Multi-Factor Authentication: A Survey †
Abstract
:1. Introduction
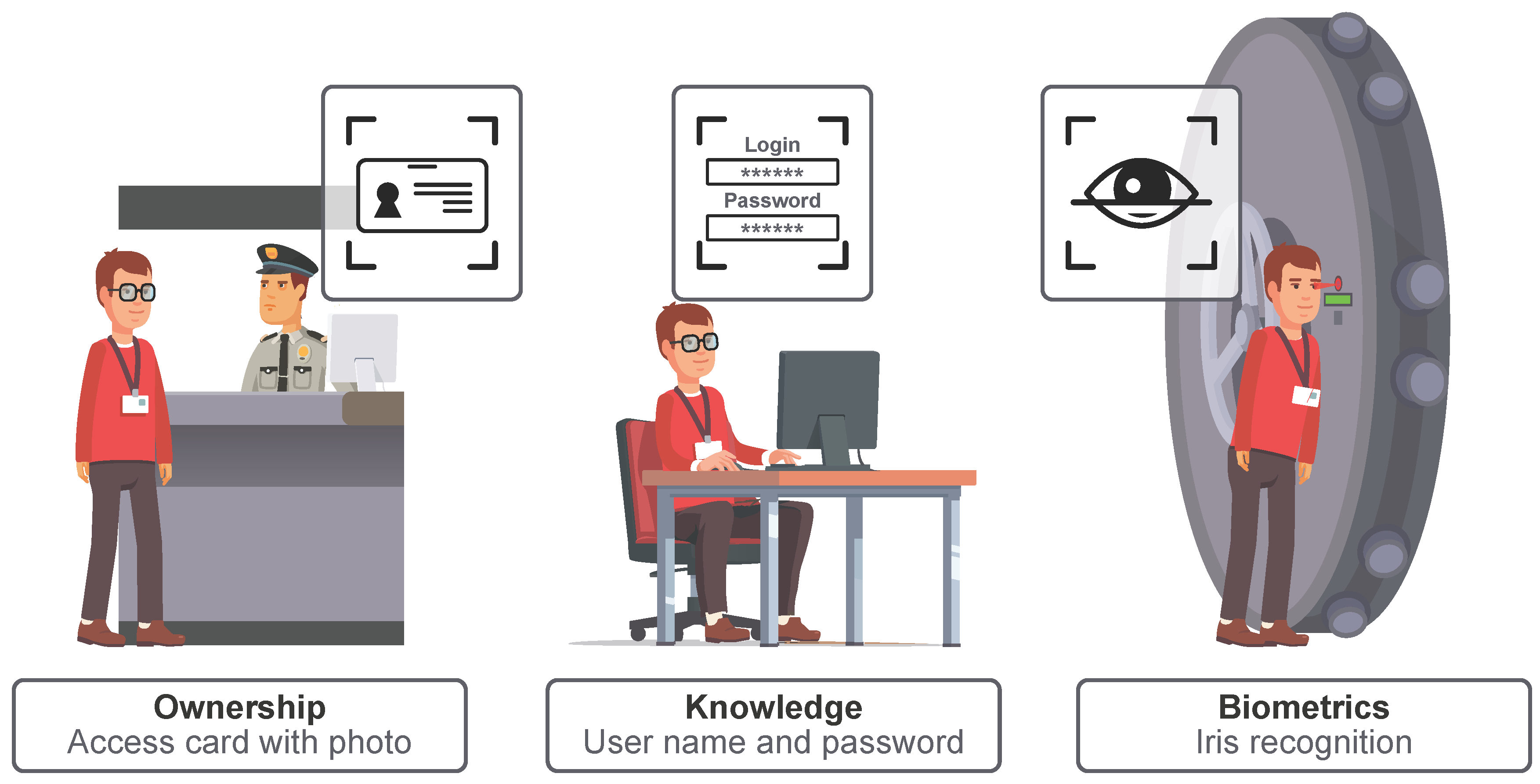
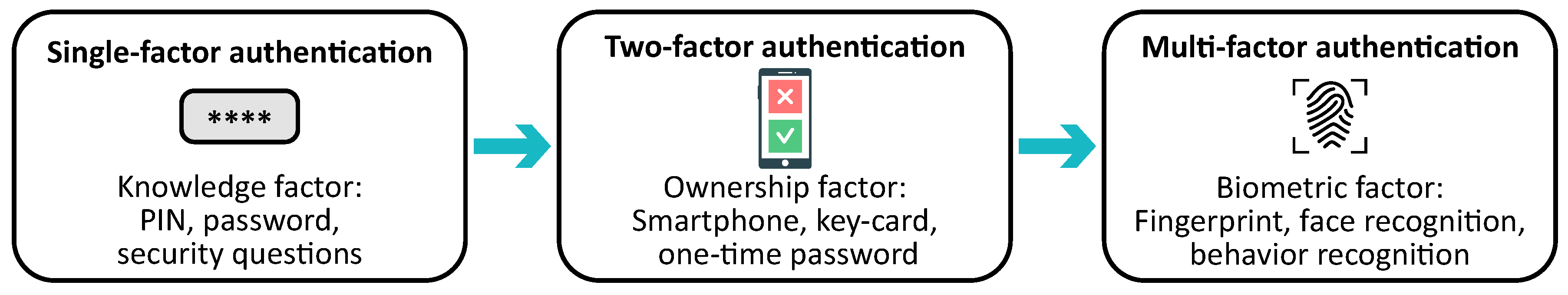
- Knowledge factor—something the user knows, such as a password or, simply, a “secret”;
- Ownership factor—something the user has, such as cards, smartphones, or other tokens;
- Biometric factor—something the user is, i.e., biometric data or behavior pattern.
- Customers first register and authenticate with the service provider to activate and manage services they are willing to access;
- Once accessing the service, the user is required to pass a simple SFA with the fingerprint/token signed in advance by the service provider;
- Once initially accepted by the system, the customer authenticates by logging in with the same username and password as setup previously in the customer portal (or social login). For additional security, the managing platform can enable secondary authentication factors. Once the user has successfully passed all the tests, the framework automatically authenticates to the service platform;
- The secondary authentication occurs automatically based on the biometric MFA, so the user would be requested to enter an additional code or provide a token password only in case the MFA fails.
- This work provides a detailed analysis of factors that are presently utilized for MFA with their corresponding operational requirements. Potential sensors to be utilized are surveyed based on the academic and industrial sources (Section 2);
- The survey is followed by the challenges related to MFA adoption from both the user experience and the technological perspectives (Section 3);
- Further, the framework based on the reversed Lagrange polynomial is proposed to allow for utilizing MFA in cases where some of the factors are missing (Section 4). A discussion on the potential evaluation methodology is also provided;
- Finally, the vision of the future of MFA is discussed (Section 5).
2. State-of-the-Art and Potential MFA Sources
2.1. Widely Deployed MFA Sensors/Sources
2.1.1. Password Protection
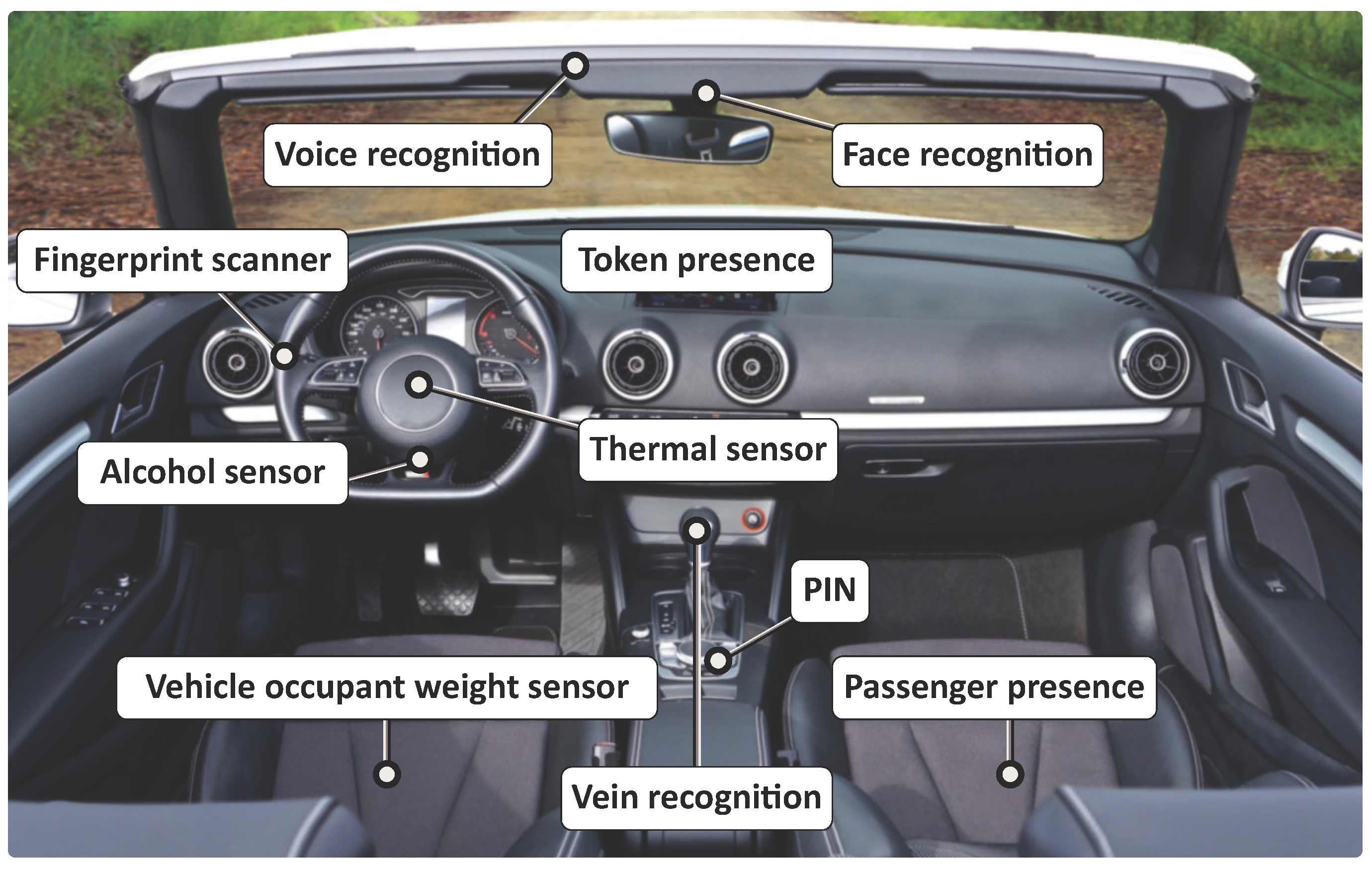
2.1.2. Token Presence
2.1.3. Voice Biometrics
2.1.4. Facial Recognition
2.1.5. Ocular-Based Methodology
2.1.6. Hand Geometry
2.1.7. Vein Recognition
2.1.8. Fingerprint Scanner
2.1.9. Thermal Image Recognition
2.1.10. Geographical Location
2.2. Future of MFA Integration
2.2.1. Behavior Detection
2.2.2. Beam-Forming Techniques
2.2.3. Occupant Classification Systems (OCS)
2.2.4. Electrocardiographic (ECG) Recognition
2.2.5. Electroencephalographic (EEG) Recognition
2.2.6. DNA Recognition
- Universality stands for the presence of factor in each person;
- Uniqueness indicates how well the factor differentiates one person from another;
- Collectability measures how easy it is to acquire data for processing;
- Performance indicates the achievable accuracy, speed, and robustness;
- Acceptability stands for the degree of acceptance of the technology by people in their daily life;
- Spoofing indicates the level of difficulty to capture and spoof the sample.
