Secret Image Sharing with Dealer-Participatory and Non-Dealer-Participatory Mutual Shadow Authentication Capabilities
Abstract
1. Introduction
2. Preliminaries
2.1. Polynomial-Based SIS Scheme
2.2. Random Grid-Based VSS – RG-VSS
| Algorithm 1 RG-VSS. |
| Input: A binary secret image S, a pair of threshold parameters . |
| Output: n shadows , . |
| Step 1: For each position , repeat Steps 2–4. |
| Step 2: Sequentially calculate , , ⋯, repeatedly using Equation (2) where is the provisional pixels, |
| . |
| Step 3: Set , , ⋯ , , ⋯ if , else . |
| Step 4: Rearrangement , , ⋯, to , , ⋯, randomly. |
| Step 5: Output n shadows . |
3. Motivation and Contribution
4. The Proposed SIS with the Mutual Shadow Authentication Ability
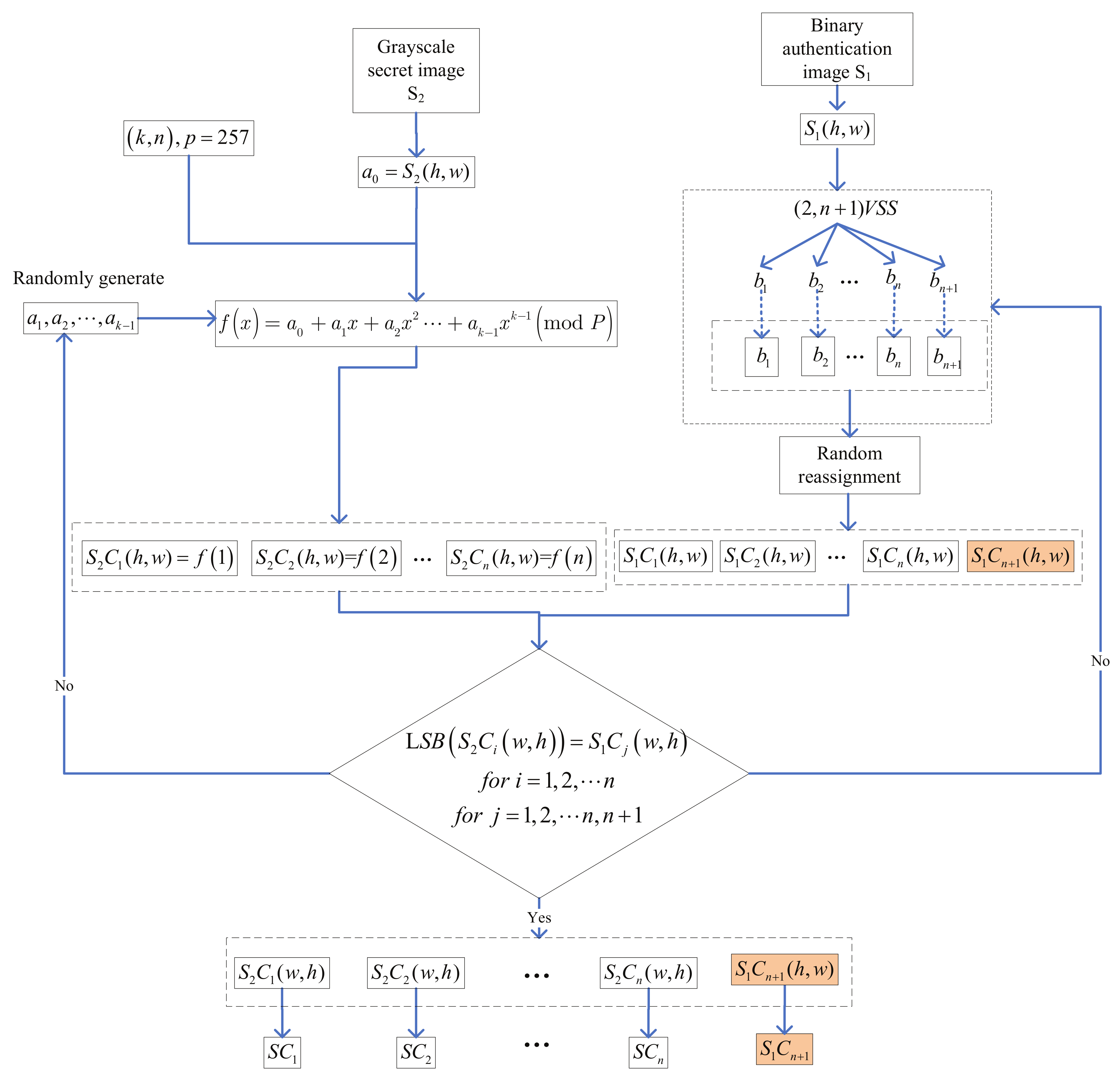
4.1. The Proposed Scheme
| Algorithm 2 The proposed secret image sharing for threshold authentication with dealer-participatory |
| and non-dealer-participatory mutual shadow authentication capabilities. |
| Input: A H×W grayscale secret image ; a H×W binary authentication image ; the threshold parameters |
| , where . |
| Output: Shadow , ; a binary authentication shadow . |
| Step 1: Specify a prime number . For each position , |
| repeat Steps 2–5. |
| Step 2: Utilize RG-VSS to split to temporary bits, denoted by , , ⋯, . |
| Randomly reassign , , ⋯, to , , ⋯, . |
| Step 3: Construct a degree polynomial, as shown below.
