Abstract
The traditional set stability of Boolean networks (BNs) refers to whether all the states can converge to a given state subset. Different from the existing results, the set stability investigated in this paper is whether all states in a given initial set can converge to a given destination set. This paper studies the set stability and set stabilization avoiding undesirable sets of BNs and Boolean control networks (BCNs), respectively. First, by virtue of the semi-tensor product (STP) of matrices, the dynamics of BNs avoiding a given undesirable set are established. Then, the set reachability and set stability of BNs from the initial set to destination set avoiding an undesirable set are investigated, respectively. Furthermore, the set stabilization of BCNs from the initial set to destination set avoiding a given undesirable set are investigated. Finally, a design method for finding the time optimal set stabilizer is proposed, and an example is provided to illustrate the effectiveness of the results.
1. Introduction
A Boolean network (BN) was first proposed by Kauffman, which laid the foundation for the study of gene regulation networks [1]. Since then, BNs have been widely investigated by researchers from biology, physics, and many other fields [2,3,4,5].
Two basic issues, stability and stabilization have been studied extensively [6,7,8,9], where the limit behavior of BNs is considered. For example, stable functions of BNs are studied in [6]. The stability of equilibria states and limit cycles in sparsely connected BNs is investigated by [7]. However, it is difficult to find all the limit cycles and fixed points for general BNs before the emergence of semi-tensor products (STP) of matrices.
STP is a new matrix product that overcomes the constraint of dimension in traditional matrix product [10,11]. All the limit cycles and fixed points of general BNs are revealed by using STP [12]. In addition, controllability [13,14], observability [15,16], optimal control [17], perturbation [18,19], and other properties [20,21,22,23,24,25,26] have also been investigated. It can be seen that STP is becoming an effective tool for studying BNs.
This paper investigates the set stability and set stabilization of Boolean control networks (BCNs) avoiding a given undesirable set. The motivations for investigating set stability and set stabilization come from two aspects.
(a) Practical problems: In some cases, the research interest focuses on whether a subset of state space of an interconnected subsystem converges to or can be stabilized to another subset, which is termed set stability from the initial set to destination set in this paper. A typical example of set stability is the partial synchronization of a collection of locally interconnected systems [27]. The other example is the finite-time consensus of finite field networks with a probabilistic time delay, which can be converted into the set stability from the state space to destination set [28].
(b) Hotspot of recent research: Set stability and set stabilization have been a research hotspot recently. Professor Guo [29] investigated the set stability and set stabilization of BCNs based on invariant subsets. The set stabilization of multivalued logical systems was studied in [30]. However, the existing results on set stability and set stabilization are from the full state space to a given state subset. Different from the existing results, the set stability and set stabilization problem studied in this paper are from the initial state set to the destination state set, which is the generation of traditional set stability and set stabilization.
Another concern that frequently occurs in biological systems is to prevent certain states of genes from being in an unfavorable or dangerous environment [31]. For example, in the treatment of diseases, some states of the genes or cell may cause new diseases, and they should be avoided [32]. In BCNs, such a situation is called state or input constrained. There are some works that focus on BCNs with state or input constraints. The reachability and controllability of BCNs under certain constraints were investigated in [33]. Professor Guo [34] studied the observability of BCNs with input constraints. The set controllability of logical control networks with state constraints was considered in [35]. Therefore, it is crucial to consider state constraints when studying the set stability and set stabilization of BCNs.
This paper investigates the set stability and set stabilization of BCNs with state constraints in the framework of STP. The contributions of this paper are as follows.
- (i)
- The dynamics of BNs and BCNs avoiding given undesirable set is established using STP.
- (ii)
- The set reachability and set stability of BNs and BCNs from the initial set to destination set are provided avoiding a given undesirable set, respectively. The criteria are provided with matrix forms, which are easily verified.
- (iii)
- The calculation formula of the transition period from each state of an initial set to a given destination set is given. The algorithm of a time optimal stabilizer is designed.
The organization of the rest of this paper is as follows: In Section 2, some preliminaries and symbol explanations of STP of matrices are provided. In Section 3, the definition of set stability of BNs avoiding undesirable states is first provided. Then, a discrete-time dynamic system is constructed, based on which the necessary and sufficient condition of set stability avoiding an undesirable set is obtained. In Section 4, the problem of the set stabilization of BCNs avoiding undesirable sets is discussed. In Section 5, a design method for finding the time optimal set stabilizer is proposed, and an example is provided to illustrate the effectiveness of the results. A brief conclusion is given in Section 6.
