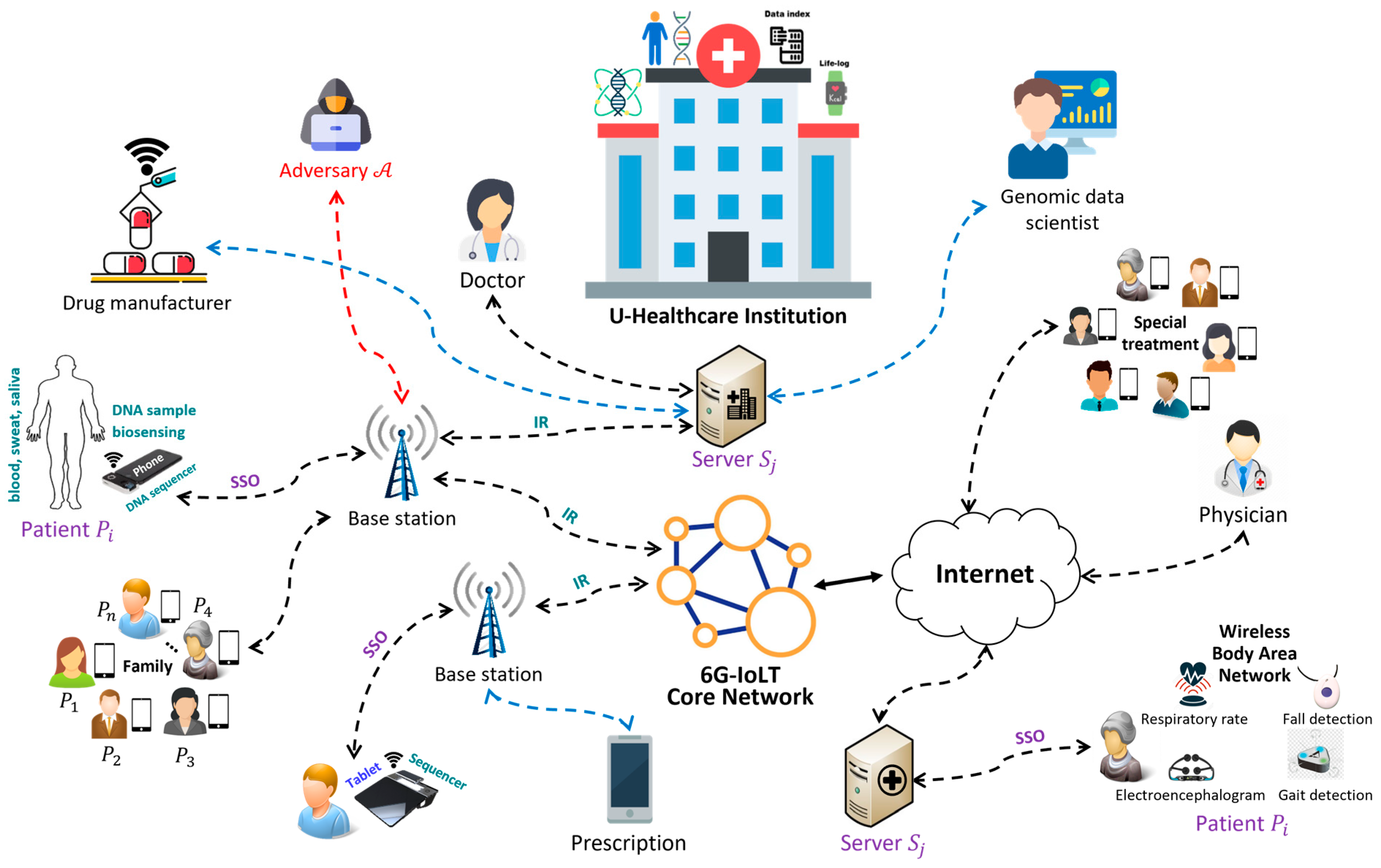
Securing Group Patient Communication in 6G-Aided Dynamic Ubiquitous Healthcare with Real-Time Mobile DNA Sequencing
Abstract
1. Introduction
1.1. Research Problems
1.2. Goals and Contributions
- (1)
- This work is the first to introduce 6G-assisted group-based U-healthcare services enabled by a real-time DNA sequencing technique constructed in IoLT environments. A patient-grouping solution helps in accelerating service communications and achieving better medical-centered services. With the assistance of 6G technology, onsite sequencing data produced by a portable TGS-based sequencer (connected to a patient’s mobile device) is transmitted to the server in a real-time manner for further healthcare processes. Thereafter, the server shares analytical results and related medical information with the patients. These procedures are secured by common group keys generated by the proposed protocol. The server is also allowed to trace the users based on their registered information for achieving a truly patient-centric service.
- (2)
- In the proposed protocol, a sequencing-device-based single sign-on (SD-SSO) function is introduced for the first time. Patients are allowed to store a single set of credentials (registered with multiple servers) on their DNA sequencers directly. Due to the SSO property, the patients only need to login to the system once per session to communicate with multiple providers. In addition, the proposed SD-SSO function is designed without the participation of a third-party center, which can reduce communication overhead and address the risk of adversaries hacking into the registration center and compromising all servers.
- (3)
- A three-factor authentication mechanism is enabled in the protocol through the integration of password (the first factor), sequencing device (the second factor), and biometrics (the third factor). Lacking only one of the three factors will result in failure of the authentication. In this way, better patient privacy and perfect forward secrecy of group keys are assured for securing U-healthcare communications. In the protocol, patient password and patient biometrics are changeable, which further enhances the security robustness.
- (4)
- The author introduces dynamic U-healthcare services enabled by a time-bound function. In this design, different services of a provider or multiple healthcare processes in a single service can be allotted in respective time ranges in accordance with specific requests. This solution makes providers flexibly adjust service time in order to provide more efficient medical processes as well as more convenient treatments for different kinds of patients. Controlling such access to the services using the time bounds can also address possible bottleneck issues where the services are requested at the same time by massive patients. Furthermore, a fast synchronizable key-derivation procedure is provided, which can rapidly reset communication keys for addressing desynchronization problems that could possibly occur in such a dynamic environment.
1.3. Paper Organization
2. Related Works
2.1. 5G, 6G, and U-Healthcare
2.2. User Authentication and Key Negotiation Solutions
3. Preliminaries
3.1. Sequencing Biosensor Technology
3.2. Biohash Function
3.3. Time-Bound Function
3.4. Complexity Assumptions
4. Problem Formulation
4.1. System Model and Adversarial Capabilities
- 𝒜 has full control over the open IoLT, which enables 𝒜 to intercept, insert, delete, or replay any transcripts conveyed between and .
- 𝒜 may attempt to attack the past communications between and based on secret parameters or on a group session key 𝒜 somehow retrieves from the current communicated messages.
