Abstract
Some properties of generalized convexity for sets and functions are identified in case of the reliability polynomials of two dual minimal networks. A method of approximating the reliability polynomials of two dual minimal network is developed based on their mutual complementarity properties. The approximating objects are from the class of quadratic spline functions, constructed based on both interpolation conditions and shape knowledge. It is proved that the approximant objects preserve both the high-order convexity and some extremum properties of the exact reliability polynomials. It leads to pointing out the area of the network where the maximum number of paths is achieved. Numerical examples and simulations show the performance of the algorithm, both in terms of low complexity, small error and shape preserving. Possibilities of increasing the accuracy of approximation are discussed.
1. Introduction
From the earliest days of network reliability, researchers have tried to develop algorithms to efficiently compute the reliability of graphs/networks. In a recent survey paper [1], Brown et al. have rediscovered the way of this research domain, by shedding light on some of the theoretical advances made in the past as well as the new directions. This scientific adventure started with the work of Moore and Shannon [2,3] and von Neumann [4], when the first foundations of the field were settled. In the late seventies [5], Valiant demonstrated that the main computational problem, i.e., to compute the reliability polynomial of a two-terminal network, is #P-complete. Therefore, when the graph parameters are growing significantly, one has to find alternative methods for estimating reliability, such as (i) applying simplifications in order to reduce the computations as much as possible so that the algorithm becomes practically effective, (ii) bounding the reliability polynomial (using combinatorial methods and/or structural properties), and (iii) approximating the reliability polynomial such that the error of approximation is bounded by a relatively small quantity.
The less investigated topics related to network reliability are the analytical properties such as shape properties of the reliability polynomials, including convexity, the number of real roots and their density, etc. In order to compensate the complexity problems of computing the coefficients of the reliability polynomial of a two-terminal network, the authors of [6,7] proposed to approximate the polynomials using structural properties of the networks. In particular, duality is a characteristic that induces complementary properties on the coefficients, which are considered in the approximations. In [8], Hermite interpolation is used for hammock networks based on previous results on the shape [9]. Cubic splines are proposed in [6,7] and are suitable for any two-terminal networks. In [7], two methods of producing cubic splines are compared—Lagrange-type interpolation procedures and Bernstein approximation operator, emphasizing the accuracy of the methods. There are several advantages for taking duality into account in the context of approximations:
- Computing the first non-trivial (different from zero) coefficient of the reliability polynomial of a network enables one to directly obtain the value of the last non-trivial (different from the binomial coefficient) coefficient of the reliability polynomial of the dual network.
- Adjusting approximated coefficients of a network can be done more efficiently when duality is considered, as more information is taken into account.
- The error of simultaneous approximation of two dual networks can be more accurately estimated when compared to a single network approximation.
1.1. Our Contribution
The mutual behaviour of two dual networks, described from the point of view of their reliability, provides us with additional information, which is used as input in the construction of the algorithms from [6,7]. In this paper, we refine the approximation technique by considering the shape properties of the reliability polynomials of two dual two-terminal networks. A profound research on the shape of the reliability polynomials of two dual two-terminal networks is presented, starting from their complementarity properties [6,7]. Their mutual behaviour referring to high-order convexity properties, tangents properties, inflection points, etc. are emphasized. We construct approximation operators that preserve as many as possible shape properties. The use of the quadratic spline functions allows us to keep control on the approximation process from the point of view of shape preserving. The notations and abbreviations used in this article are summarized in Table 1.

Table 1.
Abbreviations and notations.
1.2. Outline of the Article
In Section 2, we describe the types of networks implied in our research and introduce the main definitions and properties regarding their reliability. Section 3 contains results referring to high-order convexity properties of the reliability polynomial of a MMN and the manner, in which these properties are transferred to the dual network. Some extremum properties of the coefficients function are discussed. An algorithm for simultaneous approximation of the reliability polynomials of two dual networks is described in Section 4 based on quadratic spline functions. The approximant functions are constructed to preserve, as much as possible, the shape properties of the reliability polynomials of MMNs. In Section 5, we simulate the approximation technique using the new algorithm. The shape properties of the approximant objects are emphasized, proving the performance of the algorithm from shape preserving point of view. We conclude the article in Section 6.
