Abstract
Nowadays, blockchain is developing as a secure and trustworthy platform for secure information sharing in areas of application like banking, supply chain management, food industry, energy, the Internet, and medical services. Besides, the blockchain can be described in a decentralized manner as an immutable ledger for recording data entries. Furthermore, this new technology has been developed to interrupt a variety of data-driven fields, including the health sector. However, blockchain refers to the distributed ledger technology, which constitutes an innovation in the information recording and sharing without a trusted third party. In this paper, blockchain and Distributed Ledger-based Improved Biomedical Security system (BDL-IBS) has been proposed to enhance the privacy and data security across healthcare applications. Further, our goal is to make it possible for patients to use the data to support their care and to provide strong consent systems for sharing data among different organizations and applications, since this includes managing and accessing a high amount of medical information, and this technology can maintain data to ensure reliability. Finally, results show that new blockchain-based digital platforms allow for fast, easy, and seamless interactions between data suppliers to enhance privacy and data security, including for patients themselves.
1. Introduction
Recent trends in technology are exploited for diverse real-world applications to provide definite solutions for end users. Assimilating technological aspects in user-related application provides diverse advantages, from the quality of service (QoS) to security [1]. The healthcare platform is visualized using electronic health records (EHRs) in its digital and technical format, providing unrestricted access to the end users. Diagnosis centers and healthcare infrastructures provide different access and data sharing processes for their users through EHRs [2,3,4]. EHR is an organized set of patient-/user-related information that is digitally shared through a secure platform for ubiquitous access [5]. User applications and graphical user interfaces designed for EHR access provide access to the healthcare data through simple authorization and authentication procedures. Since sensitive information, end-to-end security, and privacy are the prime concerns in sharing EHR’s between users [6], this is vital as the technology requires additional infrastructures such as cloud, Internet of things, mobile devices, etc. for sharing EHR’s [7].
Blockchain is another technology that is commonly used in different applications for providing distributed access to resources and unalterable information [8]. The blockchain paradigm is used for administering security in different communicating and processing systems. Healthcare application does not require trusted third-parties for administering security [9]. The electronic ledger is distributed across different communicating and processing systems to improve the swiftness in security administration and privacy preservation [10]. Besides, blockchain eases EHR sharing between end-user applications and healthcare infrastructures without interrupting the communication process [11,12]. Such facilities are provided through line-of-trust and authentication with interoperability using the distributed electronic ledger technology. Modern healthcare applications concentrate on the privacy of the users and security of the information shared to prevent anonymous and unauthorized access to illegitimate users [13,14].
Trust, authentication, and privacy are the major requirements in sharing EHRs between different users. Administering the blockchain paradigm as a decentralized ledger for monitoring shared information is becoming a familiar practice in recent years [15,16]. Blockchain-assisted authentication and trust-based security are assimilated with the medical systems for improving the quality of information sharing and preventing unauthorized interruptions [17,18]. Knowing the significance of the data, biomedical systems rely on robust authentication and trust schemes for confronting diverse attacks, data leakage, tampering, and loss. EHR access control, defining security levels, verifying users, and sharing sessions are collaboratively performed using the security systems [15,17,19]. Modified and sophisticated access control, encryption/decryption schemes, and auditing features are required to handle different attacks and illegitimacy in storing and sharing EHRs. In trust-based schemes, user-centric factors are assessed to differentiate the users to provide access controls, whereas authentication schemes focus on providing data/EHR security through hashing and encryption/decryption process [20,21].
However, blockchain refers to the distributed ledger technology, which constitutes an innovation in the information recording and sharing without a trusted third party. In this paper, Blockchain and Distributed Ledger based Improved Biomedical Security system (BDL-IBS) has been proposed to enhance the privacy and data security across healthcare applications.
2. Related Works
Tang et al. [22] proposed privacy-preserving healthcare in the trusted network to enhance the trustiness among the patient and caregivers. The Sybil attack is used to find the fake patient and terminate it from the network. The proposed method is used to make the authenticated person access the healthcare center.
Computer-aid design is implemented for security, and privacy of the trusted systems is introduced by Salnitri et al. [23]. It also gives the specification of experts to use the system from various characteristics. They are also using the higher goal for the business, and external threats are maintained for the trustworthiness in the network.
S-Alex convolution neural network and dynamic game theory (SCNN-DGT) designed by Kong et al. [24] are used in the IoT-cloud computing environment for health data management. The initial step is obtaining the information of the healthcare and classifying them in Alex’s net convolutional network. This method is designed to evaluate security in the healthcare system. It validates the index screening to verify the user.
Data integrity is used for sharing the records of healthcare in a verifiable way and is introduced by Wang et al. [25]. The author developed a blockchain for privacy usage through symmetric encryption and attribute-based encryption. It attains the fine-grained access control.
Zhao et al. [26], developed key management for healthcare blockchain. The efficient key management method is used as a privacy and security mechanism in the healthcare system. It is observed by embedding the sensor to analyze the blockchain. The proposed method is used to enhance the effectiveness and high security.
Guo et al. [27] modeled a multi-authority for the Tele-medical system to improve the efficient blockchain based on the ABE scheme. In this paper, both the dynamic authentication and authorization are used for MoD service under telemedicine. ABE is mainly used to manage the system in real-time scenarios for private healthcare data. This is done in a cloud-based environment.
A blockchain is proposed for the medical records to access and permits the MedChain process, which is addressed by Daraghmi et al. [28]. Medchain is used for interoperating, secure, and effective access for patients’ privacy. The security is time-based access that gives the degree of health providers.
A blockchain is used for the Electronic Health Record system (EHRs) and is proposed by Guo et al. [29]. The authors implemented a secure attribute based on signature with multi authorities. The patients send the text according to the health as the attribute evidence to the healthcare center. The trust is given to the authorities to access the message, and both use the public and private keys to avoid the escrow problem.
The medical service framework is designed to store the secure records of the patient by using the blockchain method and is introduced by Chen et al. [30]. The storage is done on the cloud for large data access. The records are shared by its aspect based on its service related to the authorized user.
Tian et al. [31], observed medical data management with private access. The blockchain is used to protect the data in two aspects such as storing the data in the local database, encrypting the data, and sharing the key to the patient for further viewing. The shared key for security and integrity is established using sibling intractable function families (SIFF) aided by blockchain. The proposed method uses integrity, availability, and privacy of medical data for better efficiency.
Wang et al. [32] presented an e-healthcare system by using Wireless Body Area Networks WBAN. The blockchain is used to generate security and resolve the low power healthcare system. The WBAN is placed in the patient’s body and transmits the data by using the blockchain process.
A blockchain -based healthcare system using formal methods is developed by Brunese et al. [33]. This paper aims to exchange information from the patients to the hospital network by using magnetic resonance images. The data are transmitted by the formal equivalent for validation. They are modeled by radiomic features for automata.
Uddin et al. [34] proposed blockchain leveraged decentralized eHealth architecture (BDeHA). This architecture consists of three layers, including a sensing layer for obtaining the data through the sensor. The second is NEAR processing for sensing the IoT devices and the third one is FAR processing, which is comprised of cloud computing servers.
Griggs et al. [35] observed a healthcare blockchain using smart contracts for patient monitoring. The smart contracts are used for secure analysis management for communication with the sensor. They are also used to monitor the patients and professionals to give notification regarding the health.
Brodersen et al. [36], globally and across several industries, present an innovation model that will allow business to business-and-consumer transactions to be faster, more efficient, and highly secure. Many healthcare participants hope the same distributive database technologies allowing this new model can lead to similar outcomes within the industry and recognize that confusion, like many other major innovations.
