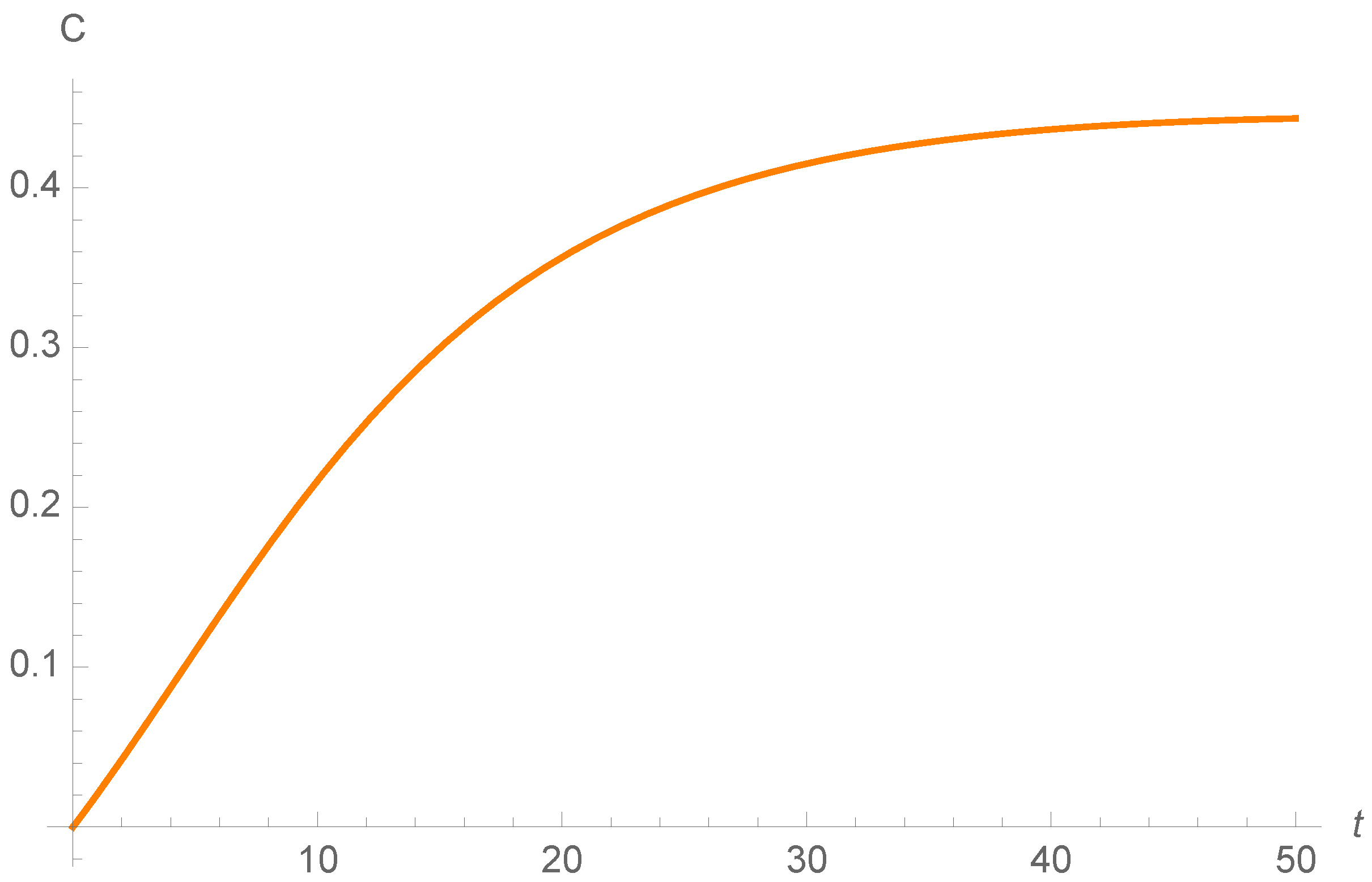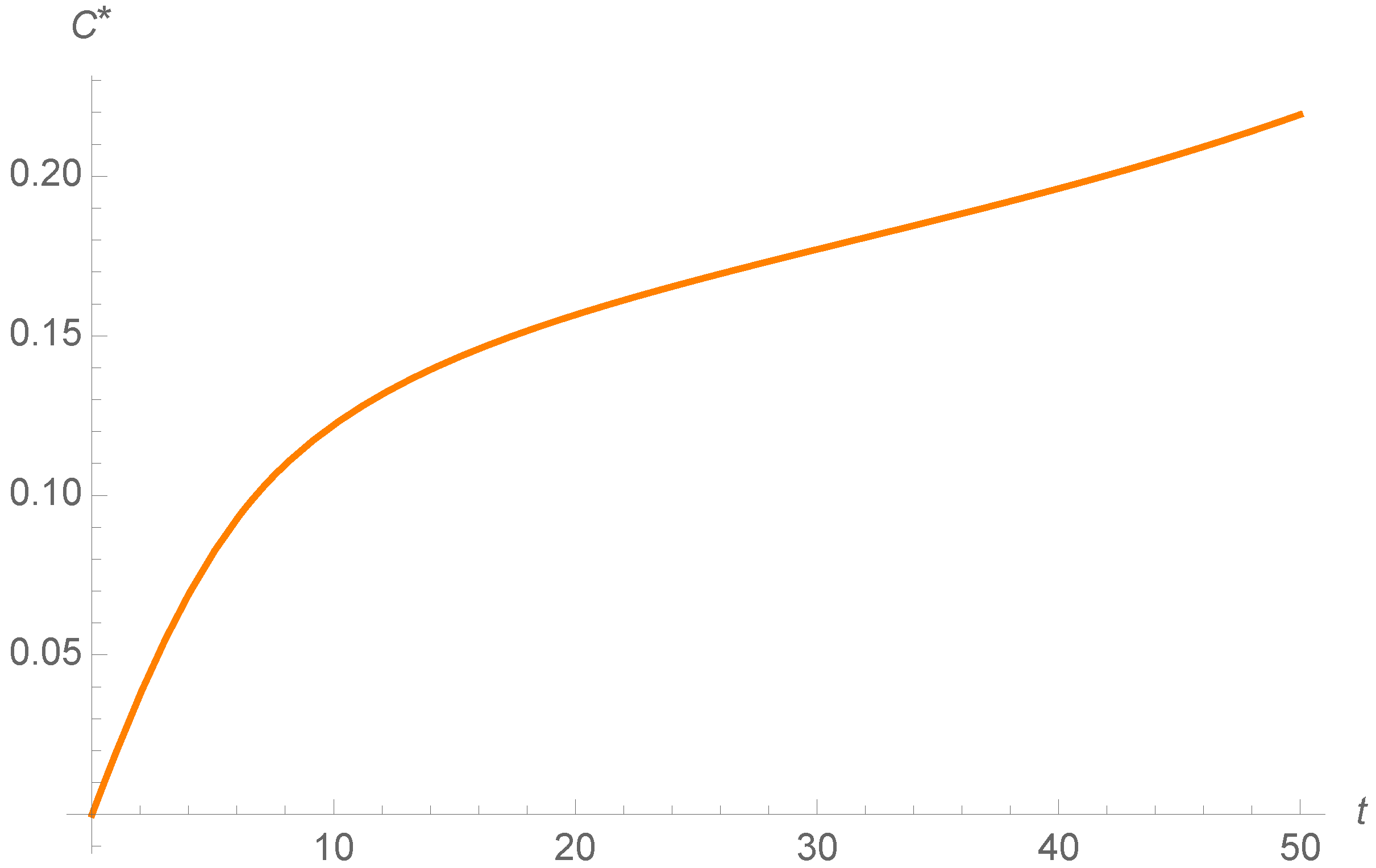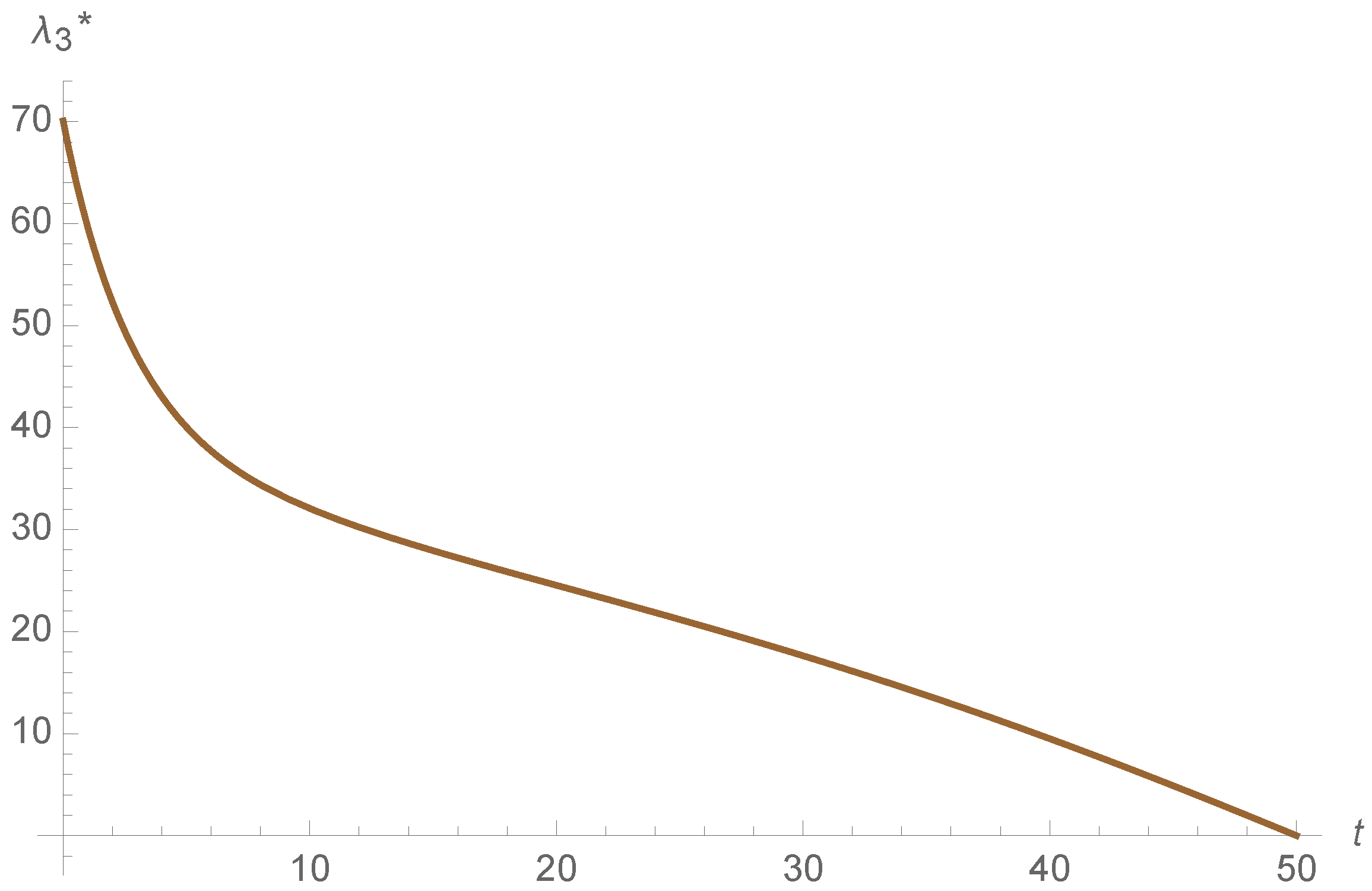1. Introduction
Nowadays, malware is one of the most important threats to security of information. The study and analysis of mathematical models to simulate malware propagation is an important task. In this sense, several mathematical models to study malware propagation have appeared in the scientific literature (see, for example, [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11]). These are compartmental models that, in most cases, are based in differential ordinary equations (as a consequence, they are deterministic and global models). Usually, each model exhibits two equilibrium points: a disease free-equilibrium point and an epidemic equilibrium point. The qualitative study of the systems shows that the basic reproductive number
plays a fundamental role in the analysis of the convergence of the system to one of these equilibrium points. Therefore, by analyzing the
, one could consider control measures at the beginning of the malware epidemic outbreak in order to determinate the evolution of the solutions and the final equilibrium reached. On the other hand, using control theory, we can find a suitable function to control the epidemic process. This function is part of the system and we can observe its influence through time (that is, we are able to control the epidemic during the time
t).
