Anomalous Traffic Detection and Self-Similarity Analysis in the Environment of ATMSim †
Abstract
:1. Introduction
2. Theoretical Background
2.1. Stochastic Self-Similar Processes
2.2. ARP Spoofing and DDoS
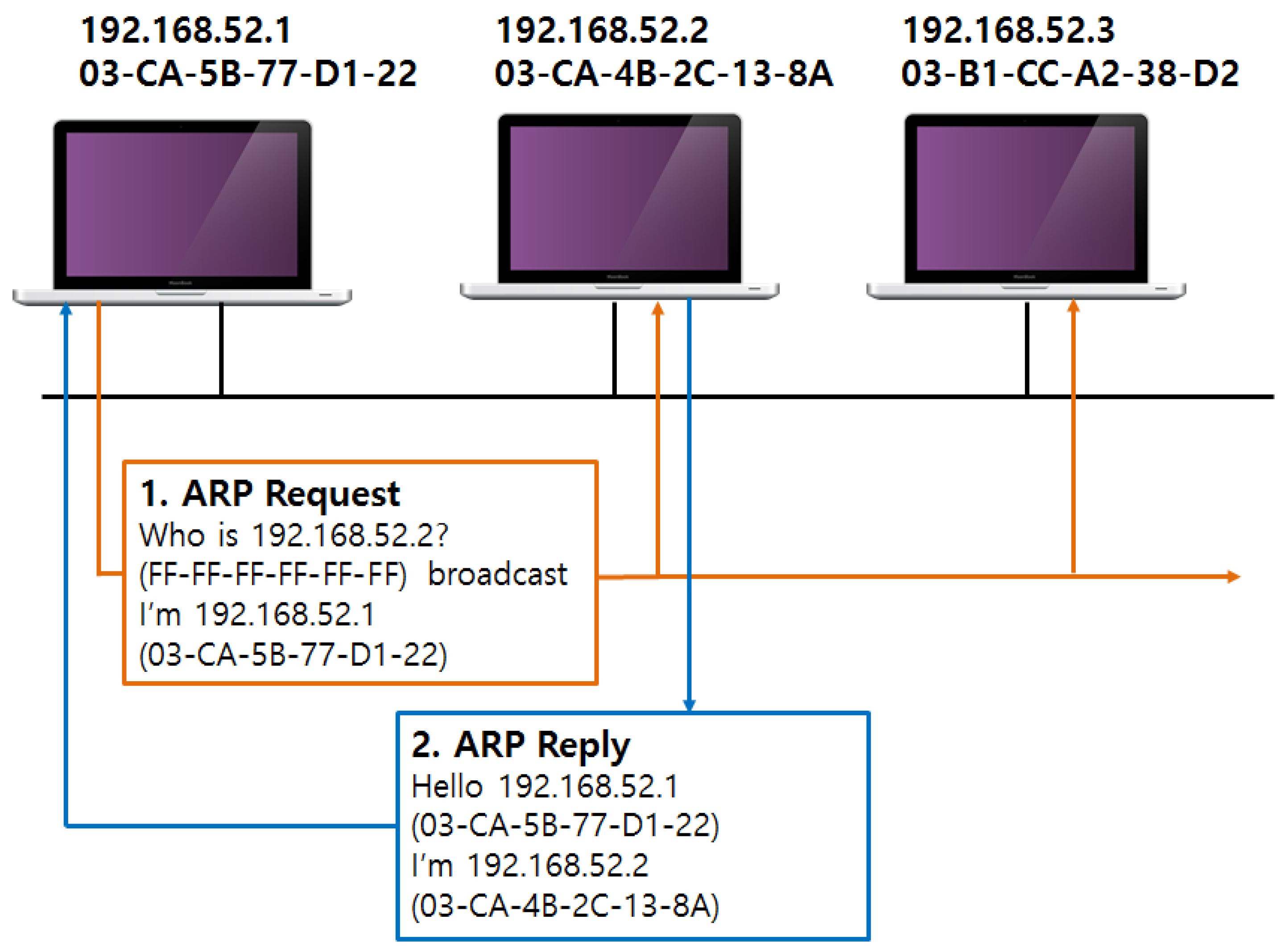
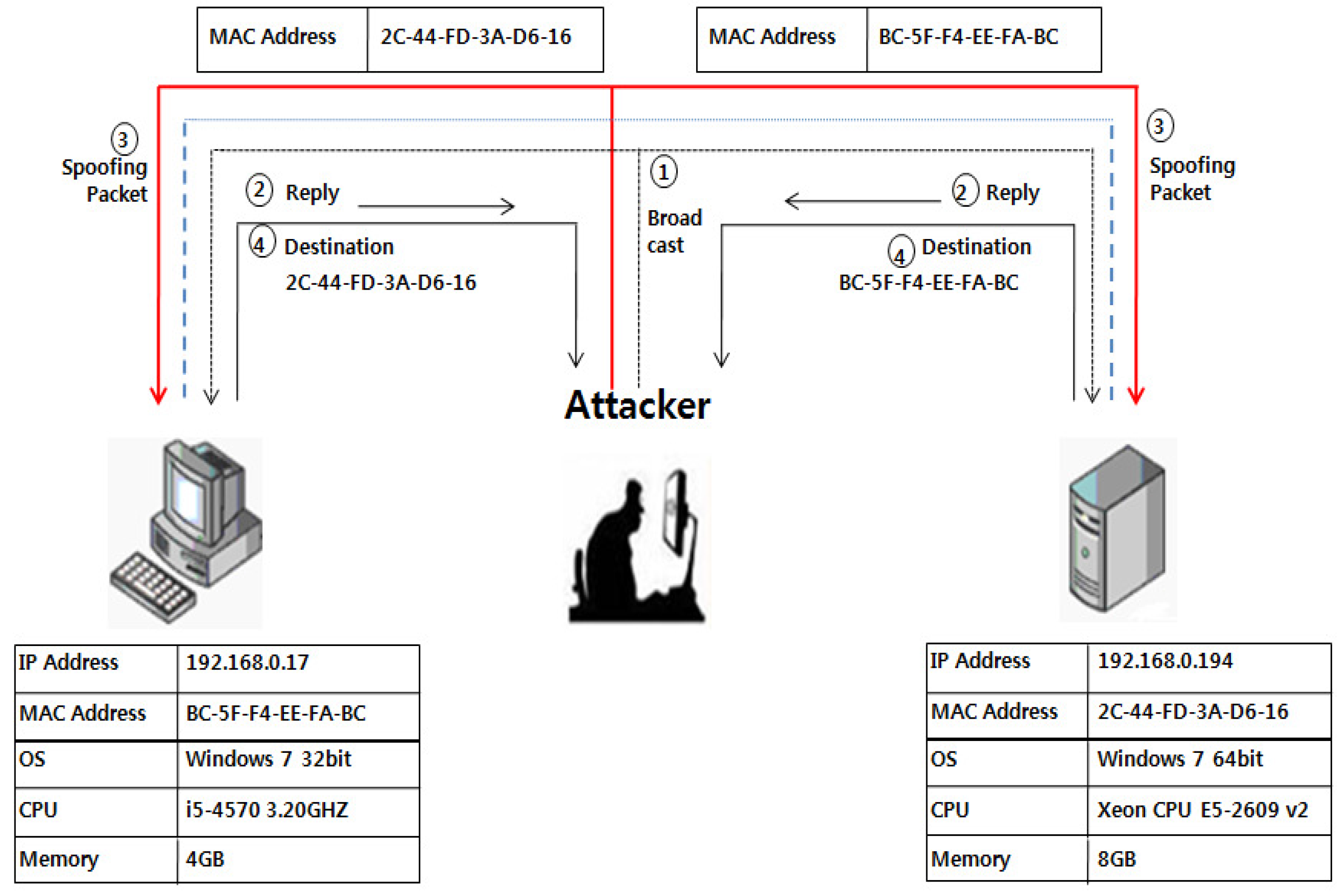
2.2.1. ARP Spoofing
- (1)
- Host A: Host B IP/MAC address mapping identification check in the local ARP cache
- (2)
- Host A → ARP request: Broadcasting of the Host B IP MAC address
- (3)
- Host B → ARP reply: Transfer of ARP reply including the Host B IP and MAC address to Host A
- (4)
- Host A: ARP cache update
- (1)
- IP address .18 ARP spoofing infection
- (2)
- IP address .10 ARP spoofing infection
- (3)
- All communications between the two nodes(.10, .18) are exposed to the hacker
2.2.2. Distributed Denial-of-Service (DDoS)
- Application level: They prevent the normal execution of application programs like sendmail, talkd, inetd, and httpd to paralyse the network function of the system.
