Abstract
Tao et al. proposed the definition of the linear summation of fractional-order matrices based on the theory of Yeh and Pei. This definition was further extended and applied to image encryption. In this paper, we propose a reformulation of the definitions of Yeh et al. and Tao et al. and analyze them theoretically. The results show that many weighted terms are invalid. Therefore, we use the proposed reformulation to prove that the effective weighted terms depend on the period of the matrix. This also shows that the image encryption methods based on the weighted fractional-order transform will lead to the security risk of key invalidation. Finally, our hypothesis is verified by the unified theoretical framework of multiple-parameter discrete fractional-order transforms.
1. Introduction
Fractional Fourier transform (FRFT) is widely used in quantum mechanics, optics, pattern recognition, time-frequency representation, signal processing, information security and other fields [1,2,3,4,5,6,7,8,9,10,11,12]. Therefore, discrete fractional Fourier transforms, mainly including weighted-type FRFTs [13,14], eigendecomposition-type FRFTs [15,16] and sampling-type FRFTs [17,18,19], have been proposed. In 2003, Yeh and Pei proposed a new computation method of the discrete FRFT [20]. This method is similar to Shih’s weighted FRFT [13], with the difference being that the fractional power of the discrete Fourier transform (DFT) is used in the definition of Yeh and Pei. Then, Tao et al. presented the linear summation of fractional-order matrices based on the method proposed by Yeh and Pei. Therefore, the fractional power for any diagonalizable periodic matrix is defined, which provides a new idea for information processing [21]. Recently, Kang et al. extended the definition of Tao et al., proposed a computation method for the multiple-parameter discrete FRFT, and further extended the method to multiple parameter discrete fractional cosine, sine, Hartley, and Hadamard transforms. These definitions can be applied to signal processing and image encryption [22]. In this paper, our analysis results show that there are only four effective weighted terms in the definition of Yeh and Pei, which will lead to the security risk of key invalidation when applied to image encryption. Furthermore, our results also show that the effective weighting term in the definition of Tao et al. is related to the period of the matrix. Such extension methods based on that definition are applied to image encryption, which will lead to the security risk of key invalidation.
The remainder of this paper is organized as follows. Preliminary knowledge is described in Section 2. Section 3 analyzes the definition of Yeh et al. Section 4 analyzes the definition of Tao et al. Effective weighted terms and security are discussed in Section 5. Finally, conclusions are presented in Section 6.
2. Preliminaries
Tao et al. proposed the idea of the linear summation of fractional-order matrices [21]. If a matrix satisfies , then is a periodic matrix with period P. Assume matrix is a matrix satisfying and its eigendecomposition form is . Let and . Then, can be computed as
In fact, the computation method of the discrete fractional Fourier transform (DFRFT) of Yeh and Pei [20] can be regarded as a special case of the definition of Tao et al. Consider DFRFT matrices , , ,…, , where . Denote the sum of these DFRFT matrices as
with coefficients
where . Tao et al. discussed the correlation between the signal length and the period of the matrix to present and . Because the fractional-order is a real number, there is no essential difference between the two. Moreover, Shih’s research also shows that the signal length is independent of the period of the matrix [13].
However, our analysis shows that the effective weighting term of such a definition depends on the period of the matrix. Next, we will reanalyze the definitions of Yeh et al. and Tao et al.
3. Theoretical Analysis of the Definition of Yeh et al.
Equation (3) is the sum of geometric progression, and its common ratio is . Then, Equation (3) can also be expressed as
where ; and Equation (4) can be further expressed as
where . Then, the definition (Equation (2)) of Yeh and Pei can be expressed as
Here, we let
Definition 1.
A new reformulation of the definition of Yeh and Pei as
In ref. [20], , , ,…, are the DFRFT; and the DFRFT has diversity. For Equation (7), we use the eigendecomposition type and the weighted type FRFT for verification.
3.1. Eigendecomposition Type FRFT
Proposition 1.
Eigendecomposition type FRFT is used as the basis function, there are only four effective weighting terms for the definition of Yeh and Pei.
