Abstract
The Industrial Internet of Things (IIoT) integrates a wide range of devices and identities, making the protection of sensitive industrial data a critical challenge. However, existing centralized systems still face limitations such as single points of failure, inefficient identity authentication, and dependence on trusted third parties (TTPs). To address these issues, we present a blockchain-based authentication and data access control scheme for IIoT systems. The proposed scheme eliminates TTP involvement by employing decentralized identifiers (DIDs) and key-aggregate searchable encryption (KASE), utilizing scalable authentication without requiring all industrial data to be stored on the blockchain. Security robustness is demonstrated through informal analysis, the Real-or-Random (ROR) model, and the AVISPA simulation tool (v1.6). Furthermore, performance evaluation using the Multiprecision Integer and Rational Arithmetic Cryptographic Library (MIRACL) SDK shows that the proposed scheme achieves computational efficiency compared with existing solutions. Overall, the results confirm that the proposed scheme provides secure, efficient, scalable, and TTP-free data management for IIoT environments.
MSC:
68-XX; 94Axx; 94A62; 68Mxx
1. Introduction
The Industrial Internet of Things (IIoT) constitutes a large-scale ecosystem in which heterogeneous devices interconnect to exchange data and collaborate for intelligent decision-making. It was projected that by 2020, more than 25 billion smart devices would be deployed worldwide [1]. Such rapid growth, however, imposes substantial burdens on existing infrastructures, particularly in terms of computation, storage, and security. To mitigate these limitations, the integration of IIoT with cloud computing has been extensively explored, leveraging the cloud’s virtually unlimited computational and storage resources.
Cloud-assisted IIoT systems are envisioned to underpin critical infrastructures such as smart manufacturing, intelligent transportation, and advanced energy systems. These systems depend on massive volumes of industrial data to enable analytics-driven operations. However, the geographical separation between centralized cloud servers (CSs) and edge devices introduces latency, limiting their effectiveness in delay-sensitive and mobile applications. Fog computing has thus been introduced as a complementary paradigm that extends cloud capabilities to the network edge [2]. By deploying fog nodes between CSs and end devices, data can be preprocessed and temporarily stored closer to its source, thereby reducing latency and improving overall system efficiency compared with the traditional device–cloud model.
In cloud-assisted IIoT systems, data sharing typically involves multiple categories of industrial information distributed among various organizations and individuals. For example, a smart factory gathers production, environmental, and energy data through gateway nodes and grants selective access to external parties. Specifically, production and energy data may be shared with the energy management provider, whereas production and environmental data may be disclosed to the quality inspection department. While such fine-grained sharing enhances collaboration and decision-making, it simultaneously heightens the risk of data breaches. To address these concerns, searchable encryption (SE) [3,4] has been adopted to enable secure keyword searches over encrypted datasets [5,6,7,8]. Nonetheless, managing multiple data categories across different entities requires numerous encryption keys, resulting in high communication and storage overhead for secure distribution and maintenance. To alleviate this issue, key-aggregate searchable encryption (KASE) [9] has been introduced and further advanced in subsequent studies [10,11]. As illustrated in Figure 1, with KASE, a factory can distribute a single aggregate key to each authorized user, thereby streamlining key management and enabling a single trapdoor to retrieve multiple classes of data.
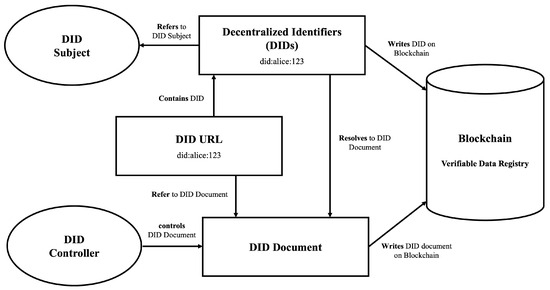
Figure 1.
DID architecture.
In parallel, blockchain technology has emerged as a promising solution due to its decentralization, immutability, and capability to enable trustless interactions without reliance on trusted third parties (TTPs) [12]. Nonetheless, cloud-assisted infrastructures remain vulnerable to adversarial attacks seeking to exploit inherent weaknesses [13]. Furthermore, most existing protocols continue to rely on trusted authorities, reintroducing centralization and associated risks such as performance bottlenecks, privacy leakage, and single points of failure. In cloud-assisted IIoT, these dependencies extend beyond data management to include user identity and access rights, which are often still governed by TTPs.
To overcome these challenges, recent studies have explored decentralized schemes that eliminate reliance on TTPs. For example, attribute-based encryption (ABE) [14] combined with blockchain supports fine-grained access control. However, such schemes remain only partially decentralized, as they still require a TTP for private key issuance and policy management, thereby exposing systems to insider threats and privacy risks. More recently, decentralized identifiers (DIDs) [15] have been proposed as a promising alternative for privacy-preserving identity management. DIDs enable devices to autonomously generate and manage their identifiers and cryptographic keys without TTP involvement, thus achieving verifiable and self-sovereign identity in distributed settings.
In this work, we propose a blockchain-enabled authentication and access control framework tailored for IIoT environments. The scheme integrates DIDs and KASE to eliminate reliance on centralized authorities for identity management, enhance self-sovereign identity, and achieve scalable, fine-grained access control. The proposed design ensures secure, efficient, and resilient authentication, thereby addressing the stringent requirements of next-generation industrial infrastructures.
