Redundancy in Key Management for WSNs
Abstract
1. Introduction
2. Related Works
2.1. Global Key
2.2. Full Pairwise Keys
2.3. Random Key Predistribution Approaches
2.4. Combinatorial Design
- a pool is composed of keys,
- the number of rings of keys, which corresponds to the maximum number of nodes, corresponds to ,
- each ring is composed by r keys,
- the same key is present in r rings, so it is shared by r nodes,
- the same set composed by more than one key cannot be present in more than one block.
3. Redundant Key Management
4. Analysis and Evaluation
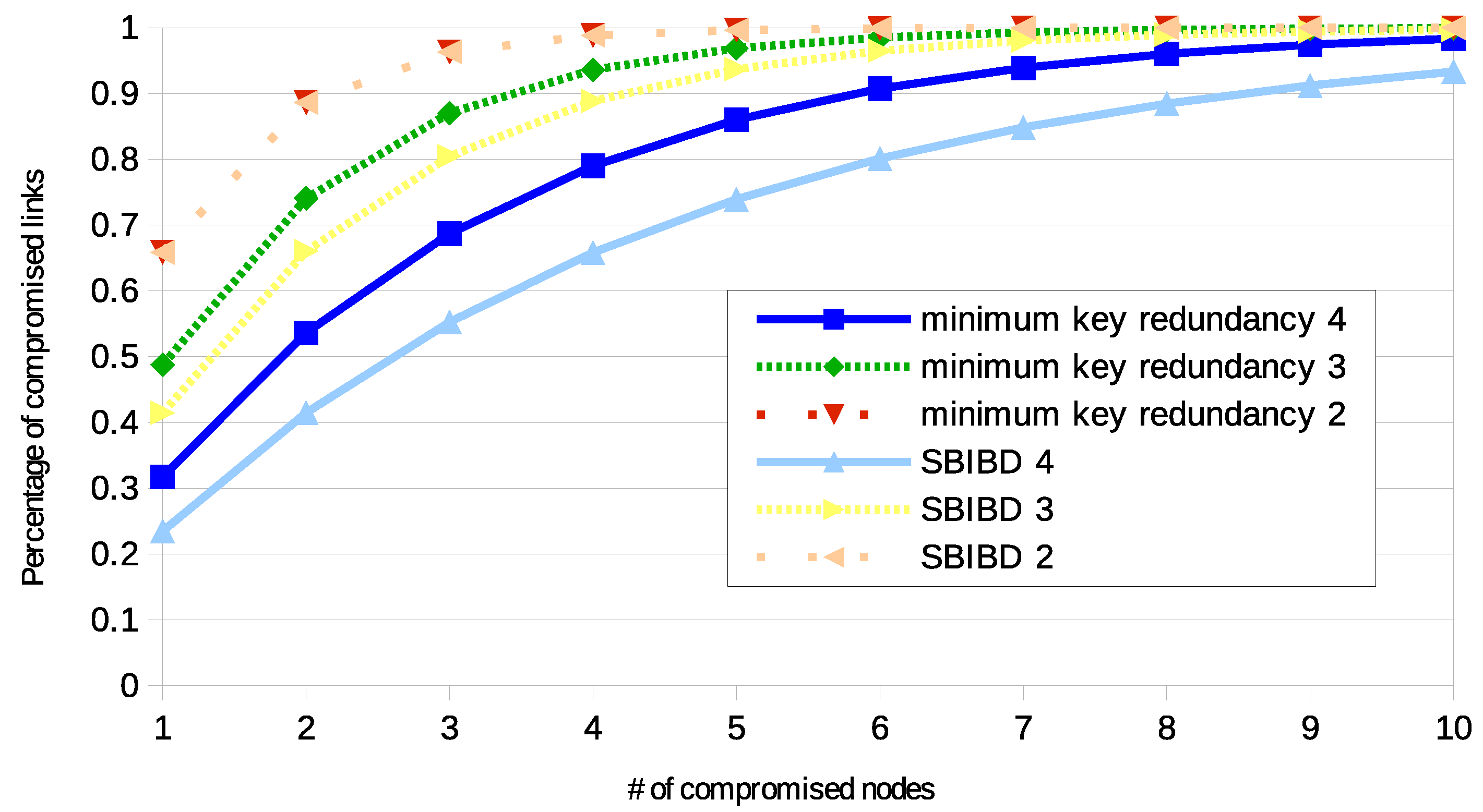
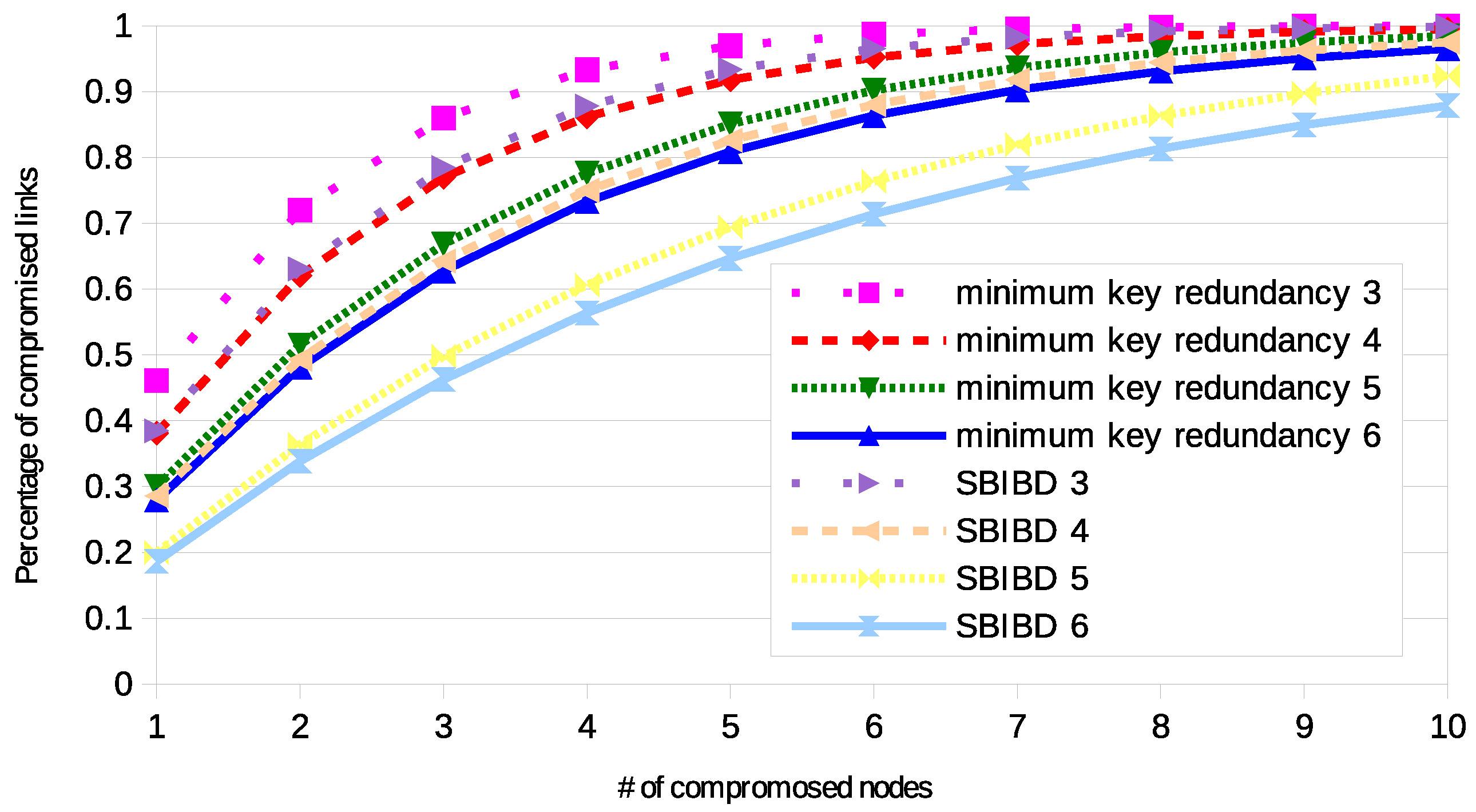
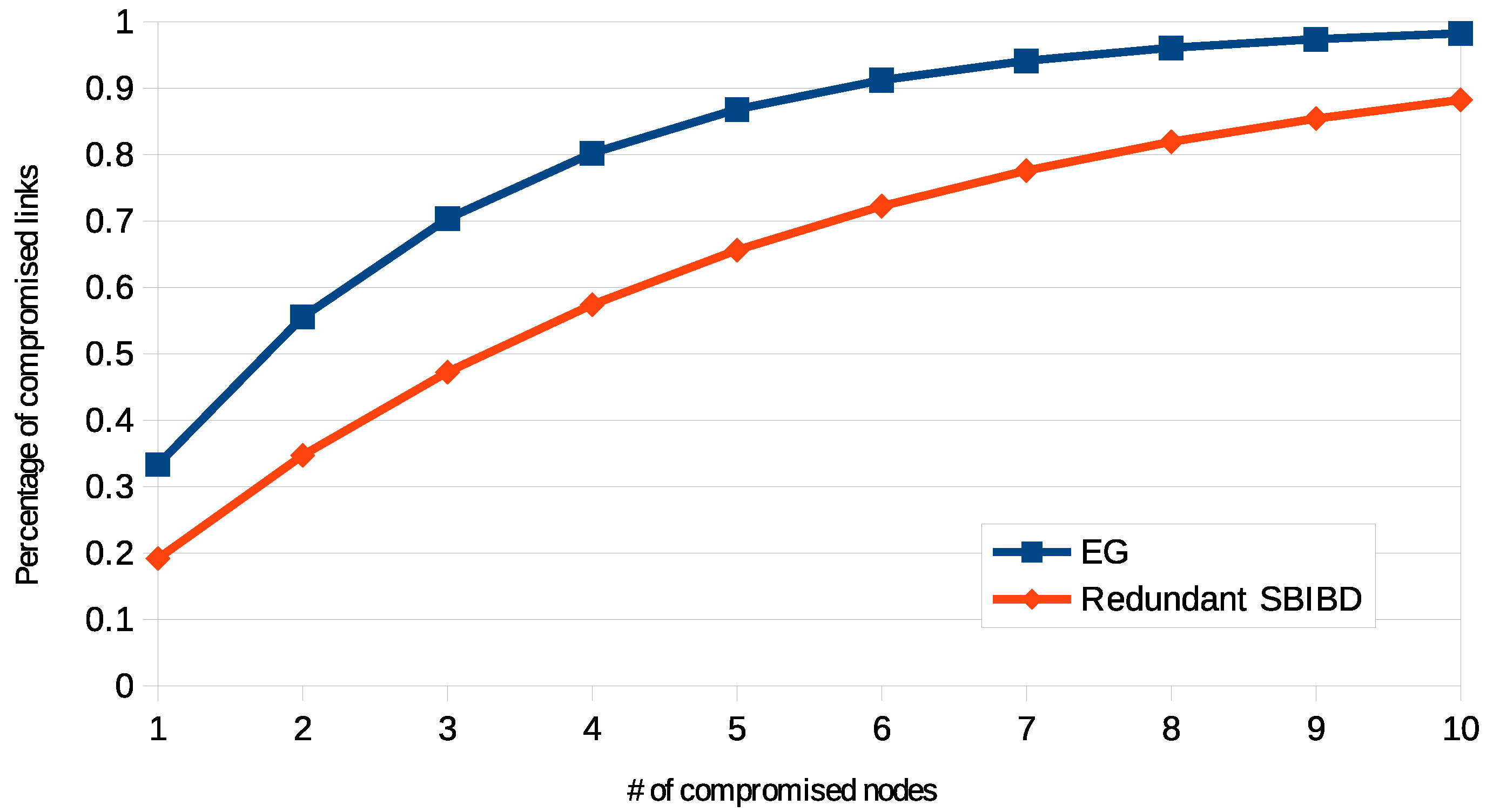
4.1. Resilience
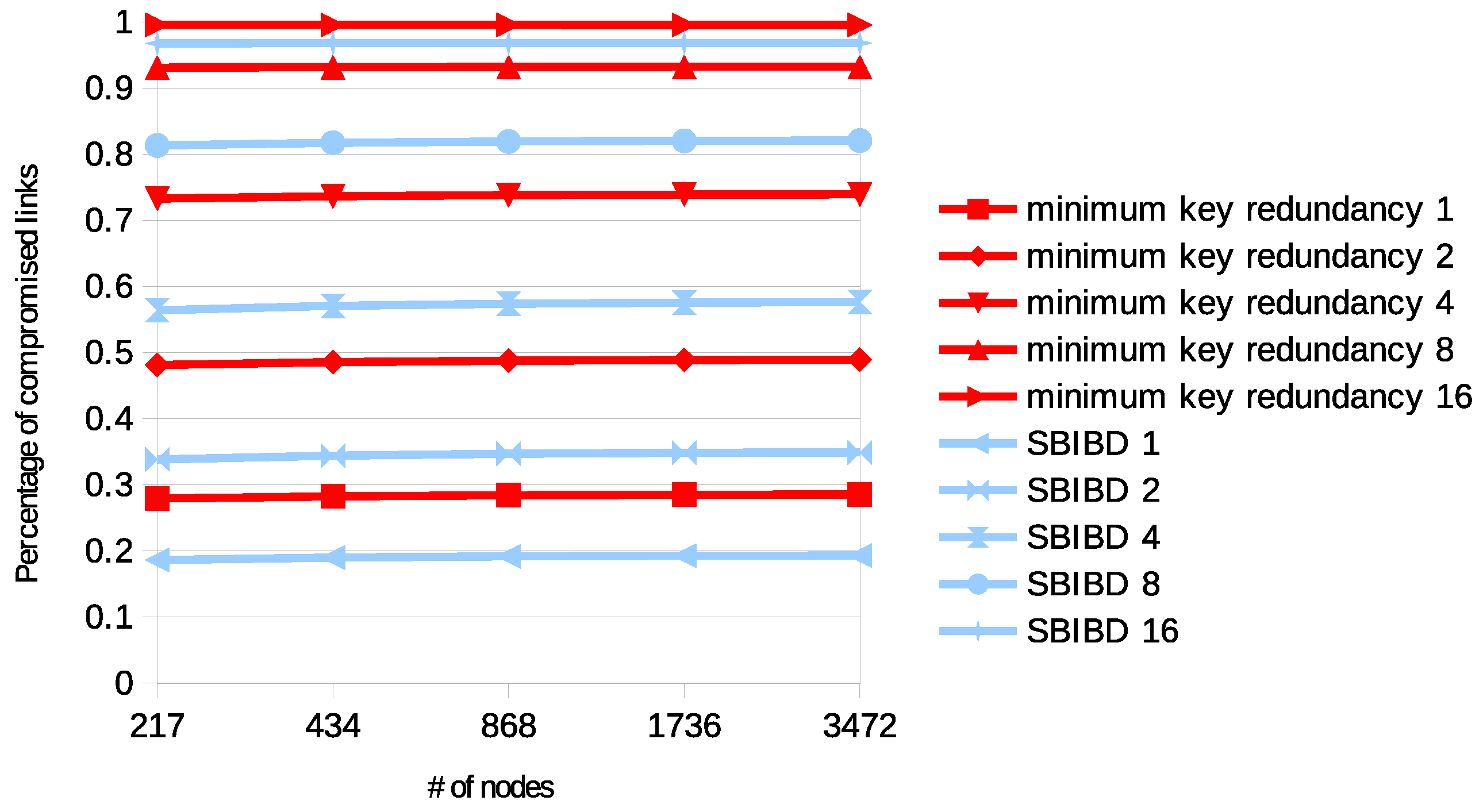
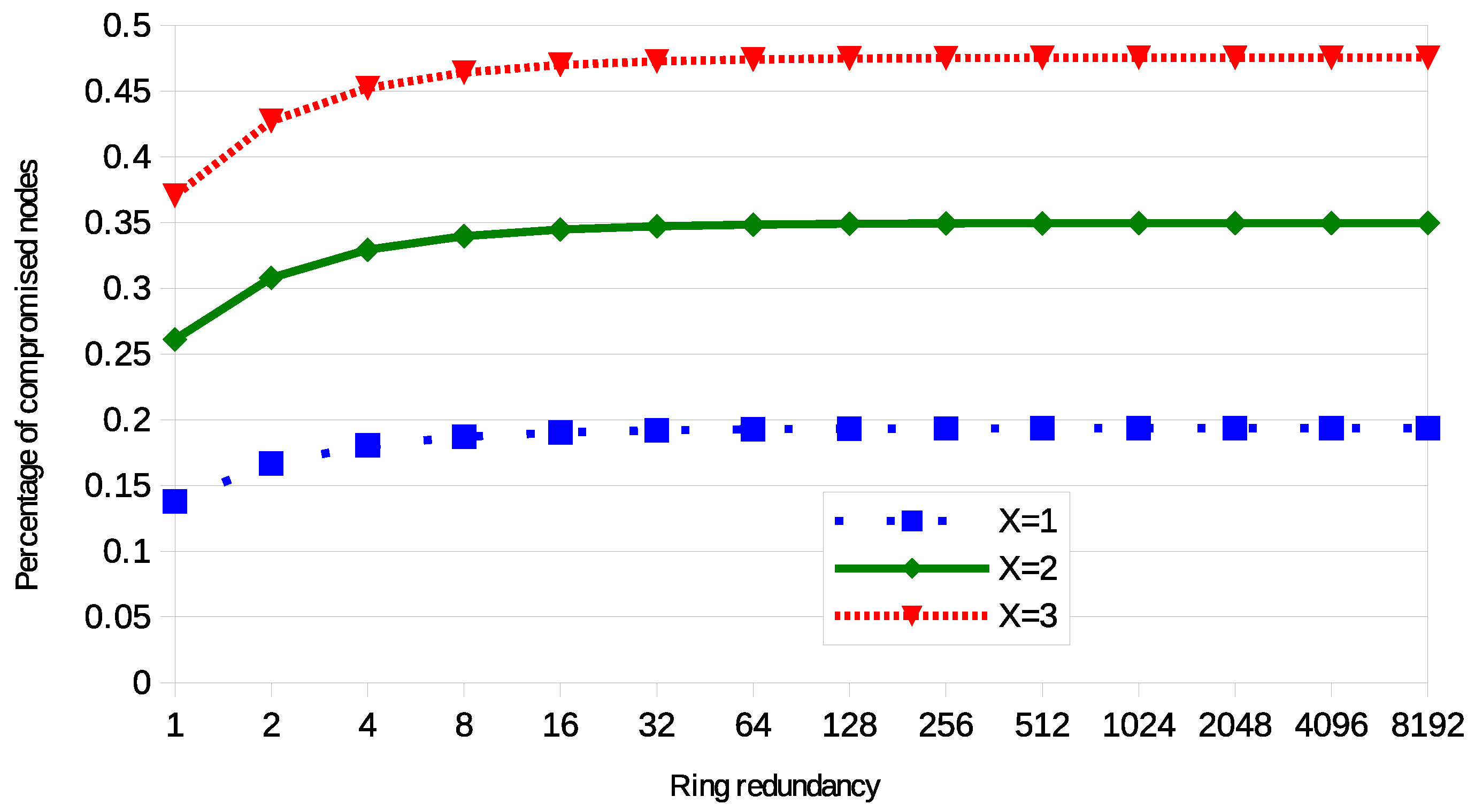
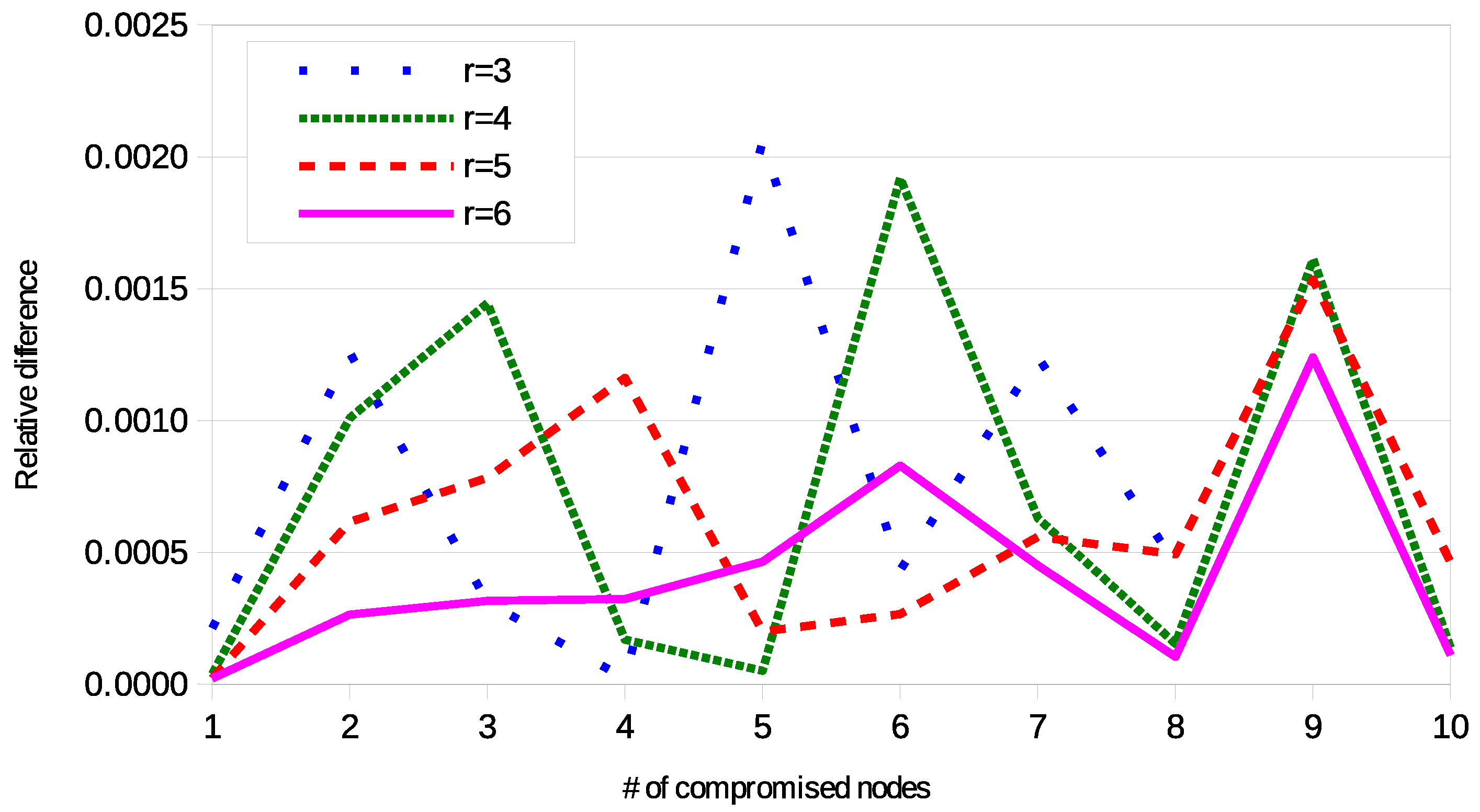
4.2. Experimental Analysis
4.3. Validation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| WSN | Wireless sensor network |
| PGK | Plain global key scheme |
| FPWK | Full pairwise keys scheme |
| SBIBD | Symmetric Balanced Incomplete Block Design |
Appendix A. Tables
| k ∖ i | 1 | 0 |
|---|---|---|
| 3 | 28 | 7 |
| 4 | 7 | 28 |
| k ∖ i | 4 | 3 | 2 | 1 | 0 |
|---|---|---|---|---|---|
| 3 | 234 | 52 | 0 | 0 | 0 |