2. Preliminaries on Network Reliability
2.1. Matchstick Minimal Two-Terminal Networks
Any network made of n identical devices that has two distinguished terminals—a source S and a terminus T—is called a two-terminal network (denoted by in the sequel). can be characterized at least by three parameters: width (w), length (l), and size—w is the size of a “minimal cut” separating S from T, l is the size of a “minimal path” from S to In general, we have (see [2]). Any of width w and length l will be called a , or of type . All functions, as reliability polynomial, its coefficients function and various approximations, related to a will be denoted by a character having the index Any satisfying is minimal (see [2]), the members of the family of minimal s being denoted by MMN.
Matchstick Minimal Networks
Let l and w be two strictly positive integers. A is a MMN if and only if it can be designed in one of the following two ways: Either start by a parallel-of-series () of width w and length l and place vertical matchsticks arbitrarily, or start with a series-of-parallel () of width w and length l and remove vertical matchsticks arbitrarily.
Another way of defining a MMN, described in [10], is by using the bijection between the set of all MMNs of length l and width w and the set of all binary matrices . At any , we associate its matchstick incidence matrix , as
- if there is a matchstick at position ;
- if there is no matchstick at position .
Hammock Networks
MMNs presenting a “brick-wall” pattern are known as hammocks [2,3,11,12]. Starting from a , by alternately deleting matchsticks, one can construct a hammock. If w and l are both even, there are two hammocks ( and ); otherwise, only one hammock exists Using the matchstick incidence matrix, we have and (see Figure 1).
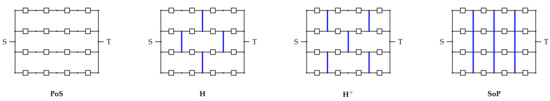
Figure 1.
Square 4-by-4 parallel-of-series, hammocks, and series-of-parallel.
Duality Properties
Let be a MMN. The dual of , denoted here by , was introduced in [2]. Duality properties were proved in [6,9] in case of particular MMNs, such as hammocks. Some duality properties, that are needed in the context of approximations (as mentioned in [6]), are recalled in the next subsection. Let us denote by the all-ones matrix and the bit-wise complement of a binary matrix as
where ⊕ denotes the XOR operation.
Theorem 1
([10]). Let be a . Then, either ( being the all parallel network) and we have is the all series network, or and we have
Notice that by Theorem 1, the dual of a is a .
2.2. Reliability Polynomial
The reliability of a is defined as the probability that the source S and the terminus T are connected, given that each device closes with probability The reliability polynomial is presented in the literature under several forms, depending on the basis of the linear space of polynomials that is taken into account. If the Bernstein basis
is used, then we have the so-called N-form (see in [2]):
The coefficient represents the number of ways one can select a subset of k devices in such that if these k devices are closed and the remaining are open, then the two terminals S and T are connected, i.e., is closed. Straightforward, well-known basic properties of can be immediately deduced from the definition.
Property 1
([2]). If is a , then
- ;
- ;
Corollary 1
([6]). Denoting by the coefficient of written in Bernstein basis, then the coefficients in (2) are . As consequence, we deduce that for all
In the sequel, we consider two dual MMNs, denoted by and All over the paper, the coefficients of the reliability polynomial of will be denoted as in (2) and the coefficients of the reliability polynomial of the dual network will be denoted by . The following complementarity property is well known:
Property 2
([2]). If and are the reliability polynomials of two dual MMNs of type respectively , then
Equation (3) leads to the following complementarity identity, proved in [6] (Property 2 p.80) for hammock networks:
Property 3
([6,7]). If and are coefficients of the reliability polynomials of two dual MMNs, and , then
for all
Identity (4) also holds for any dual 2TNs (the proof is identical).
Parallel-of-Series and Series-of-Parallel
For some type of MMNs there is a closed formula of the reliability polynomial.
Theorem 2
([13]). Let be a Then, we have
where denotes the integer part of the fraction.
The proof relies of the fact that one can write the coefficients of a using the formula
Combined with (4) one can deduce
Remark 1.
The coefficients of a also have a combinatorial interpretation, fact that allows one to deduce basic properties such as those in Proposition 1. Indeed, represents the number of ways one can distribute k balls among w urns, where the urns have height l, such that at least one urn is completely filled with balls.
Using the complementary property induced by duality (4), we deduce the following result.
Proposition 1.
Let be a Then, we have
Proof.
Any coefficient of an arbitrary is bigger that or equal to the same coefficient of an and smaller than or equal to the same coefficient of an Using Formula (6), one obtains the first inequality. As for the second inequality, we the formula for the coefficients of a , i.e., , combined with the fact that its dual is a This yields that the coefficient of an equals Therefore, a simple variable change implies the wanted result. □
3. Mutual Shape Properties of the Reliability Polynomials of Two Dual Networks
3.1. Convexity of High Order
Let us consider an interval and a function . Suppose that .