- 𝒜 may attempt to extract the secret values or registered credentials stored in a compromised and use them to attack the communication.
- 𝒜 may be a privileged insider (e.g., member of a maintenance team) who can launch even more serious attacks upon a patient’s registered information obtained from .
- 𝒜 may also be a corrupted or that can trigger similar attacks on the communication.
4.2. Formal Security Model
- (1)
- Send(Ç, ): This query allows 𝒜 to request a message to Ç; Ç replies to 𝒜 based upon the procedure of the proposed protocol.
- (2)
- Execute(): In this query, 𝒜 is allowed to eavesdrop the message conveyed between and .
- (3)
- Reveal(Ç): This query enables 𝒜 to retrieve a session key computed by Ç in accordance with the procedure of the protocol.
- (4)
- Corrupt: In a three-factor authentication protocol, this query returns to 𝒜 password , parameters stored in sequencing device , and biometrics if , , and , respectively.
- (5)
- Test(Ç): This is a statistical test query. 𝒜 is allowed to directly request Ç for the session key; Ç probabilistically replies to 𝒜 upon the outcome of a tossed coin .
5. The Proposed Protocol
5.1. Setup Phase
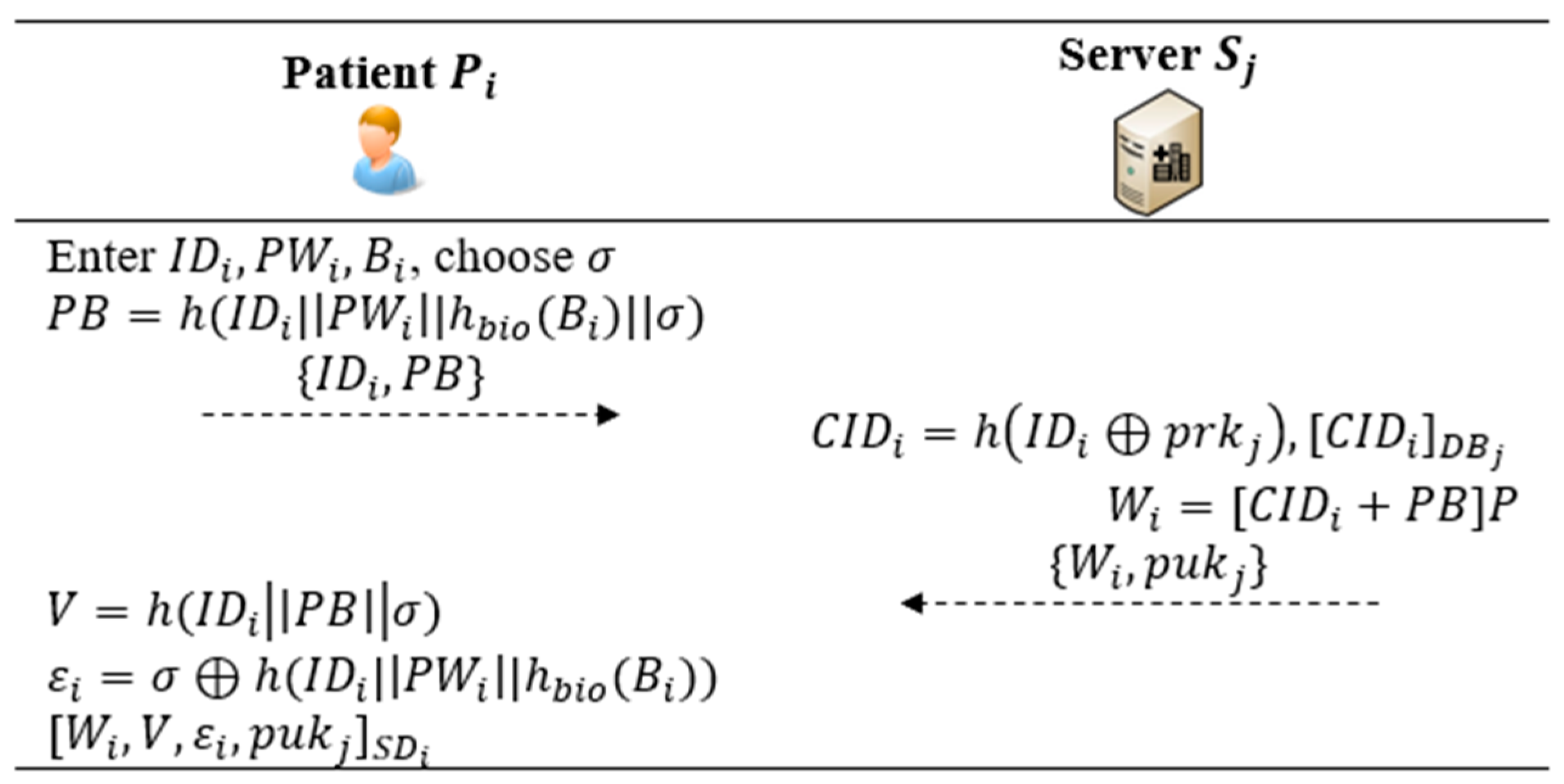
5.2. Registration Phase
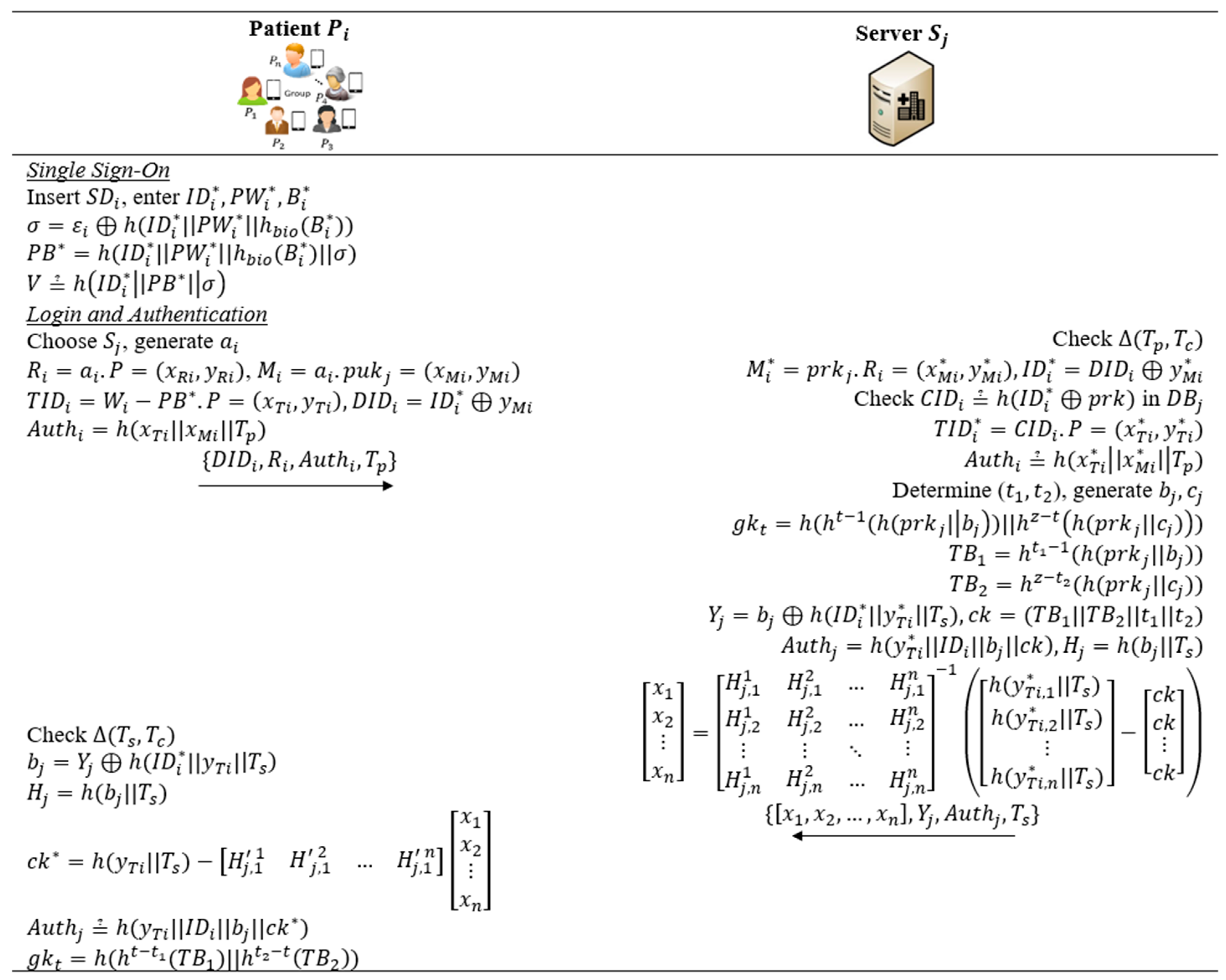
5.3. Login and Authentication Phase
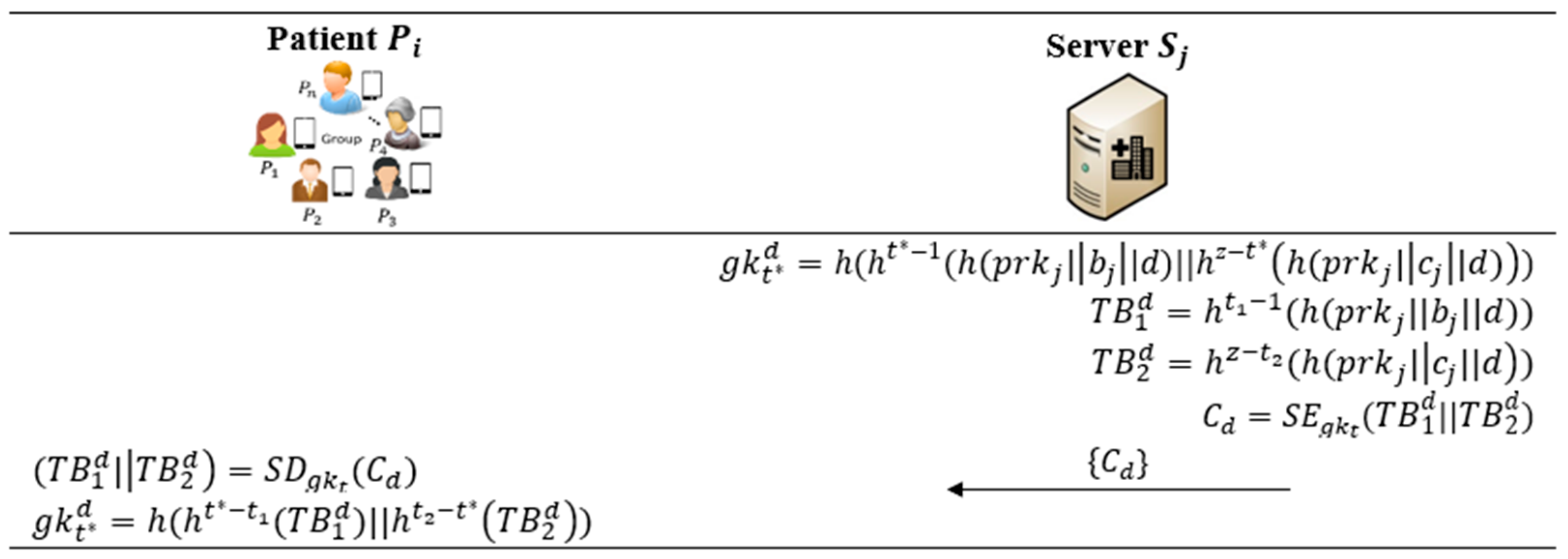
5.4. Synchronizable Key-Derivation Phase
5.5. Password and Biometrics Change Phase
6. Security Certificate
6.1. Sematic Security Discussion
- (1)
