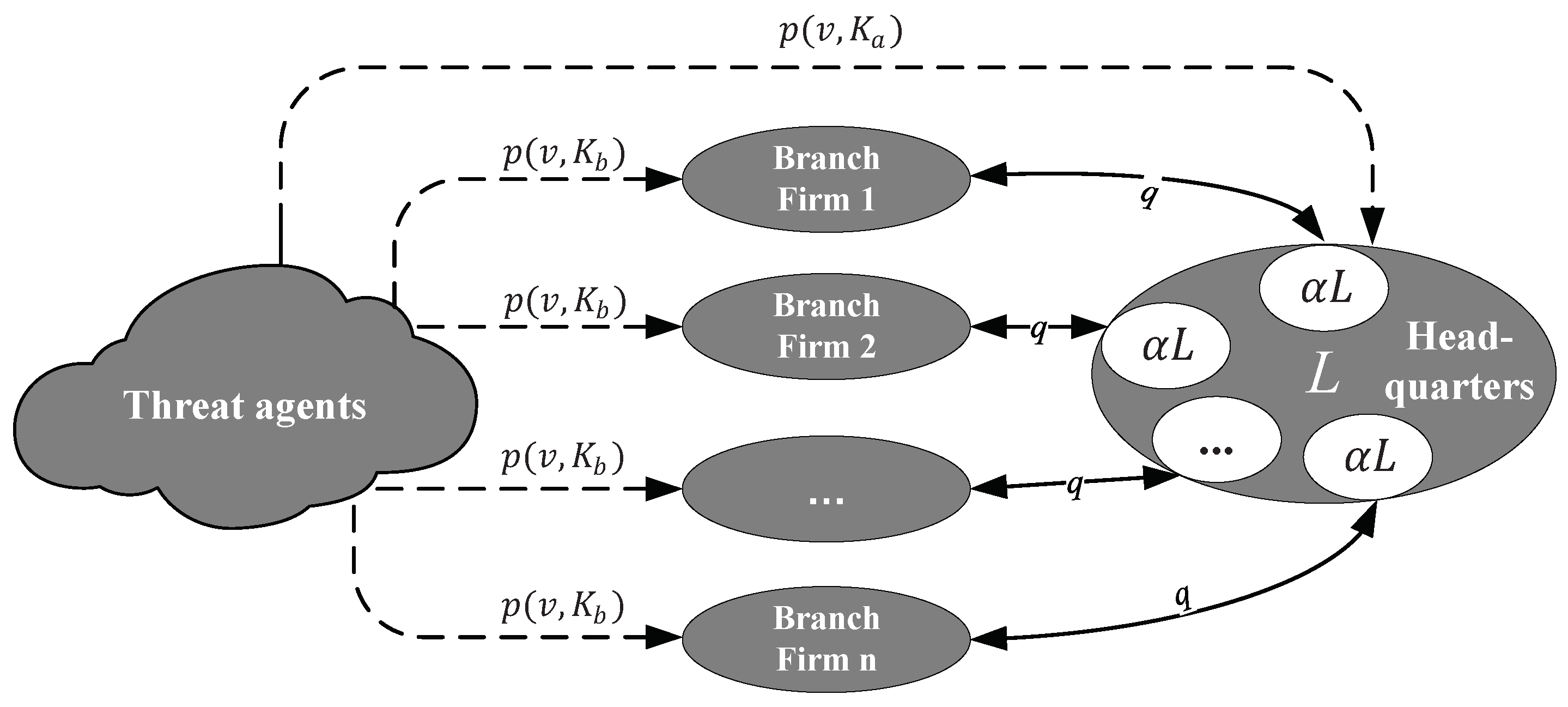
1. Introduction
The Internet of Things and communication networks have promoted the development of the network economy. However, the network interconnections also increase indirectly the probability of cybersecurity breach. It has been estimated that the global average cost on information breaches and the loss of mega data breaches are up to
$3.86 million and
$350 million, respectively [
1]. New legislation and regulations, such as the General Data Protection Regulation (GDPR), the National Cyber Incident Response Plan (NCIRP), and People’s Republic of China Network Security Law (PRCNSL), have been issued to urge firms to take cybersecurity measures. Hence, it is significant for firms to increase cybersecurity investments to avoid unnecessary losses. As we all know, there is no completely secure network environment with increasing reliance on network interconnection and information sharing [
2,
3]. Therefore, the optimal investment on cybersecurity has been investigated based on decision theory and economics model to reduce potential losses and security risks by taking the environmental factors, such as the network vulnerability and hacker attack types, etc., into account [
4,
5,
6,
7].
Interdependent firms and branches interconnect their databases or share information to improve the efficiency of information exchanges [
8,
9], which in turn would expose the participating firms or branches to security risks. On the one hand, participating firms or branches physically connect to each other through a mutual trust network or interface, and the other information systems will become vulnerable if any of them are compromised by hackers, which makes it easier for hackers to penetrate their systems via mutual trusted IT infrastructure, e.g., local area networks (LANs) and wide area networks (WANs), and steal sensitive data [
10,
11]. For example, Cainiao, the logistic arm of Alibaba, run the largest logistics database all over the world by establishing a platform integrating information resources of third-party logistics systems [
12]. Cainiao’s centralized data platform connects its logistics parties and E-commerce merchants to integrate trading, tracking and shipping operations, which makes it possible for hackers to invade the system immediately after breaking its third-party logistics or merchants with weak cybersecurity. On the other hand, the cooperation and mutual benefit for production innovation or value creation can be achieved by information sharing, while the shared information will also be accessed once any systems on the platform are compromised by hackers. For example, a logistics server breached by hackers result in not only direct losses of the logistics department, but also indirect leakage of the partner’s order information. Obviously, the more information shared, the more information loss interdependent firms or branches suffer.
