Multiparty Quantum Private Comparison Protocol Using n-Particle GHZ State
Abstract
1. Introduction
- (1)
- To achieve private comparison, the protocol employs a semi-honest TP that adheres to protocol specifications but may be curious about private data. The TP generates and distributes GHZ state qubits to all participants. Each party encodes their secret input through rotation operations on their allocated qubits and returns the modified state to the TP, which then performs single-particle quantum measurements to derive the outcomes without accessing the raw inputs.
- (2)
- To improve qubit efficiency, our scheme utilizes a distributed photon transmission mode, achieving a qubit efficiency of 1/n, which surpasses many existing MQPC protocols.
- (3)
- To ensure that the secret integers of the participants remain undisclosed to external eavesdroppers and curious participants, the protocol employs decoy-state and quantum key distribution technologies to prevent any leakage of private information.
- (4)
- To demonstrate the feasibility of the proposed protocol, we conduct a simulation experiment using IBM Qiskit, as the protocol utilizes more accessible quantum technologies, including n-particle GHZ state, rotation operations, and single-particle quantum measurements.
2. Preliminaries
2.1. n-Particle GHZ State
2.2. Rotation Operation
3. Description of the Proposed Protocol
3.1. Detailed Steps of the Protocol
- (1)
- Perform the rotation operation on each j-th qubit in to produce a new sequence, denoted as .
- (2)
- Generate a secret key , where for .
- (3)
- Perform the rotation operation on to get an encrypted quantum sequence, denoted as .
- (4)