| 4 | 0 | 234 | 468 | 0 | 13 |
| 5 | 0 | 0 | 468 | 702 | 117 |
| 6 | 0 | 0 | 78 | 936 | 702 |
| 7 | 0 | 0 | 0 | 468 | 1248 |
| 8 | 0 | 0 | 0 | 117 | 1170 |
| 9 | 0 | 0 | 0 | 13 | 702 |
| k ∖ i | 9 | 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 |
|---|---|---|---|---|---|---|---|---|---|---|
| 3 | 1120 | 210 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 4 | 0 | 0 | 2520 | 3360 | 0 | 105 | 0 | 0 | 0 | 0 |
| 5 | 0 | 0 | 0 | 1008 | 10,080 | 7560 | 1680 | 0 | 0 | 21 |
| 6 | 0 | 0 | 0 | 168 | 0 | 18,480 | 22,680 | 12,600 | 0 | 336 |
| 7 | 0 | 0 | 0 | 0 | 0 | 2520 | 31,920 | 55,440 | 23,520 | 2880 |
| 8 | 0 | 0 | 0 | 0 | 0 | 0 | 10,290 | 73,080 | 93,240 | 26,880 |
| 9 | 0 | 0 | 0 | 0 | 0 | 0 | 1120 | 42,840 | 151,200 | 98,770 |
| 10 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 13,860 | 140,448 | 198,408 |
| 11 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 2520 | 86,688 | 263,508 |
| 12 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 210 | 37,800 | 255,920 |
| 13 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 11,760 | 191,730 |
| 14 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 2520 | 113,760 |
| 15 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 336 | 53,928 |
