1. Introduction
Energy tariffing as well as trading, transmission line planning, the control and automation grid interconnection of renewables and electric transportation, energy management, electrical safeguards, cyber security, and copious data-based implementations such as (forecasting) servicing are presently the primary application aspects of ICT in energy systems. Major research and development initiatives are underway in all of these domains. Energy is regarded as a vital development strategy in a country; however, in the current circumstances, energy usage is insufficient, and prices are rising. All of these aspects have a direct impression on the Kingdom of Saudi Arabia’s progressive development. As a result, renewable energy resources must be implemented for future usage [
1,
2,
3]. Furthermore, renewable energy, for example, solar energy, is not constantly available during the day. It is vital to offer a reliable power supply for the entire day when using renewable energy sources as a hybrid power system. The primary goal of energy management control systems (EMCS) is to ensure healthy as well as safe operating parameters for building occupants whilst also reducing the facility’s energy and operational expenses. EMCS have been created to increase indoor quality while preserving more power, thanks to technological advancements in the fields of electronics, computer systems, as well as sophisticated communications [
4,
5,
6,
7].
The EMCS architecture consists of various exterior sensors and services, such as fire alarms, surveillance cameras, badge viewers, illumination systems, etc. It additionally encompasses enabling power systems, such as microgrids and power backups, building air conditioning and heating systems, as well HVAC systems. The facility administrators who are in charge of the EMCS architecture that is under threat are among the new stakeholders that must participate as a result of the increased emphasis on securing EMCS. Those currently tasked with ensuring that EMCS have the necessary level of cyber security measures as a component of their crucial infrastructure risk management programs will find important considerations in this paper that can significantly benefit information security control guidelines. The fundamental structure of many of the elements used to provide numerous assistance services presents a significant barrier to protecting energy management control systems. The EMCS elements still in use today often have a long history. The concept of networked devices did not exist when component conception and delivery first began.
Earlier technologies used to manage building loads (including lighting and space conditioning) in the first half of the twentieth century were electromechanical timers that utilized a tiny motor connected to a gearbox to activate electrical connections in accordance with a predetermined timescale. As the output shaft of the gearbox spins, one or more pairings of electrical connections either open or close. Such electromechanical gadgets were simple and dependable, and they continue to be used in some houses to regulate lights and airflow. The main disadvantage of this kind of timer for light as well as ventilation systems was its lack of flexibility. Manual intervention is needed to adjust parameters, and the operating mode is practically without a response (open-loop controllers) because the regulated process’s scheduling is not easily changed by the parameters [
8,
9,
10,
11].
In 2015, the business for energy management systems (EMS) in the United States was worth USD 7.97 billion. The increasing demand for dependable and effective information technology systems for managing, optimizing, and analyzing energy sources is likely to be a major factor driving market expansion. Investment plans in this area are expected to be driven by technological breakthroughs and the increased commercialization of novel products. An increased need for EMS in the industrial sector, particularly in manufacturing as well as power and energy sectors, for the assessment and real-time tracking of energy consumption patterns is expected to drive market expansion throughout the forecast timeframe [
12,
13,
14]. The
Figure 1 shows the market revenue for energy management systems (EMS) in the United States, by product, from 2014 to 2024 (USD Million) as per the market analysis report published by Grand View Research [
13].
Connectivity with cloud-based systems, combined with a high degree of automation, has enabled the real-time surveillance of energy-consuming machinery such as HVAC. The stated reason is expected to boost the growth of the U.S. EMS industry within the next eight years. EMS monitors optimizes and saves energy for a variety of end-user segments in the domestic, industrial, as well as manufacturing industries, encompassing power and energy, telecommunications and IT, production, retail and businesses, and healthcare. These sectors identify fast-changing power consumption as well as efficiency potential patterns in the United States, which causes product demand to increase during the projection period. Considerations on minimizing carbon footprints and reusing waste heat in operations are projected to boost demands for cost-effective as well as elevated EMS components in the coming years. Rising R&D efforts to commercialize highly efficient technologies in the United States are expected to create enormous potential for industry participants.