2. Preliminaries
In this section, we first list some notations:
- (1)
- is the set of all real matrices; is the set of n-dimensional real vectors.
- (2)
- is the i-th column (row) of matrix M; is the set of columns (rows) of matrix M.
- (3)
- is the i-th column of n-dimensional identity matrix .
- (4)
- .
- (5)
- , .
- (6)
- Assume , and then its shorthand form is .
- (7)
- () represents the column vector of length r whose all terms are 1(0).
- (8)
- Let , A is called a logical matrix if .
- (9)
- Denote by the set of dimension logical matrices.
- (10)
- Let , denotes the -element of matrix A.
- (11)
- is called a Boolean matrix if , and denote by the set of dimension Boolean matrices.
- (12)
- The following is the definition of Boolean addition of Boolean matrices
- (13)
- For any , , is called the Boolean product of X and Y, where .
- (14)
- If , then .
- (15)
- Let , then represents .
- (16)
- Assume that , . Then, .
- (17)
- For any , the logical sub-matrix of is defined as , if . Let denotes the set of all logical sub-matrix of , that is, . In particular, for any nonzero vector , . For convenience, define for any .
Definition 1
(Ref. [11]). The STP of two matrices and is defined as
where is the least common multiple of n and p, and ⊗ is the Kronecker product.
Remark 1.
The STP is a generalization of the ordinary matrix product, thus, we can simply call it “product” and omit the symbol “⋉” without confusion.
Proposition 1
(Ref. [11]). Let and . Then,
Definition 2
(Ref. [11]). Define a matrix as follows
where is called the swap matrix.
Proposition 2
(Ref. [11]). Let and be two column vectors. Then,
A function is called a Boolean function. To use matrix expression we identify and , then . Denote , where , we have the following proposition:
Proposition 3
(Ref. [11]). Let be a logical function. Then, there exists a unique matrix , such that
where is called the structure matrix of f.
3. Set Stability Avoiding Undesirable Set
In this section, we consider the stability of BN from the initial set to destination set avoiding undesirable set.
3.1. Algebraic Expression of Bn under Restricted State Set
A Markov-type BN with n nodes is described as [11]
where , are state variables; , are Boolean functions.
By virtue of Proposition 3, we obtain its algebraic expression as follows:
where , and is called the structure matrix of (1).
Consider BN (1) and suppose the undesirable set is
Define the initial set and the destination set as follows
For simplicity, assume
Using the initial set and destination set, we give the definition of set stability avoiding undesirable set of BN (1).
Definition 3.
Let represent the smallest integer such that (3) and (4) hold, which is called the transient period from to avoiding . The transient period of BN (1) is defined as .
In the following, we give the algebraic expression of BN (1) under restricted state set by constructing a matrix .
Define a Boolean matrix related to as follows
Denote by
According to , we know that, for the initial state , if , then state evolves to at the first step. We can construct the algebraic expression of BN (1) under restricted state set as
where is the state that belongs to .
Using Equation (6), we can obtain
where . Assume . indicates that state will evolve to within t steps. If , this indicates that the state can stay away from at the first t steps.
3.2. Reachability Avoiding States Set
Theorem 1.
Consider BN (1). The state is reachable from state at s-th step while avoiding Ω, if and only if .
Proof of Theorem 1.
Note that the state of BN (1) at time t can be expressed as . According to Definition 3, we know that BN (1) is reachable from to while avoiding at s-th step, if and only if,
It follows from the construction of that Equation (8) is equivalent to
which is further equivalent to
that is, . □
Remark 2.
On the basis of algebraic Equation (7), Theorem 1 proposes a necessary and sufficient condition to detect the reachability between two states while avoiding Ω. This is prepared for the Proof of Theorem 2.
In the following, we consider the set reachability of BN (1) avoiding undesirable set. According to (2), define matrix related to and the index vector related to as follows, respectively,
Theorem 2.
Proof of Theorem 2.
(1) According to Theorem 1, we know that BN (1) is reachable from to avoiding , if and only if there exists an integer such that , where . That is to say,
Remark 3.
By definition of matrix and the index vector , Theorem 2 gives a method to verify whether the given initial state set can reach the destination set while avoiding set Ω. It is noted that all the calculations involved are matrix operations, which are easy to validate by mathematical software.
The following corollary is obvious.
3.3. Set Stability Avoiding States Set
In the following, we consider the set stability problem of a BN avoiding using the largest invariant subset.
