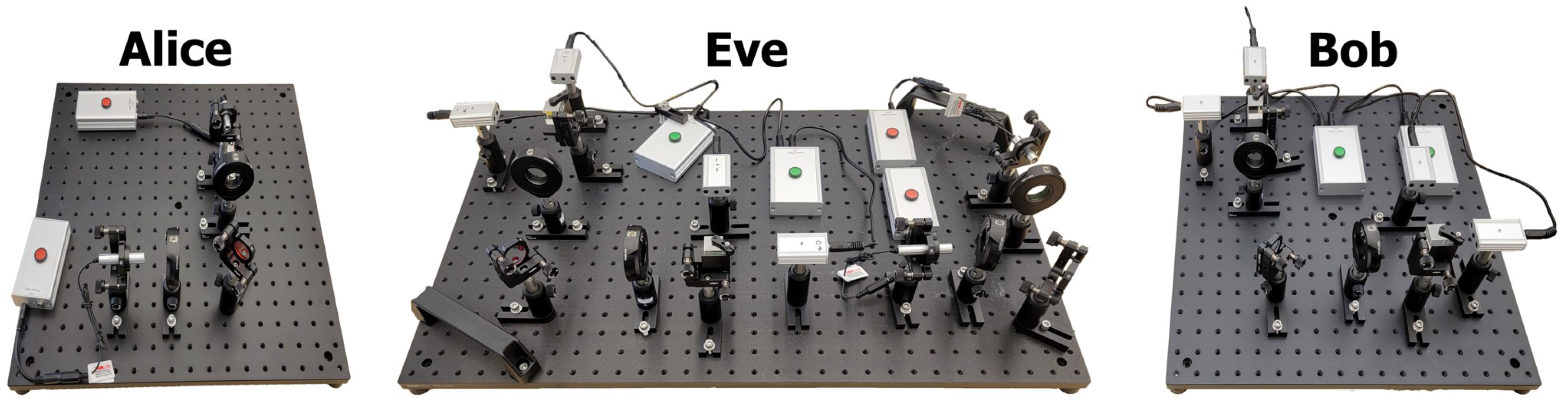
4.1. Original Thorlabs Emulation Kit
4.1.1. Operation
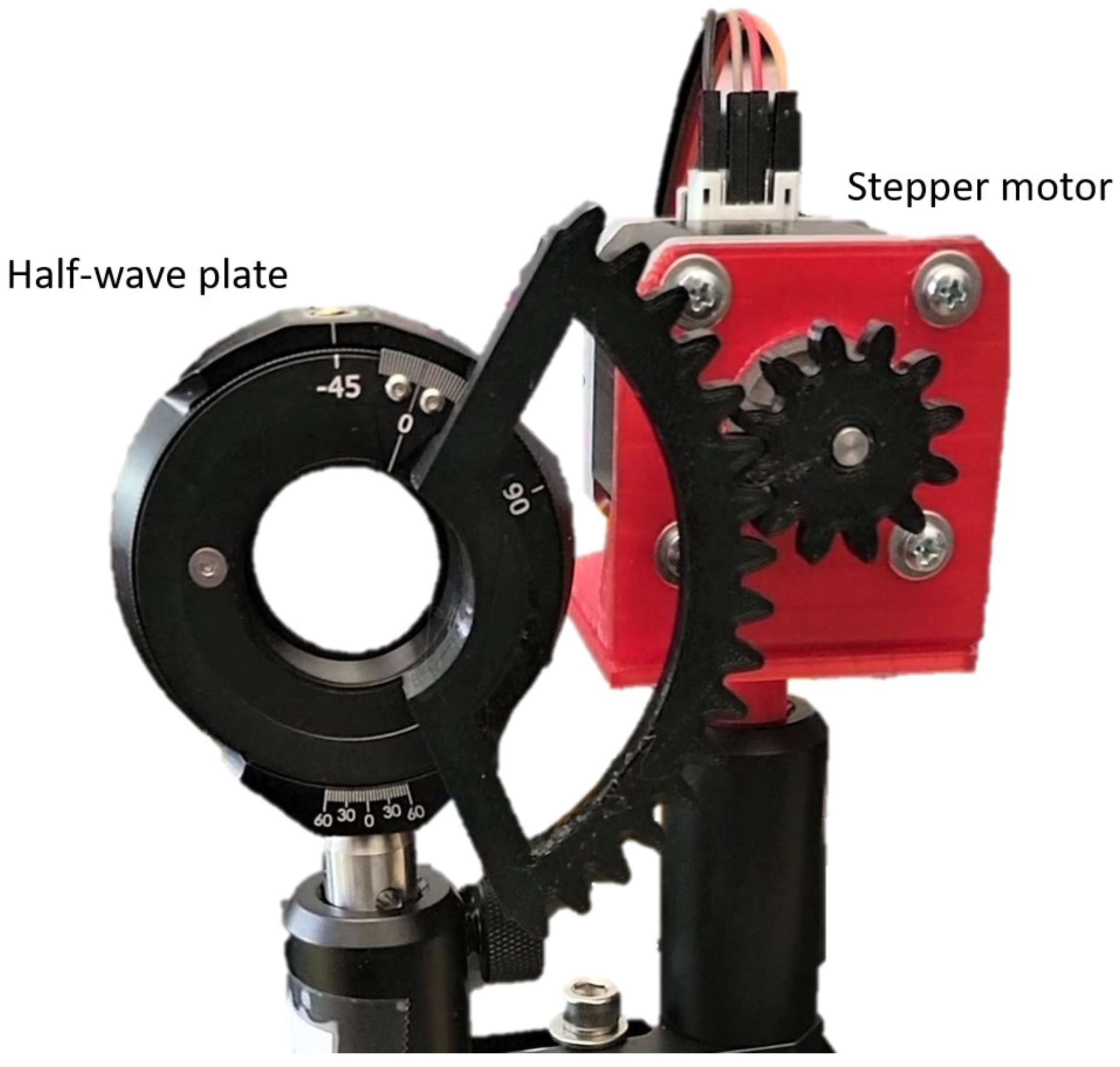
Setting up the Polarization Rotators
Data Transmission
4.2. Modifications to Include Two Wavelengths
4.2.1. Hardware
4.2.2. Software
4.3. PUF Implementation
4.4. System Setup
4.4.1. Overview
4.4.2. PUF Integration
4.4.3. Prototyping Setup (Test Bench)
5. Preliminary Results and Validation of QKD Emulation with PUF
- 1.
- Transmitting 75 trits for a constant basis and input trit combination.
- 2.
- Transmitting 75 trits by cycling through different basis and input trit combinations.
- 3.
- Transmitting a sample key of length 75 trits.
5.1. Holding Input Combinations Constant
5.2. Changing Input Combinations
5.3. Generating a Sample Key
5.4. PUF Error
5.5. Summary of Results
6. Future Work
6.1. Studying the Emulation System Error Rates
6.2. Bitwise Transform
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| QKD | Quantum Key Distribution |
| PUF | Physical Unclonable Function |
| RSA | Rivest–Shamir–Adleman |
| ECC | Elliptic Curve Cryptography |
| PNS | Photon Number Splitting |
| SSP99 | Six-State Protocol 1999 |
| ReRAM | Resistive Random-Access Memory |
| TAPKI | Ternary Addressable Public Key Infrastructure |
| HWP | Half-Wave Plate |
| PCB | Printed Circuit Board |
| IC | Integrated Circuit |
| GPIO | General-Purpose Input/Output |
| ADC | Analog-to-Digital Converter |
| RAM | Random Access Memory |
| I/O | Input/Output |
| Math Symbols | |
| ADD, | Addition Modulo 2 |
| ADD, | Addition Modulo 3 |
| ADD, | Addition Modulo 4 |
| ⊕ | XOR |
| Mask | |
| Bitwise transform | |
| Ternary transform | |
