Multi-User Nonlinear Optical Cryptosystem Based on Polar Decomposition and Fractional Vortex Speckle Patterns
Abstract
1. Introduction
2. Theoretical Background and Methodology
2.1. Polar Decomposition (PD)
2.2. Generation of FOVS
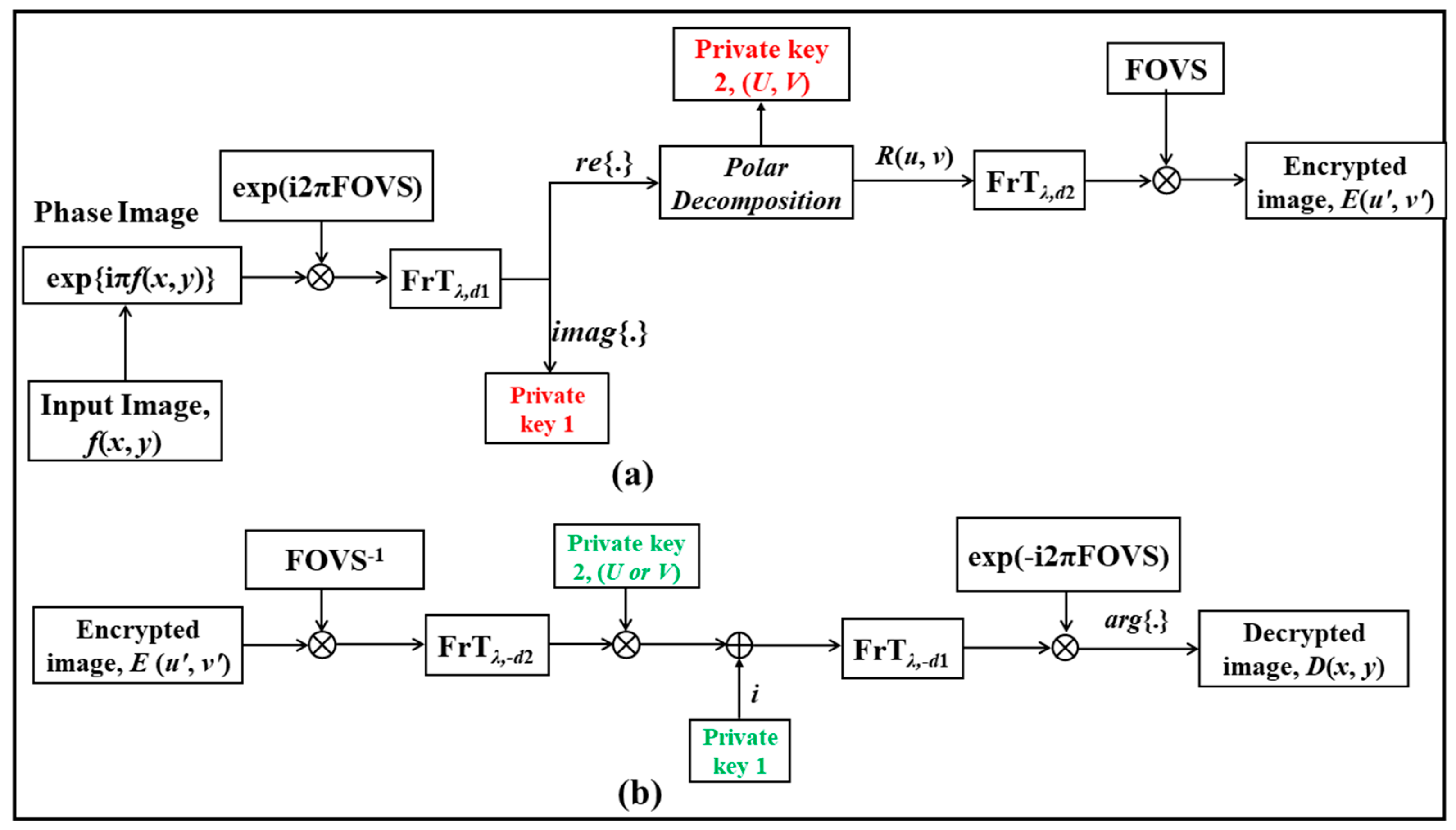
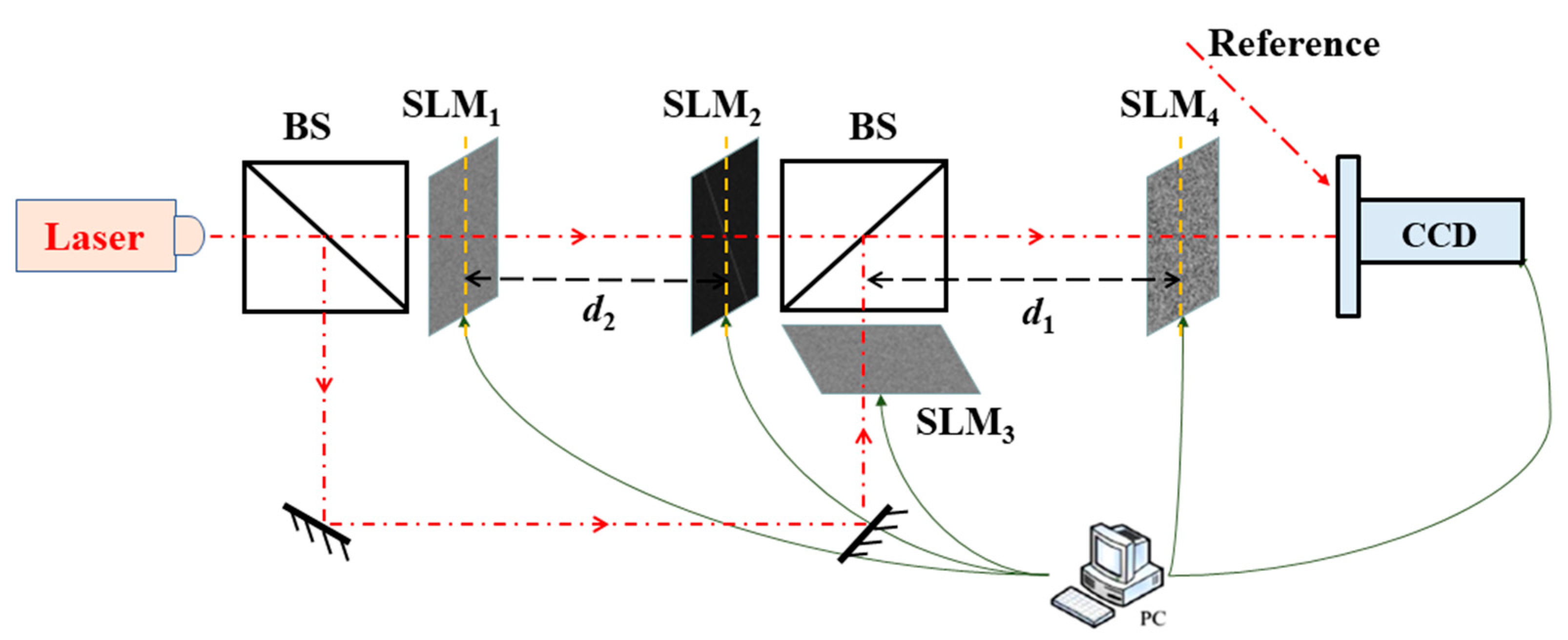
2.3. Proposed Cryptosystem
- (a)
- First, the input plaintext, , is phase encoded as and modulated with a fractional optical vortex speckle (FOVS) phase mask.
- (b)
- Then, the real and imaginary parts of are separated, i.e., re{A′(x′, y′)} and imag{A′(x′, y′)}. The imaginary part, imag{A′(x′, y′)}, is reserved as the first private key and the real part, re{A′(x, y)}, is further processed using polar decomposition to obtain two more private keys as discussed in Section 2.1.