It should be noted that security breaches often occur in chain enterprises with many sub-branches and members, such as chain hotels, big banking groups and aviation groups. BBC News reported that the two hacking attacks on Hilton Hotels Corporation exposed more than 360,000 credit cards and other information to risks, and Hilton Hotels Corporation was fined
$700,000 at that time, which would be
$420 million under GDPR [
13]. The customer data were revealed from a hotel system in UK belonging to the company, and then its brands and franchises were affected by the attack without exception. Coincidentally, there were several companies suffering similar information leakage incidents, such as HSBC Bank [
14], the Canadian Imperial Bank [
15], and Cathay Pacific [
16], who shared customer information with all their branches. Therefore, it is necessary for both headquarters and its branches to improve the level of cybersecurity to avoid losses’ expansion. Considering the bidirectional indirect information breach among headquarters of a group firm and its branches, the servers of the headquarters and its branches are usually interconnected to facilitate more efficient business operations. Once hackers or virus attack the server of one branch, the information system of headquarters might be accessed and penetrated. In addition, the information assets of all branches are actually backed up in the headquarters system, which might also be revealed if the information system of headquarters is exposed to the risks.
Previous studies mainly focused on optimizing security investment in terms of system interconnection and information sharing among homogeneous firms [
5,
11,
17]. Considering the fact that there are limited budgets on security investment which are often at a disadvantage when competing with that on other investment projects [
18], one must allocate optimally the limited budgets to all branches including headquarters to achieve the highest cybersecurity gains, which, as authors known, is rarely mentioned in previous studies. Trying to fill the research gaps, a mathematical model is developed in this paper to investigate the optimal allocation of security investment among headquarters and its n-branches with budget constraints. The indirect risks of security breaches introduced by the interconnection of information systems among headquarters and branches are taken into account. In addition, the influence of security information sharing on the allocation of security investments is also analyzed via numerical simulation. Our analysis produces the following interesting findings: When the budget is small while intrinsic vulnerability is larger relatively, the firm will give priority security investment to headquarters. The allocation on branches is positively correlated to propagation probability and almost proportional to budget, but never exceed
of the total budget, while that decreases with intrinsic vulnerability. Security information sharing can bring positive investment gains to headquarters and branches, which is conducive to improving the security level of the whole system under the same budget.
The rest of the paper is organized as follows.
Section 2 reviews the literature on the studies of the independent and interdependent security investment and allocation. In
Section 3, the mathematical model is established to describe the security investment among headquarters and its branches in a business group under the bidirectional propagation risks and budget limitation. Then, the optimal allocation of cybersecurity investment is derived and analyzed in
Section 4.
Section 5 extends the model to consider the impact of security information sharing.
Section 6 summarizes the conclusions and provides managerial implications.
4. Optimal Allocation of Cybersecurity Investment
Since branches are assumed to be homogeneous, we have
, for
. Substituting
into (
1) and (
2), we get
Proposition 1. is the necessary and sufficient condition for the existence and uniqueness of optimal allocation. Morever, when and , the group does not allocate the information security budget to its branch firms.
Proof. Then, the optimal investment allocation of a branch can be obtained by minimizing the cost function of (
3). The concavity and convexity of the cost function are not considered for the time being, thus the extreme point can be obtained by first-order condition as follows:
where
during
. The solution of the first-order condition is determined by the following:
To find the possible extreme point of the cost function, we derive:
Before judging the sign of (
6), we need to compare the sizes of
and
. According to (
4), we get
and then
It is clear to see that the right side of the above formula is negative, and, immediately, the relationship between the breach probability of headquarters and branch is
Furthermore, substituting (
9) into (
6), we get
which indicates that
is monotonic. If the solution of
exists, it must be unique, that is, the total cost function has at most one extreme point in
. Next, we discuss whether this point is the optimal allocation in two cases respectively (existence of optimal solution).
Case 1: at
. In practice, firms will never begin to protect their information systems if they suffer negative returns at the first security investment, i.e., the marginal benefit of the security investment should be greater than the marginal cost [
5]. The return here can be regarded as the relative reduction of cost function when increasing investment in information security, so
at
is beneficial for group’s security investment decision. Then, the derivative of the cost function at the right boundary
is given by
Obviously,
is always greater than zero. At this time,
can be expressed as
The cost function decreases at the left boundary and increases at the right boundary of
, thus there must be at least one minimum. The minimum must be unique in this domain because the cost function has at most one extreme. Therefore, the existence and uniqueness of optimal allocation to branches is proved. Furthermore, the condition can be derived from (
12):
When , the optimal security investments of headquarters and branch are exactly and , respectively.
Case 2: at . In contrast to Case 1, the group invests the first dollar in branches’ security, and the security cost will increase. According to given by Case 1, the total cost function increases at the left and right boundaries of . If the minimum cost exists, the number of optimal solutions must be no less than two, which conflicts with the uniqueness of solution. Therefore, the cost function will increase with in , and the minimum cost will be obtained at and .