| Quaternary transform | |
| Octal transform | |
| Quatrit |
References
- McMahon, D. Quantum Computing Explained, 1st ed.; Wiley: New York, NY, USA, 2011. [Google Scholar]
- Priyanka, M.; Sinha, U. Study of BB84 QKD protocol: Modifications and attacks. Retrieved August 2020, 8. [Google Scholar]
- Yunakovsky, S.E.; Kot, M.; Pozhar, N.; Nabokov, D.; Kudinov, M.; Guglya, A.; Kiktenko, E.O.; Kolycheva, E.; Borisov, A.; Fedorov, A.K. Towards security recommendations for public-key infrastructures for production environments in the post-quantum era. EPJ Quantum Technol. 2021, 8, 14. [Google Scholar] [CrossRef]
- Bennett, C.H.; Bessette, F.; Brassard, G.; Salvail, L.; Smolin, J. Experimental quantum cryptography. J. Cryptol. 1992, 5, 3–28. [Google Scholar] [CrossRef]
- Fickler, R.; Prabhakar, S. Chapter 8—Quantum communication with structured photons. In Structured Light for Optical Communication; Al-Amri, M.D., Andrews, D.L., Babiker, M., Eds.; Nanophotonics, Elsevier: Amsterdam, The Netherlands, 2021; pp. 205–236. [Google Scholar] [CrossRef]
- Cambou, B.F.; Montano, I.; Behunin, R.; Rodriguez, V. Secure Multi-State Quantum Key Distribution with Wavelength Division Multiplexing. US Patent App. 16/951,760, 2021. [Google Scholar]
- Hong, K.W.; Foong, O.M.; Low, T.J. Challenges in quantum key distribution: A review. In Proceedings of the 4th International Conference on Information and Network Security, Shanghai, China, 25–26 September 2016; pp. 29–33. [Google Scholar]