3. Blockchain and Distributed Ledger Based Improved Bio-Medical Security System
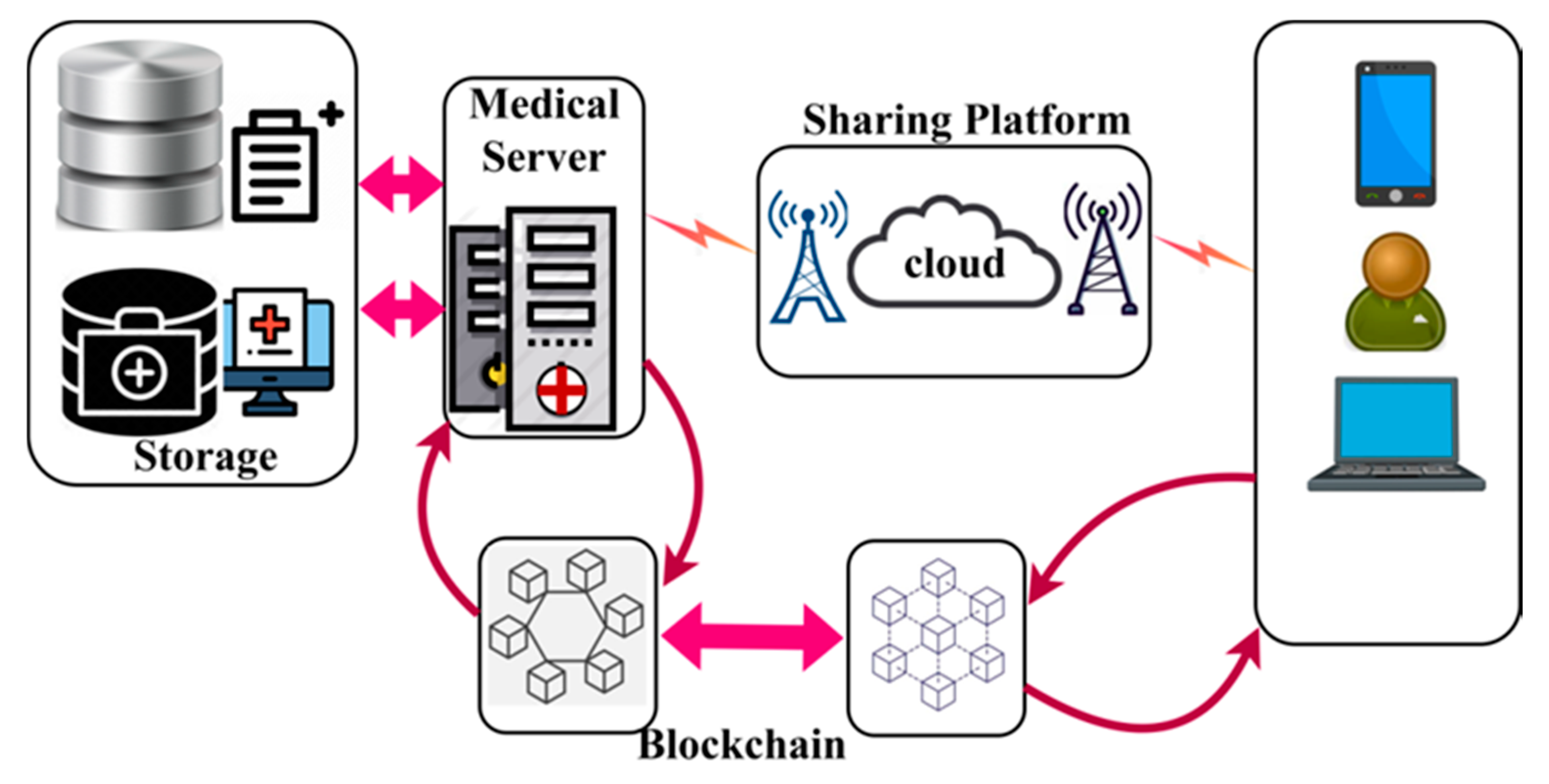
The proposed BDL-IBS is designed to improve the trust- and privacy-related specifications of the electronic shareable health records. The system focused on maximizing the sharing rate of the secured records along with less adversary impact. In this system, blockchain technology is exploited by the medical server that tracks the trust privacy factors between the users and records. In Figure 1, an illustration of a biomedical security system with blockchain technology is presented.
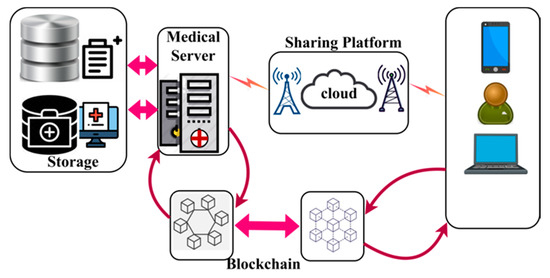
Figure 1.
Biomedical Security System with blockchain.
The components of the bio-medical system include storage and a medical server. The storage contains the health records of the end-users in a digital format. The medical server is responsible for processing user requests and responding to them with appropriate records. A common sharing platform such as cloud and associated infrastructures are responsible for sharing EHRs. The blockchain and distributed ledger are used in both the medical server and end-user applications. In the blockchain associated with the medical server, the trust and privacy factors are analyzed, whereas the privacy factors are alone assessed in the end-user blockchain. The trust factors include successful access and response to request ration, and privacy relies on convergence and complexity. The trust process is analyzed and explained in detail in the following subsections.
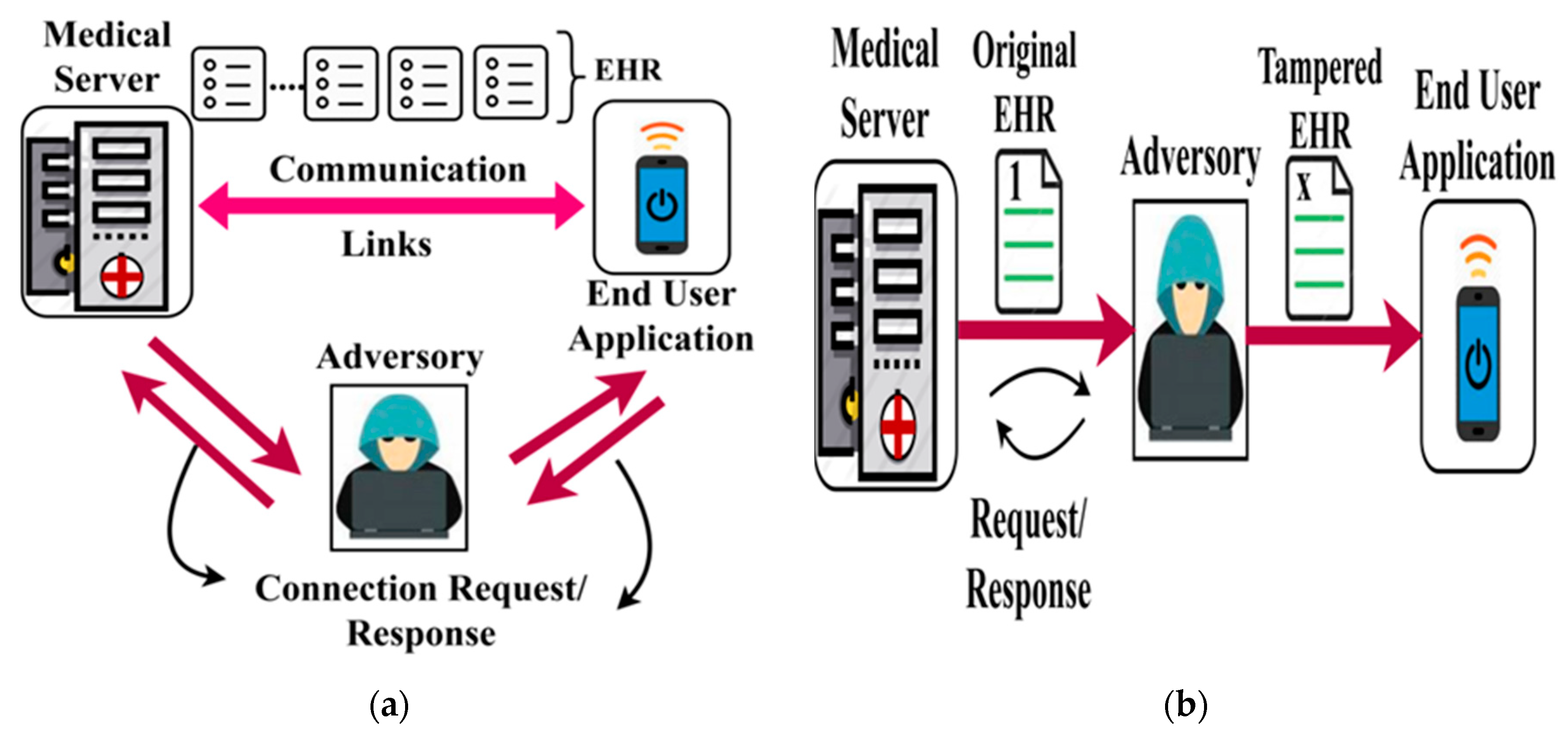
Adversary Model: In this bio-medical security system, malicious access due to man-in-middle and data tempering adversary models are considered. In a man-in-middle attack, the adversary overlaps the end user to gain access to the HER. This results in sharing health information to an adversary and thus degrading the design of a secure biomedical system. In the case of a data tempering attack, the adversary breaches HER from any node communicating with the biomedical system. It either modifies the actual data/tracks the communication through the HER information. Figure 2a,b portrays the representation of the man-in-middle and data tampering attacks over the EHR.