- Prepare decoy photons chosen from the states randomly.
- (5)
- Insert these decoy photons into at randomly positions to generate a modified quantum sequence, denoted as .
- (6)
- Send to the TP via a quantum channel.
- (1)
- Discard the decoy photons in to recover .
- (2)
- Perform the rotation operation on to obtain the decrypted quantum sequence .
- (3)
- Conduct the basis measurement on to obtain the results.
- (4)
- If all j-th qubit in are identical, confirm that each participant’s inputs are equal; otherwise, they are different.
- (5)
- Announce the results to each participant .
3.2. Correctness
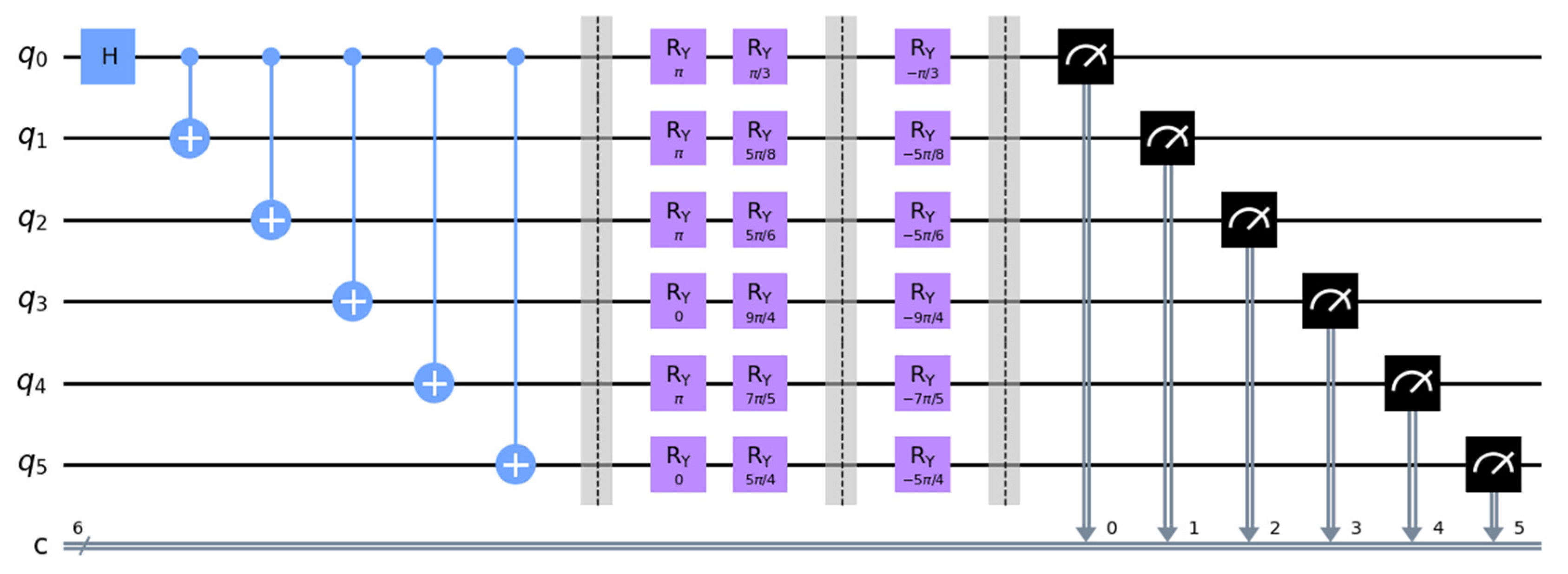
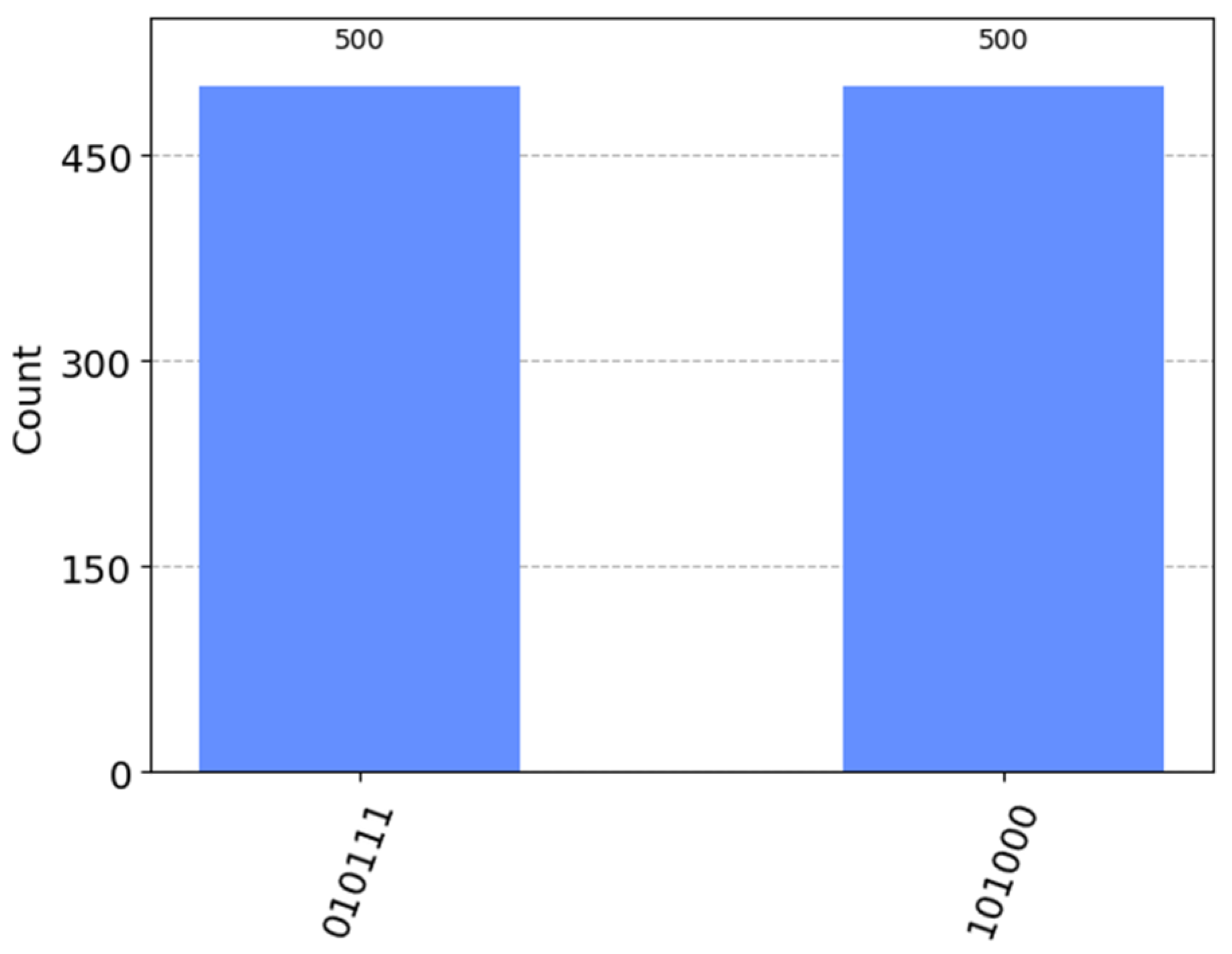
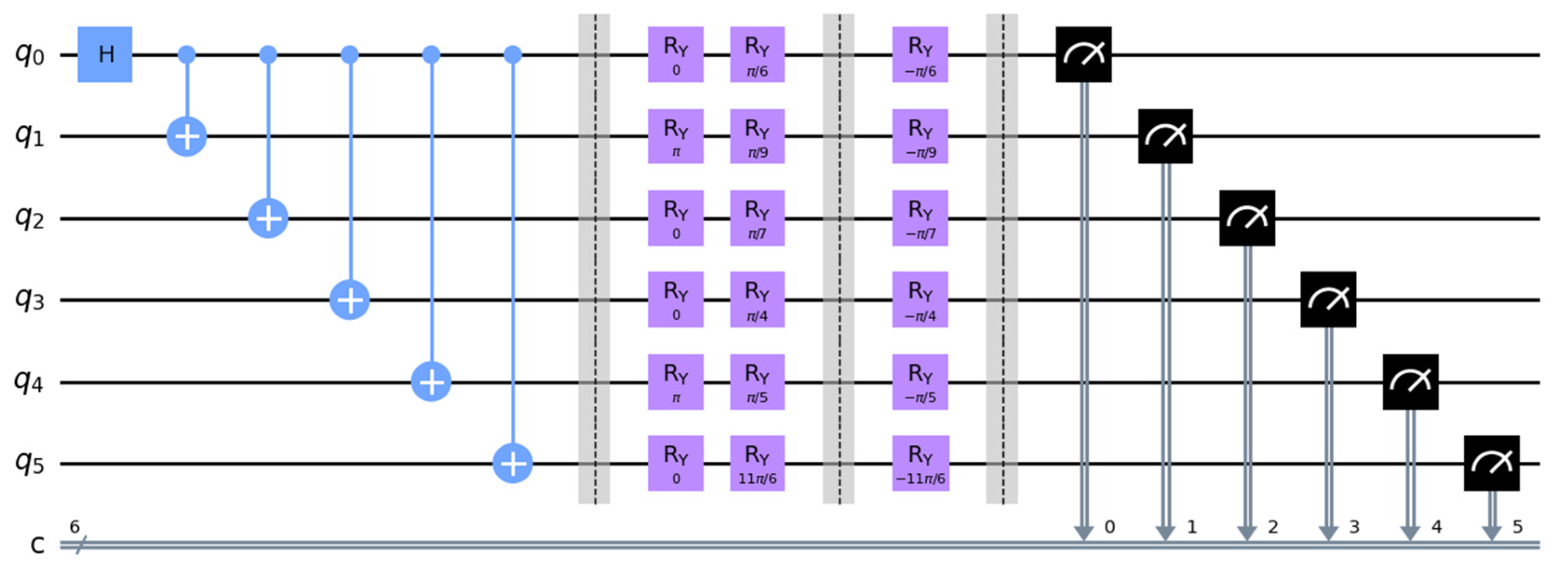
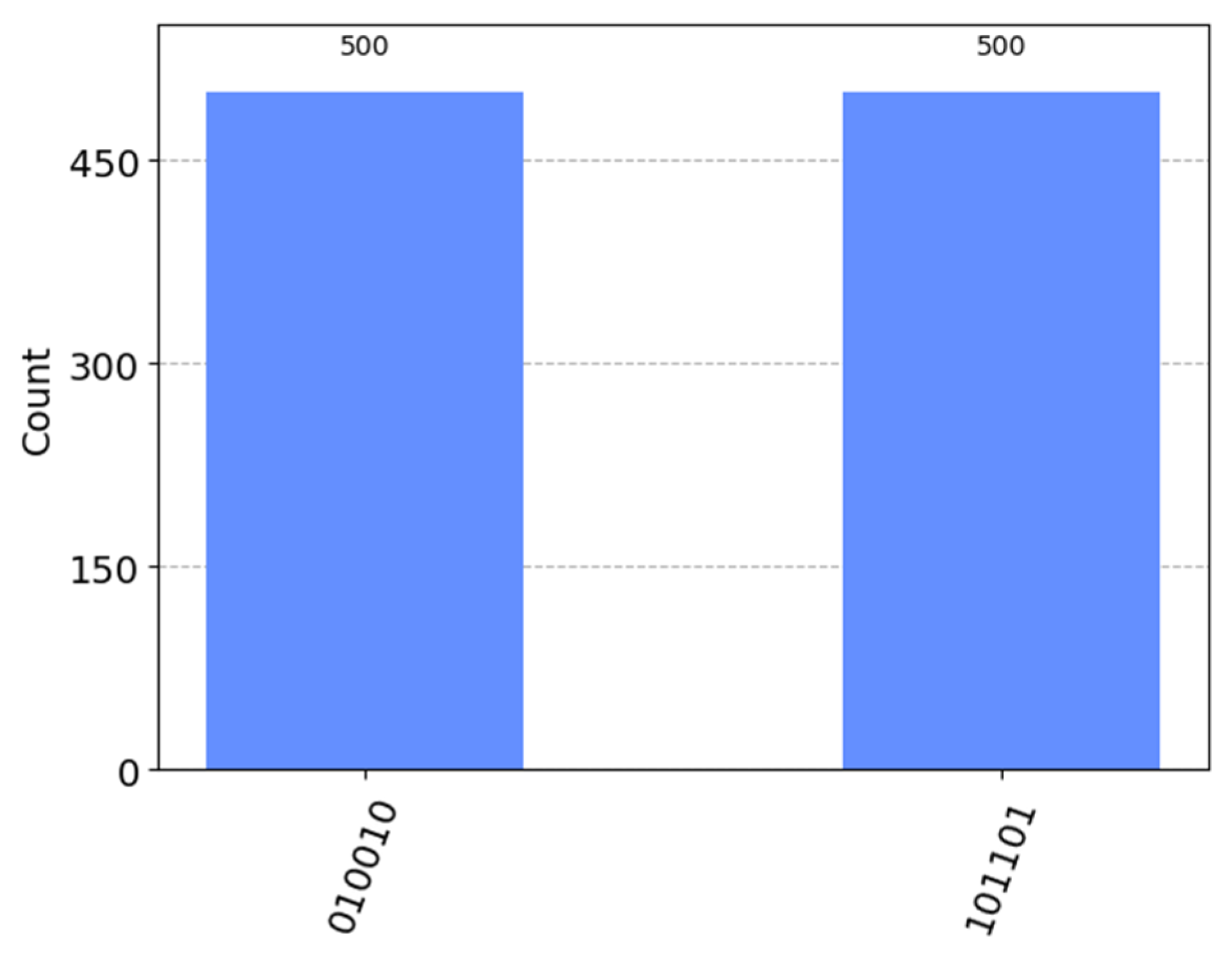
4. Simulation Experiment
- .
- .
5. Security Analysis
5.1. Outsider Attacks
5.2. Participant Attacks
6. Discussion
- (1)
- Unlike the protocols outlined in Refs. [39,40,41,42], which necessitate the creation of complex d-level states, our approach streamlines these requirements. It avoids the need for complicated quantum state preparations by utilizing n-particle GHZ states as quantum resources. This design increases practicality, facilitating implementation with existing quantum technologies, particularly through the straightforward preparation of n-particle GHZ states.
- (2)
- The existing MQPC protocols require sophisticated quantum technologies, such as quantum entanglement swapping of d-level states [41,42] and tailored unitary operations for d-level states [39]. In contrast, our approach uses rotation operations on n-particle GHZ states, which can be easily realized with current quantum technologies.