In relation to cyber security, however, EMCS continues to be terribly lacking. By employing readily available networking technologies, a variety of modern and complex control systems have lately been created. Despite the fact that they are better understood from a cybersecurity standpoint, they still need a coordinated effort and participation from many stakeholders to be protected from malicious actors that intend to do them damage. Institutions that serve critical infrastructure have to guarantee that any operational technology installed is effectively safeguarded against compromise, irrespective of how old or new it is. Numerous regulating authorities frequently demand strong cyber security for all energy management control technologies. The implementation of a strong risk management system is crucial for an organization. In this study, the security risk of EMCS was assessed using the fuzzy TOPSIS approach. Additionally, for resolving collaborative decision-making issues in a fuzzy setting, the fuzzy TOPSIS technique was implemented. It is the recommended strategy for decision-making where the input criterion’s details are unclear, yet the criteria themselves are equally significant.
The remaining part of the work is organized in the following manner. A thorough review of the literature on security risk assessment for communication networks of energy management and control systems is presented in
Section 2. The prominent MCDM technique for security risk assessment problems with fuzzy TOPSIS is introduced in
Section 3. The study’s findings are demonstrated in
Section 4 with a case including six different communication networks as alternatives. Moreover,
Section 5 discusses the research investigation. Concluding thoughts, restrictions, and future work are presented in
Section 6.
2. Related Works
Song et al. [
15] reviewed the properties of nuclear power plant control and instrumentation technologies as well as the considerations required when performing cyber security risk evaluations in compliance with the instrumentation and control device service lifecycle. The actions and considerations required for cyber security risk evaluations of instrumentation and control systems throughout the design of the system or element development and device supply phase were outlined in the following six steps: (1) system characterization and cybersecurity modelling; (2) resource and impact assessment; (3) threat assessment; (4) vulnerability assessment; (5) security control architecture; and (6) penetration testing.
To tackle the complications of security assessment, Liu et al. [
16] presented the attack scenarios as well as multiple criteria decision-making (MCDM). The total security evaluation was divided into two sections. The first is a security analytical method for power control systems centered on an attack graph, which comprises the description of core ideas, the building algorithm, the vulnerability functionality of every control stage, as well as the computation of connectivity model-based system compromise. Another was centered on quantifying the security extent at every control step. In order to benefit the vulnerability considerations obtained by the security analysis concept, a hybrid MCDM strategy incorporated with an analytic hierarchy process (AHP) and a technique for order preference by similarity to ideal solution (TOPSIS) were also presented. Ultimately, an example communication network of a power management system was modeled to validate the security evaluation. The outcome demonstrated the utility of the security evaluation.
Pan et al. [
17] investigated the information security of energy management systems (EMS). They started by expanding their analytic framework, which classifies data breaches as optimization challenges with goals stated as security metrics as well as constraints related to communication network aspects. Second, they created a co-simulation system by combining the energy system simulator DIgSILENT PowerFactory with the communications system simulator OMNeT++ as well as Matlab for EMS implementations. The framework was then utilized to run attack models for a power grid testing phase on the co-simulation-based infrastructure. The findings demonstrated how susceptible EMS is to data breaches and also how co-simulation might aid in vulnerability assessment.
Kim et al. [
18] developed a paradigm for risk assessment that quantifies the potential of cyber exploitation as well as the effects of cyberattacks. The assessment of the possibility of cyber exploitation was motivated by a work on Bayesian attack graphs (BAGs), which enabled a probability assessment that takes into account the causal association among ICSs as well as multistage cyberattacks. They presented a way to determine how far an impact would travel and hence how many functionalities would be changed whenever an ICS is abused for cyberattack consequences estimation. ICS professionals used a methodology to identify and define functional connections and critical function goals across ICSs with which they are already aware and do not demand in-depth cybersecurity expertise. They presented the methods to use their framework to determine the dangers of a nuclear power reactor plant’s protection systems, which are safety-grade digital systems. Their findings demonstrated that risk could be measured in more dimensions than as was presented in earlier studies, such as identifying that elements that were not previously deemed relevant had a high risk because of their functional connection.
