Cyber-Physical Cloud Battery Management Systems: Review of Security Aspects
Abstract
1. Introduction
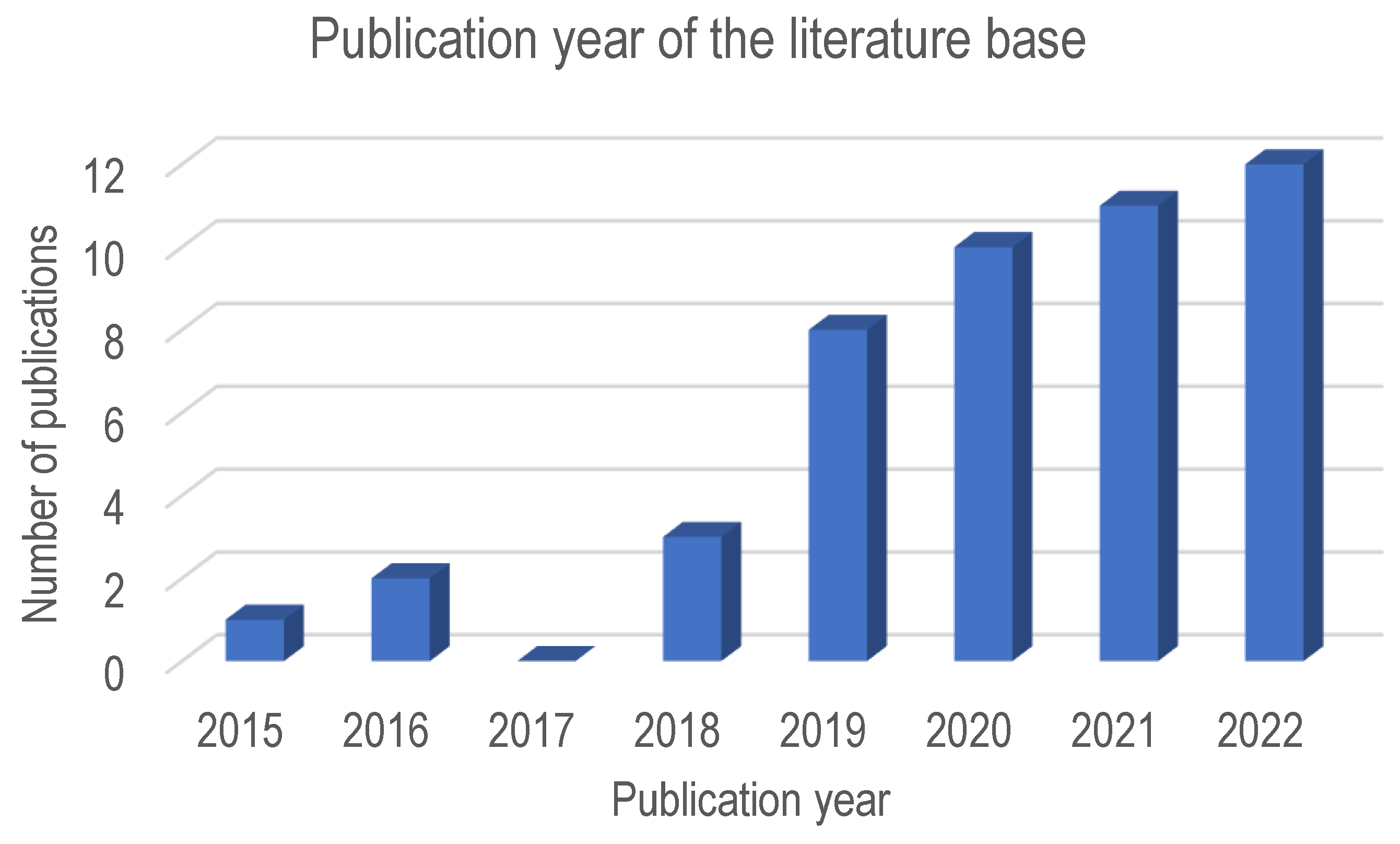
2. Literature Analysis
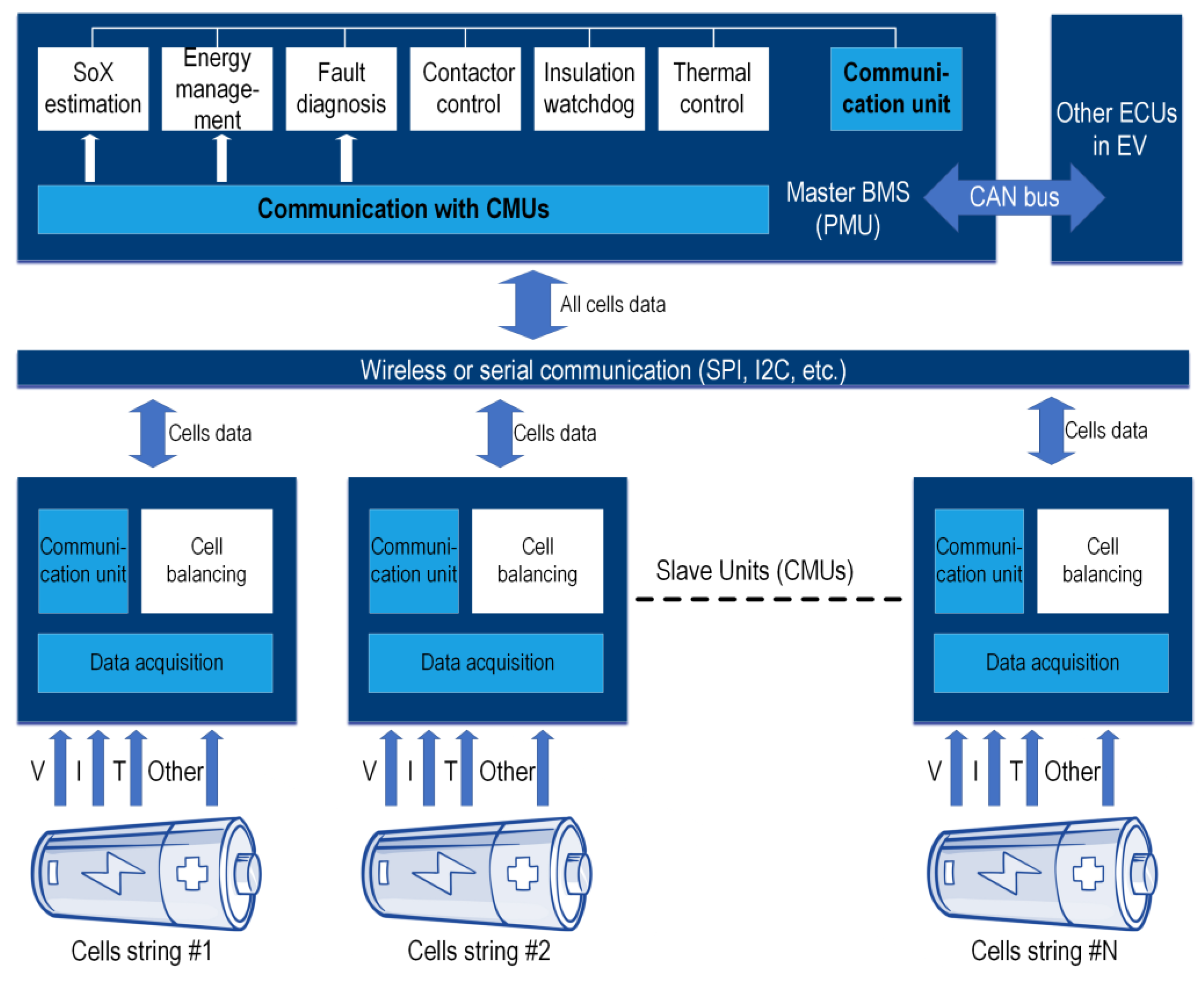
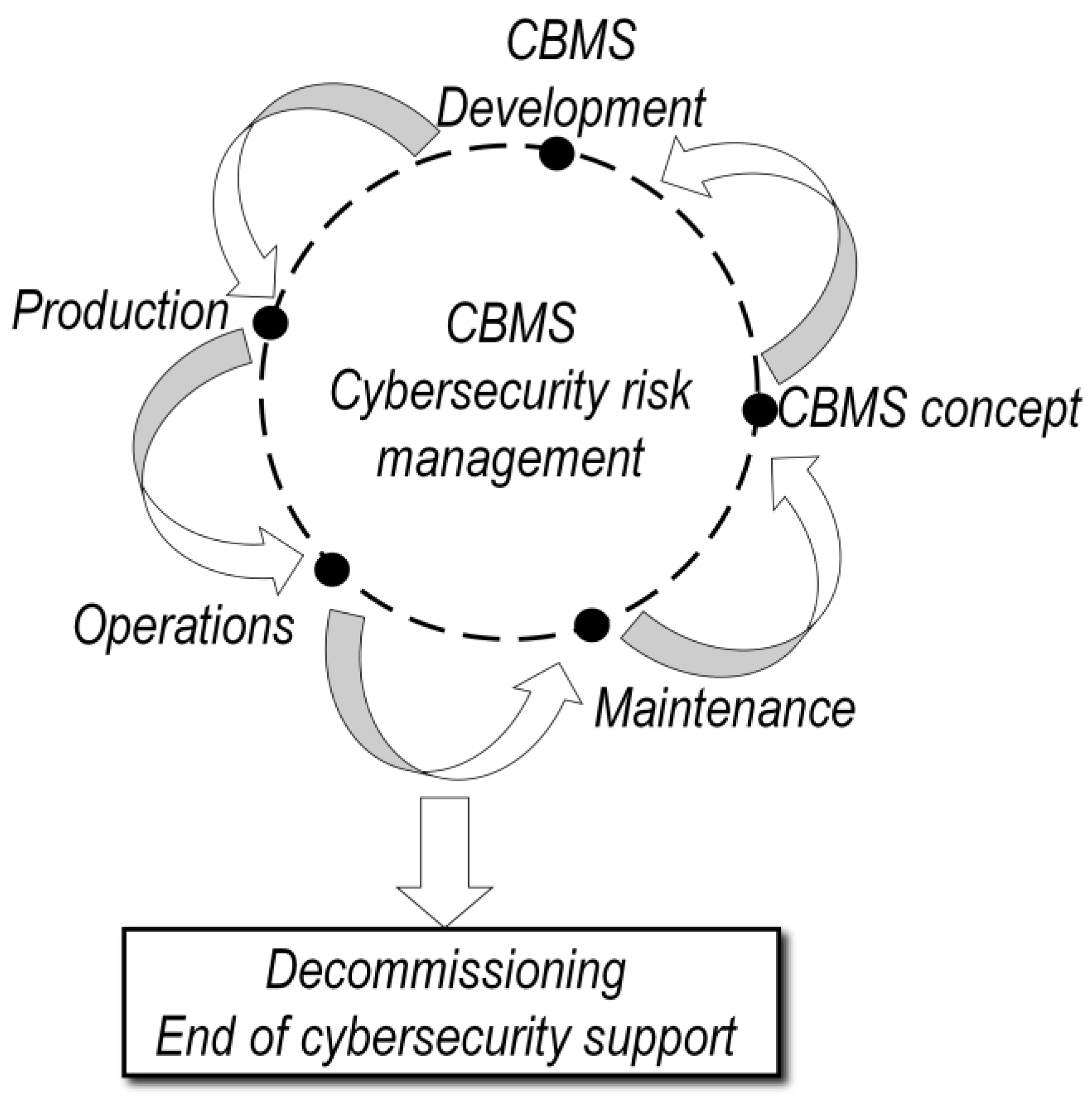
3. BMS versus CBMS: Overview of Characteristics and Architectures
- Ensuring protection and safety: The BMS measures and monitors the key variables related to the battery cells, including current, voltage, and temperature. It is also responsible for maintaining these variables within safe operating limits during charging and discharging. If, for any reason, the battery cannot be controlled within the critical safety limits, the BMS must send a command to the main contactor to shut off the battery pack. The BMS also measures the leakage current from the battery to protect against electrocution in case battery pack isolation is lost [15].