- Scharitzer, G. Basic Quantum Cryptography, version 0.9; Vienna University of Technology Institute of Automation: Vienna, Austria, 2003. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Alshehri, O.; Li, Z.H.; Al-Amri, M. Chapter 1—Basics of quantum communication. In Structured Light for Optical Communication; Al-Amri, M.D., Andrews, D.L., Babiker, M., Eds.; Nanophotonics, Elsevier: Amsterdam, The Netherlands, 2021; pp. 1–36. [Google Scholar] [CrossRef]
- Kong, P.Y. A review of quantum key distribution protocols in the perspective of smart grid communication security. IEEE Syst. J. 2020, 16, 41–54. [Google Scholar] [CrossRef]
- Ch, H.B.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing int. In Proceedings of the Conference on Computers, Systems and Signal Processing, Bangalore, India, 9–12 December 1984; Volume 175. [Google Scholar]
- Rothberg, J. Physics 225/315 Outline: Introduction to Quantum Mechanics Lecture Notes. unpublished.
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar] [CrossRef]
- Shu, H. Solving single photon detector problems. arXiv 2022, arXiv:2203.02905. [Google Scholar]
- Lo, H.K.; Ma, X.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef] [Green Version]
- Huang, A.; Sun, S.H.; Liu, Z.; Makarov, V. Quantum key distribution with distinguishable decoy states. Phys. Rev. A 2018, 98, 012330. [Google Scholar] [CrossRef] [Green Version]
- Sekar, R. A report on Decoy State Quantum Key Distribution. 2017. Available online: https://ramanans1.github.io/docs/ias_srfp2017_report.pdf (accessed on 1 May 2022).
- Bennett, C.H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 1992, 68, 3121. [Google Scholar] [CrossRef]
- Shukla, M.; Patel, S. Prominent Security of the Quantum Key Distribution Protocol. Int. J. Sci. Res. 2018, 8. Available online: https://www.ijsr.net/archive/v8i7/ART20199396.pdf (accessed on 1 May 2022).