Kim et al. [
19] proposed a blockchain-based secure intelligent energy management solution. The blockchain is a decentralized data processing platform in which all network participants share and store information. Incorporating blockchain technology to the smart grid would allow for a more reliable management of energy information, as well as lead to the improvement of the modern intelligent energy sector.
Paridari et al. [
20] suggested a revolutionary EMS cyber-physical-security system that employs security analytics to implement a resilient strategy whenever an assault is identified. Both the robust policy as well as the security assessment were driven through EMS data in this approach, where physical correlations among data points were detected to identify outliers, and the feedback control was closed through the use of an approximate value in place of the anomaly. A limited-order version of a real EMS site was used to evaluate the system.
Albakri et al. [
21] established a security risk evaluation methodology that allows cloud vendors to evaluate security threats in the cloud computing systems while also allowing cloud customers to participate in risk evaluation. By taking into account cloud clients’ judgement of security risk elements and minimizing the complexity which can occur from user involvement in the entire risk assessment process, the suggested methodology produced a more realistic and complete risk assessment output.
According to Woo and Kim [
22], contemporary power infrastructure changes need security, and the construction of a cybersecurity infrastructure becomes critical. As a result, they investigated the operations of energy information control systems and calculated the danger level for every component using the security risk measurement criteria in the Korean smart grid security model.
Maziku et al. [
23] provided a framework for assessing security vulnerabilities in an intelligent grid communication system with SDN. They specifically assessed the security concerns associated with DoS attacks on intelligent electronic devices (IEDs) as well as the IEC 61850 network. Their security score approach takes into account each IED’s crucial role and assesses its impact on the broader smart grid network. They demonstrated how SDN eliminates traffic in the smart grid network as well as enhanced the timing efficiency of IEC 61850-type communications, rendering them time-compatible.
Supervisory control and data acquisition (SCADA) solutions are commonly employed to monitor and regulate industrial processes, as per Gao et al. [
24]. They supplied critical capabilities for smart grid, that is a potential power distribution method for the coming years, such as real-time surveillance, logging/archiving, report production, as well as automation. Several SCADA designs, including hardware as well as software layout, have been developed and standardized on the foundation of such functionalities; however, the most open as well as rapidly increasing domains in the smart grid were the architecture-underlying solutions for SCADA communication as well as security. In their work, they discussed several published SCADA regulations, as well as its cutting-edge communication and security features.
Ralston et al. [
25] offered a comprehensive overview of cybersecurity as well as risk evaluation for SCADA and DCS, along with an introduction to the major industrial organizations and government organizations involved in the project, and a thorough analysis of the literature to date. The primary principles associated with risk assessment methodologies were presented with references mentioned for extra information. Risk assessment approaches such as HHM, IIM, and RFRM were included in the techniques that have been effectively applied to SCADA systems with complex interdependencies and which have underlined the necessity for quantitative metrics. Probability risk analysis (PRA) is a broad phrase that encompasses approaches such as FTA, ETA, and FEMA. The study continues with a broad description of two recent methodologies (one focused on compromise graphs and another on augmented vulnerability trees) for quantitatively determining the likelihood of an attack, the consequence of the attack, as well as the risk reduction related to a particular form of defense.
Jokar et al. [
26] concentrated on smart grid confidentiality and security considerations. Existing security methods created for conventional information technology systems could be leveraged to build smart grid security protocols. Furthermore, new approaches must be developed to fulfil the unique characteristics and requirements of the smart grid. Despite the challenges of building specific security measures for the futuristic smart grid, including such architectural uncertainty as well as a dearth of operational expertise with security assaults, some research have been conducted in this field in recent years. They reviewed the available literature on several elements of smart grid security as well as suggested future research options.