- (c)
- R(x′, y′) is then Fresnel propagated to a distance d2 to obtain the complex wavefront B(x″, y″) as follows:
- (d)
- This complex image is further modulated with the amplitude mask FOVS to obtain the final encrypted image, E(x″, y″), as follows:
3. Results
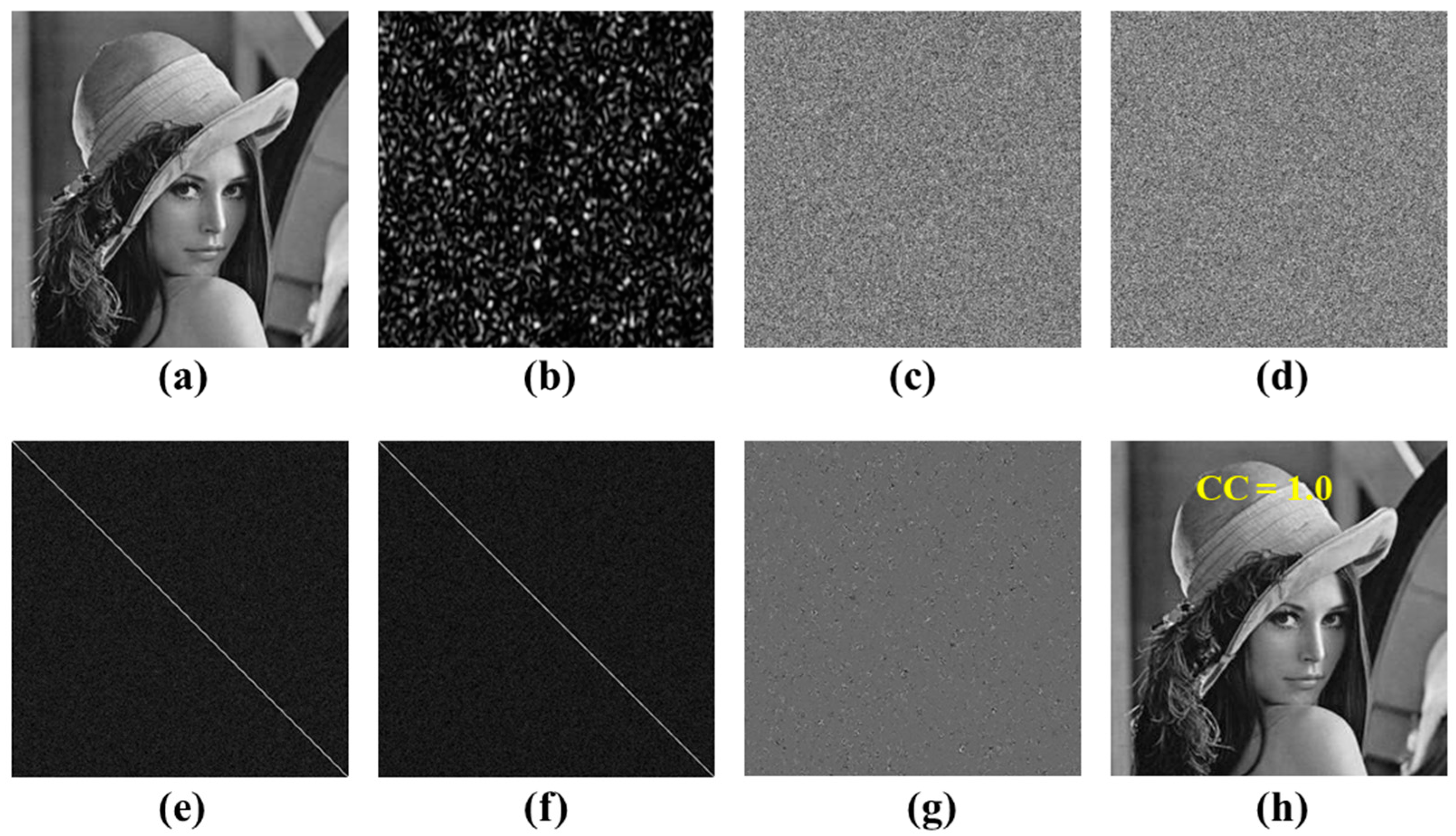
3.1. Encryption and Decryption Results
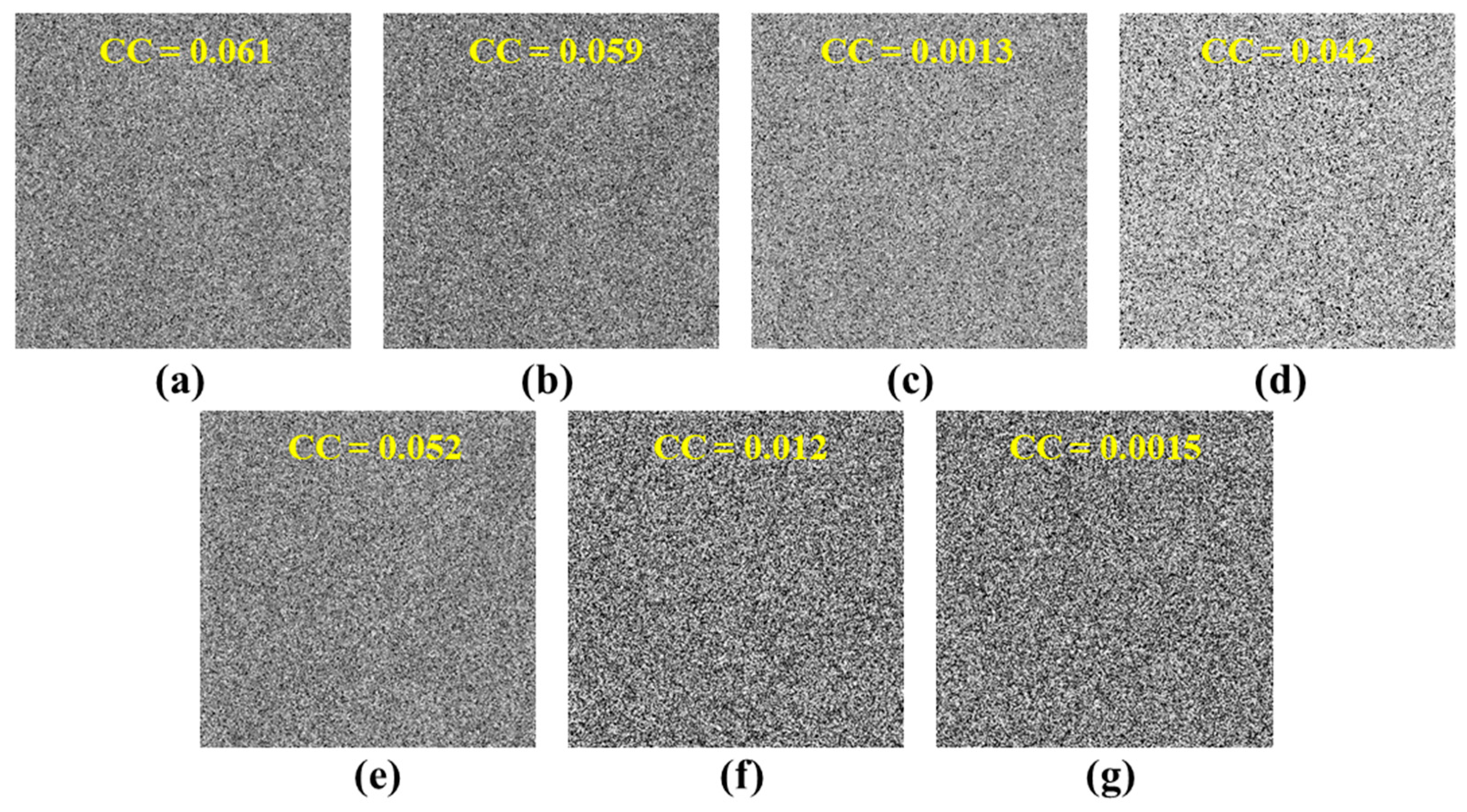
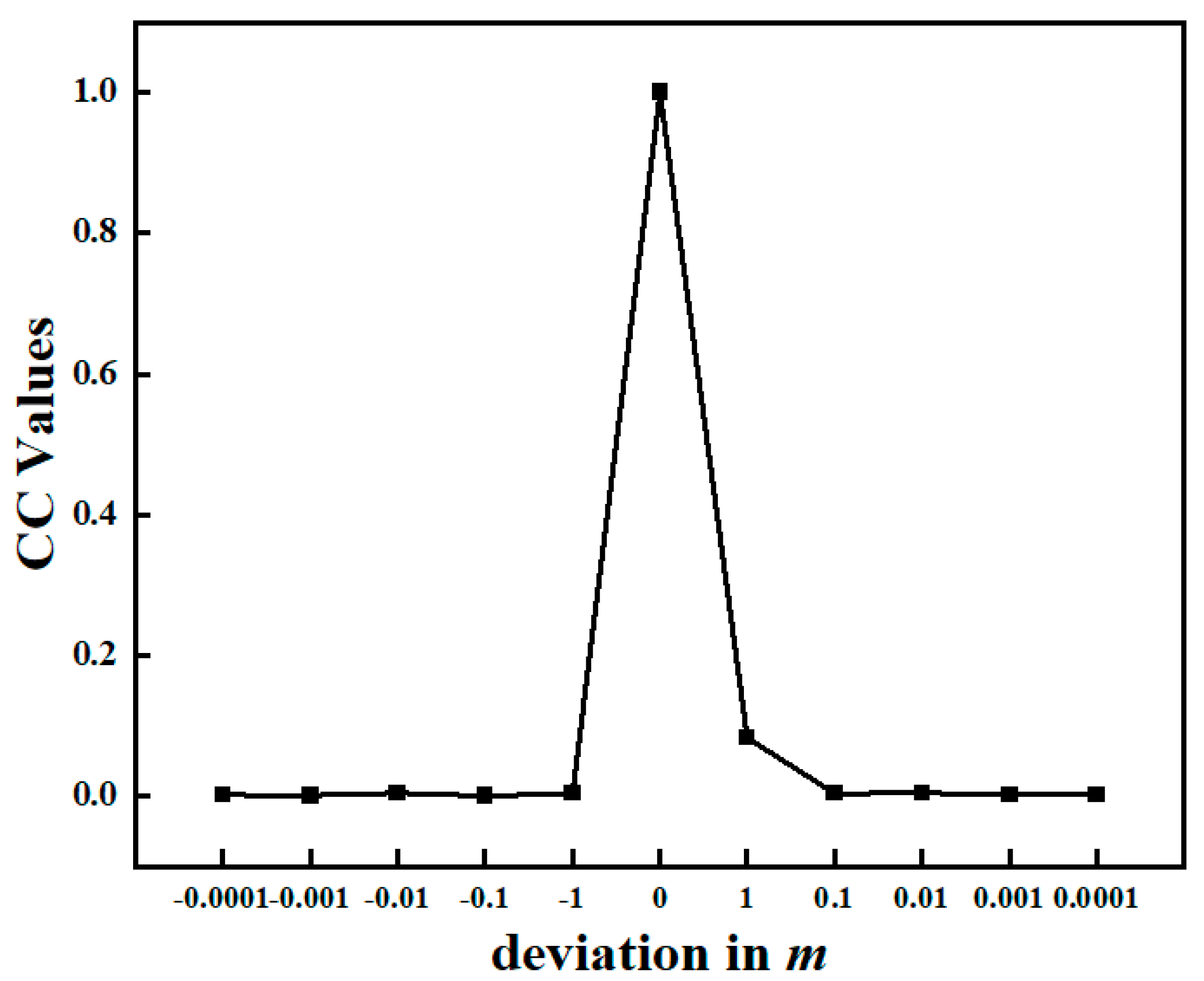
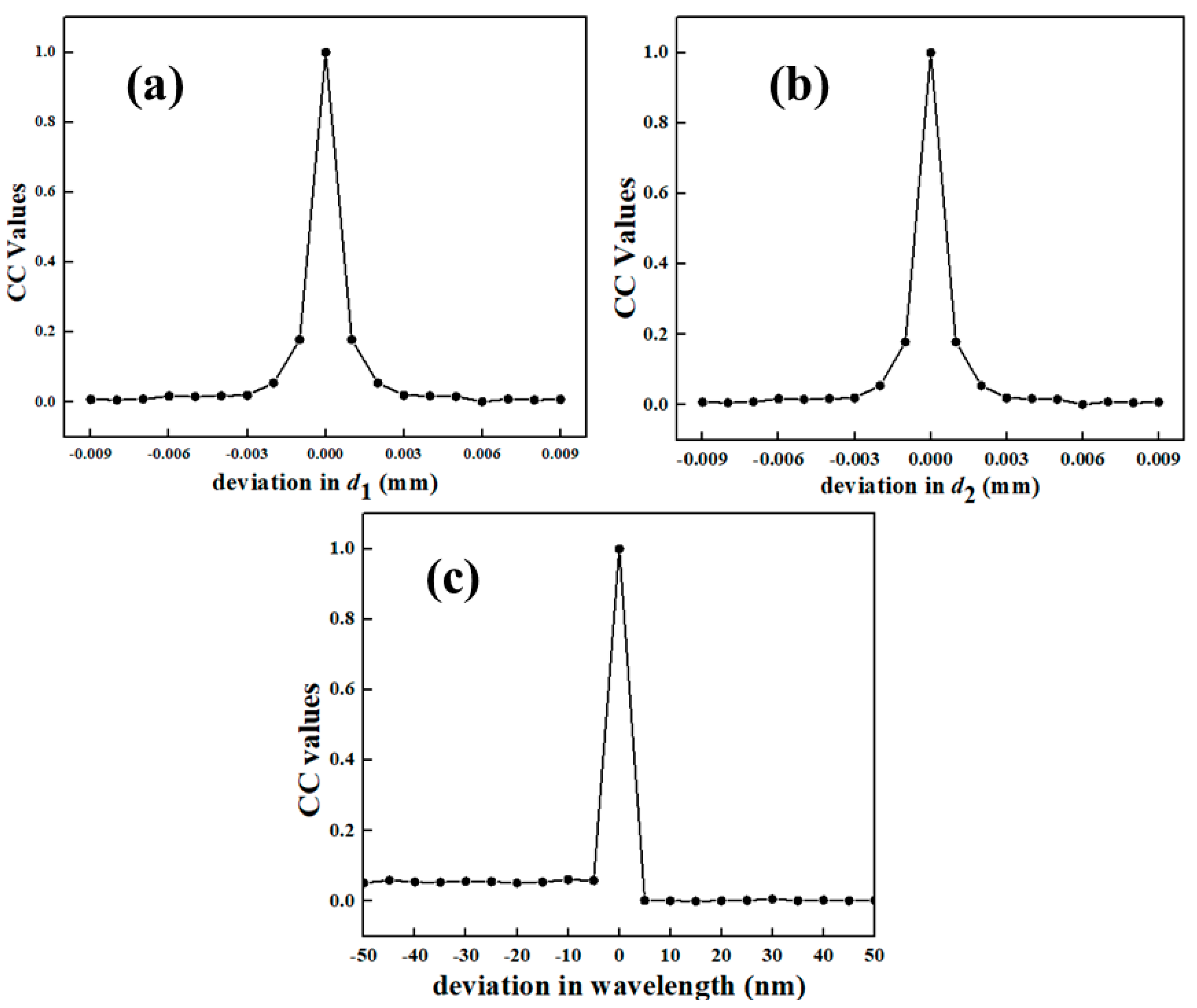
3.2. Key Sensitivity Analysis
3.3. Attack Analysis
3.3.1. Contamination Attacks
3.3.2. Known-Plaintext Attack
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Chen, W.; Javidi, B.; Chen, X. Advances in optical security systems. Adv. Opt. Photon. 2014, 6, 120–155. [Google Scholar] [CrossRef]
- Javidi, B.; Carnicer, A.; Yamaguchi, M.; Nomura, T.; Pérez-Cabré, E.; Millán, M.S.; Nishchal, N.K.; Torroba, R.; Fredy Barrera, J.; He, W.; et al. Roadmap on optical security. J. Opt. 2016, 18, 083001. [Google Scholar] [CrossRef]
- Refregier, P.; Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef] [PubMed]
- Unnikrishnan, G.; Joseph, J.; Singh, K. Optical encryption system that uses phase conjugation in a photorefractive crystal. Appl. Opt. 1998, 37, 8181–8186. [Google Scholar] [CrossRef]
- Unnikrishnan, G.; Joseph, J.; Singh, K. Optical encryption by double-random phase encoding in the fractional Fourier domain. Opt. Lett. 2000, 25, 887–889. [Google Scholar] [CrossRef] [PubMed]
- Situ, G.; Zhang, J. Double random-phase encoding in the Fresnel domain. Opt. Lett. 2004, 29, 1584–1586. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Zhao, D. Optical image encryption with simplified fractional Hartley transform. Chin. Phys. Lett. 2008, 25, 2477–2480. [Google Scholar]