|
| where , is random, for . |
| Compute , for . |
| Step 4: Randomly pick up n numbers from , scrambling these n numbers, denoted by |
| . If and , for , |
| , go to Step 5 or go to Step 2. |
| Step 5: Specify to , for . |
| Step 6:n grayscale shadows and a binary authentication shadow which assigned |
| to the dealer if there exists are output. |
- 1.
- is a binary authentication image with size of which is held or known by all participants involved and the dealer. In other words, is public.
- 2.
- In Step 1, we set a prime number ; thus, in Step 4 to guarantee the value of the shadow pixel is within and lossless recovery by utilizing the screening operation.
- 3.
- Step 3 aims at guaranteeing the threshold attribute and no pixel expansion by using the polynomial.
- 4.
- Step 4 is designed to satisfy to achieve mutual shadow authentication.
- 5.
- Since and are random, when is small, we can find a set of random values to satisfy and , for , (randomly pick up n numbers from , Scrambling these n numbers, denoted by ) in Step 4. This way, can be losslessly recovered and mutual shadow authentication ability can be realized.
| Algorithm 3 The authentication and recovery in the proposed secret image sharing for threshold |
| authentication with dealer-participatory and non-dealer-participatory mutual shadow authentication |
| capabilities. |
| Input: The binary authentication image and dealer’s binary authentication shadow , any k |
| grayscale shadows . |
| Output: k authenticating results of for or authenticating results of |
| for for each participant involved depends on there is a dealer participant or not. |
| Recovered grayscale secret image with a size of H×W. |
| Step 1: If there is a dealer, for , take the LSB (least significant bit) of , denoted by |
| , obtain the reconstructed binary authentication image through the stacking or XORing |
| operation of and . If is recognized as by HVS or , pass the authentication |
| and go to Step 3; otherwise, a fake shadow is identified, denoted by , and broadcast the dishonest |
| participant to the other participants. |
| Step 2: If there is not a dealer involved, take the LSB (least significant bit) of the participant itself’s |
| shadow, denoted by , take the LSB (least significant bit) of for , denoted by |
| for , obtain the reconstructed binary authentication image through the |
| stacking or XORing operation of and . If all the are recognized as by HVS or , |
| pass the authentication and go to Step 3; otherwise, a fake shadow is identified, denoted by , |
| and broadcast the dishonest participant to the other participants. |
| Step 3: For each position , repeat Steps 4–5. |
| Step 4: Solve the following equation to get by Lagrange interpolation function.
|
| Step 5: Compute . |
| Step 6: Output recovered grayscale secret image with a size of H×W and k authenticating results of |
| for or authenticating results of for for each |
| participant. |
- 1.
- If there is a dealer, the dealer generates k authenticating results of for . If there is not a dealer, each participant involved generates the authenticating result of for . When we mention each participant involved, it means k participants in the final recovery.
- 2.
- The LSB of can be gotten by bitwise operation.
- 3.
- In Step 1, dealer or participants authenticate each gathered shadow to estimate whether is recognized as by HVS or ; thus, mutual shadow authentication is achieved by stacking or XOR operation.
- 4.
- In Step 2, every participant involved authenticates other participants’ shadows. for denote shadows held by other participants. Each participant involved takes his/her shadow’s LSB, denoted by . The other participants involved take their shadows’ LSBs, denoted by for . Since authentication is performed in pairs in our scheme, we achieve mutual shadow authentication.
- 5.
- In Step 2, every participant involved authenticates other participants’ shadows. So if are recognized as by HVS or , pass the authentication and go to Step 3.
- 6.
