Runtime Verification Tool for the Calculus of Context-Aware Ambients
Abstract
1. Introduction
- A novel labelled reduction semantics is proposed for CCA, where the traditional reduction relation is annotated with a label representing the execution trace of the reduction step (Section 2.2).
- A new property specification language is proposed that extends LTL with context expressions and other operators to cater for the specification of properties about both the system and its context (Section 2.3). A context expression defined in Table 1 is a logical formula upon the state of the environment (context). A formal semantics of the property specification language is given over an infinite sequence of states, where a state contains both the current context information and the trace of the last reduction step. In this way, the semantic model provides a holistic view of the system execution (Section 2.3).
- A novel RV mechanism is defined based on the labelled reduction semantics of CCA and the semantics of the property specification language (Definition 5). A consequence of this is that there is no need for generating a monitor from the property specification nor for the instrumentation of a system during verification. This RV mechanism is implemented into a software tool called ccaRV depicted in Figure 1 (Section 3.1).
- A formal specification of the MQTT protocol is given in CCA and used to evaluate the RV tool ccaRV. The MQTT protocol is de facto standard messaging protocol for IoT device communication as it is designed for resource-constrained devices and low-bandwidth, high-latency or unreliable networks. It is chosen as a case study for its scalability (Section 2.4). The experimental results show that ccaRV decisions are accurate and the RV overhead is low relative to the execution time, but increases with the size of system and the size of the property (Section 3.2).
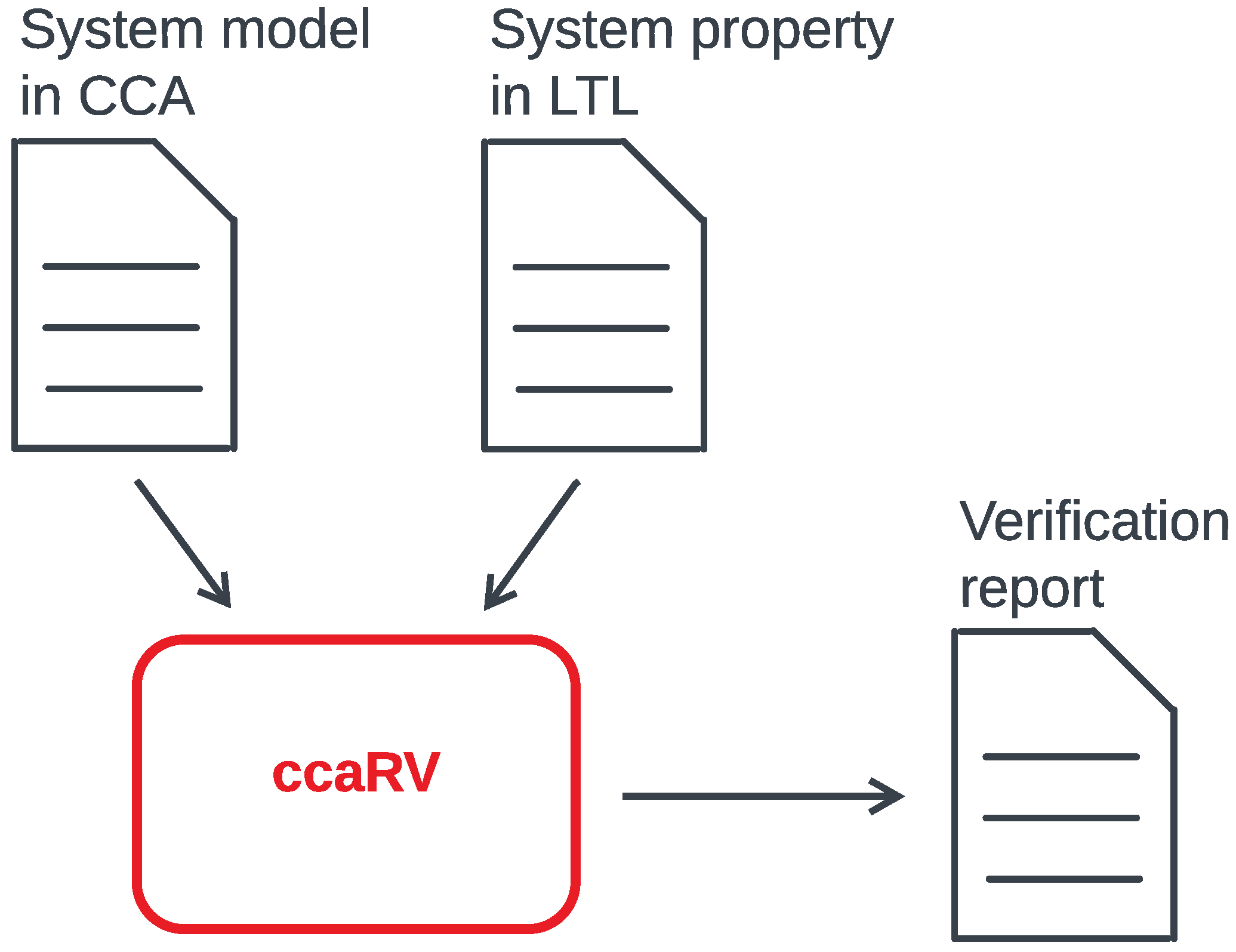
2. Materials and Methods
2.1. Overview of CCA
2.1.1. Capabilities
2.1.2. Processes
2.1.3. Context Expressions
2.2. A Labelled Reduction Semantics of CCA
- 1.
- mem[
- 2.
- !@recv().recv(v1,v2).{ @send(v1,v2).0 | send(v1,v2).0 }
- 3.
- | !@recv(x1,x2).recv(y1,y2).{ send(x1,x2).0 | @send().0 }
- 4.
- | send(z1,z2).0
- 5.
- ]
2.3. The Property Specification Language
- iff and r is a substring of the string .
- iff and (⊧ is defined in Table 3).
- iff there exists such that and not and for all , .
- iff .
- iff or .
- iff .
- iff there exists such that and for all , .
- , i.e., eventually f holds forever. This is a safety property, i.e., nothing bad can happen.
- , i.e., f always eventually holds. This is a liveness property, i.e., something good will always eventually happen.
- , i.e., a message X is sent.
- , i.e., a message X is received by ambient B.
- , i.e., a message X is sent by ambient A.