| 16 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 21 | 20,328 |
| k ∖ i | 16 | 15 | 14 | 13 | 12 | 11 | 10 | 9 | 8 | 7 | 6 | 5 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3 | 3875 | 620 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 4 | 0 | 0 | 0 | 15,500 | 15,500 | 0 | 465 | 0 | 0 | 0 | 0 | 0 |
| 5 | 0 | 0 | 0 | 0 | 0 | 18,600 | 93,000 | 46,500 | 11,625 | 0 | 0 | 186 |
| 6 | 0 | 0 | 0 | 0 | 0 | 0 | 3100 | 62,000 | 325,500 | 232,500 | 108,500 | 0 |
| k ∖ i | 8 | 7 | 6 | 5 | 4 | 3 | 2 | 1 | 0 |
|---|---|---|---|---|---|---|---|---|---|
| 6 | 325,500 | 232,500 | 108,500 | 0 | 4650 | 0 | 0 | 0 | 31 |
| 7 | 46,500 | 434,000 | 1,100,500 | 744,000 | 257,300 | 46,500 | 0 | 0 | 775 |
| 8 | 0 | 46,500 | 697,500 | 2,522,625 | 2,938,800 | 1,302,000 | 372,000 | 0 | 9300 |
| 9 | 0 0 | 0 | 93,000 | 1,441,500 | 5,894,650 | 7,579,500 | 4,185,000 | 879,625 | 86,800 |
| 10 | 0 | 0 | 3100 | 279,000 | 4,014,965 | 13,981,000 | 17,042,250 | 7,830,600 | 1,201,250 |
| 11 | 0 | 0 | 0 | 18,600 | 1,302,000 | 12,378,300 | 32,968,500 | 29,806,500 | 8,198,415 |
| 12 | 0 | 0 | 0 | 0 | 217000 | 6,466,600 | 37,874,250 | 65,193,000 | 31,369,675 |
| 13 | 0 | 0 | 0 | 0 | 15,500 | 2,173,100 | 29,434,500 | 95,759,000 | 78,870,975 |