- Hennelly, B.; Sheridan, J.T. Optical image encryption by random shifting in fractional Fourier domains. Opt. Lett. 2003, 28, 269–271. [Google Scholar] [CrossRef]
- Peng, X.; Zhang, P.; Wei, H.; Yu, B. Known-plaintext attack on optical encryption based on double random phase keys. Opt. Lett. 2006, 31, 1044–1046. [Google Scholar] [CrossRef] [PubMed]
- Peng, X.; Wei, H.; Zhang, P. Chosen-plaintext attack on lens less double-random phase encoding in the Fresnel domain. Opt. Lett. 2006, 31, 3261–3263. [Google Scholar] [CrossRef]
- Carnicer, A.; Montes-Usategui, M.; Arcos, S.; Juvells, I. Vulnerability to chosen-ciphertext attacks of optical encryption schemes based on double random phase keys. Opt. Lett. 2005, 30, 1644–1646. [Google Scholar] [CrossRef] [PubMed]
- Qin, W.; Peng, X. Asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt. Lett. 2010, 35, 118–120. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Zhao, D. A special attack on the asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt. Commun. 2012, 285, 1078–1081. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, B. Optical image encryption based on interference. Opt. Lett. 2008, 33, 2443–2445. [Google Scholar] [CrossRef] [PubMed]
- Niu, C.H.; Wang, X.L.; Lv, N.G.; Zhou, Z.H.; Li, X.Y. An encryption method with multiple encrypted keys based on interference principle. Opt. Express 2010, 18, 7827–7834. [Google Scholar] [CrossRef] [PubMed]
- Kumar, R.; Bhaduri, B. Optical image encryption using Kronecker product and hybrid phase masks. Opt. Laser Technol. 2017, 95, 51–55. [Google Scholar] [CrossRef]