Cárdenas et al. [
27] demonstrated how we can identify computer attacks that modify the behavior of the intended control system by combining knowledge about the physical process under control. They can concentrate on the eventual goal of the assault rather than the specific processes of how loopholes are attacked, and the attack is camouflaged by employing an understanding of the physical system. They investigated the consequences of stealthy assaults as well as ensure that automated attack–response systems do not force the system into an unsafe state to assess the safety and confidentiality of the processes. A secondary purpose of this work is to start a conversation among control and security professionals, two fields that have hitherto had minimal interaction.
Kuzlu et al. [
28] assembled information on various communication network needs for various smart grid technologies, including those employed in a home area network (HAN), neighborhood area network (NAN), as well as wide-area network (WAN) (WAN). Communications systems that are being used to facilitate the deployment of chosen smart grid initiatives were also discussed. Their study was meant to provide a complete library of technical needs and best practices for communication engineers to utilize when creating a smart grid system.
3. Materials and Methods
Multi-criteria decision-making (MCDM) is a methodical method for selecting the best choice among workable options. Choosing the optimal option while taking into account multiple factors is difficult in the majority of real-life challenges that decision-makers confront on a regular basis in industries, healthcare, and tertiary institutions, among many other fields. The use of several MCDM technologies, particularly fuzzy TOPSIS, is possible to resolve issues of this kind.
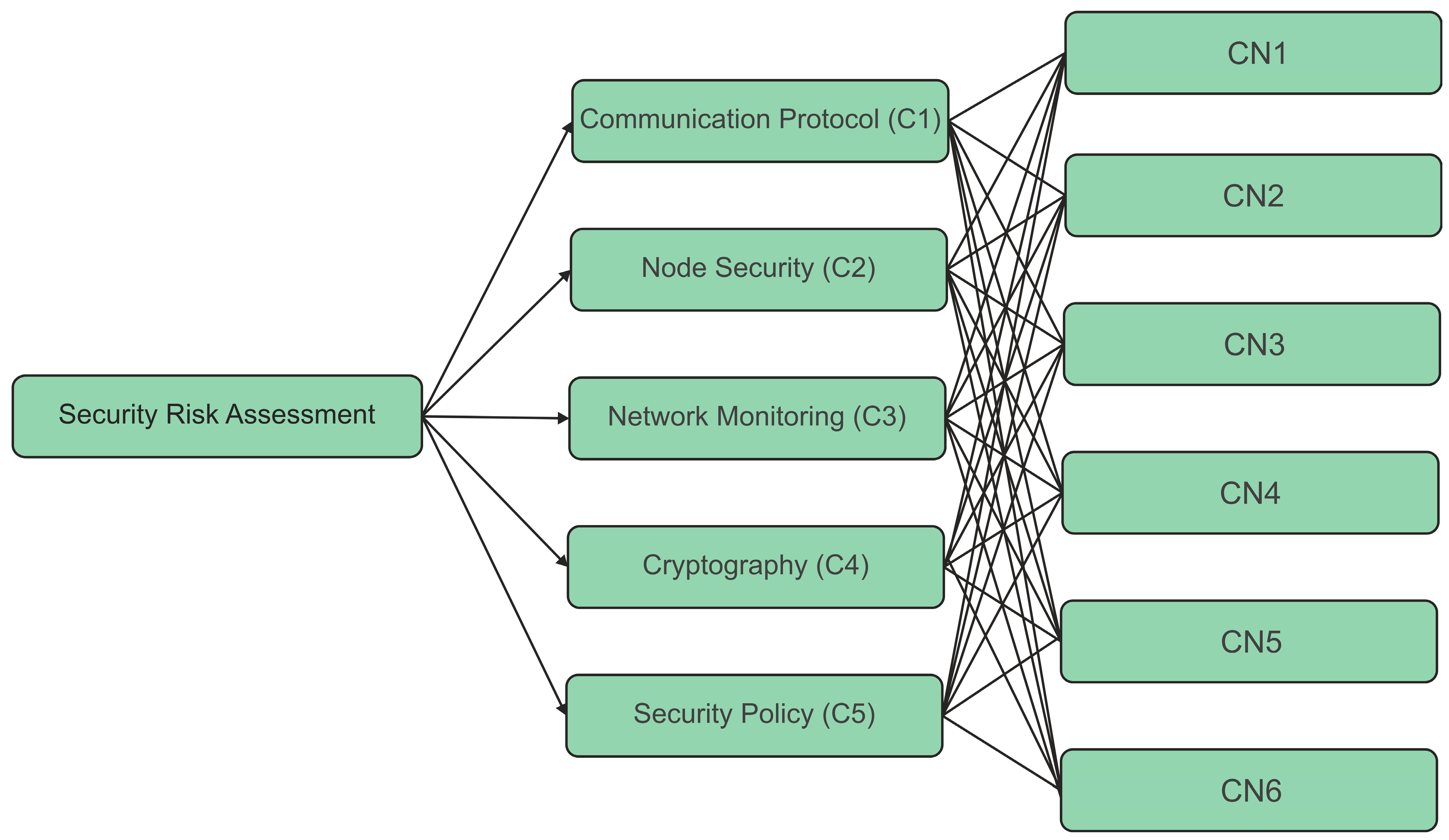
3.1. Factors Affecting the Security of Energy Management and Control System’s Communication Networks
To assess the security risk for the communications systems of power management and control systems, the variables that contribute to such complications must first be determined. These would be known as generating variables, and they can be found by analyzing current research as well as the opinions of organizational experts [
29]. Such discovered characteristics must be studied in order to assess the security risk appropriately. Numerous characteristics are gathered from the literature study in order to assess the security risk, as shown in
Table 1.
Table 1 also shows the correlations between the identified parameters and security risk. Following that, each of the discovered variables is simply summarized.
Figure 2 illustrates the hierarchical structure for the security risk assessment.
3.2. Fuzzy TOPSIS Methodology