Proof.

At present, the discrete definition [16] closest to the continuous FRFT is
where is an arbitrary orthonormal eigenvector set of the DFT. Equation (9) can be written as
where , is the kth-order DFT Hermite eigenvector, and is a diagonal matrix defined as
and
We only prove that N is odd (when N is even, the proof process is the same). In [23,24], the eigenvalues of the DFT can be expressed as . Then, the possible values of the eigenvalue are . Therefore,
Thus, Equation (7) can be written as
where and . When the eigendecomposition type FRFT is used, Equation (15) is obtained as
Therefore, we obtain Equation (16) as
From Equation (16), the diagonal matrix only contains , , , and . The multiplicities of the DFT eigenvalues are shown in Table 1. Therefore,

Table 1.
Multiplicities of the DFT eigenvalues.
When the eigenvalue is 1, can be expressed as
Therefore, we obtain
When the eigenvalue is i, can be expressed as
Therefore,
When the eigenvalue is −1, can be expressed as
Then, we can obtain
When the eigenvalue is −i, can be expressed as
Therefore,
From Equations (19), (21), (23) and (25), Equation (16) can be written as
Thus, Equation (8) is expressed as
□
Remark 1.
From Equation (27), it is not difficult to find that when,,, …,are eigendecomposition-type FRFTs, there are only four effective weighting terms defined by Yeh and Pei.
3.2. Weighted Type FRFT
Proposition 2.
Weighted type FRFT is used as the basis function, there are only four effective weighting terms for the definition of Yeh and Pei.
Proof.
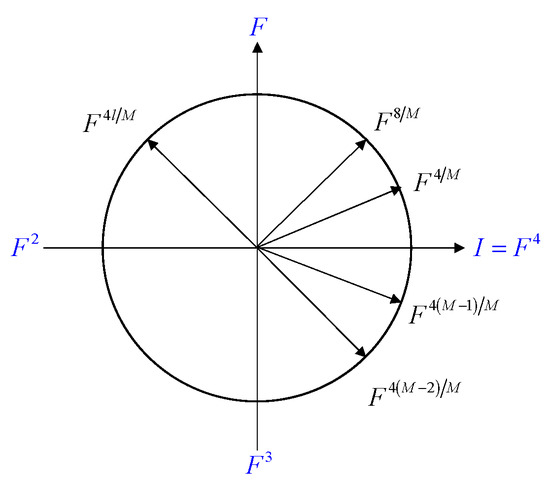
In ref. [20], , , ,…, () are the DFRFTs, which can be explained as shown in Figure 1. Therefore, the definition of Yeh and Pei is more accurate as the generalized form of Shih’s FRFT [13]. For Equation (7), we introduce the weighted fractional Fourier transform (WFRFT).

Figure 1.
Time-frequency denotation.
Shih proposed the WFRFT [13]. Shih’s WFRFT with a period of 4 is also called the 4-weighted type fractional Fourier transform (4-WFRFT), which is defined as
with
where and (F denotes the Fourier transform). Equation (29) can also be expressed as
According to the definition of the weighting coefficient [13], Equation (30) can be expressed as
where and . Here, we let
Therefore, Shih’s WFRFT can be represented as
From Equations (7) and (33), we can obtain
where and . Therefore, Equation (35) is obtained as
According to Equations (18), (20), (22) and (24), for , we can easily determine
and
Thus, Equation (35) is simplified as
Therefore, Equation (8) can be expressed as
From Equation (41), the result shows once again that there are only four effective weighted terms for the definition of Yeh and Pei.
□
Remark 2.
From Equation (41), the result shows once again that there are only four effective weighted terms for the definition of Yeh and Pei.
4. Theoretical Analysis of the Definition of Tao et al.
Tao et al. proposed the definition of the fractional power of the periodic matrix, which can be expressed as
where ( is the period of the matrix). Then,
Therefore, Equation (42) can be expressed as
Here, we let
Definition 2.
A new reformulation of the definition of Tao et al.