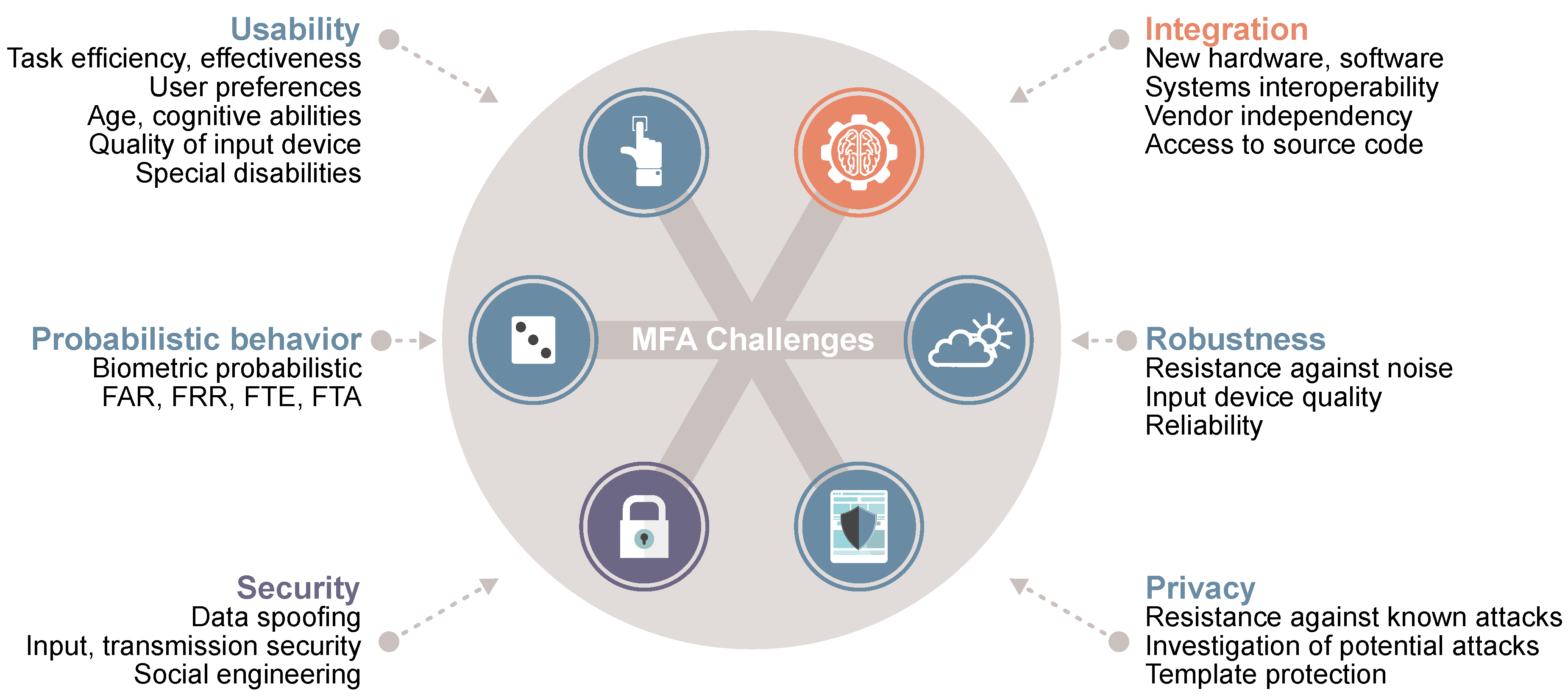
3. MFA Operation Challenges
3.1. Usability
- Task efficiency—time to register and time to authenticate with the system;
- Task effectiveness—the number login attempts to authenticate with the system;
- User preference—whether the user prefers a particular authentication scheme over another.
3.2. Integration
3.3. Security and Privacy
3.4. Robustness to Operating Environment
4. Enabling Flexible MFA Operation
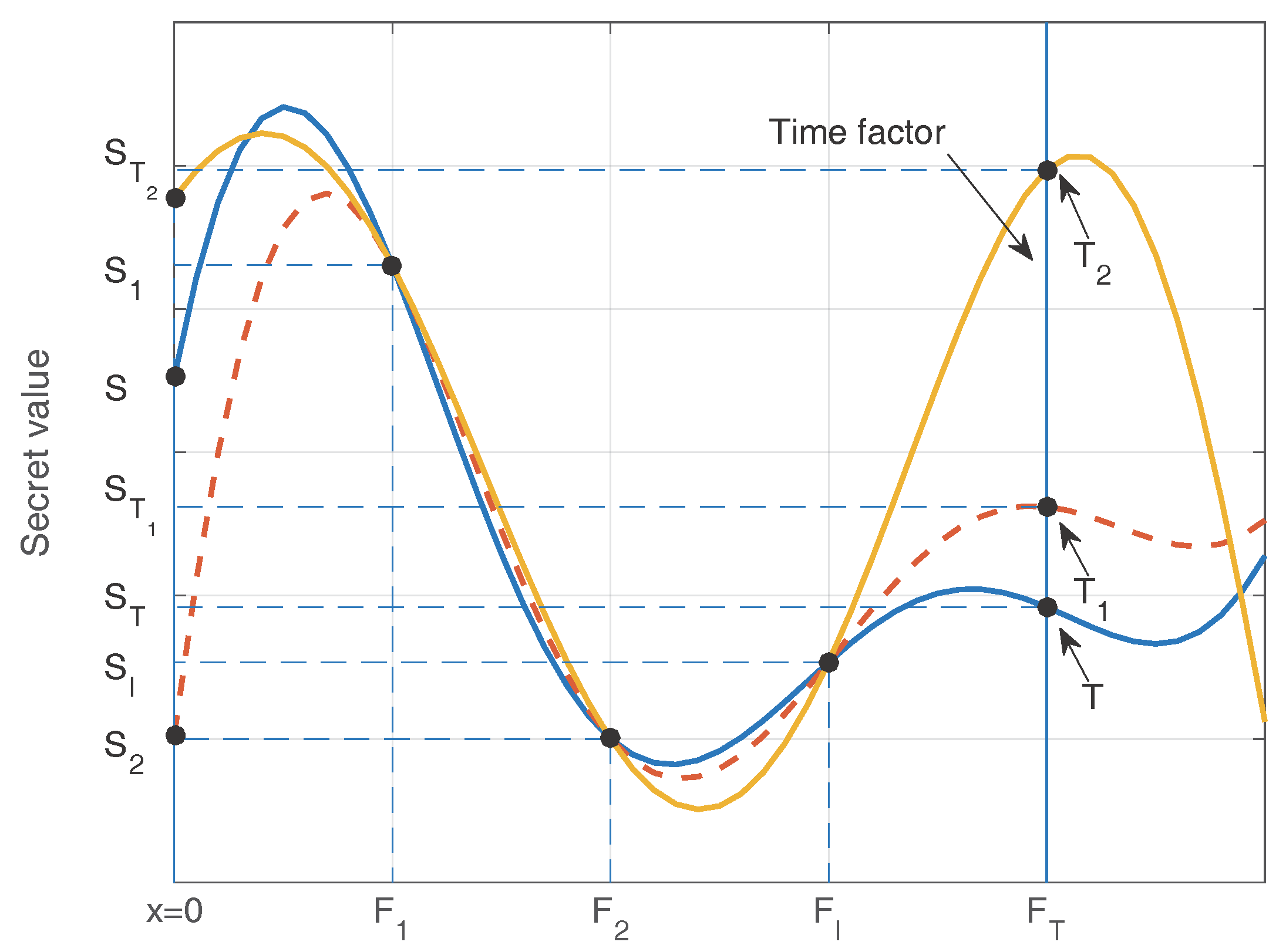
4.1. Conventional Approach
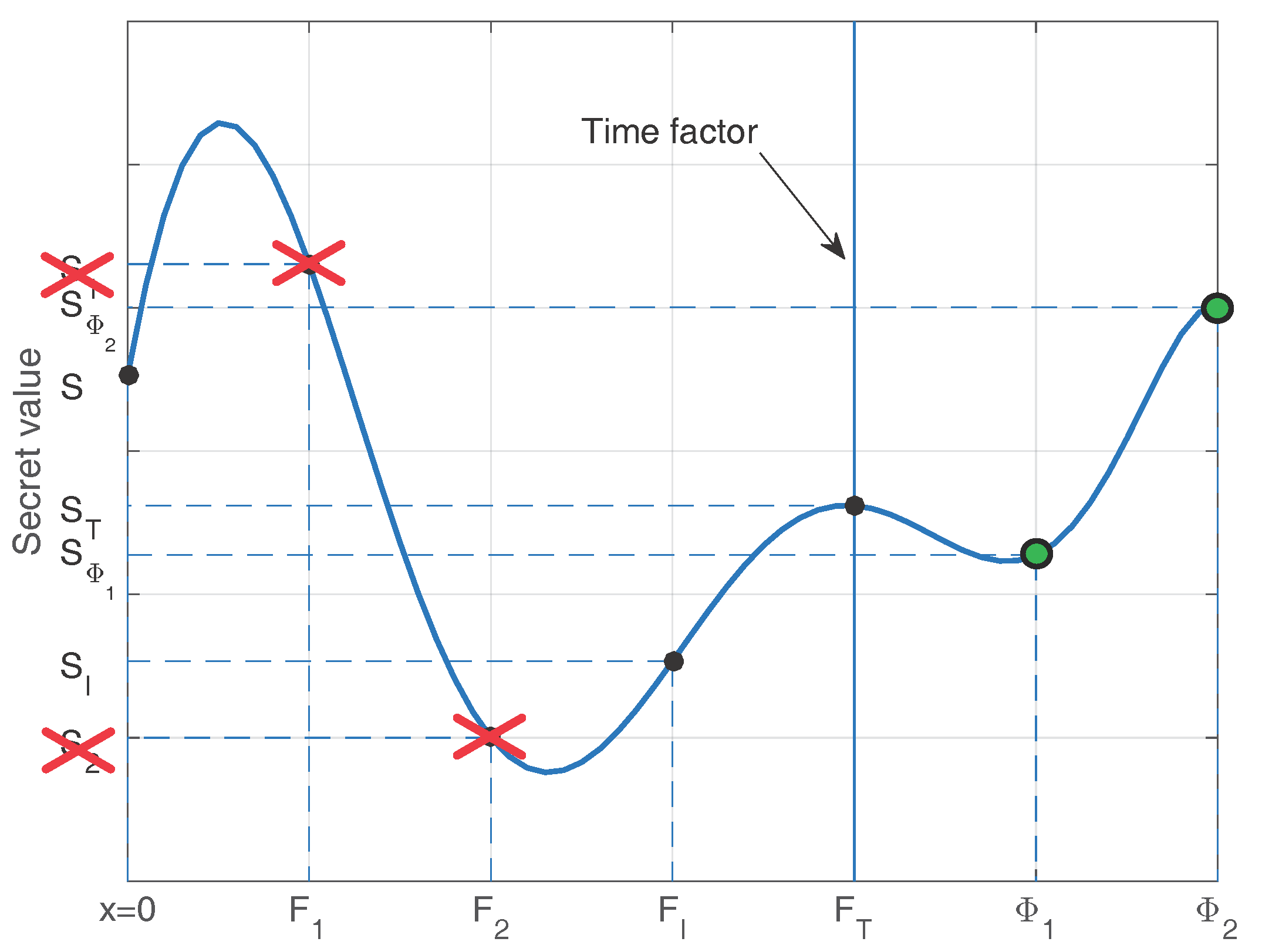
4.2. Proposed Reversed Methodology
4.3. Proposed MFA Solution for V2X Applications
4.3.1. Factor Mismatch
4.3.2. Cloud Assistance
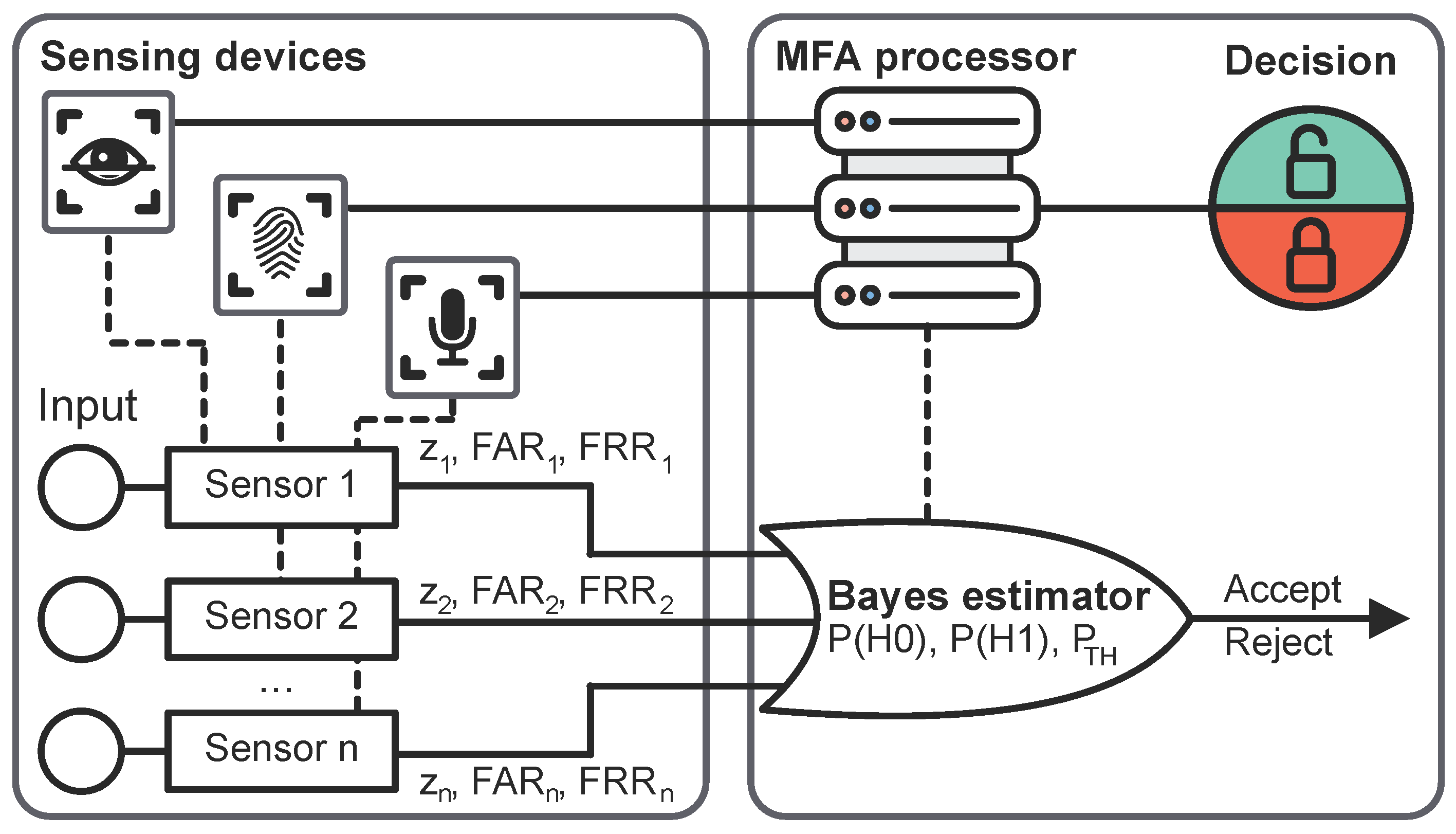
4.4. Potential Evaluation Techniques
4.4.1. Strict Decision Methodology
4.4.2. Probabilistic Decision Methodology
4.4.3. Evaluation
5. Discussion and Future Prospects
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| MFA | Multi-Factor Authentication |
| SFA | Single-Factor Authentication |
| 2FA | Two-Factor Authentication |
| SSS | Shamir’s Secret Sharing |
| PIN | Personal Identification Number |
| ID | Identification Number |
| ATM | Automated Teller Machine |
| FAR | False Accept Rate |
| FRR | False Reject Rate |
| PPG | Photoplethysmography |
| RFID | Radio-Frequency Identification |
| NFC | Near-Field Communication |
| OCS | Occupant Classification Systems |
| ECG | Electrocardiography |
| EEG | Electroencephalography |
| GPS | Global Positioning System |
| FTE | Failure to Enroll |
| FTA | Failure to Acquire |
| CER | Crossover Error Rate |
| EER | Equal Error Rate |
| V2X | Vehicle-to-Everything |
| IAM | Identity and Access Management |
References
- VNI Cisco Global Mobile Data Traffic Forecast 2016–2021. White Paper. 2017. Available online: https://www.cisco.com/c/en/us/solutions/collateral/service-provider/visual-networking-index-vni/complete-white-paper-c11-481360.pdf (accessed on 4 January 2018).
- Roy, S.; Khatwani, C. Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols. Cryptography 2017, 1, 9. [Google Scholar] [CrossRef]
- Dworkin, M.J. Recommendation for Block Cipher Modes of Operation: The CMAC Mode for Authentication. Special Publication (NIST SP)-800-38B 2016. Available online: https://www.nist.gov/publications/recommendation-block-cipher-modes-operation-cmac-mode-authentication-0 (accessed on 4 January 2018).
- Alomar, N.; Alsaleh, M.; Alarifi, A. Social authentication applications, attacks, defense strategies and future research directions: A systematic review. IEEE Commun. Surv. Tutor. 2017. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Benarous, L.; Kadri, B.; Bouridane, A. A Survey on Cyber Security Evolution and Threats: Biometric Authentication Solutions. In Biometric Security and Privacy; Springer: Berlin, Germany, 2017; pp. 371–411. [Google Scholar]