- , i.e., ambient A sent a message X to ambient B.
2.4. Case Study: The MQTT Protocol
2.4.1. Overview of the MQTT Protocol
- QoS 0 means at most one delivery. A packet is sent once; no acknowledgement is required. This is illustrated in Figure 3a. This also means the delivery is not guaranteed, the packet can get lost. Therefore, QoS level 0 is recommended when message loss is acceptable or the network bandwidth is at premium.
- QoS 1 means at least once delivery. A packet is sent repeatedly until acknowledgement is received. The packet delivery is guaranteed upon acknowledgement. This is illustrated in Figure 3b. This is the default QoS level and it offers the best trade-off between bandwidth and delivery guarantee.
- QoS 2 means exactly once delivery. A packet is sent once and is guaranteed to be delivered. There is an increased overhead associated with this quality of service. This is the highest quality of service, for use when neither loss nor duplication of messages are acceptable. The network traffic engendered by this QoS is illustrated in Figure 3c.
| Name | Direction of Flow | Description |
|---|---|---|
| CONNECT | Client to Broker | Client request to connect to Broker |
| CONNACK | Broker to Client | Connect acknowledgment |
| PUBLISH | Client to Broker or | Publish message |
| Broker to Client | ||
| PUBACK | Client to Broker or | Publish acknowledgment |
| Broker to Client | ||
| PUBREC | Client to Broker or | Publish received |
| Broker to Client | ||
| PUBREL | Client to Broker or | Publish release |
| Broker to Client | ||
| PUBCOMP | Client to Broker or | Publish complete |
| Broker to Client | ||
| SUBSCRIBE | Client to Broker | Client subscribe request |
| SUBACK | Broker to Client | Subscribe acknowledgment |
| UNSUBSCRIBE | Client to Broker | Unsubscribe request |
| UNSUBACK | Broker to Client | Unsubscribe acknowledgment |
| PINGREQ | Client to Broker | PING request |
| PINGRESP | Broker to Client | PING response |
| DISCONNECT | Client to Broker | Client is disconnecting |
2.4.2. A Formal Specification of the MQTT Protocol in CCA
| Listing 1. General form of a client ambient. |
|
| Listing 2. General form of a process abstraction representing a topic with N subscribers. |
| proc topic(topic, qos, retainFlag, payload){ if < contains(clientId1) and contains(clientId1_topic) > clientId1::send(PUBLISH,broker,topic,qos,retainFlag,payload).if <qos=0> skip.0 <qos=1> clientId1::recv(ack).0 <qos=2> clientId1::recv(pubrec).clientId1::send(PUBREL). clientId1::recv(pubcomp).0 fi < not(contains(clientId1) and contains(clientId1_topic)) > skip.0 fi | if < contains(clientId2) and contains(clientId2_topic) > clientId2::send(PUBLISH,broker,topic,qos,retainFlag,payload).if <qos=0> skip.0 <qos=1> clientId2::recv(ack).0 <qos=2> clientId2::recv(pubrec).clientId2::send(PUBREL). clientId2::recv(pubcomp).0 fi < not(contains(clientId2) and contains(clientId2_topic)) > skip.0 fi | ... | if < contains(clientIdN) and contains(clientIdN_topic) > clientIdN::send(PUBLISH,broker,topic,qos,retainFlag,payload).if <qos=0> skip.0 <qos=1> clientIdN::recv(ack).0 <qos=2> clientIdN::recv(pubrec).clientIdN::send(PUBREL). clientIdN::recv(pubcomp).0 fi < not(contains(clientIdN) and contains(clientIdN_topic)) > skip.0 fi } |
| Listing 3. General form of an ambient representing a broker. |
|
2.4.3. An Example
| Listing 4. Specification of the motion sensor and the light sensor. |
| motion_sensor[ broker::send(CONNECT, motion_sensor).broker::recv(ack). broker::send(PUBLISH, motion_sensor, motion, 1, 1, 1). broker::recv(pubrec).broker::send(PUBREL).broker::recv(pubcomp).0 ] | light_sensor[ broker::send(CONNECT, light_sensor).broker::recv(ack). broker::send(PUBLISH, light_sensor, light, 1, 1, 300). broker::recv(pubrec).broker::send(PUBREL).broker::recv(pubcomp).0 ] |
| Listing 5. Specification of the lamp and the camera. |
| lamp[ !broker::recv(packetType, _, topic, qos, retainFlag, payload).if <packetType=PUBLISH and qos=0 > skip.0 <packetType=PUBLISH and qos=1 > broker::send(PUBACK).0 <packetType=PUBLISH and qos=2 > broker::send(PUBREC). broker::recv(pubrel).broker::send(PUBCOMP).0 fi | broker::send(CONNECT, lamp).broker::recv(ack). broker::send(SUBSCRIBE, lamp, lamp).broker::recv(suback).0 ] | camera[ !broker::recv(packetType, _, topic, qos, retainFlag, payload).if <packetType=PUBLISH and qos=0> skip.0 <packetType=PUBLISH and qos=1> broker::send(PUBACK).0 <packetType=PUBLISH and qos=2> broker::send(PUBREC). broker::recv(pubrel).broker::send(PUBCOMP).0 fi | broker::send(CONNECT, camera).broker::recv(ack). broker::send(SUBSCRIBE, camera, camera).broker::recv(suback).0 ] |
| Listing 6. Specification of the microcontroller. |
| mcu[ !broker::recv(packetType, _, topic, qos, retainFlag, payload).if <packetType=PUBLISH and qos=0> Q(topic,payload,broker,mcu,lamp,camera).0 <packetType=PUBLISH and qos=1> broker::send(PUBACK). Q(topic,payload,broker,mcu,lamp,camera).0 <packetType=PUBLISH and qos=2> broker::send(PUBREC).broker::recv(pubrel). broker::send(PUBCOMP).Q(topic,payload,broker,mcu,lamp,camera).0 fi | broker::send(CONNECT, mcu).broker::recv(ack). broker::send(SUBSCRIBE, mcu, light).broker::recv(suback). broker::send(SUBSCRIBE, mcu, motion).broker::recv(suback).0 | proc Q(topic,payload,broker,mcu,lamp,camera) { if <topic=light and payload<330> broker::send(PUBLISH,mcu,lamp,1,0,on). broker::recv(puback).0 <topic=light and payload>=330> broker::send(PUBLISH,mcu,lamp,1,0,off). broker::recv(puback).0 <topic=motion and payload=1> broker::send(PUBLISH,mcu,camera,1,0,on). broker::recv(puback).0 <topic=motion and payload=0> broker::send(PUBLISH,mcu,camera,1,0,off). broker::recv(puback).0 fi } ] |
3. Results
3.1. Overview of the ccaRV Tool
| Listing 7. Syntax of an ccaRV program, where P is a process and k is a context expression defined in Table 1; f is an LTL formula defined in Table 11; <Id> stands for an identifier (i.e., a name); e for the empty string; and <Val> is a non-negative integer number. |
| <Program> ::= <DeclarationBlock> P <DeclarationBlock> ::= e | "BEGIN_DECLS" <DeclarationList> "END_DECLS" <DeclarationList> ::= e | <Declaration> <DeclarationList> <Declaration> ::= "def" <Id> "(" <ParamList> ") = {" k "}" | "mode random" | "display code" | "length = " <Val> | "display congruence" | "name" <Id> <Params> | "ltl" (<Id> | e) "{" f "}" <ParamList> ::= e | <Id> <Params><Params> ::= e | "," <Id> <Params> |
3.2. Experimental Results
3.2.1. Runtime Verification Accuracy
3.2.2. Runtime Verification Overhead
4. Discussion
5. Conclusions and Outlook
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. Proofs of the Theorems
- Q ⊢ f
- ⇒
- {from Definition 6}
- There exists an execution or run , that satisfies the formula f.