Definition 4
(Ref. [29]). A subset is called an invariant subset of BN (1) if, for any state , .
The union of all the invariant subsets contained in is the largest invariant subset of .
Lemma 1
(Ref. [29]). Consider a state subset of BN (1) with . Define a matrix related to as follows
Then, the largest invariant subset, denoted by , contained in is
where
Remark 4.
According to the properties of the largest invariant set , we know that, for any state , it holds that , and . Therefore, the stability from the initial set to destination set is equivalent to the reachability from the initial set to the largest invariant set .
Theorem 3.
Proof of Theorem 3.
(1) Note that is the index vector related to . According to Theorem 2, we know that BN (1) is reachable from to avoiding , if and only if, there exists an integer , such that
Combining the properties of the largest invariant set , we can find that Equation (17) holds if and only if BN (1) is stable from to avoiding .
(2) BN (1) is set stable from to avoiding , if and only if it is stable from to avoiding for any . That is, for any . The result is proven.
(3) If BN (1) is set stable from to avoiding , then, for any , we have . That is to say, there exists a smallest integer such that
Combining to the definition of transient period, it is easy to verify that
□
Remark 5.
Theorem 3 not only presents the criteria of set stability of BNs from the initial set to destination , but also gives the method to calculate the transition period of any given state from to set . In addition, the criteria are provided in vector form to facilitate verification.
Example 1.
Consider the Drosophila melanogaster segmentation polarity gene network
where represent four different secreted proteins wingless, and and represent two different transmembrane receptor proteins patched. Please refer to [32] and [26] for their specific meanings.
Suppose
and the undesirable set
By Lemma 1, we obtain
Then, the largest invariant subset of is obtained as follows
Next, according to the undesirable set , can be obtained as
By a direct calculation, we find the set stability vector avoiding set as follows
According to Theorem 3, Drosophila melanogaster segmentation polarity gene network (18) is set stable from set to avoiding set .
Finally, it is easily checked that . Thus, after one step, gene network (18) is set stable from set to avoiding set .
4. Set Stabilization Avoiding Undesirable Set
In this section, we consider the set stabilization of BCN from the initial set to destination set avoiding undesirable set .
4.1. Algebraic Expression of Bcn under Restricted State Set
Consider the following Markov-type BCN
where are state variables of node at time t, are controls of input node at time t, and are Boolean functions.
Definition 5.
4.2. Reachability Avoiding States Set
Define
and set
Lemma 2
(Ref. [33]). For BCN (19), the state is reachable from state at s-th step with proper control sequence while avoiding Ω, if and only if .
Assume and are defined as (9). From Definition 5 and Lemma 2, the following results are obtained.
Theorem 4.
Proof of Theorem 4.
(1) (Necessity): Assume (19) is reachable from to avoiding . According to Lemma 2, for the initial state , there exists an integer such that , where . This is equivalent to
According to the definition of , we have
(Sufficiency): Suppose there exists an integer , such that Equation (24) holds. Then, there is at least one state such that
which implies that
According to Lemma 2, we know that BCN (19) is reachable from to avoiding .
(2) (Necessity): Assume BCN (19) is reachable from to avoiding . That is, for any , BCN (19) is reachable from to avoiding . Then, according to (24), for each , there exists an integer such that
Taking , then we have
(Sufficiency): Suppose there exists an integer s such that
Therefore, for each , there exists an integer such that
which implies that BCN (19) is reachable from to avoiding . □
4.3. Set Stabilization Avoiding States Set
In the following, we consider the set stabilization problem of a BCN avoiding by using the largest control invariant subset.
Definition 6
(Ref. [29]). A subset is called a control invariant subset of BCN (19) if for any state , there exists a control sequence such that
Similarly, for BCN (19), the largest control invariant subset of a given set is the union of all the control invariant subsets contained in , denoted by .
Define
and set
Lemma 3
Similarly, based on (9) and (27), we can define a vector, called the set stabilization vector avoiding , as
where
Theorem 5.
Proof of Theorem 5.
(1) Note that ; thus, is the index vector of . According to Corollary 2 and the property of , we know that BCN (19) is set stabilizable from to avoiding , if and only if,
Since is a Boolean product, and , then (31) is equivalent to
(2) The conclusion of (2) can be easily obtained from (1).
(3) According to Theorem 4 and the property of , we know that BCN (19) is stabilizable from to avoiding , if and only if, there exists an integer , such that
Combined with the definition of , we obtain that, for any ,
□
Example 2.