1.1. Motivations
Cloud/Fog-assisted IIoT environments must support secure and efficient sharing of heterogeneous industrial data. Existing solutions introduce significant key management overhead and still rely on TTPs. This reliance creates centralization risks, privacy leakage, and single points of failure. Blockchain-based schemes attempt to reduce trust dependence, but many of them keep identity issuance and authentication under centralized control. In addition, these schemes often utilize static identity information, which increases exposure to linkability attacks and replay attacks. Furthermore, current data access control mechanisms are often insufficient for multi-category industrial data, and many existing models lack the ability to support fine-grained access policies across diverse entities in IIoT settings. These issues demonstrate the need for a decentralized authentication and access control scheme that can simplify key management for multi-category data, provide self-sovereign and privacy-preserving identity control without TTPs, and support fine-grained and flexible access control. Motivated by these requirements, this work combines DIDs and KASE within a blockchain-supported scheme to offer scalable, resilient, and fine-grained authentication and access control in Fog-assisted IIoT systems.
1.2. Contributions
The main contributions of this work can be summarized as follows:
- We present a decentralized protocol for authentication and access control in cloud-assisted IIoT environments. To guarantee scalability and strong security for participating nodes, the scheme employs DIDs and KASE. Our scheme addresses the challenges of TTP dependence, achieves efficient key management, and supports fine-grained access control in industrial data sharing.
- Within the proposed scheme, the data owner, data user, and fog node reveal only a minimal portion of personal information when exchanging messages over public networks. Each entity is capable of independently creating and maintaining its identity, along with corresponding public and private keys. Importantly, during the authentication process among the data owner, data user, and fog node, all session-related parameters are renewed in every session, with the exception of the user’s DID. These features mitigate the vulnerabilities associated with static identifiers and reduce exposure to linkability and replay attacks.
- The security guarantees of the proposed scheme are examined through a series of evaluations, including informal analysis, the Real-or-Random (ROR) model [16], and formal verification conducted using the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool [17]. These analyses demonstrate that the protocol remains secure even without any TTP involvement and confirm its robustness against a wide range of attacks.
- To analyze performance of our scheme, we measure and compare the computational costs of the proposed protocol against existing schemes. The cryptographic operations are implemented and tested using the Multiprecision Integer and Rational Arithmetic Cryptographic Library (MIRACL) SDK [18]. The results demonstrate that the protocol maintains practical efficiency while providing enhanced decentralization and stronger protection against the potential attacks.
1.3. Organization
The remainder of this paper is structured as follows. Section 2 reviews the existing state-of-the-art solutions. The preliminaries and threat model are discussed in Section 3. Section 4 details the proposed scheme, followed by a comprehensive security analysis in Section 5. Section 6 presents experimental results for cryptographic primitives, and compares the proposed scheme with related works. Finally, Section 7 concludes the paper.
2. Related Works
Over the past decade, a wide range of privacy-preserving schemes have been introduced to safeguard user data and privacy within IoT and IIoT ecosystems. Shuai et al. [19] presented a mechanism that protects sensitive data collected from industrial sensors against unauthorized access. Their approach employs Rabin cryptography as the core primitive and integrates password verification tables, aiming to balance security with computational efficiency. Srinivas et al. [20] proposed a lightweight solution supported by both formal and informal security analyses. Their system incorporates a fuzzy extractor for biometric verification, with performance validated through NS2 simulation. This design facilitates interoperability and provides users with remote control of smart home devices via Internet-enabled mobile platforms. Wazid et al. [21] designed a three-factor authentication protocol tailored for smart home environments. A registration server is utilized to manage entity enrollment and key distribution, functioning as a central server in cloud-based IoT. Their model supports authentication among users, gateways, IoT devices, and cloud servers, although the registration server primarily acts as a registrar.
Banerjee et al. [22] introduced an ABE system for privacy-preserving data protection, while Mubarakali [23] proposed a blockchain-enabled system for personal health record sharing, using attribute-based tokens to regulate access among healthcare and insurance entities. Despite their privacy benefits, both approaches depend on centralized infrastructures, which remain susceptible to single points of failure. Park and Park [24] proposed a blockchain-based privacy-preserving scheme for IoT environments, validated through testbed implementation and evaluated under the “Dolev–Yao (DY) model” adversarial model [25]. Their framework enables authentication and data sharing between data owners and users without relying on a TTP. However, the scheme employs ABE, which requires re-encryption whenever new ciphertexts are generated, which leads to additional computational overhead. Eddine et al. [26] proposed a blockchain-based security architecture for the Internet of Vehicles. While computational and communication metrics were shown to be efficient, the scheme fails to guarantee anonymity and is vulnerable to attacks such as DoS, insider threats, and device theft. Moreover, it lacks scalability features such as dynamic node addition. Tomar and Tripathi [27] introduced an ECC-based protocol for fog-enabled vehicular networks, which demonstrates low computational and communication costs. However, the scheme does not resist common attacks and similarly lacks support for dynamic scalability. Zhang et al. [28] combined ciphertext-policy attribute-based keyword search (CP-ABKS) with blockchain to provide searchable encryption, integrity verification, and auditing. Despite these advantages, ABE-based solutions often encounter challenges with re-encryption overhead and key management, particularly in large-scale deployments. Jia et al. [29] proposed an ECC-based protocol for IoT healthcare applications that ensures anonymity and untraceability but remains vulnerable to insider, DoS, and offline guessing attacks, with no scalability support. Karankar and Seth [30] proposed an ABE-based access control scheme for IoT. However, their scheme also suffers from the drawback that the entire ciphertext must be re-encrypted whenever the access policy is updated.