- Battery state estimation and monitoring: The internal states of Li-ion batteries cannot be quantified without any physical sensor. Thus, the BMS integrates algorithms to estimate the SoX parameters related to SoC, SoH, and SoP. The estimation data determine the operational boundaries of the cells such as the usable energy, remaining life, and feasible and safe charge/discharge power limits. Likewise, this information will be communicated to the vehicle’s user interface and/or extended algorithms in the vehicle’s electronic control unit (ECU).
- Controlling the battery: The battery pack is usually equipped with several actuators to control the operation of the battery, e.g., a precharge contactor to mitigate the inrush current drawn from the battery when connected to a charger, two contactors on positive and negative terminals to disconnect and isolate the battery pack in case of failure or maintenance work, MOSFET switches to control the voltage/SoC balancing between cascaded cells, etc. The BMS is responsible for continuously monitoring the battery pack and sending necessary control signals to activate/deactivate the actuators in different operating conditions of the battery.
- Condition monitoring and fault diagnosis: The BMS will continuously monitor the battery for anomalies. The battery anomalies include overvoltage, overcharge, overdischarge, unusual temperature conditions, outgassing, overcurrent, internal or external short-circuits in cells, failures in sensors or communication links that carry on critical cell data, etc.
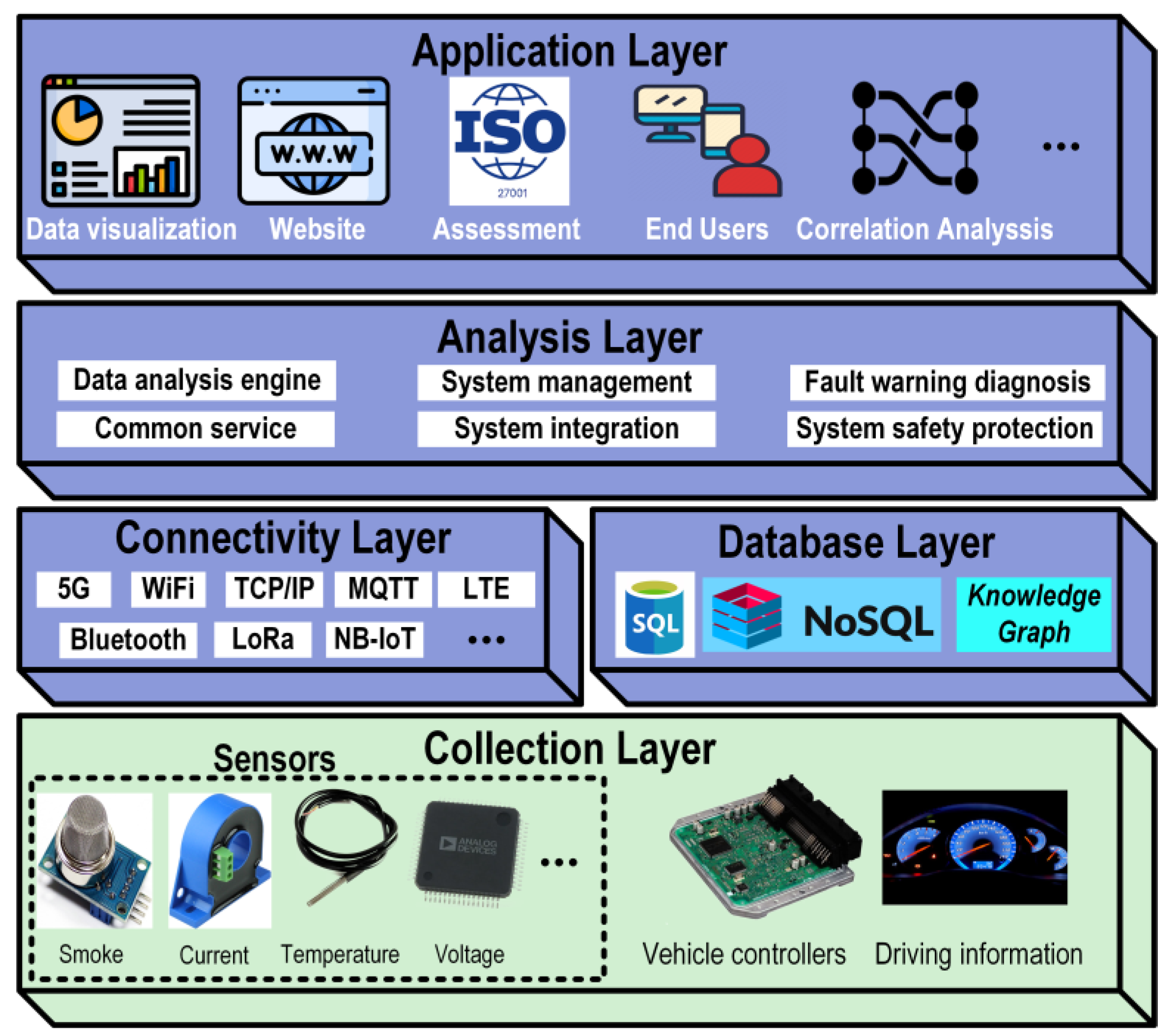
Commercialized Examples of the CBMS Concept
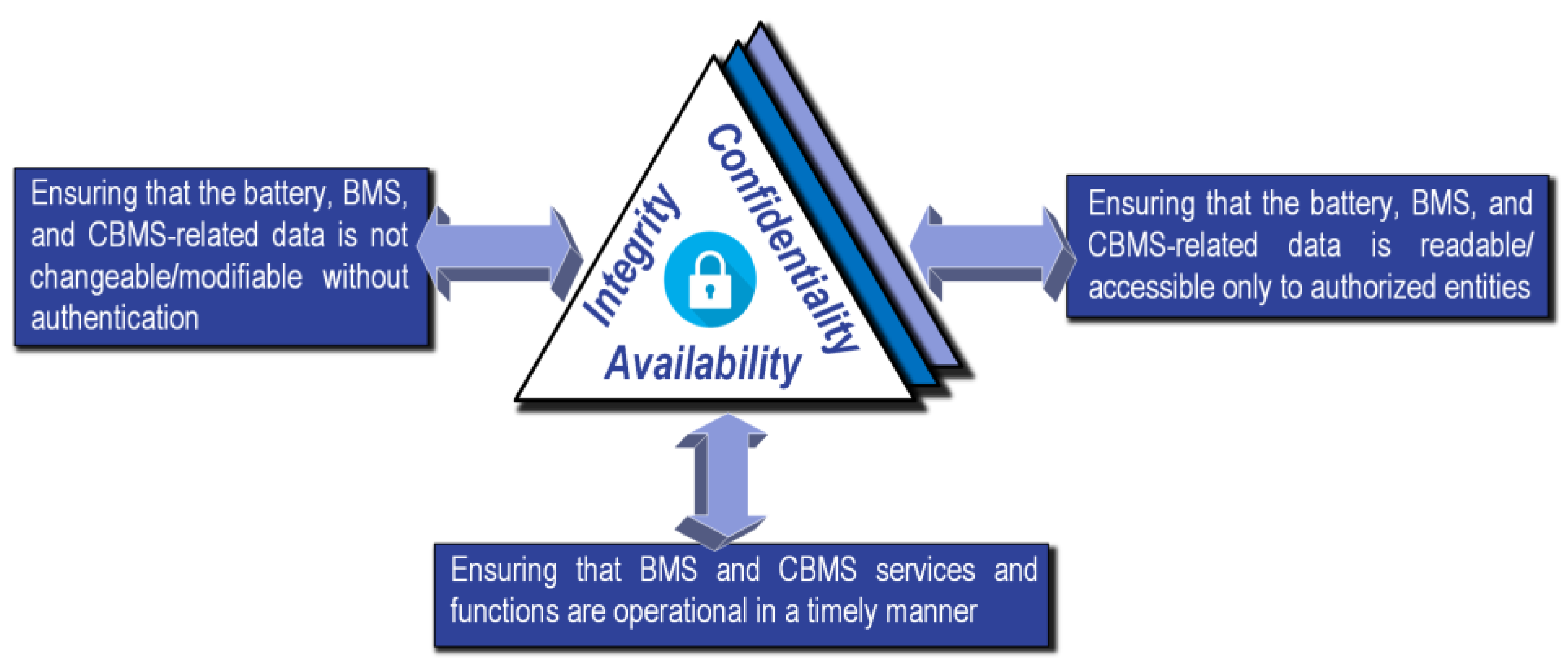
4. Cybersecurity of BMS
4.1. Literature Review on BESS Cybersecurity
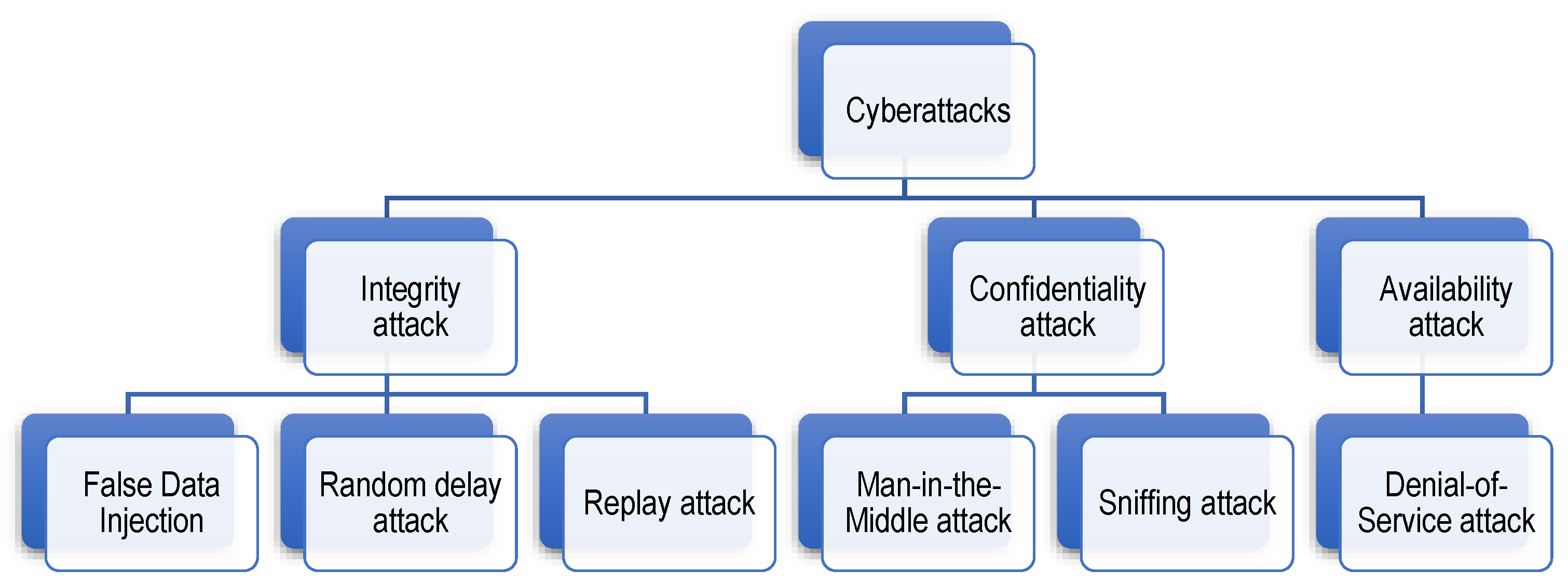
4.2. Attack Types and Scenarios
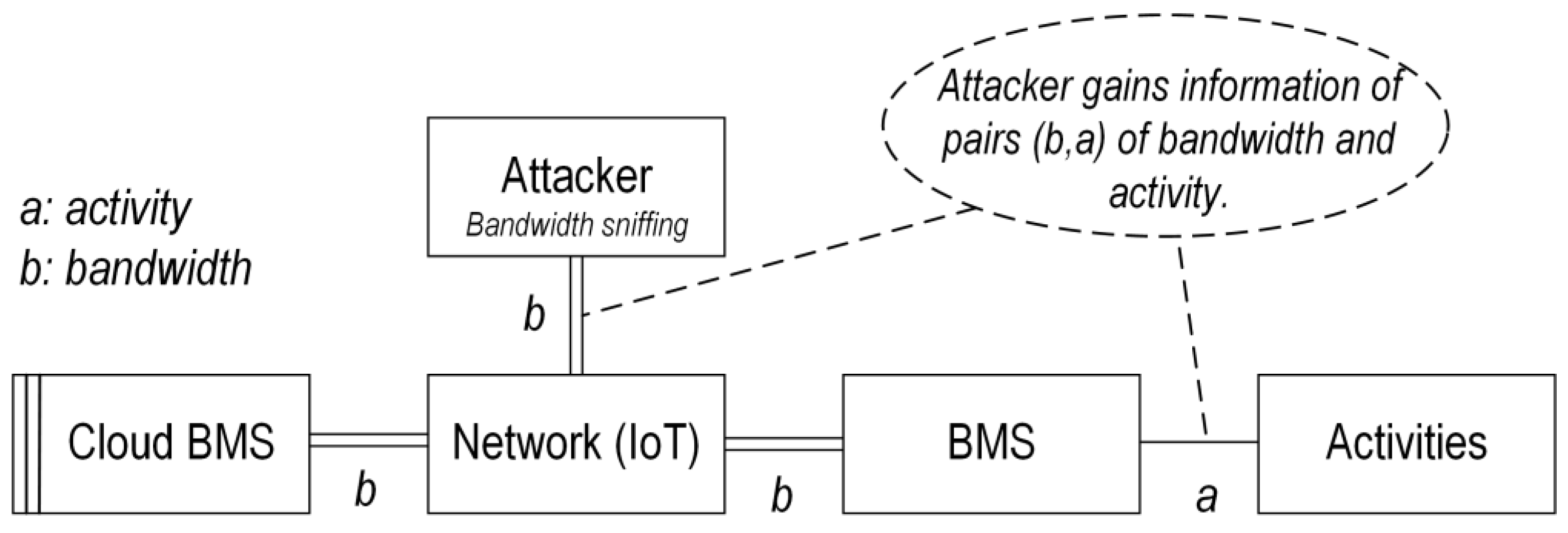
- Confidentiality attacks: The confidentiality attack refers to unauthorized access to the battery/BMS data without directly targeting to damage the system [44]. There are two types of confidentiality attacks: (1) sniffing attack (also known as snooping attack), in which the attacker only can passively listen to the data traffic (in-vehicle through CAN bus or extra-vehicle through IoT communication), and (2) man-in-the-middle (MitM) attack, in which the attacker might also have the possibility to affect the data flow, e.g., via eavesdropping, in which the attacker can relay data between two communication nodes. Regarding sniffing attacks, Ref. [50] illustrates bandwidth sniffing attacks in which the attacker can gain bandwidth information used between the BMS and CBMS to discover some information about BMS, e.g., active components of the BMS and their related activities. The graphical description of the bandwidth sniffing attack is shown in Figure 9. This attack is considered an indirect side-channel attack in which indirect information is used to gain knowledge about the system, with the possible intention to construct and launch more complex attack scenarios [50]. In Figure 9, activities refer to BMS functions or processes.