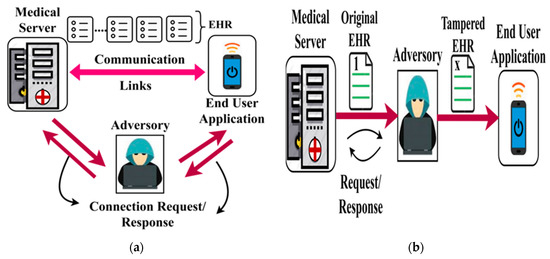
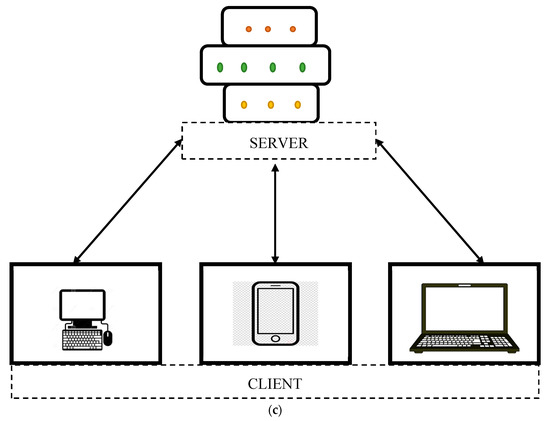
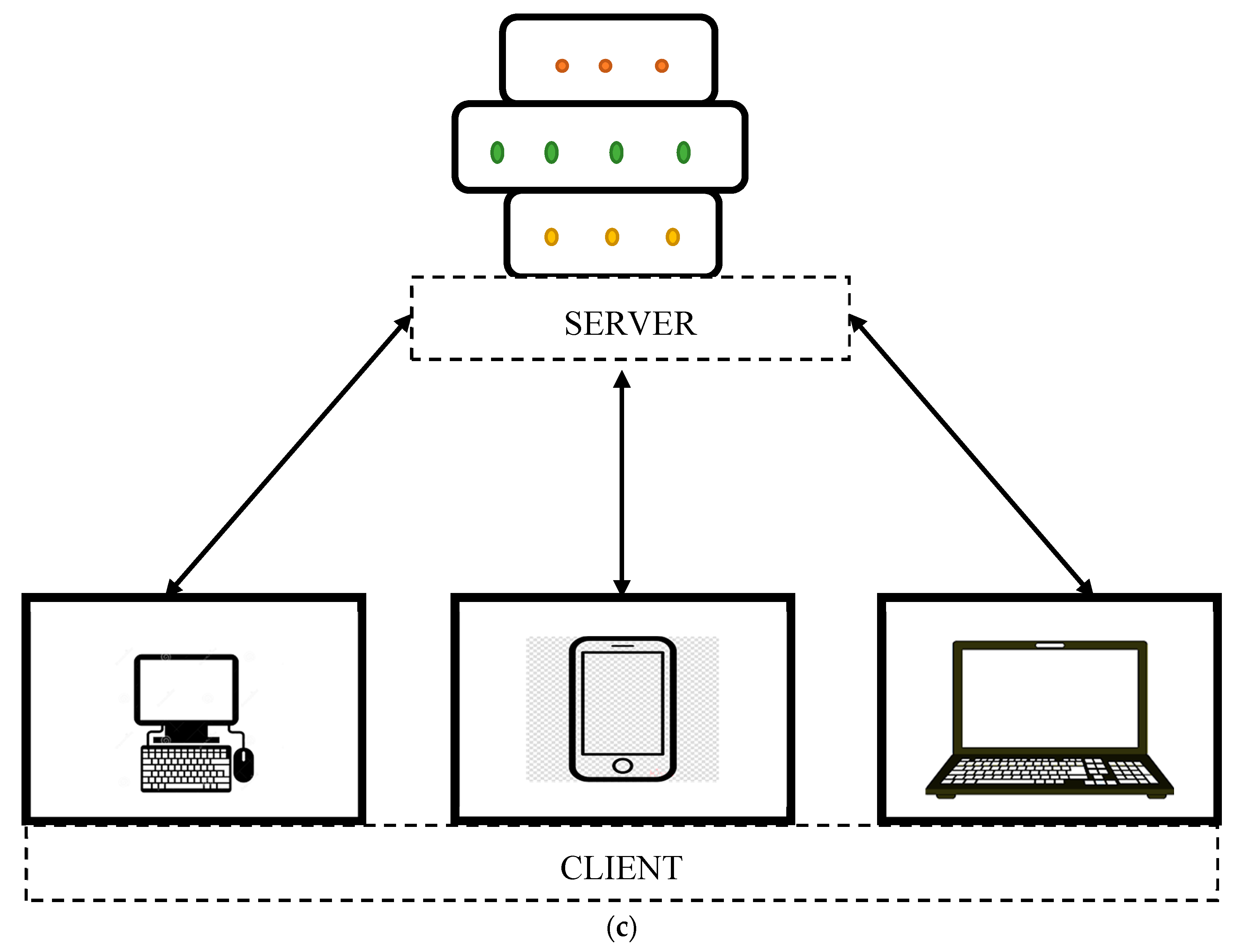
Figure 2.
(a) Man-in-middle attack. (b) Data tampering attack. (c) Server-client based blockchain technology.
For thwarting the above attack, the trust model and concentric authentication are introduced using the blockchain paradigm. As referred to earlier, the blockchain process is differentiated in both the medical server and end-user functions.
Apart from the regular two-layer network, the man-in-middle attack can be overcome by the server-client based blockchain technology as shown in Figure 2c. Since it is a server–client network, it is well suited for the medical user and end-user functions. To reduce the man-in-middle issue, a pure application-oriented implementation is followed in the objective of the proposed idea. A proper set of protocols should be determined in the server domain, and the appropriate application receives the data from the client side.
The process of trust-based validation is performed using linear decision-making, and authentication is augmented through classification-based learning.
Trust model based on Linear Decision Making: In the trust model, the factors are successful access and end-user application to fetch HER. Through conventional communication standards, the end-user application generates a query for accessing HER. The initial authorization for the end-user is provided using login ID/name and password information. This information is validated by the medical server to ensure the reputation of the user. The medical server is associated with the blockchain with the following entries, as in Table 1.

Table 1.
Blockchain Entries.
For each generated and received in the medical server, the state of (i.e., sharing EHR), the factors and are updated. This information remains unchanged in the blockchain paradigm. It is to be noted that is valid for , within which the sharing of EHR is completed. For any case of , the and the user is marked as illegitimate. For validating the above conditions, is computed as a linear combination of and successful access probability . In a given , the is computed as
The factor is the ratio of response to the query request received by the medical server. The linearity in identifying the trust for a period of relies on and , where both the factors are proportional to each other. The above linear relationship between and is is recurrently analyzed using the instance, i.e., the in all instances is verified from its previous shared count that is given as
From the above sequence, the varying or in is estimated for all the shared to the end-user. In this sequence, the varying point initiating the change in proportionality between and is identified. Such identification helps to reduce the computations and security mechanisms (authentication) to prevent losses in sharing EHR. This point from the sequence is computed using Equation (3) as
This validating point helps to hold the verification process and trust update in the blockchain, where the actual is updated until sequence. The decision for pursuing/halting EHR sharing is determined using the conditions formulated in Table 2.

Table 2.
Decision conditions.
The last three conditions in Table 2 represent the unfeasible conditions as results in a negative that is not possible in case . Similarly, the sequence and instant trust are the same in case of sharing only 1 record, after which . This provides continuous chances for EHR sharing, whereas, in practical EHR based biomedical systems, the condition does not hold. For condition, the point is detected after all the counts are shared. Therefore, the previous state of name/ID for which it is with the new or period. The blockchain is updated for the above and hence for further sharing of EHRs. The case of the first two conditions is different, where follows and as in Equations (3) and (2), respectively. The different case of condition 1 is to be differentiated from the other conditions as a trial to the user is given if the current trust is less than the previous sequence of trust. This impacts either or and hence Equation (1) is modified as
If both the and factors are not constant, then the sharing process is halted. Based on the different instances for (or) , the decision is made such that the sharing is not halted, whereas it is paused until the next update if is observed. In this pausing instance, the sharing session of the end-user application is expired. Therefore, the user has to login again to re-initiate the EHR sharing session. The time of validity based on different instances of is determined using Equations (5) and (6), respectively.