- Replay attacks: Suppose the message is intercepted by 𝒜 and it is resent to to launch a replay attack in the next session. However, timestamp in the protocol is employed to check if the message is resent. Moreover, when receiving the message , 𝒜 will also fail to compromise the key since 𝒜 does not know of for retrieving the number . Therefore, the replay attack is prevented in the proposed protocol.
- (2)
- MITM attacks: On the received message , 𝒜 may insert forged parameters and generate a candidate login message. 𝒜 aims to act as a middle man to compromise the conveyed messages without being noticed by and . However, without the private key , 𝒜 is not able to compute sufficient parameters for the verifications on and . Similarly, without and , 𝒜 can also not compute a valid message for the check on on the patient side. As a result, the protocol is free from MITM attacks.
- (3)
- Password and biometrics guessing attacks: At first, 𝒜 may attempt to directly enter a candidate password for logging to the system. However, the login request will be immediately rejected by upon the check . Suppose the hash value is somehow known to 𝒜, then 𝒜 attempts to guess based on . Other than , the values are also included in the function generating . Therefore, it is extremely hard (with a negligible success probability) for 𝒜 to guess the correct by computing candidate hashes and comparing them with the original . Using similar arguments, the biometrics is also completely protected during the communication process. Moreover, my work provides password and biometrics update functions that further assure the security of and . Therefore, a robust three-factor authentication mechanism is achieved in the proposed protocol.
