ES-HAS: ECC-Based Secure Handover Authentication Scheme for Roaming Mobile User in Global Mobility Networks
Abstract
:1. Introduction
1.1. Multi-Factor Authentication Schemes in GLOMONET
1.2. Security and Function Requirements
- Quick wrong password detection: MUs use different network-based applications which provide the credentials for users to access their services. To prove the authenticity of the MU using the services, the MU has to input the pair of identity and password. In the event of wrong input of the password, there must be a mechanism to prompt the user about the wrong input login credentials. The mechanism developed must verify the credentials and reject the request of the MUs with invalid credentials, which saves further computational and communication costs.
- Mutual authentication: In the roaming scenario, the MU is away from the HN. Therefore, the MU cannot access the services from the HN. Therefore, the foreign network serves the roaming MU present in the cell area of the FN. To access the services from the FN, the MU has to authenticate HN and FN. The FN forwards the authentication messages sent by the MU to the HN. The HN verifies the authenticity of the MU. After receiving successful verification of the MU credentials, the FN grants access to the services to the MU. In such a roaming environment, where the FN is semi-trusted, the roaming MU is not trusted and the HN is assumed to be fully trusted and thus mutual authentication between all the participating entities in the communication becomes imperative to resist security attacks, such as the man-in-the-middle attack, replay attack, and impersonation attack.
- Fairness of session key: The session key is derived between the FN and the roaming MU to establish secure communication over the insecure channel. The session key establishment requires a contribution from both communicating entities, such as the FN and MU. The derived session should not be known to the third party. Even the HN should not have knowledge of the session key agreed between the FN and MU.
- Session key update: To avoid security attacks, such as the replay attack, etc., the session is updated for every new session that is initiated between the MU and FN. To achieve the freshness of the random numbers for every session, fresh random values are chosen.
- User anonymity: User anonymity is an important security feature that the developed authentication scheme must protect. The identity of the MU should not be disclosed.
- Unlinkability: An attacker should not be able to trace the location of the MU by linking the two different sessions of the same MU.
- Resistance of well known security attacks: The designed authentication scheme should resist the security attacks, such as the replay attack, impersonation attack, stolen-smart-card attack, password-guessing attack, and the man-in-the-middle attack.
1.3. Motivation
- The session key update phase is a critical security requirement and hence must be implemented carefully while designing the authentication scheme for roaming MUs. The session key update phase maintains the freshness of the random numbers for every new session established between the MU and FN. The literature survey reveals that the authentication schemes designed for roaming MUs in GLOMONET [5,10,11,12] Could not provide the session key update phase in their proposed schemes.
- The authentication schemes developed for roaming MUs in GLOMONET should satisfy all the security requirements presented in Section 1.2.
- The design and development of lightweight secure authentication schemes are essential for resource-constrained mobile devices relative to computing power, memory and battery capacity.
1.4. Contributions of Our Research Work
- We design an efficient and more secure ECC-enabled authentication scheme for roaming MUs in GLOMONET that can potentially resist various known attacks. In the proposed scheme, a roaming MU and a serving network or FN mutually authenticate among each other during the authentication phase, and they also establish a common session key among them for secure communication.
- The BAN logic-based formal security analysis [13] proves the strength of our proposed scheme. Using such a security analysis, it is shown that the proposed scheme provides the session key security. Furthermore, to ensure other existing known attacks, the informal (non-mathematical) security analysis is also presented.
- The proposed scheme is simulated with the help of the broadly accepted automated validation of internet security protocols and applications (AVISPA) tool [14]. AVISPA tools perform formal security verification of the proposed scheme. The simulation results prove that the proposed scheme is secure against passive/active attacks, such as replay attacks and man-in-the-middle attacks.
- In addition, the proposed scheme is shown to be comparable with other existing schemes in terms of the communication and the computation costs, and it also provides better security and functionality features in comparison to those of other existing schemes. The comparative study shows that the proposed scheme is efficient and more robust for the authentication of roaming MUs as compared to other authentication schemes in GLOMONET.
1.5. Organization of the Paper
2. Literature Survey
- Their scheme provides the mobile node authentication and the FN authentication.
- Their scheme also protects user anonymity and achieves untraceability.
- Their scheme is resistant to the offline password guessing attack.
- No verification table is maintained at the server side for the password. This protects the scheme from such attacks as stolen verifier and modification attacks.
3. Mathematical Preliminaries
3.1. Basics of Elliptic Curve Cryptography
3.2. Elliptic Curve Discrete Logarithm Problem (ECDLP)
3.3. Scalar Multiplication
3.4. Elliptic Curve Diffie–Hellman Problem (ECDHP)
3.5. Elliptic Curve Diffie–Hellman (ECDH)
- End system A selects the private key where . A computes the public key as , where G is a generator point in the EC domain parameter. Let the private and public key pair of end system A be , respectively. A computes point P with the co-ordinates .
- End system A transmits to end system B over an insecure channel.
- End system B selects the private key , where . B computes the public key as , where G is a generator point in the EC domain parameter. Let the private and public key pair of end system A be , respectively. B computes point Q with co-ordinates .
- End system B transmits its public key to end system A over an insecure channel.
- The shared secret key is computed as
3.6. One-Way Hash Function
- Preimage resistance: For the given input x, it is computationally feasible to compute the hash value of x as . However, it is computationally infeasible to compute for the value x with the output value y.
- Second preimage resistance: It is computationally infeasible to obtain the second input which results in the same hash value output. Ex: If x is one input and y is the other input where such that .
- Collision resistance: A collision resistant one-way hash function takes the variable length input and generates a fixed length output of ℓ bits. The pair of inputs A indicates that an attacker randomly chooses the pair of inputs . It is computationally infeasible for a pair of inputs where to result in the same hash value such that .
3.7. Pseudo-Random Number Generators
- Select the seed based on μ. The first number is .
- At each step , the state of the PRNG is and output is . These output of the PRNG are the pseudo-random numbers, where n is some positive integer considered to be the period of the sequence [52].
3.7.1. Properties of Pseudo-Random Function
- Uniformity: This property states that the elements in the output space U generated by the pseudo-random function are divided into M equal sub-intervals, and the expected number of samples in each sub-interval k, is equal; that is, , where N is the range of the numbers uniformly distributed over the interval .
- Independence: The generated numbers in the outspace U should be independent of each other, and there should not exist any correlation between the numbers generated in succession. This implies that, given any length of output sequence where , one should not be able to predict the next number in the sequence by observing the given numbers.
- Large period: The PRNG is considered to be good if its period is large.
- Reproducibility: This property ensures that for the same seed , the same sequence of numbers is generated.
- Cryptographically Secure: The generated output sequence by the PRNGs should be cryptographically secure to be used in cryptographic applications.