| 14 | 0 | 0 | 0 | 0 | 0 | 474,300 | 16,600,500 | 103,555,500 | 144,552,225 |
| 15 | 0 | 0 | 0 | 0 | 0 | 62,620 | 7,021,500 | 87,100,700 | 206,355,375 |
| 16 | 0 | 0 | 0 | 0 | 0 | 3875 | 2,241,300 | 58,838,000 | 239,457,020 |
| 17 | 0 | 0 | 0 | 0 | 0 | 0 | 530,100 | 32,468,625 | 232,183,800 |
| 18 | 0 | 0 | 0 | 0 | 0 | 0 | 88,350 | 14,725,000 | 191,439,725 |
| 19 | 0 | 0 | 0 | 0 | 0 | 0 | 9300 | 5,471,500 | 135,639,725 |
| 20 | 0 | 0 | 0 | 0 | 0 | 0 | 465 | 1,646,100 | 83,025,750 |
| 21 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 392,150 | 43,960,015 |
| 22 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 71,300 | 20,088,775 |
| 23 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 9300 | 7,879,425 |
| 24 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 775 | 2,628,800 |
| 25 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 31 | 736,250 |
References
- Ball, M.G.; Qela, B.; Wesolkowski, S. A Review of the Use of Computational Intelligence in the Design of Military Surveillance Networks. In Recent Advances in Computational Intelligence in Defense and Security; Abielmona, R., Falcon, R., Zincir-Heywood, N., Abbass, H.A., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 663–693. [Google Scholar]