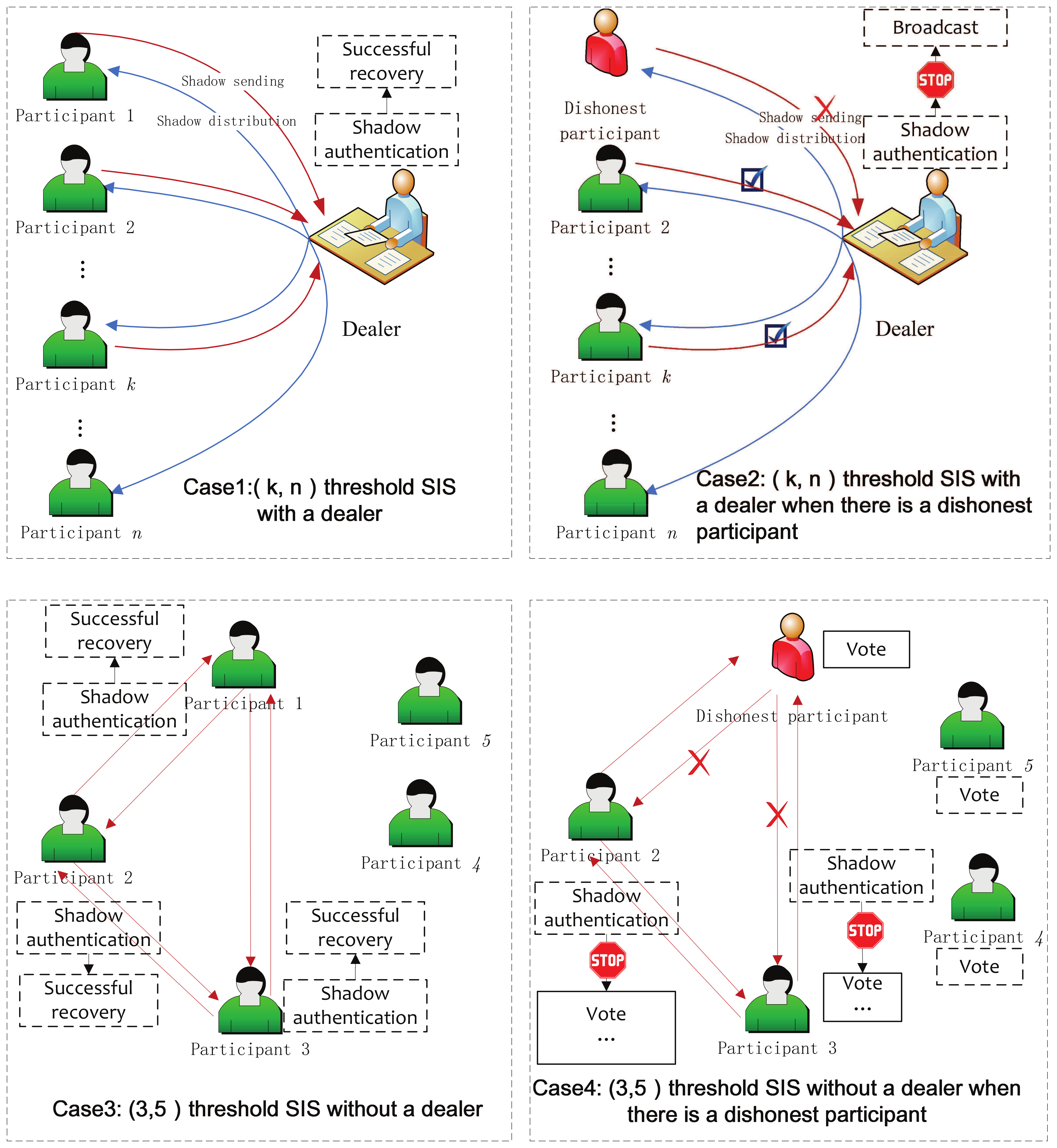
- In Step 2, when detecting a fake shadow, the participant broadcasts the dishonest participant to the other participants and stops recovery phase. Here, the scheme supposes that the participant performing shadow authentication is honest. There is no further discussion on how to authenticate and recover in the case of more than one dishonest participant in our scheme. In this paper, we focus on designing a SIS with mutual authentication capability, rather than the rules or protocols of mutual authentication among participants. However, one can design many protocols for authentication and recovery based on the proposed scheme with mutual authentication ability. For example, one can design to allow participants to perform authentication by using a vote-based protocol. Every participant authenticates other shadows, and decides whether to vote for the shadows. According to the result of a majority vote, the authenticity of the shadows is then determined by peers.
4.2. Security Analysis, Time and Space Complexity Analyses and Performance Proof
5. Experimental Results and Discussion
5.1. Experimental Illustration
- 1.