3.8. Fuzzy Extractors
- Gen . Gen is a probabilistic algorithm. On the biometric input , it extracts string and an auxiliary string .
- Rep . Rep is a deterministic algorithm. Rep produces the string on the biometric input from any vector close to along with the auxiliary string .
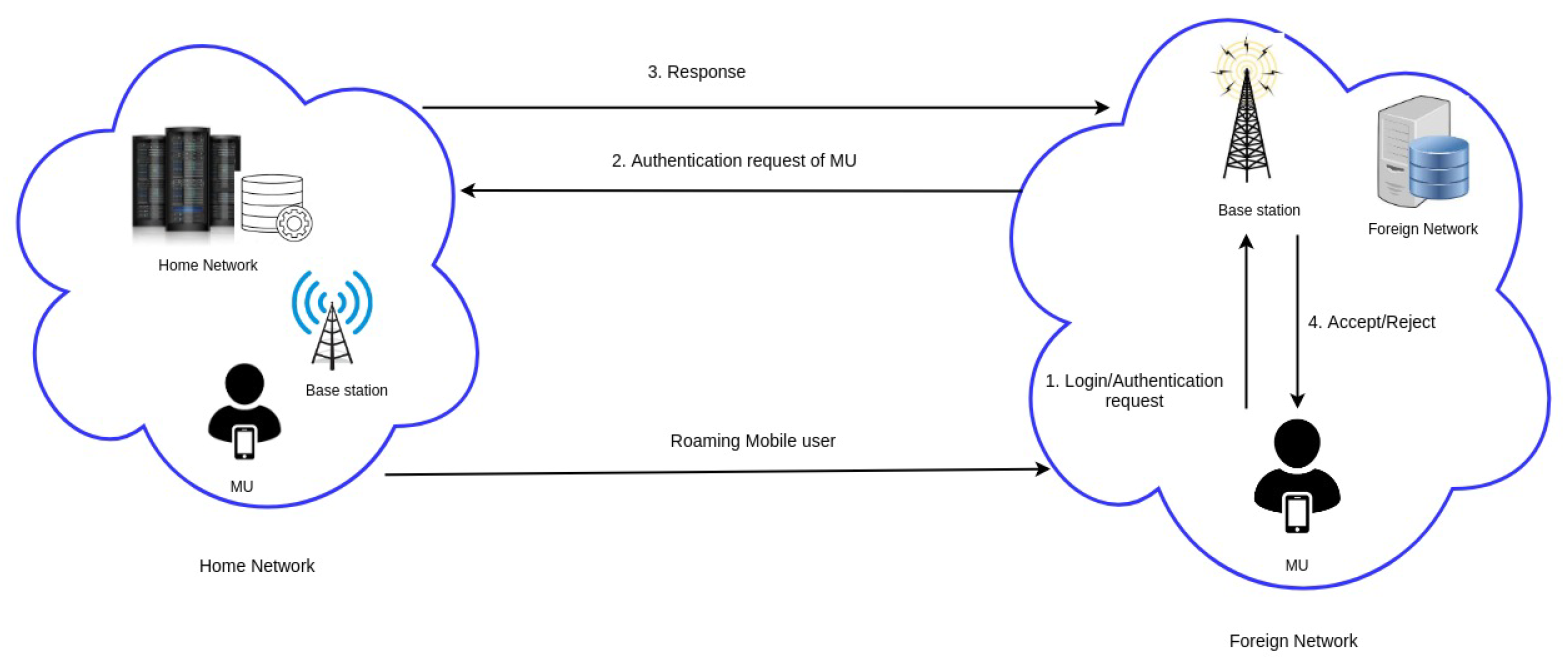
4. System Model
- Registration phase: The mobile user registers to the home network by providing credentials, identity and password. The registration phase is carried out over a secure channel. In the registration phase, the HN, after receiving the mobile user request, computes for the secret parameters. HN agrees to the domain parameters of ECC with the mobile user. These are the public key of HN, symmetric encryption key, one-way hash function. P is the generator point on ECC, and p, where p is a large prime number and n is the order of the elliptic curve (EC).
- Login or authentication phase: In the roaming scenario, the mobile user moves from their home network to the foreign network. To access services from the foreign network, the mobile user provides their identity to the foreign network. The login messages are transmitted using a wireless network through radio waves. An adversary listening to the communication channel has full control over the channel, that is, he/she can intercept, modify or alter the messages.
- The foreign network forwards the request received from the MU to the home network for the verification of the MU’s authenticity. The communication between the foreign network and the home network is considered secure.
- The home network verifies the authentication request of the mobile user received via the foreign network.
- If the MU is authentication is verified and the MU is authenticated, FN accepts the MU’s request and allows the roaming user to access the FN services. Otherwise, the FN rejects the login/authentication request sent by the MU.
4.1. Trust Model
4.2. Adversary Model
- The “Dolev–Yao threat model (DY model)” [54] is considered in our proposed scheme.
- The DY model provides an insecure channel for the communication between the entities MU, FN and HN. The FN is considered to be semi-trusted, whereas the HN is a fully trusted service provider. An attacker listening to an insecure channel has the capability to intercept the messages. The eavesdropped messages can be altered, modified or deleted.
- According to [24], there exist two dictionary spaces for mobile user’s identity and password, respectively: . Since the dictionary space is finite, an adversary can guess a pair of in polynomial time. However, it is hard for an attacker to summarize the hash results and the random numbers.
- According to [55], the adversary has full control over the public channel or insecure channel; an adversary can eavesdrop the messages transmitted over an insecure channel and then modify, alter or delete the messages to breach the security services. However, the adversary does not have any control over the secure channel.
- According to [56], the adversary can extract the stored information in the smart card through power consumption.
- An adversary can store all previous session keys. However, if the freshness of the random numbers is changed for every session, then it is difficult for an adversary to arrive at the session keys, even with the knowledge of previous session keys. This property is known as strong forward secrecy.
5. Proposed Scheme
- To establish mutual authentication among the communicating entities under the premise of anonymity;
- To derive and agree on the session key between the communicating entities fairly;
- To resist security attacks, such as stolen-smart-card attack, replay attack attack, offline password-guessing attack and impersonation attack;
- To reduce computational cost and communication cost.
5.1. Initialization Phase
- S1:
- The HN considers a non-singular elliptic curve of the form over a prime (finite) field . P is chosen as a generator point on the elliptic curve (EC).
- S2:
- The HN chooses random number as its private key and computes the HN’s public key as .
- S3:
- The symmetric encryption key of 128 bits is shared with the MU by storing it in the smart card.
- S4:
- HN computes the secret key for the foreign network as
- S5:
- HN selects the one-way hash function of the form . The input can be a variable bit length string but the output should be of a fixed length.