- Badia-Melis, R.; Ruiz-Garcia, L.; Garcia-Hierro, J.; Villalba, J.I.R. Refrigerated Fruit Storage Monitoring Combining Two Different Wireless Sensing Technologies: RFID and WSN. Sensors 2015, 15, 4781–4795. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Matetić, M.; Zhou, H.; Zhang, X.; Jemrić, T. Postharvest Quality Monitoring and Variance Analysis of Peach and Nectarine Cold Chain with Multi-Sensors Technology. Appl. Sci. 2017, 7, 133. [Google Scholar] [CrossRef]
- Alvarez, R.; Caballero-Gil, C.; Santonja, J.; Zamora, A. Algorithms for Lightweight Key Exchange. Sensors 2017, 17, 1517. [Google Scholar] [CrossRef] [PubMed]
- Shim, K. A Survey of Public-Key Cryptographic Primitives in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2016, 18, 577–601. [Google Scholar] [CrossRef]
- Gandino, F.; Celozzi, C.; Rebaudengo, M. A Key Management Scheme for Mobile Wireless Sensor Networks. Appl. Sci. 2017, 7, 490. [Google Scholar] [CrossRef]
- Simplício, M.A., Jr.; Barreto, P.S.; Margi, C.B.; Carvalho, T.C. A survey on key management mechanisms for distributed Wireless Sensor Networks. Comput. Netw. 2010, 54, 2591–2612. [Google Scholar] [CrossRef]