- (4)
- Impersonation attacks: Suppose the identity is somehow disclosed, then 𝒜 obtains and uses it to generate a fake login message for impersonating . However, it is not possible for 𝒜 to launch this impersonation attack without since the protocol can resist password and biometrics guessing attacks, as stated above. Moreover, without the knowledge of , 𝒜 can also not retrieve for further steps upon the known . Thus, impersonation attacks are resisted in the proposed protocol.
- (5)
- Lost/stolen sequencer attacks: Suppose 𝒜 has somehow stolen the sequencer ; then, 𝒜 retrieved all stored parameters. However, the important credentials are not stored in directly. Obtaining the parameters inside is not sufficient for passing the verification and for generating a valid login request message . Thus, my protocol is robust against lost/stolen sequencer attacks.
- (6)
- Desynchronization attacks: Two acknowledgement values and generated by and , respectively, are used for assuring a robust mutual authentication in the proposed protocol. and are deleted after the login and authentication procedure session is completed. In addition, after each synchronizable key-derivation procedure finishes, and do not update or store any redundant parameters used for the next communication sessions. Hence, desynchronization problems and related attacks are prevented in my work.
- (7)
- Privileged insider attacks: Suppose there is a privileged insider 𝒜 who can monitor data transmission during the registration and capture message . Upon the reception of , it is not possible for 𝒜 to compromise the communication due to the stated resistance to impersonation attacks. Using the value , 𝒜 is also not able to compute a correct for the attack on without stored in the smart card. In another scenario, even if 𝒜 somehow obtains in the database, 𝒜 still cannot pass the server verification without . Thus, the protocol can resist privileged insider attacks.
- (8)
- DoS attacks: For analysis of DoS attacks, the author discusses some possible threats that may affect communication performance of the protocol. In the login phase, the system verifies by upon the newly input credentials . If the check is not successful, the session will be immediately terminated. Hence, it is not possible for 𝒜 is not able to flood the login and authentication procedure using multiple subsequent steps. On the other hand, upon the received message from , only operates two minor computations and before the check is made. Retransmitting massive messages to for disrupting its services would not be an efficient attack due to the redundant resources of . Moreover, the communication will also be terminated once the check does not hold in the beginning. Therefore, DoS attacks are prevented in the protocol.
- (9)
- Robust mutual authentication: In the proposed communication, should be authenticated as a legitimate patient for preventing patients’ identities and possibly costly services from being compromised. Upon receiving the login request from , using the private key, computes and retrieves . These parameters are used for the verification that confirms the legitimacy of the patient . On the other hand, based on the message , retrieves the number to compute . These parameters are used for the check of the acknowledgement that confirms legitimacy of the server and assures true service provision. If one of the above checks fails, the session will be terminated and the session key will not be established successfully. Hence, a robust mutual authentication is achieved in the proposed protocol.
- (10)
- Patient anonymity and untraceability: The identity is hidden in the parameter of the login message requested by . Also, the message sent by does not reveal to the public. Therefore, the anonymity of is guaranteed during the login and authentication process. The parameters contained in and in respective communication sessions are totally not identical since different random numbers and timestamps are used for the computations. Therefore, 𝒜 is not able to identify any two login messages sent by the same patient . Hence, the proposed protocol achieves patient anonymity and patient untraceability.
- (11)
- Message unlinkability: When linking the parameters of all messages to each other, there are not any fixed values found. It means that it will not allow 𝒜 to trace for the purpose of guessing ’s identity. Thus, a message unlinkability feature is achieved in the proposed protocol.
- (12)
- Perfect forward secrecy: Suppose some sensitive data, secret parameters, or even a session key established in the current session are somehow revealed to 𝒜. Upon receiving these vales, 𝒜 attempts to attack the past communications. However, it is not possible for 𝒜 to launch the attack since the values are completely not identical in different communication sessions due to the inclusion of random numbers and timestamp values in the computations. For instance, 𝒜 cannot use the currency key to compromise the message encrypted using a key established in the past session. If the long-term private key of is compromised, the secrecy of is also not affected, because there are no associated parameters between them. Hence, a perfect forward secrecy is achieved in my protocol.
- (13)
- Perfect backward secrecy (known-key security): With similar arguments, the protocol is proven not to be vulnerable to a known-key attack, since compromise of the past key does not allow either a passive 𝒜 to compromise the future key or impersonation by an active 𝒜 in the future.
6.2. Logical Analysis Using BAN logic
- Seeing rule (R1): ;
- Interpretation rule (R2): ;
- Freshness rule (R3): ;
- Verification rule (R4): ;
- Jurisdiction rule (R5): ;
- Belief rule (R6): .
- Assumption 1 (A1): |≡ ;
- Assumption 2 (A2): |≡ ;
- Assumption 3 (A3): ;
- Assumption 4 (A4): ;
- Assumption 5 (A5): ;
- Assumption 6 (A6): ;
- Assumption 7 (A7): ;
- Assumption 8 (A8): ;
- Assumption 9 (A9): |≡ ;
- Assumption 10 (A10): ;
- Assumption 11 (A11): .
- : Based on the Message 1, we have .
- : Using A1 and R1, we have |≡ |~ .
- : According to R2, we obtain |≡ |~ .
- : Using R3 and A2, we have |≡ #.
- : Based on R4, , and , we obtain |≡ |≡ .
- : According to R5, A3, and , we obtain |≡ .
- : Based on R6 and , we obtain |≡ , |≡ , and |≡ .
- : Due to , and , we obtain |≡ .
- : Based on , A4, A5, A6, A7, A8, and , we can obtain |≡ (G1 achieved).
- : Based on , A4, A5, A6, A7, A8, and , we can obtain |≡ (G2 achieved).
- : According to the Message 2, we have
- : In accordance with R1 and A1, we obtain |≡ |~ .
- : Based upon R2, we can obtain .
- : Using R3 and A9, we have .
- : Based on R4, and , we obtain |≡ |≡ .
- : According to R5, A10, and , we obtain |≡ .
- : Based on R6 and , we obtain |≡ , |≡ , |≡ , and |≡ .
- : In accordance with , while and , we can obtain |≡ (G3 achieved).
- : Due to , , A11, and , we obtain |≡ .
- : Based on , , , and , we obtain |≡ (G4 achieved).