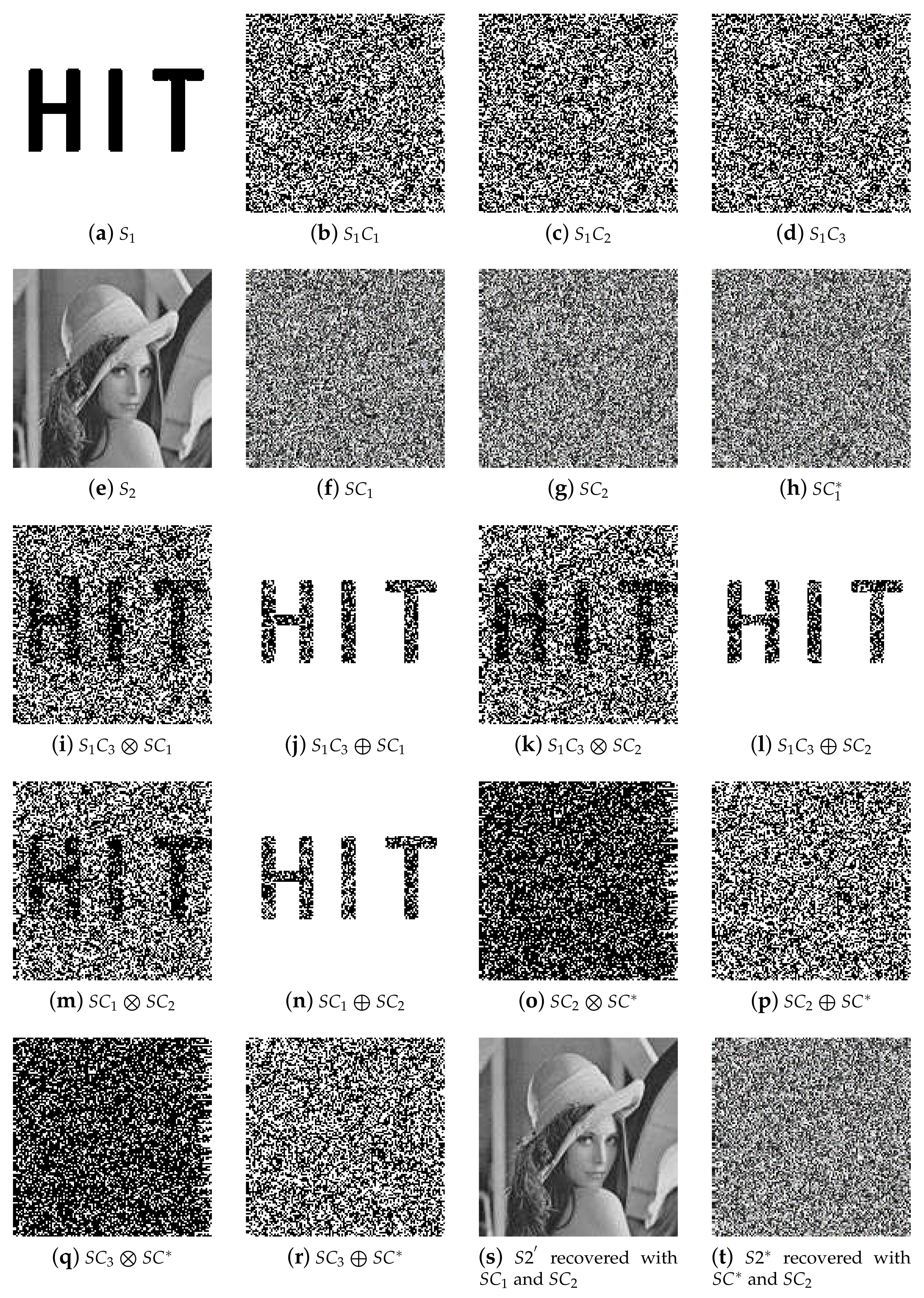
- The shadow generated by our scheme has no cross-interference and no pixel expansion of the secret image.
- 2.