- Packet level: Can be an attack method at a lower level than the application program level, for example, through packets roaming in the Transmission Control Protocol/Internet Protocol (TCP/IP), or the Ethernet layer, randomly manipulated to paralyse the network function of the target system. A representative example is an SYN flooding attack.
- Network traffic increase: Network traffic is increased to a limited bandwidth to paralyse the network. DoS attacks are approached in the above manner and have the following attack objectives:
- Destructive attack: Damage of disks, data, or systems
- Exhaustion of system resources: Excessive loads on CPU, memory, and disk usage
- Exhaustion of network resources: Depletion of the network bandwidth with garbage data
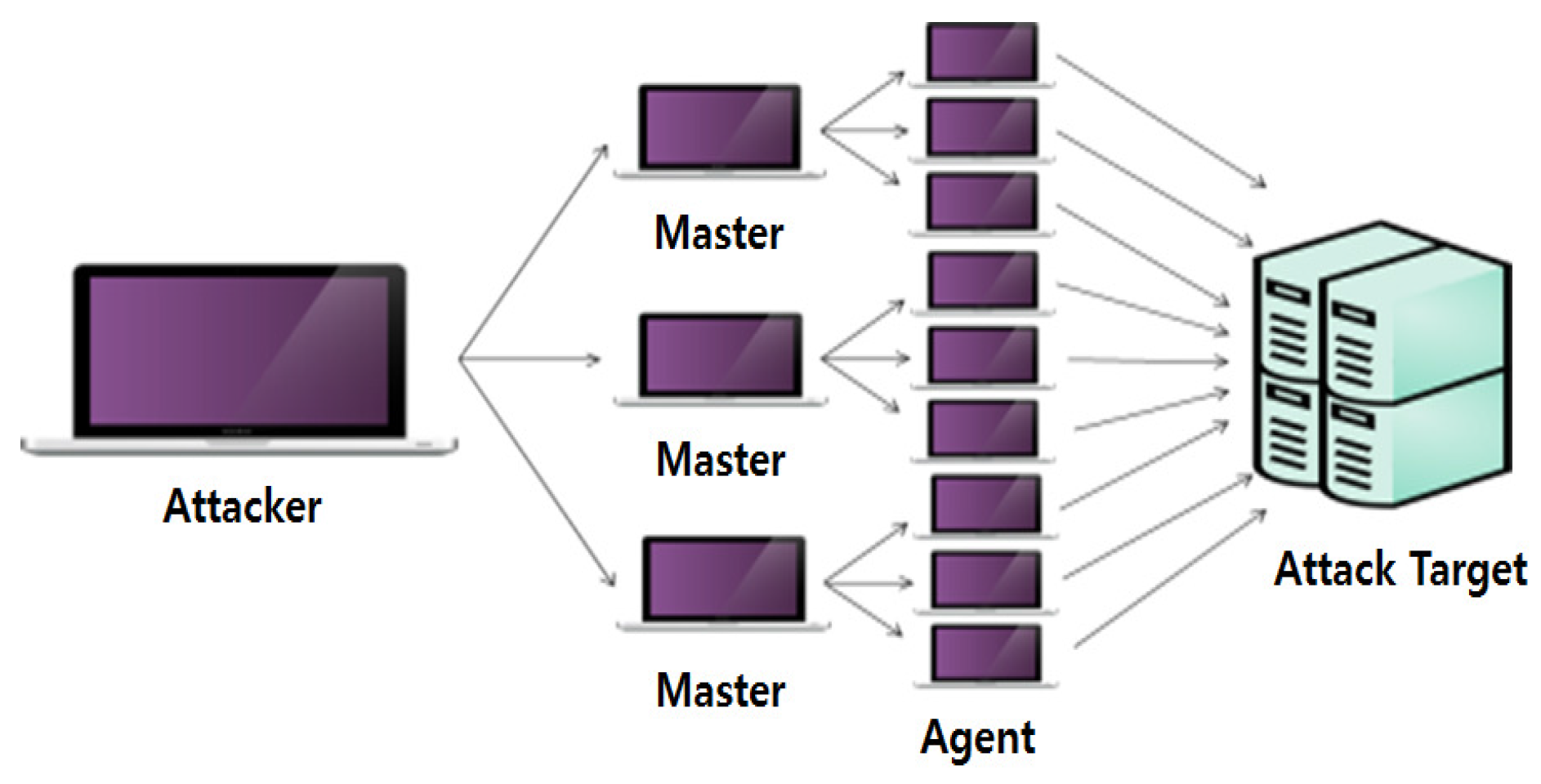
- Attacker: The computer of the hacker leading the attack
- Master: The system that directly receives commands from the attacker and manages the numerous agents
- Handler: The program that performs the above tasks on the program master system
- Agent: The system that directly attacks the attack target
- Demon program: The program that performs the above tasks on the agent system
- (1)
- Sniffing or buffer overflow are employed in populous and large-bandwidth networks that cannot be managed in detail to acquire root access.
- (2)
- The network is scanned in sections to determine attack targets and then servers that provide vulnerable services in remote locations are identified.
- (3)
- After identifying the list of vulnerable systems, an exploit list for actual attack is constructed.
- (4)
- The exploit list is compiled and installed on the system with access.
- (5)
- Attack is initiated with the installed exploit.
- Misuse detection: Specific signals are extracted from known attack patterns for intrusion detection, and hence the rate of false positives is low. However, because known attack patterns are used, the rate of false negatives is high for attacks of unknown attack patterns.
- Anomaly detection: A normal range is established and a deviation from that range is determined to be an intrusion. In contrast to the misuse detection method, anomaly detection is able to detect unknown attacks so this method has a low rate of false negatives, but there is the disadvantage that the rate of false positives is high, as attacks within the established normal range are considered normal. Generally, anomaly detection is performed based on stochastic approaches. A variety of techniques is available in addition to the stochastic method including integration of the feature extraction and abnormal behaviour measurement methods [28,29,30,31].
- Hybrid detection: This is a network intrusion detection method that combines the advantages of the misuse detection and anomaly detection methods. The pattern storage method of the misuse detection method is used to collect the pattern data, which is then utilised to determine a range that the system uses to detect abnormal phenomena using the anomaly detection method.