The above analysis shows that is the sufficient and necessary condition for the existence and uniqueness of the optimal allocation to branches, that is, if only , . Noted that if , i.e., , information security budget would be allocated to each branch only when , while is always established if . According to the above analysis, we arrive at the following proposition. If only and , the group will not allocate the security investment to branches. Proposition 1 is proved. □
Proposition 1 reveals that, if the intrinsic vulnerability is high enough while total security budget is relatively small (), the group would give priority allocation to its headquarters. Conversely, if the intrinsic vulnerability is sufficiently low for , always stand up and then the group will always invest in information security for all its headquarters and branches. It is clear that under extremely tight budgetary and external conditions, the most of the budget will be used for the security risk management of headquarters to minimize potential losses due to the fact that it stores all data of the whole information system. Security investment and breach probability satisfy the property of diminishing marginal benefit, and the breach risk of headquarters is low enough to be insensitive to security investment when intrinsic vulnerability is small. Therefore, the group will achieve more security returns by allocating part of the budget to branches, which, in practice, implies that intrinsic vulnerability of the system deserves attention and a sufficient security budget is also necessary if the group expects to achieve a higher level of information security because of the inevitable interaction of subsystems and the information liquidity under interconnected network.
On the basis of the boundary condition above, the optimal investment level (“*”in this paper indicates the optimal allocation of security investment with given budget.)
is subject to (
4) and the proportion of it in the total budget, i.e.,
, will be explored. The relationship between
or
with related factors, such as the proportion of information assets
, the propagation probability
q, the budget constraints
K, and the intrinsic vulnerability
v, etc., is significant in practical decision-making. Since it is difficult to give the analytical solution of
from (
4) directly, the implicit function analysis method is adopted in the following study. At this point, the parameter
x (
) and the optimal investment
can be determined by the implicit function of
. The derivative of the
to
x can be obtained [
38].
4.1. The Proportion of Branch Information Set
Next, we analyze the relationship of the optimal allocation with the proportion of branch information set in the whole group. The following proposition is given first.
Proposition 2. The optimal security investment for each branch increases with the proportion of branch information set α.
Proof. The relationship between
and
can be solved from (4) as follows:
According to the above condition
, it is obvious that the molecule on the right side of (
14) is positive. Combining
and
, breach probability of headquarters and branch also satisfies
Following the principle of derivation of implicit function
,
given by (
10), and
. The first order partial derivative of (
5) with respect to
can be expressed as
It is easy to obtain that (
16) is greater than zero. Thus,
is established, and then Proposition 2 is proved. □
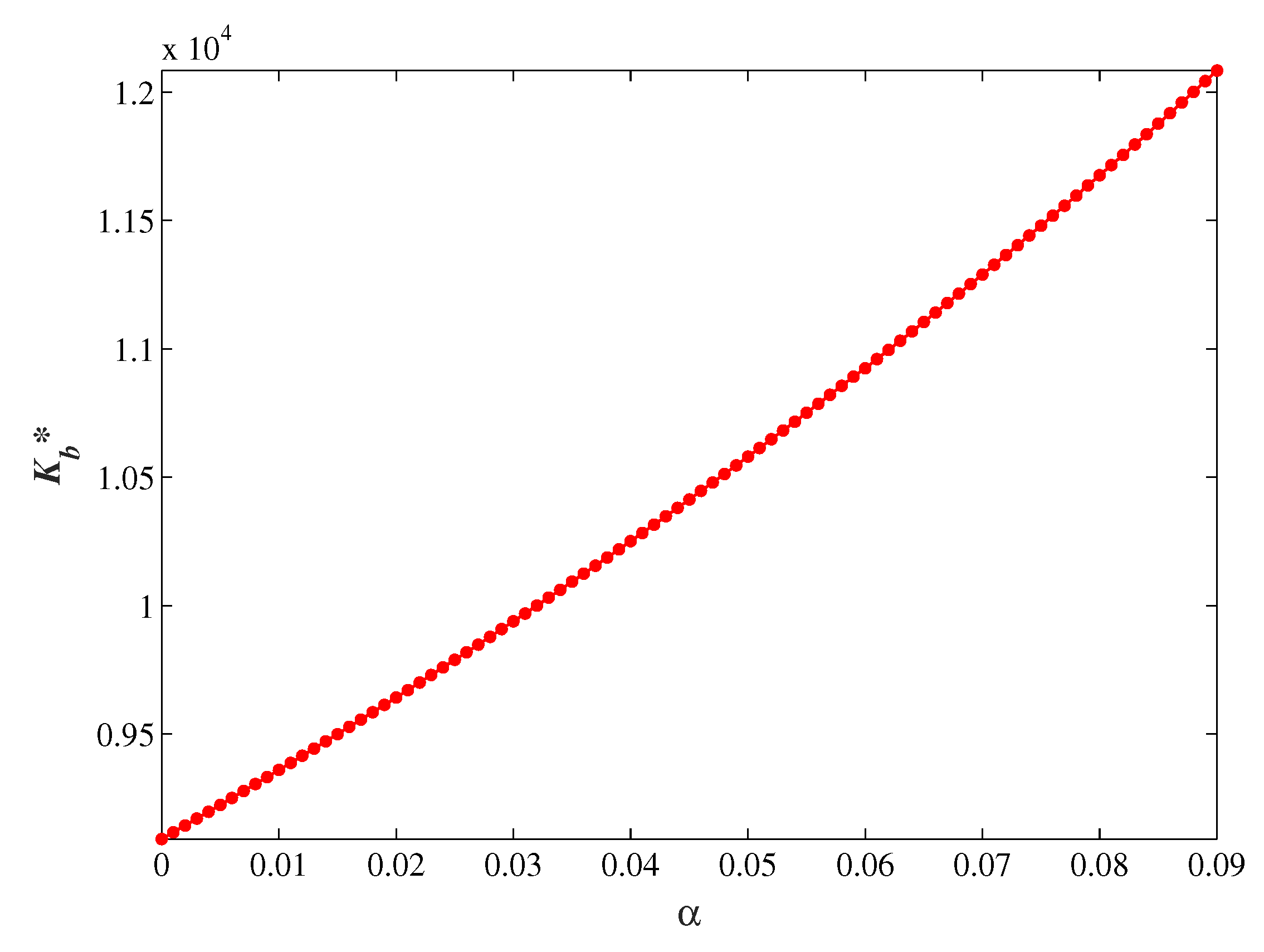
To present Proposition 2 intuitively,
Figure 2 shows numerically the relationship of the optimal allocation of security investment on each branch
with the proportion of branch information set
under
,
,
,
,
M,
(As of 2018, the cost of a data breach study by Ponemon shows that the United States and the Middle East respectively spend
$1.76 million and
$1.47 million—the most on post data breach response activities [
1]. We take the median of the two numbers as an example of numerical simulation, and let
M. Gorden and Leob [
7,
39] suggested that the optimal cybersecurity investment will not exceed 37% of potential losses. In practice, this proportion will be less, according to a breach survey of U.K. Department for Digital, Culture, Media & Sport [
40]. This paper sets the security budget as 25% of potential losses.), and
. Proposition 2 and the numerical result both indicate that the optimal security investment and its allocation
for given budget increase continuously with the proportion of its information set. The result accords with our intuition. The more valuable information stored in branch firms, the greater the potential loss it will suffer, and it is necessary to reduce the information risk by increasing the allocation of security investment to branches.