The theory of the optimal control is a classical theory [
12,
13] that has several applications in Economy, Epidemiology, etc. [
14]. This theory allows for one to obtain the solutions of a system of ordinary differential equations under some conditions by finding the minimum cost of some parameters and variables that are controlled. Therefore less control measures can be used considering this method. This problem is tackled by means of the maximum Pontryagin Principle. In this principle, several hypothesis and formulations are introduced with the aim to calculate a function to simulate these control measures. Moreover, it is possible to define the equations of the new control model taking this optimal function into account.
This approach is also used when malware propagation models are studied. Usually, compartmental models are proposed and analyzed; that is, the devices are classified into different compartments depending on their status with respect to malware -susceptible
S, infectious
I, exposed
E, recovered
R, etc. The dynamics between different compartments are ruled by means of epidemiological coefficients and, in this sense, several types of models can be proposed while taking into account the evolution of such compartments: SIR (Susceptible-Infectious-Recovered), etc. For example, in [
15], a vaccination strategy to determine the optimal control is presented. In [
8], two types of compartments are considered to construct the functional objective: the latent devices and breaking out devices. In [
5] an analysis in order to minimize the infectious and dead devices through a optimal control is introduced. In [
9], it is used the infectious devices and a delitescent strategy to remove the malware. In [
1,
4,
6,
7,
10,
13], the optimal control is calculated based on a
model. In [
11], the theory of control is used in a
model. In [
3], it is presented the optimal control of a
model. In [
2], it is studied a control strategy of a
model.
Furthermore, there exists several malware environments where this theory is used: in [
1], this theory is used to simulate malware in mobile ad hoc networks. In [
2,
5,
6], it is used to simulate malware propagation in wireless sensor networks. In [
3], it is presented a model taking into account an alert system. In [
8], it is considered scale-free networks. In [
10], it presented a information network to simulate malware.
In [
16], a compartmental
model for malware propagation was proposed and analyzed from a qualitative perspective. Furthermore, some control measures based in the analysis of the basic reproductive number were proposed. In this article, we focus on the use of control measures that are developed over the time
t. We use the theory of optimal control to do this work in this article. This control measure is different in this occasion due to it affects the system over all time
t. This permits to have a new control tool to combat malware epidemics and improve the security of computers.
In
Section 2, the model compartmental model is reviewed. In
Section 3, the basis of the control functions is shown. The optimization problem and its analysis are presented in
Section 4.
Section 5 is devoted to illustrate the theory with some simulations. Finally,
Section 6 presents the conclusions.
3. Strategy of Control
The methods employed to apply the control theory are similar in several papers. The main difference is based on the definition of the functional objective that uses the control strategy to eliminate the malware. We can distinguish two types of expressions: the compartments and parameters we can control. In this work, we have considered the infectious devices in the functional objective, since we want to maintain the number of devices as low as possible. Some works have also considered the infectious devices in this function (see, for example, [
9,
15]). However, other deal with more than one type of compartment to define this function (see, for example, [
3,
8,
11]). Moreover we will consider two independent strategies of control, recovery strategy and vaccination strategy, to make a comparison between these. Other works take into account the vaccination strategy [
15] or several parameters together [
3,
8,
11], where the recovery coefficient is also used among others. These parameters are part of this function, since our purpose is to take the smallest number of measures against the epidemic to remove it.
In this new problem, we can find a new objective that is different to the control measure based on considering the basic reproductive number under a numerical threshold that usually is
, which depends on taking measures of prevention and control. This objective is used to control the evolution of the system in each step of the time by the control variables. Subsequently, we can consider an objective in each instant of time
t. We use the Lagrangian function
L to define that objective:
These functions determinate the best form of obtained the final objective. Moreover, we define an intertemporal objective by the integral of
L in the interval
, obtaining the functional objective
. Therefore,
represents the cost of taking control measures through time. The minimization of the functional
J is used to optimize the problem and it is denoted by
V:
The objective is to optimize the control measures and, in this sense, we can consider the equations of movement as a restriction. This restriction shows the influence of the state variables and supposes a price to our problem. The Hamiltonian represents this idea:
where
and
. In this way,
is denoted as the multipliers vector, and this marks the price of the restriction of the movements equations.
In our case, we consider two strategies to remove the malware:
In both cases, the Lagrangian function has the same form:
The associated functional objective
is interpreted, as follows (see [
15]):
Moreover, we can consider the following Hamiltonian in each strategy:
where , , , , , and are the adjoins functions.