6.3. Formal Security Proof with RoR Model
7. Performance Evaluation and Comparison
7.1. Security Properties and Functionalities
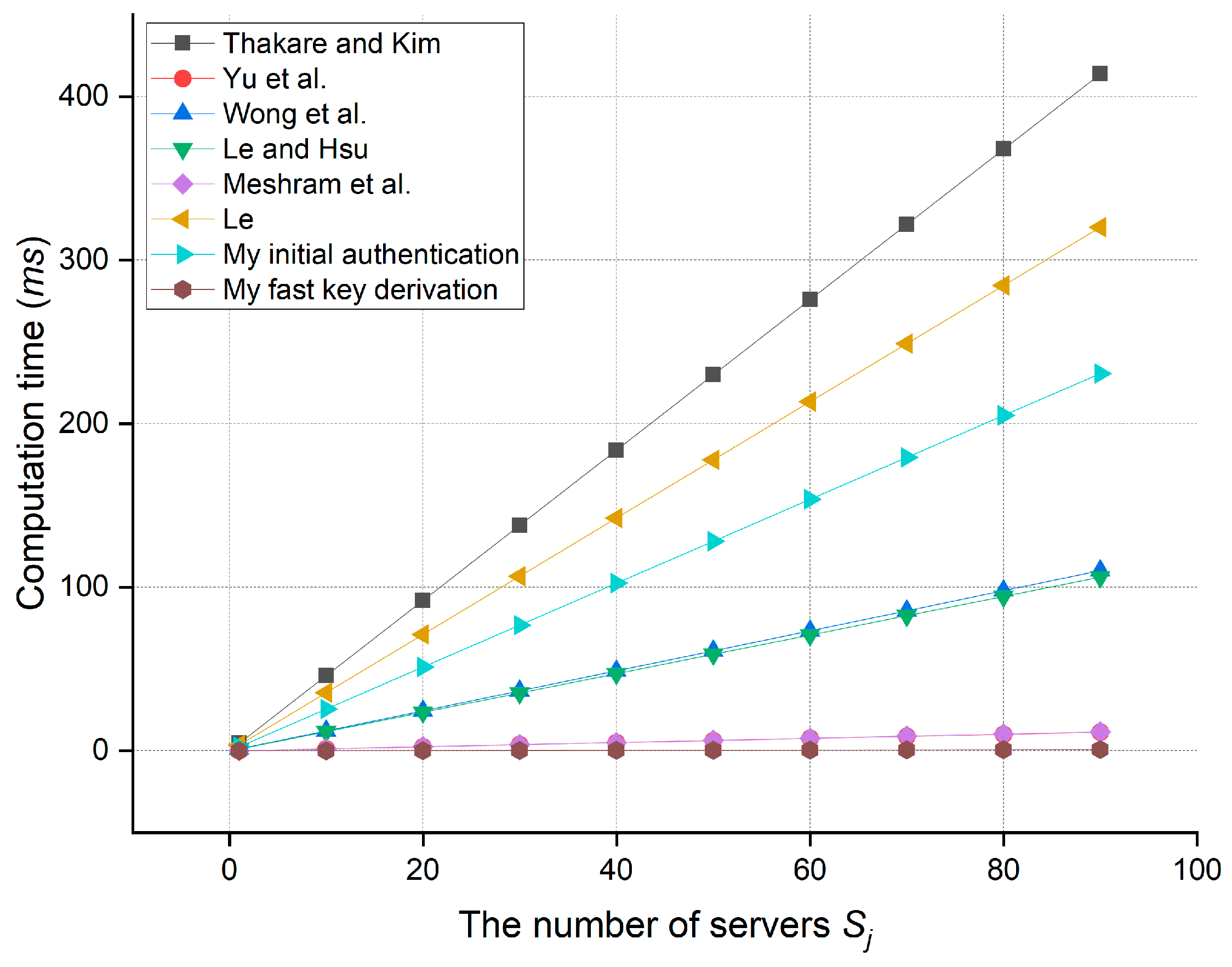
7.2. Computation Overhead
7.3. Communication Overhead
8. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Milicchio, F.; Oliva, M.; Boucher, C.; Prosperi, M. Third-generation sequencing data analytics on mobile devices: Cache oblivious and out-of-core approaches as a proof-of-concept. Procedia Comput. Sci. 2018, 134, 219–226. [Google Scholar] [CrossRef]
- Hassan, S.; Bahar, R.; Johan, M.F.; Mohamed Hashim, E.K.; Abdullah, W.Z.; Esa, E.; Abdul Hamid, F.S.; Zulkafli, Z. Next-Generation Sequencing (NGS) and Third-Generation Sequencing (TGS) for the Diagnosis of Thalassemia. Diagnostics 2023, 13, 373. [Google Scholar] [CrossRef]
- Raza, K.; Qazi, S. Chapter 5—Nanopore sequencing technology and Internet of living things: A big hope for U-healthcare. In Sensors for Health Monitoring; Dey, N., Chaki, J., Kumar, R., Eds.; Academic Press: Cambridge, MA, USA, 2019; Volume 5, pp. 95–116. [Google Scholar]
- Pizzolante, R.; Castiglione, A.; Carpentieri, B.; De Santis, A.; Palmieri, F.; Castiglione, A. On the protection of consumer genomic data in the Internet of Living Things. Comput. Secur. 2018, 74, 384–400. [Google Scholar] [CrossRef]
- Bolognini, D.; Bartalucci, N.; Mingrino, A.; Vannucchi, A.M.; Magi, A. NanoR: A user-friendly R package to analyze and compare nanopore sequencing data. PLoS ONE 2019, 14, e0216471. [Google Scholar] [CrossRef] [PubMed]
- Lacerda, J.M.T.; Valentim, R.A.M.; Araújo, B.G.d.; Morais, P.S.G.; Dantas, M.C.M. Service-oriented biomedical devices. In Proceedings of the 2014 IEEE Healthcare Innovation Conference (HIC), Seattle, WA, USA, 8–10 October 2014; pp. 203–206. [Google Scholar]
- García-Hernández, L.A.; Martínez-Martínez, E.; Pazos-Solís, D.; Aguado-Preciado, J.; Dutt, A.; Chávez-Ramírez, A.U.; Korgel, B.; Sharma, A.; Oza, G. Optical Detection of Cancer Cells Using Lab-on-a-Chip. Biosensors 2023, 13, 439. [Google Scholar] [CrossRef] [PubMed]
- Nanopore, O. Oxford Nanopore Announces £100 Million ($140M) Fundraising from Global Investors. Available online: https://nanoporetech.com/about-us/news/oxford-nanopore-announces-ps100-million-140m-fundraising-global-investors (accessed on 12 May 2023).