We know that Tao et al. define the fractional power of the periodic matrix. Next, we will analyze the DFT and the discrete Hartley transform as examples.
4.1. DFT as Periodic Matrix
Proposition 3.
DFT is used as the periodic matrix, there are only four effective weighting terms for the definition of Tao et al.
Proof.
The calculation of the fractional power of the matrix is applied to the eigenvalues, so eigenvalue decomposition of the matrix is required. Therefore, the eigendecomposition of the matrix can be expressed as
where F is the matrix of the DFT, V is the eigenvector, and D is the eigenvalue.
In refs. [23,24], the eigenvalues of the DFT can be expressed as . Then, the possible values of the eigenvalue are and . In this way, the eigenvalue matrix D can be expressed as
Then, the fractional power operation of matrix F can be expressed as
For L = F, Equation (45) can be expressed as
Therefore, we can obtain
Here, let
Then, Equation (51) can be expressed as
The multiplicities of the DFT eigenvalues are shown in Table 1. Therefore, from Equation (17), we obtain
For the sake of simplicity, Equation (52) can be expressed as
When the eigenvalues and , can be expressed using Equation (55) as
Therefore, we obtain
When the eigenvalue , , can be expressed using Equation (55) as
Therefore,
When the eigenvalue , can be expressed using Equation (55) as
Then, we can obtain
When the eigenvalue , can be expressed using Equation (55) as
Therefore,
Using Equations (57), (59), (61) and (63), we can formulate Equation (45) as
In this way, the definition of Tao et al. can be expressed as
□
Remark 3.
The DFT matrix has a period of 4, and the definition of Tao et al. has only four effective weighting terms, as shown in Equation (65).
4.2. Discrete Hartley Transform as Periodic Matrix
Proposition 4.
Discrete Hartley transform is used as the periodic matrix, there are only four effective weighting terms for the definition of Tao et al.
Proof.
We use the discrete Hartley transform as an example to verify the definition of Tao et al. The discrete Hartley transform [25] can be expressed as
The Hartley matrix has a period of 2, L = H and Equation (45) can be expressed as
where and . The fractional power of the Hartley matrix can be expressed as
where ; is the eigenvalue matrix and is the eigenvector. Therefore, Equation (67) can be expressed as
The eigenvalues of the Hartley matrix are {1, −1} [25], and the weighted sum of the diagonal matrix of Equation (69) can be expressed as
or
where . From Equation (70), we can obtain
and from Equation (71), we can obtain
Then, Equation (67) is determined as
From Equation (46), the definition of Tao et al. can be expressed as
□
Remark 4.
The Hartley matrix has a period of 2, so there are only two effective weighted terms for the definition of Tao et al. Therefore, from Equations (65) and (75), we judge that the effective weighting term defined by Tao et al. is related to the period of the matrix. InSection 5, we will prove and explain the security risk of key invalidation when this definition is applied to image encryption.
5. Discussion
5.1. Effective Weighted Terms Analysis
The definition of Tao et al. is the general form of the definition of Yeh et al. Tao et al. proposed that the fractional power of any periodic diagonalizable matrix can be expressed as Equation (42). However, our analysis in Section 4 shows that some weighting terms defined by Tao et al. are invalid, such as the weighted sum of the fractional powers of the DFT, which has only four effective weighted terms from Equation (65). We use the fractional power of the discrete Hartley transform to verify that the effective weighting terms are only two terms from Equation (75). Therefore, we judge that the effective weighting terms in the definition of Tao et al. are related to the period of the matrix.
Theorem 1.
The effective weighting terms of the Weighted fractional-order transform depend on the period of the matrix.
Assumption 1.
Thematrixis a periodic matrix satisfyingand its eigendecomposition form be.
Assumption 2.
The eigenvalues of the periodic matrixsatisfy, and these P eigenvalues can be expressed as.
Proof.
The eigenvalue can be expressed as
where Therefore, Equation (45) can be expressed as
Equation (77) can be further expressed as
where the eigenvalues . Therefore, the weighted sum of the diagonal matrix in Equation (77) can be expressed as
where with . Then, we obtain
where . For , Equation (80) can be written as
Then, Equation (77) is expressed as
□
Remark 5.