4. Optimization Problem
In this section we introduce the optimization problem which considers the following conditions:
Some border conditions: and N.
A restriction: with .
A function to optimize: V.
A solution of this problem has an optimal control
and an optimum trajectory
. When we find the optimal control, there exists an unique optimum trajectory. The existence of such solution is given by the following result:
Theorem 2. A solution of the problem exists if the following statements hold:
- 1.
The set of controls and their state variables exist.
- 2.
The admissible control set is closed and convex.
- 3.
Every right hand side of the ordinary differential equations is continuous and bounded above by a sum of the bounded control and state. Moreover, this has to be written as a linear function of u with time and state coefficients.
- 4.
The Lagrangian function is concave.
- 5.
There exists a constant and two positive numbers y , such that:
Proof. It’s easy to check that a set of controls and state variables exists. Moreover, the solutions are bounded, which implies that the admissible control set is closed and convex. Assume
, where:
Subsequently, if we consider
and
, the following is satisfied:
where
is a constant. Thus:
where
. This is satisfied in both strategies,
and
.
If we consider the constant
and the functions
, we have:
As a consequence, the Lagrangian is concave. Furthermore, the following holds:
considering
and
and
small enough. Thus, a solution of our problem exists. □
Taking into account the maximum Pontryagin Principle (see [
12]), we have a solution of the system with some conditions. These solutions verify the following:
where
- (1)
- (2)
Moreover, if we consider the minimum condition of the Pontryagin Maximum Principle, we have:
Subsequently,
We can reformulate this, as follows:
Afterwards, we obtain the following optimal systems:
5. Representations of the Models
In this section, we analyze some simulations with our control measures, when considering the derivatives of the adjoin functions and the movement equations as an unique system ordinary differential equations with the optimal control. Moreover, the following numerical values of the parameters are considered:
,
,
,
,
,
,
,
,
,
,
,
and
. The solutions of the system are shown in
Figure 2,
Figure 3,
Figure 4,
Figure 5,
Figure 6,
Figure 7,
Figure 8,
Figure 9 and
Figure 10. The simulations have been obtained using the computer algebra system Mathematica and, specifically, the function NDSolve used to solve in a numerical way the systems of ordinary differential equations.
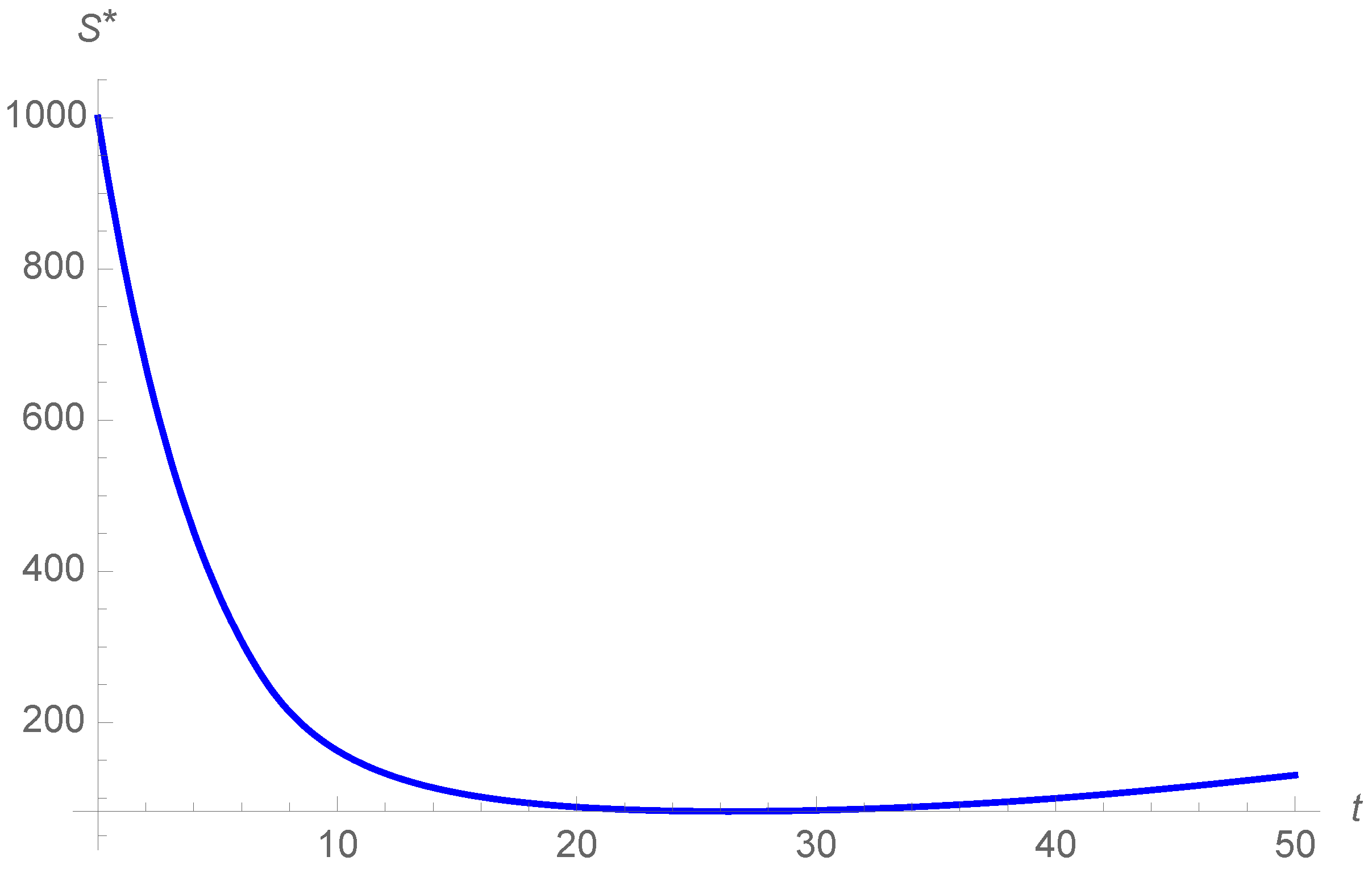
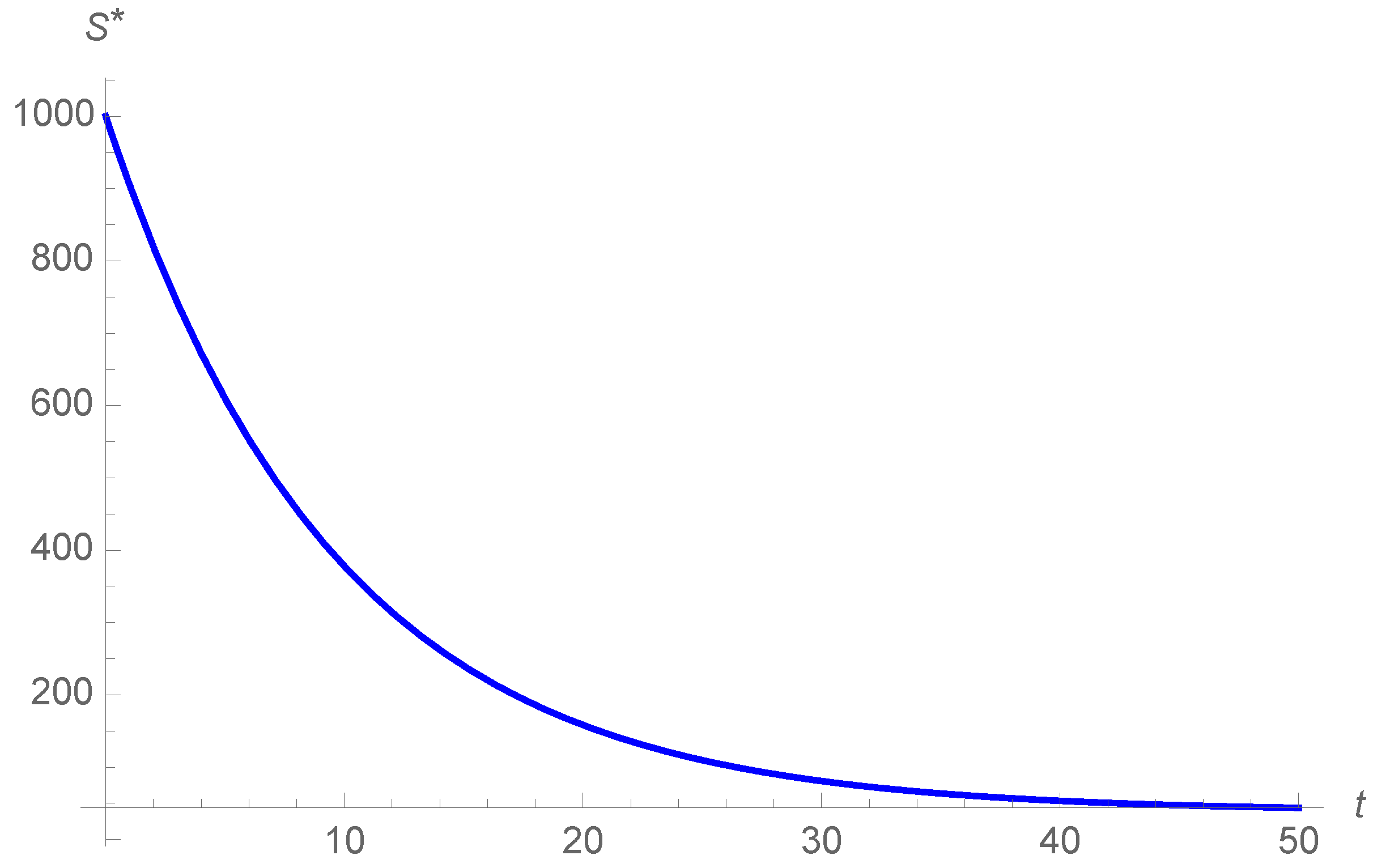
In
Figure 2,
Figure 3 and
Figure 4, we can observe the evolution of the susceptible devices. The number of susceptible devices
S decreases through time with the exception of the vaccination strategy, where the susceptible devices increase in the end. The evolution of
S when considering optimal control strategies is very similar to those without control strategies.
Figure 5,
Figure 6 and
Figure 7 show the evolution of carrier devices. When recovery strategies are considered, the graphic first increases and then decreases. However, in the case of considering vaccination strategies and no optimal control measures, the carrier devices increase a bit less than
.
Finally, in
Figure 8,
Figure 9 and
Figure 10, the evolution of infectious devices is shown. In both cases, with vaccination strategy and without control measures, the infectious devices increase first and then decrease. Nevertheless the infectious devices only decrease with recovery strategy. The increase is fewer than three devices. Therefore both strategies are efficient to remove the malware.