- Boyd, C.; Mathuria, A. Protocols for Authentication and Key Establishment; Springer: Berlin, Germany, 2013. [Google Scholar]
- Mohsin, J.; Han, L.; Hammoudeh, M.; Hegarty, R. Two Factor vs. Multi-factor, an Authentication Battle in Mobile Cloud Computing Environments. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017; ACM: New York, NY, USA, 2017; p. 39. [Google Scholar]
- Pathan, A.S.K. Security of Self-Organizing Networks: MANET, WSN, WMN, VANET; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Balloon, A.M. From Wax Seals to Hypertext: Electronic Signatures, Contract Formation, and a New Model for Consumer Protection in Internet Transactions. Emory Law J. 2001, 50, 905. [Google Scholar]
- Danny, T. MFA (Multi-Factor Authentication) with Biometrics. 2017. Available online: https://www.bayometric.com/mfa-multi-factor-authentication-biometrics/ (accessed on 4 Jaurnay 2018).
- Konoth, R.K.; van der Veen, V.; Bos, H. How anywhere computing just killed your phone-based two-factor authentication. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 22–26 February 2016; Springer: Berlin, Germany, 2016; pp. 405–421. [Google Scholar]
- Kim, J.J.; Hong, S.P. A method of risk assessment for multi-factor authentication. J. Inf. Process. Syst. 2011, 7, 187–198. [Google Scholar] [CrossRef]
- Dasgupta, D.; Roy, A.; Nag, A. Toward the design of adaptive selection strategies for multi-factor authentication. Comput. Secur. 2016, 63, 85–116. [Google Scholar] [CrossRef]
- Bonneau, J.; Herley, C.; Van Oorschot, P.C.; Stajano, F. Passwords and the evolution of imperfect authentication. Commun. ACM 2015, 58, 78–87. [Google Scholar] [CrossRef] [Green Version]
- Wang, D.; Wang, P. Offline dictionary attack on password authentication schemes using smart cards. In Information Security; Springer: Berlin, Germany, 2015; pp. 221–237. [Google Scholar]
- Ah Kioon, M.C.; Wang, Z.S.; Deb Das, S. Security analysis of MD5 algorithm in password storage. Appl. Mech. Mater. 2013, 347, 2706–2711. [Google Scholar] [CrossRef]
- Heartfield, R.; Loukas, G. A taxonomy of attacks and a survey of defence mechanisms for semantic social engineering attacks. ACM Comput. Surv. (CSUR) 2016, 48, 37. [Google Scholar] [CrossRef]
- Grassi, P.A.; Fenton, J.L.; Newton, E.M.; Perlner, R.A.; Regenscheid, A.R.; Burr, W.E.; Richer, J.P.; Lefkovitz, N.B.; Danker, J.M.; Choong, Y.Y.; et al. NIST Special Publication 800-63B. Digital Identity Guidelines: Authentication and Lifecycle Management; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2017.