- ⇒
- {from Definition 5}
- ⇒
- {from the semantics of }
- ⇒
- {from the semantics of the operator}
- ⇒
- {since }
- There exists an execution or run of the process P of the form , that satisfies the formula .
- ⇒
- {from Definition 6}
- Base case:
- and
- ⇒
- {by Definition 6}
- ⇒
- {by the semantics of LTL}
- Suppose there exists a finite sequence of reductions and .
- ⇒
- {by Definition 4}
- and and .
- ⇒
- {by the induction hypothesis}
- and .
- ⇒
- {by Theorem 3}
- .
- ⇒
- {by the semantics of LTL}
- .
- ⇒
- {by the semantics of LTL}
- .
Appendix B. CCA Specification of the Simple IoT System of Section 2.4.3
Appendix C. A Python Program for Generating an MQTT Protocol System
References
- Myers, G.J.; Sandler, C.; Badgett, T. The Art of Software Testing; John Wiley & Sons: Hoboken, NJ, USA, 2011; Volume 3. [Google Scholar]
- Clarke, E.M.; Emerson, E.A.; Sistla, A.P. Automatic verification of finite-state concurrent systems using temporal logic specifications. ACM Trans. Program. Lang. Syst. (TOPLAS) 1986, 8, 244–263. [Google Scholar] [CrossRef]
- Holzmann, J.G. The Model Checker SPIN. IEEE Trans. Softw. Eng. 1997, 23, 279–295. [Google Scholar] [CrossRef]
- Nipkow, T.; Wenzel, M.; Paulson, L.C. Isabelle/HOL: A Proof Assistant for Higher-Order Logic; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Gordon, M.J.; Melham, T.F. Introduction to HOL: A Theorem Proving Environment for Higher Order Logic; Cambridge University Press: Cambridge, UK, 1993. [Google Scholar]
- Riazanov, A.; Voronkov, A. Vampire. In Proceedings of the International Conference on Automated Deduction, Trento, Italy, 7–10 July 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 292–296. [Google Scholar]
- Barrett, C.W.; Conway, C.L.; Deters, M.; Hadarean, L.; Jovanovic, D.; King, T.; Reynolds, A.; Tinelli, C. CVC4. In Proceedings of the Computer Aided Verification—23rd International Conference, CAV 2011, Snowbird, UT, USA, 14–20 July 2011; Gopalakrishnan, G., Qadeer, S., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6806, pp. 171–177. [Google Scholar] [CrossRef]
- Havelund, K.; Peled, D. Runtime Verification: From Propositional to First-Order Temporal Logic. In Proceedings of the Runtime Verification, Limassol, Cyprus, 10–13 November 2018; Colombo, C., Leucker, M., Eds.; Springer: Cham, Switzerland, 2018; pp. 90–112. [Google Scholar]
- Bartocci, E.; Falcone, Y.; Francalanza, A.; Reger, G. Introduction to Runtime Verification. In Lectures on Runtime Verification: Introductory and Advanced Topics; Bartocci, E., Falcone, Y., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 1–33. [Google Scholar]
- Havelund, K.; Roşu, G. Runtime verification-17 years later. In Proceedings of the International Conference on Runtime Verification, Limassol, Cyprus, 10–13 November 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 3–17. [Google Scholar]
- Meredith, P.; Roşu, G. Runtime verification with the RV system. In Proceedings of the International Conference on Runtime Verification, St. Julians, Malta, 1–4 November 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 136–152. [Google Scholar]
- Reger, G.; Cruz, H.C.; Rydeheard, D. MarQ: Monitoring at runtime with QEA. In Proceedings of the International Conference on Tools and Algorithms for the Construction and Analysis of Systems, Hamilton, ON, Canada, 6–11 April 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 596–610. [Google Scholar]
- İnçki, K.; Ari, I. A novel runtime verification solution for IoT systems. IEEE Access 2018, 6, 13501–13512. [Google Scholar] [CrossRef]
- Kane, A. Runtime Monitoring for Safety-Critical Embedded Systems. Ph.D. Thesis, Carnegie Mellon University, Pittsburgh, PA, USA, 2015. [Google Scholar]
- Medhat, R.; Bonakdarpour, B.; Kumar, D.; Fischmeister, S. Runtime monitoring of cyber-physical systems under timing and memory constraints. ACM Trans. Embed. Comput. Syst. (TECS) 2015, 14, 1–29. [Google Scholar] [CrossRef]
- Leotta, M.; Ancona, D.; Franceschini, L.; Olianas, D.; Ribaudo, M.; Ricca, F. Towards a runtime verification approach for internet of things systems. In Proceedings of the International Conference on Web Engineering, Cáceres, Spain, 5–8 June 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 83–96. [Google Scholar]
- Siewe, F.; Zedan, H.; Cau, A. The Calculus of Context-aware Ambients. J. Comput. Syst. Sci. 2011, 77, 597–620. [Google Scholar] [CrossRef]
- Siewe, F. ccaPL: An CCA Programming Environment. Available online: https://fsiewe.afrilocode.net/CCA/index.html (accessed on 23 November 2023).