Niu et al. [10] introduced a KASE-based blockchain scheme for PHR sharing, yet it lacked secure mutual authentication and multi-keyword search. More recently, Trivedi and Patel [31] developed a KASE-based protocol for distributed IoT healthcare, where only authorized medical data users could query encrypted data using attribute tokens. Guo et al. [32] presented a lightweight remote authentication protocol using pseudo-identities to ensure anonymity in IoT environments. However, their scheme does not incorporate blockchain features and lacks essential functionalities such as dynamic node addition and password update. Vangala et al. [33] designed a blockchain-based authenticated key agreement protocol for precision agriculture, which proved resilient against several attacks in real-world evaluations, though scalability remains limited. Likewise, Ponnuru et al. [34] proposed a blockchain-oriented authentication mechanism for fog-assisted IIoT, but their solution still depends on a trusted third party to manage user identities and private keys. Lee et al. [35] proposed a blockchain-based KASE scheme for medical IoT to support multi-delegation. However, their scheme does not support decentralized identity and is not suitable for deployment in fog computing environments.
A summary of existing authentication and data access schemes for cloud/fog-assisted IIoT environments is provided in Table 1.

Table 1.
Comparison of previous schemes in IIoT environments.
3. Preliminaries
3.1. Decentralized Identifiers
Decentralized Identifiers (DIDs) [15] serve as unique identifiers for entities by leveraging distributed ledger technologies, without reliance on centralized authorities. Within the DID ecosystem, three key roles exist: issuers (e.g., government agencies) that generate verifiable credentials, holders who maintain these credentials in digital wallets, and verifiers responsible for validating their authenticity. The interactions among these roles and the corresponding information flows are illustrated in Figure 1.
As shown in Figure 1, the DID architecture is built upon DID Documents [15], which contain cryptographic materials, verification methods, and service endpoints used to interact with the entity represented by the DID. A DID consists of a method and a method-specific identifier that designates the DID subject, which may be a person, device, organization, or software system. The DID controller is the entity authorized to modify the DID Document, typically through possession of the relevant cryptographic keys, and the controller may or may not be identical to the DID subject. A DID URL extends the basic DID syntax by including path, query, or fragment components, enabling the precise identification of specific resources—such as a public key or service endpoint—either within the DID Document or external to it. DID Methods define the procedures for creating, resolving, updating, and deactivating DIDs and DID Documents on a verifiable data registry, such as a blockchain or decentralized storage network. DID resolvers use the corresponding DID Method to retrieve DID Documents through DID resolution, while DID URL dereferencers fetch the specific resource indicated by a DID URL. These components also form a unified and interoperable system that supports decentralized, verifiable, and fine-grained identity management across heterogeneous environment.
3.2. Threat Model
We evaluate the security of the proposed scheme using the “Dolev–Yao (DY) model” [25], which is commonly adopted for rigorous protocol analysis. In this setting, all communications are assumed to traverse untrusted channels, giving an adversary extensive control over the network. Under these assumptions, the adversary can monitor, block, or store transmitted messages, as well as manipulate their contents, fabricate new ones, and insert malicious data into ongoing exchanges.
3.3. Mathematical Preliminaries
We have outlined several mathematical definitions and cryptographic primitives to facilitate readers’ understanding of the proposed approach. The scheme is constructed on elliptic curve cryptography (ECC) and its security relies on the hardness of the elliptic curve discrete logarithm problem (ECDLP) and the elliptic curve decisional Diffie–Hellman problem (ECDDHP). Utilizing these computational assumptions, we provide a formal analysis to demonstrate the security of the proposed scheme.
Elliptic Curve Cryptography
Elliptic curve cryptography (ECC) is a public-key cryptographic scheme that employs the algebraic properties of elliptic curves to achieve security. To apply ECC in a security setting, one must first choose a large finite field , a large prime p, another prime q, and elliptic curve parameters w and v. Based on these parameters, an elliptic curve is defined as , subject to the condition . The points on this curve form an additive group, for which a base point P is specified. For an integer , scalar multiplication is expressed as:
The cryptographic strength of ECC relies on the intractability of the following problems:
- Elliptic Curve Discrete Logarithm (ECDL) Problem: Determine given .
- Elliptic Curve Decisional Diffie–Hellman (ECDDH) Problem: Given n, s, and t, decide whether .
- Elliptic Curve Computational Diffie–Hellman (ECCDH) Problem: Compute given and .
3.4. Bilinear Pairing
Bilinear maps constitute a fundamental building block of pairing-based cryptography, which underlies schemes such as identity-based encryption [36] and KASE [9]. Consider two cyclic groups and of prime order p, and let g be a generator of . A bilinear map is defined as a function that satisfies the following conditions:
- (1)
- Bilinearity: For all and , .
- (2)
- Non-degeneracy: .
When both the group operation in and the evaluation of e can be performed efficiently, the pair is termed a bilinear group.
4. Proposed Scheme
In this section, we describe the system model and access control workflow of the proposed scheme. The primary objective is to enable patients to manage and share their data securely in a real-time and a self-sovereign manner. IIoT data are stored on fog nodes, while the big data center collects only metadata required for analytical purposes rather than the raw data itself. The notations used throughout this paper are summarized in Table 2.

Table 2.
Notations for our scheme.
4.1. System Model
We begin by outlining the system model, as shown in Figure 2. The architecture is composed of four primary entities: the data user (DU), the data owner (DO), the fog node (FN), and the big data center (BDC).
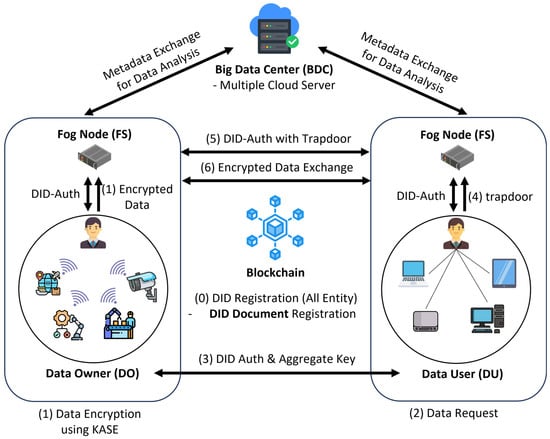
Figure 2.