- He, X.; Niedermeier, M.; de Meer, H. Dynamic key management in wireless sensor networks: A survey. J. Netw. Comput. Appl. 2013, 36, 611–622. [Google Scholar] [CrossRef]
- Eschenauer, L.; Gligor, V. A key-management scheme for distributed sensor networks. In Proceedings of the 9th ACM Conference on Computer and Communications Security, CCS ’02, Washington, DC, USA, 18–22 November 2002; pp. 41–47. [Google Scholar] [CrossRef]
- Chan, H.; Perrig, A.; Song, D. Random key predistribution schemes for sensor networks. In Proceedings of the Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003; pp. 197–213. [Google Scholar]
- Colbourn, C.J.; Dinitz, J.H. Handbook of Combinatorial Designs; CRC Press: Boca Raton, FL, USA, 2006. [Google Scholar]
- Martin, K.M. On the Applicability of Combinatorial Designs to Key Predistribution for Wireless Sensor Networks. In Coding and Cryptology; Chee, Y.M., Li, C., Ling, S., Wang, H., Xing, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 124–145. [Google Scholar]
- Çamtepe, S.A.; Yener, B. Combinatorial Design of Key Distribution Mechanisms for Wireless Sensor Networks. In Computer Security—ESORICS 2004; Samarati, P., Ryan, P., Gollmann, D., Molva, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 293–308. [Google Scholar]