- (3)
- Our protocol focuses on measurements involving Z-basis instead of d-level quantum states, making it more compatible with existing technological capabilities.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The evolution of quantum key distribution networks: On the road to the qinternet. IEEE Commun. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Zhang, W.; van Leent, T.; Redeker, K.; Garthoff, R.; Schwonnek, R.; Fertig, F.; Eppelt, S.; Rosenfeld, W.; Scarani, V.; Lim, C.C.-W.; et al. A device-independent quantum key distribution system for distant users. Nature 2022, 607, 687–691. [Google Scholar] [CrossRef] [PubMed]
- Nadlinger, D.P.; Drmota, P.; Nichol, B.C.; Araneda, G.; Main, D.; Srinivas, R.; Lucas, D.M.; Ballance, C.J.; Ivanov, K.; Tan, E.Y.-Z.; et al. Experimental quantum key distribution certified by Bell’s theorem. Nature 2022, 607, 682–686. [Google Scholar] [CrossRef] [PubMed]
- Li, Y.; Cai, W.-Q.; Ren, J.-G.; Wang, C.-Z.; Yang, M.; Zhang, L.; Wu, H.-Y.; Chang, L.; Wu, J.-C.; Jin, B.; et al. Microsatellite-based real-time quantum key distribution. Nature 2025, 640, 47–54. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.; Chang, Y.; Yang, F.; Hou, M.; Cheng, W. Quantum secure direct communication based on quantum homomorphic encryption. Mod. Phys. Lett. A 2021, 36, 2150263. [Google Scholar] [CrossRef]
- Pan, D.; Long, G.-L.; Yin, L.; Sheng, Y.-B.; Ruan, D.; Ng, S.X.; Lu, J.; Hanzo, L. The evolution of quantum secure direct communication: On the road to the qinternet. IEEE Commun. Surv. Tutor. 2024, 26, 1898–1949. [Google Scholar] [CrossRef]
- Ying, J.-W.; Wang, J.-Y.; Xiao, Y.-X.; Gu, S.-P.; Wang, X.-F.; Zhong, W.; Du, M.-M.; Li, X.-Y.; Shen, S.-T.; Zhang, A.-L.; et al. Passive-state preparation for quantum secure direct communication. Sci. China Phys. Mech. Astron. 2025, 68, 240312. [Google Scholar] [CrossRef]
- Ying, J.W.; Zhao, P.; Zhong, W.; Du, M.M.; Li, X.Y.; Shen, S.T.; Zhang, A.L.; Zhou, L.; Sheng, Y.B. Passive decoy-state quantum secure direct communication with a heralded single-photon source. Phys. Rev. Appl. 2024, 22, 024040. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.-B.; Chang, Y.; Qiu, C.; Liu, D.-M.; Hou, M. Quantum key agreement protocol based on quantum search algorithm. Int. J. Theor. Phys. 2021, 60, 838–847. [Google Scholar] [CrossRef]
- Wang, C.; Zhang, Q.; Liang, S.; Zhu, H. Secure mutual authentication quantum key agreement scheme for two-party setting with key recycling. Quantum Inf. Process. 2024, 23, 139. [Google Scholar] [CrossRef]
- He, Y.F.; Pang, Y.; Di, M. Mutual authentication quantum key agreement protocol based on Bell states. Quantum Inf. Process. 2022, 21, 290. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y.; Zhang, S. Quantum Private Set Intersection Scheme Based on Bell States. Axioms 2025, 14, 120. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Zhang, S. Quantum multi-party private set intersection using single photons. Phys. A Stat. Mech. Appl. 2024, 649, 129974. [Google Scholar] [CrossRef]
- Chen, Y.; Situ, H.; Huang, Q.; Zhang, C. A novel quantum private set intersection scheme with a semi-honest third party. Quantum Inf. Process. 2023, 22, 429. [Google Scholar] [CrossRef]
- Zhang, X.; Wei, C.; Gao, F.; Li, W.; Qin, S. Efficient semi-quantum private set intersection cardinality protocol without pre-shared key. Quantum Inf. Process. 2025, 24, 213. [Google Scholar] [CrossRef]
- Cramer, R.; Damgård, I.B.; Nielsen, J.B. Secure Multiparty Computation and Secret Sharing; Cambridge University Press: Cambridge, UK, 2015. [Google Scholar]
- Sutradhar, K.; Om, H. An efficient simulation for quantum secure multiparty computation. Sci. Rep. 2021, 11, 2206. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82), Washington, DC, USA, 3–5 November 1982; p. 160. [Google Scholar]