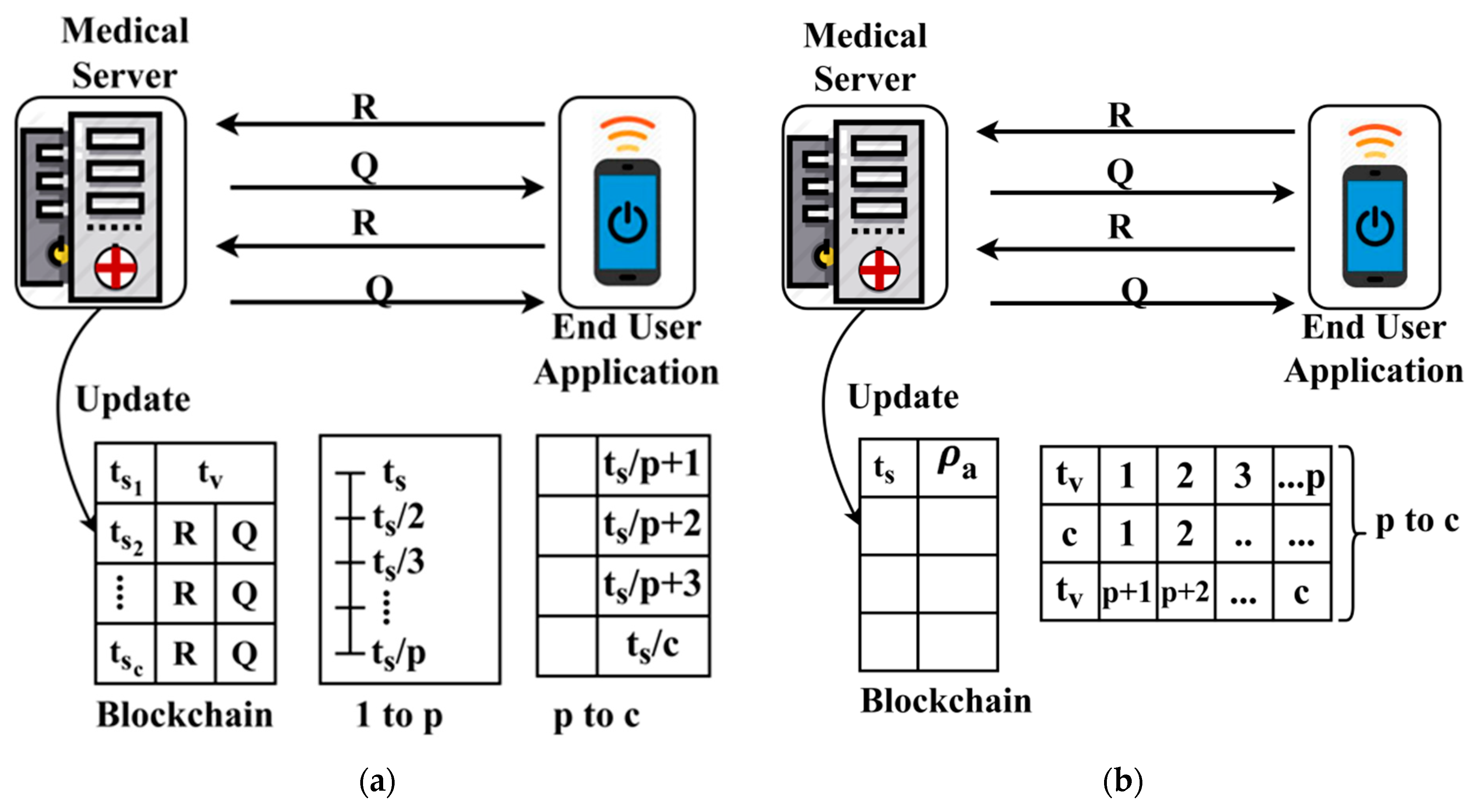
For the above Equation of computing for fluctuating , tn Figure 3a,b, respectively.
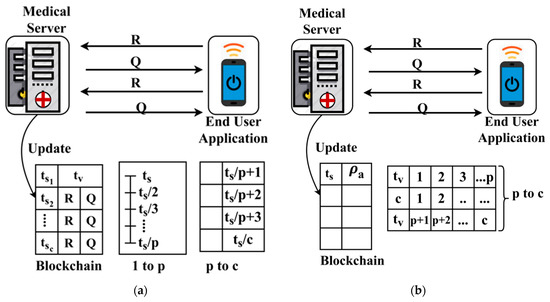
Figure 3.
(a) Sequential update (1 to p), (b) concurrent update (p to c).
The process of trust-based update in the blockchain is performed using using and factors independently. The process is consecutive if and is updated based on and concurrent if the update is based on . The process of differentiation relies on the that is identified for both the conditions where . Finally, the user with or is identified in all the instances for providing better authentication. The linear representation in Equation (2) is either fluctuate between based on and independently. The fluctuation is based on the varying and instances as differentiated by . This trust-based decision-making helps to improve the ratio of successful sharing under controlled response time. In Table 3, the observed records that are classified under different conditions of Table 1 is presented for the different sharing times.

Table 3.
Records Classified under Table 1 Condition.
There is only one ending transmission in the sharing time of 70, where condition 4 is satisfied by sharing count of . The records classified under conditions 3/5 are not sent to the end user, and hence their sessions are logged out.
4. Classification-Based Concentric Authentication
In the classification-based concentric authentication, EHR is shared. In a concentric authentication, the common classification on point serves as the decision-making for generating authentic records. The classification-based learning allocates two types of non-sequential session keys for authenticating the sharing session. This classification is based on the fluctuating as in Equation (4). The impact of either of the fluctuation varies the administration of session keys to prevent the data tampering attacks. Initially, the session is set up between the medical server, and the end-user application follows a linear mapping map: . Here, is the group of response until a count , and is the random function of the end-user . The group consists of a random generator along with a differential prime number . For the different, the variable relies on computing hashes and for the medical server and end-user, respectively. The general format of an initial authentication is denoted as . The shared record count is obtained from the blockchain, where the trust of user access coupled with the records is stored. The distributed access to blockchain stored information is assessed in both end-user and medical server levels. For this authentication process, the classification occurrences of and in is performed. As stated previously, the sequential and concurrent update of the medical server blockchain process requires different session keys and authentication procedures. Therefore, the occurrence of for condition 1 from Table 2 is the determining factor. Let and represent the fluctuating and sequential probabilities in a given time ; then,
, the above classification of probability, over is computed for all instead of to linearize the solutions as in Equation (1). Based on the relationship between and , the classification of is performed as
where For condition 1, the classification rule is framed as in Equation (9) for identifying over as in Equation (8)
where . Here in Equation (9), the probability of is computed based on the likelihood of instances and its normalization as
The above likelihood normalization of helps to classify condition or condition. This helps to decide between sequential and concurrent authentication procedure through the same concentric point from the fluctuating sequence of . The normalization identifies precise in the series of such that follows sequential authentication, whereas the previous occurrence relies on random concurrent security measures. Here, the priority of authentication is initiated from the first occurrence of of as determined by . For all the first occurrences of and , the sequence follows or and (as in Equation (6)). Using this sequence and concurrency, the authentication is presented as follows. In two cases, the occurrence of the sequence and concurrency observed is discussed below.
Case 1: The sequence initiates with
Analysis 1: The hash sequence for both and is formulated as
This hash is composed of and and is subject to verification using the user ID and session key as follows,
where and are the secret and verification keys generated for the hashes, and therefore in the sharing process, is contributed to the end-user. At the receiver end, the is used for verification. If the process of sharing the records is sequential, then is sequential until or the likelihood occurs. This is followed for all until the is reached, and then the coherency of until is observed. The verification of the process is also sequential by mapping where is observed from the range of hashes from to . The first sharing verification is performed as
where, denotes the blockchain record for the grouped storage of after the hashing process. In the verification at the user end, the relevance is first validated, followed by the verification process as in Equations (14) and (15) respectively.
In the above, the range of is valid until , i.e., the is the halting factor for sequential authentication. In the verification process, sequence as mapped in is the balancing factors where the sending and receiving sequence until is obtained. In this case, the converging interval of the proposed method is extended until the , i.e., the restricted time from 1 to is extended from to in a concentric manner. The next sequence for to authentication is discussed in Case 2.
Case 2: The sharing sequence experiences .
Analysis 2: This case is unique as both sequential and concurrent authentication is performed with interfering with other processes. It is to be noted that the convergence time from the sequential process is experienced to from the . This helps to identify more , and thus the concentricity of the authentication process is expanded, reducing the chances of convergence. In this authentication process, both and are used for performing secure sharing between the medical server and the end user. The blockchain is updated with and along with the previous sequence for the appropriate user ID. Therefore, the session is initiated by verifying the following
There are two verification steps followed for authenticating the sharing due to the fluctuating instances in . The first authentication follows Equation (14), whereas the range from to follows
The above process of authentication in sharing and receiving is performed in both the medical server and the end user. Finally, the received is verified using to sequence as in Equation (15), whereas the to received is verified as follows.
This verification is processed for all the fluctuating shared through the classification process. This prevents unnecessary convergence and overload complexity in handling medical records at different time instances. In Table 4, the and for the varying in different sharing time along with the complexity is tabulated.

Table 4.
and and Complexity.
In Table 4, the complexity is computed as the number of additional hashes generated due to to the actual existing hashes. The complexity is measured in terms of count of additional steps required for verification and authentication as observed in the keying process. If the impact of attacks is high, then the factor increases to prevent unnecessary data tampering or modification. Hence, in this case, the number of fluctuates as the classification is grouped under both the sharing instances.
5. Performance Analysis
The performance of the proposed BDL–IBS is assessed using simulations using an opportunistic network environment. In this environment, a maximum of 100,000 EHRs (unique and repeated) are shared for 110 users in different time instances. A user is capable of generating four Qs at the same time, for which the sharing interval is 90 s (max). The medical server of storage 4 × 1 TB is used for storing LHRs, and two blockchain servers with restricted read/write access are configured in this simulation environment. The medical server is capable of dispatching 20 records of size 70 mb in 1 s time. The maximum wait time for a record is 60 s, and the hash process follows hyperelliptic curve cryptography of a maximum size of 160 bits. Similarly, and is fit as 48-bits and 36-bit, respectively. Using this simulation environment, the existing 31FF [23], BDe HA [26], and SCNN–DGT [16] methods are considered for comparative analysis. For this comparative analysis, the metrics sharing ratio, response time, computation time, and convergence time are analyzed.