- Nayak, S.; Patgiri, R. 6G Communication Technology: A Vision on Intelligent Healthcare. In Health Informatics: A Computational Perspective in Healthcare; Patgiri, R., Biswas, A., Roy, P., Eds.; Springer: Singapore, 2021; pp. 1–18. [Google Scholar] [CrossRef]
- Chen, S.; Liang, Y.C.; Sun, S.; Kang, S.; Cheng, W.; Peng, M. Vision, Requirements, and Technology Trend of 6G: How to Tackle the Challenges of System Coverage, Capacity, User Data-Rate and Movement Speed. IEEE Wirel. Commun. 2020, 27, 218–228. [Google Scholar] [CrossRef]
- Khattak, S.B.A.; Nasralla, M.M.; Rehman, I.U. The Role of 6G Networks in Enabling Future Smart Health Services and Applications. In Proceedings of the 2022 IEEE International Smart Cities Conference (ISC2), Pafos, Cyprus, 26–29 September 2022; pp. 1–7. [Google Scholar]
- Nayak, S.; Patgiri, R. 6G Communication: Envisioning the Key Issues and Challenges. EAI Endorsed Trans. Internet Things 2020, 6, 166959. [Google Scholar] [CrossRef]
- Barman, S.; Shum, H.P.H.; Chattopadhyay, S.; Samanta, D. A Secure Authentication Protocol for Multi-Server-Based E-Healthcare Using a Fuzzy Commitment Scheme. IEEE Access 2019, 7, 12557–12574. [Google Scholar] [CrossRef]
- Noohani, M.Z.; Magsi, K.U. A Review Of 5G Technology: Architecture, Security and wide Applications. IRJET J. 2020, 7, 3440–3471. [Google Scholar] [CrossRef]
- Yaacoub, E.; Alouini, M. A Key 6G Challenge and Opportunity—Connecting the Base of the Pyramid: A Survey on Rural Connectivity. Proc. IEEE 2020, 108, 533–582. [Google Scholar] [CrossRef]
- Minglan, S.; Chaoying, Z.; Qiaoqiao, L.; Baolin, L.; Jianxiu, W. Holographic communication technology. In Proceedings of the 2021 International Conference on Neural Networks, Information and Communication Engineering, Qingdao, China, 27–28 August 2021. [Google Scholar]
- Letaief, K.B.; Chen, W.; Shi, Y.; Zhang, J.; Zhang, Y.A. The Roadmap to 6G: AI Empowered Wireless Networks. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef]
- Chen, Z.; Ma, X.; Zhang, B.; Zhang, Y.; Niu, Z.; Kuang, N.; Chen, W.; Li, L.; Li, S. A survey on terahertz communications. China Commun. 2019, 16, 1–35. [Google Scholar] [CrossRef]
- Gui, G.; Liu, M.; Tang, F.; Kato, N.; Adachi, F. 6G: Opening New Horizons for Integration of Comfort, Security, and Intelligence. IEEE Wirel. Commun. 2020, 27, 126–132. [Google Scholar] [CrossRef]
- Alraih, S.; Shayea, I.; Behjati, M.; Nordin, R.; Abdullah, N.F.; Abu-Samah, A.; Nandi, D. Revolution or Evolution? Technical Requirements and Considerations towards 6G Mobile Communications. Sensors 2022, 22, 762. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. Smart Mutual Authentication Protocol for Cloud Based Medical Healthcare Systems Using Internet of Medical Things. IEEE J. Sel. Areas Commun. 2021, 39, 346–360. [Google Scholar] [CrossRef]
- Chiou, S.-Y.; Ying, Z.; Liu, J. Improvement of a Privacy Authentication Scheme Based on Cloud for Medical Environment. J. Med. Syst. 2016, 40, 101. [Google Scholar] [CrossRef]
- Yuanbing, W.; Wanrong, L.; Bin, L. An Improved Authentication Protocol for Smart Healthcare System Using Wireless Medical Sensor Network. IEEE Access 2021, 9, 105101–105117. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Kumar, V.; Mahmoud, M.S.; Alkhayyat, A.; Srinivas, J.; Ahmad, M.; Kumari, A. RAPCHI: Robust authentication protocol for IoMT-based cloud-healthcare infrastructure. J. Supercomput. 2022, 78, 16167–16196. [Google Scholar] [CrossRef]
- Gupta, D.S.; Mazumdar, N.; Nag, A.; Singh, J.P. Secure data authentication and access control protocol for industrial healthcare system. J. Ambient Intell. Humaniz. Comput. 2023, 14, 4853–4864. [Google Scholar] [CrossRef]
- Alam, I.; Kumar, M. A novel authentication protocol to ensure confidentiality among the Internet of Medical Things in covid-19 and future pandemic scenario. Internet Things 2023, 22, 100797. [Google Scholar] [CrossRef] [PubMed]
- Thakare, A.; Kim, Y.-G. Secure and Efficient Authentication Scheme in IoT Environments. Appl. Sci. 2021, 11, 1260. [Google Scholar] [CrossRef]
- Yu, Y.; Taylor, O.; Li, R.; Sunagawa, B. An Extended Chaotic Map-Based Authentication and Key Agreement Scheme for Multi-Server Environment. Mathematics 2021, 9, 798. [Google Scholar] [CrossRef]
- Wong, A.-K.; Hsu, C.-L.; Le, T.-V.; Hsieh, M.-C.; Lin, T.-W. Three-Factor Fast Authentication Scheme with Time Bound and User Anonymity for Multi-Server E-Health Systems in 5G-Based Wireless Sensor Networks. Sensors 2020, 20, 2511. [Google Scholar] [CrossRef]
- Le, T.V.; Hsu, C.L. An Anonymous Key Distribution Scheme for Group Healthcare Services in 5G-Enabled Multi-Server Environments. IEEE Access 2021, 9, 53408–53422. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Y.; Tang, S.; Luo, H. Privacy Protection for E-Health Systems by Means of Dynamic Authentication and Three-Factor Key Agreement. IEEE Trans. Ind. Electron. 2018, 65, 2795–2805. [Google Scholar] [CrossRef]