Consider the BCN model presented in [36], which is a simplified model of the lac operon in the bacterium Escherichia coli:
where represent the lac mRNA, lactose in high concentrations, and lactose in medium concentrations, respectively. Moreover, represent the extracellular glucose, high extracellular lactose, and medium extracellular lactose, respectively, and are regarded as the control of input node.
The one-step transition matrix of (32) can be calculated as follows
Suppose
and the undesirable set is
We first calculate the largest control invariant subset of .
According to (9) and (13), we have
and
where is the 8-dimensional all-zero column vector. Using Lemma 3, we find
Furthermore,
Therefore, the largest control invariant subset of is
Next, we verify whether system (32) can be stabilized from set to set .
Since , then we can obtain the following constrained transition matrix:
By a direct calculation, the set stabilization vector is obtained as follows
according to Theorem 5, we know that system (32) is set stabilizable from the initial set to destination set avoiding .
Finally, it is easily checked that . That is to say, after two steps, BCN (32) can be stabilized from the initial set to destination set avoiding .
5. Design of Time Optimal Set Stabilizers
In this section, we consider the design of a state feedback controller with form
where , such that the closed loop system can be stabilized from to avoiding . In general, the stabilizer is not unique. This section only considers the design of the time optimal stabilizer. That is to say, under the time optimal stabilizer, the BCN (19) can be stabilized from set to set in the shortest time while avoiding .
First, we detect the time . It is easy to obtain from Theorem 5 and the definition of that if BCN (19) is set stabilizable from to avoiding , then
Therefore, we can find the shortest time by Equation (34) and denote it as .
It is easy to verify that Remark 4 is also applicable to BCNs. Thus, the stabilizer design problem from to is equivalent to the stabilizer design problem from to .
Next, we calculate the largest control invariant subset and set , where is the k-step reachable set composed of all the initial state , which can be steered to in s steps by proper control sequences.
Proof of Lemma 4.
A direct calculation shows that is equivalent to
This implies that , i.e., . Then,
In addition, since is the index vector of , then if and only if there exists at least one state , such that
According to Lemma 2, we know that is equivalent to that state is reachable from state at s-th step with proper control sequence while avoiding , that is . □
We divide the set into subsets, as follows:
It follows that the states in set can reach set only at the s-th step.
Then, denote by
where is a set, and is defined in (23). We further process as follows:
It follows that, for any state , it holds that and there must exist a state and a control sequence such that .
Finally, we give the design method of G to steer system (19) from to avoiding .
Using Proposition 2, we find the equivalent form of expression (22):
where . Then, system (19) can reach set from any state under state feedback control (33), if and only if the j-th column of G is designed as
where , , and .
If , then the j-th column of G can be designed freely.
Theorem 6.
| Algorithm 1 Algorithm for designing time optimal set stabilizers. |
It is easy to verify the correctness, so we omit its proof.
Example 3.
First, according to Lemma 4, we can find the 2-step reachable set of as follows:
Next, according to (35), we divide the set into 3 subsets as
Then, according to (36), we obtain that
Finally, we know from (37) that when , control should satisfy ,where , then we have
that is, , , , , and columns 2 and 5 of G are designed freely.
Then, a feasible stabilizer is:
where
In addition, we can see that the state transition diagram of the closed-loop network is shown in Figure 1 under the stabilizer (38), and . Then, the stabilizer (38) is the time optimal stabilizer for system (32).
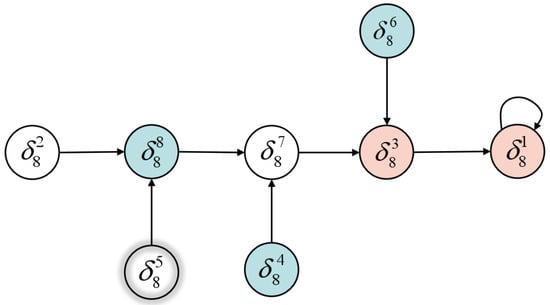
Figure 1.
The state transition diagram of Example 3.
6. Conclusions
In this paper, set stability and set stabilization avoiding undesirable set of BNs and BCNs have been investigated, respectively. Using the STP of matrices, necessary and sufficient conditions for set reachability and set stability of BNs and BCNs with constraint states have been obtained, respectively. In addition, for BNs and BCNs, the formulas for calculating the transition period from each state of initial set to a given destination set have been given, respectively. Based on the transition period, a design method of the time optimal stabilizer is proposed.