- Boudot, F.; Schoenmakers, B.; Traore, J. A fair and efficient solution to the socialist millionaires’ problem. Discret. Appl. Math. 2001, 111, 23–36. [Google Scholar] [CrossRef]
- Lo, H.K. Insecurity of quantum secure computations. Phys. Rev. A 1997, 56, 1154–1162. [Google Scholar] [CrossRef]
- Yang, Y.G.; Wen, Q.Y. An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 2009, 42, 055305. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.F.; Zhang, S.B. Efficient multiparty quantum private comparison protocol based on single photons and rotation encryption. Quantum Inf. Process. 2023, 22, 272. [Google Scholar] [CrossRef]
- Huang, X.; Chang, Y.; Cheng, W.; Hou, M.; Zhang, S.-B. Quantum private comparison of arbitrary single qubit states based on swap test. Chin. Phys. B 2022, 31, 040303. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Single-photon-based quantum secure protocol for the socialist millionaires’ problem. Front. Phys. 2024, 12, 1364140. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Two-Party Quantum Private Comparison Protocol Based on Rotational Encryption. Appl. Sci. 2025, 15, 722. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.-B.; Chang, Y.; Hou, M.; Cheng, W. Efficient quantum private comparison based on entanglement swapping of bell states. Int. J. Theor. Phys. 2021, 60, 3783–3796. [Google Scholar] [CrossRef]
- Lang, Y.F. Quantum private comparison using single bell state. Int. J. Theor. Phys. 2021, 60, 4030–4036. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Efficient Quantum Private Comparison with Unitary Operations. Mathematics 2024, 12, 3541. [Google Scholar] [CrossRef]
- Fan, P.; Rahman, A.U.; Ji, Z.; Ji, X.; Hao, Z.; Zhang, H. Two-party quantum private comparison based on eight-qubit entangled state. Mod. Phys. Lett. A 2022, 37, 2250026. [Google Scholar] [CrossRef]
- Sun, Q. Quantum private comparison with six-particle maximally entangled states. Mod. Phys. Lett. A 2022, 37, 2250149. [Google Scholar] [CrossRef]
- Ji, Z.X.; Zhang, H.G.; Fan, P.R. Two-party quantum private comparison protocol with maximally entangled seven-qubit state. Mod. Phys. Lett. A 2019, 34, 1950229. [Google Scholar] [CrossRef]
- Ji, Z.; Zhang, H.; Wang, H. Quantum private comparison protocols with a number of multi-particle entangled states. IEEE Access 2019, 7, 44613–44621. [Google Scholar] [CrossRef]
- Zhou, N.R.; Chen, Z.Y.; Liu, Y.Y.; Gong, L.H. Multi-party semi-quantum private comparison protocol of size relation with d-level GHZ states. Adv. Quantum Technol. 2025, 8, 2400530. [Google Scholar] [CrossRef]
- Wu, W.Q.; Zhao, Y.X. Quantum private comparison of size using d-level Bell states with a semi-honest third party. Quantum Inf. Process. 2021, 20, 155. [Google Scholar] [CrossRef]
- Lian, J.Y.; Li, X.; Ye, T.Y. Multi-party semiquantum private comparison of size relationship with d-dimensional Bell states. EPJ Quantum Technol. 2023, 10, 10. [Google Scholar] [CrossRef]
- Zhou, N.R.; Xu, Q.D.; Du, N.S.; Gong, L.H. Semi-quantum private comparison protocol of size relation with d-dimensional Bell states. Quantum Inf. Process. 2021, 20, 124. [Google Scholar] [CrossRef]
- Chang, Y.J.; Tsai, C.W.; Hwang, T. Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 2013, 12, 1077–1088. [Google Scholar] [CrossRef]
- Liu, W.; Wang, Y.B.; Wang, X.M. Multi-party quantum private comparison protocol using d-dimensional basis states without entanglement swapping. Int. J. Theor. Phys. 2014, 53, 1085–1091. [Google Scholar] [CrossRef]
- Wang, Q.L.; Sun, H.X.; Huang, W. Multi-party quantum private comparison protocol with n-level entangled states. Quantum Inf. Process. 2014, 13, 2375–2389. [Google Scholar] [CrossRef]
