The probability of a threat is expressed on a scale of one to five. Each of these five degrees of probability is assigned a decimal range that expresses the degree of risk. Number one is the least likely threat and number five indicates the most likely threat to the organization’s information environment. Cyber threats are evaluated in the next step by individual probability levels.
The value of endangered elements (areas) is also divided into five degrees. Number one is the least important element for an organization in terms of securing its information system. The most important element for an organization is marked with number five. Each of these vulnerable elements represents an area that may be most affected by the impact of cyber threats and in which the organization may suffer significant financial damages. These endangered elements represent areas of the information environment that can be significantly affected by the impact of cyber threats. Disruption or destruction of these elements can also be a major financial burden for organizations.
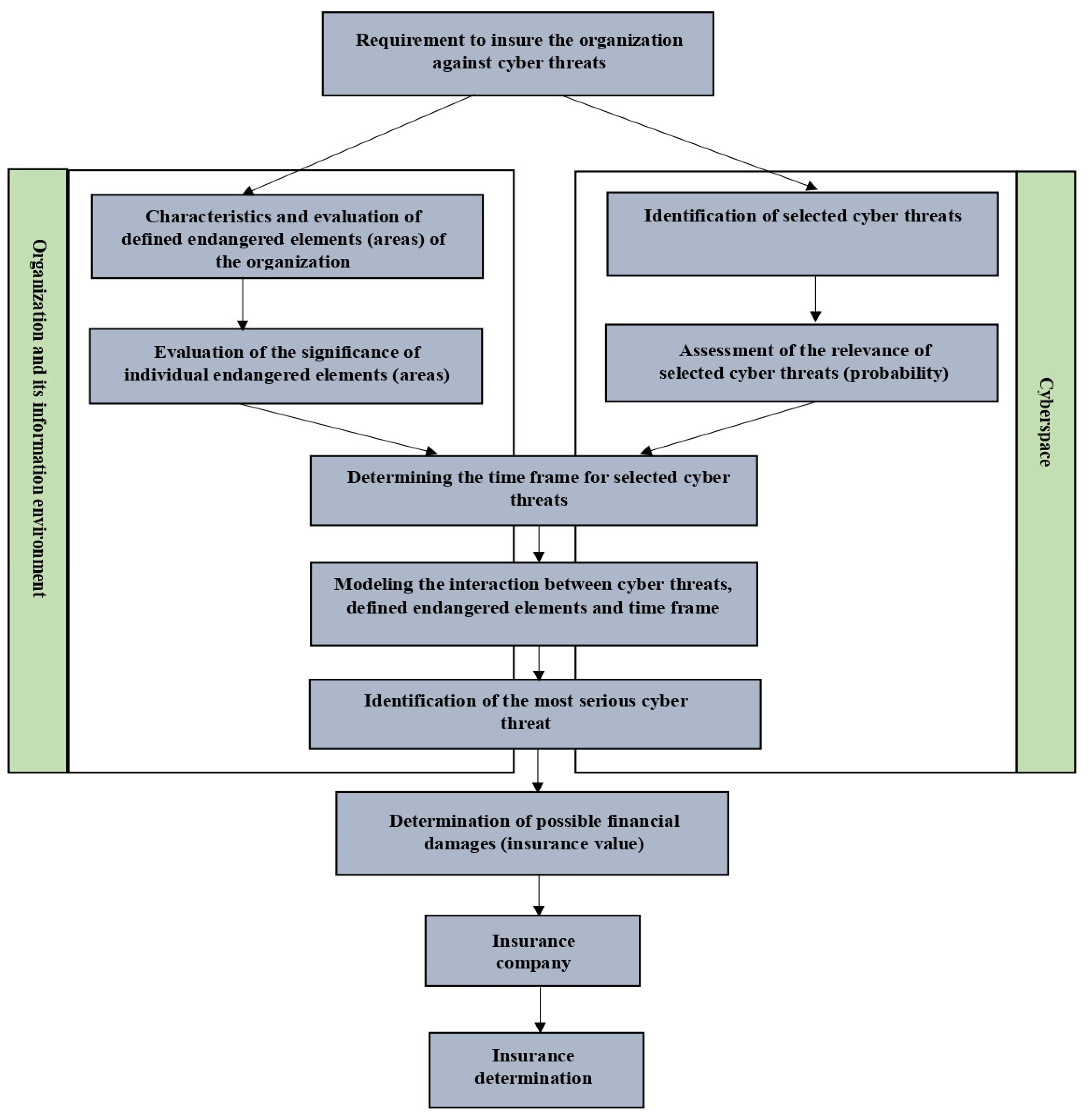
The vulnerability of endangered elements to cyber threats reflects the interaction of these two levels, which have a significant impact on the expression of future financial implications for the organization. Each endangered element has a different vulnerability to cyber threats. For some endangered elements, the interaction with the selected cyber threat does not take place. In these cases, there are no potential financial implications. The possible interaction is expressed in the risk matrix, in which we can then see all the relationships of the above-mentioned members of the proposed mathematical formula. From the vulnerability matrix, it is possible to identify cyber threats that have the greatest possible financial impact in correlation with the degree of threat of the selected endangered elements. Within the determination of the most serious possible scenarios, four cyber threats are always selected, for which the highest level of risk is expressed. These threats are compared using Saaty’s method. Using the weights assigned to the individual criteria and the geometric mean, we can determine the most considered cyber threat in terms of potential financial impacts. The expression of the interaction between cyber threats and vulnerabilities is given in the “Results” section. This risk chart is the first result of the application of the proposed algorithm for dynamic risk-assessment, which expresses the potential financial impacts on the selected organization.