5.1. Successful Sharing Ratio
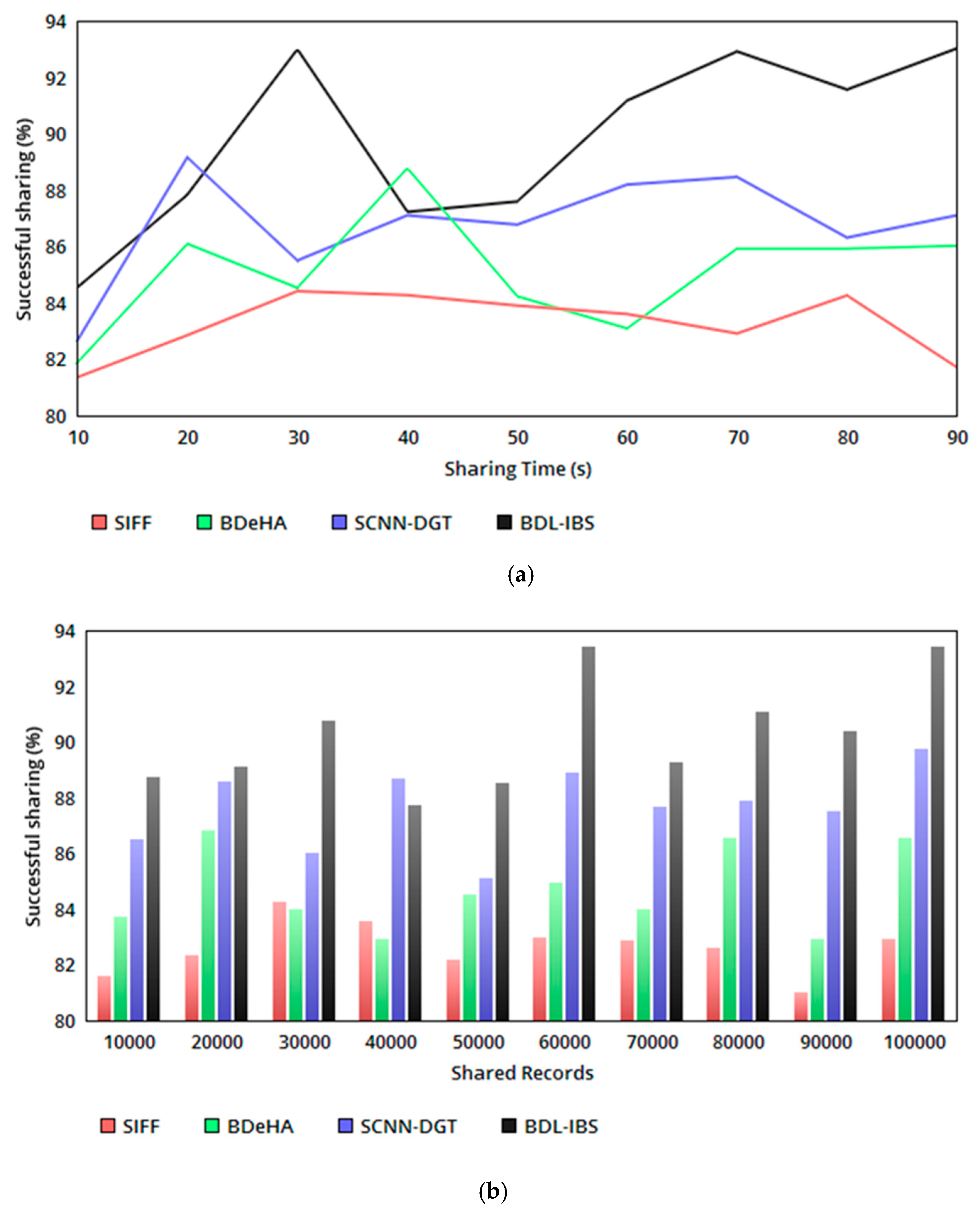
The proposed security system relies on record—user-access-based trust and differential authentication to improve the successful sharing of EHRs. The trust-based relationship between and is validated for the possible conditions in Table 2, generating and at different instances. In the sharing instances, pursuing/pausing sharing is determining based on or conditions. This condition-based decision-making determines for to instances and or for instances in either sequential/concurrent manner. The concentric sharing process follows for any instance of ; if the is maximum, then the sharing is performed either in a sequential or concurrent manner. In this process, the blockchain updates the trust for the linear and relation, which remains unchanged. Therefore, sharing for varying time and EHRs follows conditional satisfaction as in Table 2, achieving a high successful sharing ratio (refer to Figure 4a, b).
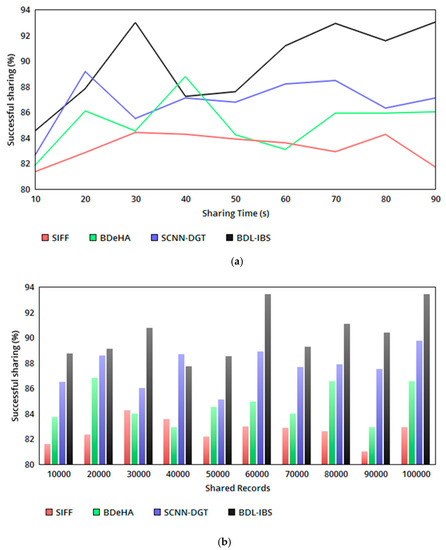
Figure 4.
(a) Successful sharing ratio versus sharing time. (b) Successful sharing ratio versus shared records.
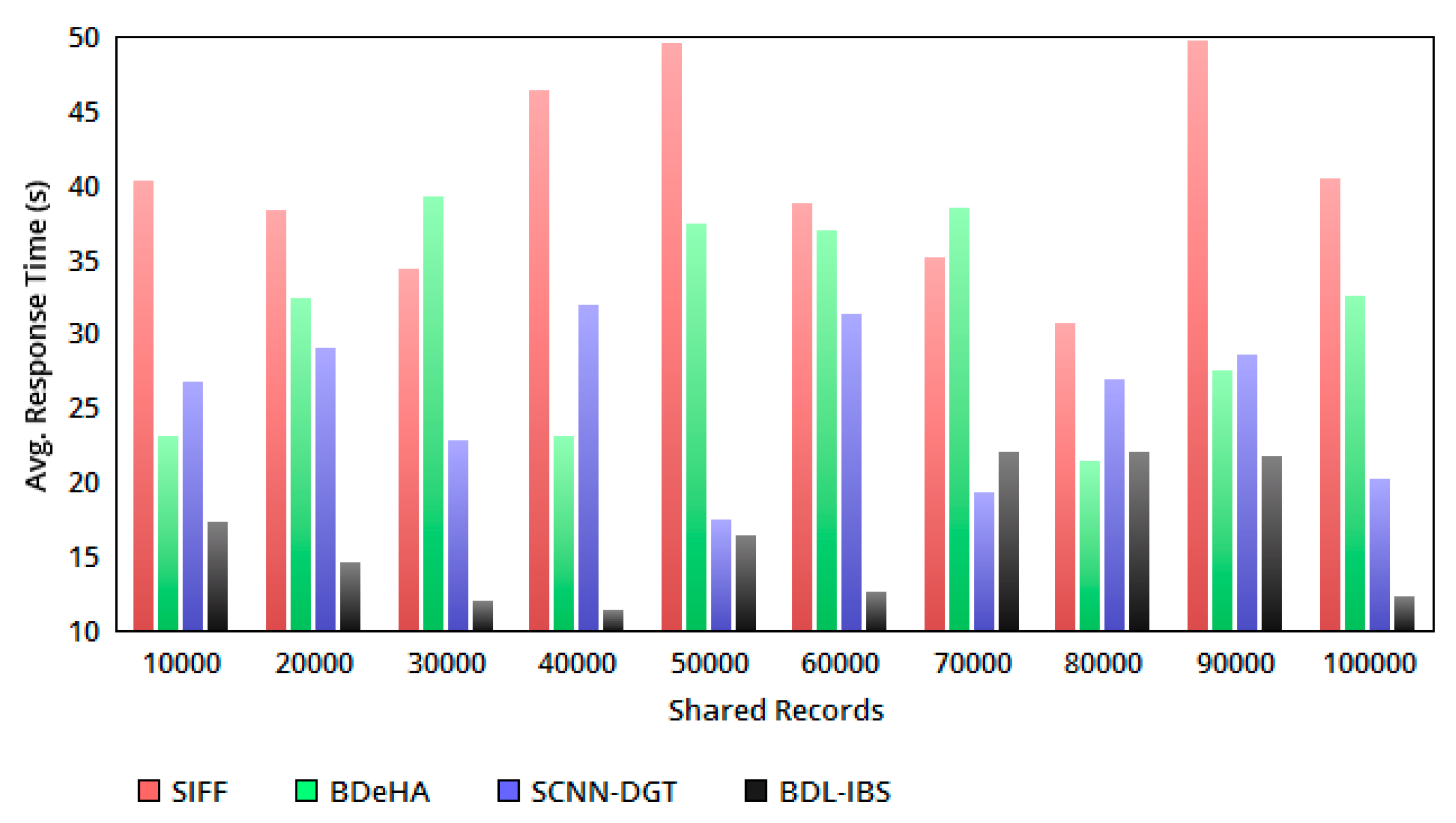
5.2. Response Time
The sharing time is ensured in all the instances of EHR processing for the received Q. If is observed, then the response time increases. For analyzing the instances of sharing , the variable and is differentiated. In this case, for is estimated as and independently. If the condition is achieved, then the varying point is identified to differentiate the sharing of EHRs. Therefore, the joint sharing is not facilitated for trust varying or condition 1 (Table 2), dissatisfying users. Hence, a small wait time in a response is experienced; this disintegrates the conditions of , where concurrent sharing and authentication is performed without additional wait time. Therefore, for the conditions 1 and 2, the response time for a Q from the end user is less compared to the other methods (refer to Figure 5).