- Kumar, R.; Sheridan, J.T.; Bhaduri, B. Nonlinear double image encryption using 2D non-separable linear canonical transform and phase retrieval algorithm. Opt. Laser Technol. 2018, 107, 353–360. [Google Scholar] [CrossRef]
- Chen, W.; Chen, X.; Sheppard, C.J.R. Optical image encryption based on diffractive imaging. Opt. Lett. 2010, 35, 3817–3819. [Google Scholar] [CrossRef]
- Rajput, S.K.; Nishchal, N.K. Image encryption using polarized light encoding and amplitude and phase truncation in the Fresnel domain. Appl. Opt. 2013, 52, 4343–4352. [Google Scholar] [CrossRef]
- Li, H. Image encryption based on gyrator transform and two-step phase-shifting interferometry. Opt. Lasers Eng. 2009, 47, 45–50. [Google Scholar] [CrossRef]
- Nishchal, N.K.; Joseph, J.; Singh, K. Securing information using fractional Fourier transform in digital holography. Opt. Commun. 2004, 235, 253–359. [Google Scholar] [CrossRef]
- Wu, J.; Liu, W.; Liu, Z.; Liu, S. Cryptanalysis of an asymmetric optical cryptosystem based on coherent superposition and equal modulus decomposition. Appl. Opt. 2015, 54, 8921–8924. [Google Scholar] [CrossRef] [PubMed]
- Kumar, R.; Bhaduri, B.; Quan, C. Asymmetric optical image encryption using Kolmogorov phase screens and equal modulus decomposition. Opt. Eng. 2017, 56, 113109. [Google Scholar] [CrossRef]
- Abuturab, M.R. Asymmetric multiple information cryptosystem based on chaotic spiral phase mask and random spectrum decomposition. Opt. Laser Technol. 2018, 98, 298–308. [Google Scholar] [CrossRef]
- Chen, H.; Zhu, L.; Liu, Z.; Tanougast, C.; Liu, F.; Blondel, W. Optical single-channel color image asymmetric cryptosystem based on hyperchaotic system and random modulus decomposition in Gyrator domains. Opt. Lasers Eng. 2020, 124, 105809. [Google Scholar] [CrossRef]