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef] [Green Version]
- Abushgra, A.A. Variations of QKD Protocols Based on Conventional System Measurements: A Literature Review. Cryptography 2022, 6, 12. [Google Scholar] [CrossRef]
- Krithika, S. Quantum key distribution (QKD): A review on technology, recent developments and future prospects. Res. J. Eng. Technol. 2017, 8, 291–294. [Google Scholar] [CrossRef]
- Bechmann-Pasquinucci, H.; Gisin, N. Incoherent and coherent eavesdropping in the six-state protocol of quantum cryptography. Phys. Rev. A 1999, 59, 4238. [Google Scholar] [CrossRef] [Green Version]
- Lo, H.K.; Chau, H.F.; Ardehali, M. Efficient quantum key distribution scheme and a proof of its unconditional security. J. Cryptol. 2005, 18, 133–165. [Google Scholar] [CrossRef] [Green Version]
- Sharifi, M.; Azizi, H. A simulative comparison of bb84 protocol with its improved version. J. Comput. Sci. Technol. 2007, 7, 204–208. [Google Scholar]
- Buttler, W.T.; Lamoreaux, S.K.; Torgerson, J.R.; Nickel, G.; Donahue, C.; Peterson, C.G. Fast, efficient error reconciliation for quantum cryptography. Phys. Rev. A 2003, 67, 052303. [Google Scholar] [CrossRef] [Green Version]
- Yan, H.; Peng, X.; Lin, X.; Jiang, W.; Liu, T.; Guo, H. Efficiency of winnow protocol in secret key reconciliation. In Proceedings of the 2009 WRI World Congress on Computer Science and Information Engineering, Washington, DC, USA, 31 March 2009–2 April 2009; IEEE: Piscataway, NJ, USA, 2009; Volume 3, pp. 238–242. [Google Scholar]
- Zhu, M.; Cui, K.; Li, S.; Kong, L.; Tang, S.; Sun, J. A Code Rate-Compatible High-Throughput Hardware Implementation Scheme for QKD Information Reconciliation. J. Light. Technol. 2022, 40, 3786–3793. [Google Scholar] [CrossRef]
- Li, H.W.; Zhang, C.M.; Jiang, M.S.; Cai, Q.Y. Improving the performance of practical decoy-state quantum key distribution with advantage distillation technology. Commun. Phys. 2022, 5, 53. [Google Scholar] [CrossRef]
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661–663. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bhunia, S.; Tehranipoor, M. Chapter 12—Hardware Security Primitives. In Hardware Security; Morgan Kaufmann: Burlington, MA, USA, 2019; pp. 311–345. [Google Scholar] [CrossRef]
- Mohanty, S.P.; Sengupta, A. Physical Unclonable Functions (PUFs). In IP Core Protection and Hardware-Assisted Security for Consumer Electronics; Institution of Engineering and Technology: London, UK, 2019; p. 1. [Google Scholar]
- Cambou, B.F.; Quispe, R.C.; Babib, B. Puf with Dissolvable Conductive Paths. US Patent App. 16/493,263, 2020. [Google Scholar]
- Bhunia, S.; Tehranipoor, M. Chapter 1—Introduction to Hardware Security. In Hardware Security; Bhunia, S., Tehranipoor, M., Eds.; Morgan Kaufmann: London, UK, 2019; pp. 1–20. [Google Scholar] [CrossRef]
- Korenda, A.R.; Afghah, F.; Cambou, B.; Philabaum, C. A Proof of Concept SRAM-based Physically Unclonable Function (PUF) Key Generation Mechanism for IoT Devices. In Proceedings of the 2019 16th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Boston, MA, USA, 10–13 June 2019; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Cambou, B.; Orlowski, M. PUF Designed with Resistive RAM and Ternary States. In Proceedings of the 11th Annual Cyber and Information Security Research Conference, CISRC’16, Oak Ridge, TN, USA, 5–7 April 2016; Association for Computing Machinery: New York, NY, USA, 2016. [Google Scholar] [CrossRef]