- Mangard, S.; Oswald, E.; Popp, T. Power Analysis Attacks: Revealing the Secrets of Smart Cards; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2007. [Google Scholar] [CrossRef]
- Harn, L.; Hsu, C.; Xia, Z. Lightweight and flexible key distribution schemes for secure group communications. Wirel. Netw. 2021, 27, 129–136. [Google Scholar] [CrossRef]
- Tselikis, C.; Douligeris, C.; Maglaras, L.; Mitropoulos, S. On the conference key distribution system with user anonymity. J. Inf. Secur. Appl. 2020, 54, 102556. [Google Scholar] [CrossRef]
- Meshram, C.; Ibrahim, R.W.; Deng, L.; Shende, S.W.; Meshram, S.G.; Barve, S.K. A robust smart card and remote user password-based authentication protocol using extended chaotic maps under smart cities environment. Soft Comput. 2021, 25, 10037–10051. [Google Scholar] [CrossRef]
- Le, T.-V. Cross-Server End-to-End Patient Key Agreement Protocol for DNA-Based U-Healthcare in the Internet of Living Things. Mathematics 2023, 11, 1638. [Google Scholar] [CrossRef]
- Normand, R.; Yanai, I. An introduction to high-throughput sequencing experiments: Design and bioinformatics analysis. Methods Mol. Biol. 2013, 1038, 1–26. [Google Scholar] [CrossRef] [PubMed]
- Mignardi, M.; Nilsson, M. Fourth-generation sequencing in the cell and the clinic. Genome Med. 2014, 6, 31. [Google Scholar] [CrossRef]
- Jujjavarapu, C.; Anandasakaran, J.; Amendola, L.M.; Haas, C.; Zampino, E.; Henrikson, N.B.; Jarvik, G.P.; Mooney, S.D. ShareDNA: A smartphone app to facilitate family communication of genetic results. BMC Med. Genom. 2021, 14, 10. [Google Scholar] [CrossRef] [PubMed]
- Borré Ortiz, Y.; Suarez, M.; Expósito, M. Importance and Recognition of the Family in Health Care: A Reflection for Nursing. Nurs. Care Open Access J. 2017, 3, 00084. [Google Scholar] [CrossRef]
- Liu, W.; Wang, X.; Peng, W.; Xing, Q. Center-Less Single Sign-On With Privacy-Preserving Remote Biometric-Based ID-MAKA Scheme for Mobile Cloud Computing Services. IEEE Access 2019, 7, 137770–137783. [Google Scholar] [CrossRef]
- Shohaimay, F.; Ismail, E.S. Improved and Provably Secure ECC-Based Two-Factor Remote Authentication Scheme with Session Key Agreement. Mathematics 2023, 11, 5. [Google Scholar] [CrossRef]
- Le, T.V.; Lu, C.F.; Hsu, C.L.; Do, T.K.; Chou, Y.F.; Wei, W.C. A Novel Three-Factor Authentication Protocol for Multiple Service Providers in 6G-Aided Intelligent Healthcare Systems. IEEE Access 2022, 10, 28975–28990. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. A secure authentication scheme with forward secrecy for industrial internet of things using Rabin cryptosystem. Comput. Commun. 2020, 160, 215–227. [Google Scholar] [CrossRef]


| Notation Used in the Protocol | Explanation |
|---|---|
| The server | |
| The patient | |
| Private key, public key of | |
| Basic point on the curve with two coordinates and | |
| Identity of | |
| Password of | |
| Biometrics of | |
| Mobile device of | |
| Sequencing device (sequencer) of | |
| Timestamp | |
| Concatenating operation | |
| ⊕ | Exclusive-or (XOR) operation |
| One-way hash function, biohash function | |
| Symmetric encryption, symmetric decryption using a key k | |
| Storing parameters in | |
| 𝒜 | Adversary |
| Notations Used in the BAN | Explanation |
|---|---|
| X |≡ M | X believes a statement M |
| X ⊲ M | X sees the statement M |
| X |~ M | X once said the statement M |
| X ⟹ M | X has jurisdiction over the statement M |
| (M, N) | M or N is one part of the formula (M, N) |
| The statement M is combined with the formula N | |
| #(M) | The formula M is fresh, meaning it has not been sent in any previous messages |
| Formula K is a secret known only by X and Y; only X and Y can use M to authenticate each other | |
| Value G is known only to X and Y; it is used for their communication |
| Notations | Explanation |
|---|---|
| Size of a hash value | |
| Size of a random number | |
| Size of a biometric value | |
| Total hash oracle queries | |
| Total Send queries | |
| Total Execute queries | |
| List of hash oracle outputs | |
| List of random oracle results | |
| List of transcripts conveyed between and | |
| Biometric false-positive probability | |
| Zipf parameters |
| Hash query is executed as follows, where are messages. If the record (, ) is found in the list , return ; if not, choose and write (, ) to ; the list is created by a similar procedure. |
| Reveal(Ç) query is executed by a simple procedure as follows. Once Ç is in an Accept state, a session key formed by Ç is returned. |
| Test(Ç) query is executed as follows. Ç tosses the coin . If , the query returns an available key ; otherwise, it returns a random number. |