Equation (46) has only P effective weighting terms. Therefore, the effective weighting terms depend on the period of the matrix. This explains our analysis in Section 4.1 and Section 4.2. Since the DFT has a period of 4, it explains that there are only four effective weighting terms in Section 3.
5.2. Security Analysis
Kang et al. extended the definitions of Yeh et al. and Tao et al., and proposed a unified framework for multiple-parameter discrete fractional-order transforms (MPDFRT) [22]. This undoubtedly provides ideas for the further application of the weighted fractional-order transform based on the periodic matrix, especially for the security of image encryption [26]. However, with the help of our research in Section 5.1, the results indicate that the theoretical framework of Kang et al. cannot provide better security.
Therefore, we refer to the theoretical framework of II MPDFRT, and assume that L is a periodic matrix satisfying and the type II MPDFRT operator is defined as
where . In Equation (83), the vector parameter ; if , then Equation (42) is obtained. It is not difficult to find that the definition of Kang et al. is an extended form of the definition of Tao et al., and its weighted term can be expressed as
where . Equation (84) can be further expressed as
where . Thus, Equation (83) can be expressed as
From Equation (45), we can obtain
where .
Definition 3.
A new reformulation of the definition of Kang et al.
whereis the same as Equation (82). Thus, Equation (88) has only P effective weighting terms. Because, Equation (88) can be further expressed as
where.
The theoretical framework of II MPDFRT is proposed in [22]; these transforms include multiple-parameter discrete fractional-order Fourier transforms (MPDFRFT), multiple-parameter discrete fractional-order cosine transforms (MPDFRCT), multiple-parameter discrete fractional-order sine transforms (MPDFRST), multiple-parameter discrete fractional-order Hartley transforms (MPDFRHT), and multiple-parameter discrete fractional-order Hadamard transforms (MPDFRHaT). In our study, these definitions can be easily defined by Equation (89).
- (a)
- MPDFRFT
The MPDFRFT is proposed in Ref. [22]. According to our reformulation process, the MPDFRFT can be redefined. Here, ( denotes the Fourier matrix, and ), and period , we let
Therefore, the MPDFRFT is redefined as
For Equation (87), when L = F, is obtained.
- (b)
- MPDFRCT
The MPDFRCT is proposed in ref. [22]. Ref. [27] presents four types of discrete cosine transform (DCT) kernel matrices, where the DCT-I () kernel is a symmetric-structured periodic matrix with period 2. Here , and and are defined as
we let
Then, the MPDFRCT is redefined:
For Equation (87), when , is obtained.
- (c)
- MPDFRST
Like the DCT, the discrete sine transform (DST) has four definitions [27]. The DST-I () kernel is a symmetric-structured periodic matrix with period 2. Therefore, with period 2. is the same as Equation (93), so the MPDFRST is redefined as
For Equation (87), when , is obtained.
- (d)
- MPDFRHT
MPDFRHT is defined in ref. [22], where the discrete Hartley transform (DHT) [25] is
Here, with period 2. Here, is the same as Equation (93), and the MPDFRHT is redefined as
For Equation (87), when , is obtained.
- (e)
- MPDFRHaT
A Hadamard matrix is a symmetric matrix whose elements are the real numbers 1 and −1. The rows (and columns) of a Hadamard matrix are mutually orthogonal [28]. The normalized Hadamard matrices of order , denoted by , can be defined recursively:
We make with period 2, and is the same as Equation (93), therefore the MPDFRHaT is redefined:
For Equation (87), when , is obtained.
Remark 6.
The transforms a–e involved here are proposed in [22]. However, definitions a–e are easy to present with the help of our reformulation. In our new reformulation, the effective weighting terms depend on the period of the matrix. For example, the base matrix L = F of MPDFRFT with period 4, so there are only four effective weighting terms. The parameter is the main key of the system. From Equation (91), it is not difficult to find that the valid keys are only . Furthermore, when , is also invalid, and only are valid. MPDFRCT, MPDFRST, MPDFRHT and MPDFRHaT have the base matrix with period 2, which has only two effective weighting terms. It is not difficult to find that the valid keys are only . Furthermore, when , is also invalid, and only are valid.