Definition 1.
The divided difference of order n of function f on points is the number defined by
Remark 2.
It is known (see, for example, in [14]) that if a function f is n-th order differentiable on a point , then the derivative equals to the limit of when all points tend to x.
The concept of convex function of high order on an interval was introduced in 1926 by E. Hopf [15]. T. Popoviciu [16] extended this concept to functions defined on an arbitrary set in 1934. Furthermore, T. Popoviciu [14] extensively studied this concept in case of real functions of several real variables.
Definition 2
([14]). Function f is said to be n-th order convex (non-concave, polynomial, non-convex, concave) on if
respectively, for all systems of points
The functions having one of the properties defined by means of (10) are generally called n-th order functions (see in [16,17]).
Remark 3.
The reliability polynomial of a network of type n is a n-th order polynomial function on , as every n-th degree polynomial has this property [15].
Remark 4.
If function f is -th order differentiable on , then, in view of Remark 2, it follows that condition (10) is expressible in terms of derivatives as follows: function f is n-th order convex (non-concave, polynomial, non-convex, concave) on if
respectively, for all The one side derivatives are considered on points a and
3.2. Convexity Properties of the Reliability Polynomials of Two Dual Minimal Networks
With the properties of convexity being accidentally mentioned, both in case of the reliability polynomial of a MMN (see in [6,7]) and in case of its coefficients sequence (see in [18]), this subsection presents the research results on the presence of various types of high-order convexity to the reliability polynomials of two dual MMNs. The impact of networks duality on the shape of the polynomials is emphasized.
Theorem 3.
If and are the reliability polynomials of two dual MMNs of type , respectively, , and , then the following holds.
- 1.
- If k is odd, then and are -th order functions of the same type on each sub-interval of : either both are -th order convex or both are -th order concave.
- 2.
- If k is even then and are -th order functions of opposite types on each sub-interval of : if one polynomial is -th order convex then the other one is -th order concave, and conversely.
Proof.
Figure 2 shows the mutual behaviour of the derivatives of the reliability polynomials of two dual hammock networks. The corresponding impact on the shape of reliability polynomials is described by the following corollaries.
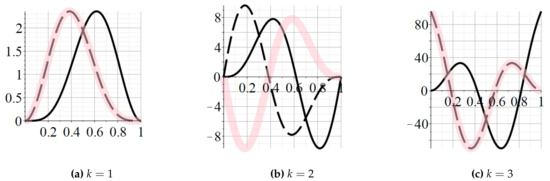
Figure 2.
(dash black line), (solid black line), and (solid pink line) for the 3-by-5 hammock network.
Corollary 2.
Suppose that and . Relation (12) implies that if is an inflection point of the polynomial then it is an inflection point of which implies that is an inflection point of
Corollary 3.
Suppose that k is odd and take in Equation (12). It follows that
which means that all derivatives of odd order of the reliability polynomials of two dual networks, and , have the same value. In particular, if one gets that the two polynomials, and , have parallel tangents at
Corollary 4.
Suppose that k is even and take in Equation (12). It follows that
In particular, if one gets that if is an inflection point of a reliability polynomial of a network then it is an inflection point of the reliability polynomial of the dual network as well.
Corollary 5.
Suppose that is a minimal network of length and width w, which means that . Property 1 implies that all derivatives of order of its reliability polynomial equal to 0 at . As consequence, the x-axis is tangent to the graph of this polynomial at and the curvature radius of tends to infinity when . All these, together with the non-negativity of a reliability polynomial over , imply that the polynomial is first-order convex in the neighborhood of the origin. Theorem 3 implies that the reliability polynomial is concave in the neighborhood of the origin. The functions and are symmetric with respect to the straight line , which implies that it is also convex in the neighborhood of the origin.
Another convexity property of functions that is important in the context of the reliability theory in case of s is the log-convexity, defined as follows:
Definition 3
([19]). A function , , is said to be log-convex (or log-concave) on E if for all and function is convex (or concave, respectively) on E.
Remark 5.
It is proved in [19], pp. 207, that the log-convex (log-concave) functions are also convex (concave) functions, but the converse is not true. Based on the results of Huh [18] and Lenz [20], the sequence of the coefficients of a the reliability polynomial is log-concave. This property will be used in the sequel, because it implies the concavity of the coefficients function of a reliability polynomial, which will be defined in the next section.