- Habib, B.; Cambou, B.; Booher, D.; Philabaum, C. Public key exchange scheme that is addressable (PKA). In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 392–393. [Google Scholar]
- Cambou, B.; Telesca, D. Ternary Computing to Strengthen Cybersecurity. In Proceedings of the Intelligent Computing, London, UK, 16–17 July 2019; Arai, K., Kapoor, S., Bhatia, R., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 898–919. [Google Scholar]
- Cambou, B.F. Encryption Schemes with Addressable Elements. US Patent App. 17/499,583, 2022. [Google Scholar]
- Cambou, B.F.; Philabaum, C.R.; Telesca, D.A. Key Exchange Schemes with Addressable Elements. US Patent 11,265,151, 2022. [Google Scholar]
- Cambou, B.; Telesca, D.; Assiri, S.; Garrett, M.; Jain, S.; Partridge, M. TRNGs from Pre-Formed ReRAM Arrays. Cryptography 2021, 5, 8. [Google Scholar] [CrossRef]
- Cambou, B. Random Number Generating Systems and Related Methods. US Patent 9,971,566, 2018. [Google Scholar]
- Cambou, B. Physically Unclonable Function Generating Systems and Related Methods. US Patent 9,985,791, 2018. [Google Scholar]






|
| Alice Basis | + | + | + | x | x | x | x |
| Bob Basis | + | + | + | x | x | x | + |
| Input | - | + | 0 | - | + | 0 | - |
| No. of Errors | 0 | 0 | 0 | 0 | 0 | 0 | 34 |
| Total No. Trits Sent | 75 | 75 | 75 | 75 | 75 | 75 | 75 |
| Alice Basis | + | + | x | x | x | + | x | + | + | x | x | x | + | x | + | + | x | x | x | + | x |
| Bob Basis | + | + | + | x | x | + | x | + | + | + | x | x | + | x | + | + | + | x | x | + | x |
| Input | - | + | - | - | + | 0 | 0 | - | + | - | - | + | 0 | 0 | - | + | - | - | + | 0 | 0 |
| Output | - | + | - | - | + | 0 | 0 | - | + | - | - | + | 0 | 0 | - | + | 0 | - | + | 0 | 0 |
| Alice Basis | + | x | + | x | x | + | + | + | + | x | + | x | + | x | x | + | x | x | x | x | + | x |
| Bob Basis | x | x | x | + | x | x | x | x | + | + | + | + | x | x | + | + | + | x | + | x | x | + |
| Alice Input | - | + | + | - | - | + | - | - | + | + | - | - | - | + | + | + | + | - | + | - | + | + |
| Bob Output | + | + | - | + | - | 0 | - | 0 | + | 0 | - | 0 | 0 | + | - | + | - | - | 0 | - | 0 | - |
| Sifted Key | + | - | + | - | + | + | - | - |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Riggs, B.; Partridge, M.; Cambou, B.; Burke, I.; Rios, M.A.; Heynssens, J.; Ghanaimiandoab, D. Multi-Wavelength Quantum Key Distribution Emulation with Physical Unclonable Function. Cryptography 2022, 6, 36. https://doi.org/10.3390/cryptography6030036
Riggs B, Partridge M, Cambou B, Burke I, Rios MA, Heynssens J, Ghanaimiandoab D. Multi-Wavelength Quantum Key Distribution Emulation with Physical Unclonable Function. Cryptography. 2022; 6(3):36. https://doi.org/10.3390/cryptography6030036
Chicago/Turabian StyleRiggs, Brit, Michael Partridge, Bertrand Cambou, Ian Burke, Manuel Aguilar Rios, Julie Heynssens, and Dina Ghanaimiandoab. 2022. "Multi-Wavelength Quantum Key Distribution Emulation with Physical Unclonable Function" Cryptography 6, no. 3: 36. https://doi.org/10.3390/cryptography6030036
APA StyleRiggs, B., Partridge, M., Cambou, B., Burke, I., Rios, M. A., Heynssens, J., & Ghanaimiandoab, D. (2022). Multi-Wavelength Quantum Key Distribution Emulation with Physical Unclonable Function. Cryptography, 6(3), 36. https://doi.org/10.3390/cryptography6030036