System model.
- Big data center (): The is composed of multiple cloud servers and analytical tools, which receive data from fog nodes to perform large-scale processing. Data uploaded from the IoT network is analyzed within the and subsequently utilized to provide requested services to users. This hierarchical architecture supports efficient and secure management of IoT data in fog-enabled systems.
- Fog node (): Each FN is responsible for managing a single IoT network, while interconnected collectively form a resilient fog-enabled infrastructure. This infrastructure enables secure data processing and facilitates data sharing. Data collected from IoT devices are transmitted to the BDC upon request for advanced services.
- Data owner (): The serves as a domain administrator, responsible for collecting data from IIoT devices deployed in designated areas to capture and deliver real-time information to data users. Each device is associated with a data owner who oversees the IoT network and supports scalability by managing the integration of new devices. Acting as the IIoT device owner, the establishes the connection between the IoT network and the FN.
- Data user (): The refers to a domain administrator in another network domain who requests access to data managed by the and utilizes the shared data within their own domain.
The communication flow of the proposed scheme can be described as follows:
- S1:
- Both the and the generate their respective DIDs and perform DID-based authentication with their associated FN to initiate IIoT service access. Once the authentication is completed, the encrypts the IIoT data and uploads it to the .
- S2:
- When the intends to access the IIoT data of the , it sends a data request message to the DO and performs DID authentication. After successful authentication, the issues and transmits an aggregate key corresponding to the requested data to the .
- S3:
- To retrieve the encrypted data, the generates a trapdoor and forwards it to its . The then communicates with the ’s domain and performs DID authentication. Upon successful verification, the requested encrypted data is transferred to the ’s FN and subsequently decrypted. The then receives the encrypted data, decrypts it using the aggregate key, and utilizes the retrieved information within its own IIoT domain.
4.2. Initialization Phase
In this initialization phase, the , , and generate their respective parameters required for subsequent operations. Once these parameters are produced, they are recorded on the blockchain to enable the next phase. The initialization procedure is identical for the , , and .
- S1:
- The begins by constructing a bilinear group of prime order q, an elliptic curve , and defining a non-degenerate bilinear map . The also specifies the maximum number of documents n with indices , selects a generator , a random secret , and a cryptograhpic hash function .
- S2:
- The first creates its decentralized identifier and then computes for every . A polynomial of degree is subsequently constructed. In addition, the generates two distinct key pairs: , which is used for authentication, and , which is employed for data sharing. Each key pair includes a secret key and its associated public key.
- S3:
- Finally, the publishes the document on the blockchain.
4.3. Registration Phase
To join the proposed network, both the and undergo a registration phase by performing DID-based authentication with their respective s. Through this process, each of them establishes a pre-shared key with the in its domain. The registration procedure of the is identical to that of the DU and proceeds as follows:
- S1:
- The begins the process by generating a random nonce and sending a registration request, which includes , to through a secure communication channel.
- S2:
- Upon reception, resolves the on-chain DID document to obtain the public parameters together with . It then creates a challenge and transmits it back to the via the secure channel.
- S3:
- Once the challenge is received, the computes and , and subsequently returns the tuple to .
- S4:
- then verifies the response by checking the equality . If the condition holds, both entities compute the shared session key, where the derives and derives .
4.4. Data Upload Phase
Once the initialization phase is completed, the proceeds to encrypt the data before uploading it to the . The detailed steps are as follows:
- S1:
- The chooses a random value and generates the public parameters for each index i, represented as for . These values are computed as , , and . The data index value is then derived as .
- S2:
- The encrypts the data using the pre-shared session key . Finally, the encrypted data are uploaded by the to the .
4.5. Data Request and Aggregate Key Sharing Phase
To initiate the data access phase, the issues a request to the to obtain the aggregate key. Upon confirming the validity of the request, the delegates authorization to to handle subsequent access control procedures. The detailed process of this phase is outlined below.
- S1:
- The begins by generating a random nonce and a challenge value . It then computes and transmits the tuple to the .
- S2:
- Upon receiving the message, the selects a random nonce and generates a challenge . It retrieves the public key of the from its DID document stored on the blockchain. Subsequently, the computes , , and . It then derives the session key and computes the aggregate key as . The aggregate key is encrypted using the session key to obtain . Finally, the sends to the .
- S3:
- Upon receiving the response, retrieves the ’s public key from the DID document recorded on the blockchain. It then constructs and verifies the validity of the received message by checking whether . If it is hold, the computes the session key as and decrypts using this session key to recover the aggregate key . Finally, the securely stores for use in subsequent data access operations.
4.6. Fog-Enabled Data Sharing Phase
The initiates a data access request to its domain-specific fog node . During this process, the communicates with using their established pre-shared key and transmits the corresponding trapdoor. Subsequently, the fog node in the ’s domain performs DID-based authentication with . Upon successful verification, shares the requested encrypted data with based on the received trapdoor information.
- S1:
- selects the random number and computes , , and the trapdoor . Subsequently, is encrypted using pre-shared key and transmitted to .
- S2:
- Upon receiving the message, decrypts it using to obtain . It verifies the correctness of the message by checking . If the verification succeeds, generates a random value and challenge , computes , and sends to .
- S3:
- After receiving the request, generates a random number and challenge , computes , , and . It then derives the session key . and transmits to .
- S4:
- Upon receiving the response, retrieves the ’s public key from the blockchain and computes . It verifies whether . If valid, it derives the session key . , encrypt the trapdoor using , and forwards it to .