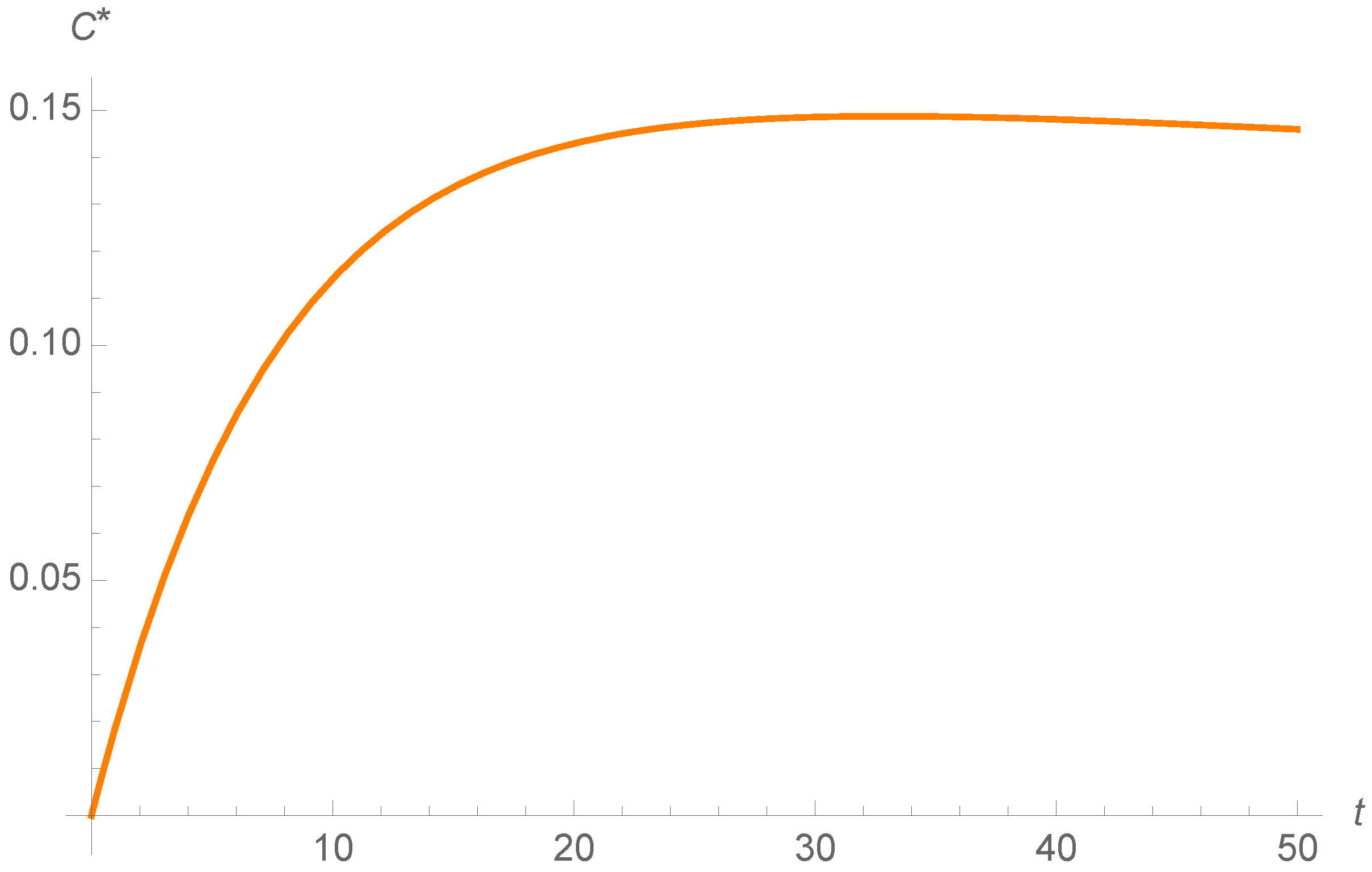
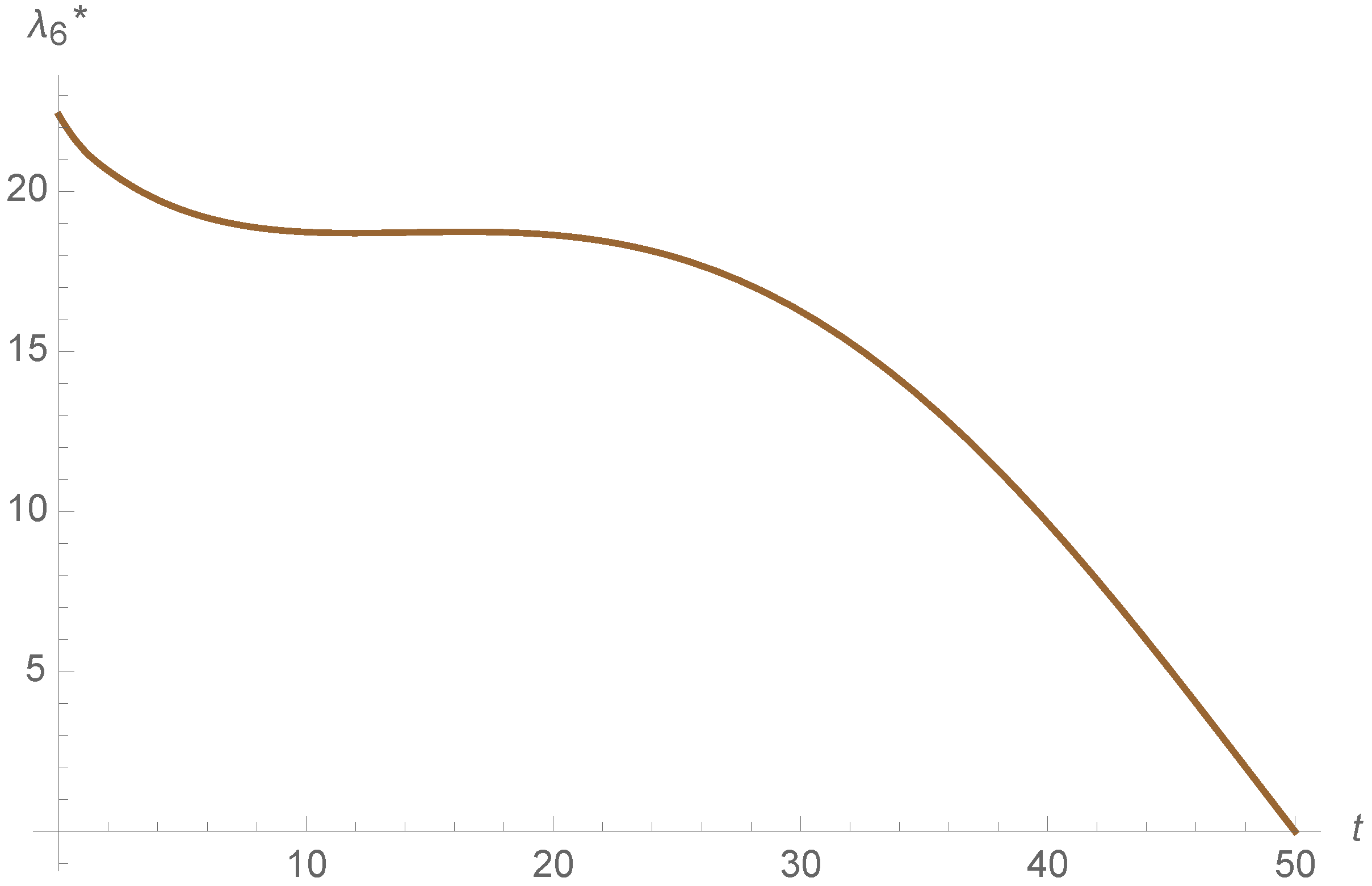
On the other hand, the evolution of the optimal control is illustrated in
Figure 11 and
Figure 12. We can observe how the function is constant and then it decreases considering both control strategies. This permits consider less recovery and vaccination rates through time and eliminate the epidemic. Therefore, the measures to control the epidemic are high at the beginning and we can then consider lower measures. This can help to save control measures to eliminate the epidemic without consider the same value during all the epidemic for
or
v, like taking into account prevention measures.
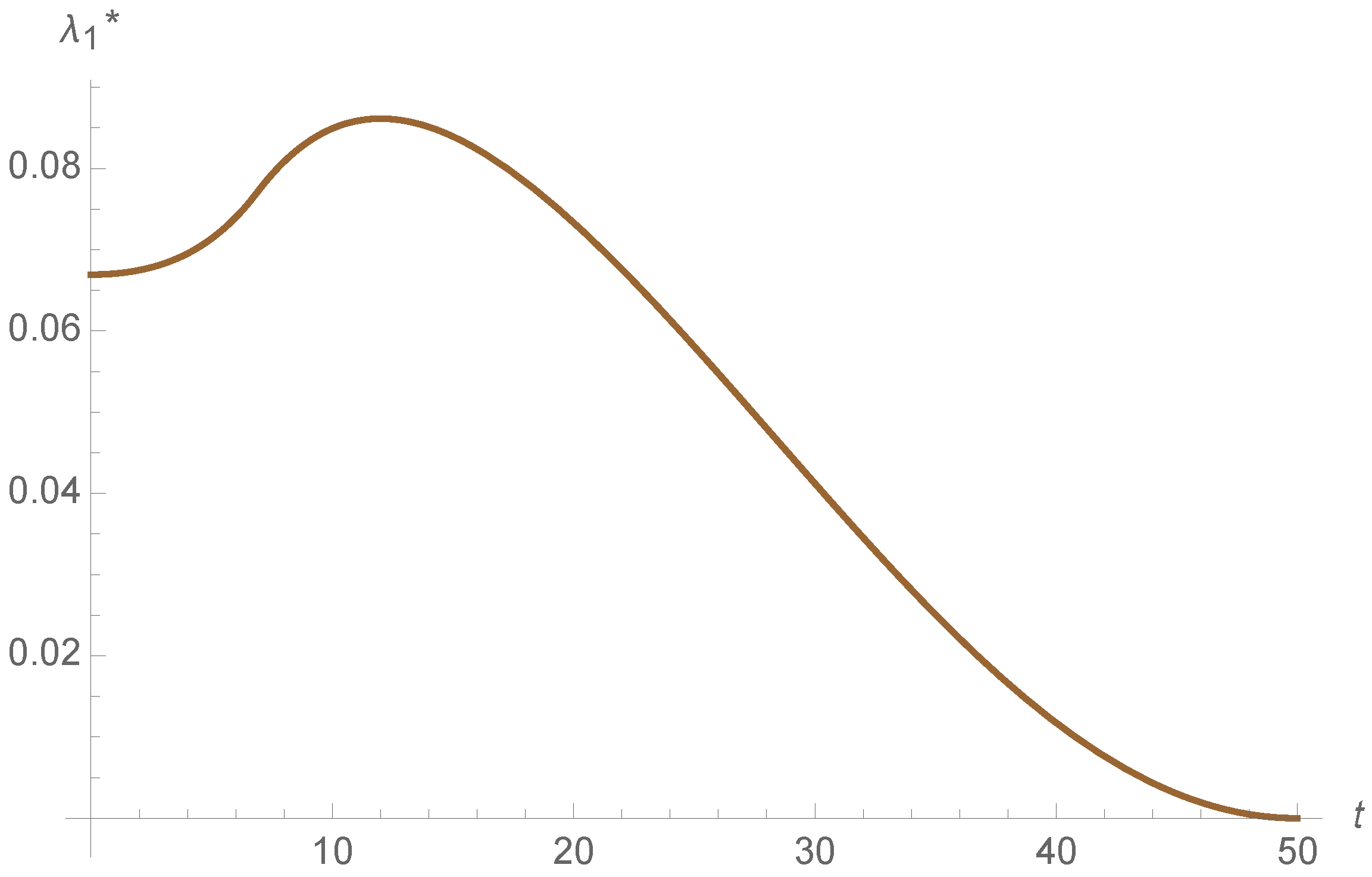
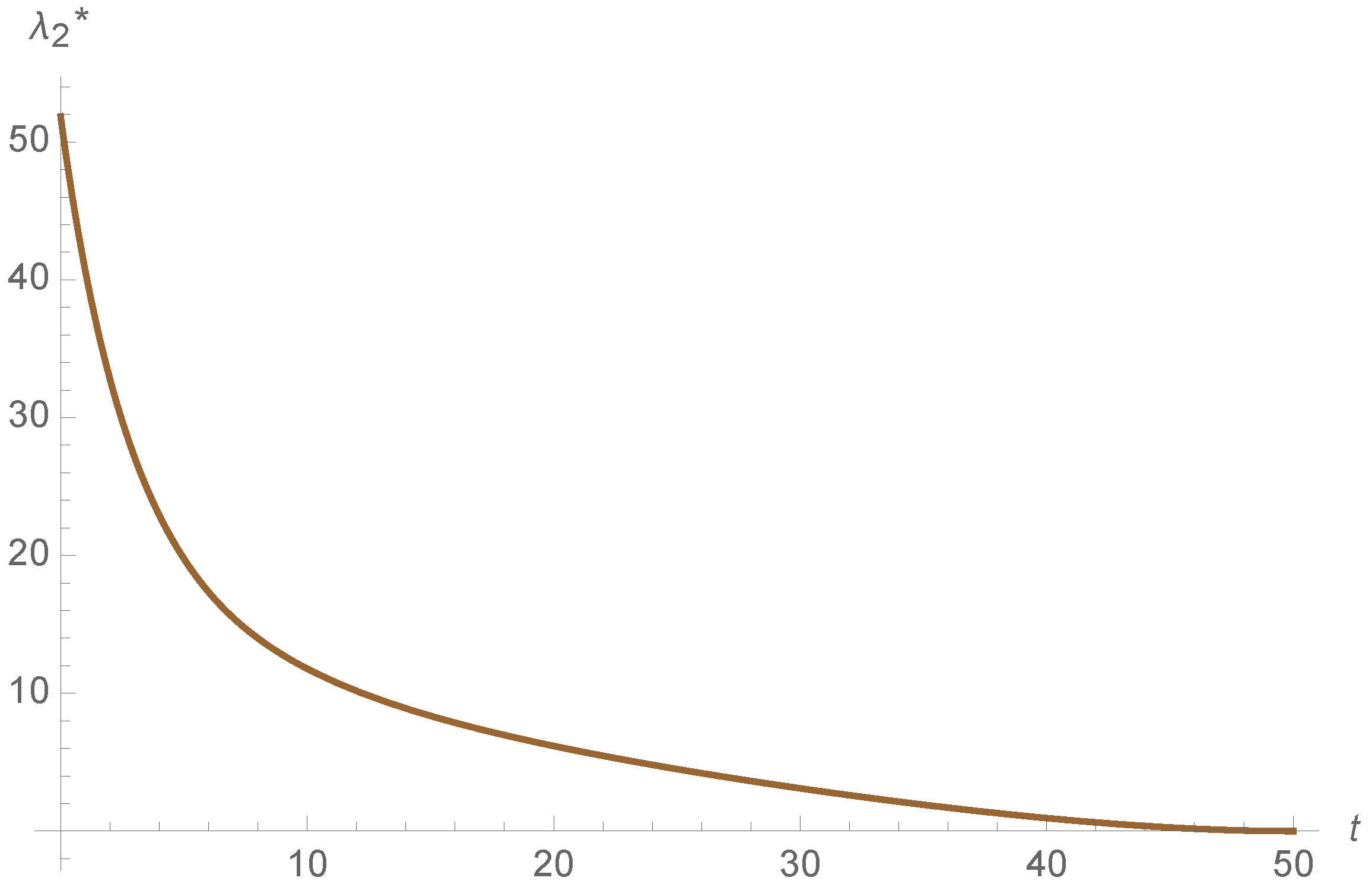