- Zhao-Xu, J.; Tian-Yu, Y. Multi-party quantum private comparison based on the entanglement swapping of d-level cat states and d-level Bell states. Quantum Inf. Process. 2017, 16, 177. [Google Scholar] [CrossRef]
- Ye, T.Y.; Hu, J.L. Multi-party quantum private comparison based on entanglement swapping of Bell entangled states within d-level quantum system. Int. J. Theor. Phys. 2021, 60, 1471–1480. [Google Scholar] [CrossRef]
- Zhou, R.G.; Huo, M.; Hu, W.; Zhao, Y. Dynamic multiparty quantum secret sharing with a trusted party based on generalized GHZ state. IEEE Access 2021, 9, 22986–22995. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Wang, X.; Zhang, S.; Khan, M.K. QF2PM: Quantum-Secure Fine-Grained Privacy-Preserving Profile Matching for Mobile Social Networks. IEEE Trans. Netw. Sci. Eng. 2025; early access. [Google Scholar]
- Wu, Y.T.; Chang, H.; Guo, G.D.; Song, L. Multi-party quantum key agreement protocol with authentication. Int. J. Theor. Phys. 2021, 60, 4066–4077. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y.; Zhang, S. Two-Party Quantum Private Comparison with Pauli Operators. Axioms 2025, 14, 549. [Google Scholar] [CrossRef]
- Quan, R.; Hong, H.; Xiang, X.; Cao, M.; Li, X.; Li, B.; Dong, R.; Liu, T.; Zhang, S. Enhancing quantum time transfer security: Detecting intercept-resend attacks with energy-time entanglement. New J. Phys. 2024, 26, 093012. [Google Scholar] [CrossRef]
- Hu, W.W.; Zhou, R.G.; Luo, J. Semi-quantum secret sharing in high-dimensional quantum system using product states. Chin. J. Phys. 2022, 77, 1701–1712. [Google Scholar] [CrossRef]
- Zhou, Y.; Ding, H.J.; Liu, J.Y.; Zhang, C.H.; Zhou, X.Y.; Wang, Q. Finite-key security analysis against the Trojan-horse attack on practical reference-frame-independent measurement-device-independent quantum key distribution. Phys. Rev. Appl. 2025, 23, 024007. [Google Scholar] [CrossRef]
- Tsai, C.W.; Yang, C.W.; Lin, J. Multiparty mediated quantum secret sharing protocol. Quantum Inf. Process. 2022, 21, 63. [Google Scholar] [CrossRef]
| Protocol | Quantum Resource | The Need for Entanglement Swapping | The Need for Unitary Operations | Measurement Manner for TP | Measurement Manner for Users | Qubit Efficiency |
|---|---|---|---|---|---|---|
| Liu et al. [39] | d-level basis state | No | Yes | d-level single-particle measurement | No | |
| Wang et al. [40] | d-level n-particle entangled state and d-level two-particle entangled state | No | No | d-level single-particle measurement | d-level single-particle measurement | |
| Ji and Ye [41] | d-level n + 1-particle cat state and d-level two-particle Bell state | Yes | Yes | d-level n + 1-particle cat state measurement | d-level two-particle Bell state measurement | + 1) |
| Ye and Hu [42] | d-level two-particle Bell entangled state | Yes | Yes | d-level two-particle Bell entangled state | d-level two-particle Bell entangled state | + 2) |
| Ours | n-particle GHZ state | No | Yes | Z-basis | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hou, M.; Wu, Y.; Zhang, S. Multiparty Quantum Private Comparison Protocol Using n-Particle GHZ State. Mathematics 2025, 13, 3422. https://doi.org/10.3390/math13213422
Hou M, Wu Y, Zhang S. Multiparty Quantum Private Comparison Protocol Using n-Particle GHZ State. Mathematics. 2025; 13(21):3422. https://doi.org/10.3390/math13213422
Chicago/Turabian StyleHou, Min, Yue Wu, and Shibin Zhang. 2025. "Multiparty Quantum Private Comparison Protocol Using n-Particle GHZ State" Mathematics 13, no. 21: 3422. https://doi.org/10.3390/math13213422
APA StyleHou, M., Wu, Y., & Zhang, S. (2025). Multiparty Quantum Private Comparison Protocol Using n-Particle GHZ State. Mathematics, 13(21), 3422. https://doi.org/10.3390/math13213422