4.2. Propagation Probability
Proposition 3. If , where and , the group would not allocate cybersecurity funds to branches. The optimal cybersecurity investment of a branch increases and approaches with propagation probability q when .
Proof. Since
in (
10), the sign of
is determined by
, which is
Let
for convenience, then it is apparent that
As
according to (
9), we can obtain
Therefore,
, i.e., the optimal allocation of cybersecurity budget to branches will increase with the propagation probability. Substituting
into
, we can obtain the lowest propagation probability that the group begins to consider for investing in the cybersecurity of branches:
where
and
. Since
monotonically increases with
q, the group will allocate all its budget to headquarters at
, and the upper limit of security investment allocated to each branch can be calculated by substituting
into
and simplifying it as
The upper limit of
can be easily obtained from (
21). □
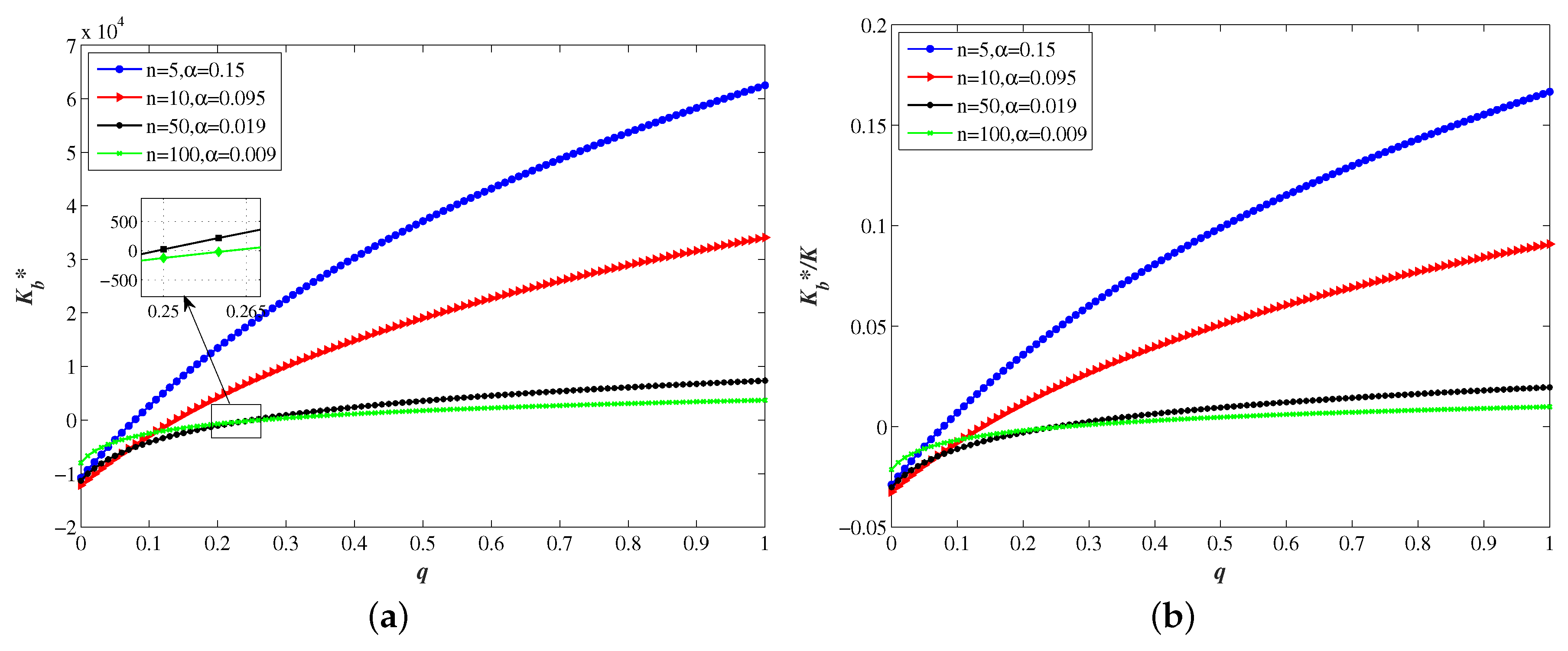
Figure 3 numerically analyzes the response of optimal security allocation to propagation probability considering different numbers of branch under
,
,
,
, and
. We can see that, with the increase of propagation probability
q, the cybersecurity of branches has been paid more and more attention. If
, the risks caused by indirect breach from branches are not enough to attract sufficient attention from the overall situation, thus the group does not invest in branches’ security. The internal security risks have grown in the real network environment when the systems of headquarters and its branches are more interconnected and exposed. Then, there are more channels and ways for the intruders to launch attacks, and more investment is required accordingly.