- Kumar, R.; Bhaduri, B.; Nischal, N.K. Nonlinear QR code based optical image encryption using spiral phase transform, equal modulus decomposition and singular value decomposition. J. Opt. 2018, 20, 015701. [Google Scholar] [CrossRef]
- Chen, L.; He, B.; Chen, X.; Gao, X.; Liu, J. Optical image encryption based on multi-beam interference and common vector decomposition. Opt. Commun. 2016, 361, 6–12. [Google Scholar] [CrossRef]
- Kumar, R.; Quan, C. Asymmetric multi-user optical cryptosystem based on polar decomposition and Shearlet transform. Opt. Lasers Eng. 2019, 120, 118–126. [Google Scholar] [CrossRef]
- Sachin; Kumar, R.; Singh, P. Multiuser optical image authentication platform based on sparse constraint and polar decomposition in Fresnel domain. Phys. Scr. 2022, 47, 115101. [Google Scholar] [CrossRef]
- Cris, V.M.; Vardhan, H.; Prabhakar, S.; Kumar, R.; Reddy, S.G.; Choudhary, S.; Singh, R.P. An asymmetric optical cryptosystem using physically unclonable functions in the Fresnel domain. In Proceedings of the Holography Meets Advanced Manufacturing, University of Tartu, Tartu, Estonia, 20–22 February 2023; MDPI: Basel, Switzerland, 2023. [Google Scholar]
- Mosso, F.; Bolognini, N.; Pérez, D.G. Experimental optical encryption system based on a single-lens imaging architecture combined with a phase retrieval algorithm. J. Opt. 2015, 17, 065702. [Google Scholar] [CrossRef]
- Weng, D.; Zhu, N.; Wang, Y.; Xie, J.; Liu, J. Experimental verification of optical image encryption based on interference. Opt. Commun. 2011, 284, 2485–2487. [Google Scholar] [CrossRef]