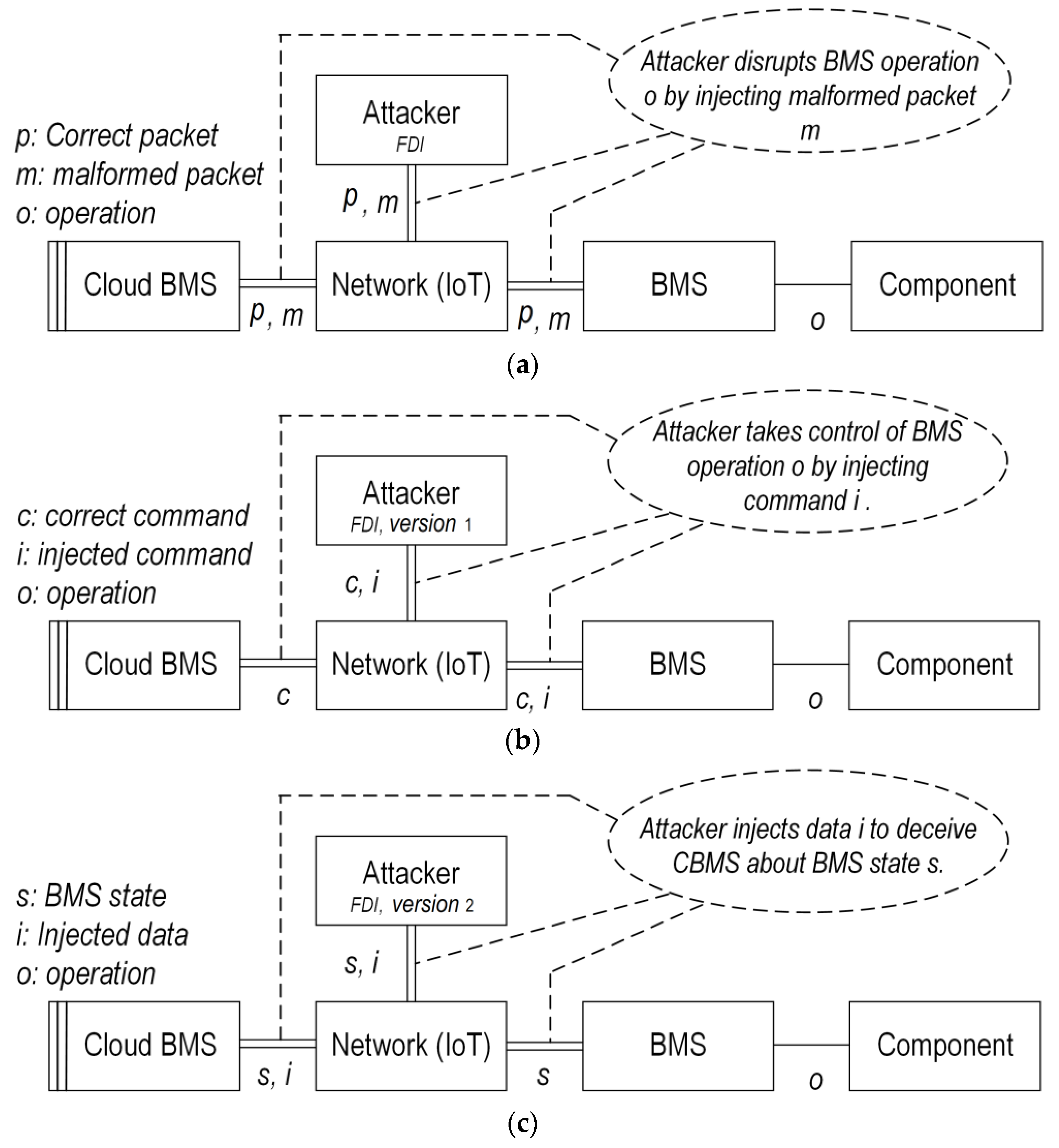
- Integrity attacks: These refer to malicious cyberincidents that lead to the corruption, unauthorized modification, or alteration of the CBMS algorithms/data [37]. Three types of integrity attacks may be considered within the CBMS context: (1) FDI attack refers to deliberate manipulation of the CBMS data such as VIT measurements of cells by injecting false data vectors into the original data. The FDI attacks have a complicated nature and their construction requires some knowledge about the behavior and model of the BESS such that they would normally bypass or circumvent bad data detectors. (2) Random delay attacks are where a random delay will be deliberately introduced to the sequence of BMS control commands or data. (3) Replay attacks occur by wiretapping and repeatedly broadcasting the battery/CBMS measurements/data. Integrity attacks have great potential to compromise EV/pack safety, e.g., to falsify the SoX estimation results, delay the performance of actuators in the battery pack, etc. The graphic illustration of the FDI attack is shown in Figure 10a. Ref [50] presents two different versions of the FDI attack: (1) Injecting control commands to take control of the battery pack; (2) injecting falsified data to deceive the BMS as if the data are originally provided by CBMS, causing troubles for BMS algorithms such as SoX estimation. The two FDI versions are illustrated in Figure 10b,c [50].
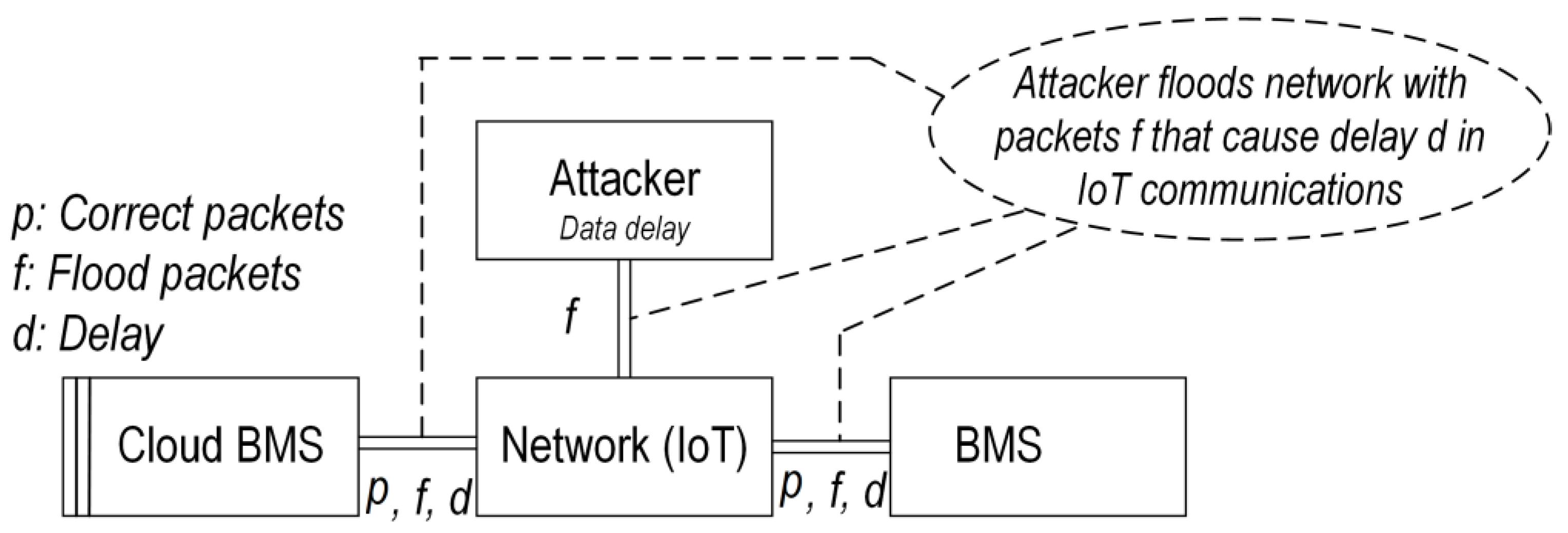
- Availability attacks: Refers to the denial-of-service (DoS), in which the attacker seeks to make the CBMS services unavailable to EVs [52]. DoS can be fulfilled by either flooding the network or crashing the network. Flooding happens when the IoT receives too much information to buffer, which will slow down and eventually stop its services. The most challenging DoS is the distributed DoS (DDoS), in which multiple attackers orchestrate a synchronized DoS attack on CBMS.
4.3. Cyber-Risks and Impacts
- Functional impacts: These occur when a system, component, function, or algorithm in CBMS is no longer functioning correctly due to a malicious cyberattack. For instance, [56] refers to a “denial-of-charging” cyberattack that falsifies the SoC estimation algorithm in BMS to prevent the battery pack from being fully charged. This could lead to prolonged driving due to the lower charge available. Integrity attacks can lead to malfunctioning of BMS algorithms, e.g., causing divergence of SoX estimators, resulting in suboptimal solutions in thermal and energy management, etc.
- Financial and privacy losses: Attacks against BMS sensors or algorithms such as voltage sensors or SoC/SoP estimation algorithms can result in BMS malfunctioning, which in turn can result in accelerated degradation of the battery [57]. For example, falsified SoC data can cause the battery to be operated at very high or very low SoC regions, which will speed up the aging processes of the battery. Falsified SoH data can result in wrong battery maintenance implications, e.g., the battery could either be serviced/maintained too soon when maintenance is not required or too late when the battery has undergone expensive damages. Manipulation of the cooling-related sensors and/or algorithms may result in accelerated aging of the battery. In one case example, the BMS was compromised to turn on the battery heater, draining all the charge [29]. Such scenarios can occur, for example, through false injecting of CAN messages to the EV CAN bus (e.g., through CHAdeMO charger connection). Likewise, critical information can be compromised under cyberattacks, which could lead to loss of privacy, e.g., GPS data, driving profiles, etc. Last, but not least, technology and intellectual property theft can occur by stealing confidential manufacturing data (battery cell data, BMS design data, layouts, etc.) through confidentiality attacks.