- S5:
- After decrypting using , computes , , , and . It then verifies the data index by checking . Finally, encrypts using the session key and forwards it to .
- S6:
- decrypts using , and re-encrypts them with the session key , and transmit the result to the . Upon decryption, the recovers the data D as .
Correctness of Data Decryption
Proof.
□
- S1:
- We begin with the expression and substitute the definition of . The expression then becomes
- S2:
- Using the bilinearity property of the pairing, specifically we combine the two pairings involving as follows:This transformation merges structurally related factors and prepares the expression for substitution of the explicit form of .
- S3:
- We expand the internal product according to the ciphertext definition:This step makes explicit the dependency of the expression on the structural index sets associated with the ciphertext components.
- S4:
- Exploiting the multiplicative distributivity of the pairing, we distribute the pairing over all factors in both numerator and denominator:
- S5:
- Rearranging symmetric terms and isolating cancellable components, we obtainwhere duplicated factors in the distributed pairings have been consolidated.
- S6:
- We substitute the definition of the ciphertext component obtaining
- S7:
- Finally, we complete the derivation by canceling the symmetric pairing terms. The bilinear map satisfies . This rule implies Both terms appear in opposite positions in the expression. As a result, they cancel. The entire expression then reduces to
5. Security Analysis
In this section, we evaluate the security strength of the proposed protocol through multiple analyses, including informal reasoning, the ROR model [16], and formal verification using the AVISPA tool [17].
5.1. ROR Model
In most authentication protocols, each entity verifies the legitimacy of its communication partner and establishes a shared session key. To assess the security of this session key, the ROR model [16] is employed. This model enables the evaluation of a protocol’s resistance against both passive and active adversarial behaviors. Specifically, the adversary interacts with instantiated participants through a series of games and attempts to distinguish between a random nonce and a real session key using a test query.
To formally analyze session key security under the ROR model, we define the participating entities, the adversary , and the corresponding query operations. In particular, we focus our formal security analysis on the key agreement and aggregate key sharing processes between the and . This analysis involves two entities: data owner and data user , where i represent specific instance of each participants. The adversary is assumed to have full control over public communication channels, with the capability to intercept, modify, delete, and replay transmitted messages. Based on these capabilities, can perform the following types of queries:
- : This query models a passive attack, in which the adversary eavesdrops on the message exchanges between and over an insecure public channel. The can record all transmitted data without altering any message content.
- : This query represents an active attack, allowing to inject crafted messages into an oracle session and observe the resulting responses. This enables to attempt to manipulate or replay protocol messages.
- : This query initiates the security experiment. A fair coin is flipped to determine the response. If the session key shared between and is considered fresh, then receives a random value when , and the actual when . If the freshness condition is not met, the oracle returns ⊥.
ROR Proof
In accordance with the ECDDHP and ECDLP previously defined in Section Elliptic Curve Cryptography, this game is executed to prove the Theorem 1 presented below and to confirm the session key security of the proposed scheme.
Theorem 1.
Assume that is an adversary operating within polynomial time t against our scheme P. Then, ’s advantage in violating the semantic security of P is expressed as:
Here, and correspond to the number of hash and send queries issued by the adversary, respectively. The function denotes the range of a collision-resistant hash function H, while represents the success probability of in solving the ECDDHP within polynomial time t.
Proof.
The proof proceeds through a sequence of four games, , where denotes the event that the adversary wins the corresponding game. The formal reasoning for each game is detailed below.
- Game : The initial game, denoted as , models the real interaction between the adversary and the our protocol. A random bit c is chosen at the beginning of the game, and the corresponding winning advantage of is computed as:
- Game : In this game, denoted , the adversary passively eavesdrops on all communications within our scheme using the query. It then invokes to decide whether the returned value represents the true session key or a random bitstring. The session key , computed as and , can only be derived by obtaining the secret keys of both and , which is infeasible under the ECDDHP assumption. Therefore, ’s advantage in this game satisfies the bound:
- Game : Game represents an active attack in which the adversary interacts with the system by issuing and queries. In this phase, attempts to impersonate a legitimate participant ( or ) by manipulating multiple queries. However, is unable to derive the participants’ secret keys or the random value , since both rely on the hardness of the ECDDHP and ECDLP problems. Moreover, due to the collision resistance of the hash function, cannot produce a valid hash collision within polynomial time. Consequently, by applying the birthday paradox, the adversary’s advantage can be expressed as follows:
- Game : The final game, denoted , simulates an extended active attack scenario. Similarly to the conditions in Game , must recover both and to reconstruct the correct session key . Nevertheless, even after executing the eavesdropping attack, distinguishing these keys from or , would require solving the ECDDHP. As this problem remains computationally infeasible, cannot obtain the valid session key, implying that
Once all four games () have been executed, ’s final task is to determine the correct value of the bit c. Given this setting, the advantage of in distinguishing the real session key from a random one is given by
Using the triangular inequality along with Equations (3)–(5), the following conclusion can be drawn:
Subsequently, multiplying both sides of Equation (7) by 2 provides the final result.
□
5.2. Informal Analysis
5.2.1. Impersonation Attacks
In an impersonation attack, an adversary attempts to masquerade as a legitimate DO or DU to gain unauthorized access to the DO’s data. However, such an attack is infeasible in our scheme, as the adversary is unable to derive the shared key , which relies on secret values accessible only to legitimate participants. Obtaining a valid secret key would require solving the ECDDHP, while deriving valid authentication parameters would involve computing the proof values , . As these depend on private random values, such computations are infeasible, ensuring robustness against impersonation attacks.