3. ATMSim Architecture and Graphic User Interface
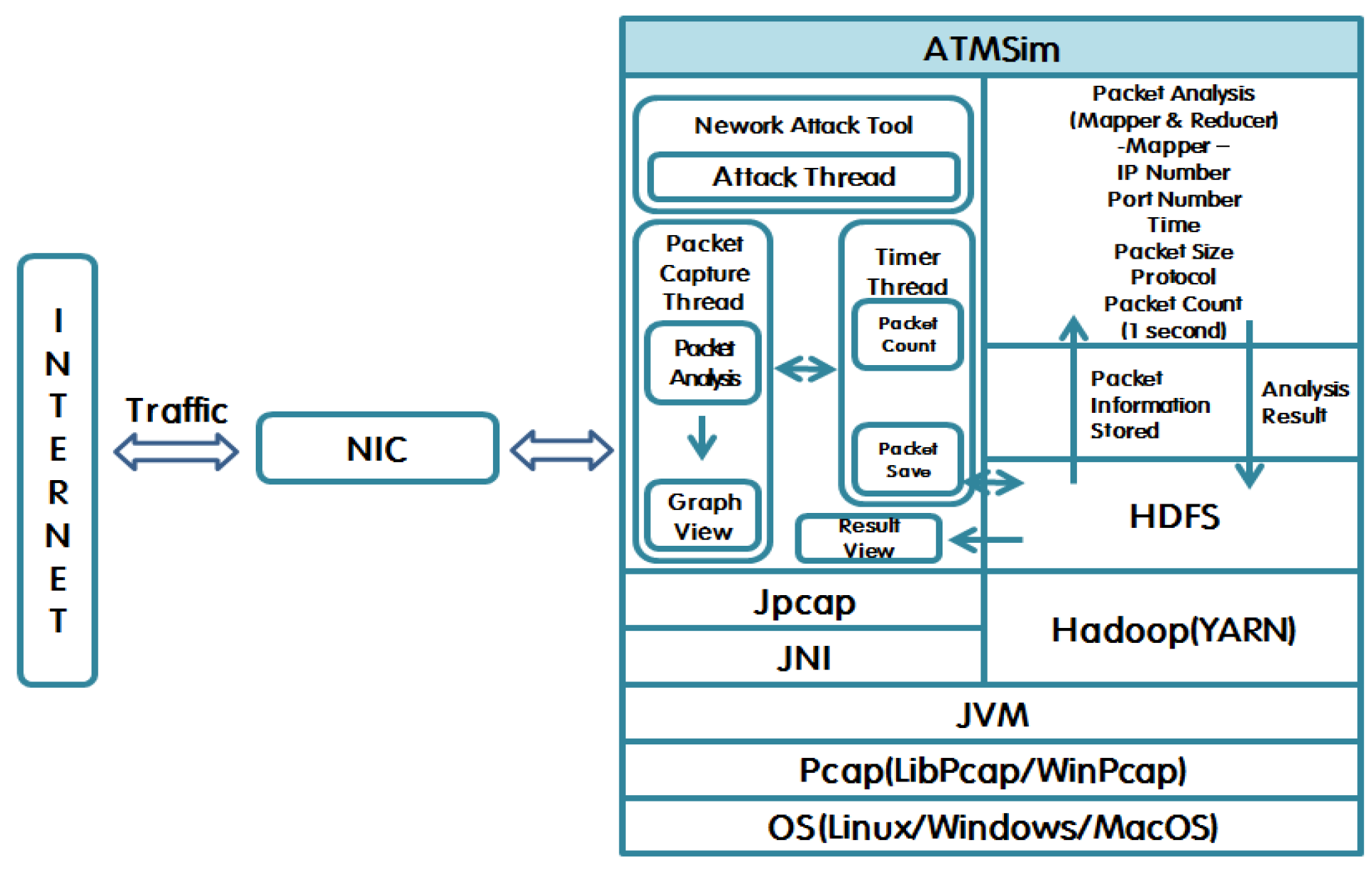
3.1. ATMSim Architecture
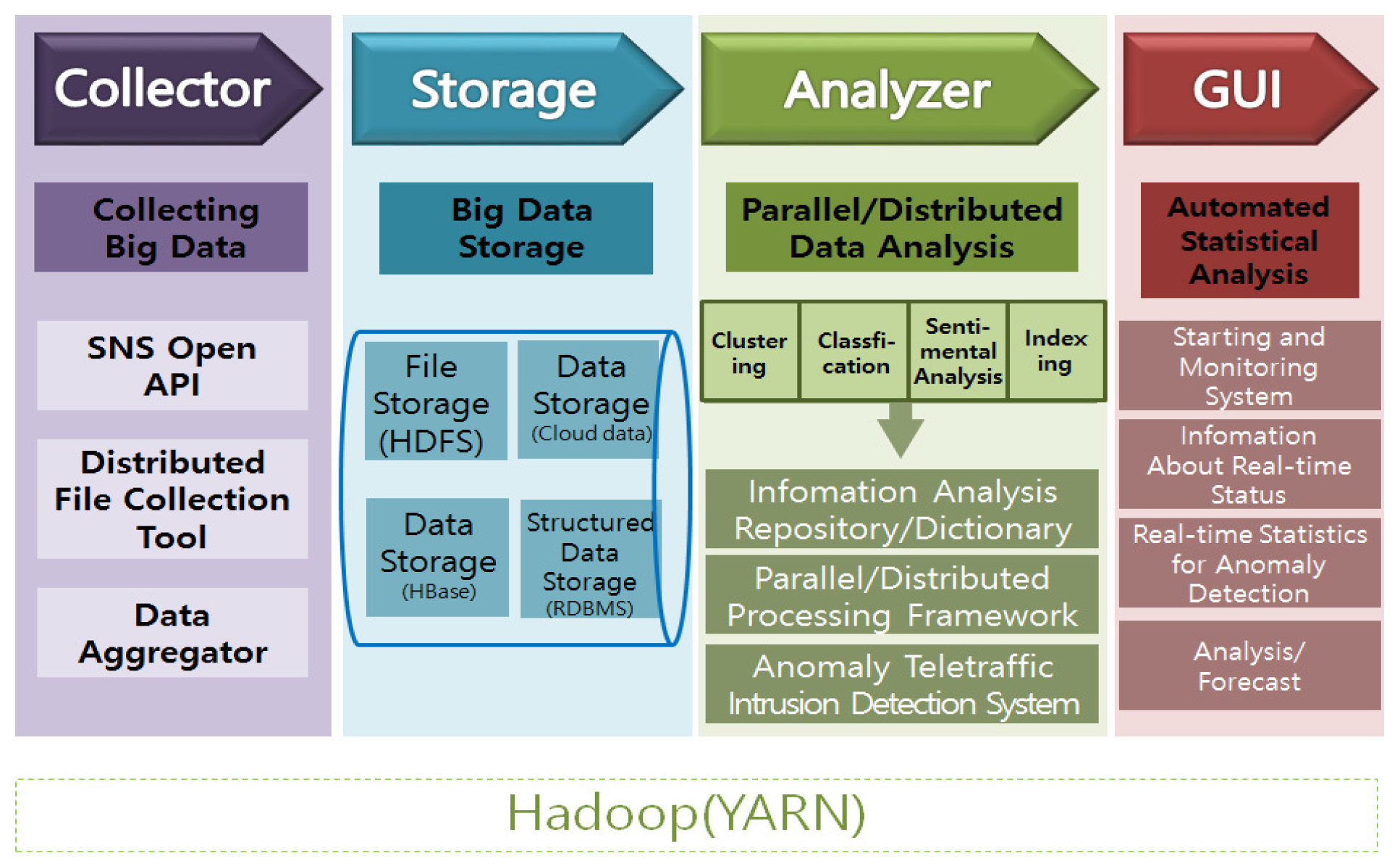
- The collector module acquires data from web page data, SNS data, and the system log (e.g., Facebook, Twitter) and distributes the data to file collection tools, data collection robots, and data aggregators.