- Safety impacts: BMS is usually programmed with hard limits to avoid safety risks, e.g., by comparing cell voltages to the safe voltage limits. However, such limits might be overridden under malicious BMS firmware updates, which may result in battery overcharge and/or overdischarge. Small overcharge will result in accelerated aging of the battery, while overcharge in the scale of minutes might cause more serious risks such as internal short-circuits and thermal runaways [57]. Cooling system performance may also be interpreted through cyberattacks against thermal management systems, leading to the thermal runaway risk. Thus, it is important to devise efficient failsafes (e.g., mechanical override design features) to disconnect the battery in such cases [58]. Poor estimation of SoX data might also result in conditions that compromise the safety, e.g., leading to lower maneuverability of the EV on the road or misleading drivers about the achievable EV performance such as acceleration, etc. There is also a safety risk when the battery pack is disconnected, or its performance is limited due to a cyberattack while the EV is in driving mode.
- Side impacts: The CBMS large databases can be used to develop battery models and algorithms for other lifecycle stages such as second-life battery applications. Attacks against the CBMS database can result in data poisoning and data corruption and this will further affect the battery and BMS designs that are fulfilled based on these corrupted datasets.
4.4. CBMS Attack Detection Methods and Mitigation Strategies
4.5. Methods for Enhancing the Cybersecurity of the BMS/CBMS
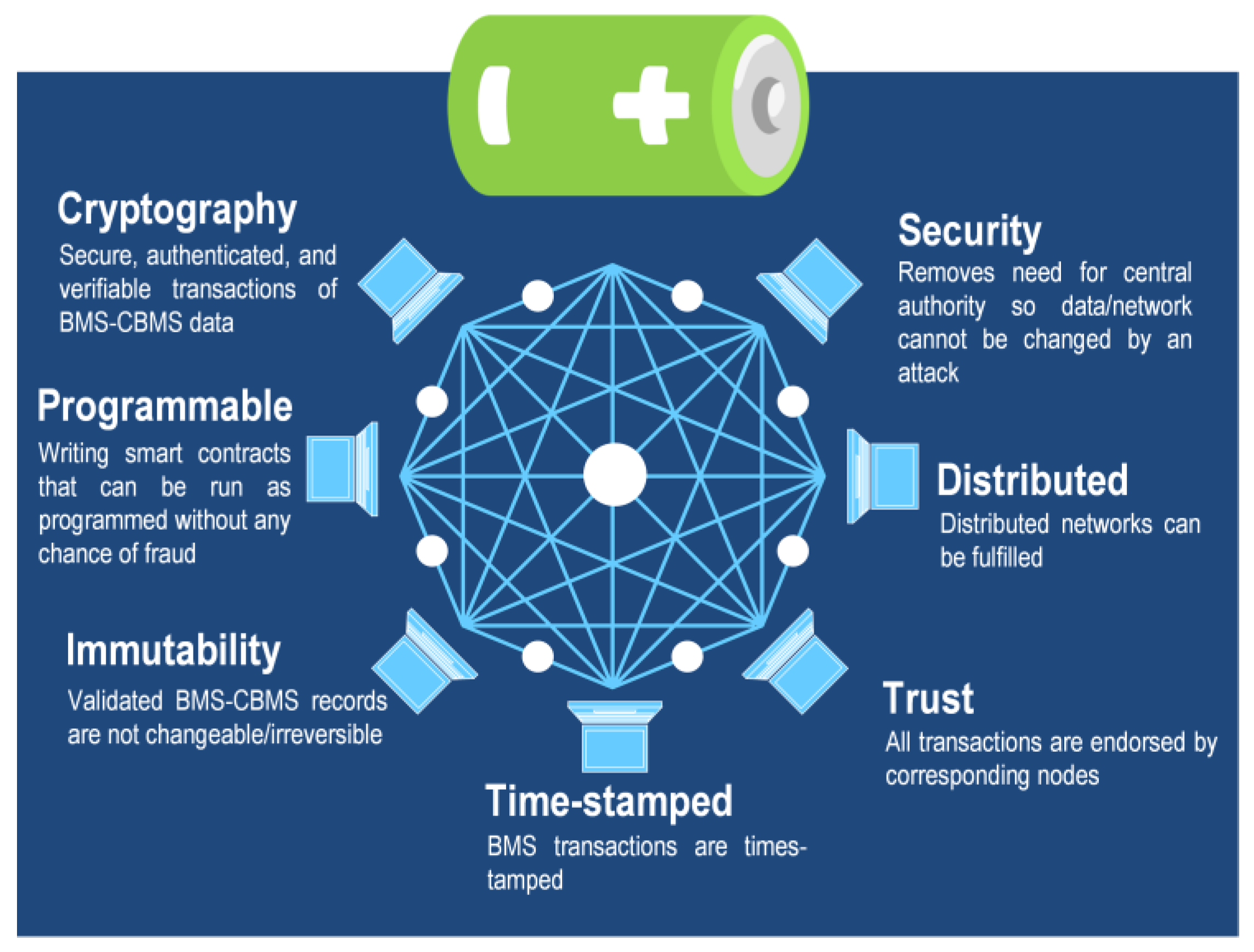
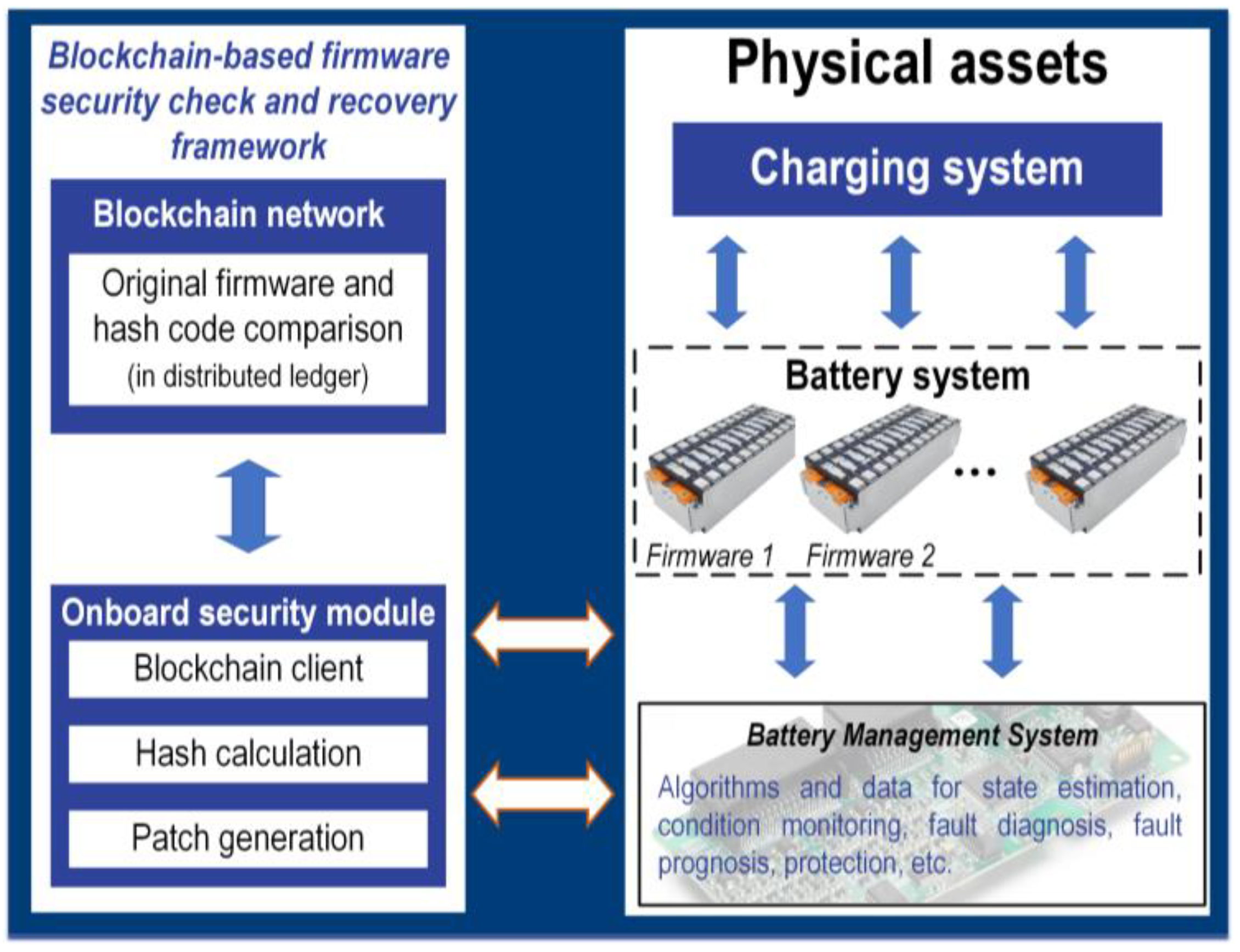
- Blockchain technology: Blockchain is a secure distributed database for maintaining constantly growing data records. It was initially developed to secure cryptocurrency transactions, but lately, it has been explored for new cloud applications including CBMSs. Concerning the CBMSs, it has been discussed that the blockchain can be used to enhance both software and hardware aspects [68]. For instance, the blockchain can be used to manage critical activities related to the transaction and sharing of battery data between the CBMS and the BMS terminal nodes [52]. The blockchain transactions are time-stamped, cryptic, and immutable, meaning that the data cannot be read or modified from single communication nodes. Furthermore, transactions will be endorsed by corresponding nodes so the authenticity of the communication nodes and data can be validated. Likewise, the distributed/decentralized nature of the blockchain significantly lowers the cybersecurity risk in case of successful attacks on one or more communication nodes. Key features of blockchain technology are described in Figure 12 [73].
- Resilient software design: Design-for-cybersecurity (DFC) can be used to enhance the robustness of the CBMS software against cyberthreats. An example of DFC is the design of robust and resilient state estimation algorithms that are capable of detecting and/or neutralizing cyberattacks and their effects. Several CPS-based applications have reported the use of secure algorithms such as secure state estimators to protect against cyberattacks. For example, Refs. [78,79] designed a secure Kalman filter (KF)-based algorithm for dynamic state estimation in energy grids. The algorithm was designed to detect the onset of an FDI attack and the location (specific communication nodes) where the attack was launched. Thus, with the resilient algorithm, the state estimations will recover to the true state estimates even though the measurements are manipulated. Another example was presented in [80], where a resilient algorithm was designed for finite-time secure state estimation in a centrifugal pump to protect it against sensor attacks. A resilient SOC estimation algorithm based on artificial neural networks (ANNs) was proposed in [30]. The algorithm was designed to neutralize the effect of cyberattacks on the battery data so the SOC estimations remain valid under attack conditions. Such techniques can be used to develop secure algorithms, for example, secure SoX estimation algorithms or cyberattack detection algorithms with the ability to discriminate between a failure (such as a sensor failure of cell failure) and a cyberattack. In this context, Ref. [44] highlighted the ability of AI-based data-driven methods in sensor measurement forecast (pseudo-measurement generation), which will offer redundancy for when the sensors are attacked. Similarly, Ref. [81] provided a few recommendations to enhance IoT-related security, e.g., through secure coding, formatting the source codes as libraries, executables, and obfuscation codes, which will prevent source code changes due to cyberattacks. As argued in [81], secure coding may refer to designing secure CBMS software together with a rule-checker for secure coding and an incorporated weakness analyzer. BMS software updates should also be performed securely. In this regard, researchers have suggested code-signing firmware updates [82]. The security of BMS source codes should also take into account reliable libraries throughout the source code [83].
- Cross-verification of BMS and CBMS: One potential solution to ensure the credibility of the CBMS algorithmic results such as SOX estimation results could be to perform the related calculations in different ways on both BMS and CBMS. The results obtained on the onboard BMS can then be used to cross-verify the accuracy of the CBMS algorithms and their robustness [28]. A great mismatch between the results of the onboard BMS and the CBMS potentially indicates an unusual situation such as a cyberattack launched against CBMS or IoT communication links.
