Numerical Simulation Study on Reverse Source Tracing for Heating Pipeline Network Leaks Based on Adjoint Equations
Abstract
1. Introduction
2. Literature Review
- (1)
- To investigate the settings of pressure wave monitoring points, time steps, and corresponding boundary conditions for complex pipe networks within OpenFOAM 5.0.
- (2)
- To examine the construction of the adjoint equation within the PISO algorithm for complex pipe networks, transforming the reverse source tracing problem into a solution of the adjoint equation.
- (3)
- To explore how to calculate the time difference in pressure signal reception at various monitoring points based on the pressure waveforms obtained, determine the possible locations of leaks, and thereby study how to accurately locate the leak source.
- (4)
- Therefore, this paper applies the reverse source tracing technology based on the adjoint equation to water supply networks, aiming to more rapidly achieve leak detection and location in complex networks.
3. Methodology
3.1. Reverse Method
3.2. Experiments and Simulations
3.2.1. Experimental Framework
3.2.2. Simulations
3.2.3. Leak Detection and Correlation Analysis
3.2.4. Leak Location Identification
4. Results and Discussion
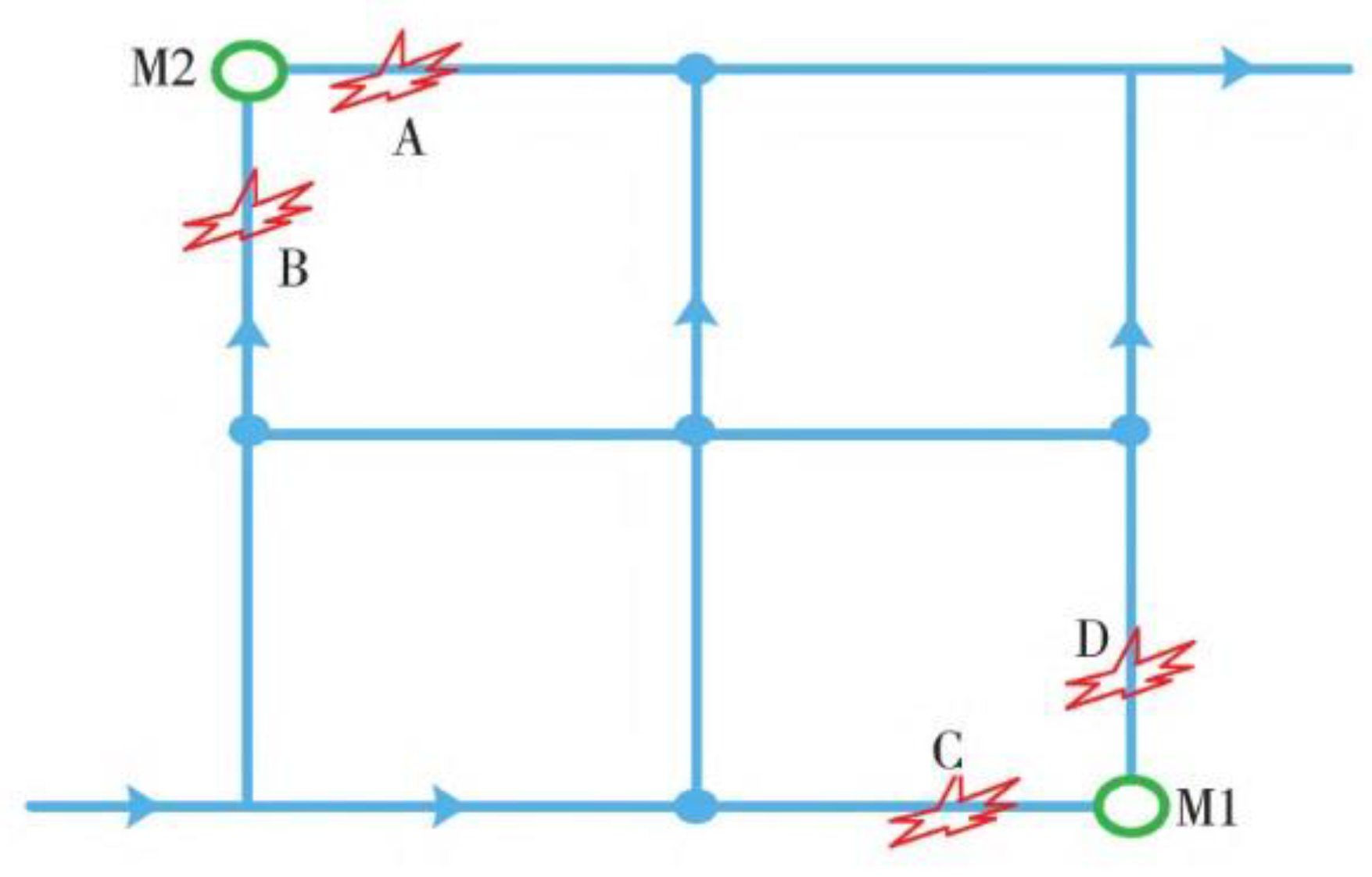
4.1. Leak Localization
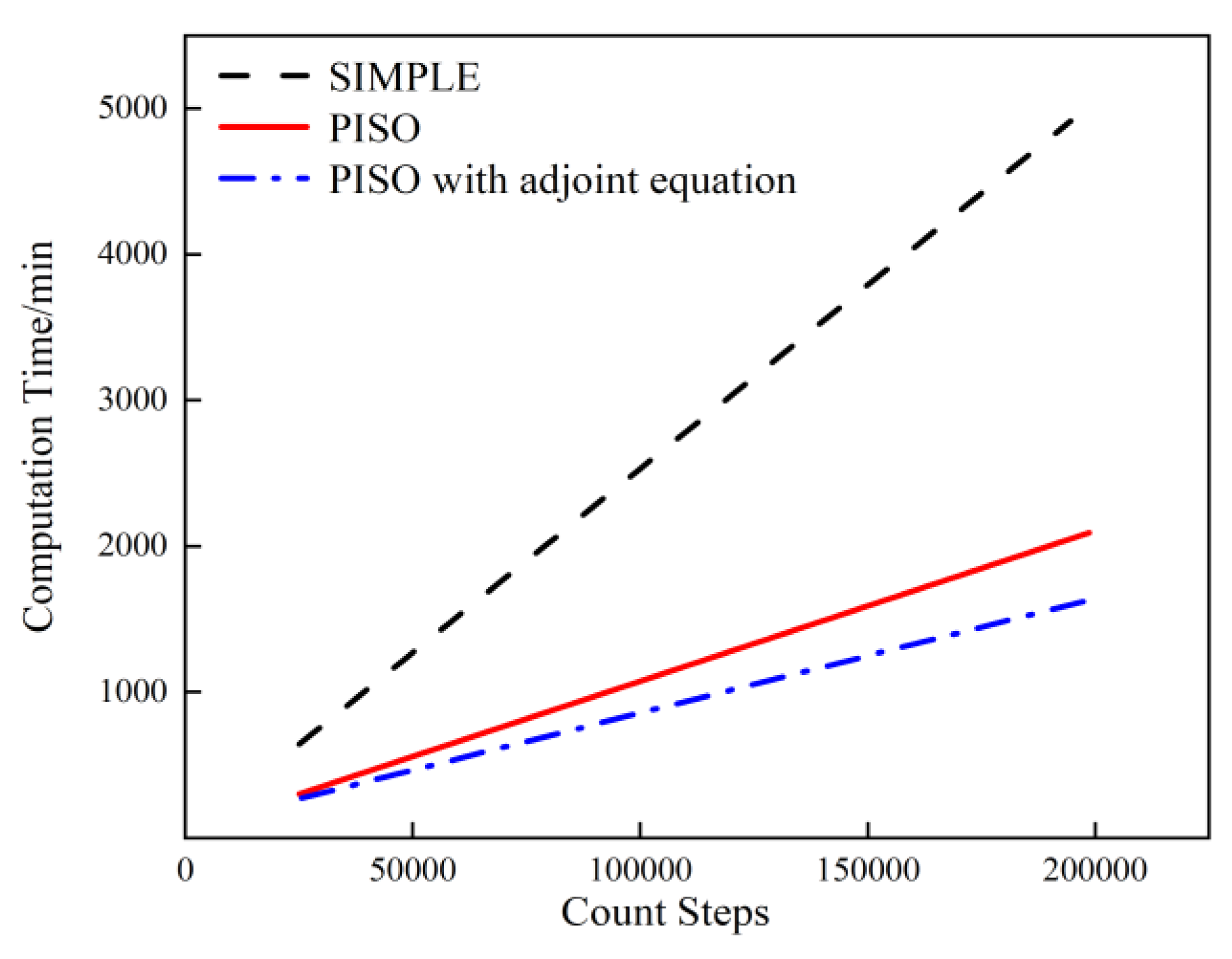
4.2. Algorithm Comparison
4.3. Experimental Validation
5. Conclusions
- Based on the forward pressure transport model, an objective function was introduced to combine the adjoint theory with the sensitivity analysis method to derive the forward adjoint equation. The sensitivity function was derived for pressure, and the adjoint