5.2. Registration Phase
- Step 1:
- MU → HN:In the registration phase, the MU is free to choose his/her identity and password . After choosing , and random number , the MU computes the followingThe MU submits to the HN through a secure channel.
- Step 2:
- HN → MU:.The HN receives the request from the MU and the HN chooses its random number . HN’s server public key is computed aswhere x is a random number , and P is a generator point on the elliptic curve. For every foreign network , the HN computes secret key , where is the server shared symmetric key with 128 bits. The HN stores in its database for future communication. The HN sends the smart card with the parameters to the MU through a secure channel.
- Step 3:
- MU:With the received message, the MU computes the followingThe computed value of is stored in the smart card. The smart contains the parameters .
5.3. Login Phase
- Step 1:
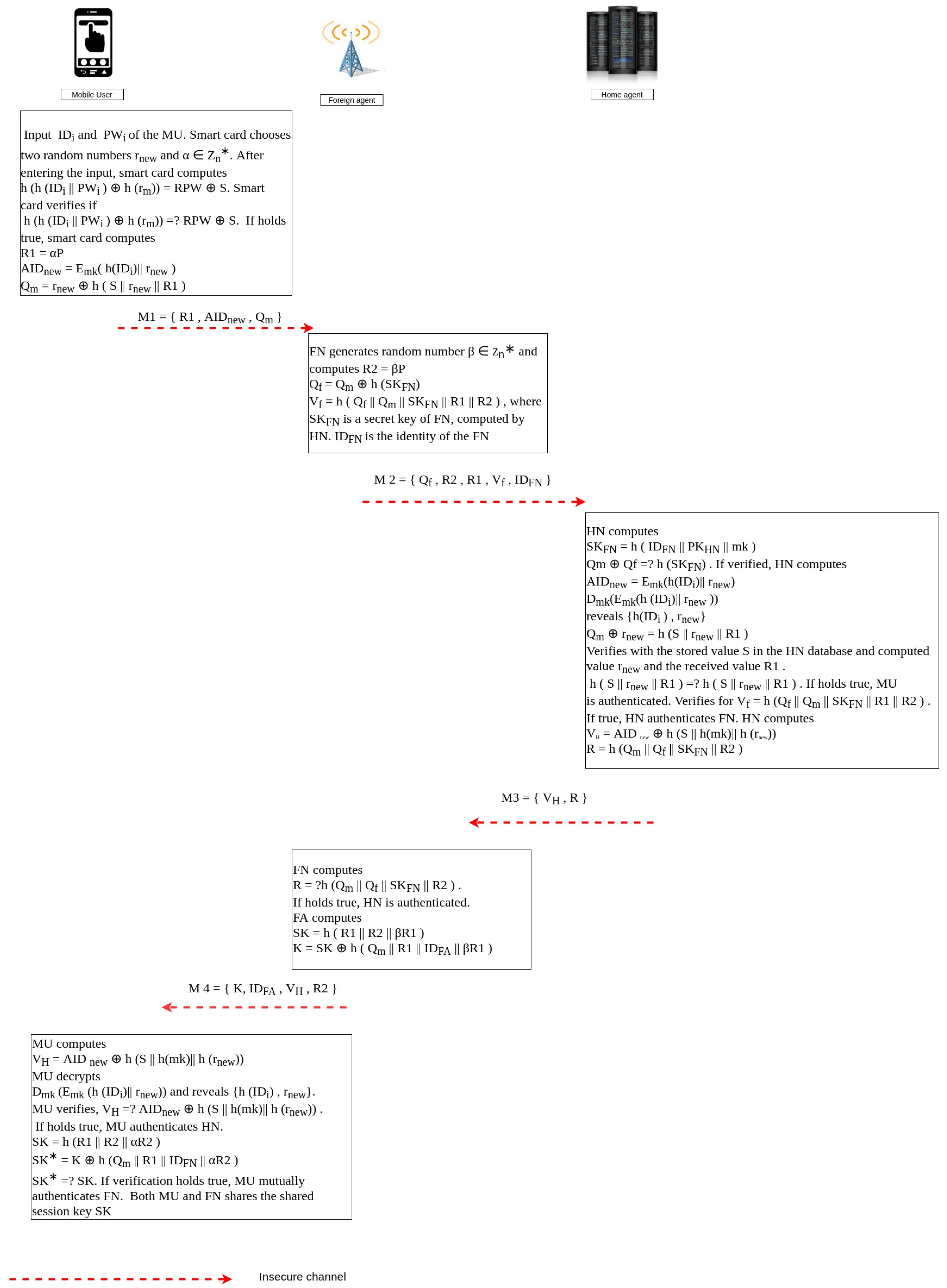
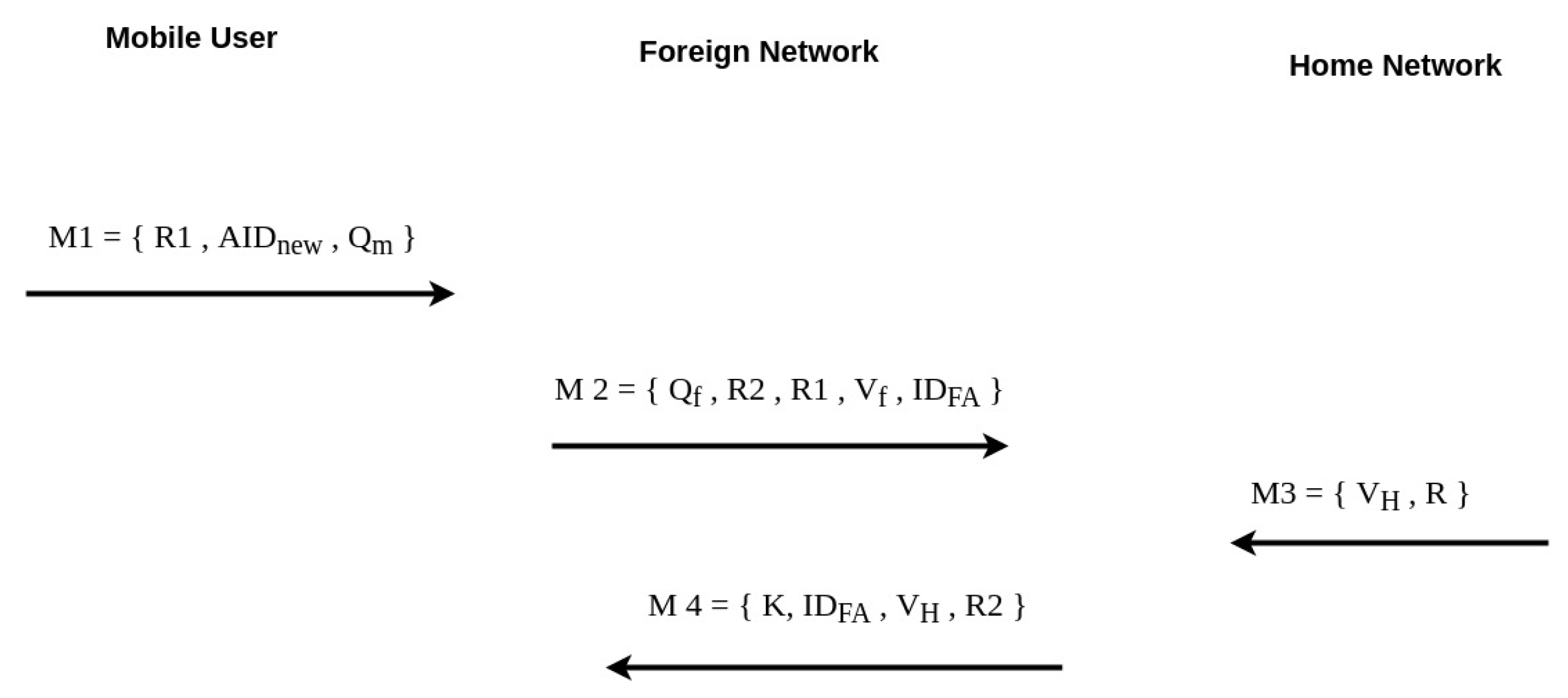
- MU → FN: Smart card is inserted into the smart card terminal by the MU. The smart card terminal asks for the input of and password of the MU. After entering the input, smart card chooses two random numbers and . The smart card verifies ifThe MU sends the message to FN over insecure channel.