Therefore, we take MPDFRHaT as an example for numerical verification analysis, and the code is shown in the Appendix A. M is a positive integer greater than or equal to 4. For example, if M = 6, there are 6 weighting terms and the vector parameters . The size of the image is selected as 256 × 256, so N = 256.
The image encryption/decryption based on MPDFRHaT is shown in Figure 2, and Figure 2a is the original image (plaintext). We set the encryption keys as:
the encrypted image (ciphertext) is shown in Figure 2b, and the plaintext is encrypted into a noise image. Therefore, the decryption keys are
the decrypted image is shown in Figure 2c. The image is restored losslessly, because decryption process is equivalent to the inverse transformation of MPDFRHaT. To verify the validity of the keys, the wrong decryption keys are selected,
where the keys , , , and are wrong. The decrypted result is shown in Figure 2d, and the original image is well restored. This verifies our above analysis results. Because the weighted terms with the keys (, , , and ) are invalid, these keys are also invalid. This shows that the keys (, , , and ) have no effect on the encryption/decryption process, regardless of the value. The wrong decryption key is selected again,
where the key is wrong. The decryption result is shown in Figure 2e, and no information about the original image is obtained. This indicates that the key is valid.
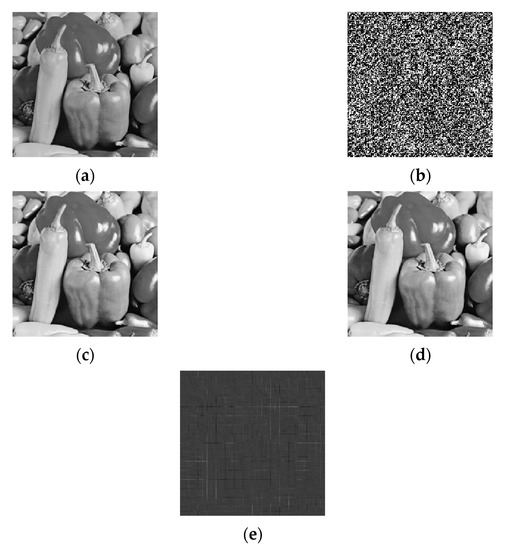
Figure 2.
Encryption/decryption based on the MPDFRHaT: (a) plaintext, (b) ciphertext, (c) decrypted image with the correct keys, (d) decrypted image with the wrong keys (, , , and ), (e) decrypted image with the wrong key .
A numerical simulation also verified that many keys are invalid for the image encryption based on MPDFRHaT, which again supports our hypothesis. This security risk comes from the periodicity of the basis matrix. Strictly speaking, the period of the matrix determines the number of weighted terms of the weighted fractional-order transform. This discovery provides an important reference for future research.
6. Conclusions
In this paper, we propose a reformulation of the definition of Yeh et al., and the eigendecomposition type FRFT and the weighted type FRFT are verified. The results show that there are only four effective weighting terms. Furthermore, we determine that the definition of Tao et al. is an extended definition for that of Yeh et al., and propose a reformulation of the former. The fractional power of the DFT and the fractional power of the discrete Hartley transform are verified, and the results show that the effective weighting terms are defined as four terms and two terms, respectively. We perform a further analysis, and the results show that the effective weighting terms depend on the period of the matrix, which will lead to the security risk of key invalidation. Therefore, we propose a reformulation of the unified framework for MPDFRT, and determine that many keys are invalid for image encryption. Finally, we take MPDFRHaT as an example to verify that there is only one valid key, with other keys being invalid. Our observations prove once again that the effective weighting terms of the weighted fractional-order transform based on the periodic matrix depend on the period of the matrix, which will lead to the security risk of key invalidation for image encryption.