| Corrupt() query is executed as follows. If , the query outputs password . If , the query outputs parameters stored in . If , the query outputs biometrics . |
| Execute(, ) query is executed in succession with execution of Send(Ç, ) query. It is presented as follows. sends to and sends to . we have ← Send(, start), ← Send(, ) At last, and are returned. |
Based on the logical procedure of the protocol, the Send query is simulated as follows.
|
| Attributes | [21] | [23] | [25] | [26] | [27] | [28] | [29] | [30] | [31] | [36] | [37] | Mine |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Resists replay attacks | O | O | O | O | O | O | O | O | O | O | O | O |
| Resists MITM attacks | O | O | O | O | O | O | O | O | O | O | O | O |
| Resists online password guessing attacks | – | O | O | O | O | O | O | O | O | O | O | O |
| Resists offline password guessing attacks | – | O | O | O | O | O | O | O | O | O | O | O |
| Resists impersonation attacks | O | O | O | O | O | O | O | O | O | O | O | O |
| Resists lost sequencer or smart card attacks | O | O | – | O | – | – | O | X | X | O | O | O |
| Resists desynchronization attacks | O | O | O | O | O | O | O | X | O | X | O | O |
| Resists privileged insider attacks | O | O | O | O | O | O | O | O | O | O | O | O |
| Resists DoS attacks | O | O | O | O | O | O | O | O | O | O | O | O |
| Provides mutual authentication | O | O | O | O | O | O | O | O | O | O | O | O |
| Provides user anonymity | O | O | O | O | O | O | O | X | X | O | O | O |
| Provides user untraceability | O | O | O | O | O | X | O | O | O | X | O | O |
| Provides message unlinkability | O | O | O | O | O | X | O | O | O | X | O | O |
| Provides perfect forward secrecy | O | O | O | O | O | O | O | O | O | O | O | O |
| Provides perfect backward secrecy | O | O | O | O | O | O | O | O | O | O | O | O |
| Provides password update | – | O | O | X | O | O | O | X | X | O | O | O |
| Provides biometrics update | – | – | – | – | – | – | O | X | X | – | O | O |
| Provides three-factor authentication | X | X | X | X | X | X | O | O | O | X | O | O |
| Provides SD-SSO | X | X | X | X | X | X | X | X | X | X | X | O |
| Provides mathematics-based security proof | X | X | O | O | O | X | O | X | O | X | O | O |
| Provides group-based dynamic services | X | X | X | X | X | X | X | X | X | X | X | O |
| Provides LOC-based U-healthcare application | X | X | X | X | X | X | X | X | X | X | O | O |
| Supports patient-centric service | O | X | O | X | O | O | X | O | O | O | X | O |
| Notation | Operation | Computation Time (ms) |
|---|---|---|
| Hash function | ≈0.00069 | |
| EC point addition | ≈0.0069 | |
| EC point multiplication | ≈0.508 | |
| Symmetric encryption or decryption | ≈0.00054 | |
| Modular squaring | ≈0.00069 | |
| Square root module 𝑁 | ≈1.169 | |
| Chebyshev chaotic polynomial mapping | ≈0.02881 |
| Protocols | Total Computation Time (ms) | |||||
|---|---|---|---|---|---|---|
| Computation Complexities | Computation Time (ms) | Computation Complexities | Computation Time (ms) | |||
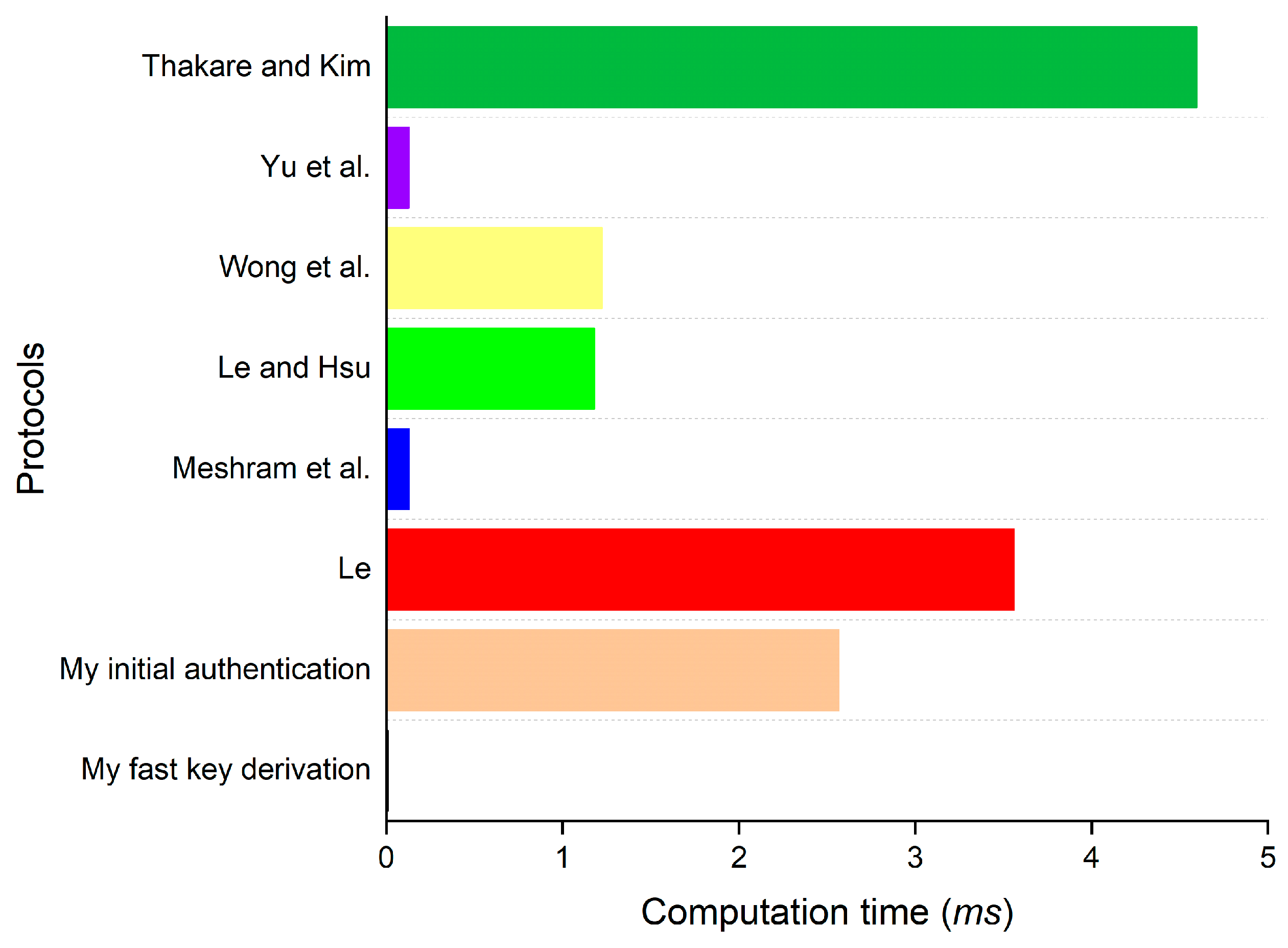
| Thakare and Kim [28] | + | ≈2.04028 | + + | ≈2.55794 | ≈4.59822 | |
| Yu et al. [29] | + | ≈0.06452 | + | ≈0.06314 | ≈0.12766 | |
| Wong et al. [30] | ≈0.04953 | ≈1.17491 | ≈1.22444 | |||
| Le and Hsu [31] | + + | ≈0.00744 | + | ≈1.17353 | ≈1.18097 | |
| Meshram et al. [36] | + | ≈0.06521 | + | ≈0.06383 | ≈0.12904 | |
| Le [37] | + | ≈2.03530 | + | ≈1.52592 | ≈3.56122 | |
| Mine | Initial authentication | + | ≈1.53987 | + | ≈1.02704 | ≈2.56691 |
| Fast key derivation | + | ≈0.00261 | + | ≈0.00675 | ≈0.00936 | |
| Parameters | Length (Bits) |
|---|---|
| Asymmetric encryption or decryption (e.g., Rabin system) | 1024 |
| Chebyshev polynomial | 1024 |
| Symmetric encryption or decryption | 256 |
| Identity | 128 |
| Password | 128 |
| Biometrics | 128 |
| Random number | 160 |
| Hash value | 160 |
| EC point multiplication | 320 |
| Timestamp | 32 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Le, T.-V. Securing Group Patient Communication in 6G-Aided Dynamic Ubiquitous Healthcare with Real-Time Mobile DNA Sequencing. Bioengineering 2023, 10, 839. https://doi.org/10.3390/bioengineering10070839
Le T-V. Securing Group Patient Communication in 6G-Aided Dynamic Ubiquitous Healthcare with Real-Time Mobile DNA Sequencing. Bioengineering. 2023; 10(7):839. https://doi.org/10.3390/bioengineering10070839
Chicago/Turabian StyleLe, Tuan-Vinh. 2023. "Securing Group Patient Communication in 6G-Aided Dynamic Ubiquitous Healthcare with Real-Time Mobile DNA Sequencing" Bioengineering 10, no. 7: 839. https://doi.org/10.3390/bioengineering10070839
APA StyleLe, T.-V. (2023). Securing Group Patient Communication in 6G-Aided Dynamic Ubiquitous Healthcare with Real-Time Mobile DNA Sequencing. Bioengineering, 10(7), 839. https://doi.org/10.3390/bioengineering10070839