In today’s current technology arena, a security risk assessment is still a crucial business concern. This decision procedure involves far too many variables, including economical, technical, societal, as well as risk aspects. Security risk assessment focused on reducing uncontrollable factors and enhancing controllable factors is not a simple undertaking. The fuzzy technique can be a good benchmark to analyze security risk in this MCDM situation. Fuzzy TOPSIS is another multicriteria approach that has gained popularity due to its straightforward methodology as well as readily programmable computing procedure. Hwang and Yoon proposed the TOPSIS method in 1981 [
30,
31,
32]. It was employed to select the top alternatives centered on many criteria. The TOPSIS method’s prominence could be judged by its use in numerous fields to tackle MCDM problems [
33,
34,
35]. TOPSIS is a form of MCDM techniques that employs fuzzy numbers to tackle the challenges involving human judgement and ambiguity. Numerous techniques which blend TOPSIS with fuzzy logic and can be successfully deployed for handling group decision-making challenges have been developed over the last two decades [
36,
37].
TOPSIS’ basic principle is to choose an option depending on its proximity from the optimum answer. The disadvantage of a standard TOPSIS is that it utilizes the crisp value to choose the best option. Furthermore, there are numerous cases where clear facts are insufficient to mimic a real-life situation, particularly when human judgment is involved in the decision-making procedure. In such a case, the decision must be taken while keeping ambiguity and uncertainty in mind. As a result, rather than providing judgement in the form of a single crisp number, the decision-maker can assess the circumstance utilizing interval judgement and the linguistic phrase. Many TOPSIS researchers have utilized the fuzzy set concept, employing the language notion to cope with ambiguity and imprecise data. The decision-language maker’s phrases are translated as triangular, trapezoidal, quadrilateral, as well as Gaussian fuzzy numbers [
38,
39,
40]. The employment of a particular form of fuzzy number is determined by the nature as well as features of the recognized problems, as well as the eventual nature of their solutions. For example, the triangle membership function is the most basic and is commonly used to express linguistic words. There are several methods available for assessing and rating alternates with different criteria. Each method has benefits and difficulties over the others. Fuzzy TOPSIS is a popular multicriteria decision-making method. Fuzzy TOPSIS has the benefit of being easy in its computational approach, easy to reflect human preferences, and allowing clear trade-offs between numerous criteria [
41,
42]. Additionally, the technique is classed as a co-operating approach, with the evidence that while no ideal situation exists, a system with optimal settings on all standards is attainable. As a consequence, fuzzy TOPSIS with a triangle membership function is employed in this work for the security risk assessment of the communication networks of energy management and control systems [
43,
44,
45,
46,
47].