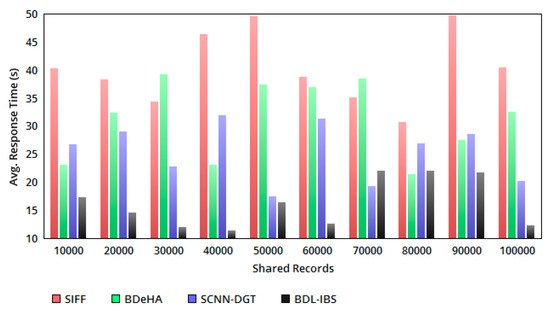
Figure 5.
Avg. response time versus shared records.
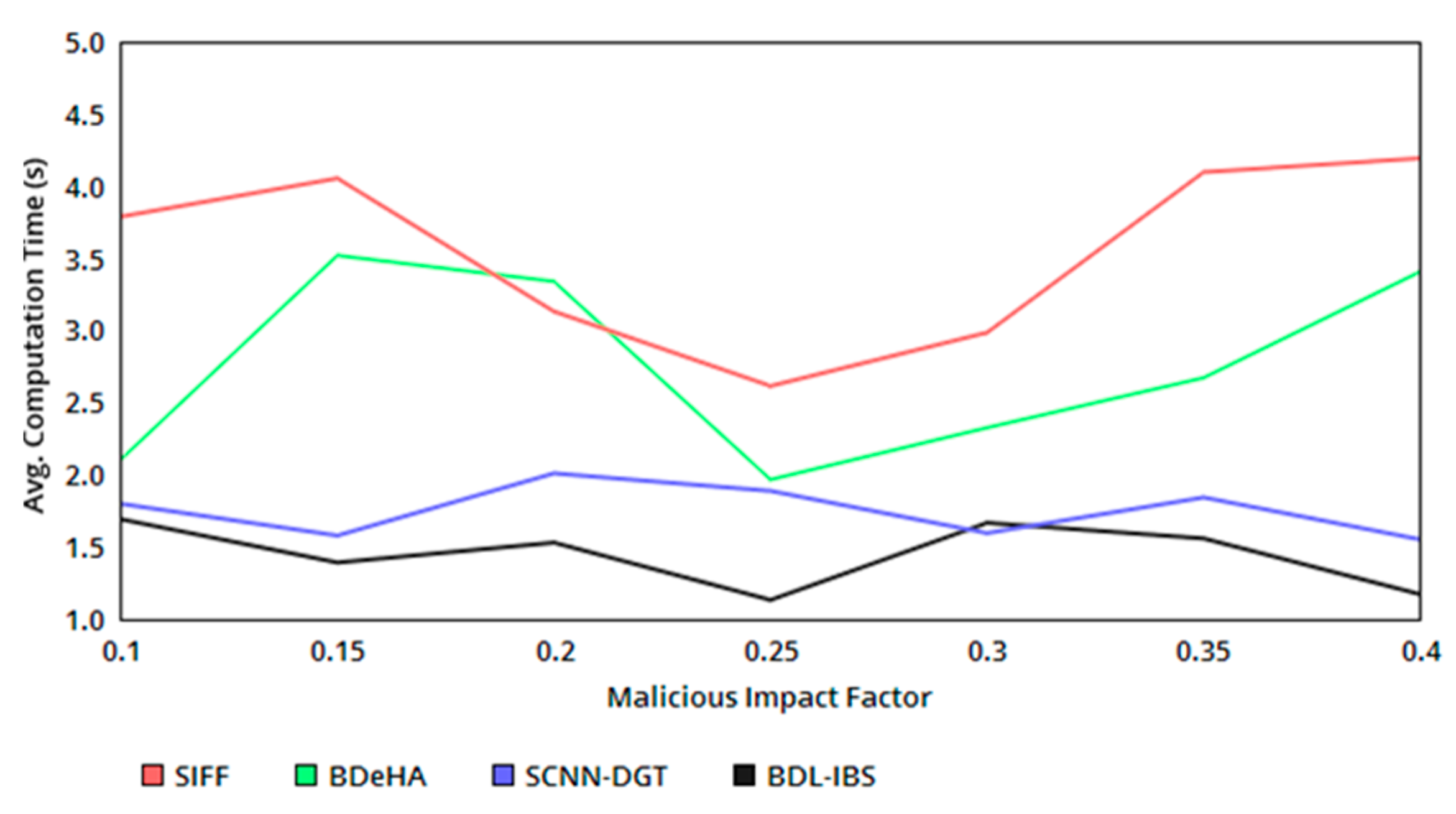
5.3. Computation Time
Figure 6 presents the computation time of the proposed system as a comparative analysis with the existing methods. The authentication computing process requires either of the instances based on , from which HMB and Hu are commonly adapted for the varying impact of untrusted users (classified under conditions 3 and 5 from Table 2). This helps to process the same number of with the different authentication process and thereby reduces the complexity and required computations in the sequential sharing. Instead, the concurrent dissemination process of the records requires a change in first-level authentication as Equations (12) and (17) to satisfy , confining within . Therefore, the required computation increases by 1, and hence some additional time for verifying the second authentication is required. The verifying process is common in both the instances, demanding less/same time of computation. Hence, the overall computation time is differentiated by , and and is less in the proposed security system.
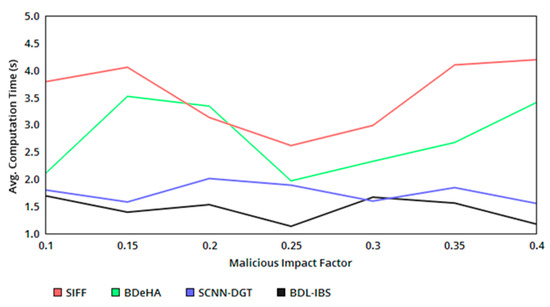
Figure 6.
Avg. computation time versus malicious impact factor.
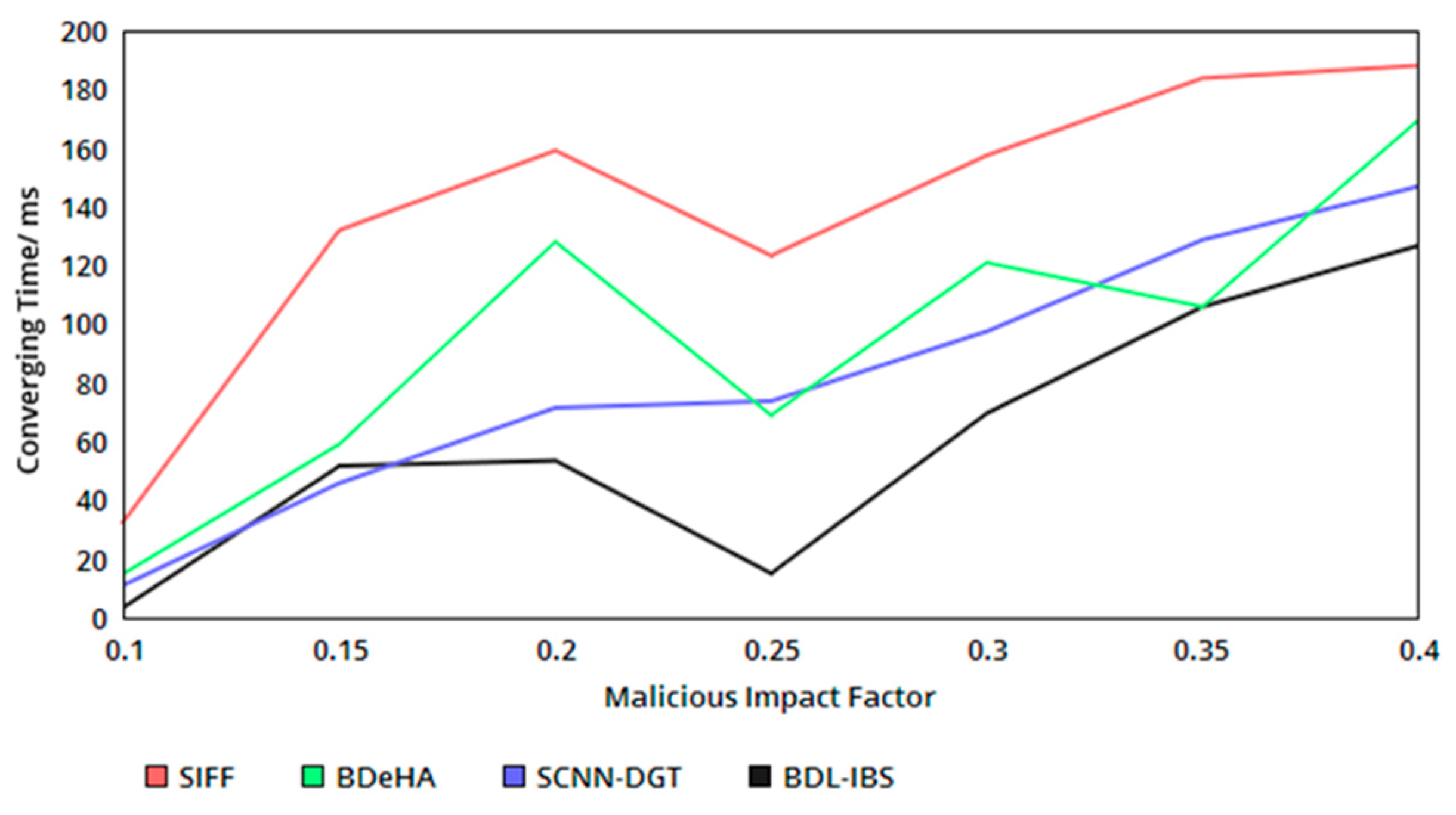
5.4. Convergence Time
The proposed security system achieves less convergence time in the authentication process. The convergence is identified using the classification of based on the occurrence of the and . Following the classification process, for , or , the converging time is identified in forehand, restricting in breaches in sharing and shared data tampering. Therefore, the identification based on and helps to divide the authentication for and instances. The verification and authentication observed for the above conditions are different, without generating different point and probabilities. Here, detection of segregates the authentication process for sequential and concurrent instances as and without requiring a new hash or verification procedure. As the number of convergence increases, the concurrency is increased without requiring additional computation steps. Therefore, the probabilistic classification of and for achieves less convergence in the proposed security system (refer to Figure 7). In Table 5, the comparative analysis results are tabulated.