operator was introduced to derive the transient flow field backward adjoint equation. The results prove that the backward tracing method can be used for pipeline leak detection.
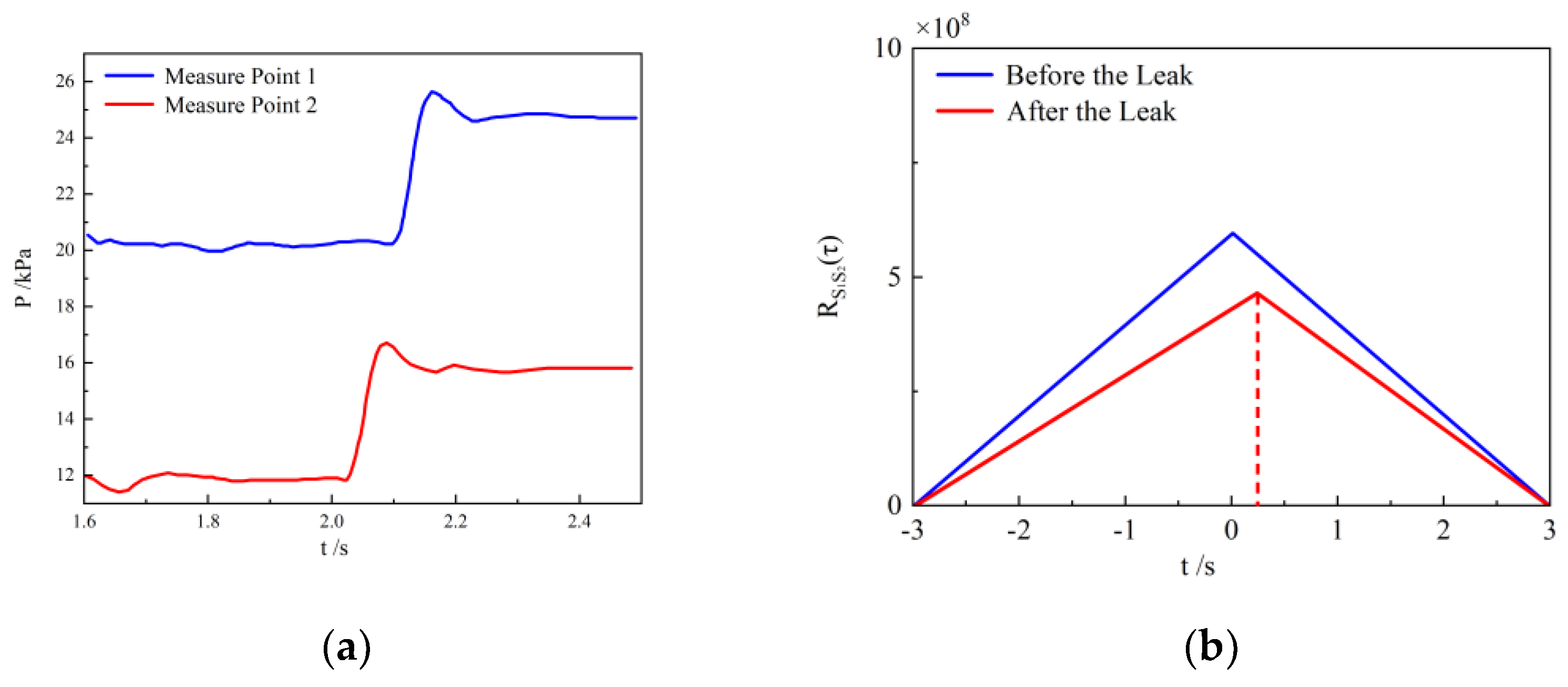
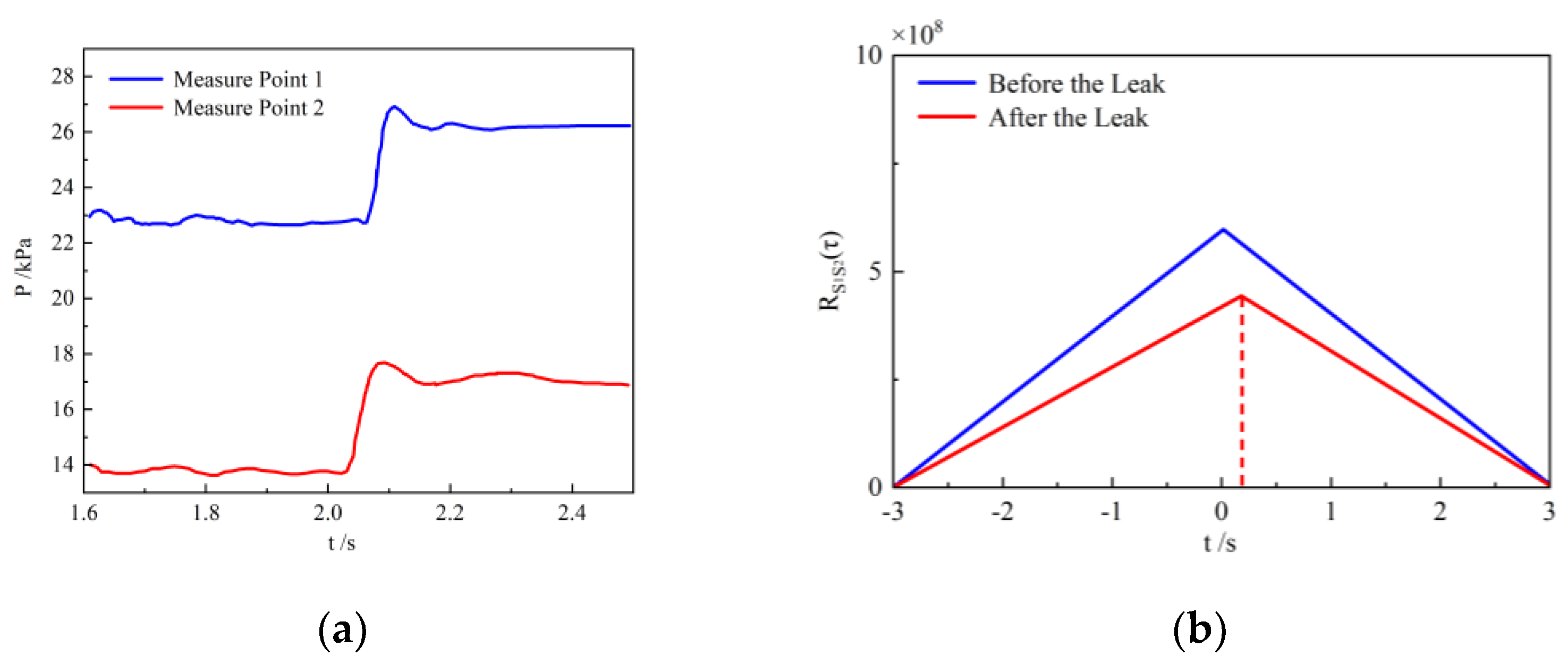
- Within OpenFOAM 5.0, the construction of the complex pipeline fluid flow numerical simulation model and the solution of the adjoint equation were completed. The pressure change at the leak hole during the leak was monitored, and a cross-correlation method was used for correlation analysis. It was found that after the pipeline leak, the maximum value of the signal correlation coefficient shifted near zero. Through the correlation comparison diagram, it can be seen that the emergence of pipeline leakage leads to a decrease in the maximum correlation coefficient value.