- Li, J.; Shen, L.; Pan, Y.; Li, R. Optical image encryption and hiding based on a modified Mach-Zehnder interferometer. Opt. Express 2014, 22, 4849–4860. [Google Scholar] [CrossRef]
- Shen, X.; Dou, S.; Lei, M.; Chen, Y. Optical image encryption based on a joint Fresnel transform correlator with double optical wedges. Appl. Opt. 2016, 55, 8513–8522. [Google Scholar] [CrossRef] [PubMed]
- Zea, A.; Barrera, J.F.; Torroba, R. Experimental optical encryption of grayscale information. Appl. Opt. 2017, 56, 5883–5889. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Zhao, M.; Xing, Y.; Zhang, H.; Li, L.; Kim, S.; Zhou, X.; Wang, Q. Designing optical 3D images encryption and reconstruction using monospectral synthetic aperture integral imaging. Opt. Express 2018, 26, 11084–11099. [Google Scholar] [CrossRef]
- Rajput, S.K.; Matoba, O. Optical voice encryption based on digital holography. Opt. Lett. 2017, 42, 4619–4622. [Google Scholar] [CrossRef]
- Zhang, H.; Zeng, J.; Lu, X.; Wang, Z.; Zhao, C.; Cai, Y. Review on fractional vortex beam. Nanophotonics 2022, 11, 241–273. [Google Scholar] [CrossRef]
- Zeng, J.; Liu, X.; Wang, F.; Zhao, C.; Cai, Y. Partially coherent fractional vortex beam. Opt. Express 2018, 26, 26830–26844. [Google Scholar] [CrossRef]
- Kotlyar, V.V.; Kovalev, A.A.; Nalimov, A.G. Topological Charge of Optical Vortices, 1st ed.; CRC Press: Boca Raton, FL, USA, 2022. [Google Scholar]
- Shikder, A.; Nishchal, N.K. Measurement of the fractional charge of an optical vortex beam through interference fringe location. Appl. Opt. 2023, 62, D58–D67. [Google Scholar] [CrossRef]
- Higham, N.J. Computing the polar decomposition—With applications. SIAM J. Sci. Stat. Comput. 1986, 7, 1160–1174. [Google Scholar] [CrossRef]