- Step 2:
- FN → HN:After receiving the message from MU. FN generates random number and computes the followingwhere is a secret key of FN, computed by HN. is the identity of the FN. FN sends to HN.
5.4. Authentication Phase
- Step 1:
- HN → FN:The HN computes the following:If verified, the HN computes the following,verified with the stored value S in the HN database and computed value and the received value .After the authentication verification is completed between the MU and FN, the HN computes the following:After all the computations, the HN sends the message to the FN over a secure channel.
- Step 2:
- Foreign Network → Mobile User:After receiving the message from the HN, the FN computes the following:If it holds true, the HN is authenticated. The FN computes the following:The FN sends a message to the MU over an insecure channel.
- Step 3:
- MU:After receiving the message from the foreign network, the mobile user computes the following:If verification holds true, the MU mutually authenticates the FN. Both the MU and FN share the shared session key .
5.5. Session Key Update Phase
- Step 1:
- MU → FN:The roaming mobile user periodically updates the session key to achieve freshness in the random numbers. The session key update phase is presented in Figure 4. The MU chooses a new random number and computes.The MU sends message to the FN over an insecure channel.
- Step 2:
- FN → MU:After receiving message from the MU, the FN chooses a new random number . The FN computes the following:The FN sends message to the MU.
- Step 3:
- Mobile User:After receiving from the FN, the MU computes the following:If the verification holds true, message integrity is achieved and message authentication is verified. Therefore, the MU updates the session key as
5.6. Password Change Phase
- Step 1:
- .Verifies if .
- Step 2:
- If it holds true, the smart card allows the MU to update the current password with the new password . The smart card asks the MU to enter the new password . After that, the smart card computes.The parameter , which is stored in the smart card, is replaced with .
5.7. Proposed Two-Factor Authentication Scheme Extended to Multi-Factor Authentication Scheme
5.8. Registration Phase
- Step 1:
- MU → HN:In the registration phase, the MU is free to choose his/her identity and password along with the biometric fingerprint. The mobile device extracts the fingerprint information from the fuzzy extractor technique . After choosing , and random number , the MU computes the following:The MU submits to the HN through a secure channel.
- Step 2:
- HN → MU:.The HN receives the request from the MU and the HN chooses its random number . The HN’s server public key is computed aswhere x is a random number , and P is a generator point on the elliptic curve. HN stores in it’s database for future communication. HN sends the smart card with the parametersto the MU through secure channel.
- Step 3:
- MU:With the received message, MU computes the followingThe computed value of is stored in the smart card. The smart card contains the parameters .
6. Informal Security Analysis of the Proposed Scheme (ES-HAS)
6.1. Security against User Anonymity
6.2. Security against Stolen Smart Card Attack
6.3. Security against Offline Password-Guessing Attack
6.4. Security against Replay Attack
6.5. Perfect Forward Secrecy
6.6. Security against Impersonation Attack
- Impersonate a FN.If an adversary intercepts the message and transmitting over an insecure channel during the AESK phase and sends the same message to HN, on receiving , the HN computes . is a public key and is a secret key computed by the HN.The HN verifies if .If it holds true, the HN authenticates the FN based on its secret key computed by the HN. Thus, it is difficult for an adversary to impersonate a legal FN.
- Impersonate a MU.With the interception of message transmitting over an insecure channel, the adversary tries to reveal the identity of the parameters by capturing message and thus . The HN uses its secret key for encrypting the identity and random number of MU. To perform decryption, an adversary must have the server secret key. Thus, it is difficult to impersonate a valid MU.
6.7. Man-in-the-Middle Attack
6.8. Local Password Verification
6.9. Security against User Untraceability
7. Formal Security Analysis of the Proposed Scheme (ES-HAS) Using BAN Logic
- Message meaning rule for shared secrets:
- Nonce-verification rule:
- Jurisdiction rule:
- Receiving rule: and
- Freshness-propagation rule:
- Session-key rule:
- G1
- :
- G2
- :
- G3
- :
- G4
- :
- G5
- :
- Message M1:.
- Message M2:. Where is a secret key of FN, computed by HN.
- Message M3:.
- Message M4:.
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- .