- The storage module is stored and managed by the file storage, and real-time analysis and filtering are performed through data storage and structure data storages.
- The analysis and cluster of the analyser module classify the parallel and distributed data. The analyser module is responsible for the important roles of content analysis, explanation analysis, prediction analysis, natural language processing, and text mining. Also, anomaly-based teletraffic intrusion detection systems (AT-IDSs) detect anomalous traffic using the MapReduce framework.
- Real-time statistical data is acquired in this step and the statistical analysis results are automatically provided.
- Figure 5 shows the ATMSim system architecture.
3.2. ATMSim Operation
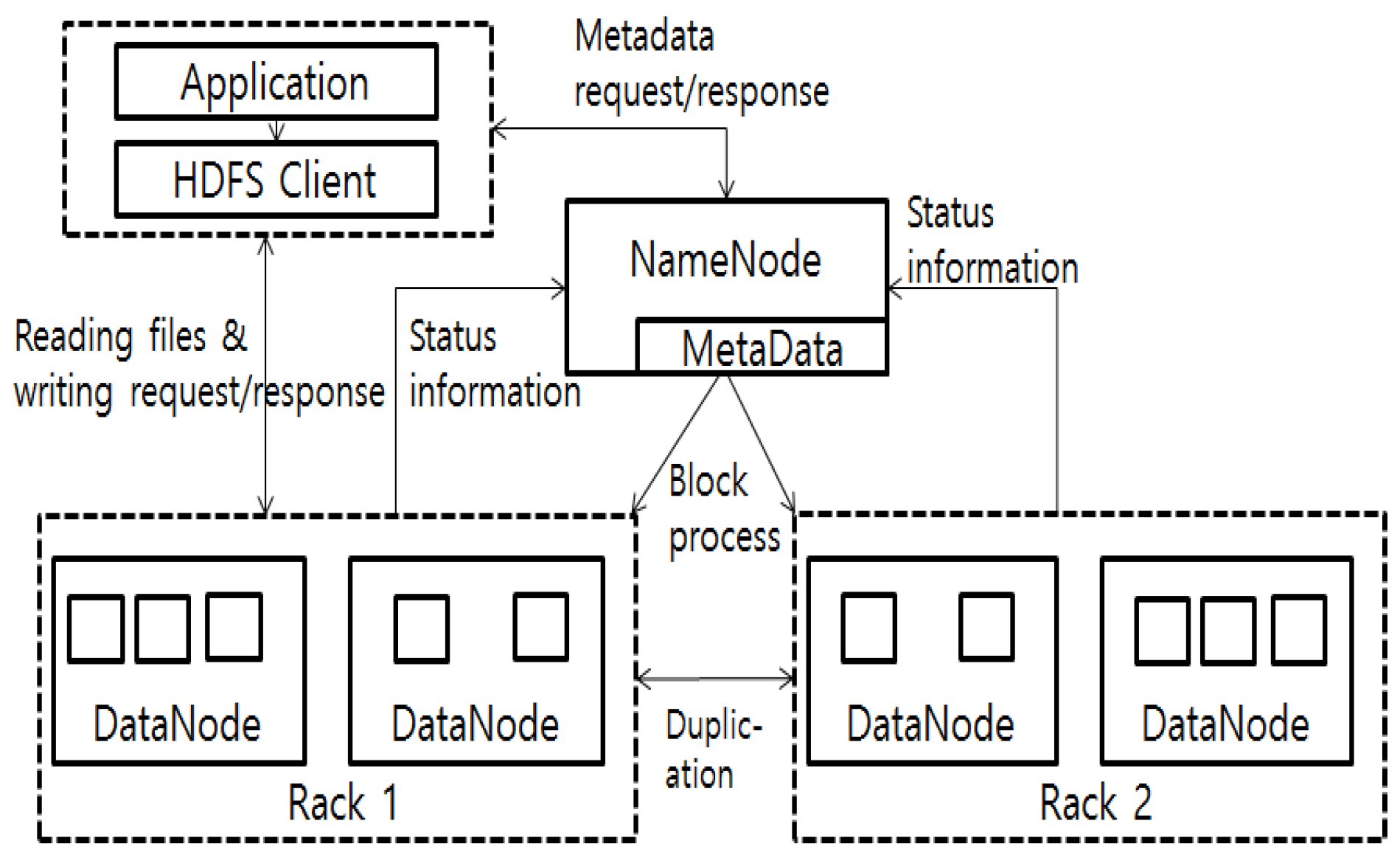
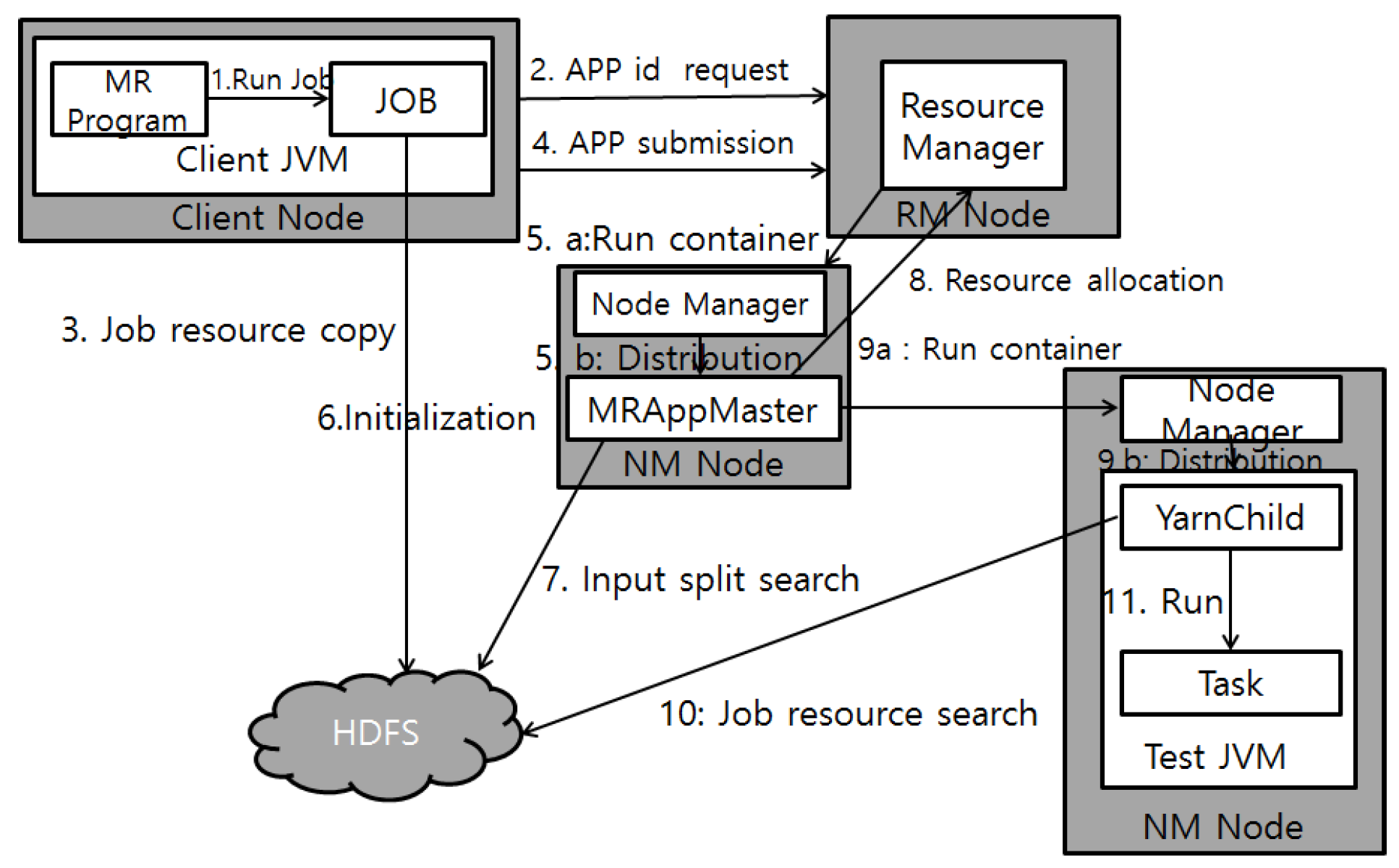
3.3. Apache Hadoop YARN
3.4. The AT-IDS on Hadoop
- Storage: A large amount of data cannot be stored in the current system.