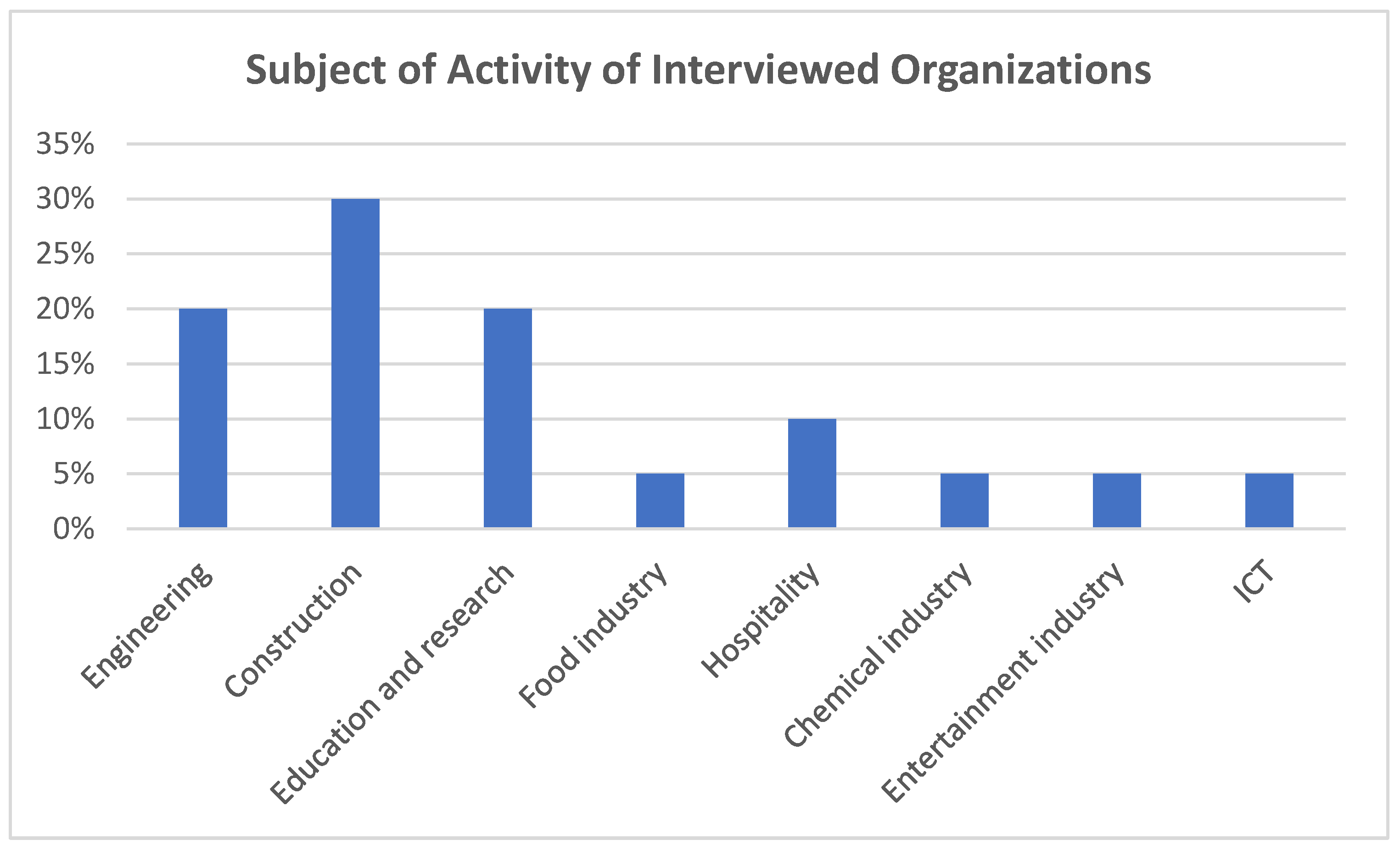
Defining a Pricing of Endangered Elements
The following endangered elements are used to identify potential impacts on an organization’s information environment. For each endangered element, a method of its financial expression is proposed.