- Gunson, N.; Marshall, D.; Morton, H.; Jack, M. User perceptions of security and usability of single-factor and two-factor authentication in automated telephone banking. Comput. Secur. 2011, 30, 208–220. [Google Scholar] [CrossRef]
- Schneier, B. Two-factor authentication: Too little, too late. Commun. ACM 2005, 48, 136. [Google Scholar] [CrossRef]
- Petsas, T.; Tsirantonakis, G.; Athanasopoulos, E.; Ioannidis, S. Two-factor authentication: Is the world ready?: Quantifying 2FA adoption. In Proceedings of the 8th European Workshop on System Security, Bordeaux, France, 21 April 2015; ACM: New York, NY, USA, 2015; p. 4. [Google Scholar]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Sun, J.; Zhang, R.; Zhang, J.; Zhang, Y. Touchin: Sightless two-factor authentication on multi-touch mobile devices. In Proceedings of the Conference on Communications and Network Security (CNS), San Francisco, CA, USA, 29–31 October 2014; pp. 436–444. [Google Scholar]
- Bruun, A.; Jensen, K.; Kristensen, D. Usability of Single- and Multi-factor Authentication Methods on Tabletops: A Comparative Study. In Proceedings of the International Conference on Human-Centred Software Engineering, Paderborn, Germany, 16–18 September 2014; Springer: Berlin, Germany, 2014; pp. 299–306. [Google Scholar]
- Harini, N.; Padmanabhan, T.R. 2CAuth: A new two factor authentication scheme using QR-code. Int. J. Eng. Technol. 2013, 5, 1087–1094. [Google Scholar]
- Scheidt, E.M.; Domangue, E. Multiple Factor-Based User Identification and Authentication. U.S. Patent 7,131,009, 31 October 2006. [Google Scholar]
- Bhargav-Spantzel, A.; Squicciarini, A.C.; Modi, S.; Young, M.; Bertino, E.; Elliott, S.J. Privacy preserving multi-factor authentication with biometrics. J. Comput. Secur. 2007, 15, 529–560. [Google Scholar] [CrossRef]
- Banyal, R.K.; Jain, P.; Jain, V.K. Multi-factor authentication framework for cloud computing. In Proceedings of the Fifth International Conference on Computational Intelligence, Modelling and Simulation (CIMSim), Seoul, Korea, 24–25 September 2013; pp. 105–110. [Google Scholar]
- Frank, M.; Biedert, R.; Ma, E.; Martinovic, I.; Song, D. Touchalytics: On the applicability of touchscreen input as a behavioral biometric for continuous authentication. IEEE Trans. Inf. Forensics Secur. 2013, 8, 136–148. [Google Scholar] [CrossRef]
- Jorgensen, Z.; Yu, T. On mouse dynamics as a behavioral biometric for authentication. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 22–24 March 2011; ACM: New York, NY, USA, 2011; pp. 476–482. [Google Scholar]
- National Research Council; Whither Biometrics Committee. Biometric Recognition: Challenges and Opportunities; National Academies Press: Washington, DC, USA, 2010. [Google Scholar]
- Huang, X.; Xiang, Y.; Bertino, E.; Zhou, J.; Xu, L. Robust multi-factor authentication for fragile communications. IEEE Trans. Dependable Secur. Comput. 2014, 11, 568–581. [Google Scholar] [CrossRef]
- Tahir, H.; Tahir, R. BioFIM: Multifactor Authentication for Defeating Vehicle Theft. In Proceedings of the World Congress on Engineering, London, UK, 2–4 July 2008; Volume 1, pp. 1–3. [Google Scholar]
- Coventry, L.; De Angeli, A.; Johnson, G. Usability and biometric verification at the ATM interface. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Ft. Lauderdale, FL, USA, 5–10 April 2003; ACM: New York, NY, USA, 2003; pp. 153–160. [Google Scholar]
- SC Media UK. 68% of Europeans Want to Use Biometric Authentication for Payments. 2016. Available online: https://www.scmagazineuk.com/68-of-europeans-want-to-use-biometric-authentication-for-payments/article/530818/ (accessed on 4 January 2018).
- Khan, R.; Hasan, R.; Xu, J. SEPIA: Secure-PIN-authentication-as-a-service for ATM using mobile and wearable devices. In Proceedings of the 3rd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), San Francisco, CA, USA, 30 March–3 April 2015; pp. 41–50. [Google Scholar]
- Adeoye, O.S. Evaluating the performance of two-factor authentication solution in the banking sector. Int. J. Comput. Sci. 2012, 9, 457–462. [Google Scholar]
- Aloul, F.; Zahidi, S.; El-Hajj, W. Two factor authentication using mobile phones. In Proceedings of the International Conference on Computer Systems and Applications, Rabat, Morocco, 10–13 May 2009; pp. 641–644. [Google Scholar]
- Ometov, A.; Bezzateev, S.; Kannisto, J.; Harju, J.; Andreev, S.; Koucheryavy, Y. Facilitating the Delegation of Use for Private Devices in the Era of the Internet of Wearable Things. IEEE Internet Things J. 2017, 4, 843–854. [Google Scholar] [CrossRef]
- Parmar, D.N.; Mehta, B.B. Face recognition methods & applications. arXiv, 2014; arXiv:1403.0485. [Google Scholar]
- Sunehra, D. Fingerprint based biometric ATM authentication system. Int. J. Eng. Invent. 2014, 3, 22–28. [Google Scholar]
- Security Intelligence. The Move to Multifactor Authentication: Are Passwords Past Their Prime? 2016. Available online: https://securityintelligence.com/news/the-move-to-multifactor-authentication-are-passwords-past-their-prime/ (accessed on 4 January 2018).
- National Highway Traffic Safety Administration. Learn How to Protect Your Car. 2016. Available online: https://www.nhtsa.gov/vehicle-theft-prevention (accessed on 4 January 2018).
- Garcia, F.D.; Oswald, D.; Kasper, T.; Pavlidès, P. Lock It and Still Lose It-on the (in) Security of Automotive Remote Keyless Entry Systems. In Proceedings of the USENIX Security Symposium, Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- Verdult, R.; Garcia, F.D.; Ege, B. Dismantling Megamos Crypto: Wirelessly Lockpicking a Vehicle Immobilizer. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 14–16 August 2013; pp. 703–718. [Google Scholar]
- Symeonidis, I.; Mustafa, M.A.; Preneel, B. Keyless car sharing system: A security and privacy analysis. In Proceedings of the IEEE International Smart Cities Conference (ISC2), Trento, Italy, 12–15 September 2016; pp. 1–7. [Google Scholar]
- Dmitrienko, A.; Plappert, C. Secure free-floating car sharing for offline cars. In Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, Scottsdale, AZ, USA, 22–24 March 2017; ACM: New York, NY, USA, 2017; pp. 349–360. [Google Scholar]
- Neha; Chatterjee, K. Authentication techniques for e-commerce applications: A review. In Proceedings of the International Conference on Computing, Communication and Automation (ICCCA), Noida, India, 29–30 April 2016; pp. 693–698. [Google Scholar]
- Fan, K.; Ge, N.; Gong, Y.; Li, H.; Su, R.; Yang, Y. An ultra-lightweight RFID authentication scheme for mobile commerce. Peer-to-Peer Netw. Appl. 2017, 10, 368–376. [Google Scholar] [CrossRef]
- Nor, N.A.; Narayana Samy, G.; Ahmad, R.; Ibrahim, R.; Maarop, N. The Proposed Public Key Infrastructure Authentication Framework (PKIAF) for Malaysian Government Agencies. Adv. Sci. Lett. 2015, 21, 3161–3164. [Google Scholar] [CrossRef]
- Labati, R.D.; Genovese, A.; Muñoz, E.; Piuri, V.; Scotti, F.; Sforza, G. Biometric recognition in automated border control: A survey. ACM Comput. Surv. (CSUR) 2016, 49, 24. [Google Scholar] [CrossRef]
- Grigoras, C. Applications of ENF analysis in forensic authentication of digital audio and video recordings. J. Audio Eng. Soc. 2009, 57, 643–661. [Google Scholar]
- Gill, P.; Jeffreys, A.J.; Werrett, D.J. Forensic application of DNA ‘fingerprints’. Nature 1985, 318, 577–579. [Google Scholar] [CrossRef] [PubMed]
- Han, K.; Potluri, S.D.; Shin, K.G. On authentication in a connected vehicle: Secure integration of mobile devices with vehicular networks. In Proceedings of the International Conference on Cyber-Physical Systems (ICCPS), Philadelphia, PA, USA, 8–11 April 2013; pp. 160–169. [Google Scholar]
- Ishtiaq Roufa, R.M.; Mustafaa, H.; Travis Taylora, S.O.; Xua, W.; Gruteserb, M.; Trappeb, W.; Seskarb, I. Security and privacy vulnerabilities of in-car wireless networks: A tire pressure monitoring system case study. In Proceedings of the 19th USENIX Security Symposium, Washington, DC, USA, 11–13 August 2010; pp. 11–13. [Google Scholar]
- Chaurasia, B.K.; Verma, S. Infrastructure based authentication in VANETs. Int. J. Multimed. Ubiquitous Eng. 2011, 6, 41–54. [Google Scholar]
- Rossi, B. Connected car security: why identity should be in the driving seat. 2016. Available online: http://www.information-age.com/connected-car-security-why-identity-should-be-driving-seat-123461078/ (accessed on 4 January 2018).