- Cardelli, L.; Gordon, A.D. Mobile Ambients. Theor. Comput. Sci. 2000, 240, 177–213. [Google Scholar] [CrossRef]
- Pnueli, A. The temporal logic of programs. In Proceedings of the 18th Annual Symposium on Foundations of Computer Science (sfcs 1977), Providence, RI, USA, 31 October–2 November 1977; pp. 46–57. [Google Scholar]
- MQTT Version 3.1.1. Edited by Andrew Banks and Rahul Gupta. 29 October 2014. OASIS Standard. Available online: http://docs.oasis-open.org/mqtt/mqtt/v3.1.1/os/mqtt-v3.1.1-os.html (accessed on 17 March 2025).
- MQTT Version 5.0. Edited by Andrew Banks, Ed Briggs, Ken Borgendale, and Rahul Gupta. 07 March 2019. OASIS Standard. Available online: https://docs.oasis-open.org/mqtt/mqtt/v5.0/os/mqtt-v5.0-os.html (accessed on 17 March 2025).
- ISO/IEC 20922:2016; Information Technology—Message Queuing Telemetry Transport (MQTT) v3.1.1.2016. ISO/IEC: Geneva, Switzerland, 2016. Available online: https://www.iso.org/standard/69466.html (accessed on 17 March 2025).
- Siewe, F. ccaRV: A Runtime Verification Tool for CCA. Available online: https://fsiewe.afrilocode.net/CCA/index.html (accessed on 23 April 2025).
- Taleb, R.; Hallé, S.; Khoury, R. Uncertainty in runtime verification: A survey. Comput. Sci. Rev. 2023, 50, 100594. [Google Scholar] [CrossRef]
- Almakhour, M.; Sliman, L.; Samhat, A.E.; Mellouk, A. Verification of smart contracts: A survey. Pervasive Mob. Comput. 2020, 67, 101227. [Google Scholar] [CrossRef]
- Colombo, C.; Pace, G.J.; Schneider, G. LARVA—Safer Monitoring of Real-Time Java Programs (Tool Paper). In Proceedings of the 2009 7th IEEE International Conference on Software Engineering and Formal Methods (SEFM 2009), Los Alamitos, CA, USA, 23–27 November 2009; pp. 33–37. [Google Scholar] [CrossRef]
- Ellul, J.; Pace, G.J. Runtime Verification of Ethereum Smart Contracts. In Proceedings of the 2018 14th European Dependable Computing Conference (EDCC), Iasi, Romania, 10–14 September 2018; pp. 158–163. [Google Scholar] [CrossRef]
- Caldas, R.; García, J.A.P.; Schiopu, M.; Pelliccione, P.; Rodrigues, G.; Berger, T. Runtime verification and field-based testing for ros-based robotic systems. IEEE Trans. Softw. Eng. 2024, 50, 2544–2567. [Google Scholar] [CrossRef]
- Mahe, E.; Bannour, B.; Gaston, C.; Le Gall, P. Efficient interaction-based offline runtime verification of distributed systems with lifeline removal. Sci. Comput. Program. 2025, 241, 103230. [Google Scholar] [CrossRef]
- Rodríguez, G.V.; Castañeda, A. Towards Efficient Runtime Verified Linearizable Algorithms. In Proceedings of the Runtime Verification, Istanbul, Turkey, 15–17 October 2024; Ábrahám, E., Abbas, H., Eds.; Springer: Cham, Switzerland, 2024; pp. 262–281. [Google Scholar]
- Castañeda, A.; Rodríguez, G.V. Asynchronous wait-free runtime verification and enforcement of linearizability. In Proceedings of the 2023 ACM Symposium on Principles of Distributed Computing, Orlando, FL, USA, 19–23 June 2023; pp. 90–101. [Google Scholar]
- Falcone, Y. On Decentralized Monitoring. In Proceedings of the Verification and Evaluation of Computer and Communication Systems, Tbilisi, Georgia, 28–30 September 2022; Nouri, A., Wu, W., Barkaoui, K., Li, Z., Eds.; Springer: Cham, Switzerland, 2022; pp. 1–16. [Google Scholar]
- Bonakdarpour, B.; Fraigniaud, P.; Rajsbaum, S.; Rosenblueth, D.; Travers, C. Decentralized Asynchronous Crash-resilient Runtime Verification. J. ACM 2022, 69, 34. [Google Scholar] [CrossRef]
- Bauer, A.; Falcone, Y. Decentralised LTL monitoring. Form. Methods Syst. Des. 2016, 48, 46–93. [Google Scholar] [CrossRef]