- The accuracy of the simulated leak location under different leak hole sizes and different inlet pressures was compared. The results showed that the accuracy of the location based on the backward tracing method was between 92%~96%, indicating that this method can be applied to complex pipeline leak detection and positioning.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Tu, R.; Jiao, Y.; Qiu, R.; Liao, Q.; Xu, N.; Du, J.; Liang, Y. Energy saving and consumption reduction in the transportation of petroleum products: A pipeline pricing optimization perspective. Appl. Energy 2023, 342, 121135. [Google Scholar] [CrossRef]
- Zhang, Z.; Xiang, S.; Yuan, Z.; Tang, H. A coupling prediction model of annular pressure build-up for deepwater oil and gas wells during transient-state testing. Geoenergy Sci. Eng. 2023, 230, 212162. [Google Scholar] [CrossRef]
- Su, W.; Li, J.; Lu, Z.; Jin, X.; Zhang, J.; Liu, Z.; Zhang, X. Performance analysis and optimization of a solar assisted heat pump-driven vacuum membrane distillation system for liquid desiccant regeneration. Energy Convers. Manag. 2024, 301, 118047. [Google Scholar] [CrossRef]
- Su, W.; Han, Y.; Liu, Z.; Jin, X.; Liu, Z.; Yang, D.; Zhang, X. Absorption heat pumps for low-grade heat utilization: A comprehensive review on working pairs, classification, system advances and applications. Energy Convers. Manag. 2024, 315, 118760. [Google Scholar] [CrossRef]
- Su, W.; Han, Y.; Jin, X.; Liu, Z.; Zhang, X. Energy, economic, and environmental evaluation of a GAX-based cross-type absorption-resorption heat pump. Energy Convers. Manag. 2024, 300, 117952. [Google Scholar] [CrossRef]
- Chen, X.; Liu, H.; Sun, X.; Zan, B.; Liang, M. Chloride corrosion behavior on heating pipeline made by AISI 304 and 316 in reclaimed water. RSC Adv. 2021, 11, 38765–38773. [Google Scholar] [CrossRef]
- Adedeji, K.B.; Hamam, Y.; Abe, B.T.; Abu-Mahfouz, A.M. Pressure Management Strategies for Water Loss Reduction in Large-Scale Water Piping Networks: A Review. In Advances in Hydroinformatics; Gourbesville, P., Cunge, J., Caignaert, G., Eds.; Springer: Singapore, 2018; pp. 465–480. [Google Scholar] [CrossRef]
- Latif, J.; Shakir, M.Z.; Edwards, N.; Jaszczykowski, M.; Ramzan, N.; Edwards, V. Review on condition monitoring techniques for water pipelines. Measurement 2022, 193, 110895. [Google Scholar] [CrossRef]
- Kim, M.-S.; Lee, S.-K. Detection of leak acoustic signal in buried gas pipe based on the time–frequency analysis. J. Loss Prev. Process Ind. 2009, 22, 990–994. [Google Scholar] [CrossRef]