- Kleberger, P.; Olovsson, T.; Jonsson, E. Security aspects of the in-vehicle network in the connected car. In Proceedings of the Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 528–533. [Google Scholar]
- Calandriello, G.; Papadimitratos, P.; Hubaux, J.P.; Lioy, A. Efficient and robust pseudonymous authentication in VANET. In Proceedings of the 4th International Workshop on Vehicular ad hoc Networks, Montreal, QC, Canada, 9–14 September 2007; ACM: New York, NY, USA, 2007; pp. 19–28. [Google Scholar]
- Yang, Y.; Wei, Z.; Zhang, Y.; Lu, H.; Choo, K.K.R.; Cai, H. V2X security: A case study of anonymous authentication. Pervasive Mob. Comput. 2017, 41, 259–269. [Google Scholar] [CrossRef]
- De Luca, A.; Hang, A.; Von Zezschwitz, E.; Hussmann, H. I Feel Like I’m Taking Selfies All Day!: Towards Understanding Biometric Authentication on Smartphones. In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing Systems, Seoul, Korea, 18–23 April 2015; ACM: New York, NY, USA, 2015; pp. 1411–1414. [Google Scholar]
- Clarke, N. Transparent User Authentication: Biometrics, RFID and Behavioural Profiling; Springer: Berlin, Germany, 2011. [Google Scholar]
- Rane, S.; Wang, Y.; Draper, S.C.; Ishwar, P. Secure biometrics: Concepts, authentication architectures, and challenges. IEEE Signal Process. Mag. 2013, 30, 51–64. [Google Scholar] [CrossRef]
- Bhagavatula, C.; Ur, B.; Iacovino, K.; Kywe, S.M.; Cranor, L.F.; Savvides, M. Biometric authentication on iPhone and Android: Usability, perceptions, and influences on adoption. In Proceedings of the Usable Security (USEC), San Diego, CA, USA, 21 February 2016; pp. 1–10. [Google Scholar]
- Wimberly, H.; Liebrock, L.M. Using fingerprint authentication to reduce system security: An empirical study. In Proceedings of the Symposium on Security and Privacy (SP), Berkeley, CA, USA, 22–25 May 2011; pp. 32–46. [Google Scholar]
- De Cristofaro, E.; Du, H.; Freudiger, J.; Norcie, G. A comparative usability study of two-factor authentication. arXiv, 2013; arXiv:1309.5344. [Google Scholar]
- Jin, A.T.B.; Ling, D.N.C.; Goh, A. Biohashing: Two factor authentication featuring fingerprint data and tokenised random number. Pattern Recognit. 2004, 37, 2245–2255. [Google Scholar] [CrossRef]
- Ratha, N.K.; Connell, J.H.; Bolle, R.M. Enhancing security and privacy in biometrics-based authentication systems. IBM Syst. J. 2001, 40, 614–634. [Google Scholar] [CrossRef]
- Jain, A.K.; Ross, A. Multibiometric systems. Commun. ACM 2004, 47, 34–40. [Google Scholar] [CrossRef]
- Schroff, F.; Kalenichenko, D.; Philbin, J. Facenet: A unified embedding for face recognition and clustering. In Proceedings of the Conference on Computer Vision and Pattern Recognition, Boston, MA, USA, 7–12 June 2015; pp. 815–823. [Google Scholar]
- Feng, T.; Liu, Z.; Kwon, K.A.; Shi, W.; Carbunar, B.; Jiang, Y.; Nguyen, N. Continuous mobile authentication using touchscreen gestures. In Proceedings of the Technologies for Homeland Security (HST) Conference, Waltham, MA, USA, 13–15 November 2012; pp. 451–456. [Google Scholar]
- Ross, A.; Jain, A. Information fusion in biometrics. Pattern Recognit. Lett. 2003, 24, 2115–2125. [Google Scholar] [CrossRef]
- Kun, A.L.; Royer, T.; Leone, A. Using tap sequences to authenticate drivers. In Proceedings of the 5th International Conference on Automotive User Interfaces and Interactive Vehicular Applications, Eindhoven, The Netherlands, 28–30 October 2013; ACM: New York, NY, USA, 2013; pp. 228–231. [Google Scholar]
- Hwang, M.S.; Li, L.H. A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2000, 46, 28–30. [Google Scholar] [CrossRef]
- Khan, S.H.; Akbar, M.A.; Shahzad, F.; Farooq, M.; Khan, Z. Secure biometric template generation for multi-factor authentication. Pattern Recognit. 2015, 48, 458–472. [Google Scholar] [CrossRef]
- Busold, C.; Taha, A.; Wachsmann, C.; Dmitrienko, A.; Seudié, H.; Sobhani, M.; Sadeghi, A.R. Smart keys for cyber-cars: Secure smartphone-based NFC-enabled car immobilizer. In Proceedings of the 3rd ACM Conference on Data and Application Security and Privacy, San Antonio, TX, USA, 18–20 February 2013; ACM: New York, NY, USA, 2013; pp. 233–242. [Google Scholar]
- Urien, P.; Piramuthu, S. Elliptic curve-based RFID/NFC authentication with temperature sensor input for relay attacks. Decis. Support Syst. 2014, 59, 28–36. [Google Scholar] [CrossRef]
- Fan, K.; Gong, Y.; Liang, C.; Li, H.; Yang, Y. Lightweight and ultralightweight RFID mutual authentication protocol with cache in the reader for IoT in 5G. Secur. Commun. Netw. 2016, 9, 3095–3104. [Google Scholar] [CrossRef]
- Acharya, S.; Polawar, A.; Pawar, P. Two factor authentication using smartphone generated one time password. J. Comput. Eng. (IOSR-JCE) 2013, 11, 85–90. [Google Scholar] [CrossRef]
- Lee, J.D.; Caven, B.; Haake, S.; Brown, T.L. Speech-based interaction with in-vehicle computers: The effect of speech-based e-mail on drivers’ attention to the roadway. Hum. Factors 2001, 43, 631–640. [Google Scholar] [CrossRef] [PubMed]
- Thullier, F.; Bouchard, B.; Menelas, B.A.J. A Text-Independent Speaker Authentication System for Mobile Devices. Cryptography 2017, 1, 16. [Google Scholar] [CrossRef]
- Hautamäki, R.G.; Kinnunen, T.; Hautamäki, V.; Laukkanen, A.M. Automatic versus human speaker verification: The case of voice mimicry. Speech Commun. 2015, 72, 13–31. [Google Scholar] [CrossRef]
- Hautamäki, R.G.; Kinnunen, T.; Hautamäki, V.; Leino, T.; Laukkanen, A.M. I-vectors meet imitators: On vulnerability of speaker verification systems against voice mimicry. In Proceedings of the Interspeech, Lyon, France, 25–29 August 2013; pp. 930–934. [Google Scholar]
- Ahonen, T.; Hadid, A.; Pietikainen, M. Face description with local binary patterns: Application to face recognition. IEEE Trans. Pattern Anal. Mach. Intell. 2006, 28, 2037–2041. [Google Scholar] [CrossRef] [PubMed]
- Zhao, W.; Chellappa, R.; Phillips, P.J.; Rosenfeld, A. Face recognition: A literature survey. ACM Comput. Surv. (CSUR) 2003, 35, 399–458. [Google Scholar] [CrossRef]
- Smeets, D.; Claes, P.; Vandermeulen, D.; Clement, J.G. Objective 3D face recognition: Evolution, approaches and challenges. Forensic Sci. Int. 2010, 201, 125–132. [Google Scholar] [CrossRef] [PubMed]
- Kakadiaris, I.A.; Passalis, G.; Toderici, G.; Murtuza, M.N.; Lu, Y.; Karampatziakis, N.; Theoharis, T. Three-dimensional face recognition in the presence of facial expressions: An annotated deformable model approach. IEEE Trans. Pattern Anal. Mach. Intell. 2007, 29, 640–649. [Google Scholar] [CrossRef] [PubMed]
- Wójtowicz, W.; Ogiela, M.R. Biometric watermarks based on face recognition methods for authentication of digital images. Secur. Commun. Netw. 2015, 8, 1672–1687. [Google Scholar] [CrossRef]
- Wildes, R.P. Iris recognition: An emerging biometric technology. Proc. IEEE 1997, 85, 1348–1363. [Google Scholar] [CrossRef]
- Tan, T.; He, Z.; Sun, Z. Efficient and robust segmentation of noisy iris images for non-cooperative iris recognition. Image Vis. Comput. 2010, 28, 223–230. [Google Scholar] [CrossRef]
- Bhattacharyya, D.; Ranjan, R.; Alisherov, F.; Choi, M. Biometric authentication: A review. Int. J. u- e-Serv. Sci. Technol. 2009, 2, 13–28. [Google Scholar]
- Bowyer, K.W.; Burge, M.J. Handbook of Iris Recognition; Springer: Berlin, Germany, 2016. [Google Scholar]
- Wong, A.L.; Shi, P. Peg-Free Hand Geometry Recognition Using Hierarchical Geometry and Shape Matching. In MVA; Citeseer: Hong Kong, China, 2002; pp. 281–284. [Google Scholar]
- Zheng, G.; Wang, C.J.; Boult, T.E. Application of projective invariants in hand geometry biometrics. IEEE Trans. Inf. Forensics Secur. 2007, 2, 758–768. [Google Scholar] [CrossRef]
- Guo, J.M.; Liu, Y.F.; Chu, M.H.; Wu, C.C.; Le, T.N. Contact-free hand geometry identification system. In Proceedings of the 18th IEEE International Conference on Image Processing (ICIP), Brussels, Belgium, 11–14 September 2011; pp. 3185–3188. [Google Scholar]
- Phan, D.; Siong, L.Y.; Pathirana, P.N.; Seneviratne, A. Smartwatch: Performance evaluation for long-term heart rate monitoring. In Proceedings of the International Symposium on Bioelectronics and Bioinformatics (ISBB), Beijing, China, 14–17 October 2015; pp. 144–147. [Google Scholar]
- Zhang, Z. Photoplethysmography-based heart rate monitoring in physical activities via joint sparse spectrum reconstruction. IEEE Trans. Biomed. Eng. 2015, 62, 1902–1910. [Google Scholar] [CrossRef] [PubMed]
- Lu, S.; Zhao, H.; Ju, K.; Shin, K.; Lee, M.; Shelley, K.; Chon, K.H. Can photoplethysmography variability serve as an alternative approach to obtain heart rate variability information? J. Clin. Monit. Comput. 2008, 22, 23–29. [Google Scholar] [CrossRef] [PubMed]
- Kumar, A.; Hanmandlu, M.; Madasu, V.K.; Lovell, B.C. Biometric authentication based on infrared thermal hand vein patterns. In Proceedings of the Digital Image Computing: Techniques and Applications (DICTA’09), Melbourne, Australia, 1–3 December 2009; pp. 331–338. [Google Scholar]
- Kang, W.; Wu, Q. Contactless palm vein recognition using a mutual foreground-based local binary pattern. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1974–1985. [Google Scholar] [CrossRef]
- Piekarczyk, M.; Ogiela, M.R. Touch-Less Personal Verification Using Palm and Fingers Movements Tracking. In New Trends in Analysis and Interdisciplinary Applications; Springer: Berlin, Germany, 2017; pp. 603–609. [Google Scholar]
- Tome, P.; Vanoni, M.; Marcel, S. On the vulnerability of finger vein recognition to spoofing. In Proceedings of the International Conference of the Biometrics Special Interest Group (BIOSIG), Darmstadt, Germany, 10–12 September 2014; pp. 1–10. [Google Scholar]
- Tome, P.; Marcel, S. On the vulnerability of palm vein recognition to spoofing attacks. In Proceedings of the International Conference on Biometrics (ICB), Phuket, Thailand, 9–22 May 2015; pp. 319–325. [Google Scholar]
- Titcomb, J. Why Your Smartphone’s Fingerprint Scanner Isn’t as Secure as You Might Think. 2017. Available online: http://www.telegraph.co.uk/technology/2017/04/11/smartphone-fingerprint-scanners-could-easily-fooled-fake-prints/ (accessed on 4 January 2018).