- Camtepe, S.A.; Yener, B. Combinatorial Design of Key Distribution Mechanisms for Wireless Sensor Networks. IEEE/ACM Trans. Netw. 2007, 15, 346–358. [Google Scholar] [CrossRef]
- Srinivasa, K.G.; Poornima, V.; Archana, V.; Reshma, C.; Venugopal, K.R.; Patnaik, L.M. Combinatorial Approach to Key Generation using Multiple Key Spaces for Wireless Sensor Networks. In Proceedings of the 2008 16th International Conference on Advanced Computing and Communications, Chennai, India, 14–17 December 2008; pp. 279–284. [Google Scholar] [CrossRef]
- Lee, J.; Stinson, D.R. A combinatorial approach to key predistribution for distributed sensor networks. In Proceedings of the IEEE Wireless Communications and Networking Conference, New Orleans, LA, USA, 13–17 March 2005; Volume 2, pp. 1200–1205. [Google Scholar] [CrossRef]
- Ruj, S.; Roy, B. Key Predistribution Using Partially Balanced Designs in Wireless Sensor Networks. In Parallel and Distributed Processing and Applications; Stojmenovic, I., Thulasiram, R.K., Yang, L.T., Jia, W., Guo, M., de Mello, R.F., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 431–445. [Google Scholar]
- Bechkit, W.; Challal, Y.; Bouabdallah, A.; Tarokh, V. A Highly Scalable Key Pre-Distribution Scheme for Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2013, 12, 948–959. [Google Scholar] [CrossRef]