- From message , we have the following:: . From jurisdiction rule R3 and , we have(Goal G1)
- From message , , we have(Goal G2)
- From message , and freshness propagation rule 5, we have. (Goal G3)From session-key rule 6 and , we have(Goal G4)
- From message , and session-key rule 6, we have(Goal G5)
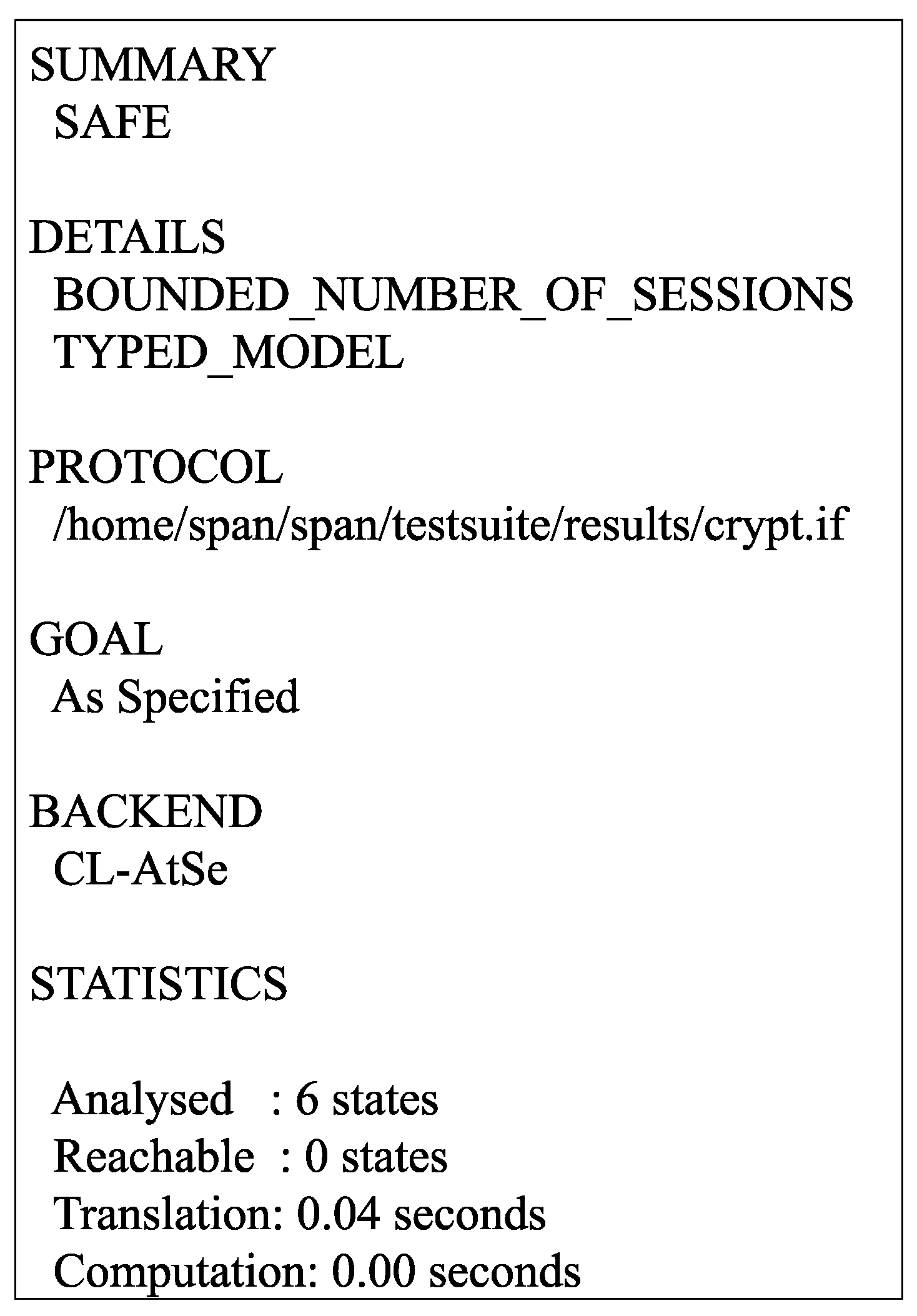
8. Formal Security Verification of the Proposed Scheme (ES-HAS) Using AVISPA Tool
8.1. Overview of AVISPA
- SUMMARY: It summarizes about the executed protocol safe or unsafe property, where safe signifies that the tested protocol is safe and unsafe signifies that the tested protocol is insecure.
- DETAILS: This section gives details about the conditions that are used in the test to make the protocol safe or unsafe.
- PROTOCOL: This section provides the name of the protocol that is to be tested.
- GOAL: The test’s goal is specified in this section.
- BACKEND: The backend name that is used to execute the test is specified in this section.
- COMMENTS and STATISTICS: This section demonstrates the attacker simulation if the test is unsafe.
- agent: It indicates the principal roles used in the HLPSL language and i denotes the intruder.
- const: It indicates constants.
- public_key: It indicates the public key used by agents in the test.
- symmetric_key: It specifies about the symmetric key used by the agents in the test.
- text: This can be used for nonces or sometimes for messages.
- nat: This signifies the natural numbers that are used in non-message contexts.
8.2. HLPSL Implementation
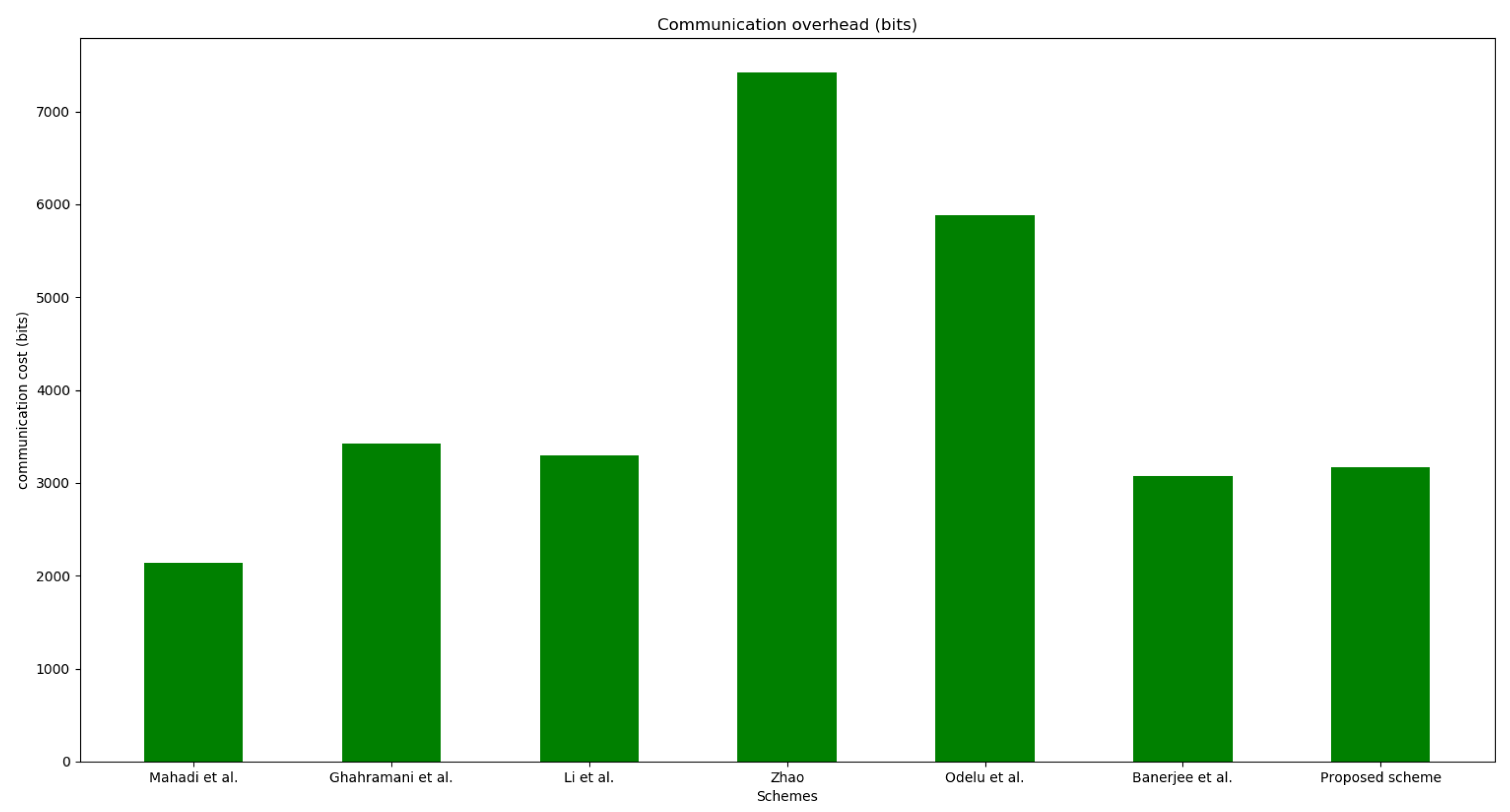
9. Performance Analysis and Comparison
- time taken to execute one hash function.