5.2.2. Replay Attacks
A replay attack occurs when an adversary intercepts and re-transmits valid messages to gain data access. Our scheme prevents such attacks by including random number in important verification messages to verify freshness. Even if attempts to reuse previous messages, it would need to derive the shared key , the random number , and the secret key , which is infeasible. Therefore, the proposed scheme remains secure against replay attacks.
5.2.3. Man-in-the-Middle Attacks
Section 5.2.1 shows that the adversary cannot derive the shared key or the proof parameters , , without solving the ECDDHP. As a result, is unable to reconstruct valid verification parameters or impersonate legitimate entities. Consequently, the proposed scheme is resistant to man-in-the-middle attacks.
5.2.4. Privileged Insider Attacks
This attack arises when a associated with a TTP attempts to compromise the confidentiality of data belonging to the or . In the proposed scheme, no centralized TTP is involved in managing the entities’ key pairs, owing to the DIDs. Each participant independently generates, maintains, and controls its own private credentials. Consequently, the absence of centralized key management effectively eliminates insider privileges, making the scheme inherently resilient against privileged insider attacks.
5.2.5. Fine-Grained Control and Self-Sovereignty
In the proposed scheme, the and initializes system parameters independently of any TTP. Data is secured using KASE, with ciphertexts maintained in the . The KASE mechanism enables flexible ciphertext updates and single-key decryption across multiple datasets. Because users locally create their own key pairs, the design eliminates reliance on a key generation center or central trust body, ensuring decentralized, fine-grained, and self-sovereign access management.
5.2.6. Providing Password Update Mechanism
In the proposed scheme, entities do not need to request assistance from a TTP to update their secret keys. Each participant can independently renew its key pair and corresponding public parameters by updating the associated public/private key entries within its own DID document on the blockchain.
5.2.7. Secure Mutual Authentication
Section 5.2.1, Section 5.2.2 and Section 5.2.3 demonstrate that deriving secret parameters is computationally infeasible for an adversary without solving the ECDDHP. In the data request and aggregate key sharing process, the and derive session keys and based on the intractability of the ECDLP and ECDDHP. Consequently, the proposed scheme guarantees secure mutual authentication.
5.3. Formal Security Verification Using AVISPA
In this section, the proposed scheme is implemented and verified using the AVISPA tool [17], an AVISPA-based formal analysis extensively adopted in cryptographic protocol research. AVISPA evaluates the robustness of security schemes, focusing on their resistance to replay and man-in-the-middle attacks. Protocols are first described using the High-Level Protocol Specification Language (HLPSL) [37] and automatically converted into an Intermediate Format (IF) by the HLPSL2IF translator. The generated IF model is analyzed through one of four verification engines—OFMC [38], CL-AtSe [39], SATMC [40], or TA4SP [41]. Each backend provides an independent simulation report verifying the security soundness of the proposed protocol.
Simulation Results
As shown in Figure 3 and Figure 4, the OFMC and CL-AtSe backends report consistent verification results. The analysis confirms that the proposed – aggregate key sharing process withstands potential replay and man-in-the-middle attacks within the specified threat models [42].
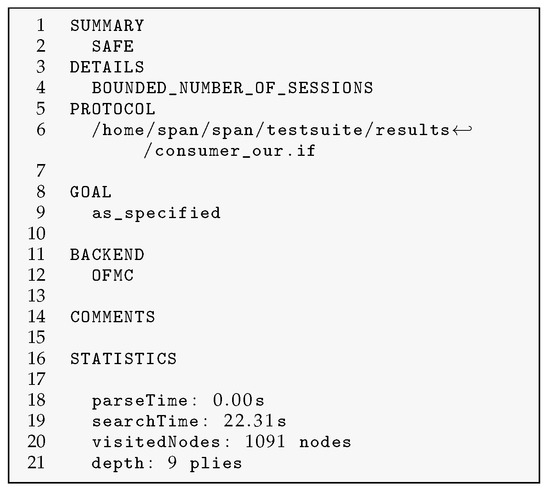
Figure 3.
Result of OFMC.
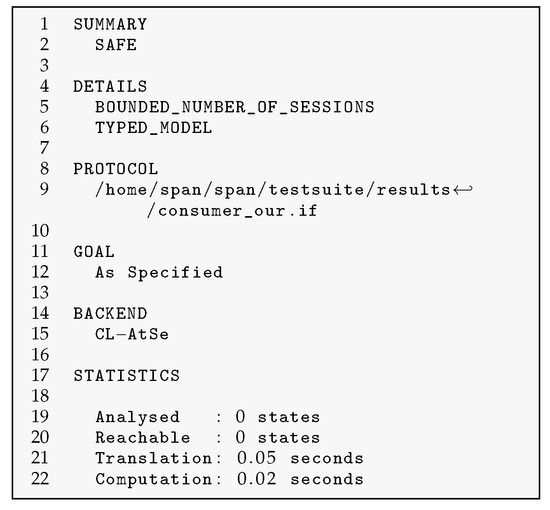
Figure 4.
Result of CLAtSe.
6. Comparative Analysis
In this section, we compare the performance and security features of our scheme with those of recent schemes in [10,31,32,33,34].
Limitations: This study aims to design a theoretically sound security protocol applicable to real-world industrial environments. However, implementing and testing the proposed scheme in a full-scale system equipped with an actual fog computing infrastructure remains challenging due to practical constraints such as resource availability and deployment cost. Therefore, the experimental evaluation was conducted in a controlled testbed environment using a Raspberry Pi platform, which serves as a lightweight representative model for mobile or edge devices. While this setup effectively validates the feasibility and performance of the proposed scheme, further large-scale deployment and real-world verification will be pursued in future work.