- (1)
Hardware
The area of hardware includes not only computer devices and their accessories, but also other technical components that ensure the functions of the information system. We can apply this valuation option if the hardware has a lower price than EUR 1622.
Valuation at acquisition costs is the method is applied in the case of assets that are acquired for consideration (the price includes related costs such as installation and transportation, patents and licenses or exploration, geological and other works). Costs related to the purchase price may also include interest on the loan.
Repurchase valuation costs represents the price for which the asset was acquired at the time of its entry into accounting, i.e., a deposit of tangible assets, tangible assets as a gift or tangible assets acquired free of charge on the basis of financial leasing (in cases where the actual costs of creating the asset cannot be ascertained).
Actual costs are tangible assets that have been created by the business itself. These are direct or indirect costs that were incurred in the course of production or other activities (
Pavlík 2019).
Another way of valuing hardware is based on its current residual value, which arises when depreciating long-term tangible assets that have a higher price than EUR 1622. As part of the expression of this type of property, the accelerated depreciation method was chosen according to the following formula:
In the following year:
where:
- (2)
Lost turnover
The following formula is designed to express lost turnover
where:
Uz = last year’s turnover;
CVh = the price of a normal number of products made in one hour;
Hv = the number of hours when the products are not produced.
- (3)
Fees
Fees related to the realization of a cyber threat can be applied in several cases. If this is the type of organization in which the main business is the production process, then this organization may be sanctioned for non-compliance with the production plan. This situation can occur in the event of a disruption in the function of the organization’s information system, whose main task is to ensure the operation of production machines. If the required number of products were not fulfilled within the time schedule, the organization would also incur large financial losses.
These fines can be issued either by the central management of the organization (in the event of a malfunction of the information system at the branch of the organization), or the fine can be issued by the supplier of the material or service. If the material is not sold by the supplier within a certain time interval, these third-party entities may experience a loss of profit. A similar situation can also occur on the customer’s side. If the receiving entity does not receive the relevant product or service from the organization within a certain period of time, it loses the profit from the sale. This situation also occurs with an organization that has become the subject of a cyber incident. Another entity that can impose sanctions on a given organization is the competent supervisory authority. This policy is governed by the General Data Protection Regulation (GDPR).
No predefined formula can be used to represent this category financially. The amount of the fine is always an individual matter, and depends on supplier–customer relationships. In the case of the general GDPR regulation, the amount of fines is set between EUR 10,000,000 and EUR 20,000,000, or 4% of the company’s total turnover (
Pavlík 2019).
- (4)
Software
For the purposes of this research, the amount of cost that would have to be incurred to reinstall the software in the event of a breach will be used. Since the organization owns a license to operate the software tools, it is not necessary to repurchase the software at a new price. There may also be a situation where the software is acquired and tied to the hardware it was purchased with; however, this possibility is not very likely in the case of small and medium-sized enterprises (
Pavlík 2019).
- (5)
Data reconstruction and recovery costs
The cost of data reconstruction and recovery can be defined as the costs incurred for the recovery of data resources, which can be represented by hardware and software resources. In the event of a breach of these data resources, stored or backed-up data may be irretrievably lost or damaged. It is also possible to determine the average cost of lost or stolen data from available statistical sources. This average cost is reported to be USD 141 per person (
Ponemon Institute 2017).
The following formula can be used:
where:
NR = data reconstruction costs;
CD = the cost of lost or stolen data for one person;
PD = the number of data items that can be lost or stolen.