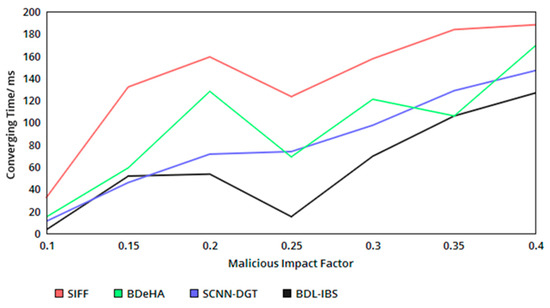
Figure 7.
Converging time versus malicious impact factor.

Table 5.
Comparative Analysis.
From Table 5, it is seen that the proposed security system is capable of achieving better performance by reducing the response time and increasing the ratio of successful sharing through trust-based validations. In the authentication process, the computation and converging time are found to be less since the instances of sharing are segregated based on .
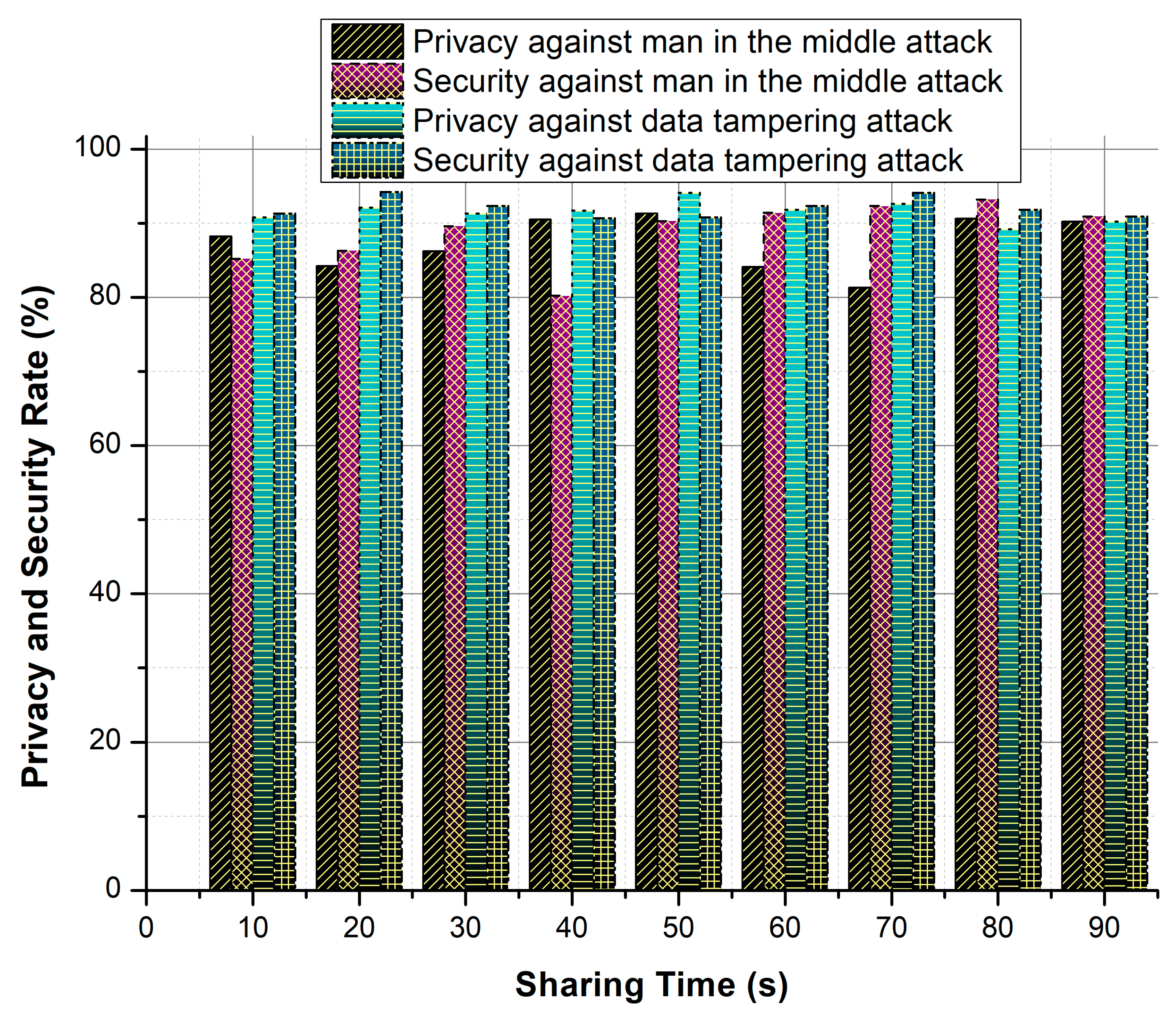
As in Table 5 and in Figure 8, the proposed security system achieves a very high performance for analyzing various attacks. The better performance is achieved by consuming low response time, less computation time and reduced converging time. As opposite, it achieves a high successful sharing rate.
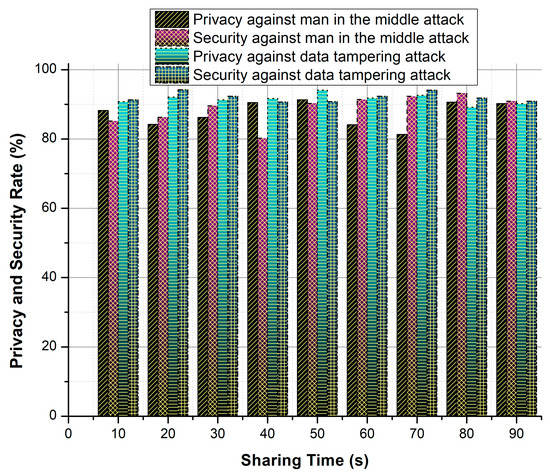
Figure 8.
Privacy and security ratio against attacks.
6. Conclusions
This paper introduced a blockchain and distributed ledger-based improved biomedical security system for improving the privacy and security of EHRs. This security system relies on the blockchain paradigm for providing trust validation through linear decision-making. The authentication of EHRs is preceded using classification-based learning for identifying sequential and concurrent sharing. The process is focused on both user-level and sharing-level security and privacy of the biomedical systems. The classification of sharing instances helps to reduce the complex and overloaded computations in the authentication process with less computation time. The blockchain technology coupled with this process helps to share trust-related information and differentiate the sharing based on classification instances. The experimental analysis of the proposed security system shows that it is capable of increasing the sharing ratio by 8.077% and 7.03% for sharing time and records, respectively. It also achieves 20.11% less response time compared to the other methods. In the case of authentication, the proposed system confines computation and convergence time by 10.26% and 12.31%.
Author Contributions
Formal analysis, H.L.; funding acquisition, H.L.; methodology, R.G.C.; project administration, O.S.M.; resources, R.G.C.; software, H.L.; supervision, O.S.M.; validation, O.S.M.; visualization, R.G.C. All authors have read and agreed to the published version of the manuscript.