- Speed: When considering a large amount of data and the processing speed of the computer, the processing speeds of at least a supercomputer are necessary.
- Variety: A diverse range of data including images, text, and video need to be processable. Taking into consideration the above three problems, this study proposes a new platform detection system applying Hadoop to the AT-IDS, overcoming the problems through the high-capacity data storage of the Hadoop HDFS and the processing system MR.
4. Scenario Design and Simulation Modeling
4.1. Scenario Design
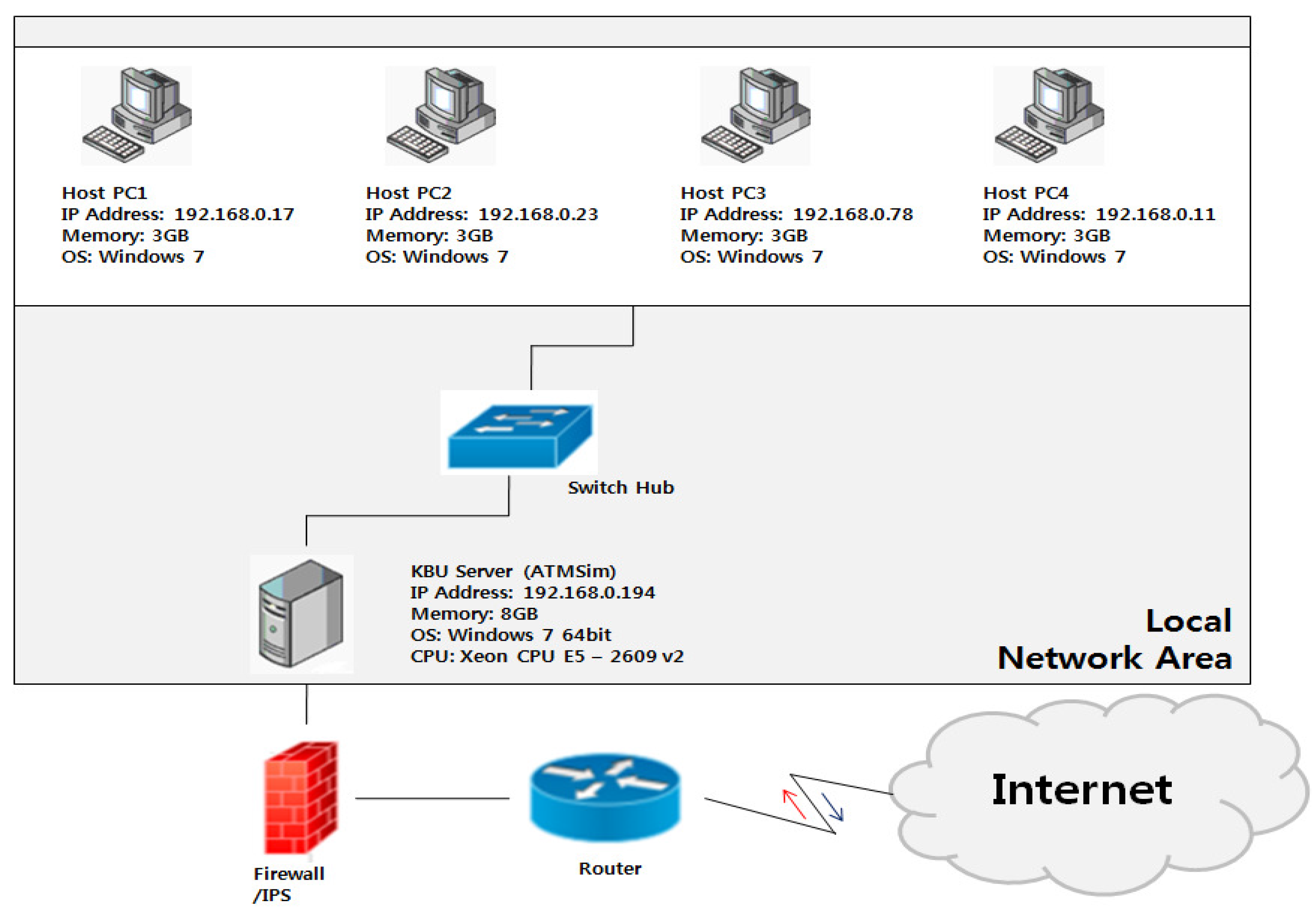
4.2. Simulation Modeling
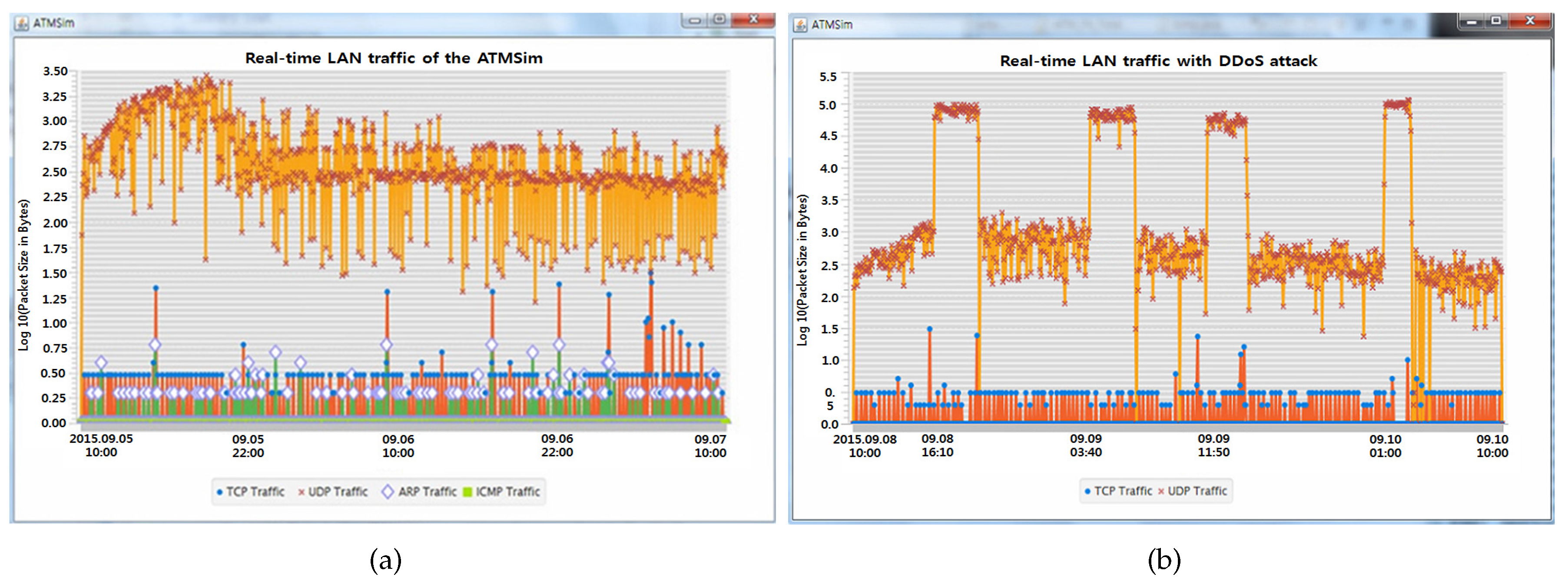
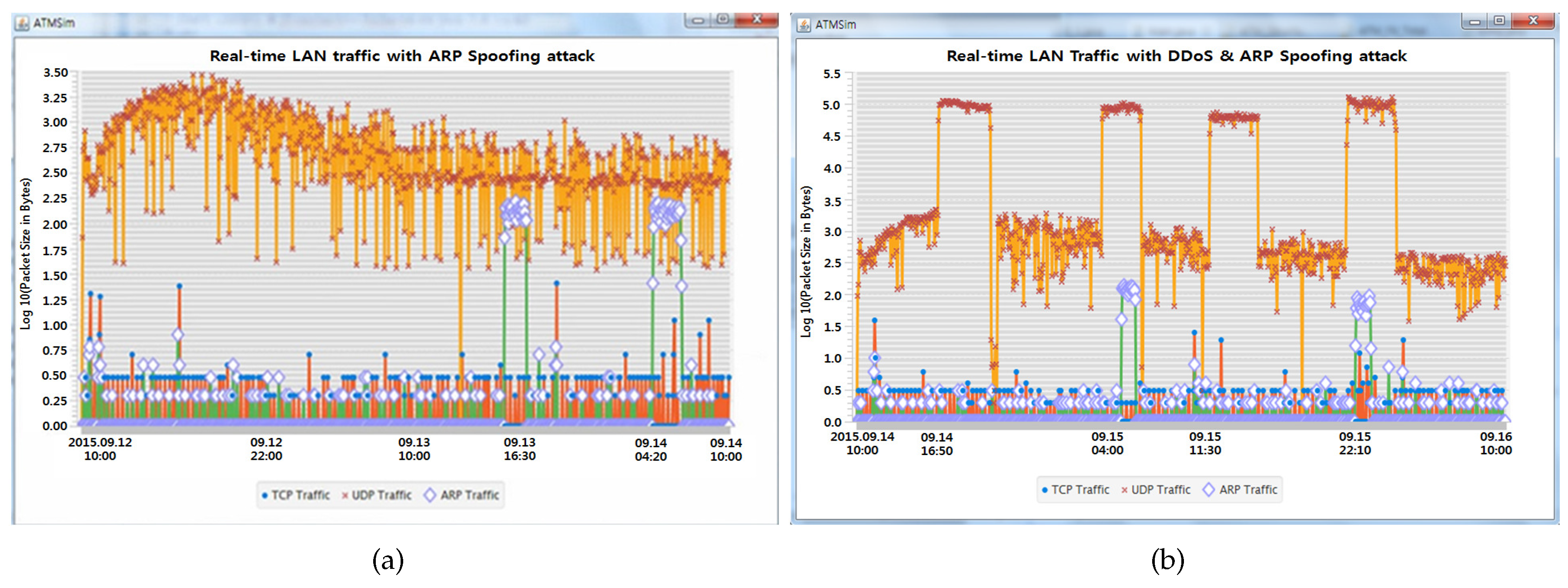
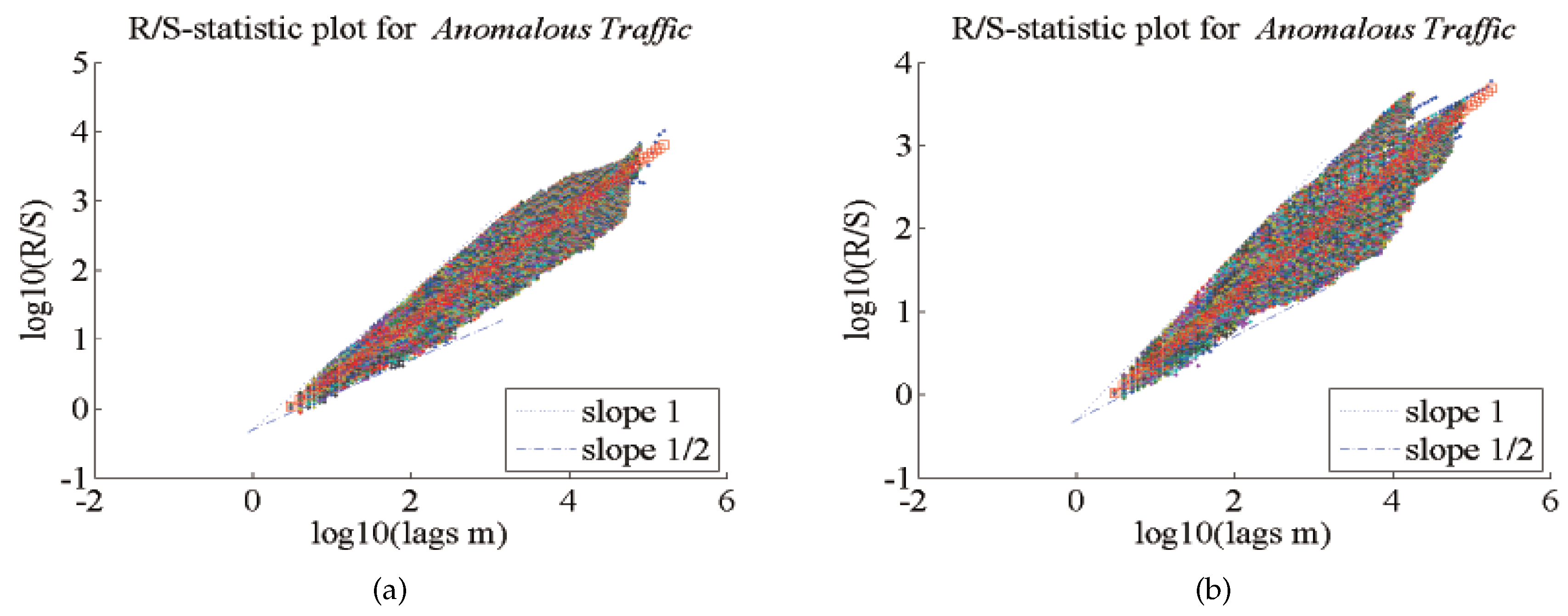
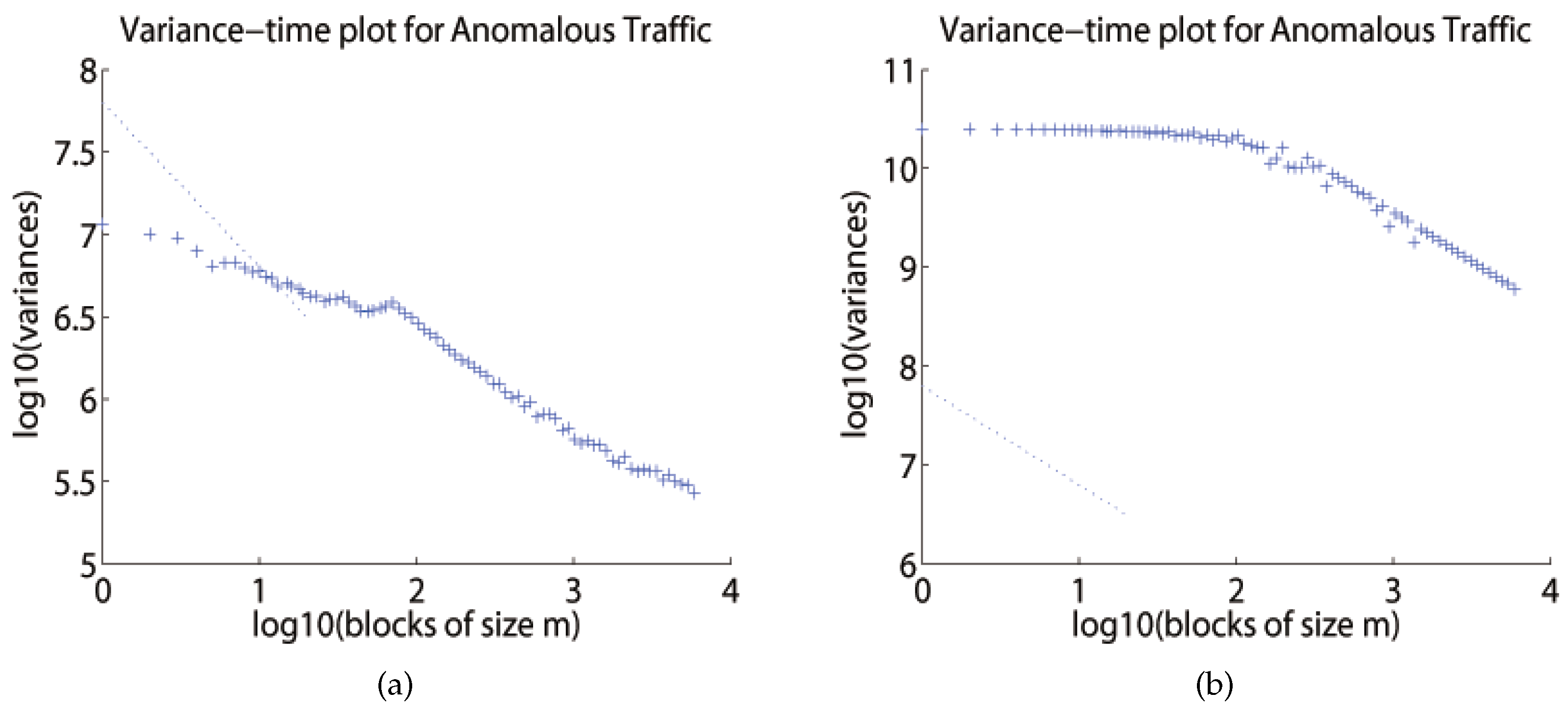
5. Simulation and Result Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| ANN | Artificial Neural Network |
| ARP | Address Resolution Protocol |
| AT-IDS | Anomaly-based Teletraffic Intrusion Detection System |
| ATMSim | Anomaly Teletraffic detection Measurement analysis Simulator |
| DoS | Denial-of-Service |
| DDoS | Distributed Denial-of-Service |
| GFS | Google File System |
| HDFS | Hadoop Distributed File System |
| IDS | Intrusion Detection System |
| IPS | Intrusion Prevention System |
| LAN | Local Area Network |
| MITM | Man-In-The-Middle Attack |
| MR | Map Reduce |
| NIC | Network Interface Card |
| SNS | Social Networking Services |
| ST-IDS | Signature-based Teletraffic Intrusion Detection System |
| TCP | Transmission Control Protocol |
| TCP/IP | Transmission Control Protocol/Internet Protocol |
| UDP | User Datagram Protocol |
References
- Kim, J. A Study on Mitigation Mechanism of DDoS Attacks Utilizing SDN. Master’s Thesis, Department of Information Security, Dongguk University, Seoul, Korea, 2015. [Google Scholar]
- Kim, J. Influence and Response of the Upsurge of Internet Information; Technical Report; Samsung Economic Research Institute: Seoul, Korea, 2007. [Google Scholar]
- Hong, S. An Efficient Prevention Technique Using the Reliable ARP Table for ARP Spoofing Attacks. Master’s Thesis, Department of Computing, Soongsil University, Seoul, Korea, 2011. [Google Scholar]
- Cho, J. A Study of Security Authentication Mechanism for DDoS Attack Prevention in the Internet Environment. Master’s Thesis, Department of Infomation & Communications, Gwangju University, Gwangju, Korea, 2012. [Google Scholar]
- Lee, H. Design of Effective Corresponding Model as a Security Policy Against Attacks of IP Spoofing in Enterprise Networks. Ph.D. Thesis, Department of Computer Science, Gyeongsang National University, Jinju, Korea, 2013. [Google Scholar]