- Bimpas, M.; Amditis, A.; Uzunoglu, N. Detection of water leaks in supply pipes using continuous wave sensor operating at 2.45 GHz. J. Appl. Geophys. 2010, 70, 226–236. [Google Scholar] [CrossRef]
- Bolotina, I.; Borikov, V.; Ivanova, V.; Mertins, K.; Uchaikin, S. Application of phased antenna arrays for pipeline leak detection. J. Pet. Sci. Eng. 2018, 161, 497–505. [Google Scholar] [CrossRef]
- Folkman, S.; Rice, J.; Sorenson, A.; Braithwaite, N. Survey of water main failures in the United States and Canada. J. AWWA 2012, 104, 70–79. [Google Scholar] [CrossRef]
- Parks, J. Water Loss Management and Customer Care. J. AWWA 2004, 96, 66–68. [Google Scholar] [CrossRef]
- Lambert, A.O. International Report: Water losses management and techniques. Water Supply 2002, 2, 1–20. [Google Scholar] [CrossRef]
- Nagaosa, R.S. A new numerical formulation of gas leakage and spread into a residential space in terms of hazard analysis. J. Hazard. Mater. 2014, 271, 266–274. [Google Scholar] [CrossRef]
- Sekhavati, J. Computational methods for pipeline leakage detection and localization: A review and comparative study. J. Loss Prev. Process Ind. 2022, 77, 104771. [Google Scholar] [CrossRef]
- Rajasekaran, U.; Kothandaraman, M. A Survey and Study of Signal and Data-Driven Approaches for Pipeline Leak Detection and Localization. J. Pipeline Syst. Eng. Pract. 2024, 15, 3124001. [Google Scholar] [CrossRef]
- Korlapati, N.V.S. Review and analysis of pipeline leak detection methods. J. Pipeline Sci. Eng. 2022, 2, 100074. [Google Scholar] [CrossRef]
- Datta, S. A review on different pipeline fault detection methods. J. Loss Prev. Process Ind. 2016, 41, 97–106. [Google Scholar] [CrossRef]
- Siebert, H.; Isermann, R. Pipeline leak detection and location by on-line-correlation with a process computer. Automatic 1977, 25, 69–74. [Google Scholar]
- Isermann, R. Proeess fault detection based on modeling and estimation methods. Automatic 1984, 20, 38–40. [Google Scholar] [CrossRef]
- Billmann, L.; Isermann, R. Leak Detection Methods for Pipelines. IFAC Proc. Vol. 1984, 17, 1813–1818. [Google Scholar] [CrossRef]
- Imoto, T.; Nakai, Y. Discrimination of peripheral and central vestibular disorders by means of a quantitative statistical method. J. Biomed. Eng. 1984, 6, 40–44. [Google Scholar] [CrossRef]
- Digernes, T. Real-Time Failure-Detection and Identification Applied to Supervision of Oil Transport in Pipelines. MIC 1980, 1, 39–49. [Google Scholar] [CrossRef]