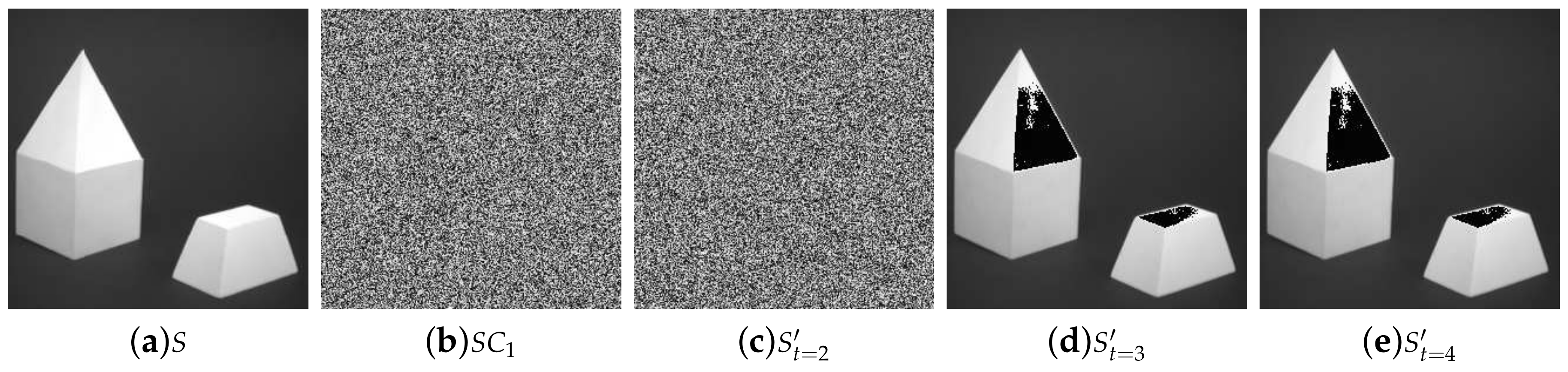
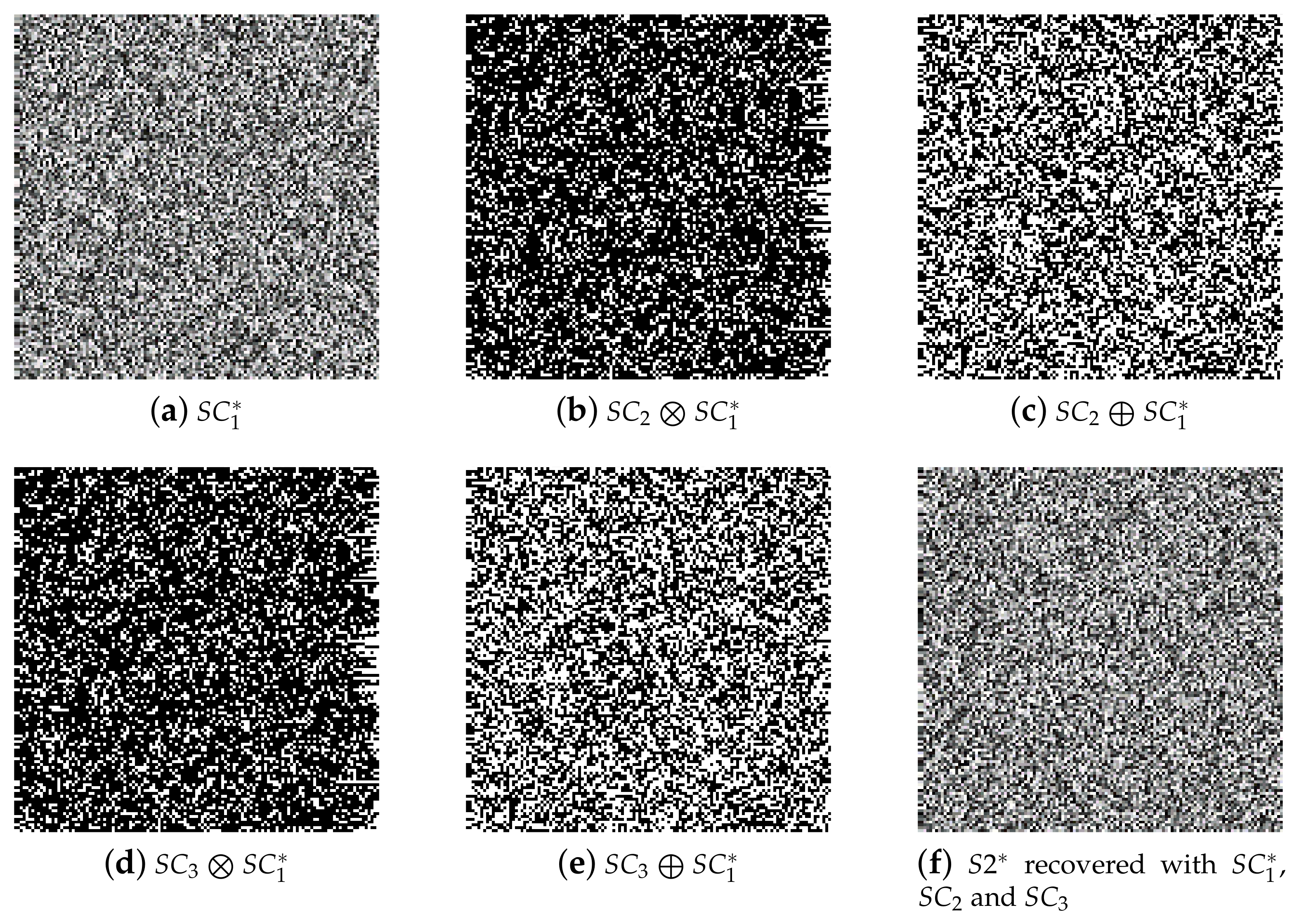
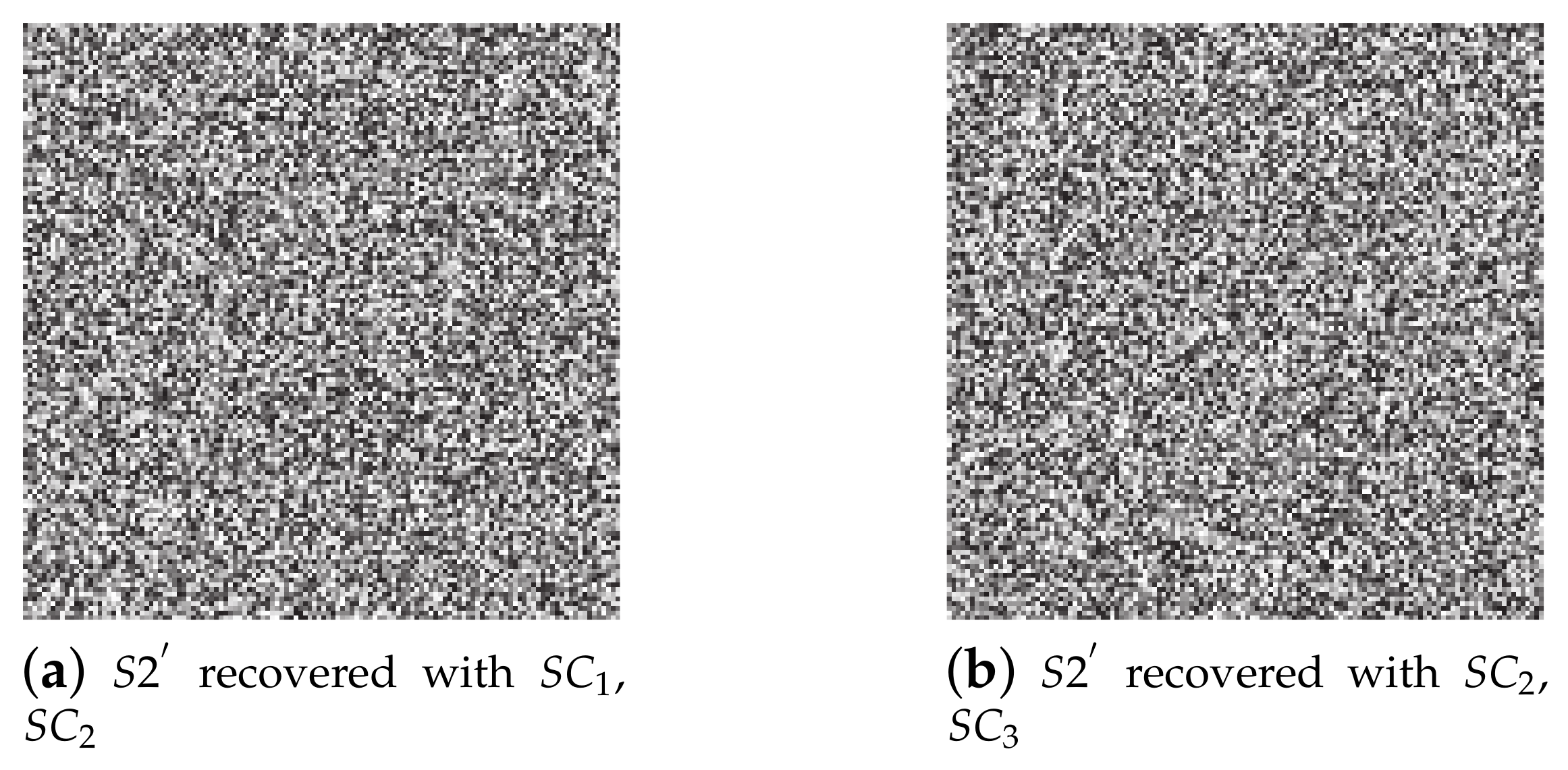
- Figure 7 shows the security of the proposed SIS when recovered with fewer than k shadows; the recovered image leaks no secret details.
- 3.
- One can losslessly reconstruct the secret image with any number k or more of shadows.
- 4.
- The binary authentication image is lossily reconstructed, so one can carry out authentication by only stacking or XORing operation.
- 5.
- The mutual authentication ability is gained based on SIS itself rather than another technique.
- 6.
- An SIS with dealer-participatory and non-dealer-participatory mutual shadow authentication for a general threshold is achieved, where . Since when k is fixed, as n increases more requirements should be satisfied. Through experiments, we give the suggestion that the condition is .
5.2. Comparisons with Relative Schemes
- 1.