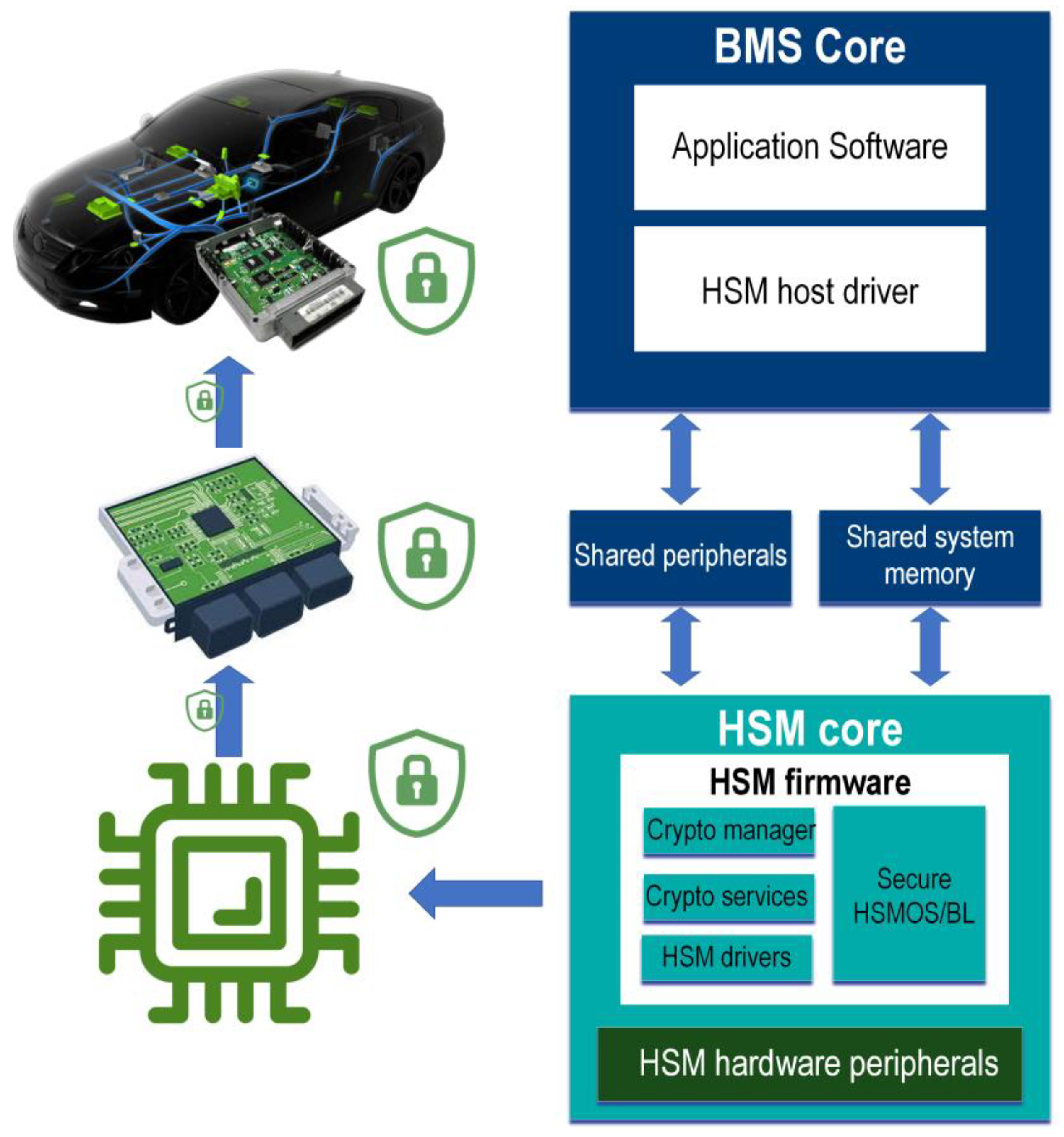
- Hardware Security Modules (HSMs): CPUs with security stacks and embedded HSMs are the nuclei of vehicle cybersecurity. They are used to protect safety-critical vehicle tasks such as the functioning of airbags, steering, and braking systems. Similarly, BMS processors can be protected against cyberthreats through the use of HSMs [84]. The basic architecture of an HSM is depicted in Figure 14. As shown, the HSM can be connected to the BMS microprocessor as separate hardware, which includes an individual processor, cryptographic functions, and dedicated memory to support hardware security firmware [84]. The BMS enhanced by HSM can perform autonomous authenticity and integrity checks, for example, when a software update is to be installed, for secure in-vehicle communications through the CAN bus, and in case of extra-vehicle communications to the IoT and CBMS. Reference [84] also suggested a procedure for the determination of the ASILs by including the cybersecurity risks in the functional safety analysis. Accordingly, it pinpoints the importance of end-to-end (E2E) protection for the exchange of critical data to ensure an ASIL D requirement, e.g., for data that are linked to the braking signals, steering angle, battery pack safety, etc.
- Encryption: Encryption refers to the process of encoding BMS/CBMS software data/information to prevent unauthorized access and/or data alternation [85]. Encryption can help ensure that sensitive battery/BMS data is kept confidential and that only authorized assets have access to the data. Internal communications, such as communication from slave boards to master BMS or vehicle CAN communication, as well as IoT communications from BMS to the CBMS and vice versa, can be effectively protected using cryptographic protocols such as TLS [81]. For example, end-to-end encryption based on NISTIR guidance on cryptography and key management has been suggested to assure the integrity and confidentiality of battery data [86,87]. Likewise, to protect against MitM cyberattacks, additional end-point security protocols (such as IEC 62351-7) and role-based access control (RBAC) based on IEC 62351-8 can be considered [88]. Regarding different battery data stored on CBMS, database encryption is an effective solution to prevent data stealth. Database encryption transfers different battery data (state data, link data, metadata, etc.) into cipher text which cannot be comprehended by unauthorized users (e.g., by attackers). Examples of database encryption methods are the hashing technique, SHA256 encryption, etc. [81]. In this regard, the National Renewable Energy Laboratory (NREL) also highlights the effectiveness of encryption in protecting both data-at-rest (data stored on BMS and/or CBMS) and data-in-flight (battery transactions real-time data) [58]. Despite being a powerful solution, encryption has some weaknesses. Encryption requires key management to encrypt and decrypt data or codes, and if the key is stolen, intercepted, or compromised, the data encryption can be broken. To ensure key security, Ref. [89] suggested a pluggable key management device with a key management protocol and integrated formal analysis to assure security compliance. It is also noteworthy that encryption protocols and algorithms are somehow susceptible to vulnerabilities such as side-channel attacks. Moreover, encryption is useless in the case of specific attack types against CBMS such as random delay attacks.
- User authentication and access control [90,91]: User authentication provides an additional layer of security against unauthorized access to the battery, CBMS, and related data. Multifactor authentication or passwords can be used when accessing the battery database on the cloud, CAN bus through the OBD port, before performing maintenance, or when configuration/reconfiguration of the BMS or CBMS software is planned. Adopting ISO 15118 multimodal and multipass authentication processes was suggested in [92]. Likewise, in the case of adopting the MQTT protocol for IoT communications, Ref. [81] suggested that access to the broker should be restricted by deploying authentication keys on both sides including the clients and broker. In this context, Ref. [81] recommended using proper tools for checking the login history to track unauthorized access attempts.
5. Existing Regulations and Standards
6. Potential Future Research Domains
- ▪
- TARA analysis and definition of ACILs: A detailed TARA analysis needs to be fulfilled to understand different cyberthreats and their influence on the CBMS performances and the associated risks to EVs’ functional safety. Such analysis will further help to quantify the ACILs required for CBMS cybersecurity design procedures, as suggested in SAE J3061. This review reviewed and addressed the potential threats to some extent. However, their link to ACILs is yet to be established in future works. New BMS architectures and topologies are being proposed and it is important to identify new vulnerabilities associated with them. For example, the effect of EMI attacks on wireless BMSs can be further explored.
- ▪
- Cybersecurity analysis, test, and validation platforms: The cybersecurity of BMS is a recent topic and there is still a lack of modeling and simulation tools that can be used to analyze, test, and validate cybersecurity designs. As an example of such cybersecurity test setups, one can refer to the open-source platform named CEE developed by NREL, which is capable of emulating both physical land network aspects (including OCPP or Open Charge Point Protocol) of EVSEs [36]. The platform was successfully used to emulate different attack scenarios such as DOS and MitM attacks. Further research is required to develop more flexible platforms to enable the assessment of a broader range of use cases.
- ▪
- Algorithm design: New efficient algorithms should be designed to reinforce CBMS cybersecurity. This involves the design of secure and resilient algorithms that are robust against cyberattacks, such as manipulated data. Likewise, detection algorithms should be designed and integrated into the CBMS to enable the detection of cyberattacks. Discussions regarding how the CBMS should respond to such attacks (in terms of battery control and prioritization of signals from the cloud) also need further exploration. The algorithm design should also take into account the possibility of system faults and preferably be capable of distinguishing between attack conditions and failure conditions (e.g., failures in sensors, etc.).
- ▪
- Cybersecurity in second life: CBMS cybersecurity should further be explored in different lifecycle stages, including when moving EV batteries from first-life to second-life. In this context, future work can focus, for example, on how to pass on battery-related data from one stage of life to another in a secure manner. Research should be fulfilled to determine which data, when, and how it should be transferred while ensuring the cybersecurity requirements.
- A systematic review of individual topics: This paper is a scoping review where various topics related to CBMS cybersecurity are discussed. In the future, full systematic reviews can be carried out to analyze each aspect in more depth. For instance, some topics such as cyberattack detection methods, etc., require a dedicated review study.
- Standardization: The standards review fulfilled in Section 5 showed that no standards exist to address the design requirements of the BMS, CBMS, and their cybersecurity requirements. However, as reviewed, many useful tools and frameworks are proposed for automotive cybersecurity, including SAE J3061 and ISO 21434. Such tools can be used to further analyze cybersecurity in the CBMS context and develop new requirements and/or tailor the existing requirements for the DFC.
- Artificial Intelligence for BMS Cybersecurity: AI can be used to process vast amounts of battery data to establish baseline behavioral patterns and use them to continuously monitor the CBMS concerning cyberattacks. AI can also leverage threat intelligence feeds, security databases, and historical cyberattack data to identify potential vulnerabilities and predict emerging threats against the CBMS. Last, but not least, AI-powered incident response systems can be used to automate the identification, containment, and remediation of cyberattacks, minimizing the impacts on the CBMS, battery, and EV/grid operations.