Consider a . The reliability polynomial of this network, expressed in Bernstein basis, is defined by (2). Knowing the reliability polynomial is equivalent to knowing the corresponding function defined by (13). We consider the dual network together with its reliability polynomial . Let us define two functions, which we call coefficients functions in the sequel: and by
In fact, function (respectively, ) is the segmentary linear function obtained based on the coefficient functions of the reliability polynomials two dual hammock networks, as defined in [7,18,20]. Knowing the reliability polynomials of the two dual networks is equivalent to knowing the two coefficient functions defined by (13) and (14).
Remark 6.
The coefficient function is concave on . The coefficients function is concave functions on . This shape is a consequence of Property 1 and Remark 5.
3.3. Extremal Properties of the Coefficients Functions
The sequence of coefficients of the reliability polynomial have some monotony properties, that are consequences both of their complementarity property (4) and of Remark 5. The concavity of functions and on , together with Property 1, imply that the index of the maximum coefficient of the two reliability polynomials is in , and , respectively. We construct, in the next section, a method to approximate the reliability polynomials of two dual networks, denoted here by of -type, and its dual of -type. We prove that the maximum coefficient of the approximate reliability polynomial of the is reached in the same interval as the maximum coefficient of the exact polynomial. The most frequent interval that contains the index of the maximum point of , as identified by studying the completely known reliability polynomials of small size hammock networks and also small size compositions of series and parallel, is
Few networks have the index of the maximum coefficient of the reliability polynomial not belonging to but to a larger interval,
Few examples are presented in Table 2. The maximum coefficient of the reliability polynomial is denoted by , and the value of the index k of the maximum coefficient is denoted by in this table.

Table 2.
Extremal values of the coefficients functions for small hammocks.
A special case is presented by Parallel-of-series and Series-of-parallel networks. In case of a , we proved that index of the maximum value of the coefficients (6) is in We omit the proof of this property both because of its length and because it exceeds the purpose of this paper. However, we remark that the coefficients of the reliability polynomial of all types of network have the same extremal property, which we retrieve to its approximant.
4. Shape-Preserving Simultaneous Approximation of the Reliability Polynomials of Two Dual Two-Terminal Networks
4.1. An Efficient Constructive Method
In this section, we intend to build a method of approximation of functions and by means of a spline function, starting from the properties of the reliability polynomials described above and in [11,21]. Some generalized convexity properties as described in [22] will be used. We construct segmentary polynomial function meant to imitate the shape of functions and . As proved in [17], given a continuous function on a bounded closed interval, the Bernstein approximation polynomial of degree s of this function preserves the convexity of the approximated function (see also in [23,24]). This property gave us the idea of approximating functions and by means of polynomials imitating the Bernstein polynomial of third degree in [6]. The results of the cubic spline approximation algorithm presented in [6] constructed both by means of Lagrange interpolation and by a weakened Bernstein type approximation operator are compared in [7]. Furthermore, the algorithm from in [6] is refined in [7] in order to improve the accuracy of the approximation. In this paper, we describe a version of the approximation algorithm from in [7] obtained by replacing the cubic splines with quadratic splines. The initial information on the two coefficients functions and refers to their values on intervals and respectively. We also have shape information on these functions, i.e., the concavity of these functions is a consequence of the results from [18,20]. We complete the missing information from intervals and respectively by the known information on the shape of the coefficients functions and . This is the reason to carefully chose the initial knots in order to generate a function having the same shape as and . In order to approximate and we construct two continuous quadratic spline functions and that verify the following conditions:
for some points and .
Remark 7.
If and , it is always possible to find two numbers and such as the two conditions and are valid. Indeed, one can always compute and by means of the technique from [11]. Then, one can compute and using the coefficients complementarity relation (4). The relation(4) implies that at least two of the four coefficients verify the needed conditions.
In order to define the two functions and , we have previously taken into account the convexity properties of the second-degree polynomial that allows us to define approximation operators that preserve some shape properties of the approximated curve. In the sequel we define an approximation function by interpolating the coefficients functions using quadratic splines conveniently chosen in order to preserve the convexity and concavity shapes. Function is searched as
Here,
are the straight line segments determined by points and , for all respectively. Furthermore, the coefficients are obtained using the interpolation conditions:
Function is searched as
Here,
are the straight line segments determined by points and , for all . As above, the coefficients are obtained using the interpolation conditions:
The interpolation conditions (18) and (20) lead to the following systems of linear equations in order to compute the functions and using (17) and (19):
The approximation algorithm, based on determining the functions and using the solutions of the two systems of equations obtained by Cramer’s rule, is as follows.