- Benkherouf, A.; Allidina, A.Y. Leak detection and location in gas pipelines. IEE Proc. D Control Theory Appl. 1988, 135, 142. [Google Scholar] [CrossRef]
- Zhang, X. Statistical leak detection in gas and liquid pipelines. Pipes Pipelines Int. 1993, 38, 26–29. [Google Scholar]
- Zhang, X. Statistieal methods for detection and localization of leak in pipelines. Offshore Mech. Arctie Eng. Conf. 1992, 38, 85–92. [Google Scholar]
- Liou, J.C.P. Pipeline Integrity Monitoring Using System Impulse Response. In Volume 2: Design, Construction, and Operation Innovations; Compression and Pump Technology; SCADA, Automation, and Measurement; System Simulation; Geotechnical and Environmental; American Society of Mechanical Engineers: Calgary, AB, Canada, 1996; pp. 1137–1142. [Google Scholar] [CrossRef]
- Ferrante, M.; Brunone, B.; Rossetti, A.G. Harmonic analysis of pressure signal during transients for leak detection in pressurized pipes. In Proceedings of the 4th International Conference on Water Pipeline Systems, York, UK, 28–30 March 2001. [Google Scholar]
- Vítkovský, J.P.; Simpson, A.R.; Lambert, M.F. Leak Detection and Calibration Using Transients and Genetic Algorithms. J. Water Resour. Plann. Manag. 2000, 126, 262–265. [Google Scholar] [CrossRef]
- Verde, C. Leakage location in pipelines by minimal order nonlinear observer. In Proceedings of the 2001 American Control Conference. (Cat. No.01CH37148), Arlington, VA, USA, 25–27 June 2001; IEEE: New York, NY, USA, 2001; Volume 2, pp. 1733–1738. [Google Scholar] [CrossRef]
- Mpesha, W.; Hanif Chaudhry, M.; Gassman, S.L. Leak detection in pipes by frequency response method using a step excitation. J. Hydraul. Res. 2002, 40, 55–62. [Google Scholar] [CrossRef]
- Hemerly Costa, A.L.; Miranda De Souza, J.N.; De Medeiros, J.L. Detection, Localization and Quantification of Leaks in Pipeline Networks Using a Parameter Estimation Approach. In Proceedings of the 4th International Pipeline Conference, Parts A and B, Calgary, AB, Canada, 30 September–3 October 2002; ASMEDC: New York, NY, USA, 2002; pp. 1029–1035. [Google Scholar] [CrossRef]
- Ferrante, M.; Brunone, B. Pipe system diagnosis and leak detection by unsteady-state tests. 2. Wavelet analysis. Adv. Water Resour. 2003, 26, 107–116. [Google Scholar] [CrossRef]
- Covas, D.; Ramos, H.; Graham, N.; Maksimovic, C. Application of hydraulic transients for leak detection in water supply systems. Water Supply 2004, 4, 365–374. [Google Scholar] [CrossRef]