- Jain, A.; Bolle, R.; Pankanti, S. Biometrics: Personal Identification in Networked Society; Springer: Berlin, Germany, 2006; Volume 479. [Google Scholar]
- Maltoni, D.; Maio, D.; Jain, A.; Prabhakar, S. Handbook of Fingerprint Recognition; Springer: Berlin, Germany, 2009. [Google Scholar]
- De Luca, A.; Lindqvist, J. Is secure and usable smartphone authentication asking too much? Computer 2015, 48, 64–68. [Google Scholar] [CrossRef]
- Kong, S.G.; Heo, J.; Boughorbel, F.; Zheng, Y.; Abidi, B.R.; Koschan, A.; Yi, M.; Abidi, M.A. Multiscale fusion of visible and thermal IR images for illumination-invariant face recognition. Int. J. Comput. Vis. 2007, 71, 215–233. [Google Scholar] [CrossRef]
- Guzman, A.M.; Goryawala, M.; Wang, J.; Barreto, A.; Andrian, J.; Rishe, N.; Adjouadi, M. Thermal imaging as a biometrics approach to facial signature authentication. IEEE J. Biomed. Health Inform. 2013, 17, 214–222. [Google Scholar] [CrossRef] [PubMed]
- Hu, S.; Choi, J.; Chan, A.L.; Schwartz, W.R. Thermal-to-visible face recognition using partial least squares. JOSA A 2015, 32, 431–442. [Google Scholar] [CrossRef] [PubMed]
- Denning, D.E.; MacDoran, P.F. Location-based authentication: Grounding cyberspace for better security. Comput. Fraud Secur. 1996, 1996, 12–16. [Google Scholar] [CrossRef]
- Fridman, L.; Weber, S.; Greenstadt, R.; Kam, M. Active authentication on mobile devices via stylometry, application usage, web browsing, and GPS location. IEEE Syst. J. 2017, 11, 513–521. [Google Scholar] [CrossRef]
- Hammad, A.; Faith, P. Location Based Authentication. U.S. Patent 9,721,250, 1 August 2017. [Google Scholar]
- Vacca, J.R. Biometric Technologies and Verification Systems; Butterworth-Heinemann: Oxford, UK, 2007. [Google Scholar]
- Banerjee, S.P.; Woodard, D.L. Biometric authentication and identification using keystroke dynamics: A survey. J. Pattern Recognit. Res. 2012, 7, 116–139. [Google Scholar] [CrossRef]
- Shrestha, B.; Mohamed, M.; Tamrakar, S.; Saxena, N. Theft-resilient mobile wallets: Transparently authenticating NFC users with tapping gesture biometrics. In Proceedings of the 32nd Annual Conference on Computer Security Applications, Los Angeles, CA, USA, 5–9 December 2016; ACM: New York, NY, USA, 2016; pp. 265–276. [Google Scholar]
- Gascon, H.; Uellenbeck, S.; Wolf, C.; Rieck, K. Continuous Authentication on Mobile Devices by Analysis of Typing Motion Behavior. In Proceedings of the Conference “Sicherheit”, Sicherheit, Schutz und Verlässlichkeit, 19–21 March 2014; pp. 1–12. [Google Scholar]
- Buschek, D.; De Luca, A.; Alt, F. Improving accuracy, applicability and usability of keystroke biometrics on mobile touchscreen devices. In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing Systems, Seoul, Korea, 18–23 April 2015; ACM: New York, NY, USA, 2015; pp. 1393–1402. [Google Scholar]
- Meng, W.; Wong, D.S.; Furnell, S.; Zhou, J. Surveying the development of biometric user authentication on mobile phones. IEEE Commun. Surv. Tutor. 2015, 17, 1268–1293. [Google Scholar] [CrossRef]
- Buriro, A.; Crispo, B.; Del Frari, F.; Wrona, K. Touchstroke: Smartphone user authentication based on touch-typing biometrics. In Proceedings of the International Conference on Image Analysis and Processing, Niagara Falls, ON, Canada, 22–24 July 2015; Springer: Berlin, Germany, 2015; pp. 27–34. [Google Scholar]
- Sae-Bae, N.; Ahmed, K.; Isbister, K.; Memon, N. Biometric-rich gestures: A novel approach to authentication on multi-touch devices. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Montreal, QC, Canada, 22–27 April 2006; ACM: New York, NY, USA, 2012; pp. 977–986. [Google Scholar]
- Lee, W.H.; Lee, R.B. Implicit Smartphone User Authentication with Sensors and Contextual Machine Learning. In Proceedings of the 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Denver, CO, USA, 26–29 June 2017; pp. 297–308. [Google Scholar]
- Burgbacher, U.; Hinrichs, K. An implicit author verification system for text messages based on gesture typing biometrics. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, oronto, ON, Canada, 26 April 26–1 May 2014; ACM: New York, NY, USA, 2014; pp. 2951–2954. [Google Scholar]
- Hachaj, T.T.; Ogiela, M.R.; Baraniewicz, D. Evaluation of Gesture Description Language in the role of touchless interface for virtual reality environment. Prz. Elektrotech. 2017, 93, 57–66. [Google Scholar] [CrossRef]
- Van Goethem, T.; Scheepers, W.; Preuveneers, D.; Joosen, W. Accelerometer-based device fingerprinting for multi-factor mobile authentication. In Proceedings of the International Symposium on Engineering Secure Software and Systems, London, UK, 6–8 April 2016; Springer: Berlin, Germany, 2016; pp. 106–121. [Google Scholar]
- Figueira, C.; Matias, R.; Gamboa, H. Body Location Independent Activity Monitoring. In Proceedings of the International Joint Conference on Biomedical Engineering Systems and Technologies (BIOSIGNALS), Rome, Italy, 21–23 February 2016; pp. 190–197. [Google Scholar]
- Grankin, M.; Khavkina, E.; Ometov, A. Research of MEMS accelerometers features in mobile phone. In Proceedings of the 12th Conference of Open Innovations Association FRUCT, Oulu, Finland, 5–9 November 2012; pp. 31–36. [Google Scholar]
- Wang, W.; Xi, J.; Chen, H. Modeling and recognizing driver behavior based on driving data: A survey. Math. Prob. Eng. 2014, 2014. [Google Scholar] [CrossRef]
- Igarashi, K.; Miyajima, C.; Itou, K.; Takeda, K.; Itakura, F.; Abut, H. Biometric identification using driving behavioral signals. In Proceedings of the International Conference on Multimedia and Expo, Taipei, Taiwan, 27–30 June 2004; Volume 1, pp. 65–68. [Google Scholar]
- McCall, J.C.; Trivedi, M.M. Driver behavior and situation aware brake assistance for intelligent vehicles. Proc. IEEE 2007, 95, 374–387. [Google Scholar] [CrossRef]
- Oliver, N.; Pentland, A.P. Driver behavior recognition and prediction in a SmartCar. In Proceedings of the International Society for Optics and Photonics Meeting, Orlando, FL, USA, 24–28 April 2000; Volume 4023, pp. 280–290. [Google Scholar]
- Shi, E.; Niu, Y.; Jakobsson, M.; Chow, R. Implicit Authentication through Learning User Behavior. In Proceedings of the 13th International Conference, ISC 2010, Boca Raton, FL, USA, 25–28 October 2010; Springer: Berlin, Germany, 2010; Volume 6531, pp. 99–113. [Google Scholar]
- Nothacker, K.H.; Basaran, P.A.; Rettus, S.I.; Strasser, M.J.; Aziz, I.; Walton, J.P.; Saul, Z.M.; Faykus, C.T. Method and System for Monitoring Intoxication. U.S. Patent 9,192,334, 24 November 2015. [Google Scholar]
- He, D.; Zeadally, S. An analysis of RFID authentication schemes for Internet of Things in healthcare environment using elliptic curve cryptography. IEEE Internet Things J. 2015, 2, 72–83. [Google Scholar] [CrossRef]
- Xiao, L.; Chen, T.; Han, G.; Zhuang, W.; Sun, L. Channel-Based Authentication Game in MIMO Systems. In Proceedings of the Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 Decembe 2016; pp. 1–6. [Google Scholar]
- Zhao, N.; Zhang, Z.; Rehman, M.U.; Ren, A.; Yang, X.; Zhao, J.; Zhao, W.; Dong, B. Authentication in Millimeter-Wave Body-Centric Networks through Wireless Channel Characterization. IEEE Trans. Antennas Propag. 2017, 65, 6616–6623. [Google Scholar] [CrossRef]
- Gapeyenko, M.; Samuylov, A.; Gerasimenko, M.; Moltchanov, D.; Singh, S.; Aryafar, E.; Yeh, S.P.; Himayat, N.; Andreev, S.; Koucheryavy, Y. Analysis of human-body blockage in urban millimeter-wave cellular communications. In Proceedings of the International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–7. [Google Scholar]
- Mercedes-Benz SUV Operation Manual. Occupant Classification System (OCS). 2017. Available online: http://www.mersuv.com/mbread-149.html (accessed on 4 January 2018).
- Farmer, M.E.; Jain, A.K. Occupant classification system for automotive airbag suppression. In Proceedings of the Computer Society Conference on Computer Vision and Pattern Recognition, Madison, WI, USA, 18–20 June 2003; Volume 1. [Google Scholar]
- Mehney, M.A.; McCarthy, M.C.; Fullerton, M.G.; Malecke, F.J. Vehicle Occupant Weight Sensor Apparatus. U.S. Patent 6,039,344, 6 July 2000. [Google Scholar]
- Ferro, M.; Pioggia, G.; Tognetti, A.; Carbonaro, N.; De Rossi, D. A sensing seat for human authentication. IEEE Trans. Inf. Forensics Secur. 2009, 4, 451–459. [Google Scholar] [CrossRef]
- Silva, H.; Lourenço, A.; Fred, A. In-vehicle driver recognition based on hand ECG signals. In Proceedings of the International conference on Intelligent User Interfaces, Lisbon, Portugal, 14–17 February 2012; ACM: New York, NY, USA, 2012; pp. 25–28. [Google Scholar]
- Pham, T.; Ma, W.; Tran, D.; Nguyen, P.; Phung, D. Multi-factor EEG-based user authentication. In Proceedings of the International Joint Conference on Neural Networks (IJCNN), Beijing, China, 6–11 July 2014; pp. 4029–4034. [Google Scholar]
- Paranjape, R.; Mahovsky, J.; Benedicenti, L.; Koles, Z. The electroencephalogram as a biometric. In Proceedings of the Canadian Conference on Electrical and Computer Engineering, Toronto, ON, Canada, 13–16 May 2001; Volume 2, pp. 1363–1366. [Google Scholar]
- Chuang, J.; Nguyen, H.; Wang, C.; Johnson, B. I think, therefore I am: Usability and security of authentication using brainwaves. In Proceedings of the International Conference on Financial Cryptography and Data Security, Okinawa, Japan, 1 April 2013; Springer: Berlin, Germany, 2013; pp. 1–16. [Google Scholar]
- Mohanchandra, K.; Lingaraju, G.; Kambli, P.; Krishnamurthy, V. Using brain waves as new biometric feature for authenticating a computer user in real-time. Int. J. Biom. Bioinform. (IJBB) 2013, 7, 49. [Google Scholar]
- Siswoyo, A.; Arief, Z.; Sulistijono, I.A. Application of Artificial Neural Networks in Modeling Direction Wheelchairs Using Neurosky Mindset Mobile (EEG) Device. EMITTER Int. J. Eng. Technol. 2017, 5, 170–191. [Google Scholar] [CrossRef]
- Reid, Y.; Storts, D.; Riss, T.; Minor, L. Authentication of Human Cell Lines by STR DNA Profiling Analysis. Eli Lilly & Company and the National Center for Advancing Translational Sciences, 2013. Available online: https://www.ncbi.nlm.nih.gov/books/NBK144066/ (accessed on 4 January 2018).