The algorithm:
- Step 1.
- Compute the values of two coefficients and using some technique from literature. If and are chosen then we use the method from [11] and then we compute the values and using (4).Here, we put and .
- Step 2.
- Compute the coefficients of the approximate functions and , by
- Step 3.
- Step 4.
- Compute ,
- Step 5.
- Compute ,
- Step 6.
- Computefor each .
- Step 7.
- Compute , and .
- Step 8.
- If then replace , and put (or converse, if the dual coefficient is negative).
- Step 9.
- Output the approximation polynomials
Remark 8.
The overall time complexity of computing and is , when This fact can be easily deduce either by inspecting each step of our algorithm or by adapting the proof of Theorem 5 from in [7].
4.2. Shape and Extremum Properties of the Approximation Operator
In this subsection we suppose that both and and at least one inequality is strict. It implies that .
Remark 9.
All the invariant properties proved in [7] (Property 14, Corollary 15 and Property 16) in case of the use of an approximation operator constructed by means of cubic spline functions stay valid. One can prove that the approximate reliability polynomial of two dual networks obtained by using quadratic splines keep invariant the complementarity relations (3), (4) and their consequences in a similar manner as in [7], which means that
Remark 10.
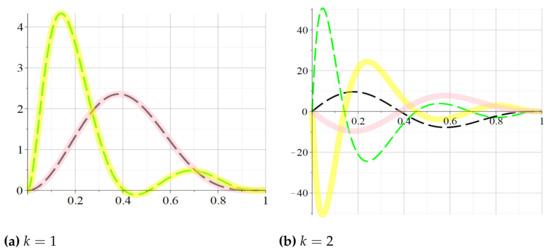
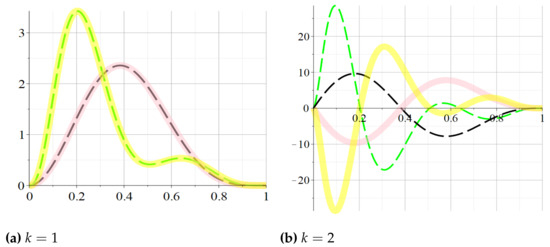
As a consequence of (28), it follows that all the properties of the derivatives of the reliability polynomials of two dual networks proved in the previous section, Theorem 3, stay valid in case of the approximation polynomials. The corollaries of Theorem 3 stay also valid, implying that the same type of high-order convexity are retrieved to the approximation polynomials. Simulations on small-sized MMNs, showing these shape properties are in Figure 3 and Figure 4.

Figure 3.
(dash black line), (solid pink line), and (dash green line) and (solid yellow line) for the 3-by-5 hammock network with input data

Figure 4.
(dash black line), (solid pink line), and (dash green line) and (solid yellow line) for the 3-by-5 hammock network with input data
It is proved in [18,20] that the coefficients sequence of the reliability polynomial of a MMN has the log-concavity property. It implies, as discussed above, that the coefficients functions and are concave on intervals and , respectively. The concavity is preserved by the spline approximation functions and . As consequence of the known information on the coefficients function (13) and (14), it follows that there are two numbers and such as and .
Property 4.
If and and if such as , then function is concave and on interval .
Proof.
It is either obvious or elementary to prove that
Using these inequalities, one gets that , and . The concavity of the parabola is a consequence of the negativity of A. The non-negativity of function is a consequence of its definition (17) and the hypothesis on s. □
Remark 11.
If and and if is chosen such as then
As consequence, function is concave and on .
If and , then we denote the length of interval by in the sequel.
Property 5.
Suppose that and . Suppose that s is chosen such that . Let us denote by the maximum point of function on . Then,
Proof.
Let us denote the length of intervals , and by , and , respectively. Because , it follows that and . The abscissa of the vertex of parabola is
From the hypothesis and also as in the proof of Property 4, one gets
which means that the abscissa of the maximum point is greater than the middle of the interval . The same procedure applies in case of the dual network. □
Property 6.
Suppose that and . Suppose that . Let us denote by the maximum point of function on . Then,
Proof.
The lower bound is a particular case of Property 5. To prove the upper bound property, we search for a real number S such as
This inequality is equivalent to
Because of the hypothesis , one gets
which meas that and
as required. □
Property 7.
Suppose that and . Suppose that s is chosen such that . Let us denote by the maximum point of function on . Let If
then
Proof.