Funding
Thanks to the Lanzhou Jiaotong University Tianyou Young Talent Promotion Program (2019) for supporting this work.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Piras, E.M.; Cabitza, F.; Lewkowicz, M.; Bannon, L. Personal health records and patient-oriented infrastructures: Building technology, shaping (new) patients and healthcare practitioners. Comput. Support. Cooper. Work CSCW 2019, 28, 1001–1009. [Google Scholar] [CrossRef]
- Tsai, M.F.; Hung, S.Y.; Yu, W.J.; Chen, C.C.; Yen, D.C. Understanding physicians adoption of electronic medical records: Healthcare technology self-efficacy, service level and risk perspectives. Comput. Stand. Interfaces 2019, 66, 103342. [Google Scholar] [CrossRef]
- Muthu, B.A.; Sivaparthipan, C.B.; Manogaran, G.; Sundarasekar, R.; Kadry, S.; Shanthini, A.; Dasel, A. IOT based wearable sensor for diseases prediction and symptom analysis in healthcare sector. Peer Peer Netw. Appl. 2020, 1–12. [Google Scholar] [CrossRef]
- Baskar, S.; Shakeel, P.M.; Kumar, R.; Burhanuddin, M.A.; Sampath, R. A dynamic and interoperable communication framework for controlling the operations of wearable sensors in smart healthcare applications. Comput. Commun. 2020, 149, 17–26. [Google Scholar] [CrossRef]
- Gu, D.; Li, T.; Wang, X.; Yang, X.; Yu, Z. Visualizing the intellectual structure and evolution of electronic health and telemedicine research. Int. J. Med. Inform. 2019, 130, 103947. [Google Scholar] [CrossRef]
- Manogaran, G.; Lopez, D. A survey of big data architectures and machine learning algorithms in healthcare. Int. J. Biomed. Eng. Technol. 2017, 25, 182–211. [Google Scholar] [CrossRef]
- Enaizan, O.; Zaidan, A.A.; Alwi, N.H.M.; Zaidan, B.B.; Alsalem, M.A.; Albahri, O.S.; Albahri, A.S. Electronic medical record systems: Decision support examination framework for individual, security and privacy concerns using multi-perspective analysis. Health Technol. 2018, 10, 795–822. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. Continuous patient monitoring with a patient centric agent: A block architecture. IEEE Access 2018, 6, 32700–32726. [Google Scholar] [CrossRef]
- Zhang, P.; Schmidt, D.C.; White, J.; Lenz, G. Block chain technology offers potential in healthcare. Pharmac. Econ. Outcomes News 2018, 809, 1–41. [Google Scholar]
- Radanović, I.; Likić, R. Opportunities for use of block chain technology in medicine. Appl. Health Econ. Health Policy 2018, 16, 583–590. [Google Scholar] [CrossRef]
- Firdaus, A.; Anuar, N.B.; Razak, M.F.A.; Hashem, I.A.T.; Bachok, S.; Sangaiah, A.K. Root exploit detection and features optimization: Mobile device and block chain based medical data management. J. Med. Syst. 2018, 42, 112. [Google Scholar] [CrossRef] [PubMed]
- Manogaran, G.; Varatharajan, R.; Lopez, D.; Kumar, P.M.; Sundarasekar, R.; Thota, C. A new architecture of internet of things and big data ecosystem for secured smart healthcare monitoring and alerting. Futur. Gener. Comput. Syst. 2017, 80, 1–10. [Google Scholar] [CrossRef]
- Tanwar, S.; Parekh, K.; Evans, R. Block chain—Based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 2020, 50, 102407. [Google Scholar]
- Pujitha, A.K.; Sivaswamy, J. Solution to overcome the sparsity issue of annotated data in medical domain. CAAI Trans. Intell. Technol. 2018, 3, 153–160. [Google Scholar] [CrossRef]
- Sun, Y.; Lo, F.P.W.; Lo, B. Security and privacy for the internet of medical things enabled healthcare systems: A survey. IEEE Access 2019, 7, 183339–183355. [Google Scholar] [CrossRef]
- Thakur, S.; Singh, A.K.; Ghrera, S.P.; Elhoseny, M. Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed. Tools Appl. 2019, 78, 3457–3470. [Google Scholar] [CrossRef]
- Raisaro, J.L.; Troncoso-Pastoriza, J.R.; Misbach, M.; Sousa, J.S.; Pradervand, S.; Missiaglia, E.; Michielin, O.; Ford, B.; Hubaux, J.P. MedCo: Enabling secure and privacy-Preserving exploration of distributed clinical and genomic data. IEEE/ACM Trans. Computat. Biol. Bioinform. 2019, 16, 1328–1341. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Conti, M.; Vasilakos, A.V. A novel authentication and key agreement scheme for implantable medical devices deployment. IEEE J. Biomed. Health Inform. 2017, 22, 1299–1309. [Google Scholar] [CrossRef]
- Shakeel, P.M.; Baskar, S.; Dhulipala, V.R.S.; Mishra, S.; Jaber, M.M. Maintaining security and privacy in health care system using learning based deep-Q-networks. J. Med. Syst. 2018, 42, 186. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Gope, P.; Choo, K.K.R.; Tapas, N. Anonymity preserving and lightweight multimedical server authentication protocol for telecare medical information system. IEEE J. Biomed. Health Inform. 2019, 23, 1749–1759. [Google Scholar] [CrossRef]
- Fatima, A.; Colomo-Palacios, R. Security aspects in healthcare information systems: A systematic mapping. Proc. Comput. Sci. 2018, 138, 12–19. [Google Scholar] [CrossRef]
- Tang, W.; Ren, J.; Zhang, Y. Enabling trusted and privacy-preserving healthcare services in social media health networks. IEEE Trans. Multimed. 2019, 21, 579–590. [Google Scholar] [CrossRef]
- Salnitri, M.; Angelopoulos, K.; Pavlidis, M.; Diamantopoulou, V.; Mouratidis, H.; Giorgini, P. Modelling the interplay of security, privacy and trust in sociotechnical systems: A computer-aided design approach. Softw. Syst. Model. 2019, 19, 467–491. [Google Scholar] [CrossRef]
- Kong, F.; Zhou, Y.; Xia, B.; Pan, L.; Zhu, L. A security reputation model for IoT health data using S-AlexNet and dynamic game theory in cloud computing Environment. IEEE Access 2019, 7, 161822–161830. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, D.; Zhang, Y. Block chain-based personal health records sharing scheme with data ontegrity verifiable. IEEE Access 2019, 7, 102887–102901. [Google Scholar] [CrossRef]
- Zhao, H.; Bai, P.; Peng, Y.; Xu, R. Efficient key management scheme for health block chain. CAAI Trans. Intell. Technol. 2018, 3, 114–118. [Google Scholar] [CrossRef]
- Guo, R.; Shi, H.; Zheng, D.; Jing, C.; Zhuang, C.; Wang, Z. Flexible and efficient block chain-based ABE scheme with multi-authority for medical on demand in telemedicine system. IEEE Access 2019, 7, 88012–88025. [Google Scholar] [CrossRef]
- Daraghmi, E.Y.; Daraghmi, Y.A.; Yuan, S.M. MedChain: A design of block chain-based system for medical records access and permissions management. IEEE Access 2019, 7, 164595–164613. [Google Scholar] [CrossRef]
- Guo, R.; Shi, H.; Zhao, Q.; Zheng, D. Secure attribute-based signature scheme with multiple authorities for block chain in electronic health records systems. IEEE Access 2018, 6, 11676–11686. [Google Scholar] [CrossRef]
- Chen, Y.; Ding, S.; Xu, Z.; Zheng, H.; Yang, S. Block chain-based medical records secure storage and medical service framework. J. Med. Syst. 2018, 43, 5. [Google Scholar] [CrossRef]
- Tian, H.; He, J.; Ding, Y. Medical data management on blockchain with privacy. J. Med. Syst. 2019, 43, 26. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Han, K.; Alexandridis, A.; Chen, Z.; Zilic, Z.; Pang, Y.; Jeon, G.; Piccialli, F. A block chain-based eHealthcare system interoperating with WBANs. Future Gener. Comput. Syst. 2019, 110, 675–685. [Google Scholar] [CrossRef]
- Brunese, L.; Mercaldo, F.; Reginelli, A.; Santone, A. A block chain based proposal for protecting healthcare systems through formal methods. Proc. Comput. Sci. 2019, 159, 1787–1794. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. Blockchain leveraged decentralized IoTeHealth framework. Internet Things 2020, 9, 100159. [Google Scholar] [CrossRef]
- Griggs, K.N.; Ossipova, O.; Kohlios, C.P.; Baccarini, A.N.; Howson, E.A.; Hayajneh, T. Healthcare blockchain system using smart contracts for secure automated remote patient monitoring. J. Med. Syst. 2018, 42, 130. [Google Scholar] [CrossRef] [PubMed]
- Brodersen, C.; Kalis, B.; Leong, C.; Mitchell, E.; Pupo, E.; Truscott, A.; Accenture, L. Blockchain: Securing A New Health Interoperability Experience. Available online: http://www.truevaluemetrics.org/DBpdfs/Technology/Blockchain/2-49-accenture_onc_blockchain_challenge_response_august8_final.pdf (accessed on 27 July 2020).
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).