- Ruj, S.; Nayak, A.; Stojmenovic, I. Pairwise and Triple Key Distribution in Wireless Sensor Networks with Applications. IEEE Trans. Comput. 2013, 62, 2224–2237. [Google Scholar] [CrossRef]
- Gandino, F.; Ferrero, R.; Rebaudengo, M. A Key Distribution Scheme for Mobile Wireless Sensor Networks: q - s -Composite. IEEE Trans. Inf. Forensics Secur. 2017, 12, 34–47. [Google Scholar] [CrossRef]

© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gandino, F.; Montrucchio, B.; Rebaudengo, M. Redundancy in Key Management for WSNs. Cryptography 2018, 2, 40. https://doi.org/10.3390/cryptography2040040
Gandino F, Montrucchio B, Rebaudengo M. Redundancy in Key Management for WSNs. Cryptography. 2018; 2(4):40. https://doi.org/10.3390/cryptography2040040
Chicago/Turabian StyleGandino, Filippo, Bartolomeo Montrucchio, and Maurizio Rebaudengo. 2018. "Redundancy in Key Management for WSNs" Cryptography 2, no. 4: 40. https://doi.org/10.3390/cryptography2040040
APA StyleGandino, F., Montrucchio, B., & Rebaudengo, M. (2018). Redundancy in Key Management for WSNs. Cryptography, 2(4), 40. https://doi.org/10.3390/cryptography2040040