One may write the abscissa , which was computed above, as
Taking into account that, and , one gets
Due to (31), it follows the required inequality,
which ends the proof. □
Corollary 6.
Suppose that and . Suppose that t is chosen such that and condition (31) holds, i.e., , where
Let us denote by the maximum point of function on . Then the abscissa of the maximum point of the dual network has the same boundary property:
Proof.
The boundary properties of the quadratic spline approximation of the coefficients function in case of the dual case are obtained following the same reasoning as in the proof of Properties 5 and 7, using the coefficients and . □
Remark 12.
Practical simulations show that the hypothesis on s of being chosen such that is a necessary condition for Properties 4, 5, and 7. The following examples show that the sufficiency does not hold. There are cases when but (31) holds, which is shown by the following examples. The necessary and sufficient condition for Property 7 consists in both hypotheses.
Example 1.



We consider few cases of small hammock networks as in [11]. After performing simulations taking and we have obtained that in cases inequality implies (31). This implication is not valid in cases . Table 3, Table 4 and Table 5 contain the numerical results obtained in each case. The exact coefficients included in Table 3, Table 4 and Table 5 are taken from [11].

Table 3.
The case of with : if we have (31) valid but the coefficient is less than

Table 4.
The case of of : if we have (31) valid but the coefficient is less than the binomial.

Table 5.
The case of of : if we have (31) valid but the coefficient is less than the binomial.
Example 2.
A few interesting negative results, showing various behaviour of the approximant if , are found in the following cases:
- If and then and , which means that the approximant is concave. As one can see, Property 4 and Property 5 are valid. But , exceeding the upper bound from Property 7.
- If and , then and , which means that the approximant is convex. As neither Property 4, nor Property 5, nor Property 7 is valid.
- If and then and , which means that the approximant is concave, validating Property 4. But and also . It means that Property 5 is true, but Property 7 is not valid.
- If -dual and then and , which means that the approximant is convex. As neither Property 4, nor Property 5, nor Property 7 is valid.
- If -dual and then and , which means that the approximant is concave, validating Property 4. However, and also . It means that Property 5 is true, but Property 7 is not valid.
4.3. Error Estimation
In this subsection, we also suppose that both and and at least one of the inequalities is strict. The small amount of initial data and of theoretic information on the reliability polynomial of a MMN arise difficulties in assessing the error of the approximation. The error of the corresponding approximated reliability polynomial is determined using the Chebychev distance between functions, because it gives information on the number of exact decimals obtained by approximation. As consequence, one can prove that the same upper bound of the error of this approximation as obtained in [7]. All the same, a more refined upper bound than the result from [7] is proved in this subsection in case of approximation using quadratic spline functions.
Proposition 2.
Let be a -type MMN, and let us denote
Then we have
Proof.
Using the definition of and we obtain
However, according to the algorithm,
and, using (4), one can compute
for each . Taking into account (17), we evaluate as follows:
According to (17) and (19), the absolute maximum value of this second degree polynomial is the absolute value of the ordinate of its vertex. The maximum value of this function on is either in the maximum point of this polynomial or a value in the extremities of this interval. An elementary computation gives
for all Replacing this value in the previous evaluation of the approximation error one gets the required upper bound. □
Remark 13.
The error of approximation can be improved by conveniently choosing the initial coefficients, and , if possible.
5. Simulation Results
We have conducted simulations for hammock networks of size The exact coefficients are extracted from [11]. First, we have implemented our algorithm and with input data and the corresponding
The results are illustrated in Table 6. The first row in each sub-table represents the exact coefficients. The second rows represent the results obtained by means of our algorithm. We notice that the first four non-zero approximations are rather big compared with the exact values, while the last approximated coefficients are much closer to the exact values.

Table 6.
Exact coefficients of the 3-by-5 hammock and its dual, and approximations using our algorithm with input points , as well with input point
Second, we have implemented the algorithm with input data and the corresponding In this scenario we had to change the systems of Equations (21) and (22). More exactly, the new equations we had to solve are
We notice from the third row in each sub-table of Table 6 that using more information (extra coefficients) our algorithm outputs a much finer approximation. Indeed, when computing the error of approximation for the two versions, we have obtained for the version using and for the version using , clearly pointing out the advantage of the second version. This implies that our algorithm can be adapted using more information (extra coefficients) in order to produce better results.