- (6)
Damage to reputation
For the financial expression of reputation of the organization, it is necessary to characterize what is meant by this term. In the context of insurance against cyber threats, “damage to reputation” means future financial damage that will be caused by the realization of a cyber threat in certain areas of the organization. These areas are suppliers, customers and sponsors. These are financial resources that the organization may lose within a certain time-frame, due to an undesirable event. The reputation of the organization (also called goodwill in the field of economics), can be expressed financially using a mathematical apparatus. In this case, it is mainly about advertising and the image of the organization. In the area of advertising and image, the organization is evaluated as a whole, not only based on certain areas. To express the financial amount that reflects the area of advertising and image, it is necessary to measure the profitability of investments in this category. Furthermore, it is necessary to take into account the synergy that the company creates in order to reach the market.
In every organization, employees and managers invest their time, money and energy in creating the image of the organization. This process is primarily focused on approaching new customers, and suppliers, and maintaining existing contacts. For this reason, the calculations in this category are focused on this point (
Pavlík 2019).
Staff qualifications
where:
KBZ = qualifications of current employees;
Xi = monthly earnings from performances created by all current employees;
Ni = the monthly cost of training for all employees.
Advertising and Brand
where:
RI = advertising and image;
PPK = average income per client;
Nki = new clients per year;
Zki = lost clients per year;
Nir = advertising costs per year;
n = the value of the observed period.
P = perspective;
Xi = total income from the calculated year;
Xip = total income from the previous year;
n = the value of the observed period.
- (7)
Costs of reporting data loss or leakage to supervisory authorities
In the case of insurance against cyber threats, the costs of reporting data loss or leakage to supervisory authorities should also be taken into account. In the case of loss or leakage of personal data, the time interval for reporting this event to the competent supervisory authority is 72 h, according to the general GDPR regulation. In this category, we may also include notifications to, and communications with, other parties affected by the data or information leak. This issue is also closely related to maintaining the reputation of the organization (
Pavlík 2019).
For the purpose of expressing this parameter, the following formula may be used:
where:
NU = the cost of loss or data-leakage notification;
MZZ = the number of customers or other entities that may be affected by loss or data leakage;
HM = the hourly wage of employees who will be in contact with the entities concerned;
TU = the number of hours spent on contacting the affected entities.
Another part of the proposed algorithm is the determination of the vulnerability of the endangered element to the cyber threat. This situation occurs in the event that during the realization of a cyber threat there is an impact on the endangered element (which may not always be the case). In this mathematical part, the relationship between the cyber threat and the endangered element is assessed. This relationship is also expressed on a five-point scale, where number 1 means the least impact of the cyber threat on the endangered element, and number 5 the highest impact of the cyber threat on the endangered element.
The last part of the process of determining the potential financial impacts of cyber threats on the organization’s information environment is the time frame. The time dimension represents the expression of a cyber-threat scenario from the point of view of its development. The time frame is divided into five levels. Each of these levels represents the duration of the cyber threat in relation to its severity. To determine the degree of cyber threat in terms of time evolution, two dimensions of this problem are compared. The first dimension represents the time dimension, which is shown on the x-axis.
As we can see, the individual degrees of the time frame, which also determine the relevance of the cyber threat, are divided into five categories. Each of these degrees is characterized by a length of time that also affects the relevance of the cyber threat. The time length that is assigned to the individual degrees can be seen in the following table (
Table 2). Each degree also contains a value that defines its importance in correlation with the relevance of the cyber threat. The time frame of individual levels was determined on the basis of an analysis of the principle of selected cyber threats. Expert studies that focus on this issue were also examined.
In the time dimension, it is hypothesized that the longer a cyber threat lasts, the more severe its impacts on the organization’s information environment can be. The second dimension of this problem involves the relevance of the cyber threat, which is indicated on the y-axis. The severity of a cyber threat evolves over time. Therefore, if the duration of a cyber threat is shorter, then the effects of the implementation of this threat tend to be smaller. If the cyber threat lasts for a longer period of time, its potential impacts on the organization’s information environment can be more serious. The time frame and individual degrees for the course of the cyber threat can be seen in
Figure 3.
It is necessary to mention that the time dimension is not relevant for every endangered element in the organization’s information environment. If we take into account, for example, the interruption of the production process or business and thus also the generation of profit, the time dimension of the cyber threat represents a relatively big problem. In the event of an organization being unable to produce a profit, due to the realization of a cyber incident, this fact can have great a impact from a time point-of- view. The longer this state lasts, the greater the probability of more serous impacts of the cyber threat, thus also endangering the functioning of the given organization. In the event of a breach of data or information, or the possibility of fines by supervisory authorities, the time dimension does not represent a more serious problem. In this case, these are endangered elements that are more static from the point of view of the duration of the cyber incident, and their variability does not increase much with the duration of the cyber threat and its impacts.