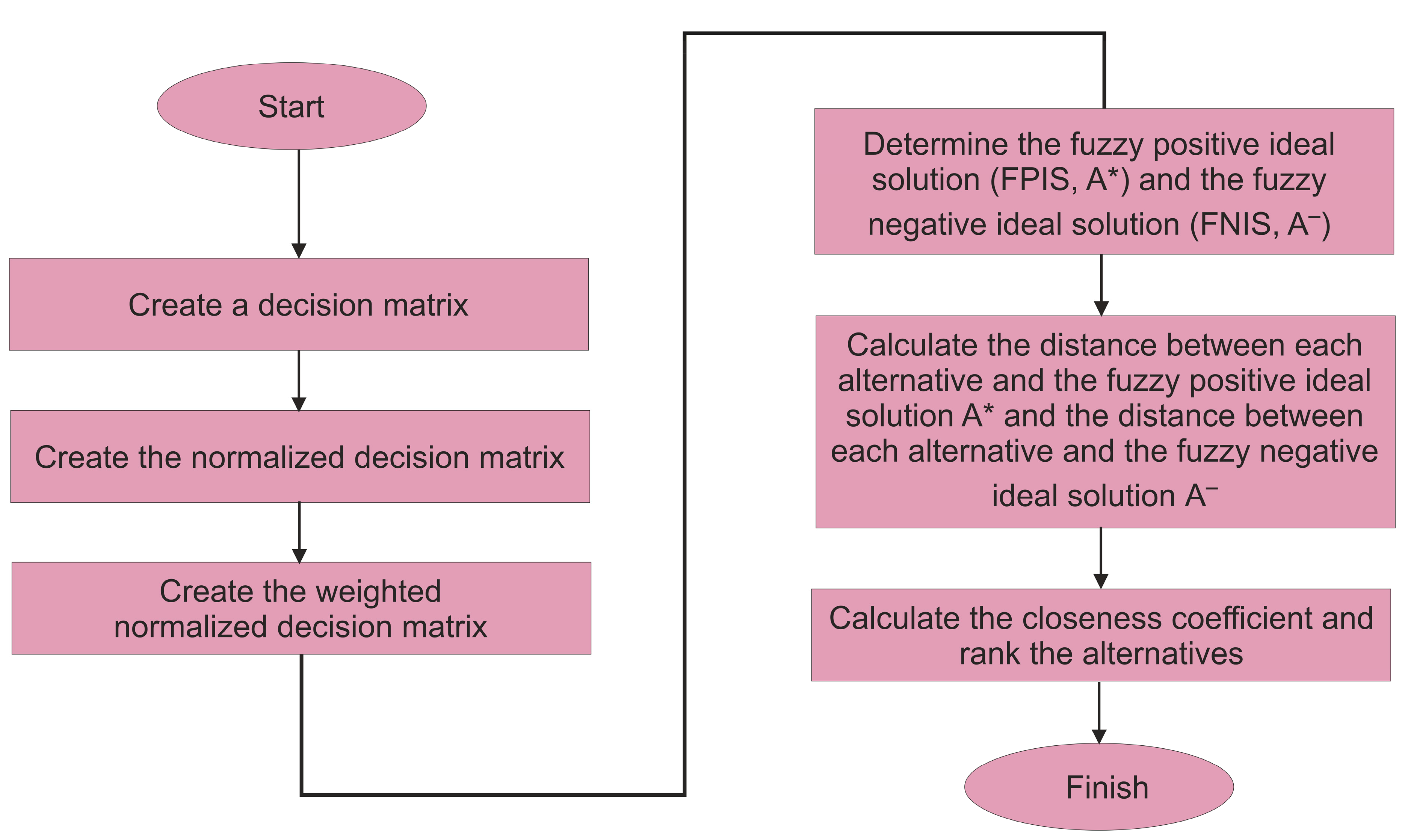
The sequential step-by-step method for weighting analysis and importance ranking with the use of fuzzy TOPSIS is as follows, as shown in
Figure 3:
The fuzzy TOPSIS technique is used to assess 5 criteria as well as 6 possible alternatives in this research study.