- Reddy, H.P.; Narasimhan, S.; Bhallamudi, S.M. Simulation and State Estimation of Transient Flow in Gas Pipeline Networks Using a Transfer Function Model. Ind. Eng. Chem. Res. 2006, 45, 3853–3863. [Google Scholar] [CrossRef]
- Taghvaei, M.; Beck, S.B.M.; Boxall, J.B. Leak and feature detection in a water distribution network. In Proceedings of the 10th BHR Group International Conference in the Pressure Surges Series, Edinburgh, UK, 14–16 May 2008; pp. 125–135. [Google Scholar]
- Ferraz, I.N.; Garcia, A.C.B.; Bernardini, F.C. Artificial Neural Networks Ensemble Used for Pipeline Leak Detection Systems. In Proceedings of the 2008 7th International Pipeline Conference, Calgary, AB, Canada, 29 September–3 October 2008; ASMEDC: New York, NY, USA, 2008; Volume 1, pp. 739–747. [Google Scholar] [CrossRef]
- Ahadi, M.; Bakhtiar, M.S. Leak detection in water-filled plastic pipes through the application of tuned wavelet transforms to Acoustic Emission signals. Appl. Acoust. 2010, 71, 634–639. [Google Scholar] [CrossRef]
- Ayala-Cabrera, D.; Herrera, M.; Montalvo, I.; Pérez-García, R. Towards the visualization of water supply system components with GPR images. Math. Comput. Model. 2011, 54, 1818–1822. [Google Scholar] [CrossRef][Green Version]
- Wachla, D.; Przystalka, P.; Moczulski, W. A Method of Leakage Location in Water Distribution Networks using Artificial Neuro-Fuzzy System. IFAC-Pap. 2015, 48, 1216–1223. [Google Scholar] [CrossRef]
- Moser, G.; German Paal, S.; Smith, I.F.C. Performance comparison of reduced models for leak detection in water distribution networks. Adv. Eng. Inform. 2015, 29, 714–726. [Google Scholar] [CrossRef]
- Bermúdez, J.-R.; López-Estrada, F.-R.; Besançon, G.; Valencia-Palomo, G.; Torres, L.; Hernández, H.-R. Modeling and Simulation of a Hydraulic Network for Leak Diagnosis. MCA 2018, 23, 70. [Google Scholar] [CrossRef]
- Yang, X.; Fang, H.; Yu, X.; Li, S.; Liu, H. Study on the mechanism of vibration signal generation in water supply pipeline leaks. Measurement 2024, 229, 114415. [Google Scholar] [CrossRef]
- Fu, H.; Yang, L.; Liang, H.; Wang, S.; Ling, K. Diagnosis of the single leakage in the fluid pipeline through experimental study and CFD simulation. J. Pet. Sci. Eng. 2020, 193, 107437. [Google Scholar] [CrossRef]
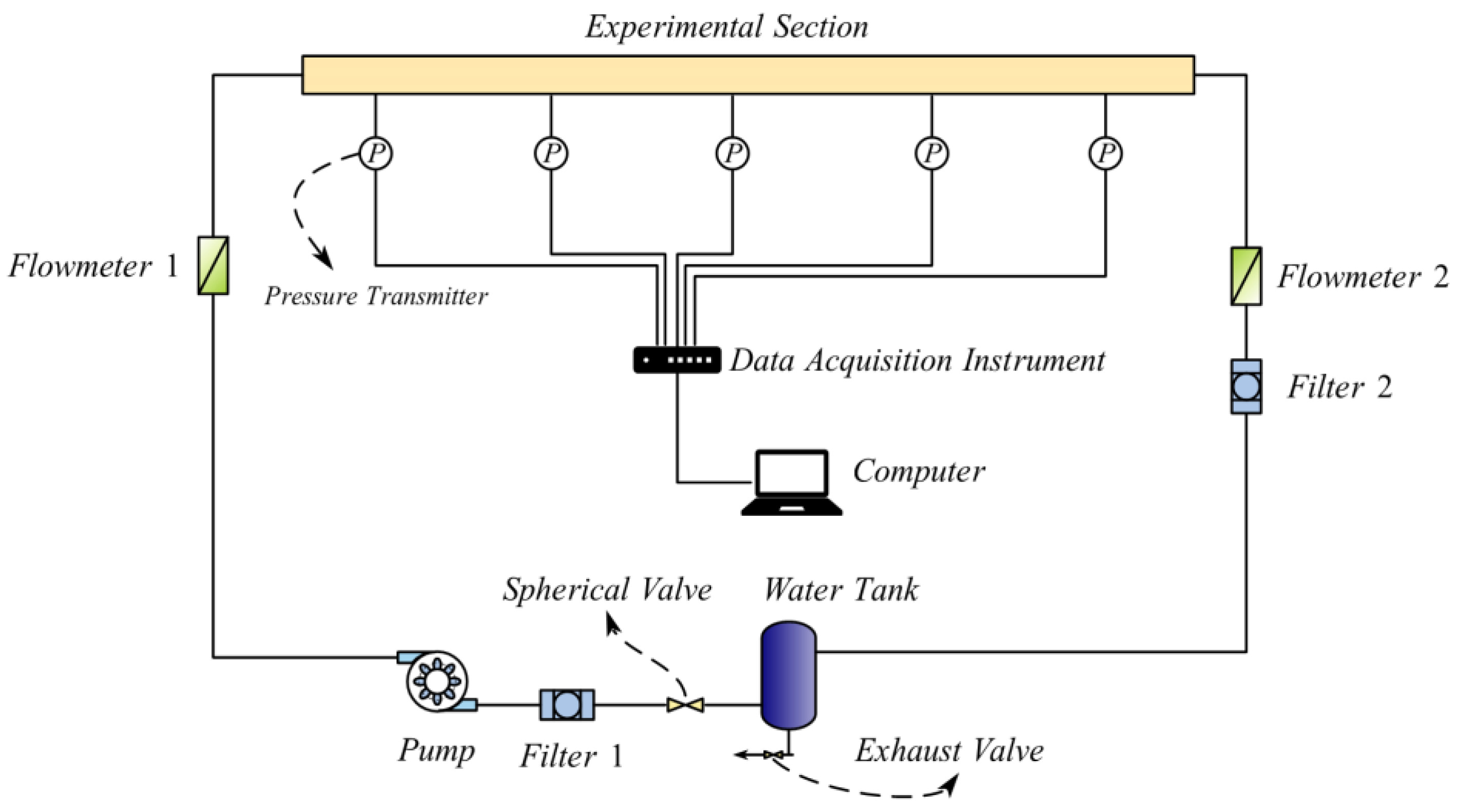

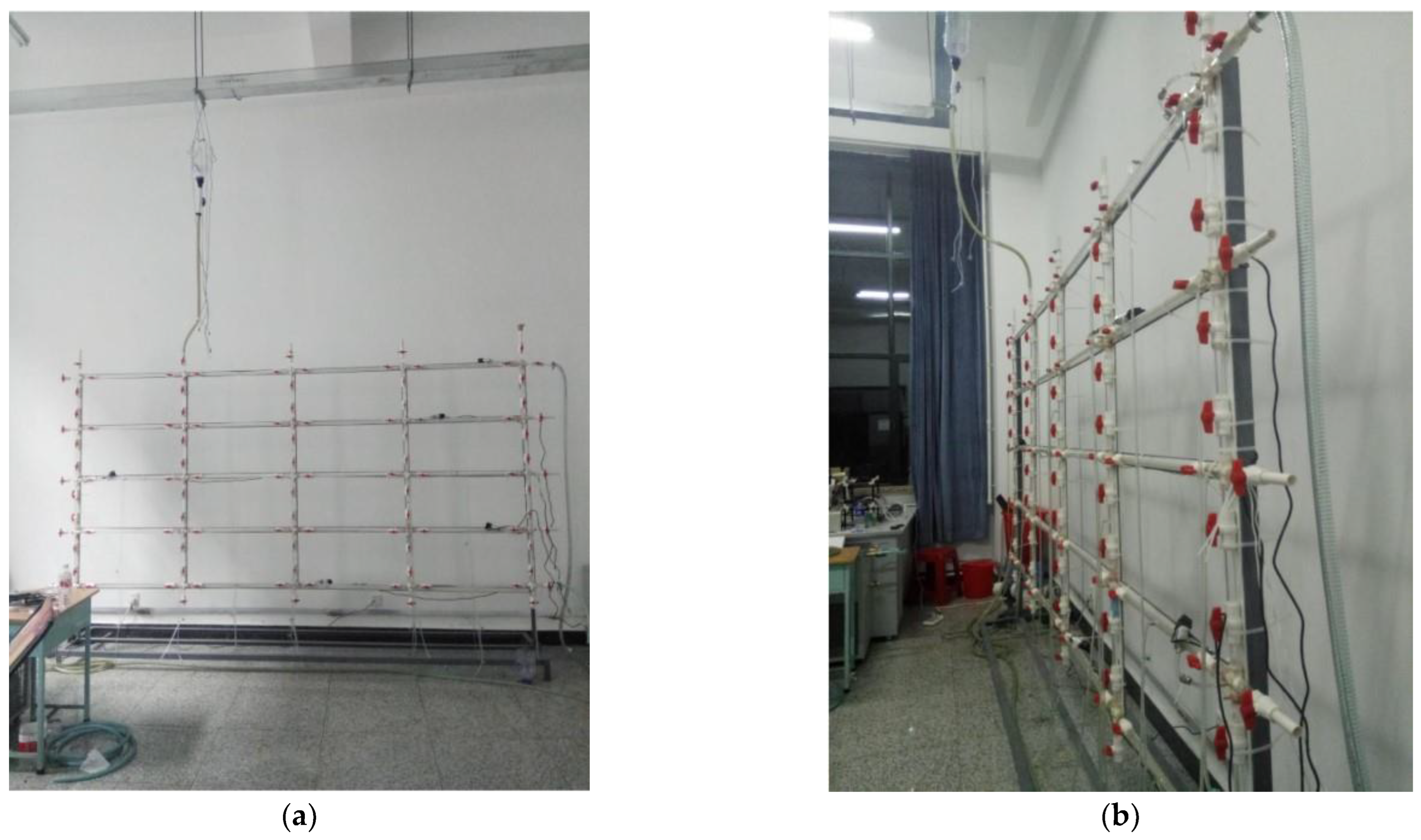
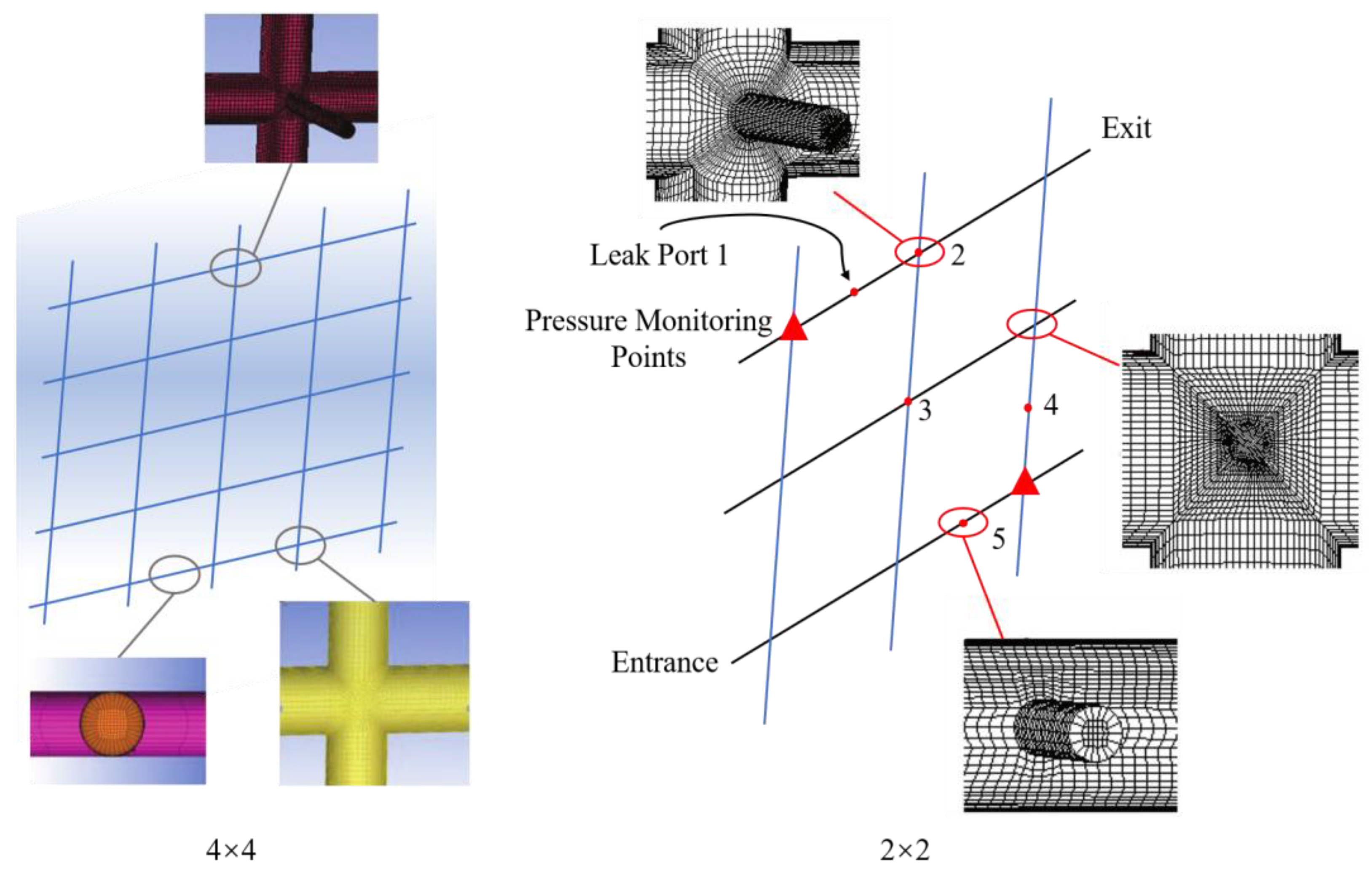

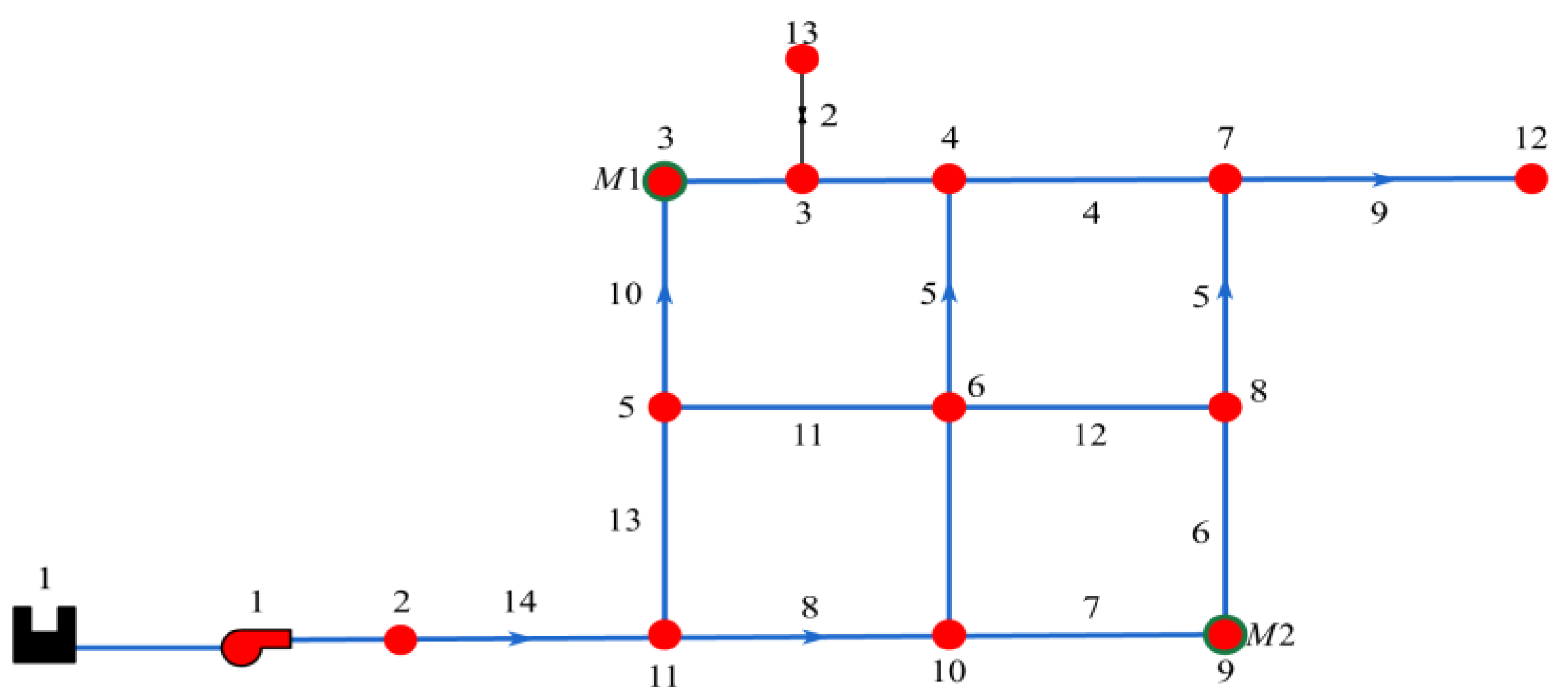