Figure 3 also illustrates that, when
,
decreases with increasing
n, which simply means that the more branches there are in the group, the less security investment each branches will obtain, while the security information investment in its headquarters has been always guaranteed. We also see that, consistent with common sense,
gradually approaches
as
q increases, which indicates that the amount of security investment allocated to headquarters is always higher than that allocated to each branch, and although the investment proportion of headquarters will decrease as the number of branches increases, it is still higher than the average level of
.
4.3. Total Budget Constraints
Next, the relationship between the total investment budget K and optimal security investment of each branch will be investigated.
Proposition 4. The cybersecurity investment of each branch increase almost linearly with the total security budget K, and its proportion approach to with decreasing rate.
Proof. The first-order derivative of
to
K can be solved from (
7) as follows:
which is obviously greater than zero. Similar to the proof of Proposition 3, it is clear to see that
according to (
10), which indicates that
increases monotonously with
.
Solving the equation of
about
K, we obtain the relationship of
K with
as
where
monotonically increases with
. It is easy to obtain that the range of
A is [
], which is very small and can be negligible relative to
. Therefore,
is approximately proportional to
K with the ratio of
. With the increasing of
K,
A is close to the constant
, and the linear relationship between
and
K is more obvious. From (
23), the investment proportion of each branch can be expressed as
Obviously, the monotonicity of the
is determined by
. Then, we derive the derivative of
with respect to
as
which is easy to prove to be less than zero. Therefore, with the increase of
increases,
decreases, and
increases.
According to Proposition 1, when , . As K increases, is gradually close to zero, so the investment proportions of each branch and headquarters approach from 0 and 1, respectively, which indicates that, when the cybersecurity budget is sufficient, the headquarters and branches will divide the budget equally. □
Figure 4 numerically shows the relationship of optimal security investment with a total budget for intuitive analyses of Proportion 4 under the conditions of
,
,
,
, and
. The result indicates that the optimal security investment of each branch and its proportion both increase with total security budget. It is clear that
is approximately proportional to
K, while its proportion slows down and approaches
. In addition, the efficiency of cybersecurity investment
will promote the group to increase the investment proportion to its branches.
The theoretical and numerical results clearly reveal that the increased budget will be approximately divided equally among all departments on the basis of the original allocation. When the budget is small, the investment proportion of branches will be sensitive to other factors, such as propagation probability, intrinsic vulnerability, and branch information set, etc., which will be ignored with sufficient budget. At this time, the headquarters and branches will enjoy the same level of cybersecurity. The efficiency of security investment cannot significantly affect the linear relationship between the investment amount of branches and the total budget, but high efficiency will greatly promote the group to pay more attention to the cybersecurity of branches.
4.4. Intrinsic Vulnerability
The intrinsic vulnerability is determined by the internal configuration of the system. In general, the system configuration and performance of headquarters and branches are the same, and hence we assume that there is an equal internal vulnerability among them. In this section, the impact of intrinsic vulnerability on optimal cybersecurity allocation will be investigated numerically.
Due to that fact that an accurate analytical solution of
is impossible to obtain from the equation of
, and the implicit function analysis method is also incapable of drawing any interrelated results; therefore, the numerical simulation is employed to verify the relationship between
and
v under conditions of
,
,
,
,
, and
as shown in
Figure 5.
It is clear to see that the proportion of security investment to each branch decreases with the increase of intrinsic vulnerability under different budgets, and the decline rate is gradually increasing. The varies between , and, when intrinsic vulnerability is very high, the most favorable decision is not to protect the branch system, which is consistent with the conclusion of Proposition 1. Such results imply that, in order to minimize potential losses, it is better for the group to focus the most or even all of budgets on protecting the cybersecurity of headquarters as the intrinsic vulnerability increases because the potential losses caused by indirect propagation from branches will be much smaller than those caused by direct breach of the headquarters system. However, it is a radical strategy to allocate all budgets to headquarters, which can be improved by increasing total budgets for cybersecurity.
5. Extension to Effects of Security Information Sharing
Sharing computer security vulnerabilities, breaches, intrusions, and technological solutions is an effective way to help organizations prevent, detect and correct security breaches proactively. Studies have also pointed out that security information sharing could reduce the uncertainty of network security investment to a certain extent, and thus depress the value of deferred options related to the investment [
24,
25,
30]. President Obama signed the Cybersecurity Information Sharing Act (CISA) in 2015 to improve the level of cybersecurity in the United States. The US Department of Homeland Security (DHS) has made security information sharing an important strategy. Some security-based sharing organizations have been established and funded to exchange cybersecurity threat information, such as the industry-based Information Sharing and Analysis Centers (ISACs) and the Computer Emergency Readiness Team (CERT). The industry and the UK government also jointly launched an initiative, named Cyber Security Information Sharing Partnership (CISP), to share threat information in order to enhance the public awareness and reduce negative influences on businesses. Thus, we plan to study the impact of security information sharing on the optimal allocation of security investment within a business group in this section.