- Implementation: Research can also be focused to address the implementation challenges of the CBMSs, e.g., establishment of proper communication tools and protocols (with sufficient bandwidth and acceptable data transmission delay) to support a sustainable, smooth, and secure two-way transmission of data between physical and digital BMSs. Likewise, the design of CBMS architecture can be enhanced to address the flexibility, modularity, scalability, and cybersecurity of the cloud platform.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Nomenclature
| Acronym | Definition |
| ACIL | Automotive Cybersecurity Integration Level |
| AI | Artificial Intelligence |
| ANN | Artificial Neural Network |
| ASIL | Automotive Safety Integrated Level |
| BaaS | Blockchain-as-a-Service |
| BESS | Battery Energy Storage System |
| BMS | Battery Management System |
| CAN | Controller Area Network |
| CBMS | Cloud BMS |
| CCS | Combined Charging System |
| CEBS | Cloud-Enabled Battery Solution |
| CIA | Confidentiality, Integrity, Availability |
| CMU | Cell Monitoring Unit |
| CPS | Cyber-Physical System |
| DDoS | Distributed Denial-of-Service |
| DFC | Design-for-Cybersecurity |
| DoS | Denial-of-Service |
| E2E | End-to-End |
| ECM | Equivalent Circuit Model |
| ECU | Electronic Control Unit |
| EMI | Electromagnetic Interference |
| EV | Electric Vehicle |
| EVSE | Electric Vehicle Supply Equipment |
| FDI | False Data Injection |
| FPGA | Field Programmable Gate Array |
| FSDD | False Sensor Data Detection |
| GDPR | General Data Protection Regulation |
| GPS | Global Positioning System |
| HARA | Hazard Analysis and Risk Assessment |
| HTTP | Hyper Text Transport Protocol |
| IoT | Internet of Things |
| Li-on | Lithium-ion |
| MitM | Man-in-the-Middle |
| ML | Machine Learning |
| MOSFET | Metal Oxide Semiconductor Field Effect Transistor |
| MQTT | Message Queuing Telemetry Transport |
| OBC | Onboard Charger |
| OBD | Onboard Diagnostics |
| OEM | Original Equipment Manufacturer |
| PMU | Pack Monitoring Unit |
| SoC | State-of-Charge |
| SoH | State-of-Health |
| SoP | State-of-Power |
| SoX | State-of-X |
| TARA | Threat Analysis and Risk Assessment |
| TLS | Transport Layer Security |
| TRL | Technology Readiness Level |
| UBMC | Universal Battery Management Cloud |
| V2C | Vehicle-to-Cloud |
| V2E | Vehicle-to-Everything |
| V2G | Vehicle-to-Grid |
| V2I | Vehicle-to-Infrastructure |
| V2P | Vehicle-to-Pedestrian |
| V2V | Vehicle-to-Vehicle |
| V2X | Vehicle-to-X |
| VIT | Voltage, Current, Temperature |
| WPTM | Wireless Power Transfer Module |
References
- Zhou, L.; Lai, X.; Li, B.; Yao, Y.; Yuan, M.; Weng, J.; Zheng, Y. State Estimation Models of Lithium-Ion Batteries for Battery Management System: Status, Challenges, and Future Trends. Batteries 2023, 9, 131. [Google Scholar] [CrossRef]
- Habib, A.A.; Hasan, M.K.; Issa, G.F.; Singh, D.; Islam, S.; Ghazal, T.M. Lithium-Ion Battery Management System for Electric Vehicles: Constraints, Challenges, and Recommendations. Batteries 2023, 9, 152. [Google Scholar] [CrossRef]
- Gandoman, F.H.; El-Shahat, A.; Alaas, Z.M.; Ali, Z.M.; Berecibar, M.; Abdel Aleem, S.H. Understanding Voltage Behavior of Lithium-Ion Batteries in Electric Vehicles Applications. Batteries 2022, 8, 130. [Google Scholar] [CrossRef]
- Naseri, F.; Gil, S.; Barbu, C.; Cetkin, E.; Yarimca, G.; Jensen, A.; Larsen, P.; Gomes, C. Digital twin of electric vehicle battery systems: Comprehensive review of the use cases, requirements, and platforms. Renew. Sustain. Energy Rev. 2023, 179, 113280. [Google Scholar] [CrossRef]
- Naseri, F.; Barbu, C.; Sarikurt, T. Optimal sizing of hybrid high-energy/high-power battery energy storage systems to improve battery cycle life and charging power in electric vehicle applications. J. Energy Storage 2022, 55, 105768. [Google Scholar] [CrossRef]
- Naseri, F.; Schaltz, E.; Stroe, D.-I.; Gismero, A.; Farjah, E. An enhanced equivalent circuit model with real-time parameter identification for battery state-of-charge estimation. IEEE Trans. Ind. Electron. 2021, 69, 3743–3751. [Google Scholar] [CrossRef]
- Naseri, F.; Karimi, S.; Farjah, E.; Schaltz, E. Supercapacitor management system: A comprehensive review of modeling, estimation, balancing, and protection techniques. Renew. Sustain. Energy Rev. 2022, 155, 111913. [Google Scholar] [CrossRef]
- Xing, Y.; Ma, E.W.; Tsui, K.L.; Pecht, M. Battery management systems in electric and hybrid vehicles. Energies 2011, 4, 1840–1857. [Google Scholar] [CrossRef]
- Wang, Y.; Tian, J.; Sun, Z.; Wang, L.; Xu, R.; Li, M.; Chen, Z. A comprehensive review of battery modeling and state estimation approaches for advanced battery management systems. Renew. Sustain. Energy Rev. 2020, 131, 110015. [Google Scholar] [CrossRef]
- Crawford, A.J.; Choi, D.; Balducci, P.J.; Subramanian, V.R.; Viswanathan, V.V. Lithium-ion battery physics and statistics-based state of health model. J. Power Sources 2021, 501, 230032. [Google Scholar] [CrossRef]
- Li, W.; Rentemeister, M.; Badeda, J.; Jöst, D.; Schulte, D.; Sauer, D.U. Digital twin for battery systems: Cloud battery management system with online state-of-charge and state-of-health estimation. J. Energy Storage 2020, 30, 101557. [Google Scholar] [CrossRef]
- ISO 26262-1:2018. Road Vehicles—Functional Safety. 2018. Available online: https://www.iso.org/standard/68383.html (accessed on 21 May 2023).
- Xu, J.; Li, S.; Mi, C.; Chen, Z.; Cao, B. SOC based battery cell balancing with a novel topology and reduced component count. Energies 2013, 6, 2726–2740. [Google Scholar] [CrossRef]
- Gocmen, S.; Cetkin, E. Experimental investigation of air cooling with/out tab cooling in cell and module levels for thermal uniformity in battery packs. ASME J. Heat Mass Transf. 2023, 145, 022903. [Google Scholar] [CrossRef]
- Piao, C.H.; Cong, T. Study on isolation monitoring of high-voltage battery system. Appl. Mech. Mater. 2011, 44, 571–575. [Google Scholar] [CrossRef]
- Samanta, A.; Williamson, S.S. A survey of wireless battery management system: Topology, emerging trends, and challenges. Electronics 2021, 10, 2193. [Google Scholar] [CrossRef]
- Schneider, G.; Maier, H.; Häcker, J.; Siegele, S. Electricity storage with a solid bed High Temperature Thermal Energy Storage system (HTTES)—A methodical approach to improve the pumped thermal grid storage concept. In Proceedings of the 14th International Renewable Energy Storage Conference 2020 (IRES 2020), Düsseldorf, Germany, 10–12 March 2020; pp. 26–33. [Google Scholar]
- Yang, S.; Zhang, Z.; Cao, R.; Wang, M.; Cheng, H.; Zhang, L.; Jiang, Y.; Li, Y.; Chen, B.; Ling, H. Implementation for a cloud battery management system based on the CHAIN framework. Energy AI 2021, 5, 100088. [Google Scholar] [CrossRef]
- Gonzalez, I.; Calderón, A.J.; Folgado, F.J. IoT real time system for monitoring lithium-ion battery long-term operation in microgrids. J. Energy Storage 2022, 51, 104596. [Google Scholar] [CrossRef]
- Alzahrani, A.; Wangikar, S.M.; Indragandhi, V.; Singh, R.R.; Subramaniyaswamy, V. Design and Implementation of SAE J1939 and Modbus Communication Protocols for Electric Vehicle. Machines 2023, 11, 201. [Google Scholar] [CrossRef]
- McMahan, S. Bosch Cloud-Based Battery Management System Extends EV Battery Life. Available online: https://eepower.com/news/bosch-cloud-based-battery-management-extends-ev-battery-service-life/# (accessed on 21 May 2023).
- Semiconductors, N. AI-Powered Cloud-Connected Battery Management System for Electric Vehicles. NXP Semiconductors. Available online: https://www.nxp.com/company/about-nxp/ai-powered-cloud-connected-battery-management-system-for-electric-vehicles:NW-NXP-AI-POWERED-CLOUD-CONNECTED-BATTERY (accessed on 21 May 2023).
- Ricardo. Connected Battery Management System. Available online: https://www.ricardo.com/en/services/technical-consulting/software-development-and-applications/connected-battery-management-system (accessed on 21 May 2023).
- Panasonic. Panasonic Announces UBMC Service—A Cloud-Based Battery Management Service to Ascertain Battery State in Electric Mobility Vehicles. Available online: https://news.panasonic.com/global/press/en201210-1 (accessed on 21 May 2023).
- REPLY. Cloud-Enabled Battery Solution—CEBS. Available online: https://www.reply.com/en/automotive-and-manufacturing/cloud-enabled-battery-solution-cebs (accessed on 21 May 2023).
- Tanizawa, T.; Suzumiya, T.; Ikeda, K. Cloud-connected battery management system supporting e-mobility. Fujitsu Sci. Tech. J. 2015, 51, 27–35. [Google Scholar]
- Möller, D.P.; Haas, R.E. Guide to Automotive Connectivity and Cybersecurity; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Madeline, C.; Richard, S. Cybersecurity of Battery Management Systems. In Readout: Horiba Technical Reports; HORIBA: Singapore, 2019; pp. 82–89. [Google Scholar]
- Eiza, M.H.; Ni, Q. Driving with sharks: Rethinking connected vehicles with vehicle cybersecurity. IEEE Veh. Technol. Mag. 2017, 12, 45–51. [Google Scholar] [CrossRef]
- Rahman, S.; Aburub, H.; Mekonnen, Y.; Sarwat, A.I. A study of EV BMS cyber security based on neural network SOC prediction. In Proceedings of the 2018 IEEE/PES Transmission and Distribution Conference and Exposition (T&D), Denver, CO, USA, 16–19 April 2018; pp. 1–5. [Google Scholar]
- Greenberg, A. Hackers remotely kill a jeep on the highway. Wired 2015, 7, 21–22. [Google Scholar]
- Ochoa, J. Security-Enhanced Cyber-Physical Battery Management System Using Blockchain and Security Hardening Technology; Texas A&M University: Kingsville, TX, USA, 2020. [Google Scholar]
- Gumrukcu, E.; Arsalan, A.; Muriithi, G.; Joglekar, C.; Aboulebdeh, A.; Zehir, M.A.; Papari, B.; Monti, A. Impact of Cyber-attacks on EV Charging Coordination: The Case of Single Point of Failure. In Proceedings of the 2022 4th Global Power, Energy and Communication Conference (GPECOM), Cappadocia, Turkey, 14–17 June 2022; pp. 506–511. [Google Scholar]
- Hong, J. Cyber security issues in connected vehicle of intelligent transport system. Indian J. Sci. Technol. 2016, 9, 96027. [Google Scholar] [CrossRef]
- Bhusal, N.; Gautam, M.; Benidris, M. Cybersecurity of electric vehicle smart charging management systems. In Proceedings of the 2020 52nd North American Power Symposium (NAPS), Virtual Event, 11–14 April 2021; pp. 1–6. [Google Scholar]
- Sanghvi, A.; Markel, T. Cybersecurity for electric vehicle fast-charging infrastructure. In Proceedings of the 2021 IEEE Transportation Electrification Conference & Expo (ITEC), Chicago, IL, USA, 21–25 June 2021; pp. 573–576. [Google Scholar]
- Metere, R.; Pourmirza, Z.; Walker, S.; Neaimeh, M. An Overview of Cyber Security and Privacy on the Electric Vehicle Charging Infrastructure. arXiv 2022, arXiv:2209.07842. [Google Scholar]
- Acharya, S.; Dvorkin, Y.; Pandžić, H.; Karri, R. Cybersecurity of smart electric vehicle charging: A power grid perspective. IEEE Access 2020, 8, 214434–214453. [Google Scholar] [CrossRef]
- Park, Y.; Onar, O.C.; Ozpineci, B. Potential cybersecurity issues of fast charging stations with quantitative severity analysis. In Proceedings of the 2019 IEEE CyberPELS (CyberPELS), Knoxville, TN, USA, 29 April–1 May 2019; pp. 1–7. [Google Scholar]
- Johnson, J.; Berg, T.; Anderson, B.; Wright, B. Review of electric vehicle charger cybersecurity vulnerabilities, potential impacts, and defenses. Energies 2022, 15, 3931. [Google Scholar] [CrossRef]
- Bharathidasan, M.; Indragandhi, V.; Suresh, V.; Jasiński, M.; Leonowicz, Z. A review on electric vehicle: Technologies, energy trading, and cyber security. Energy Rep. 2022, 8, 9662–9685. [Google Scholar] [CrossRef]
- ISO 15118-20:2022. Road Vehicles—Vehicle to Grid Communication Interface. 2022. Available online: https://www.iso.org/standard/77845.html (accessed on 21 May 2023).