By means of matrix , the test method of reachability from one state to the others was given. Moreover, we constructed the set stability vector H (set stabilization vector ) based on constrained matrix , which can give the criteria of set stability (set stabilization) under the state constraint in vector form. It is noted that all the calculations involved are matrix operations, which are easy to validate by mathematical software. In general, all the results in this paper can be extended to mixed-valued logical (control) networks. The method proposed in this paper is helpful to the study of partial stability and partial stabilization under state constraints.
However, computational complexity is the main obstacle to study large-scale logical (control) networks using STP. In this paper, the set stability under state constraints was studied theoretically. We will consider the problem of reducing computational complexity in the future.
Author Contributions
W.L., S.F. and J.Z. obtained the set stability of BNs and set stabilization of BCNs avoiding undesirable set with the STP of matrices, and W.L. drafted the paper. All authors have read and agreed to the published version of the manuscript.
Funding
This work were supported by the Natural Science Foundation of Shandong Province ZR2019BF023 and the National Natural Science Foundation (NNSF) of China under Grants 62103176.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kauffman, S.A. Metabolic stability and epigenesis in randomly constructed genetic nets. J. Theor. Biol. 1969, 22, 437–467. [Google Scholar] [CrossRef]
- Akutsu, T.; Hayashida, M.; Ching, W.K.; Ng, M.K. Control of Boolean networks: Hardness results and algorithms for tree structured networks. J. Theor. Biol. 2007, 244, 670–679. [Google Scholar] [CrossRef] [PubMed]
- Albert, R.; Barabási, A.L. Dynamics of complex systems: Scaling laws for the period of Boolean networks. Phys. Rev. Lett. 2000, 84, 5660. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fauré, A.; Naldi, A.; Chaouiya, C.; Thieffry, D. Dynamical analysis of a generic Boolean model for the mammalian cell cycle. Bioinformatics 2006, 22, e124–e131. [Google Scholar] [CrossRef] [Green Version]
- Shmulevich, I. On the Lyapunov Exponent of Monotone Boolean Networks. Mathematics 2020, 8, 1035. [Google Scholar] [CrossRef]
- Rämö, P.; Kesseli, J.; Yli-Harja, O. Stability of functions in Boolean models of gene regulatory networks. Chaos 2005, 15, 034101. [Google Scholar] [CrossRef] [PubMed]
- Walker, C.C. Stability of equilibrial states and limit cycles in sparsely connected, structurally complex Boolean nets. Complex Syst. 1987, 1, 1063–1086. [Google Scholar]
- Watta, P.B.; Wang, K.; Shringarpure, R. Dynamical Boolean systems: Stability analysis and applications. In Proceedings of the SPIE’s 1995 Symposium on OE/Aerospace Sensing and Dual Use Photonics, SPIE 2492, Orlando, FL, USA, 17 April 1995; pp. 512–523. [Google Scholar]
- Bilke, S.; Sjunnesson, F. Stability of the Kauffman model. Phys. Rev. E 2001, 65, 016129. [Google Scholar] [CrossRef] [Green Version]
- Cheng, D.; Qi, H.; Zhao, Y. An Introduction to Semi-Tensor Product of Matrices and Its Applications; World Scientific: Singapore, 2012. [Google Scholar]
- Cheng, D.; Qi, H. Analysis and Control of Boolean Networks: A Semi-Tensor Product Approach; Springer: London, UK, 2011. [Google Scholar]
- Cheng, D.; Qi, H. A linear represeatation of dynamics of Boolean networks. IEEE Trans. Autom. Control 2010, 55, 2251–2258. [Google Scholar] [CrossRef]
- Zhu, Q.; Gao, Z.; Liu, Y.; Gui, W. Categorization problem on controllability of boolean control networks. IEEE Trans. Autom. Control 2020, 66, 2297–2303. [Google Scholar] [CrossRef]
- Jiang, B.; Liu, Y.; Kou, K.; Wang, Z. Controllability and observability of linear quaternion-valued systems. Acta Math. Sin. Engl. Ser. 2021, 36, 1299–1314. [Google Scholar] [CrossRef]
- Yu, Y.; Meng, M.; Feng, J.E. Observability of Boolean networks via matrix equations. Automatica 2020, 111, 108621. [Google Scholar] [CrossRef]