| Researchers | Methods for Pipe Leak Detection | Characteristics of Methods |
|---|---|---|
| Isermann [21] | Fault-Sensitive Filtering Method | Linearizing the pipeline model is quite challenging. |
| Digemes [24] | Fault Model Detection Method | The experimental results are consistent with the model outcomes. |
| Benkberouf [25] | Kalman Filtering Method | They cannot fully correspond with the actual conditions. |
| Zhang [26] | Dynamic Mass Balance Method | Combining pattern recognition theory with the method of least squares. |
| Ferrante [34] | Wavelet Transform Method | Addressing the issue of information leakage in the transformation from time domain to frequency domain. |
| Mesh Count | 2,120,000 | 4,420,000 | 9,060,000 |
|---|---|---|---|
| Pmax (kPa) | 26.17 | 26.33 | 26.35 |
| Pmin (kPa) | 21.09 | 21.16 | 21.17 |
| P (kPa) | 5.08 | 5.17 | 5.18 |
| i…N | 2 | 3 | 4 | 6 | 7 | 8 | 9 | 10 | 12 |
|---|---|---|---|---|---|---|---|---|---|
| Ei | 1.9239 | 0.0058 | 0.0106 | 0.3523 | 0.2101 | 0.2439 | 0.0618 | 0.1040 | 0.2357 |
| Leak Hole Size (mm) | Leak Volume (%) | Actual Distance to M2 (m) | Calculated Distance to M2 (m) | Error (%) |
|---|---|---|---|---|
| 4 | 1.5 | 1.264 | 1.339 | 5.95 |
| 6 | 2.8 | 1.338 | 5.82 | |
| 8 | 3.2 | 1.333 | 5.43 | |
| 10 | 4.1 | 1.327 | 4.96 | |
| 12 | 5.7 | 1.324 | 4.78 | |
| 14 | 6.5 | 1.323 | 4.7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, J.; Zhu, Y.; Zou, S.; Xue, S.; Chen, L.; Hou, W.; Xin, S.; Li, J.; Liu, Z. Numerical Simulation Study on Reverse Source Tracing for Heating Pipeline Network Leaks Based on Adjoint Equations. Processes 2024, 12, 2710. https://doi.org/10.3390/pr12122710
Wang J, Zhu Y, Zou S, Xue S, Chen L, Hou W, Xin S, Li J, Liu Z. Numerical Simulation Study on Reverse Source Tracing for Heating Pipeline Network Leaks Based on Adjoint Equations. Processes. 2024; 12(12):2710. https://doi.org/10.3390/pr12122710
Chicago/Turabian StyleWang, Jie, Yue Zhu, Songyu Zou, Shuai Xue, Le Chen, Weilong Hou, Shengwei Xin, Jinglan Li, and Zhongyan Liu. 2024. "Numerical Simulation Study on Reverse Source Tracing for Heating Pipeline Network Leaks Based on Adjoint Equations" Processes 12, no. 12: 2710. https://doi.org/10.3390/pr12122710
APA StyleWang, J., Zhu, Y., Zou, S., Xue, S., Chen, L., Hou, W., Xin, S., Li, J., & Liu, Z. (2024). Numerical Simulation Study on Reverse Source Tracing for Heating Pipeline Network Leaks Based on Adjoint Equations. Processes, 12(12), 2710. https://doi.org/10.3390/pr12122710