In general, a group’s internal departments and branches often share their security information, such as hacking attempts including successful and unsuccessful cases, methods to prevent vulnerabilities, and ways to minimize economic loss. If one firm shares security information, it will help other firms to prevent future breaches to reduce security breaches probability to a certain extent. The reduction in the breaches probability could be regarded as a virtual increase in security investments for other firms.
Specifically, if a branch invests on cybersecurity and share security information with the headquarters, the effective investment amount of the headquarters is . On the contrary, if the headquarters shares security information with its branches, the effective expenditures each branch spends on cybersecurity could be expressed as . We assume that the headquarters and branch firms in the group share all their security information respectively, and sharing security information will bring the security investment benefits by to the sharing partners, where is denoted as the benefited rate of security information sharing. Notice that full sharing of security information does not achieve a 100% benefited rate due to the repeatability of security information and the uncertainty of external attacks. Therefore, reflects the security sharing efficiency, and means that sharing security information is completely invalid for reducing the system breach risk, at which time the optimal allocation is consistent with that of non-sharing security information discussed above.
Replacing
and
with
and
, then rewrite (
2) as
whose first-order derivative to
is
where
and
. Since the analytical solution of
cannot be obtained from
directly and it is also hard to find relevant results through an implicit function analysis method. Therefore, the numerical method is used to solve the first-order condition by bringing all into the cost function. We have ergodically verified whether the extreme point obtained by the numerical method is the minimum on the domain of
.
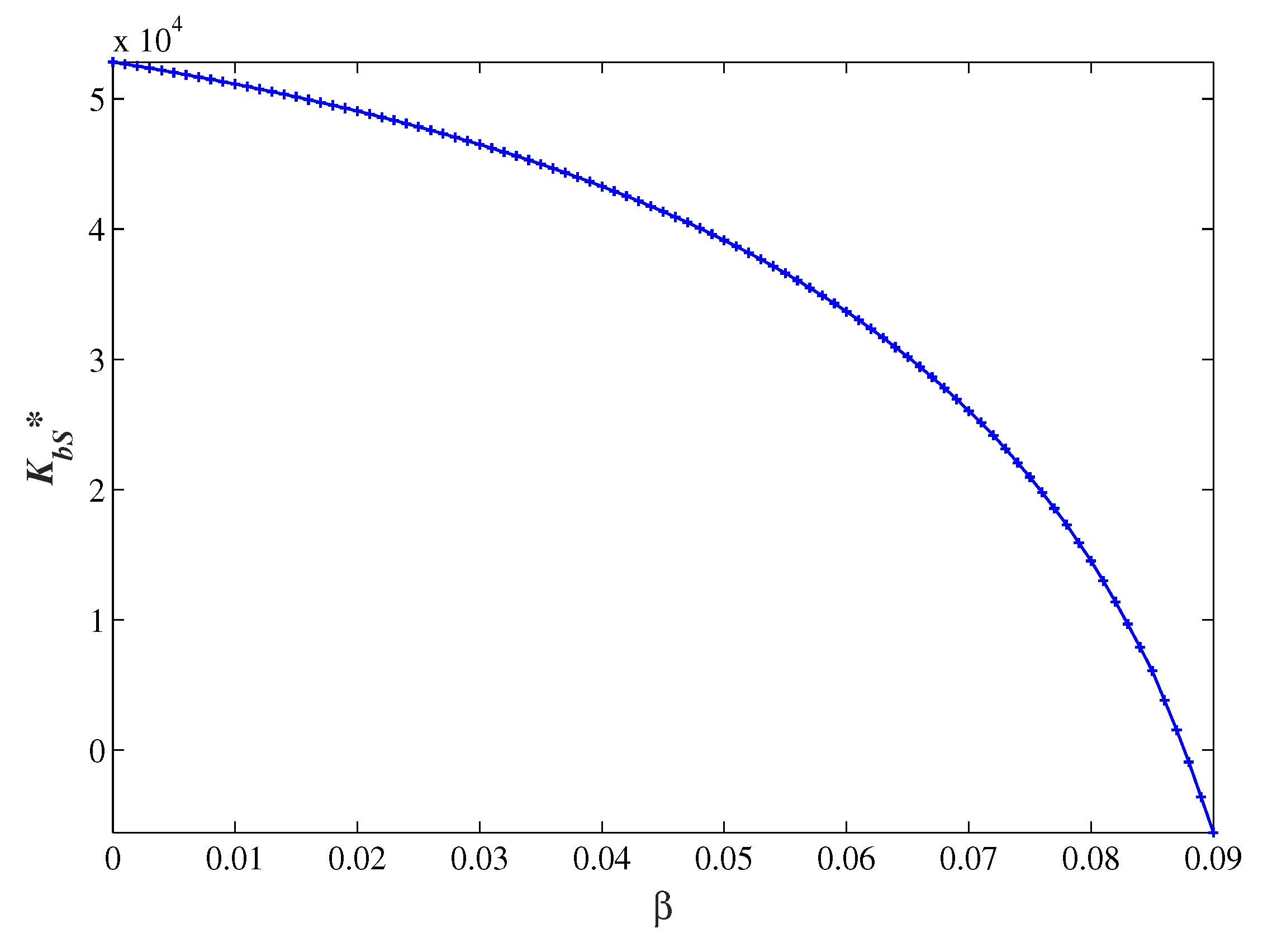
Figure 6 shows the changes of the optimal allocation to each branch
with respect to the benefited rate
, where
,
,
,
,
,
, and
.