- Ganguly, R.; Kazemloo, S.; Bonakdarpour, B. Crash-Resilient Decentralized Synchronous Runtime Verification. IEEE Trans. Dependable Secur. Comput. 2024, 21, 1017–1031. [Google Scholar] [CrossRef]
- Visconti, E.; Bartocci, E.; Falcone, Y.; Nenzi, L. Adaptable Configuration of Decentralized Monitors. In Proceedings of the Formal Techniques for Distributed Objects, Components, and Systems, Groningen, The Netherlands, 17–21 June 2024; Springer: Berlin/Heidelberg, Germany, 2024; pp. 197–217. [Google Scholar] [CrossRef]
- Audrito, G.; Damiani, F.; Stolz, V.; Torta, G.; Viroli, M. Distributed runtime verification by past-CTL and the field calculus. J. Syst. Softw. 2022, 187, 111251. [Google Scholar] [CrossRef]
- Ancona, D.; Franceschini, L.; Ferrando, A.; Mascardi, V. RML: Theory and practice of a domain specific language for runtime verification. Sci. Comput. Program. 2021, 205, 102610. [Google Scholar] [CrossRef]
- Barrnger, H.; Goldberg, A.; Havelund, K.; Sen, K. Eagle monitors by collecting facts and generating obligations. In Proceedings of the TACAS”04, Warsaw, Poland, 7–11 April 2003. [Google Scholar]
- Meredith, P.O.; Jin, D.; Griffith, D.; Chen, F.; Roşu, G. An overview of the MOP runtime verification framework. Int. J. Softw. Tools Technol. Transf. 2012, 14, 249–289. [Google Scholar] [CrossRef]
- Garavel, H.; Mateescu, R. SEQ. OPEN: A tool for efficient trace-based verification. In Proceedings of the International SPIN Workshop on Model Checking of Software, Barcelona, Spain, 1–3 April 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 151–157. [Google Scholar]
- Ferrando, A.; Malvone, V. Runtime Verification via Rational Monitor with Imperfect Information. ACM Trans. Softw. Eng. Methodol. 2025. [Google Scholar] [CrossRef]
- Aceto, L.; Attard, D.P.; Francalanza, A.; Ingólfsdóttir, A. On benchmarking for concurrent runtime verification. In Proceedings of the International Conference on Fundamental Approaches to Software Engineering, Luxembourg, 27 March–1 April 2021; Springer International Publishing: Cham, Switzerland, 2021; pp. 3–23. [Google Scholar]
- Aceto, L.; Achilleos, A.; Attard, D.P.; Exibard, L.; Francalanza, A.; Ingólfsdóttir, A. A monitoring tool for linear-time μHMLImage 1. Sci. Comput. Program. 2024, 232, 103031. [Google Scholar] [CrossRef]
- Sen, K.; Vardhan, A.; Agha, G.; Rosu, G. Decentralized runtime analysis of multithreaded applications. In Proceedings of the 20th IEEE International Parallel & Distributed Processing Symposium, Rhodes Island, Greece, 25–29 April 2006; p. 11. [Google Scholar]
- Hertz, B.; Luppen, Z.; Rozier, K.Y. Integrating runtime verification into a sounding rocket control system. In Proceedings of the NASA Formal Methods Symposium, Virtual, 24–28 May 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 151–159. [Google Scholar]
- Zhao, Y.; Zhu, E.; Hoxha, B.; Fainekos, G.; Deshmukh, J.; Lindemann, L. Distributionally Robust Predictive Runtime Verification under Spatio-Temporal Logic Specifications. ACM Trans. Cyber Phys. Syst. 2025, 9, 1–26. [Google Scholar] [CrossRef]
- Fredericks, E.M.; Ramirez, A.J.; Cheng, B.H. Towards run-time testing of dynamic adaptive systems. In Proceedings of the 2013 8th International Symposium on Software Engineering for Adaptive and Self-Managing Systems (SEAMS), San Francisco, CA, USA, 20–21 May 2013; pp. 169–174. [Google Scholar]
- Rozier, K.Y. On the Evaluation and Comparison of Runtime Verification Tools for Hardware and Cyber-Physical Systems. In Proceedings of the RV-CuBES, Seattle, WA, USA, 13–16 September 2017; pp. 123–137. [Google Scholar]