- Yun, Y.W. The ‘123’ of biometric technology. Synth. J. 2002, 3, 83–96. [Google Scholar]
- Kraus, L.; Antons, J.N.; Kaiser, F.; Möller, S. User experience in authentication research: A Survey. In Proceedings of the PQS 2016, Berlin, Germany, 29–31 August 2016; pp. 54–58. [Google Scholar]
- Katsini, C.; Belk, M.; Fidas, C.; Avouris, N.; Samaras, G. Security and Usability in Knowledge-based User Authentication: A Review. In Proceedings of the 20th Pan-Hellenic Conference on Informatics, Patras, Greece, 10–12 November 2016; ACM: New York, NY, USA, 2016; p. 63. [Google Scholar]
- Nicholson, J.; Coventry, L.; Briggs, P. Age-related performance issues for PIN and face-based authentication systems. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Paris, France, 27 April–2 May 2013; ACM: New York, NY, USA, 2013; pp. 323–332. [Google Scholar]
- Harby, F.; Qahwaji, R.; Kamala, M. End-Users’ Acceptance of Biometrics Authentication to Secure E-Commerce within the Context of Saudi Culture: Applying the UTAUT Model. In Globalization, Technology Diffusion and Gender Disparity: Social Impacts of ICTs; Information Science Reference: Hershey, PA, USA, 2012; pp. 225–246. [Google Scholar]
- Ogiela, M.R.; Ogiela, L. Behavioral Keys in Cryptography and Security Systems. In Proceedings of the International Conference on Intelligent Networking and Collaborative Systems, Toronto, ON, Canada, 24–26 August 2017; Springer: Berlin, Germany, 2017; pp. 296–300. [Google Scholar]
- Al-Ameen, M.N.; Wright, M.; Scielzo, S. Towards Making Random Passwords Memorable: Leveraging Users’ Cognitive Ability Through Multiple Cues. In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing Systems, Seoul, Korea, 18–23 April 2015; ACM: New York, NY, USA, 2015; pp. 2315–2324. [Google Scholar]
- Belk, M.; Fidas, C.; Germanakos, P.; Samaras, G. The interplay between humans, technology and user authentication: A cognitive processing perspective. Comput. Hum. Behav. 2017, 76, 184–200. [Google Scholar] [CrossRef]
- Ma, Y.; Feng, J.; Kumin, L.; Lazar, J. Investigating user behavior for authentication methods: A comparison between individuals with down syndrome and neurotypical users. ACM Trans. Access. Comput. (TACCESS) 2013, 4, 15. [Google Scholar] [CrossRef]
- Melicher, W.; Kurilova, D.; Segreti, S.M.; Kalvani, P.; Shay, R.; Ur, B.; Bauer, L.; Christin, N.; Cranor, L.F.; Mazurek, M.L. Usability and security of text passwords on mobile devices. In Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems, San Jose, CA, USA, 7–12 May 2016; ACM: New York, NY, USA, 2016; pp. 527–539. [Google Scholar]
- Von Zezschwitz, E.; De Luca, A.; Hussmann, H. Honey, I shrunk the keys: Influences of mobile devices on password composition and authentication performance. In Proceedings of the 8th Nordic Conference on Human-Computer Interaction: Fun, Fast, Foundational, Helsinki, Finland, 26–30 October 2014; ACM: New York, NY, USA, 2014; pp. 461–470. [Google Scholar]
- Fathi, R.; Salehi, M.A.; Leiss, E.L. User-friendly and secure architecture (UFSA) for authentication of cloud services. In Proceedings of the 8th International Conference on Cloud Computing (CLOUD), New York, NY, USA, 27 June–2 July 2015; pp. 516–523. [Google Scholar]
- Aumi, M.T.I.; Kratz, S. AirAuth: Evaluating in-air hand gestures for authentication. In Proceedings of the 16th International Conference on Human-Computer Interaction with Mobile Devices & Services, Toronto, ON, Canada, 23–26 September 2014; ACM: New York, NY, USA, 2014; pp. 309–318. [Google Scholar]
- Da Silva, H.P.; Fred, A.; Lourenço, A.; Jain, A.K. Finger ECG signal for user authentication: Usability and performance. In Proceedings of the 6th International Conference on Biometrics: Theory, Applications and Systems, Arlington, VA, USA, 29 September–2 October 2013; pp. 1–8. [Google Scholar]
- Michelin, R.A.; Zorzo, A.F.; Campos, M.B.; Neu, C.V.; Orozco, A.M. Smartphone as a biometric service for web authentication. In Proceedings of the 11th International Conference for Internet Technology and Secured Transactions (ICITST), Barcelona, Spain, 5–7 December 2016; pp. 405–408. [Google Scholar]
- Conti, V.; Collotta, M.; Pau, G.; Vitabile, S. Usability Analysis of a Novel Biometric Authentication Approach for Android-Based Mobile Devices. J. Telecommun. Inf. Technol. 2014, 4, 34–43. [Google Scholar]
- Maple, C.; Norrington, P. The usability and practicality of biometric authentication in the workplace. In Proceedings of the First International Conference on Availability, Reliability and Security, Vienna, Austria, 20–22 April 2006; pp. 1–7. [Google Scholar]
- Matyáš, V.; Říha, Z. Biometric authentication–security and usability. In Advanced Communications and Multimedia Security; Springer: Berlin, Germany, 2002; pp. 227–239. [Google Scholar]
- NetworkWorld. Solving the Challenge of Multi-Factor Authentication Adoption. 2017. Available online: https://www.networkworld.com/article/3197096/lan-wan/solving-the-challenge-of-multi-factor-authentication-adoption.html (accessed on 4 January 2018).
- TechTarget. Logical, Physical Security Integration Challenges. 2017. Available online: http://searchsecurity.techtarget.com/magazineContent/Logical-physical-security-integration-challenges (accessed on 4 January 2018).
- Tolosana, R.; Vera-Rodriguez, R.; Ortega-Garcia, J.; Fierrez, J. Preprocessing and feature selection for improved sensor interoperability in online biometric signature verification. IEEE Access 2015, 3, 478–489. [Google Scholar] [CrossRef]
- Galbally, J.; Satta, R. Biometric Sensor Interoperability: A Case Study in 3D Face Recognition. In Proceedings of the ICPRAM, Rome, Italy, 24–26 February 2016; pp. 199–204. [Google Scholar]
- Alonso-Fernandez, F.; Fierrez, J.; Ramos, D.; Gonzalez-Rodriguez, J. Quality-based conditional processing in multi-biometrics: application to sensor interoperability. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2010, 40, 1168–1179. [Google Scholar] [CrossRef]
- Bandara, H.; De Silva, S.R.P.; Weerasinghe, P.D. The universal biometric system. In Proceedings of the International Conference on Advances in ICT for Emerging Regions, Colombo, Sri Lanka, 24–26 August 2015; pp. 1–6. [Google Scholar]
- Jain, A.K.; Nandakumar, K. Biometric Authentication: System Security and User Privacy. IEEE Comput. 2012, 45, 87–92. [Google Scholar] [CrossRef]
- Biggio, B.; Akhtar, Z.; Fumera, G.; Marcialis, G.L.; Roli, F. Security evaluation of biometric authentication systems under real spoofing attacks. IET Biom. 2012, 1, 11–24. [Google Scholar] [CrossRef]
- Marcel, S.; Nixon, M.S.; Li, S.Z. Handbook of Biometric Anti-Spoofing; Springer: Berlin, Germany, 2014; Volume 1. [Google Scholar]
- Uludag, U.; Jain, A.K. Attacks on biometric systems: A case study in fingerprints. In Proceedings of the SPIE, San Jose, CA, USA, 19–22 January 2004; Volume 5306, pp. 622–633. [Google Scholar]
- He, D.; Zeadally, S. Authentication protocol for an ambient assisted living system. IEEE Commun. Mag. 2015, 53, 71–77. [Google Scholar] [CrossRef]
- Rodrigues, R.N.; Kamat, N.; Govindaraju, V. Evaluation of biometric spoofing in a multimodal system. In Proceedings of the 4th IEEE International Conference on Biometrics: Theory Applications and Systems (BTAS), Washington, DC, USA, 27–29 September 2010; pp. 1–5. [Google Scholar]
- Jain, A.K.; Nandakumar, K.; Nagar, A. Biometric template security. EURASIP J. Adv. Signal Process. 2008, 2008, 113. [Google Scholar] [CrossRef]
- Andreev, S.; Hosek, J.; Olsson, T.; Johnsson, K.; Pyattaev, A.; Ometov, A.; Olshannikova, E.; Gerasimenko, M.; Masek, P.; Koucheryavy, Y.; et al. A unifying perspective on proximity-based cellular-assisted mobile social networking. IEEE Commun. Mag. 2016, 54, 108–116. [Google Scholar] [CrossRef]
- Ometov, A.; Zhidanov, K.; Bezzateev, S.; Florea, R.; Andreev, S.; Koucheryavy, Y. Securing network-assisted direct communication: The case of unreliable cellular connectivity. In Proceedings of the Trustcom/ BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 826–833. [Google Scholar]
- Chingovska, I.; Anjos, A.; Marcel, S. On the effectiveness of local binary patterns in face anti-spoofing. In Proceedings of the International Conference of theBiometrics Special Interest Group (BIOSIG), Darmstadt, Germany, 6–7 September 2012; pp. 1–7. [Google Scholar]
- Vaidya, B.; Makrakis, D.; Mouftah, H.T. Improved two-factor user authentication in wireless sensor networks. In Proceedings of the 6th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Niagara Falls, NU, Canada, 11–13 October 2010; pp. 600–606. [Google Scholar]
- Rathgeb, C.; Uhl, A. A survey on biometric cryptosystems and cancelable biometrics. J. Inf. Secur. (EURASIP) 2011. [Google Scholar] [CrossRef]
- Chen, B.; Chandran, V. Biometric template security using higher order spectra. In Proceedings of the International Conference on Acoustics Speech and Signal Processing (ICASSP), Dallas, TX, USA, 14–19 March 2010; pp. 1730–1733. [Google Scholar]
- Fierrez, J.; Ortega-Garcia, J.; Toledano, D.T.; Gonzalez-Rodriguez, J. BioSec baseline corpus: A multimodal biometric database. Pattern Recognit. 2007, 40, 1389–1392. [Google Scholar] [CrossRef]
- Fierrez, J.; Galbally, J.; Ortega-Garcia, J.; Freire, M.R.; Alonso-Fernandez, F.; Ramos, D.; Toledano, D.T.; Gonzalez-Rodriguez, J.; Siguenza, J.A.; Garrido-Salas, J.; et al. BiosecurID: A multimodal biometric database. Pattern Anal. Appl. 2010, 13, 235–246. [Google Scholar] [CrossRef]
- Gomez-Barrero, M.; Rathgeb, C.; Galbally, J.; Busch, C.; Fierrez, J. Unlinkable and irreversible biometric template protection based on bloom filters. Inf. Sci. 2016, 370, 18–32. [Google Scholar] [CrossRef]
- Fan, Y.; Zhang, Z.; Trinkle, M.; Dimitrovski, A.D.; Song, J.B.; Li, H. A cross-layer defense mechanism against GPS spoofing attacks on PMUs in smart grids. IEEE Trans. Smart Grid 2015, 6, 2659–2668. [Google Scholar] [CrossRef]
- Heng, L.; Work, D.B.; Gao, G.X. GPS signal authentication from cooperative peers. IEEE Trans. Intell. Trans. Syst. 2015, 16, 1794–1805. [Google Scholar] [CrossRef]
- Lichtman, M.; Jover, R.P.; Labib, M.; Rao, R.; Marojevic, V.; Reed, J.H. LTE/LTE-A jamming, spoofing, and sniffing: Threat assessment and mitigation. IEEE Commun. Mag. 2016, 54, 54–61. [Google Scholar] [CrossRef]
- Sheng, Y.; Tan, K.; Chen, G.; Kotz, D.; Campbell, A. Detecting 802.11 MAC layer spoofing using received signal strength. In Proceedings of the 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 1768–1776. [Google Scholar]
- Wayman, J.; Jain, A.; Maltoni, D.; Maio, D. An introduction to biometric authentication systems. Biom. Syst. 2005, 1–20. [Google Scholar] [CrossRef]
- Benchmark. Deploying Fingerprint Biometrics. 2017. Available online: http://benchmarkmagazine.com/deploying-fingerprint-biometrics/ (accessed on 1 January 2017).