6.1. Security Features
Table 3 presents a summary of the security features of the proposed scheme alongside existing schemes [10,31,32,33,34]. Earlier studies overlook several vital security aspects; however, the proposed scheme successfully meets all major security objectives while maintaining decentralization and supporting fine-grained access control without the need for a TTP.

Table 3.
Security features comparison.
6.2. Computational Cost
The performance evaluation was conducted on a Raspberry Pi 4B platform equipped with a 64-bit quad-core 1.5 GHz processor, 8 GB memory, and Ubuntu 20.04.2 LTS. The MIRACL [18] cryptographic library was employed to implement the proposed scheme. This configuration enabled direct measurement of computational overhead and facilitated comparison with previously proposed schemes.
The metrics , , , , , and represent the mean execution times for hashing, scalar point multiplication and addition, bilinear pairing, modular exponentiation, and PUF operations, respectively. Each cryptographic primitive was executed 100 times to obtain reliable averages. Table 4 summarizes the computational requirements, and Table 5 reports the comparative evaluation results.

Table 4.
Performance evaluation—computation cost.

Table 5.
Comparative Analysis—Computational Cost.
The assessment involves three major operational phases: (1) data encryption and upload conducted by the , (2) search and ciphertext retrieval performed by the or server, and (3) decryption by the . The parameters m, , and indicate the total number of indices generated, search results obtained, and ciphertexts decrypted, respectively.
For comparison with existing fog-assisted schemes that do not adopt KASE, the computation performed by users was treated as data encryption and upload, the fog node’s intermediary tasks were regarded as data sharing, and the server’s operations were considered as data decryption when estimating total computational overhead.
While the proposed scheme incurs slightly higher computational cost than prior schemes, it achieves broader and more robust security guarantees. Schemes such as those by Guo et al. [32], Vangala et al. [33], and Ponnuru et al. [34] lack fine-grained access control and formal analysis, whereas Niu et al. [10] and Trivedi and Patel [31] do not support decentralization. Moreover, none of the previous schemes preserve data self-sovereignty. In KASE-based approaches, the computational cost varies depending on the number of keywords associated with the requested data; as the number of keywords increases, the computation overhead also grows. However, schemes that do not adopt KASE cannot achieve the same level of fine-grained and flexible data access control. Thus, our scheme attains comprehensive security while ensuring decentralized operation and self-sovereign data management.
7. Conclusions
The proposed integration allows data owners, data users, and fog nodes to independently manage their identities and cryptographic credentials without reliance on a TTP. Security verification through informal analysis, the Real-or-Random model, and the AVISPA tool confirmed resistance to major network attacks, including replay, impersonation, and man-in-the-middle scenarios. Moreover, implementation results using the MIRACL library demonstrate that the proposed scheme achieves strong security with only moderate computational overhead compared with existing methods. Overall, the proposed scheme achieves secure authentication, fine-grained access control, and data self-sovereignty for industrial IoT networks. The proposed scheme provides a promising foundation for building scalable and trustworthy IIoT infrastructures in next-generation industrial ecosystems.
Funding
This research received no external funding.
Data Availability Statement
No new data were created or analyzed in this study.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. Integration of cloud computing and Internet of Things: A survey. Future Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on fog computing: Architecture, key technologies, applications and open issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the IEEE Symposium on Security and Privacy 2025, Berkeley, CA, USA, 14–17 May 2020; IEEE Computer Societ: Washington, DC, USA, 2000; pp. 44–55. [Google Scholar]
- Boneh, D.; Di Crescenzo, G.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 506–522. [Google Scholar]
- Li, J.; Lin, X.; Zhang, Y.; Han, J. KSF-OABE: Outsourced attributebased encryption with keyword search function for cloud storage. IEEE Trans. Serv. Comput. 2017, 10, 715–725. [Google Scholar] [CrossRef]
- Hoang, T.; Yavuz, A.A.; Guajardo, J. A secure searchable encryption framework for privacy-critical cloud storage services. IEEE Trans. Serv. Comput. 2021, 14, 1675–1689. [Google Scholar] [CrossRef]
- Yin, H.; Zhang, W.; Deng, H.; Qin, Z.; Li, K. An attribute-based searchable encryption scheme for cloud-assisted IIoT. IEEE Internet Things J. 2023, 10, 11014–11023. [Google Scholar] [CrossRef]
- Gao, H.; Huang, H.; Xue, L.; Xiao, F.; Li, Q. Blockchain-enabled finegrained searchable encryption with cloud–edge computing for electronic health records sharing. IEEE Internet Things J. 2023, 10, 18414–18425. [Google Scholar] [CrossRef]
- Cui, B.; Liu, Z.; Wang, L. Key-aggregate searchable encryption for group data sharing via cloud storage. IEEE Trans. Comput. 2016, 65, 2374–2385. [Google Scholar] [CrossRef]
- Niu, J.; Li, X.; Gao, J.; Han, Y. Blockchain-based anti-key-leakage key aggregation searchable encryption for IoT. IEEE Internet Things J. 2020, 7, 1502–1518. [Google Scholar] [CrossRef]
- Liu, Z.; Li, T.; Li, P.; Jia, C.; Li, J. Verifiable searchable encryption with aggregate keys for data sharing system. Future Gener. Comput. Syst. 2018, 78, 778–788. [Google Scholar] [CrossRef]
- Rajasekaran, A.S.; Azees, M.; Al-Turjman, F. A comprehensive survey on blockchain technology. Sustain. Energy Technol. Assess. 2022, 52, 102039. [Google Scholar] [CrossRef]
- Babu, P.R.; Palaniswamy, B.; Reddy, A.G.; Odelu, V.; Kim, H.S. A survey on security challenges and protocols of electric vehicle dynamic charging system. Secur. Privacy 2022, 5, e210. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; IEEE Computer Societ: Washington, DC, USA, 2007; pp. 321–334. [Google Scholar]
- Sporny, M.; Longley, D.; Sabadello, M.; Reedm, D.; Steele, O.; Allen, C. Decentralized Identifiers (DIDs) v1.1, W3C Proposed Recommendation, July 2025. Available online: https://www.w3.org/TR/did-1.1/ (accessed on 3 September 2025).