- Chandwani, A.; Dey, S.; Mallik, A. Cybersecurity of onboard charging systems for electric vehicles—Review, challenges and countermeasures. IEEE Access 2020, 8, 226982–226998. [Google Scholar] [CrossRef]
- Kharlamova, N.; Hashemi, S.; Træholt, C. Data-driven approaches for cyber defense of battery energy storage systems. Energy AI 2021, 5, 100095. [Google Scholar] [CrossRef]
- Johnson, J.; Hoaglund, J.R.; Trevizan, R.D.; Nguyen, T.A. Physical Security and Cybersecurity of Energy Storage Systems. In U.S. DOE Energy Storage Handbook; Sandia National Laboratories: Albuquerque, NM, USA, 2020. [Google Scholar]
- Maheshwari, P.U.; Bhargavi, S.; Umarani, S. Advancements in Cyber Security for Autonomous Vehicles. Int. J. Wirel. Netw. Secur. 2021, 7, 33–40. [Google Scholar]
- Tran-Jørgensen, P.W.; Kulik, T.; Boudjadar, J.; Larsen, P.G. Security analysis of cloud-connected industrial control systems using combinatorial testing. In Proceedings of the 17th ACM-IEEE International Conference on Formal Methods and Models for System Design, La Jolla, CA, USA, 9–11 October 2019; pp. 1–11. [Google Scholar]
- Kulik, T.; Larsen, P.G. Extensions to Formal Security Modeling Framework. 2018. Available online: https://github.com/kuliktomas/FCSVIoT/commit/189c7962f7f0870fa5315c31a71a6b35e896e47d (accessed on 3 June 2023).
- Ahmad, W.; Rasool, A.; Javed, A.R.; Baker, T.; Jalil, Z. Cyber security in iot-based cloud computing: A comprehensive survey. Electronics 2022, 11, 16. [Google Scholar] [CrossRef]
- Kulik, T.; Gomes, C.; Macedo, H.D.; Hallerstede, S.; Larsen, P.G. Towards secure digital twins. In Leveraging Applications of Formal Methods, Verification and Validation, Proceedings of the 11th International Symposium, ISoLA 2022, Rhodes, Greece, 22–30 October 2022; Springer: Berlin/Heidelberg, Germany, 2022; Part IV; pp. 159–176. [Google Scholar]
- Kharlamova, N.; Hashemi, S.; Træholt, C. The cyber security of battery energy storage systems and adoption of data-driven methods. In Proceedings of the 2020 IEEE Third International Conference on Artificial Intelligence and Knowledge Engineering (AIKE), Laguna Hills, CA, USA, 9–13 December 2020; pp. 188–192. [Google Scholar]
- Krishna, G.; Singh, R.; Gehlot, A.; Akram, S.V.; Priyadarshi, N.; Twala, B. Digital Technology Implementation in Battery-Management Systems for Sustainable Energy Storage: Review, Challenges, and Recommendations. Electronics 2022, 11, 2695. [Google Scholar] [CrossRef]
- Yang, S.; Liu, X.; Li, S.; Zhang, C. Advanced Battery Management System for Electric Vehicles; Springer Nature: Berlin/Heidelberg, Germany, 2022. [Google Scholar]
- Mhaisen, N.; Fetais, N.; Massoud, A. Secure smart contract-enabled control of battery energy storage systems against cyber-attacks. Alex. Eng. J. 2019, 58, 1291–1300. [Google Scholar] [CrossRef]
- Guo, L.; Yang, B.; Ye, J.; Chen, H.; Li, F.; Song, W.; Du, L.; Guan, L. Systematic assessment of cyber-physical security of energy management system for connected and automated electric vehicles. IEEE Trans. Ind. Inform. 2020, 17, 3335–3347. [Google Scholar] [CrossRef]
- Rohde, K.W. Cyber Security of DC Fast Charging: Potential Impacts to the Electric Grid; Idaho National Lab. (INL): Idaho Falls, ID, USA, 2019.
- Sripad, S.; Kulandaivel, S.; Pande, V.; Sekar, V.; Viswanathan, V. Vulnerabilities of electric vehicle battery packs to cyberattacks. arXiv 2017, arXiv:1711.04822. [Google Scholar]
- Hodge, C.; Hauck, K.; Gupta, S.; Bennett, J.C. Vehicle Cybersecurity Threats and Mitigation Approaches; National Renewable Energy Lab. (NREL): Golden, CO, USA, 2019.
- Idaho National Laboratory. Cyber Security Research and Development: Cyber Assessment Report of Level 2 AC Powered Electric Vehicle Supply Equipment; Idaho National Laboratory: Hong Kong, China, 2018.
- Acharya, S.; Dvorkin, Y.; Karri, R. Public plug-in electric vehicles + grid data: Is a new cyberattack vector viable? IEEE Trans. Smart Grid 2020, 11, 5099–5113. [Google Scholar] [CrossRef]
- Morrison, G.S. Threats and Mitigation of DDoS Cyberattacks Against the US Power Grid via EV Charging. Master’s Thesis, Wright State University, Dayton, OH, USA, 2018. [Google Scholar]
- Johnson, J.; Anderson, B.; Wright, B.; Graves, R.; Daley, J.; Quiroz, J.; Pratt, R.; Carroll, T.; O’Neil, L.; Dindlebeck, B. Securing Electric Vehicle Charging Infrastructure—Final Report; Sandia National Laboratory: Albuquerque, NM, USA, 2021.
- Pasetti, M.; Ferrari, P.; Bellagente, P.; Sisinni, E.; de Sá, A.O.; do Prado, C.B.; David, R.P.; Machado, R.C.S. Artificial neural network-based stealth attack on battery energy storage systems. IEEE Trans. Smart Grid 2021, 12, 5310–5321. [Google Scholar] [CrossRef]
- Kong, W.W.; Luo, Y.; Qi, Y.; Wang, Y. Full Protection Scheme and Energy Optimization Management of the Battery in Internal Combustion Engine Vehicles Based on Power Partitioning Model; SAE Technical Paper; SAE International: Warrendale, PA, USA, 2019; ISSN 0148-7191. [Google Scholar]
- Xie, J.; Chen, J.; Li, L.; Chen, Y. Advanced Battery Early Warning and Monitoring System. U.S. Patent US9177466B2, 3 November 2015. [Google Scholar]
- Liao, H.-J.; Lin, C.-H.R.; Lin, Y.-C.; Tung, K.-Y. Intrusion detection system: A comprehensive review. J. Netw. Comput. Appl. 2013, 36, 16–24. [Google Scholar] [CrossRef]
- Junejo, K.N.; Goh, J. Behaviour-based attack detection and classification in cyber physical systems using machine learning. In Proceedings of the 2nd ACM International Workshop on Cyber-Physical System Security, Xi’an, China, 30 May 2016; pp. 34–43. [Google Scholar]
- Lee, H.; Bere, G.; Kim, K.; Ochoa, J.J.; Park, J.-H.; Kim, T. Deep learning-based false sensor data detection for battery energy storage systems. In Proceedings of the 2020 IEEE CyberPELS (CyberPELS), Miami, FL, USA, 13 October 2020; pp. 1–6. [Google Scholar]
- Dey, S.; Khanra, M. Cybersecurity of plug-in electric vehicles: Cyberattack detection during charging. IEEE Trans. Ind. Electron. 2020, 68, 478–487. [Google Scholar] [CrossRef]
- Lee, I. Internet of Things (IoT) cybersecurity: Literature review and IoT cyber risk management. Future Internet 2020, 12, 157. [Google Scholar] [CrossRef]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Inayat, U.; Zia, M.F.; Mahmood, S.; Khalid, H.M.; Benbouzid, M. Learning-based methods for cyber attacks detection in IoT systems: A survey on methods, analysis, and future prospects. Electronics 2022, 11, 1502. [Google Scholar] [CrossRef]
- Kim, T.; Ochoa, J.; Faika, T.; Mantooth, H.A.; Di, J.; Li, Q.; Lee, Y. An overview of cyber-physical security of battery management systems and adoption of blockchain technology. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 10, 1270–1281. [Google Scholar] [CrossRef]
- Ochoa, J.J.; Bere, G.; Aenugu, I.R.; Kim, T.; Choo, K.-K.R. Blockchain-as-a-Service (BaaS) for battery energy storage systems. In Proceedings of the 2020 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 6–7 February 2020; pp. 1–6. [Google Scholar]
- Bere, G.; Ochoa, J.J.; Kim, T.; Aenugu, I.R. Blockchain-based firmware security check and recovery for battery management systems. In Proceedings of the 2020 IEEE Transportation Electrification Conference & Expo (ITEC), Chicago, IL, USA, 23–26 June 2020; pp. 262–266. [Google Scholar]
- Liu, M.; Yeoh, W.; Jiang, F.; Choo, K.-K.R. Blockchain for Cybersecurity: Systematic Literature Review and Classification. J. Comput. Inf. Syst. 2022, 62, 1182–1198. [Google Scholar] [CrossRef]
- Faika, T.; Kim, T.; Ochoa, J.; Khan, M.; Park, S.-W.; Leung, C.S. A blockchain-based Internet of Things (IoT) network for security-enhanced wireless battery management systems. In Proceedings of the 2019 IEEE Industry Applications Society Annual Meeting, Baltimore, MD, USA, 29 September–3 October 2019; pp. 1–6. [Google Scholar]
- Kazemi, Z.; Safavi, A.A.; Naseri, F.; Urbas, L.; Setoodeh, P. A secure hybrid dynamic-state estimation approach for power systems under false data injection attacks. IEEE Trans. Ind. Inform. 2020, 16, 7275–7286. [Google Scholar] [CrossRef]
- Kazemi, Z.; Safavi, A.A.; Setoodeh, P. Efficient resilient dynamic co-estimation framework for cyber-physical systems under sensor attacks. IET Control Theory Appl. 2020, 14, 3526–3536. [Google Scholar] [CrossRef]
- Kazemi, Z.; Safavi, A.A.; Arefi, M.M.; Naseri, F. Finite-Time Secure Dynamic State Estimation for Cyber–Physical Systems Under Unknown Inputs and Sensor Attacks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 52, 4950–4959. [Google Scholar] [CrossRef]
- Kumbhar, S.; Faika, T.; Makwana, D.; Kim, T.; Lee, Y. Cybersecurity for battery management systems in cyber-physical environments. In Proceedings of the 2018 IEEE Transportation Electrification Conference and Expo (ITEC), Long Beach, CA, USA, 13–15 June 2018; pp. 934–938. [Google Scholar]
- Stykas, V. Smart Car Chargers. Plug-n-Play for Hackers. 2021. Available online: https://www.pentestpartners.com/security-blog/smart-car-chargers-plug-n-play-for-hackers/ (accessed on 3 June 2023).