- time taken to execute one symmetric encryption/decryption operation.
- time taken to execute multiplication operation on elliptic curve.
- time of a fuzzy extractor.
- time taken to execute one asymmetric encryption/decryption operation.
- time taken to perform ECC point addition.
- time taken for sign operation.
- time of signature verification.
10. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Odelu, V.; Das, A.K.; Goswami, A. An efficient biometric-based privacy-preserving three-party authentication with key agreement protocol using smart cards. Secur. Commun. Netw. 2015, 8, 4136–4156. [Google Scholar] [CrossRef] [Green Version]
- Park, Y.; Park, Y. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Yu, S.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. A secure and efficient three-factor authentication protocol in global mobility networks. Appl. Sci. 2020, 10, 3565. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Choo, K.K.R. A robust biometrics based three-factor authentication scheme for global mobility networks in smart city. Future Gener. Comput. Syst. 2018, 83, 607–618. [Google Scholar] [CrossRef]
- Madhusudhan, R.; Shashidara, R. A secure and lightweight authentication scheme for roaming service in global mobile networks. J. Inf. Secur. Appl. 2018, 38, 96–110. [Google Scholar] [CrossRef]
- Kuo, W.C.; Wei, H.J.; Cheng, J.C. An efficient and secure anonymous mobility network authentication scheme. J. Inf. Secur. Appl. 2014, 19, 18–24. [Google Scholar] [CrossRef]
- Guo, D.; Wen, F. A More Robust Authentication Scheme for Roaming Service in Global Mobility Networks Using ECC. Int. J. Netw. Secur. 2016, 18, 217–223. [Google Scholar]
- Lee, C.C.; Lai, Y.M.; Chen, C.T.; Chen, S.D. Advanced secure anonymous authentication scheme for roaming service in global mobility networks. Wirel. Pers. Commun. 2016, 94, 1281–1296. [Google Scholar] [CrossRef]
- Karuppiah, M.; Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Khan, M.K.; Saravanan, R.; Basu, S. A dynamic id-based generic framework for anonymous authentication scheme for roaming service in global mobility networks. Wirel. Pers. Commun. 2017, 93, 383–407. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Chaudhry, S.A.; Barnawi, A.; Al-Barakati, A.; Alsharif, M.H. A privacy preserving authentication scheme for roaming in IoT-based wireless mobile networks. Symmetry 2020, 12, 287. [Google Scholar] [CrossRef] [Green Version]
- Madhusudhan, R.; Shashidhara, R. Mobile user authentication protocol with privacy preserving for roaming service in GLOMONET. Peer-to-Peer Netw. Appl. 2020, 13, 82–103. [Google Scholar] [CrossRef]
- Kang, D.; Lee, H.; Lee, Y.; Won, D. Lightweight user authentication scheme for roaming service in GLOMONET with privacy preserving. PLoS ONE 2021, 16, e0247441. [Google Scholar] [CrossRef] [PubMed]
- Burrows, J.H. Secure Hash Standard; Technical Report; Department of Commerce: Washington, DC, USA, 1995.
- AVISPA. Automated Validation of Internet Security Protocols and Applications. 2019. Available online: http://www.avispa-project.org/ (accessed on 1 March 2019).
- Hwang, M.; Yang, W. Conference key distribution schemes for secure digital mobile communication network. IEEE J. Select. Areas Commun. 1995, 13, 416–420. [Google Scholar] [CrossRef]
- Hwang, M. Dynamic participation in a secure conference scheme for mobile communications. IEEE Trans. Veh. Technol. 1999, 48, 1469–1474. [Google Scholar] [CrossRef]
- Buttyan, L.; Gbaguidi, C.; Staamann, S.; Wilhelm, U. Extensions to an authentication technique proposed for the global mobility network. IEEE Trans. Commun. 2000, 48, 373–376. [Google Scholar] [CrossRef] [Green Version]
- Hwang, K.; Chang, C. A self-encryption mechanism for authentication of roaming and teleconference services. IEEE Trans. Wirel. Commun. 2003, 2, 400–407. [Google Scholar] [CrossRef]
- Zhu, J.; Ma, J. A new authentication scheme with anonymity for wireless environments. IEEE Trans. Consum. Electron. 2004, 50, 231–235. [Google Scholar]
- Lee, C.; Hwang, M.; Liao, I. Security enhancement on a new authentication scheme with anonymity for wireless environments. IEEE Trans. Ind. Electron. 2006, 53, 1683–1687. [Google Scholar] [CrossRef]
- Wei, Y.; Qiu, H.; Hu, Y. Security analysis of authentication scheme with anonymity for wireless environments. In Proceedings of the 2006 International Conference on Communication Technology, Guilin, China, 27–30 November 2006; pp. 1–4. [Google Scholar]
- Huang, X.; Chen, X.; Li, J.; Xiang, Y.; Xu, L. Further observations on smart-card-based password-authenticated key agreement in distributed systems. IEEE Trans. Parallel Distrib. Syst. 2013, 25, 1767–1775. [Google Scholar] [CrossRef]
- Juang, W.S.; Chen, S.T.; Liaw, H.T. Robust and efficient password-authenticated key agreement using smart cards. IEEE Trans. Ind. Electron. 2008, 55, 2551–2556. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W.; Wu, T.C. Novel anonymous authentication scheme using smart cards. IEEE Trans. Ind. Inform. 2012, 9, 10. [Google Scholar] [CrossRef]
- Xu, G.; Liu, J.; Lu, Y.; Zeng, X.; Zhang, Y.; Li, X. A novel efficient MAKA protocol with desynchronization for anonymous roaming service in global mobility networks. J. Netw. Comput. Appl. 2018, 107, 83–92. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. An efficient mutual authentication and key agreement scheme preserving strong anonymity of the mobile user in global mobility networks. J. Netw. Comput. Appl. 2015, 62, 1–8. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Babamohammadi, A.; Abbasinezhad-Mood, D.; Nikooghadam, M. Efficient privacy-preserving authentication scheme for roaming consumer in global mobility networks. Int. J. Commun. Syst. 2019, 32, e3904. [Google Scholar] [CrossRef]
- Arshad, H.; Rasoolzadegan, A. A secure authentication and key agreement scheme for roaming service with user anonymity. Int. J. Commun. Syst. 2017, 30, e3361. [Google Scholar] [CrossRef]
- Chen, R.; Peng, D. An anonymous authentication scheme with the enhanced security for wireless communications. Wirel. Pers. Commun. 2017, 97, 2665–2682. [Google Scholar] [CrossRef]