We can see that decreases and approaches zero as increases continuously. On the one hand, the increase of benefited rate means a reduced repetition rate of security information and more complete data information containing breaches and technology solutions, which is equivalent to indirectly improving the total budget of the whole system. Obviously, all branches will benefit after increasing the security investment of headquarters, and, along with the enhancement of headquarters security level, security measures and experiences can be shared with all branches, thus further improving the security level of the whole group. On the other hand, it is more efficient for the group to centralize its budget to protect cybersecurity at headquarters than to decentralize its budget to all branches. At this time, the headquarters achieves lower security risks, and all branches indirectly improve the stability of the system through the security information shared by the headquarters. On the contrary, if the budget allocation of all branches is increased, there is a weak improvement of information system for the single branch, and the headquarters will also get less security information from branches, which is very disadvantageous to the whole system. Therefore, the group chooses to reduce actual security investments in branches under security information sharing.
Next, the interesting issue is the influence of security information sharing on the relationship of optimal allocation with propagation probability.
Table 2 shows the numerical analysis of the response of
and
to
q by varying
v of 0.1, 0.3, 0.5, 0.7 compared with that of no security information sharing (
).The other constant parameters are set as
,
,
,
,
, and
. Several indicates are obtained from
Table 2. First,
increases with
q, but, with the larger v, the less the security investment
and
allocated to each branch, which are consistent with the conclusions in
Section 4.2 and
Section 4.4. Second, the investment allocation to branches under no security information sharing is more than that under security information sharing, i.e.,
, which is not affected by intrinsic vulnerability. Since security information sharing brings more virtual investment from headquarters to branches than from branches to headquarters, the actual investment allocation of each branch would slowly respond to the increasing propagation probability. To reduce cost and improve security levels, the group could reduce its security investment in branches. Third, we need to pay attention to the critical value of propagation probability, expressed as
and
, when optimal security investment in each branch is greater than or equal to zero under the two cases. We note that both
and
increasing with
v and
always stands, and, when
v is small, the optimal allocation to branches is always greater than zero regardless of sharing security information or not. It is also very intuitive that the optimal security investments of security information sharing are allocated to branches later than that of no information sharing with the same conditions because of the virtual investment effect. As security risks increase between interconnected systems, the group will start to invest in branches’ cybersecurity at slightly higher propagation probability.
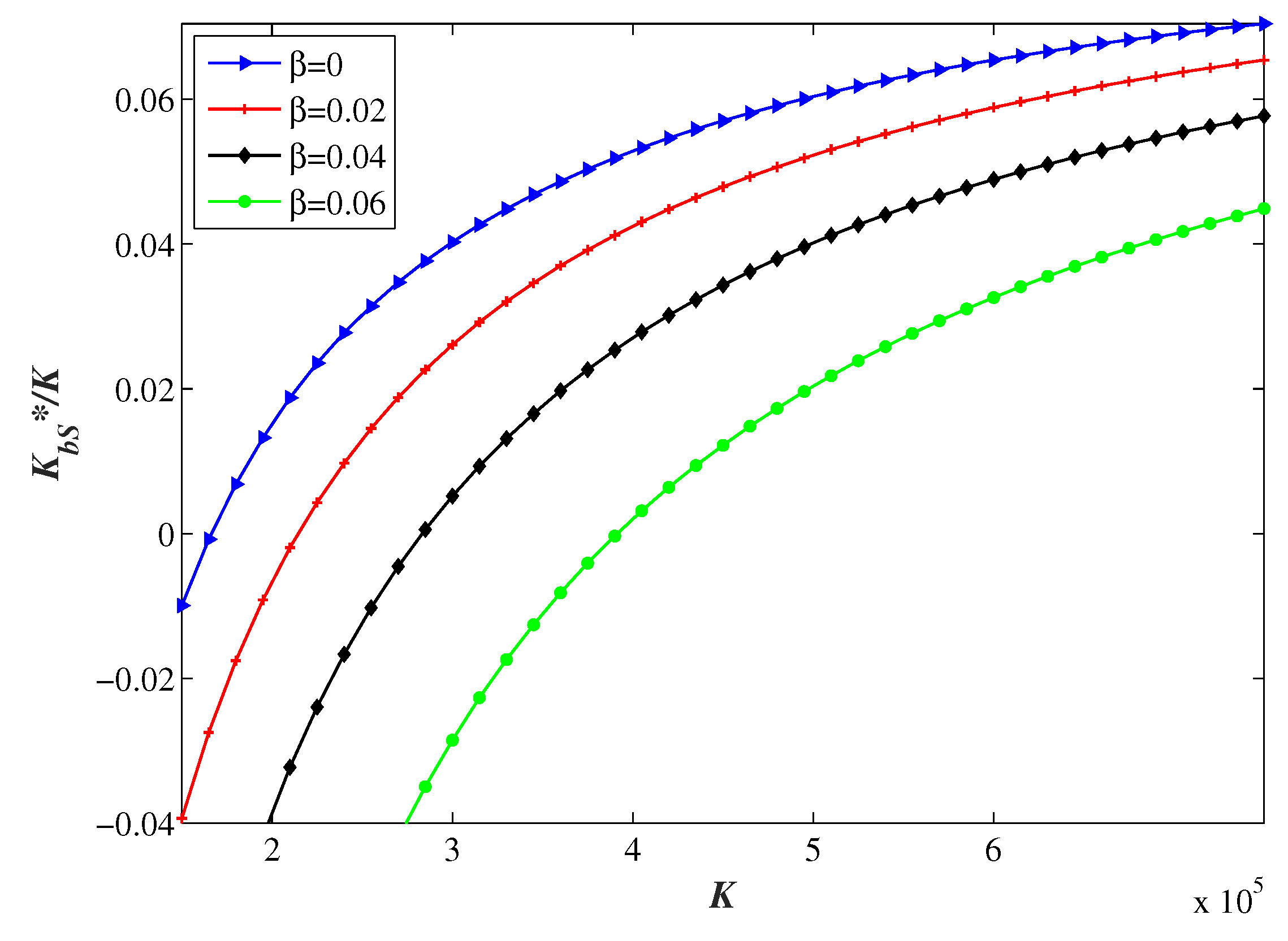
Finally, the relationship between
and total budget at different level of
, 0.02, 0.04, and 0.06 will be analyzed, where
,
,
,
, and
. The curve of
in
Figure 7 is actually the same as the red line in
Figure 4b when there is no information sharing, and
also increases with the total budget
K, which is consistent with the non-sharing result. Under the same budget, the increase in the benefited rate
makes the group more inclined to protect the headquarters system because the security information sharing will enhance virtually the security level of the branches, and thus the investment amount will be increased actually. Furthermore, at the zero point that the group begins to invest in branches’ security, the corresponding budget
K will increase with
, which is mainly because the group with a small budget expends all the funds for the security risk management of headquarters which stores all the information. Coupled with the virtual investment effect brought by security information sharing, the security investment budget will be allocated to branches only when the total security budget is larger.