- Inspired by Yan et al.’s work [21], we improve the SIS scheme to be suitable for the case with and without dealer by extending the sharing method of the authentication image from RG-VSS to RG-VSS. Yan et al. utilize the RG-VSS to split every pixel of authentication image into two temporary bits; one is assigned to binary authentication shadow, and another one guides the generation of secret pixels in polynomial-based SIS. We use RG-VSS to split every pixel of authentication image into temporary bits; one is assigned to the binary authentication shadow, and the others are used to guide the generation of secret shadows in polynomial-based SIS. Thus, in our scheme, any actor (participants or dealer) can be specified as a combiner. Yan et al.’s scheme works when there is a dealer.
- 2.
- As shown in Figure 9, when we share extreme image Figure 9a by Yan et al.’s and our threshold SISs respectively, we can see through our eyes that the shadows (Figure 9b–d) generated by Yan et al.’s reveal the secret, while ours (Figure 9e–g do not). The reason is that we use the pixels generated by RG-VSS to guide the LSBs of pixels generated by the polynomial-based SIS, while Yan et al. use the pixels generated by RG-VSS to guide the MSBs of pixels generated by the polynomial-based SIS. Besides, based on the above Lemmas 2 and 3, the conditions are satisfied. Unfortunately, Yan et al.’s use MSBs of pixels, which is the most significant bit, may cause information disclosure when gets larger and larger. In contrast, we use the LSB, which will be better.
- 3.
- Due to the characteristics of RG-VSS and RG-VSS, in the authentication phase, the shadow passes verification when the binary authentication image is always well recognized in our scheme. The shadow passes verification when the binary authentication image recovered respectively, by stacking or XORing, is always well recognized or losslessly recovered in Yan et al.’s scheme.
- 1.
- The proposed scheme is threshold SIS scheme. Contrarily, the scheme in Bhattacharjee et al.’s [25] work is threshold.
- 2.
- Bhattacharjee et al. embed the shares into several cover images; this leads to the need to extract shares from stegoimages during the recovery phase, and thus increases decoding complexity. Contrarily, we do not use a cover image at all. In addition, Bhattacharjee et al.’s scheme generates shadows of reduced size in the encoding phase by using a kind of encryption technology which increases encoding complexity.
- 3.
- Bhattacharjee et al.’s scheme has the characteristics of no key requirements but several cover image requirements, while our scheme only requires an authentication image to be public.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Naor, M.; Shamir, A. Visual cryptography. In Advances in Cryptology-EUROCRYPT’94 Lecture Notes in Computer Science, Workshop on the Theory and Application of Cryptographic Techniques, Perugia, Italy, 9–12 May 1995; Springer: Perugia, Italy, 1995; pp. 1–12. [Google Scholar]
- Wang, G.; Liu, F.; Yan, W. Basic Visual Cryptography Using Braille. Int. J. Digit. Crime Forensics 2016, 8, 85–93. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Wu, C.M.; Sun, Q.D.; Bi, W. Threshold changeable secret image sharing scheme based on interpolation polynomial. Multimed. Tools Appl. 2019, 78, 18653–18667. [Google Scholar] [CrossRef]
- Yang, C.N.; Ciou, C.B. Image secret sharing method with two-decoding-options: Lossless recovery and previewing capability. Image Vis. Comput. 2010, 28, 1600–1610. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C.; Wang, Y.; Lei, Z.; Ji, W. Cheating Identifiable Secret Sharing Scheme Using Symmetric Bivariate Polynomial. Inf. Sci. 2018, 453, 21–29. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C. Scalable secret image sharing scheme with essential shadows. Signal Process. Image Commun. 2017, 58, 49–55. [Google Scholar] [CrossRef]
- Chor, B.; Goldwasser, S.; Micali, S.; Awerbuch, B. Verifiable Secret Sharing and Achieving Simultaneity in the Presence of Faults. In Proceedings of the IEEE 26th Annual Symposium on Foundations of Computer Science, Portland, OR, USA, 21–23 October 1985; pp. 383–395. [Google Scholar] [CrossRef]
- Feldman, P. A practical scheme for non-interactive verifiable secret sharing. In Proceedings of the Annual Symposium on Foundations of Computer Science, Los Angeles, CA, USA, 12–14 October 1987; pp. 427–438. [Google Scholar] [CrossRef]