Author Contributions
Methodology, T.Z.; software, T.Z.; validation, T.Z. and Y.C.; writing—original draft preparation, Y.C.; writing—review and editing, T.Z.; supervision, T.Z.; funding acquisition, T.Z. Both authors have read and agreed to the published version of the manuscript.
Funding
This study was supported by the Fundamental Research Funds for the Central Universities (N2123016); and the Scientific Research Projects of Hebei colleges and universities (QN2020511).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
On behalf of my co-authors, we would like to express our great appreciation to editor and reviewers.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
| MPDFRHaT_code |
| function F = FHa(alpha,M,N) |
| % This code is written by Tieyu Zhao, E-mail: zhaotieyu@neuq.edu.cn; |
| % alpha is the transform order; |
| % M is the resulting weighting term; |
| % N is the length of the signal; |
| Ha = hadamard(N)/(sqrt(N)); |
| %This function handles only the cases where n,n/12,or n/20 is a power |
| % of 2. |
| for k = 0:M − 1 |
| yy = Ha^(2*k/M); |
| y{k + 1} = yy; |
| end |
| % celldisp(y); |
| u = zeros(M); |
| for k = 1:M |
| for h = 1:M |
| u(h,k) = exp(2*pi*i*(h − 1)*(k − 1)/M); % IDFT |
| end |
| end |
| for k = 1:M |
| YY = zeros(N); |
| for h = 1:M |
| YY = YY + u(h,k)*y{h}; |
| end |
| G{k} = YY; |
| end |
| % celldisp(G) |
| X = zeros(1,M); |
| for k = 0:M − 1 |
| X(k + 1) = X(k + 1) + exp(-pi*i*k*alpha(k + 1)); |
| end |
| F = zeros(N); |
| for k = 0:M − 1 |
| F = F + X(k + 1)*G{k + 1}/M; % MPDFRHaT |
| end |
References
- Almeida, L.B. The fractional Fourier transform and time-frequency representations. IEEE Trans. Signal Process. 1994, 42, 3084–3091. [Google Scholar] [CrossRef]
- Namias, V. The fractional order Fourier transform and its application to quantum mechanics. IMA J. Appl. Math. 1980, 25, 241–265. [Google Scholar] [CrossRef]
- Ozaktas, H.M.; Kutay, M.A. The Fractional Fourier Transform; Wiley: Chichester, UK, 2001. [Google Scholar]
- Mendlovic, D.; Ozaktas, H.M. Fractional Fourier transforms and their optical implementation: I. JOSA A 1993, 10, 1875–1881. [Google Scholar] [CrossRef] [Green Version]
- Ozaktas, H.M.; Mendlovic, D. Fractional Fourier transforms and their optical implementation: II. JOSA A 1993, 10, 2522–2531. [Google Scholar] [CrossRef] [Green Version]
- Bernardo, L.M.; Soares, O.D. Fractional Fourier transforms and optical systems. Opt. Commun. 1994, 110, 517–522. [Google Scholar] [CrossRef]
- Ozaktas, H.M.; Kutay, M.A.; Mendlovic, D. Introduction to the fractional Fourier transform and its applications. Adv. Imaging Electron. Phys. 1999, 106, 239–291. [Google Scholar]
- Ozaktas, H.M.; Barshan, B.; Mendlovic, D.; Onural, L. Convolution, filtering, and multiplexing in fractional Fourier domains and their relation to chirp and wavelet transforms. JOSA A 1994, 11, 547–559. [Google Scholar] [CrossRef] [Green Version]
- Kutay, M.A.; Ozaktas, H.M.; Arikan, O.; Onural, L. Optimal filtering in fractional Fourier domains. IEEE Trans. Signal Process. 1997, 45, 1129–1143. [Google Scholar] [CrossRef] [Green Version]
- Erden, M.F.; Kutay, M.A.; Ozaktas, H.M. Applications of the fractional Fourier transform to filtering, estimation and restoration. In Proceedings of the IEEE-EURASIP Workshop on Nonlinear Signal and Image Processing (NSIP’99), Antalya, Turkey, 20–23 June 1999; pp. 481–485. [Google Scholar]