- Xie, Q.; Hu, B.; Tan, X.; Wong, D.S. Chaotic maps-based strong anonymous authentication scheme for roaming services in global mobility networks. Wirel. Pers. Commun. 2017, 96, 5881–5896. [Google Scholar] [CrossRef]
- Wei, F.; Vijayakumar, P.; Jiang, Q.; Zhang, R. A mobile intelligent terminal based anonymous authenticated key exchange protocol for roaming service in global mobility networks. IEEE Trans. Sustain. Comput. 2018, 5, 268–278. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P.; Liu, J. Improved privacy-preserving authentication scheme for roaming service in mobile networks. In Proceedings of the 2014 IEEE wireless communications and networking conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 3136–3141. [Google Scholar]
- Li, H.; Yang, Y.; Pang, L. An efficient authentication protocol with user anonymity for mobile networks. In Proceedings of the 2013 IEEE wireless communications and networking conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 1842–1847. [Google Scholar]
- Shin, S.; Yeh, H.; Kim, K. An efficient secure authentication scheme with user anonymity for roaming user in ubiquitous networks. Peer-to-Peer Netw. Appl. 2015, 8, 674–683. [Google Scholar] [CrossRef]
- Farash, M.S.; Chaudhry, S.A.; Heydari, M.; Sajad Sadough, S.M.; Kumari, S.; Khan, M.K. A lightweight anonymous authentication scheme for consumer roaming in ubiquitous networks with provable security. Int. J. Commun. Syst. 2017, 30, e3019. [Google Scholar] [CrossRef]
- Karuppiah, M.; Kumari, S.; Das, A.K.; Li, X.; Wu, F.; Basu, S. A secure lightweight authentication scheme with user anonymity for roaming service in ubiquitous networks. Secur. Commun. Netw. 2016, 9, 4192–4209. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zhang, Y.; Chen, C.; Bu, J. A strong user authentication scheme with smart cards for wireless communications. Comput. Commun. 2010, 34, 367–374. [Google Scholar] [CrossRef]
- Odelu, V.; Banerjee, S.; Das, A.K.; Chattopadhyay, S.; Kumari, S.; Li, X.; Goswami, A. A secure anonymity preserving authentication scheme for roaming service in global mobility networks. Wirel. Pers. Commun. 2017, 96, 2351–2387. [Google Scholar] [CrossRef]
- Zhao, D.; Peng, H.; Li, L.; Yang, Y. A secure and effective anonymous authentication scheme for roaming service in global mobility networks. Wirel. Pers. Commun. 2014, 78, 247–269. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Xu, L.; Kumari, S.; Sangaiah, A.K. A novel mutual authentication scheme with formal proof for smart healthcare systems under global mobility networks notion. Comput. Electr. Eng. 2018, 68, 107–118. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Park, Y.; Tanwar, S. Design of an anonymity-preserving group formation based authentication protocol in global mobility networks. IEEE Access 2018, 6, 20673–20693. [Google Scholar] [CrossRef]
- Karuppiah, M.; Saravanan, R. A secure authentication scheme with user anonymity for roaming service in global mobility networks. Wirel. Pers. Commun. 2015, 84, 2055–2078. [Google Scholar] [CrossRef]
- Lu, Y.; Xu, G.; Li, L.; Yang, Y. Robust privacy-preserving mutual authenticated key agreement scheme in roaming service for global mobility networks. IEEE Syst. J. 2019, 13, 1454–1465. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. Lightweight and energy-efficient mutual authentication and key agreement scheme with user anonymity for secure communication in global mobility networks. IEEE Syst. J. 2016, 10, 1370–1379. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Shojafar, M.; Conti, M. Pakit: Proactive authentication and key agreement protocol for internet of things. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 348–353. [Google Scholar]
- Wan, Z.; Xu, Z.; Liu, S.; Ni, W.; Ye, S. An internet of things roaming authentication protocol based on heterogeneous fusion mechanism. IEEE Access 2020, 8, 17663–17672. [Google Scholar] [CrossRef]
- Ghahramani, M.; Javidan, R.; Shojafar, M. A secure biometric-based authentication protocol for global mobility networks in smart cities. J. Supercomput. 2020, 76, 8729–8755. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Li, G.; Yang, L. An enhanced authentication scheme with privacy preservation for roaming service in global mobility networks. Wirel. Pers. Commun. 2013, 68, 1477–1491. [Google Scholar] [CrossRef]
- Neil, K. Ëlliptc Curve Cryptosystem. Math. Comput. 1987, 48, 203–209. [Google Scholar]
- Rogaway, P.; Shrimpton, T. Cryptographic hash-function basics: Definitions, implications, and separations for preimage resistance, second-preimage resistance, and collision resistance. In International Workshop on Fast Software Encryption; Springer: Berlin, Germany, 2004; pp. 371–388. [Google Scholar]
- Bhattacharjee, K.; Maity, K.; Das, S. A search for good pseudo-random number generators: Survey and empirical studies. arXiv 2018, arXiv:1811.04035. [Google Scholar]
- Dodis, Y.; Ostrovsky, R.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. SIAM J. Comput. 2008, 38, 97–139. [Google Scholar] [CrossRef] [Green Version]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Das, A.K.; Khan, M.K.; Karuppiah, M.; Baliyan, R. A novel and provably secure authentication and key agreement scheme with user anonymity for global mobility networks. Secur. Commun. Netw. 2016, 9, 3527–3542. [Google Scholar] [CrossRef] [Green Version]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Annual International Cryptology Conference; Springer: Berlin, Germany, 1999; pp. 388–397. [Google Scholar]
- Nikooghadam, M.; Amintoosi, H.; Kumari, S. A provably secure ECC-based roaming authentication scheme for global mobility networks. J. Inf. Secur. Appl. 2020, 54, 102588. [Google Scholar] [CrossRef]
- Li, X.; Sangaiah, A.K.; Kumari, S.; Wu, F.; Shen, J.; Khan, M.K. An efficient authentication and key agreement scheme with user anonymity for roaming service in smart city. Pers. Ubiquitous Comput. 2017, 21, 791–805. [Google Scholar] [CrossRef]



| Authors | Year | Strengths | Weaknesses |
|---|---|---|---|