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Public Key Cryptography—PKC 2005, Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Automated Validation of Internet Security Protocols and Applications. Available online: https://people.irisa.fr/Thomas.Genet/span/ (accessed on 3 September 2025).
- MIRACL Cryptographic SDK. Available online: https://github.com/miracl/MIRACL (accessed on 19 August 2025).
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. A secure authentication scheme with forward secrecy for Industrial Internet of Things using Rabin cryptosystem. Comput. Commun. 2020, 160, 215–227. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N. Anonymous lightweight chaotic map-based authenticated key agreement protocol for Industrial Internet of Things. IEEE Trans. Depend. Secure Comput. 2018, 17, 1133–1146. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Depend. Secure Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Giri, D. Anonymous Fine-Grained User Access Control Scheme for Internet of Things Architecture. In Proceedings of the 5th International Conference on Mathematics and Computing, Bhubaneswar, India, 6–9 February 2019; pp. 1–18. [Google Scholar]
- Mubarakali, A. Healthcare services monitoring in cloud using secure and robust healthcare-based BLOCKCHAIN (SRHB) approach. Mobile Netw. Appl. 2020, 25, 1330–1337. [Google Scholar] [CrossRef]
- Park, K.; Park, Y. MIoT-CDPS: Complete decentralized privacy-preserving scheme for medical internet of things. Internet Things 2024, 27, 101250. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Eddine, M.S.; Ferrag, M.A.; Friha, O.; Maglaras, L. EASBF:An efficient authentication scheme over blockchain for fog computing enabled Internet of Vehicles. J. Inf. Secur. Appl. 2021, 59, 102802. [Google Scholar]
- Tomar, A.; Tripathi, S. Blockchain-assisted authentication and key agreement scheme for fog-based smart grid. Clust. Comput. 2022, 25, 451–468. [Google Scholar] [CrossRef]
- Zhang, J.; Yang, Y.; Liu, X.; Ma, J. An efficient blockchain-based hierarchical data sharing for healthcare Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 7139–7150. [Google Scholar] [CrossRef]
- Jia, X.; Luo, M.; Wang, H.; Shen, J.; He, D. A blockchain-assisted privacy-aware authentication scheme for Internet of Medical Things. IEEE Internet Things J. 2022, 9, 21838–21850. [Google Scholar] [CrossRef]
- Karankar, N.; Seth, A. An IoT system for access control using blockchain and message queuing system. EURASIP J. Inf. Secur. 2025, 2025, 31. [Google Scholar] [CrossRef]
- Trivedi, H.S.; Patel, S.J. Key-aggregate searchable encryption with multi-user authorization and keyword untraceability for distributed IoT healthcare systems. Trans. Emerg. Telecommun. Technol. 2023, 34, 4. [Google Scholar] [CrossRef]
- Guo, Y.; Zhang, Z.; Guo, Y.; Xiong, P. BSRA: Blockchain-based secure remote authentication scheme for fog-enabled Internet of Things. IEEE Internet Things J. 2024, 11, 3348–3361. [Google Scholar] [CrossRef]
- Vangala, A.; Das, A.K.; Mitra, A.; Das, S.K.; Park, Y. Blockchain-enabled authenticated key agreement scheme for mobile vehicles-assisted precision agricultural IoT networks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 904–919. [Google Scholar] [CrossRef]
- Ponnuru, R.B.; Kumar, S.A.P.; Azab, M.; Alavalapati, G.R. BAAP-FIoT: Blockchain-Assisted Authentication Protocol for Fog-Enabled Internet of Things Environment. IEEE Internet Things J. 2025, 12, 15681–15696. [Google Scholar] [CrossRef]
- Lee, J.; Oh, J.; Kwon, D.; Kim, M.; Kim, K.; Park, Y. Blockchain-enabled key aggregate searchable encryption scheme for personal health record sharing with multidelegation. IEEE Internet Things J. 2024, 11, 17482–17494. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-Based Encryption from the Weil Pairing. In Proceedings of the CRYPTO: Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Oheimb, D.V. The High-Level Protocol Specification Language HLPSL Developed in the EU Project AVISPA. Available online: https://www.davoh.de/cs/talks/AVISPA-HLPSL.pdf (accessed on 2 August 2025).
- Basin, D.; Modersheim, S.; Vigano, L. OFMC: A Symbolic Model Checker for Security Protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- Turuani, M. The CL-Atse Protocol Analyser. In Proceedings of the RTA: International Conference on Rewriting Techniques and Applications, Seattle, WA, USA, 12–14 August 2006; pp. 277–286. [Google Scholar]
- Armando, A.; Compagna, L. SATMC: A SAT-Based Model Checker for Security Protocols. In Proceedings of the European Workshop on Logics in Artificial Intelligence, Lisbon, Portugal, 27–30 September 2004; pp. 730–733. [Google Scholar]
- Boichut, Y.; Ham, P.C.; Kouchnarenko, O. Automatic Verification of Security Protocols Using Approximations; INRIA: Rocquencourt, France, 2005; Research Report inria-00070291. [Google Scholar]
- Park, K. The AVISPA Simulation of Our Scheme. Available online: https://github.com/ISNPL/AVISPA_DADAC (accessed on 6 November 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).