The numerical analysis results suggest that sharing security information can bring the virtual investment to branches. In turn, the group can reduce the investment allocation to branches for the overall benefit when the budget is fixed, further highlighting the value of security investment in cybersecurity defense.
6. Discussion and Conclusions
In this paper, we built a mathematical model to study both theoretically and numerically the optimal allocation of security investment among the headquarters and its branches in a group under budget limitation. The relationships between various characteristics of investment environment and optimal security investment are considered, such as the proportion of branch’s information set, propagation probability, budget constraints, and intrinsic vulnerability. In addition, the influence of security information sharing on optimal allocation is also investigated numerically. First, we study the reallocation of security investment within a group considering the intra-group characteristics, for example, the systems among the headquarters and its branches are interconnected, and the headquarters stores all the information of the whole group, which is different from the previous studies on the optimal security investment between interconnection organizations. Second, this paper assumes that the interconnected headquarters and branches are heterogeneous with different importance levels to cybersecurity and are invested to varying degrees, which is more realistic than homogeneous assumption proposed in previous studies for simplifying processing. Third, our study introduces the benefited rate rather than the sharing portion to investigate the influence of security information sharing on investment allocation among the headquarters and branches, which will be propitious to arrange the limited budget for a higher security level.
The following findings and some insights into managerial practices of security investment have been summarized:
- (1)
Proposition 1 reveals that when the intrinsic vulnerability of the system is high and the total budgets are insufficient, the group will allocate all the budgets to protect cybersecurity of the headquarters. This is reasonable since the headquarters stores all the information of the group, and the data security of headquarters becomes a priority when the system security is poor. Therefore, the assessment of intrinsic vulnerability and security budget becomes obviously significant for the security of the whole group.
- (2)
Security investment of branch increases with the propagation probability, but the group will not allocate the budget to its branches when the propagation probability is low. This is to be expected since the mutual trust and authorization inevitably increases the likelihood of indirect breaches; the group will allocate more security funds to their branches as the propagation probability grows. Surprisingly, groups with a large number of branch firms are more likely to increase the investment of headquarters because it is difficult for them to protect the system security of many branches under the limited budget.
- (3)
The proportion of security investment allocated to each branch grows with total budget and propagation probability, but never exceed the level of . The higher the efficiency of investment, the lower the security budget of branches. This demonstrates that the security investment is efficient, and the group can transfer more security funds to headquarters, which indicates the importance of headquarters’ cybersecurity again. This finding reminds the group that, in response to the deteriorating cybersecurity situation, adequate security investment budgets should be prepared, and interconnectivity and exposure between systems should be monitored timely.
- (4)
The allocation of security investment on each branch decreases with the increase of intrinsic vulnerability, and a higher budget will improve the underinvestment caused by higher intrinsic vulnerability. This indicates that the more vulnerable the system is, the more the group needs to allocate security funds to headquarters where more information is stored. When the total budget is large, the underinvestment of branches can be improved.
- (5)
The numerical analysis results in extensions show that the higher benefited rate, the less investment is allocated to branches. Under a security information sharing case, the total budget required for branches allocated investment is greater than that without information sharing. This can be explained by the fact that security information sharing can indirectly offset part of security investment, which alleviates the group’s pressure on the security budget allocation to a certain extent.
There are also some limitations in our study. In general, cybersecurity involves two issues: defenses and attacks. This paper only discusses the information breach probability caused by an attacker from the perspective of defenders. In the future research, we will take the attackers’ strategies into consideration and further explores the offensive and defensive behaviors among them. In terms of the security information sharing mechanism, this paper only sets a benefit rate parameter to express. One can refer to some models of security knowledge sharing to make the research more detailed and perfect. For example, Safa et al. discussed the organizational support in the role of security knowledge sharing [
41] and He et al. adopted decision theory to discuss the costs involved in information sharing and cybersecurity [
42]. In addition, most studies have always followed the information breach function proposed by Gorden and Leob [
7], and one can also try to explore more realistic models instead.