- Khalid, A.; Sundararajan, A.; Hernandez, A.; Sarwat, A.I. Facts approach to address cybersecurity issues in electric vehicle battery systems. In Proceedings of the 2019 IEEE Technology & Engineering Management Conference (TEMSCON), Atlanta, GA, USA, 12–14 June 2019; pp. 1–6. [Google Scholar]
- Bierbaum, D.; Stampa, R. Smart Synthesis of Cybersecurity and Functional Safety. ATZelectron. Worldw. 2021, 16, 8–11. [Google Scholar] [CrossRef]
- Kulik, T.; Dongol, B.; Larsen, P.G.; Macedo, H.D.; Schneider, S.; Tran-Jørgensen, P.W.; Woodcock, J. A survey of practical formal methods for security. Form. Asp. Comput. 2022, 34, 1–39. [Google Scholar] [CrossRef]
- van Eekelen, M.; Poll, E.; Hubbers, E.; Vieira, B.; van den Broek, F. An End-to-End Security Design for Smart EV-Charging for Enexis and ElaadNL; ElaadNL: Arnhem, The Netherlands, 2014. [Google Scholar]
- Pillitteri, Y.V.; Brewer, L.T. NISTIR 7628 Revision 1 Guidelines for Smart Grid Cybersecurity; Smart Grid Interoperability Panel (SGIP): Gaithersburg, MD, USA, 2014; p. 668. [Google Scholar]
- Rubio, J.E.; Alcaraz, C.; Lopez, J. Addressing security in OCPP: Protection against man-in-the-middle attacks. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–5. [Google Scholar]
- Ubys, L.; Nicolas Vancea, V.; Kulik, T.; Gorm Larsen, P.; Boudjadar, J.; Aranha, D.F. Formal Model In-The-Loop for Secure Industrial Control Networks. In Proceedings of the Formal Aspects of Component Software: 18th International Conference, FACS 2022, Virtual Event, 10–11 November 2022; pp. 74–89. [Google Scholar]
- ElaadNL. Security Architecture for Electric Vehicle Charging Infrastructure, Version 1.0; European Network for Cyber Security: Den Haag, The Netherlands, 2019. [Google Scholar]
- ElaadNL. Security Architecture for Electric Vehicle Charging Infrastructure, Version 2.0; European Network for Cyber Security: Den Haag, The Netherlands, 2019. [Google Scholar]
- Vaidya, B.; Mouftah, H.T. Multimodal and multi-pass authentication mechanisms for electric vehicle charging networks. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020; pp. 371–376. [Google Scholar]
- Gottumukkala, R.; Merchant, R.; Tauzin, A.; Leon, K.; Roche, A.; Darby, P. Cyber-physical system security of vehicle charging stations. In Proceedings of the 2019 IEEE Green Technologies Conference (GreenTech), Lafayette, LA, USA, 3–6 April 2019; pp. 1–5. [Google Scholar]
- Chhaya, S.; Ghatikar, R. Cybersecurity Platform and Certification Framework Development for EXtreme Fast Charging (XFC) Infrastructure Ecosystem. In Proceedings of the DOE Vehicle Technologies Office Annual Merit Review; Electric Power Research Institute, Inc.: Washington, DC, USA, 2021. [Google Scholar]
- Alcaraz, C.; Lopez, J. Digital twin: A comprehensive survey of security threats. IEEE Commun. Surv. Tutor. 2022, 24, 1475–1503. [Google Scholar] [CrossRef]
- ISO 12405-4:2018. Electrically Propelled Road Vehicles—Test Specification for Lithium-Ion Traction Battery Packs and Systems—Part 4: Performance Testing. 2018. Available online: https://www.iso.org/standard/71407.html (accessed on 21 May 2023).
- IEC 62660-1:2018. Secondary Lithium-Ion Cells for the Propulsion of Electric Road Vehicles—Part 1: Performance Testing. 2018. Available online: https://webstore.iec.ch/publication/28965 (accessed on 21 May 2023).
- Rosewater, D.M. IEEE Draft Battery Management System (BMS) Recommended Practice; Sandia National Lab. (SNL-NM): Albuquerque, NM, USA, 2020.
- J3061_201601. Cybersecurity Guidebook for Cyber-Physical Vehicle Systems. 2016. Available online: https://www.sae.org/standards/content/j3061_201601/ (accessed on 21 May 2023).
- ISO/IEC 27001. Information Security Management Systems. 2022. Available online: https://www.iso.org/standard/27001 (accessed on 21 May 2023).
- IEC 62443-4-2:2019. Security for Industrial Automation and Control Systems—Part 4-2: Technical Security Requirements for IACS Components. 2019. Available online: https://www.iecee.org/certification/iec-standards/iec-62443-4-22019-34421 (accessed on 21 May 2023).
- P2686. Recommended Practice for Battery Management Systems in Energy Storage Applications. 2018. Available online: https://standards.ieee.org/ieee/2686/7394/ (accessed on 21 May 2023).
- ISO/SAE 21434:2021. Road Vehicles—Cybersecurity Engineering. 2021. Available online: https://www.iso.org/standard/70918.html (accessed on 21 May 2023).
- X.1373. Vehicle-to-Infrastructure: Secure Software Update. 2017. Available online: https://www.itu.int/rec/T-REC-X.1373-201703-I/en (accessed on 21 May 2023).
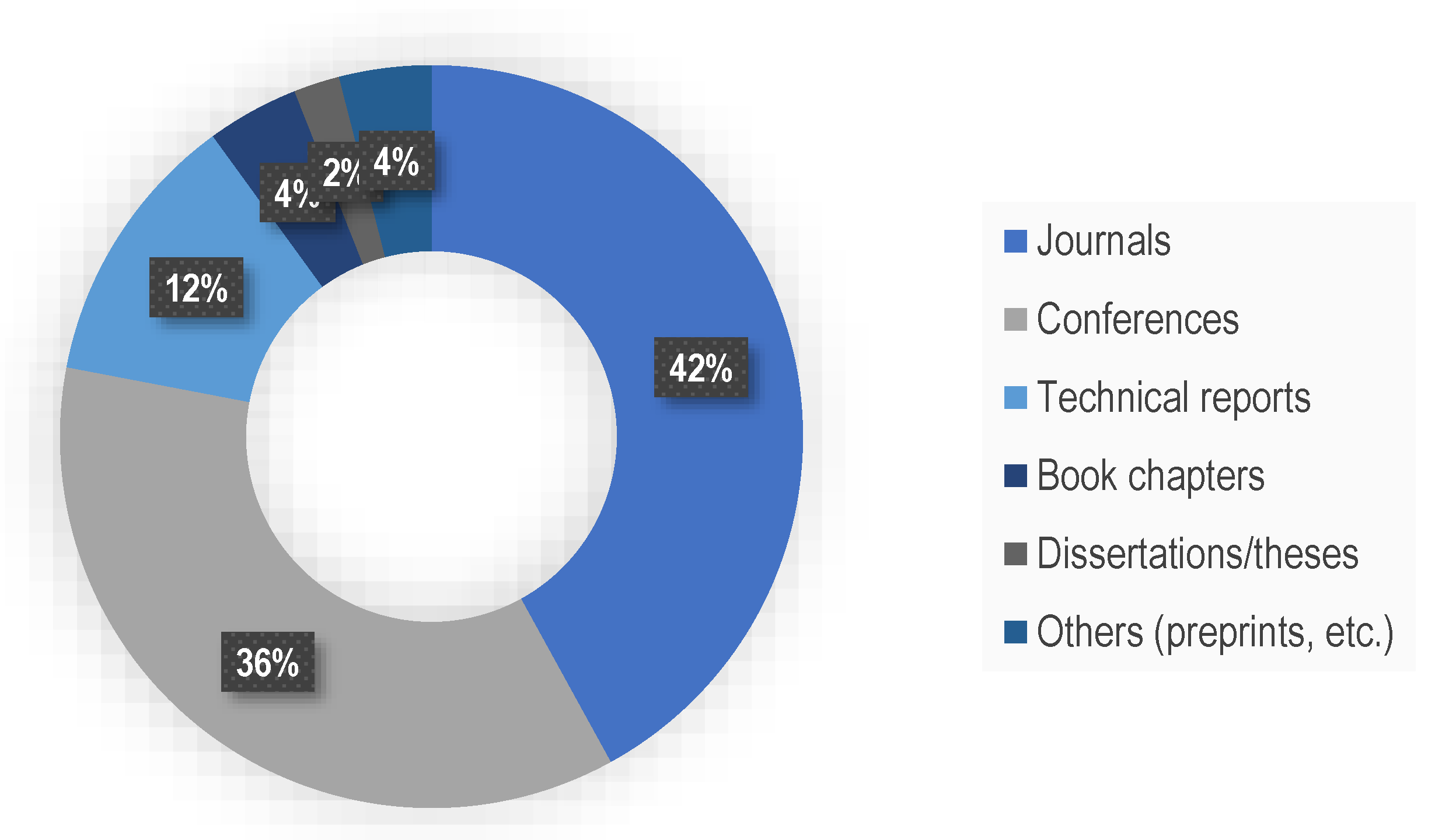


| Search Index | Specific Content |
|---|---|
| Database | Scopus, IEEE Xplore, gray literature. |
| Publication Type | Peer-reviewed journal and conference articles, book chapters, technical reports, dissertations/theses. |
| Search Strings | “cloud battery management system”, “cloud BMS”, “battery digital twin”, “battery cybersecurity”, “vehicle cybersecurity”, “battery security”. |
| Search Period | 2000–2023. |
| No. | Solution Name | Company | Description |
|---|---|---|---|
| 1 | Bosch™ Mobility Solutions | Bosch™ | CBMS takes into account driving conditions such as driving style and driving environment (drive cycle) to adjust battery operation to maximize the battery lifetime. Battery tears and wear are deductible by about 20%. |
| 2 | EVE-AiTM | NXP | The CBMS is multifunctional and has AI-based SOC/SOH prediction capability. It offers recommendations in terms of remaining range and optimum driving speeds. Faster diagnostic and reduced downtime are achievable. |
| 3 | UBMC (Universal Battery Management Cloud) | Panasonic | The CBMS is based on a new AI-driven solution for accurate SOC prediction. The AI algorithm is trained with massive data accumulated at Panasonic during product development. It comes with an API to support fleet operators through the recommendation of service/replacement of batteries. It also contains a solution to provide the driving range in specific routes and a recommendation system to book the most convenient charging points [24]. |
| 4 | Connected BMS | Ricardo | It offers advanced battery prognostics to reduce degradation and increase uptime. A +13% improvement in battery life is achievable [23]. |
| 5 | CEBS (Cloud-enabled Battery Solution) | Replay | The CBMS is equipped with cell-level IoT sensors to transmit battery data toward an external gateway via mobile radio or WLAN to the cloud. The use cases are related to optimized battery charging [25]. |
| 6 | Cloud-connected BMS | Fujitsu | It is based on a solution to grasp the condition of the shared batteries that will enable users to replace batteries (in swap stations) with peace of mind [26]. |
| 7 | Batter Intelligence as a Service | Bamomas | The CBMS offers remote battery fleet monitoring, in-depth battery analytics, and predictive maintenance. It also offers a web application and an API to provide insights into the health and condition of batteries. |
| 8 | iBMS (intelligent BMS) | Udantech | It provides a cloud–terminal collaborative control to enhance the performance of the onboard BMS. It also supports SOC calibration and remote balancing. |
| 9 | COMSOL ServerTM, COMSOL CompilerTM, and COMSOL API for use with Java® | COMSOL | Multiphysics models and battery digital twins produced in COMSOL can be used to update/calibrate the light-weighted models on the onboard BMS to maintain model fidelity over time |
| Potential Attack Paths | Impacts on CBMS | Countermeasures | |
|---|---|---|---|
|
|
| |
| Potential cyberattacks against CBMSs | |||
| Confidentiality |
| ||
| Integrity |
| ||
| Attack Detection | |||
| |||
| Availability |
| ||
| Standard/Policy/Regulation | Year | Title | Relevance |
|---|---|---|---|
| SAE J3061 [99] | 2016 | Cybersecurity guidebook for cyber-physical vehicle systems. |
|
| ISO/IEC 27001 [100] | 2022 | Information security management systems. |
|
| IEC62443 [101] | 2009 | Industrial communication networks—network and system security. |
|
| IEEE P2686 [102] | 2019 | Recommended practice for battery management systems in energy storage applications. |
|
| ISO/SAE 21434 [103] | 2021 | Road vehicles—cybersecurity engineering. |
|
| X.1373 [104] | 2017 | Secure software update capability for intelligent transportation system communication devices. |
|
| - | 2022 | Cybersecurity best practices for the safety of modern vehicles. |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Naseri, F.; Kazemi, Z.; Larsen, P.G.; Arefi, M.M.; Schaltz, E. Cyber-Physical Cloud Battery Management Systems: Review of Security Aspects. Batteries 2023, 9, 382. https://doi.org/10.3390/batteries9070382
Naseri F, Kazemi Z, Larsen PG, Arefi MM, Schaltz E. Cyber-Physical Cloud Battery Management Systems: Review of Security Aspects. Batteries. 2023; 9(7):382. https://doi.org/10.3390/batteries9070382
Chicago/Turabian StyleNaseri, Farshid, Zahra Kazemi, Peter Gorm Larsen, Mohammad Mehdi Arefi, and Erik Schaltz. 2023. "Cyber-Physical Cloud Battery Management Systems: Review of Security Aspects" Batteries 9, no. 7: 382. https://doi.org/10.3390/batteries9070382
APA StyleNaseri, F., Kazemi, Z., Larsen, P. G., Arefi, M. M., & Schaltz, E. (2023). Cyber-Physical Cloud Battery Management Systems: Review of Security Aspects. Batteries, 9(7), 382. https://doi.org/10.3390/batteries9070382