- Choi, J. Education System Design and Implementation of Network Attacks. Ph.D. Thesis, Ewha Womans University Graduate School of Education, Seoul, Korea, 2006. [Google Scholar]
- Ha, D.J. Network-Based Intrusion Detection Firewall. Master’s Thesis, Yeungnam University Graduate School, Gyeongsan, Korea, 2001. [Google Scholar]
- Lee, S. Detection of Bandwidth Exhausting Attacks Using an Improved Prediction Method and its Responding Model. Ph.D. Thesis, Department of Computer Science, Gyeongsang National University, Jinju, Korea, 2015. [Google Scholar]
- Callegari, C.; Coluccia, A.; D’Alconzo, A.; Ellens, W.; Giordano, S.; Mandjes, M.; Pagano, M.; Pepe, T.; Ricciato, F.; Zuraniewski, P. Chapter A Methodological Overview on Anomaly Detection. In Data Traffic Monitoring and Analysis; Lecture Notes in Computer Science; Biersack, E., Callegari, C., Matijasevic, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; Volume 7754, pp. 148–183. [Google Scholar]
- Jeong, H.D.; Kim, H.; Ahn, W.; Oh, J.; Lee, D.; Ye, S.K.; Lee, J.R. Analysis and Detection of Anomalous Network Traffic. In Proceedings of the 2016 10th IEEE International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Fukuoka, Japan, 6–8 July 2016; pp. 403–408. [Google Scholar]
- Lee, J.; Ye, S.K.; Jeong, H.D. ATMSim: An Anomaly Teletraffic Detection Measurement Analysis Simulator. Simul. Model. Pract. Theory 2014, 49, 98–109. [Google Scholar] [CrossRef]
- Li, M. An Approach to Reliably Identifying Signs of DDoS Flood Attacks Based on LRD Traffic Pattern Recognition. Comput. Secur. 2004, 23, 549–558. [Google Scholar] [CrossRef]
- Li, M. Change Trend of Averaged Hurst Parameter of Traffic under DDoS Flood Attacks. Comput. Secur. 2006, 25, 213–220. [Google Scholar] [CrossRef]
- Leland, W.; Taqqu, M.; Willinger, W.; Wilson, D. On the Self-Similar Nature of Ethernet Traffic (Extended Version). IEEE ACM Trans. Netw. 1994, 2, 1–15. [Google Scholar] [CrossRef]
- Park, K.; Willinger, W. Chapter Self-Similar Network Traffic: An Overview. In Self-Similar Network Traffic and Performance Evaluation; Park, K., Willinger, W., Eds.; John Wiley & Sons, Inc.: New York, NY, USA, 2000; pp. 1–38. [Google Scholar]
- Jeong, H.D.; Lee, J.S.; McNickle, D.; Pawlikowski, K. Self-Similar Properties of Malicious Teletraffic. Int. J. Comput. Syst. Sci. Eng. 2012, 28, 1–7. [Google Scholar]
- Jeong, H.D.; Lee, J.S.; McNickle, D.; Pawlikowski, K. Comparison of Various Estimators in Simulated FGN. Simul. Model. Pract. Theory 2007, 15, 1173–1191. [Google Scholar] [CrossRef]