Table 2 shows the criterion classification which is positive for all criteria as well as the weight assigned to each criterion.
We assume that our decision-making team consists of K participants. The kth decision-maker’s subjective assessment of the alternative Ai with respect to criterion Cj is indicated by , and the weight of criterion Cj is correspondingly indicated by .
The fuzzy rating scale was developed to account for the fuzziness of individual experiences and perception while assessing attitudes in several areas of psychological research. This scale’s adaptability and expressiveness enable us to adequately represent the results of numerous inquiries concerning psychological assessment. The fuzzy scale used in the analysis is illustrated in
Table 3.
A normalized choice matrix can be created by applying the following relation to both positive and negative ideal possibilities:
The weighted standardized decision matrix can be created by multiplying each criterion’s weight in the normalized fuzzy decision matrix with the help of the following equation, keeping in mind the variable weights of each criterion:
where
indicates weight of criterion
.
The FPIS and FNIS of the alternative solutions can be well characterized using Equation (4) as well as (5):
within which
represents the highest proportion of i across all choices, whereas
represents the least quantity of i across all alternatives. B and C represent the positive as well as negative ideal solutions, respectively.
The distance between every alternative as well as FPIS, in addition to that between every alternative and FNIS, is calculated with the help of Equations (6) and (7), respectively:
Formula (8) can be employed to measure the separation between two triangular fuzzy integers (a1,b1,c1) and (a2,b2,c2), where d is the separation between the two.
Note that and are crisp numbers.
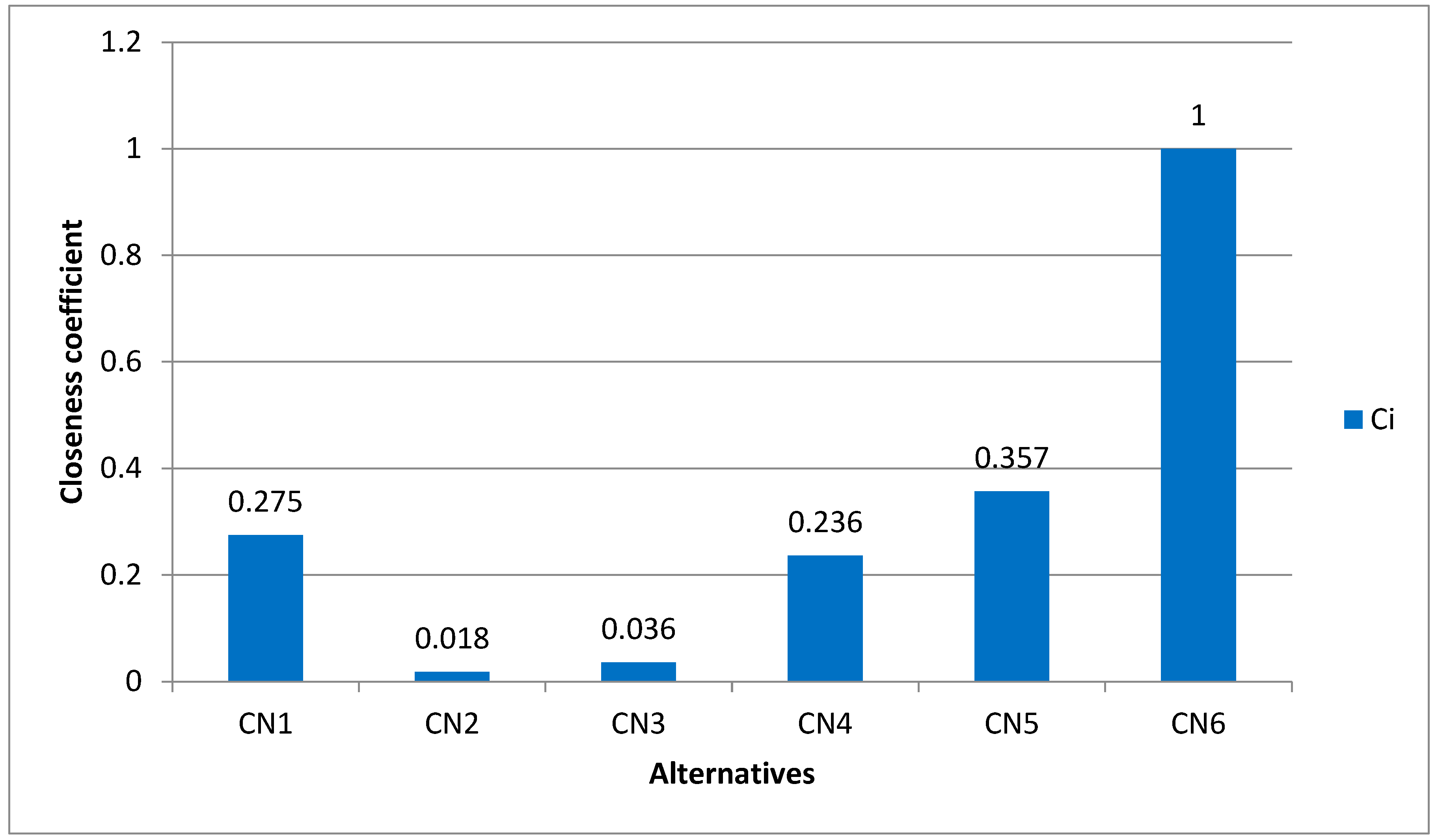
The closeness coefficient of each choice can now be determined using the formula below:
5. Discussion
Machine learning and AI were hardly addressed in the expert interviews despite the fact that the most recent research indicates that approaches for detecting false data injection (FDI) assaults are actively being investigated using artificial intelligence (AI) techniques. This difference could be the result of two factors. One explanation could be that the interviewees’ areas of specialization were primarily energy systems rather than, for example, computer science. An additional consideration might be the academic study’s forward-looking nature (as all academic research ought to be). As a result, the use of AI in attack vectors may increase in the coming years. This shift might be consistent with the growing (noncriminal) use of AI across a range of fields and daily applications [