Properties of the Approximated Polynomials
The approximated polynomials were also computed and some of the theoretical results were verified. Indeed, when we investigate the shape properties of the approximated polynomials we notice that they preserve the complementary properties. Of the properties we choose to illustrate here is the behavior of the derivatives. In Figure 3 we plot the derivatives of the approximated polynomials using the variant of the algorithm with input data , and in Figure 4 those obtained with input data We plot the first two derivatives, and observe the following:
- ;
- .
The Case of Self-Dual Networks
As our method is using some extra information provided by means of duality, we have simulated the case of self-dual networks. We have considered the 5-by-5 hammock network, a case for which we have In Figure 5, we have plot the first derivatives of the networks and of the approximations.
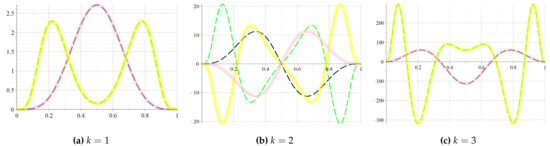
Figure 5.
(dash black line), (solid pink line), and (dash green line) and (solid yellow line) for the 5-by-5 hammock network.
Both the reliability polynomial as well as its approximant satisfy This mainly comes from the fact that In this case, the error of approximation is lower than Notice than, even if less information is used for the particular case of self-dual networks, the error of approximation is comparable with the case of smaller networks such as the 3-by-5 hammock. This fact points out that our method could eventually be used in the case of some larger networks.
6. Conclusions
In this paper, we have studied the shape properties of the reliability polynomials of two dual networks. Mutual behaviour of these polynomials, referring to high level convexity, inflection points, and extremal properties of coefficients functions, are studied. The research from in [6,7] is developed on new bases, taking into account some requirements of shape preserving. We have proposed a technique for simultaneously approximating the reliability polynomials of two dual MMNs, choosing the input data based on their shape properties, in order to obtain results preserving some shapes. Our simulations point out that the quadratic splines approach gives much better results than other types of approximation operators if shape criteria are taken into account together with the size of the error and the complexity of computation. Some possibilities of improving the output are discussed.
Our technique uses complementary properties induced by the notion of duality, which is considered for planar two-terminal networks only. It would be of interest to extend these methods to non-planar networks, in general. Here, we refer to all-terminal, k-terminal, and two-terminal networks.
On another hand, our approach is taking into account, for the first time, some extremal properties both at the level of the original object and its approximate one. For example, identifying the maximum coefficient of the reliability polynomial has a significant meaning, as it points out the length/index where the maximum number of paths is achieved. There are no techniques, to our knowledge, for locating the maximum of the coefficients of the reliability polynomial of a network in the scientific literature. Therefore, by proposing a method for solving this problem, our article opens the road in developing approximation techniques for this matter.
Based on the significance of the shape and extremal properties in improving the results obtained by means of an approximation procedure, it is of interest to approach other approximation problems using this kind of input conditions.
Author Contributions
Conceptualization, G.C. and V.-F.D. and S.H.H.; formal analysis, G.C. and V.-F.D.; investigation, G.C. and V.-F.D. and S.H.H.; resources, G.C. and V.-F.D. and S.H.H.; writing—original draft preparation, G.C. and V.-F.D. and S.H.H.; writing—review and editing, G.C. and V.-F.D.; supervision, G.C.; funding acquisition, G.C. and V.-F.D. and S.H.H. All authors have read and agreed to the published version of the manuscript.
Funding
“V.-F. Drăgoi was supported by a grant of the Romanian Ministry of Education and Research, CNCS-UEFISCDI, project number PN-III-P4-ID-PCE-2020-2495, within PNCDI III – ThUNDER2 = Techniques for Unconventional Nano-Designing in the Energy-Reliability Realm.” “S.-H. Hoară was supported by the Polytechnic University of Timişoara, according to HCA 14/2.02.2021 (updated HCA 78/8.06.2021) regarding Creşterea calităţii cercetării ştiinţifice avansate în UPT.”