- Pedersen, T.P. Non-Interactive and Information Theoretic Secure Verifiable Secret Sharing. In Proceedings of the International Cryptology Conference on Advances in Cryptology, Santa Barbara, CA, USA, 11–15 August 1991; pp. 129–140. [Google Scholar] [CrossRef]
- Laih, C.S.; Harn, L.; Lee, J.Y.; Hwang, T. Dynamic Threshold Scheme Based on the Definition of Cross-Product in an N-Dimensional Linear Space. In Advances in Cryptology—CRYPTO’ 89 Proceedings; Brassard, G., Ed.; Springer: New York, NY, USA, 1990; pp. 286–298. [Google Scholar]
- Charnes, C.; Martin, K.; Pieprzyk, J.; Safavi-Nainil, R. Secret sharing in hierarchical groups. In Information and Communications Security; Han, Y., Okamoto, T., Qing, S., Eds.; Springer: Berlin/Heidelberg, Germany, 1997; pp. 81–86. [Google Scholar]
- Rong, Z.; Jie Zhao, J.; Dai, F.; Qun Zhao, F. A new image secret sharing scheme to identify cheaters. Comput. Stand. Interfaces 2009, 31, 252–257. [Google Scholar] [CrossRef]
- Liu, Y.X.; Sun, Q.D.; Yang, C.N. (k,n) secret image sharing scheme capable of cheating detection. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 72. [Google Scholar] [CrossRef]
- Hu, C.; Li, R.; Bo, M.; Wei, L.; Bie, R. Privacy-preserving combinatorial auction without an auctioneer. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 38. [Google Scholar] [CrossRef]
- Wang, Z.H.; Chang, C.C.; Huynh, A.; Li, M.C. Sharing a Secret Image in Binary Images with Verification. J. Inf. Hiding Multimed. Signal Process. 2011, 2, 78–90. [Google Scholar]
- Lin, C.C.; Tsai, W.H. Secret image sharing with steganography and authentication. J. Syst. Softw. 2004, 73, 405–414. [Google Scholar] [CrossRef]
- Yang, C.N.; Chen, T.S.; Yu, K.H.; Wang, C.C. Improvements of image sharing with steganography and authentication. J. Syst. Softw. 2007, 80, 1070–1076. [Google Scholar] [CrossRef]
- Yang, C.N.; Ouyang, J.F.; Harn, L. Steganography and authentication in image sharing without parity bits. Opt. Commun. 2012, 285, 1725–1735. [Google Scholar] [CrossRef]
- Yan, X.; Gong, Q.; Li, L.; Yang, G.; Lu, Y.; Liu, J. Secret image sharing with separate shadow authentication ability. Signal Process. Image Commun. 2019, 115721. [Google Scholar] [CrossRef]
- Kafri, O.; Keren, E. Keren, E. Encryption of pictures and shapes by random grids. Opt. Lett. 1987, 12, 377–379. [Google Scholar] [CrossRef]
- Yan, X.; Liu, X.; Yang, C.N. An enhanced threshold visual secret sharing based on random grids. J. Real-Time Image Process. 2018, 14, 61–73. [Google Scholar] [CrossRef]
- Ghoreishi, S.F.; Imani, M. Bayesian Optimization for Efficient Design of Uncertain Coupled Multidisciplinary Systems; American Control Conference (ACC): Denver, CO, USA, 2020. [Google Scholar]
- Bhattacharjee, T.; Maity, S.P. An image-in-image communication scheme using secret sharing and M-ary spread spectrum watermarking. Microsyst. Technol. 2017, 4263–4276. [Google Scholar] [CrossRef]


| Properties | Our Scheme | Yan et al. [21] | Bhattacharjee et al. [25] |
|---|---|---|---|
| Threshold | progressive quality access | ||
| Dealer participatory | No | Yes | No |
| Verification operation | VCS(OR/XOR) | VCS(OR/XOR) | Watermark |
| Recovery operation | Lagrange interpolation | Lagrange interpolation | Pixel rearrangement |
| Cover images | No | No | Yes |
| Pixel expansion | No | No | No (reduced shadow size) |
| Technology | Polynomial-based SIS and RG-VSS | Polynomial-based SIS and RG-VSS | Data hiding |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, Y.; Yan, X.; Qi, J.; Lu, Y.; Zhou, X. Secret Image Sharing with Dealer-Participatory and Non-Dealer-Participatory Mutual Shadow Authentication Capabilities. Mathematics 2020, 8, 234. https://doi.org/10.3390/math8020234
Jiang Y, Yan X, Qi J, Lu Y, Zhou X. Secret Image Sharing with Dealer-Participatory and Non-Dealer-Participatory Mutual Shadow Authentication Capabilities. Mathematics. 2020; 8(2):234. https://doi.org/10.3390/math8020234
Chicago/Turabian StyleJiang, Yue, Xuehu Yan, Jianqing Qi, Yuliang Lu, and Xuan Zhou. 2020. "Secret Image Sharing with Dealer-Participatory and Non-Dealer-Participatory Mutual Shadow Authentication Capabilities" Mathematics 8, no. 2: 234. https://doi.org/10.3390/math8020234
APA StyleJiang, Y., Yan, X., Qi, J., Lu, Y., & Zhou, X. (2020). Secret Image Sharing with Dealer-Participatory and Non-Dealer-Participatory Mutual Shadow Authentication Capabilities. Mathematics, 8(2), 234. https://doi.org/10.3390/math8020234