48,
49,
50,
51,
52,
53]. The novel approach described in this article was created to evaluate the security risks associated with various communication networks of energy management and control system infrastructures. As previously mentioned, any malfunction in the information infrastructure, particularly in the critical connectivity, can have far-reaching effects, such as significant reductions in public safety for a prolonged period of time, irrecoverable harmful damage of the architecture, or large-scale financial loss. The dangers connected with such technologies increase due to the potential for such infrastructure interruption. The presence of security risks thus necessitates the development of efficient techniques for security risk assessment. The prevention of incidents and the stopping of operations at CII is a crucial concern for any nation. An assessment of the most likely and dangerous threats is the first step in implementing appropriate precautions. The risk management approach does not, therefore, begin with risk identification. To begin reducing the most hazardous threats, it is vital to assess the significance of each risk and its likelihood. Implementing scientific and computational procedures that need a significant amount of data and calculations will produce the most appropriate solutions to the problem. Experts can verbally provide the initial data using analogous group decision-making techniques. Every specialist has a unique perspective on the assessment criteria. The fuzzy TOPSIS rating system is then used to determine the significance of expert judgments. Additionally, because the prediction model may be used in different situations, it outperforms traditional approaches. As a result, it is an effective tool for handling such issues.
By utilizing efficient MCDM techniques, risks can be regularly checked in order to avoid repercussions which might shut down or harm the system. The basis for a risk assessment must be due to expert understanding, which enables the prediction of future breakdowns in the communication networks of energy management and control systems by determining the frequency of malfunctions and their effects. Since erroneous information can result in significant losses, it is important to accurately gather information regarding the risks realized and the accidents that have happened. As a result, it is a subject that is of great importance and relevance to any nation.