- Yang, Y.; Liu, Y.; Lou, J.; Wang, Z. Observability of switched Boolean control networks using algebraic forms. Discret. Contin. Dyn. Syst.-S 2021, 14, 1519–1533. [Google Scholar] [CrossRef]
- Wu, Y.; Guo, Y.; Toyoda, M. Policy iteration approach to the infinite horizon average optimal control of probabilistic Boolean networks. IEEE Trans. Neural Netw. Learn. Syst. 2021, 32, 2910–2924. [Google Scholar] [CrossRef]
- Li, H.; Wang, S.; Li, X.; Zhao, G. Perturbation analysis for controllability of logical control networks. SIAM J. Control Optim. 2020, 58, 3632–3657. [Google Scholar] [CrossRef]
- Wang, S.; Li, H. Graph-based function perturbation analysis for observability of multi-valued logical networks. IEEE Trans. Neural Netw. Learning Syst. 2020. [Google Scholar] [CrossRef]
- Wang, S.; Li, H. Resolution of fuzzy relational inequalities with Boolean semi-tensor product composition. Mathematics 2021, 9, 937. [Google Scholar] [CrossRef]
- Lu, J.; Li, B.; Zhong, J. A novel synthesis method for reliable feedback shift registers via Boolean networks. Sci. China Inf. Sci. 2021, 64, 152207. [Google Scholar] [CrossRef]
- Guo, Y.; Wu, Y.; Gui, W. Stability of discrete-time systems under restricted switching via logic dynamical generator and STP-based mergence of hybrid states. IEEE Trans. Autom. Control 2021. [Google Scholar] [CrossRef]
- Wu, J.; Zhong, J.; Liu, Y.; Gui, W. State Estimation of Networked Finite State Machine with Communication Delays and Losses. IEEE Trans. Circuits Syst. II Express Briefs 2021. [Google Scholar] [CrossRef]
- Liu, Z.; Zhong, J.; Liu, Y.; Gui, W. Weak Stabilization of Boolean Networks Under State-Flipped Control. IEEE Trans. Neural Netw. Learn. Syst. 2021. [Google Scholar] [CrossRef]
- Fu, S.; Zhao, J.; Wang, J. Input-output decoupling control design for switched Boolean control networks. J. Frankl. Inst. 2018, 355, 8576–8596. [Google Scholar] [CrossRef]
- Li, H.; Yang, X.; Wang, S. Robustness for stability and stabilization of Boolean networks with stochastic function perturbations. IEEE Trans. Autom. Control 2021, 66, 1231–1237. [Google Scholar] [CrossRef]
- Chen, H.; Liang, J.; Lu, J. Partial synchronization of interconnected Boolean networks. IEEE Trans. Cybern. 2017, 47, 258–266. [Google Scholar] [CrossRef] [PubMed]
- Li, Y.; Li, H.; Wang, S. Finite-time consensus of finite field networks with stochastic time delays. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 3128–3132. [Google Scholar] [CrossRef]
- Guo, Y.; Wang, P.; Gui, W.; Yang, C. Set stability and set stabilization of Boolean control networks besed on invariant subsets. Automatica 2015, 61, 106–112. [Google Scholar] [CrossRef]
- Li, F.; Li, H.; Xie, L. On stabilization and set stabilization of multivalued logical systems. Automatica 2017, 80, 41–47. [Google Scholar] [CrossRef]
- Sui, H. Gene expression profiling, genetic networks, and cellular states: An integrating concept for tumorigenesis and drug discovery. J. Mol. Med. 1999, 77, 469–480. [Google Scholar] [CrossRef]
- Xiao, Y.; Dougherty, E. The impact of function perturbations in Boolean networks. Bioinformatics 2007, 23, 1265–1273. [Google Scholar] [CrossRef] [Green Version]
- Li, Z.; Song, J. Controllability of Boolean control networks avoiding states set. Sci. China Inf. Sci. 2014, 57, 1–13. [Google Scholar] [CrossRef]
- Guo, Y.; Ding, Y. Observability of Boolean control networks with input constraints. In Proceedings of the 2017 13th IEEE International Conference on Control & Automation (ICCA), Ohrid, Macedonia, 3–6 July 2017; pp. 719–722. [Google Scholar]
- Li, Y.; Li, H.; Li, Y. Constrained set controllability of logical control networks with state constraints and its applications. Appl. Math. Comput. 2021, 405, 126259. [Google Scholar] [CrossRef]
- Montalva-Medel, M.; Ledger, T.; Ruz, G.A.; Goles, E. Lac Operon Boolean Models: Dynamical Robustness and Alternative Improvements. Mathematics 2021, 9, 600. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).