- Leland, W.; Taqqu, M.; Willinger, W.; Wilson, D. On the Self-Similar Nature of Ethernet Traffic. In Proceedings of the ACM SIGCOM’93, San Francisco, CA, USA, 13–17 September 1993; pp. 183–193. [Google Scholar]
- Beran, J. Statistics for Long-Memory Processes; Chapman and Hall: New York, NY, USA, 1994. [Google Scholar]
- Taqqu, M. Self-Similar Processes. In Encyclopedia of Statistical Sciences; Kotz, S., Johnson, N., Eds.; John Wiley and Sons, Inc.: New York, NY, USA, 1988; Volume 8. [Google Scholar]
- Taqqu, M.; Teverovsky, V.; Willinger, W. Estimators for Long-Range Dependence: An Empirical Study. Fractals 1995, 3, 785–788. [Google Scholar] [CrossRef]
- Bae, J. Network Access Control and Management Using ARP Spoofing in Various Windows Environment. Master’s Thesis, Department of Electrical and Computer Engineering, Sungkyunkwan University Graduate School, Suwon, Korea, 2011. [Google Scholar]
- Wagner, R. Address Resolution Protocol Spoofing and Man in-the-Middle Attacks; SANS Institute InfoSec Reading Room: Singapore, 2001. [Google Scholar]
- Lee, J.Y.; Yoon, M.S.; Lee, H. Monitoring and Investigation of DoS Attack. KNOM Rev. 2004, 6, 21–32. [Google Scholar]
- Kaspersky. Lab. Kaspersky DDoS Intelligence Report Q2 2015; Kaspersky: Moscow, Russia, 2015. [Google Scholar]
- Seo, S. Detection and Protection of DoS/DDoS Attacks in WiBro System. Master’s Thesis, School of Engineering, Information and Communications University, Daejeon, Korea, 2009. [Google Scholar]
- Huang, J.; Nicol, D.M.; Campbell, R. Denial-of-Service Threat to Hadoop/YARN Clusters with Multi-tenancy. In Proceedings of the IEEE International Congress on Big Data, Anchorage, AK, USA, 27 June–2 July 2014; pp. 48–55. [Google Scholar]
- Coluccia, A.; D’Alconzo, A.; Ricciato, F. Distribution-based anomaly detection via generalized likelihood ratio test: A general Maximum Entropy approach. Comput. Netw. 2013, 57, 3446–3462. [Google Scholar] [CrossRef]
- Fiadino, P.; D’Alconzo, A.; Schiavone, M.; Casas, P. Challenging Entropy-based Anomaly Detection and Diagnosis in Cellular Networks. In Proceedings of the 2015 ACM Conference on Special Interest Group on Data Communication (SIGCOMM ’15), London, UK, 17–21 August 2015; pp. 87–88. [Google Scholar]
- Karatepe, I.; Zeydan, E. Anomaly Detection in Cellular Network Data Using Big Data Analytics. In Proceedings of the 20th European Wireless Conference, Barcelona, Spain, 14–16 May 2014; pp. 1–5. [Google Scholar]