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All the data supporting our simulation results can be found within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Brown, J.I.; Colbourn, C.J.; Cox, D.; Graves, C.; Mol, L. Network reliability: Heading out on the highway. Networks 2020, 77, 146–160. [Google Scholar] [CrossRef]
- Moore, E.F.; Shannon, C.E. Reliable circuits using less reliable relays—Part I. J. Frankl. Inst. 1956, 262, 191–208. [Google Scholar] [CrossRef]
- Moore, E.F.; Shannon, C.E. Reliable circuits using less reliable relays—Part II. J. Frankl. Inst. 1956, 262, 281–297. [Google Scholar] [CrossRef]
- von Neumann, J. Probabilistic Logics and the Synthesis of Reliable Organisms from Unreliable Components. In Automata Studies; Shannon, C.E., Ed.; Princeton University Press: Princeton, NJ, USA, 1956; pp. 43–98. [Google Scholar]
- Valiant, L. The Complexity of Enumeration and Reliability Problems. SIAM J. Comput. 1979, 8, 410–421. [Google Scholar] [CrossRef]
- Cristescu, G.; Drăgoi, V.F. Cubic Spline Approximation of the Reliability Polynomials of Two Dual Hammock Networks. Transylv. J. Math. Mech. 2019, 11, 77–90. [Google Scholar]
- Cristescu, G.; Drăgoi, V.F. Efficient Approximation of Two-Terminal Networks Reliability Polynomials Using Cubic Splines. IEEE Trans. Reliab. 2021, 70, 1193–1203. [Google Scholar] [CrossRef]
- Dăuş, L.; Jianu, M. Full Hermite interpolation of the reliability of a hammock network. Appl. Anal. Discret. Math. 2020, 14, 198–220. [Google Scholar] [CrossRef] [Green Version]
- Dăuş, L.; Jianu, M. The Shape of the Reliability Polynomial of a Hammock Network. In Intelligent Methods in Computing, Communications and Control; Dzitac, I., Dzitac, S., Filip, F.G., Kacprzyk, J., Manolescu, M.J., Oros, H., Eds.; Springer International Publishing: Cham, Swizerland, 2021; pp. 93–105. [Google Scholar]
- Drăgoi, V.F.; Beiu, V. Fast reliability ranking of matchstick minimal networks. Networks 2021, 1–22. [Google Scholar] [CrossRef]
- Cowell, S.R.; Beiu, V.; Dăuş, L.; Poulin, P. On the Exact Reliability Enhancements of Small Hammock Networks. IEEE Access 2018, 6, 25411–25426. [Google Scholar] [CrossRef]
- Drăgoi, V.F.; Beiu, V. Studying the Binary Erasure Polarization Subchannels Using Network Reliability. IEEE Commun. Lett. 2020, 24, 62–66. [Google Scholar] [CrossRef]
- Drăgoi, V.F.; Cristescu, G. Bhattacharyya Parameter of Monomial Codes for the Binary Erasure Channel: From Pointwise to Average Reliability. Sensors 2021, 21, 2976. [Google Scholar] [CrossRef] [PubMed]
- Popoviciu, T. Les fonctions convexes; Actualités Scientifiques et Industrielles: Paris, France, 1945. [Google Scholar]
- Hopf, E. Ueber die zusammenhänge zwischen gewissen höheren Differenzenquotienten reeller Funktionen eines Variablen und deren differenzierbarkeitseigenschaften. Ph.D. Thesis, Friedrich-Wilhelms Universitat zu Berlin, Berlin, Germany, 1926. [Google Scholar]
- Popoviciu, T. Sur le prolongement des fonctions convexes d’ordre supérieur. Bull. Math. Soc. Roum. Des Sc. 1934, 36, 75–108. [Google Scholar]
- Popoviciu, T. Sur l’approximation des fonctions convexes d’ordre supérieur. Mathematica (Cluj) 1935, 10, 49–54. [Google Scholar]
- Huh, J. h-Vectors of matroids and logarithmic concavity. Adv. Math. 2015, 270, 49–59. [Google Scholar] [CrossRef]
- Webster, R. Convexity; Oxford University Press: Oxford, UK, 1994. [Google Scholar]
- Lenz, M. The f-vector of a representable-matroid complex is log-concave. Adv. Appl. Math. 2013, 51, 543–545. [Google Scholar] [CrossRef]
- Cowell, S.R.; Dăuş, L.; Beiu, V.; Poulin, P. On hammock networks - sixty years after. In Proceedings of the 2017 12th International Conference on Design Technology of Integrated Systems In Nanoscale Era (DTIS), Palma de Mallorca, Spain, 4–6 April 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Cristescu, G.; Lupşa, L. Non-Connected Convexities and Applications; Springer: Berlin/Heidelberg, Germany, 2002; Volume 68. [Google Scholar]
- Lorentz, G.G. Bernstein Polynomials; University of Toronto Press: Totonto, ON, Canada, 1953. [Google Scholar]
- Natanson, I.P. Constructive Function Theory: Volume I: Uniform Approximation; Frederick Ungar Publishing Company: New York, NY, USA, 1964. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).