- Oussama, N.; Assia, B.; Lemnouar, N. Secure image encryption scheme based on polar decomposition and chaotic map. Int. J. Inform. Commun. Technol. 2017, 10, 437–453. [Google Scholar] [CrossRef]
- Reddy, S.G.; Prabhakar, S.; Kumar, A.; Banerji, J.; Singh, R.P. Higher order optical vortices and formation of speckles. Opt. Lett. 2014, 39, 4364–4367. [Google Scholar] [CrossRef] [PubMed]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mandapati, V.C.; Vardhan, H.; Prabhakar, S.; Sakshi; Kumar, R.; Reddy, S.G.; Singh, R.P.; Singh, K. Multi-User Nonlinear Optical Cryptosystem Based on Polar Decomposition and Fractional Vortex Speckle Patterns. Photonics 2023, 10, 561. https://doi.org/10.3390/photonics10050561
Mandapati VC, Vardhan H, Prabhakar S, Sakshi, Kumar R, Reddy SG, Singh RP, Singh K. Multi-User Nonlinear Optical Cryptosystem Based on Polar Decomposition and Fractional Vortex Speckle Patterns. Photonics. 2023; 10(5):561. https://doi.org/10.3390/photonics10050561
Chicago/Turabian StyleMandapati, Vinny Cris, Harsh Vardhan, Shashi Prabhakar, Sakshi, Ravi Kumar, Salla Gangi Reddy, Ravindra P. Singh, and Kehar Singh. 2023. "Multi-User Nonlinear Optical Cryptosystem Based on Polar Decomposition and Fractional Vortex Speckle Patterns" Photonics 10, no. 5: 561. https://doi.org/10.3390/photonics10050561
APA StyleMandapati, V. C., Vardhan, H., Prabhakar, S., Sakshi, Kumar, R., Reddy, S. G., Singh, R. P., & Singh, K. (2023). Multi-User Nonlinear Optical Cryptosystem Based on Polar Decomposition and Fractional Vortex Speckle Patterns. Photonics, 10(5), 561. https://doi.org/10.3390/photonics10050561