- Sun, B.; Yu, F.; Wu, K.; Leung, V. Mobility Based Anomaly Detection in Cellular Mobile Networks. In Proceedings of the 3rd ACM Workshop on Wireless Security (WiSe’04), Philadelphia, PA, USA, 1 October 2004; pp. 61–69. [Google Scholar]
- Jeong, H.D.J.; Ryu, M.U.; Ji, M.J.; Cho, Y.B.; Ye, S.K.; Lee, J.S.R. DDoS Attack Analysis Using the Improved ATMSim. J. Internet Comput. Serv. 2016, 17, 19–28. [Google Scholar] [CrossRef]
- Song, M. A study on Detection and Protection for ARP Spoofing Attack based on Routing Trace. Master’s Thesis, Department of Computer Engineering, National University of Science and Technology, Seoul, Korea, 2014. [Google Scholar]
- Ogiela, M.; Ogiela, U. Towards Cognitive Cryptography. J. Internet Serv. Inf. Secur. 2014, 4, 58–63. [Google Scholar]
- Ogiela, M.; Ogiela, U. Bio-inspired Approaches for Secret Data Sharing Techniques. In Proceedings of the Signal Processing, Computer Networks and Telecommunications (ICIIBMS), Okinawa, Japan, 28–30 November 2015; pp. 75–78. [Google Scholar]
- Ogiela, M.; Ogiela, U. Bio-Inspired Cryptographic Techniques in Information Management Applications. In Proceedings of the 2016 IEEE 30th International Conference on Advanced Information Networking and Applications, Crans-Montana, Switzerland, 23–25 March 2016; pp. 1059–1063. [Google Scholar]
- Wang, G.; Hao, J.; Ma, J.; Huang, L. A new approach to intrusion detection using Artificial Neural Networks and fuzzy clustering. Expert Syst. Appl. 2010, 37, 6225–6232. [Google Scholar] [CrossRef]




| Approaches | Techniques | Advantages and Disadvantages |
|---|---|---|
| Statistical-based |
|
|
| Knowledge-based |
|
|
| Machine learning-based |
|
|
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jeong, H.-D.J.; Ahn, W.; Kim, H.; Lee, J.-S.R. Anomalous Traffic Detection and Self-Similarity Analysis in the Environment of ATMSim. Cryptography 2017, 1, 24. https://doi.org/10.3390/cryptography1030024
Jeong H-DJ, Ahn W, Kim H, Lee J-SR. Anomalous Traffic Detection and Self-Similarity Analysis in the Environment of ATMSim. Cryptography. 2017; 1(3):24. https://doi.org/10.3390/cryptography1030024
Chicago/Turabian StyleJeong, Hae-Duck J., WonHwi Ahn, Hyeonggeun Kim, and Jong-Suk R. Lee. 2017. "Anomalous Traffic Detection and Self-Similarity Analysis in the Environment of ATMSim" Cryptography 1, no. 3: 24. https://doi.org/10.3390/cryptography1030024
APA StyleJeong, H.-D. J., Ahn, W., Kim, H., & Lee, J.-S. R. (2017). Anomalous Traffic Detection and Self-Similarity Analysis in the Environment of ATMSim. Cryptography, 1(3), 24. https://doi.org/10.3390/cryptography1030024