- Schirmer, S.; Torens, C. Safe operation monitoring for specific category unmanned aircraft. In Automated Low-Altitude Air Delivery: Towards Autonomous Cargo Transportation with Drones; Springer: Berlin/Heidelberg, Germany, 2021; pp. 393–419. [Google Scholar]
- Li, Q.; Li, Y.; Mao, X.; Wang, T.; Li, T. A Framework for Runtime Safety of Industrial Control Systems Through Runtime Verification. IEEE Internet Things J. 2025, 12, 15587–15599. [Google Scholar] [CrossRef]






| Production Rules | Description | Production Rules | Description | ||||
|---|---|---|---|---|---|---|---|
| (Processes) | (Context expressions) | ||||||
| inactivity | empty context | ||||||
| parallel composition | true | ||||||
| block | false | ||||||
| name restriction | name match | ||||||
| replication | hole | ||||||
| ambient | location context | ||||||
| context-guarded prefix | parallel composition | ||||||
| if-then | conjunction | ||||||
| … | disjunction | ||||||
| negation | |||||||
| if-then-else | spatial next modality | ||||||
| somewhere modality | |||||||
| arithmetic | |||||||
| search | |||||||
| process abstraction | |||||||
| M | (Capabilities) | (Locations) | |||||
| one transition | @ | any parent | |||||
| move into ambient n | specific parent n | ||||||
| move out of parent | # | any child | |||||
| delete ambient n | specific child n | ||||||
| receive data from | any sibling | ||||||
| send data to | specific sibling n | ||||||
| process abstraction call | locally | ||||||
| Production Rules | Description | ||
|---|---|---|---|
| C | |||
| P | process | ||
| ⊙ | hole | ||
| ambient | |||
| parallel composition | |||
| restriction | |||
| block | |||
| ⊧ | ||||
| C | ⊧ | if | ||
| C | ⊧ | if | ||
| C | ⊧ | if | ||
| C | ⊧ | if | ||
| C | ⊧ | if | ||
| C | ⊧ | if | ||
| C | ⊧ | if | ||
| C | ⊧ | if | ||
| C | ⊧ | if | or |
| Context Expression | Description | ||
|---|---|---|---|
| = | self contains n. | ||
| = | n contains self. | ||
| = | n contains m. | ||
| = | self is with n. | ||
| = | n is with m. | ||
| = | self contains . | ||
| = | d contains . | ||
| (S1) | |
| (S2) | |
| (S3) | |
| (S4) | |
| (S5) | |
| (S6) | |
| (S7) | |
| (S8) | |
| (S9) | |
| (S10) | if |
| (S11) | if |
| (S12) | |
| (S13) | |
| (S14) | |
| (S15) | |
| (S16) | |
| (S17) | |
| (S18) | |
| (S19) | |
| (S20) |
| = | ∅ | |
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = | ∅ | |
| = | ||
| = | ∅ | |
| = | ||
| = | ||
| = | ||
| = | ||
| = | ||
| = |
| (R1) | |
| (R2) | |
| (R3) | |
| (R4) | |
| (R5) | |
| (R6) | |
| (R7) | |
| (R8) | |
| (R9) | |
| (R10) | |
| (R11) | |
| (R12) | |
| (R13) | |
| (R14) | |
| (R15) | |
| (R16) | |
| (R17) | |
| (R18) | |
| (R19) | |
| (R20) | |
| (R21) | |
| (R22) | |
| (R23) | |
| (R24) | |
| (R25) | |
| (R26) | |
| (R27) | if |
| (R28) | |
| , for some i, . | |
| (R29) | |
| (R30) | |
| . | |
| (R31) | |
| Notation | Execution Trace | Description |
|---|---|---|
| “skip” | capability “skip” is executed. | |
| “delete ambient ambient A” | ambient A is deleted. | |
| “local: A ===(X)===> A” | A sends message X to itself. | |
| “child to parent: A ===(X)===> B” | A sends a message X to its parent B. | |
| “parent to child: A ===(X)===> B” | A sends a message X to its child B. | |
| “sibling to sibling: A ===(X)===> B” | A sends a message X to its sibling B. | |
| “ambient A moves into ambient B” | A executes the capability “inB”. | |
| “ambient A moves out of ambient B” | A executes the capability “out”. | |