- Ratha, N.; Bolle, R. Automatic Fingerprint Recognition Systems; Springer: Berlin, Germany, 2007. [Google Scholar]
- Sariyanidi, E.; Gunes, H.; Cavallaro, A. Automatic analysis of facial affect: A survey of registration, representation, and recognition. IEEE Trans. Pattern Anal. Mach. Intell. 2015, 37, 1113–1133. [Google Scholar] [CrossRef] [PubMed]
- Raja, K.B.; Raghavendra, R.; Stokkenes, M.; Busch, C. Multi-modal authentication system for smartphones using face, iris and periocular. In Proceedings of the International Conference on Biometrics (ICB), Phuket, Thailand, 19–22 May 2015; pp. 143–150. [Google Scholar]
- Golfarelli, M.; Maio, D.; Malton, D. On the error-reject trade-off in biometric verification systems. IEEE Trans. Pattern Anal. Mach. Intell. 1997, 19, 786–796. [Google Scholar] [CrossRef]
- Sanmorino, A.; Yazid, S. A survey for handwritten signature verification. In Proceedings of the 2nd International Conference on Uncertainty Reasoning and Knowledge Engineering (URKE), Jalarta, Indonesia, 14–15 August 2012; pp. 54–57. [Google Scholar]
- Jain, A.K.; Ross, A.; Prabhakar, S. An introduction to biometric recognition. IEEE Trans. Circuits Syst. Video Technol. 2004, 14, 4–20. [Google Scholar] [CrossRef]
- Kholmatov, A.; Yanikoglu, B. Identity authentication using improved online signature verification method. Pattern Recognit. Lett. 2005, 26, 2400–2408. [Google Scholar] [CrossRef]
- Utter, T.; Proefke, D.; Baillargeon, R. Multiple Vehicle Authentication for Entry and Starting Systems. U.S. Patent 20070001805, 4 January 2007. [Google Scholar]
- Cranor, L.F.; Garfinkel, S. Security and Usability: Designing Secure Systems that People Can Use; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2005. [Google Scholar]
- Ometov, A.; Masek, P.; Malina, L.; Florea, R.; Hosek, J.; Andreev, S.; Hajny, J.; Niutanen, J.; Koucheryavy, Y. Feasibility characterization of cryptographic primitives for constrained (wearable) IoT devices. In Proceedings of the International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), Sydney, Australia, 14–18 March 2016; pp. 1–6. [Google Scholar]
- SC Media UK. Making the Case for the Use of Biometrics in Multi-Factor Authentication. 2016. Available online: https://www.scmagazineuk.com/making-the-case-for-the-use-of-biometrics-in-multi-factor-authentication/article/545395/ (accessed on 1 January 2018).
- Lai, C.P.; Ding, C. Several generalizations of Shamir’s secret sharing scheme. Int. J. Found. Comput. Sci. 2004, 15, 445–458. [Google Scholar] [CrossRef]
- Ometov, A.; Orsino, A.; Militano, L.; Araniti, G.; Moltchanov, D.; Andreev, S. A novel security-centric framework for D2D connectivity based on spatial and social proximity. Comput. Netw. 2016, 107, 327–338. [Google Scholar] [CrossRef]
- Yang, C.C.; Chang, T.Y.; Hwang, M.S. A(t,n) multi-secret sharing scheme. Appl. Math. Comput. 2004, 151, 483–490. [Google Scholar] [CrossRef]
- Dehkordi, M.H.; Mashhadi, S. An efficient threshold verifiable multi-secret sharing. Comput. Stand. Interfaces 2008, 30, 187–190. [Google Scholar]
- Smart, N.P. Secret Sharing Schemes. In Cryptography Made Simple; Springer: Berlin, Germany, 2016; pp. 403–416. [Google Scholar]
- Harn, L.; Lin, C. Strong (n, t, n) verifiable secret sharing scheme. Inf. Sci. 2010, 180, 3059–3064. [Google Scholar] [CrossRef]
- Ogiela, L.; Ogiela, M.R.; Takizawa, M. Safety and Standardization of Data Sharing Techniques and Protocols for Management of Strategic Data. In Proceedings of the 31st International Conference on Advanced Information Networking and Applications (AINA), Taipei, Taiwan, 27–29 March 2017; pp. 1076–1081. [Google Scholar]
- Kaya, K.; Selçuk, A.A. Threshold cryptography based on Asmuth–Bloom secret sharing. Inf. Sci. 2007, 177, 4148–4160. [Google Scholar] [CrossRef]
- Niinuma, K. Biometric Authentication Device, Biometric Authentication Method and Computer Readable, Non-Transitory Medium. U.S. Patent 9,542,543, 10 January 2017. [Google Scholar]
- Koved, L. Usable Multi-Factor Authentication and Risk-Based Authorization; Technical Report; International Business Machines Corp: Yorktown Heights, NY, USA, 2015. [Google Scholar]
- Thakkar, D. False Acceptance Rate (FAR) and False Recognition Rate (FRR) in Biometrics. 2017. Available online: https://www.bayometric.com/false-acceptance-rate-far-false-recognition-rate-frr/ (accessed on 4 January 2018).
- Castanedo, F. A review of data fusion techniques. Sci. World J. 2013, 2013, 704504. [Google Scholar] [CrossRef] [PubMed]
- Biometric Signature ID. Biometric signature ID Scores an Outstanding 99.97% Accuracy against Identity Fraud from Tolly Group. 2017. Available online: https://www.biosig-id.com/news-and-events/press-releases/193-biometric-signature-id-scores-an-outstanding-99-97-accuracy-against-identity-fraud-from-tolly-group (accessed on 4 January 2018).
- Weiner, S. The Future of Biometrics Could Be Your Heart. 2017. Available online: http://www.popularmechanics.com/technology/security/a28443/biometric-heart-scanner/ (accessed on 4 January 2018).
- O’Neal, M.; Balagani, K.; Phoha, V.; Rosenberg, A.; Serwadda, A.; Karim, M.E. Context-Aware Active Authentication using Touch Gestures, Typing Patterns and Body Movement; Technical Report; Louisiana Technical University: Ruston, LA, USA, 2016. [Google Scholar]
- NSTC Subcommittee on Biometrics & Identity Management. Biometrics Metrics Report v0.3; Technical Report; U.S. Military Academy: New York, NY, USA, 2012. [Google Scholar]
- Townsend, K. Passive Authentication May Be the Future for User Authentication, and It’s Just Beginning to Appear. 2016. Available online: http://www.securityweek.com/passive-authentication-future-user-authentication (accessed on 4 January 2018).
- Walters, R. Continuous Authentication: The Future of Identity and Access Management (IAM). 2016. Available online: https://www.networkworld.com/article/3121240/security/continuous-authentication-the-future-of-identity-and-access-management-iam.html (accessed on 4 January 2018).
- Bartlett, M.S.; Movellan, J.R.; Sejnowski, T.J. Face recognition by independent component analysis. IEEE Trans. Neural Netw. 2002, 13, 1450–1464. [Google Scholar] [CrossRef] [PubMed]
- Wright, J.; Yang, A.Y.; Ganesh, A.; Sastry, S.S.; Ma, Y. Robust face recognition via sparse representation. IEEE Trans. Pattern Anal. Mach. Intell. 2009, 31, 210–227. [Google Scholar] [CrossRef] [PubMed]
- Berry, P. Biometrics and Artificial Neural Networks: How Big Data Collection Works in Your Favor. 2014. Available online: http://chicagopolicyreview.org/2014/03/04/biometrics-and-artificial-neural-networks-how-big-data-collection-works-in-your-favor/ (accessed on 4 January 2018).
- Sadikoglu, F.; Uzelaltinbulat, S. Biometric Retina Identification Based on Neural Network. Procedia Comput. Sci. 2016, 102, 26–33. [Google Scholar] [CrossRef]
- Yao, Y.; Marcialis, G.L.; Pontil, M.; Frasconi, P.; Roli, F. Combining flat and structured representations for fingerprint classification with recursive neural networks and support vector machines. Pattern Recognit. 2003, 36, 397–406. [Google Scholar] [CrossRef]
- Derakhshani, R.; Ross, A. A texture-based neural network classifier for biometric identification using ocular surface vasculature. In Proceedings of the International Joint Conference on Neural Networks, Orlando, FL, USA, 12–17 August 2007; pp. 2982–2987. [Google Scholar]
- Zhang, X.; Yao, L.; Kanhere, S.S.; Liu, Y.; Gu, T.; Chen, K. MindID: Person Identification from Brain Waves through Attention-based Recurrent Neural Network. arXiv, 2017; arXiv:1711.06149. [Google Scholar]
- Salloum, R.; Kuo, C.C.J. ECG-based biometrics using recurrent neural networks. In Proceedings of the International Conference on Acoustics, Speech and Signal Processing (ICASSP), New Orleans, LA, USA, 5–9 March 2017; pp. 2062–2066. [Google Scholar]
- Biometrics Research Group, Inc. Mobile Biometric Applications. 2017. Available online: http://chicagopolicyreview.org/2014/03/04/biometrics-and-artificial-neural-networks-how-big-data-collection-works-in-your-favor/ (accessed on 4 January 2018).
- Acuity Market Intelligence. The Global Biometrics and Mobility Report: The Convergence of Commerce and Privacy. 2016. Available online: http://www.acuity-mi.com/GBMR_Report.php (accessed on 4 January 2018).


| Factor | Universality | Uniqueness | Collectability | Performance | Acceptability | Spoofing |
|---|---|---|---|---|---|---|
| Password | n/a | L | H | H | H | H |
| Token | n/a | M | H | H | H | H |
| Voice | M | L | M | L | H | H |
| Facial | H | L | M | L | H | M |
| Ocular-based | H | H | M | M | L | H |
| Fingerprint | M | H | M | H | M | H |
| Hand geometry | M | M | M | M | M | M |
| Location | n/a | L | M | H | M | H |
| Vein | M | M | M | M | M | M |
| Thermal image | H | H | L | M | H | H |
| Behavior | H | H | L | L | L | L |
| Beam-forming | n/a | M | L | L | L | H |
| OCS | n/a | L | L | L | L | M |
| ECG | L | H | L | M | M | L |
| EEG | L | H | L | M | L | L |
| DNA | H | H | L | H | L | L |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ometov, A.; Bezzateev, S.; Mäkitalo, N.; Andreev, S.; Mikkonen, T.; Koucheryavy, Y. Multi-Factor Authentication: A Survey. Cryptography 2018, 2, 1. https://doi.org/10.3390/cryptography2010001
Ometov A, Bezzateev S, Mäkitalo N, Andreev S, Mikkonen T, Koucheryavy Y. Multi-Factor Authentication: A Survey. Cryptography. 2018; 2(1):1. https://doi.org/10.3390/cryptography2010001
Chicago/Turabian StyleOmetov, Aleksandr, Sergey Bezzateev, Niko Mäkitalo, Sergey Andreev, Tommi Mikkonen, and Yevgeni Koucheryavy. 2018. "Multi-Factor Authentication: A Survey" Cryptography 2, no. 1: 1. https://doi.org/10.3390/cryptography2010001
APA StyleOmetov, A., Bezzateev, S., Mäkitalo, N., Andreev, S., Mikkonen, T., & Koucheryavy, Y. (2018). Multi-Factor Authentication: A Survey. Cryptography, 2(1), 1. https://doi.org/10.3390/cryptography2010001