To sum up, both of the strategies are efficient in this example. However, the propagation of the adjoins functions is different in both models, as it is shown in
Figure 13,
Figure 14,
Figure 15,
Figure 16,
Figure 17 and
Figure 18. This indicates that the cost of the state variables is different in both control strategies. Moreover the adjoin functions satisfy the final condition
for all
, as illustrated in
Figure 13,
Figure 14,
Figure 15,
Figure 16,
Figure 17 and
Figure 18.
6. Conclusions
In this work, a control analysis of a model (that considers carrier devices) to simulate malware spreading is done. This permits to control the measures of recovery and vaccination; that is, we have obtained a control function that help us to decrease the number of infectious with the minimum control measures of recovery and vaccination strategies.
Note that, in this model, all of the epidemiological parameters are constant during the whole evolution. However, during the epidemic, we can apply different measures to modify some of them, while considering the control of some of this parameters. Therefore, we do not need to maintain high prevention measures in order to eliminate the malware outbreak, but we might only apply high levels at the beginning of the epidemic process. However, this kind of models are not autonomous and are more difficult to trait.
Taking into account the simulations, we can observe the behavior of the evolution of the system and the control function. Additionally, we have obtained very similar control measures with both strategies (vaccination strategy and recovery strategy). Therefore, both strategies seem to be efficient.