| “local call to the abstraction T in the ambient A” | A calls its own abstraction T. | |
| “call to the abstraction A::T in the ambient B” | B calls abstraction T of its sibling A. | |
| “call to the abstraction A@T in the ambient B” | B calls abstraction T of its parent A. | |
| “call to the abstraction A#T in the ambient B” | B calls abstraction T of its child A. | |
| “binding: -> , …, -> ” | the variables are bound to the names , by the statement. |
| Production Rules | Description | ||
|---|---|---|---|
| Trace predicate | |||
| Context expression | |||
| Post-condition | |||
| Conjunction | |||
| Disjunction | |||
| Implication | |||
| Equivalence | |||
| Next (temporal) | |||
| Until | |||
| Release | |||
| Weak until | |||
| Always | |||
| Sometime | |||
| Negation | |||
| Formula | Graphical Semantics |
|---|---|
| f |  |
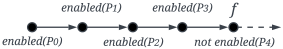 | |
 | |
 | |
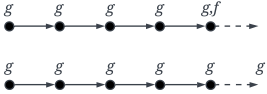 | |
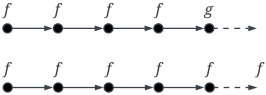 | |
 | |
 |
| Name | Property in LTL | Description |
|---|---|---|
| P1(Z) | [](trace("Z===(CONNECT")-> | A client Z that sends a CONNECT |
| <>trace("CONNACK)===>Z")) | request eventually receives | |
| a CONNACK acknowledgement. | ||
| P2 | [](trace("SUBSCRIBE,camera")-> | The camera requests a subscription |
| <>trace("SUBSCRIBE,lamp")) | before the lamp. | |
| P3(Z) | [](trace("Z===(PUBLISH")-> | A device Z cannot publish |
| contains(broker,Z)) | if it is not connected to the broker. | |
| P4 | <>(trace("SUBSCRIBE,lamp, | The client lamp requests to subscribe |
| motion")) | to the motion topic. | |
| P5 | [](trace("PUBLISH, | If the light level is <330 (e.g., 300), |
| light_sensor,light,1, | eventually the lamp must turn on. | |
| 1,300")-><>trace("1,0,on | ||
| )===>lamp")) | ||
| P6 | [](trace("PUBLISH, | If the light level is≥ 330 (e.g., 600), |
| light_sensor,light,1, | eventually the lamp must turn off. | |
| 1,600")-><>trace("1,0,off | ||
| )===>lamp")) | ||
| P7(Z,Y) | <>((!contains(broker,Z_Y)) | A client Z publishes on a topic Y |
| &&trace("PUBLISH,Z,Y")) | it is not subscribed to. | |
| P8 | <>[](contains(broker, | The microcontroller mcu |
| mcu_light)) | subscribes to the light topic. | |
| P9 | <>(contains(broker,mcu) | The microcontroller mcu connects |
| &&!contains(broker,lamp)) | to the broker before the lamp. | |
| P10 | <>(trace("SUBSCRIBE, | The motion sensor subscribes to |
| motion_sensor")) | a topic. |
| Property | Expected Decision | Actual Decision over 2000 Runs |
|---|---|---|
| P1 (lamp) | pass | pass |
| P2 | fail | fail |
| P3 (mcu) | pass | pass |
| P4 | fail | fail |
| P5 | pass | pass |
| P6 | pass | pass |
| P7 (mcu, lamp) | pass | pass |
| P7 (motion_sensor, lamp) | fail | fail |
| P7 (camera, lamp) | fail | fail |
| P8 | pass | pass |
| P9 | fail | fail |
| P10 | fail | fail |
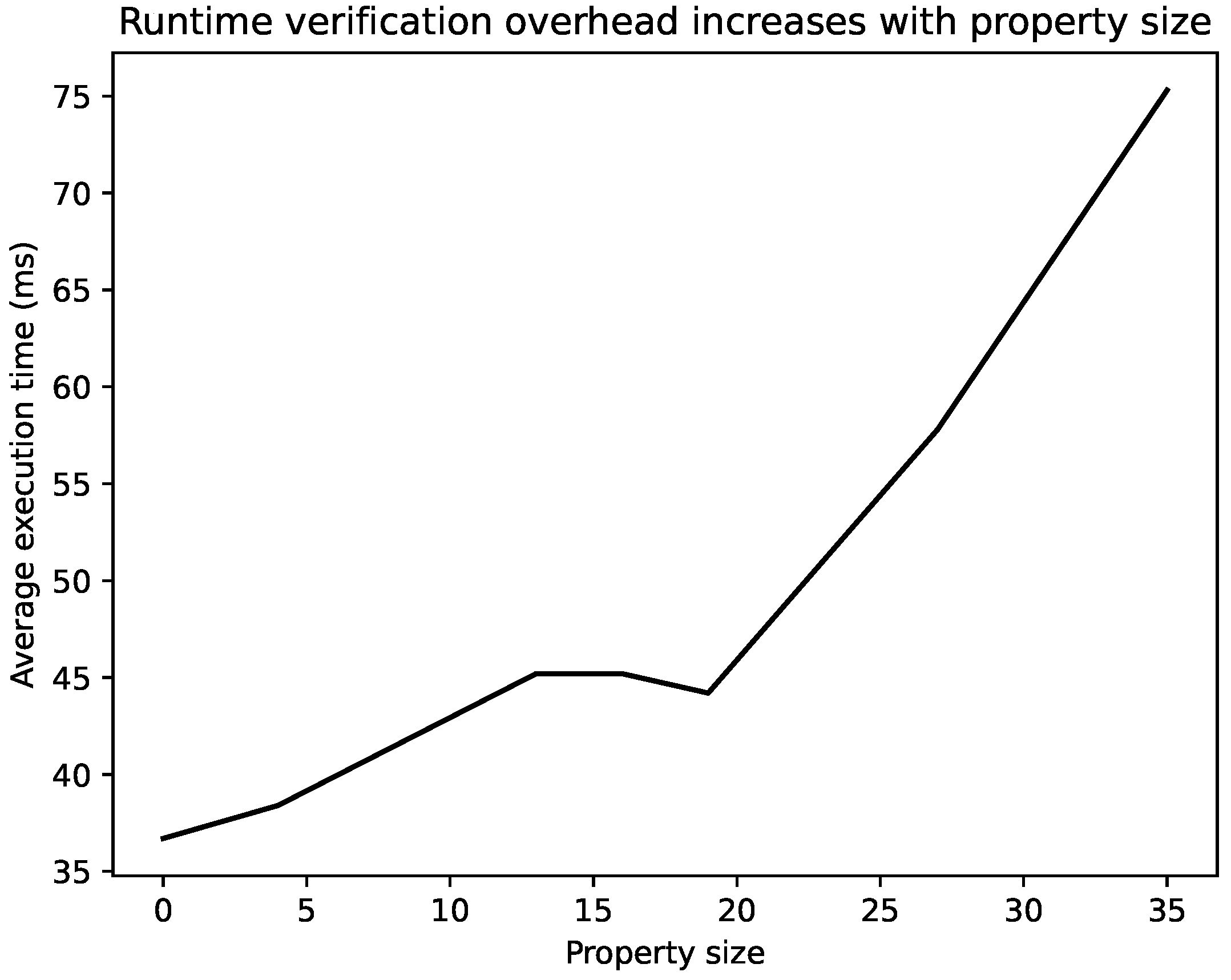
| Property Size | Property in LTL | Average Execution Time (ms) | Standard Deviation (ms) |
|---|---|---|---|
| 0 | No property (baseline) | 36.7 | 8.0 |
| 4 | P1 (lamp) | 38.4 | 8.4 |
| 13 | P1 (lamp) && P3 (mcu) | 45.2 | 8.9 |
| 16 | P1 (lamp) && P3 (mcu) && P5 | 45.2 | 9.2 |
| 19 | P1 (lamp) && P3 (mcu) && P5 && P1 (camera) | 44.2 | 9.3 |
| 27 | P1 (lamp) && P3 (mcu) && P5 && P1 (camera) | ||
| && P7 (mcu, lamp) | 57.8 | 9.5 | |
| 35 | P1 (lamp) && P3 (mcu) && P5 && P1 (camera) | ||
| && P7 (mcu, lamp) && P7 (mcu, camera) | 75.3 | 10.1 |
| Context Expression | |
|---|---|
| Size | Specification |
| 10 | somewhere(broker[true]|true)&& |
| somewhere(next(lamp[true]|true)|true) | |