- Unnikrishnan, G.; Joseph, J.; Singh, K. Optical encryption by double-random phase encoding in the fractional Fourier domain. Opt. Lett. 2000, 25, 887–889. [Google Scholar] [CrossRef]
- Lohmann, A.W. Image rotation, Wigner rotation, and the fractional Fourier transform. JOSA A 1993, 10, 2181–2186. [Google Scholar] [CrossRef]
- Shih, C.C. Fractionalization of Fourier-Transform. Opt. Commun. 1995, 118, 495–498. [Google Scholar] [CrossRef]
- Santhanam, B.; McClellan, J.H. The discrete rotational Fourier transform. IEEE Trans. Signal Process. 1996, 44, 994–998. [Google Scholar] [CrossRef]
- Pei, S.C.; Yeh, M.H.; Tseng, C.C. Discrete fractional Fourier transform based on orthogonal projections. IEEE Trans. Signal Process. 1999, 47, 1335–1348. [Google Scholar]
- Candan, C.; Kutay, M.A.; Ozaktas, H.M. The discrete fractional Fourier transform. IEEE Trans. Signal Process. 2000, 48, 1329–1337. [Google Scholar] [CrossRef] [Green Version]
- Ozaktas, H.M.; Ankan, O.; Kutay, M.A.; Bozdagi, G. Digital computation of the fractional Fourier transform. IEEE Trans. Signal Process. 1996, 44, 2141–2150. [Google Scholar] [CrossRef] [Green Version]
- Erseghe, T.; Kraniauskas, P.; Cariolaro, G. Unified fractional Fourier transform and sampling theorem. IEEE Trans. Signal Process. 1999, 47, 3419–3423. [Google Scholar] [CrossRef]
- Kraniauskas, P.; Cariolaro, G.; Erseghe, T. Method for defining a class of fractional operations. IEEE Trans. Signal Process. 1998, 46, 2804–2807. [Google Scholar] [CrossRef]
- Yeh, M.-H.; Pei, S.-C. A method for the discrete fractional Fourier transform computation. IEEE Trans. Signal Process. 2003, 51, 889–891. [Google Scholar]
- Tao, R.; Zhang, F.; Wang, Y. Linear Summation of Fractional-Order Matrices. IEEE Trans. Signal Process. 2010, 58, 3912–3916. [Google Scholar] [CrossRef]
- Kang, X.J.; Tao, R.; Zhang, F. Multiple-Parameter Discrete Fractional Transform and its Applications. IEEE Trans. Signal Process. 2016, 64, 3402–3417. [Google Scholar] [CrossRef]
- McClellan, J.; Parks, T. Eigenvalue and eigenvector decomposition of the discrete Fourier transform. IEEE Trans. Audio Electroacoustics. 1972, 20, 66–74. [Google Scholar] [CrossRef]
- Dickinson, B.; Steiglitz, K. Eigenvectors and functions of the discrete Fourier transform. IEEE Trans. Acoust. Speech Signal Process. 1982, 30, 25–31. [Google Scholar] [CrossRef]
- Pei, S.C.; Tseng, C.C.; Yeh, M.H.; Shyu, J.J. Discrete fractional Hartley and Fourier transforms. IEEE Trans. Circuits Syst. II Analog. Digit. Signal Process. 1998, 45, 665–675. [Google Scholar]
- Zhao, T.; Yuan, L.; Chi, Y. Image encryption using linear weighted fractional-order transform. J. Vis. Commun. Image Represent. 2021, 77, 103098. [Google Scholar] [CrossRef]
- Pei, S.C.; Yeh, M.H. The discrete fractional cosine and sine transforms. IEEE Trans. Signal Process. 2001, 49, 1198–1207. [Google Scholar]
- Pei, S.C.; Yeh, M.H. Discrete fractional Hadamard transform. In Proceedings of the 1999 IEEE International Symposium on Circuits and Systems (ISCAS’99), Orlando, FL, USA, 30 May–2 June 1999; Volume 3, pp. 179–182. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).