| Jiang et al. [49] | 2012 | Protects user anonymity, user untraceability and provides two-factor security. Mutual authentication between MU, FN and HN are achieved. | Session key agreement is static and depends on static key agreement. |
| Kuo et al. [6] | 2014 | Their scheme protects user anonymity with untraceability. Their scheme is resilient to security attacks such as impersonation attack, replay attack, smart-card-loss attack and man-in-the-middle attack. In addition, their scheme also achieves mutual authentication and secrecy of the session key. | User untraceability is not achieved. |
| Guo et al. [7] | 2016 | Protects user anonymity and untraceability resists impersonation attack, stolen-smart-card attack, server masquerading attack and replay attacks, achieves mutual authentication and perfect forward security. | Their scheme is vulnerable to insider attack and the scheme provides no session key update. |
| CC Lee et al. [8] | 2017 | Protects user anonymity, resilient to masquerade attack, man-in-the-middle attack, stolen-smart-card attack, and offline password-guessing attack. In addition, their scheme achieves perfect forward and backward secrecy. | Their scheme cannot resist replay attacks. |
| Marimuthu et al. [9] | 2017 | Provides untraceability and secure against security attacks such as known key, insider, offline password-guessing, replay, stolen verifier, forgery and man-in-the-middle attacks. Achieves mutual authentication, user friendliness and local password verification. | Security pitfalls of their scheme are as follows: absence of user anonymity and vulnerable to security attacks, such as offline password guessing and impersonation attacks, has no password change option and no local password verification. |
| Shashidhara et al. [5] | 2018 | Protects user anonymity, and their scheme is resilient to forgery and replay attacks. | Scheme does not provide session key update phase. |
| Xiong Li et al. [4] | 2018 | Resists security attacks such as session key, replay, forgery, device lost, and denial-of-service attacks and achieves user anonymity, untraceability and mutual authentication. | Their scheme does not provide local password verification, perfect forward secrecy is not achieved, and is vulnerable to denial-of-service attack. |
| Madhusudhan and Shashidhara [11] | 2020 | Resists security attacks such as insider, offline password guessing attack, impersonation attack, bit flipping attack, replay, stolen verifier attack. In addition, their scheme achieves user anonymity, local password verification, perfect forward secrecy and mutual authentication. | Their scheme does not protect user untraceability and does not provide session key update. |
| Bander et al. [10] | 2020 | Their scheme achieves user anonymity and untraceability, resilient to security attacks, such as stolen verifier attack, insider attack, stolen-smart-card attack, forgery attack, and known session-specific parameter attack. In addition, their scheme achieves user anonymity and protects user untraceability, perfect forward secrecy and mutual authentication. | Their scheme does not protect against password guessing and does not provide session key update. |
| Kang et al. [12] | 2020 | Their scheme achieves user anonymity and untraceability, resilient to security attacks such as mobile node impersonation attack, insider attack, foreign bypass attack and session-key-derived attack. In addition, their scheme achieves perfect forward secrecy and mutual authentication. | Their scheme does not provide session key update. |
| Notation | Representation |
|---|---|
| MU | Mobile User |
| FN | Foreign Network |
| HN | Home Network |
| MU’s identity | |
| MU’s password | |
| HN’s identity | |
| FN’s identity | |
| Secret key of FN | |
| Public key of HN | |
| Server master key is a symmetric key of 128 bit | |
| SK | Session key exchanged with FN and MU |
| X | Secret key of HN |
| P | Generator point |
| p | Large prime number |
| n | Elliptic curve order |
| h | Cryptographic hash function, , where l = 160 bits |
| symmetric encryption algorithm | |
| where a |
| Notation | Definition |
|---|---|
| P believes X: P would be entitled to believe X. | |
| P sees X: P can receive and read X | |
| P said X: P once said X | |
| P controls X: P has jurisdiction over X | |
| Fresh (X): The formula X is fresh | |
| X is integrated with y; y should be kept secret | |
| K is used as a shared key between P and Q | |
| The formula y is shared between two principals P and Q | |
| Y is hash of X |
| S1 | S2 | S3 | S4 | S5 | S6 | S7 | S8 | S9 | |
|---|---|---|---|---|---|---|---|---|---|
| Mahadi et al. [57] | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Ghahramani et al. [48] | Yes | No | Yes | No | No | No | Yes | No | No |
| Li et al. [4] | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| Zhao [40] | No | No | No | Yes | Yes | Yes | No | Yes | No |
| Odelu et al. [39] | Yes | No | Yes | Yes | Yes | Yes | No | Yes | No |
| Banerjee et al. [42] | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| Li et al. [58] | No | No | No | No | Yes | Yes | Yes | Yes | Yes |
| Ours | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
K. S., S.; Rangasamy, J.; S. Kamath, S.; Lee, C.-C. ES-HAS: ECC-Based Secure Handover Authentication Scheme for Roaming Mobile User in Global Mobility Networks. Cryptography 2021, 5, 35. https://doi.org/10.3390/cryptography5040035
K. S. S, Rangasamy J, S. Kamath S, Lee C-C. ES-HAS: ECC-Based Secure Handover Authentication Scheme for Roaming Mobile User in Global Mobility Networks. Cryptography. 2021; 5(4):35. https://doi.org/10.3390/cryptography5040035
Chicago/Turabian StyleK. S., Suvidha, Jothi Rangasamy, Shyam S. Kamath, and Cheng-Chi Lee. 2021. "ES-HAS: ECC-Based Secure Handover Authentication Scheme for Roaming Mobile User in Global Mobility Networks" Cryptography 5, no. 4: 35. https://doi.org/10.3390/cryptography5040035
APA StyleK. S., S., Rangasamy, J., S. Kamath, S., & Lee, C.-C. (2021). ES-HAS: ECC-Based Secure Handover Authentication Scheme for Roaming Mobile User in Global Mobility Networks. Cryptography, 5(4), 35. https://doi.org/10.3390/cryptography5040035