| 22 | somewhere(broker[true]|true)&& |
| somewhere(next(lamp[true]|true)|true)&& | |
| somewhere(lamp[true]|camera[true]|true)&& | |
| somewhere(next(motion[true]|true)|true) | |
| 42 | somewhere(broker[true]|true)&& |
| somewhere(next(lamp[true]|true)|true)&& | |
| somewhere(lamp[true]|camera[true]|true)&& | |
| somewhere(next(motion[true]|true)|true)&& | |
| somewhere(broker[light[true]|true]|camera[true]|true)&& | |
| somewhere(mcu[true]|next(true)|true) | |
| 56 | somewhere(broker[true]|true)&& |
| somewhere(next(lamp[true]|true)|true)&& | |
| somewhere(lamp[true]|camera[true]|true)&& | |
| somewhere(next(motion[true]|true)|true)&& | |
| somewhere(broker[light[true]|true]|camera[true]|true)&& | |
| somewhere(mcu[true]|next(true)|true)&& | |
| somewhere(next(true)|camera[true]|true)&& | |
| somewhere(next(light[true]|next(true)|true)|true) | |
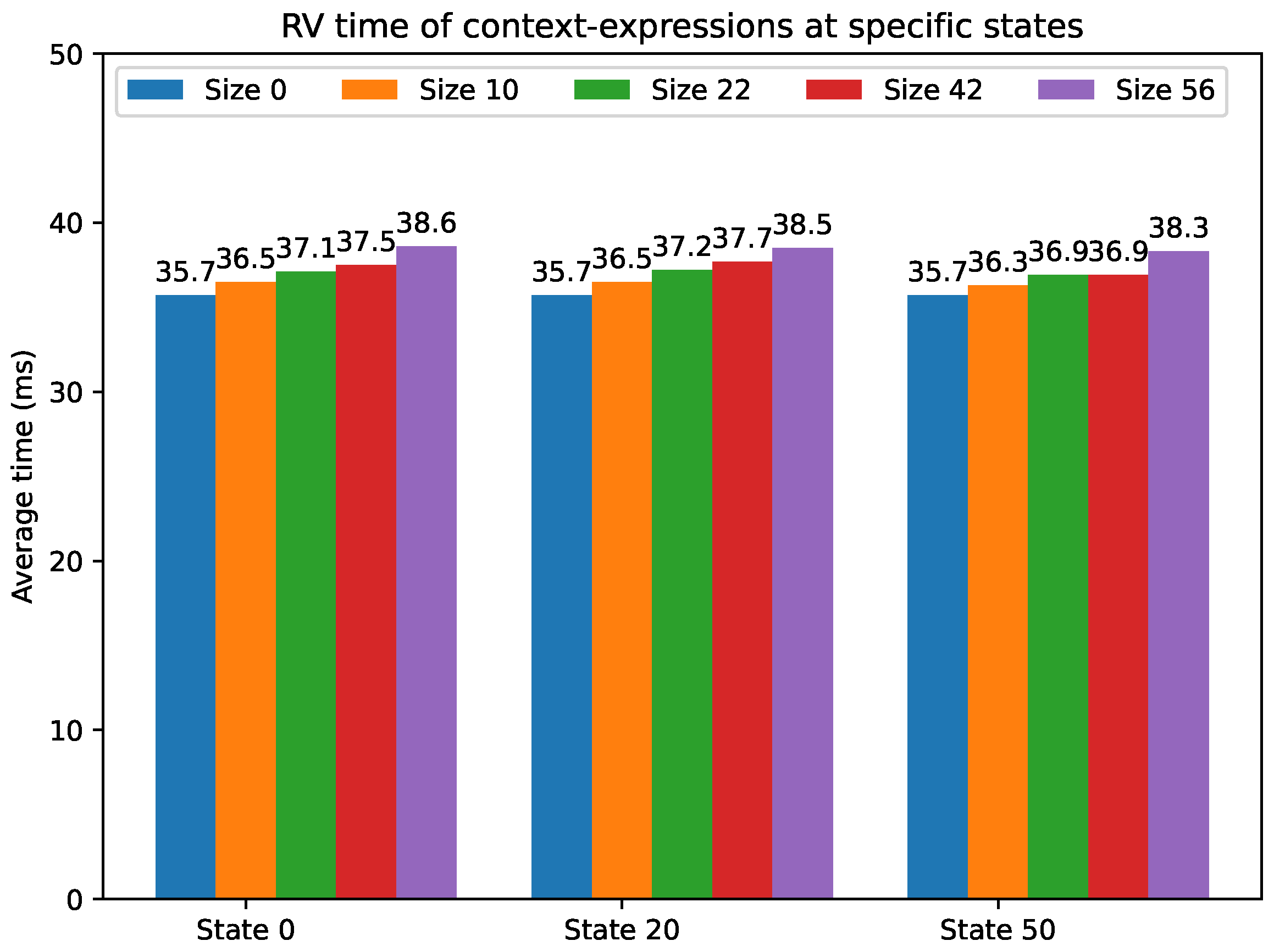
| Context Expression Size | Average Execution Time (ms) | Standard Deviation (ms) | ||||
|---|---|---|---|---|---|---|
| State 0 | State 20 | State 50 | State 0 | State 20 | State 50 | |
| 0 | 35.7 | 35.7 | 35.7 | 8.1 | 8.1 | 8.1 |
| 10 | 36.2 | 36.5 | 36.3 | 8.2 | 8.2 | 8.3 |
| 22 | 37.1 | 37.2 | 36.9 | 8.1 | 7.8 | 9.6 |
| 42 | 37.5 | 37.7 | 36.9 | 8.2 | 9.8 | 8.9 |
| 56 | 38.6 | 38.5 | 38.3 | 11.9 | 10.8 | 8.3 |
| Size | Average Execution Time (ms) | Average Verification Time (ms) | Average Verification Overhead (ms) | ||||||
|---|---|---|---|---|---|---|---|---|---|
| QoS 0 | QoS 1 | QoS 2 | QoS 0 | QoS 1 | QoS 2 | QoS 0 | QoS 1 | QoS 2 | |
| 5 | 23.1 | 25.7 | 26.2 | 28.2 | 27.2 | 30.4 | 5.1 | 1.5 | 4.2 |
| 10 | 64.0 | 71.9 | 72.6 | 72.4 | 75.4 | 87.8 | 8.4 | 3.5 | 15.2 |
| 15 | 143.0 | 159.5 | 160.8 | 150.5 | 165.2 | 179.7 | 7.5 | 5.7 | 18.9 |
| 20 | 238.7 | 276.4 | 271.5 | 253.7 | 315.5 | 283.3 | 15 | 39.1 | 11.8 |
| 25 | 397.4 | 458.1 | 448.6 | 430.8 | 558.1 | 505.7 | 33.4 | 100 | 57.1 |
| 30 | 615.2 | 721.3 | 694.9 | 672.1 | 825.1 | 741.5 | 56.9 | 103.8 | 46.6 |
| 35 | 925.1 | 1078.7 | 1048.7 | 997.2 | 1203.4 | 1158.5 | 72.1 | 124.7 | 109.8 |
| 40 | 1344.5 | 1563.2 | 1516.9 | 1438.2 | 1822.8 | 1650 | 93.7 | 259.6 | 133.1 |
| 45 | 1854.4 | 2154.2 | 2090.4 | 2013.4 | 2587 | 2309.7 | 159 | 432.8 | 219.3 |
| Size | Standard Deviation of Execution Time (ms) | Standard Deviation of Verification Time (ms) | ||||
|---|---|---|---|---|---|---|
| QoS 0 | QoS 1 | QoS 2 | QoS 0 | QoS 1 | QoS 2 | |
| 5 | 6.8 | 7.8 | 7.8 | 6.5 | 7.9 | 7.7 |
| 10 | 10.7 | 11.6 | 11.4 | 10.0 | 11.2 | 11.8 |
| 15 | 16.0 | 15.8 | 17.1 | 14.8 | 17.2 | 16.4 |
| 20 | 19.2 | 22.3 | 21.5 | 21.9 | 22.6 | 23.8 |
| 25 | 23.5 | 29.3 | 25.9 | 27.3 | 32.4 | 33.1 |
| 30 | 34.7 | 39.1 | 39.9 | 35.3 | 38.5 | 35.6 |
| 35 | 47.5 | 54.0 | 49.0 | 62.2 | 62.3 | 65.1 |
| 40 | 58.6 | 59.6 | 63.3 | 62.6 | 63.8 | 72.5 |
| 45 | 67.5 | 77.9 | 86.4 | 69.6 | 79.5 | 83.3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Siewe, F. Runtime Verification Tool for the Calculus of Context-Aware Ambients. Mathematics 2025, 13, 3606. https://doi.org/10.3390/math13223606
Siewe F. Runtime Verification Tool for the Calculus of Context-Aware Ambients. Mathematics. 2025; 13(22):3606. https://doi.org/10.3390/math13223606
Chicago/Turabian StyleSiewe, François. 2025. "Runtime Verification Tool for the Calculus of Context-Aware Ambients" Mathematics 13, no. 22: 3606. https://doi.org/10.3390/math13223606
APA StyleSiewe, F. (2025). Runtime Verification Tool for the Calculus of Context-Aware Ambients. Mathematics, 13(22), 3606. https://doi.org/10.3390/math13223606






