Estimate-Based Dynamic Memory-Event-Triggered Control for Nonlinear Networked Control Systems Subject to Hybrid Attacks
Abstract
1. Introduction
- Both the designed DMETM and memory-event-triggered output feedback controller are formulated in discrete time. This means that only the system output data are necessary for the joint design of the memory-event-triggered controller and the DMETM, which makes the approach more practical and applicable to the actual system.
2. Problem Formalization
System Model
3. Estimate-Based DMETC Design Against Hybrid Attacks
3.1. Sampled-Data Observer Design
3.2. DMETM Design
3.3. Hybrid Attacks
3.4. Output Feedback Controller Design
4. Stability Analysis
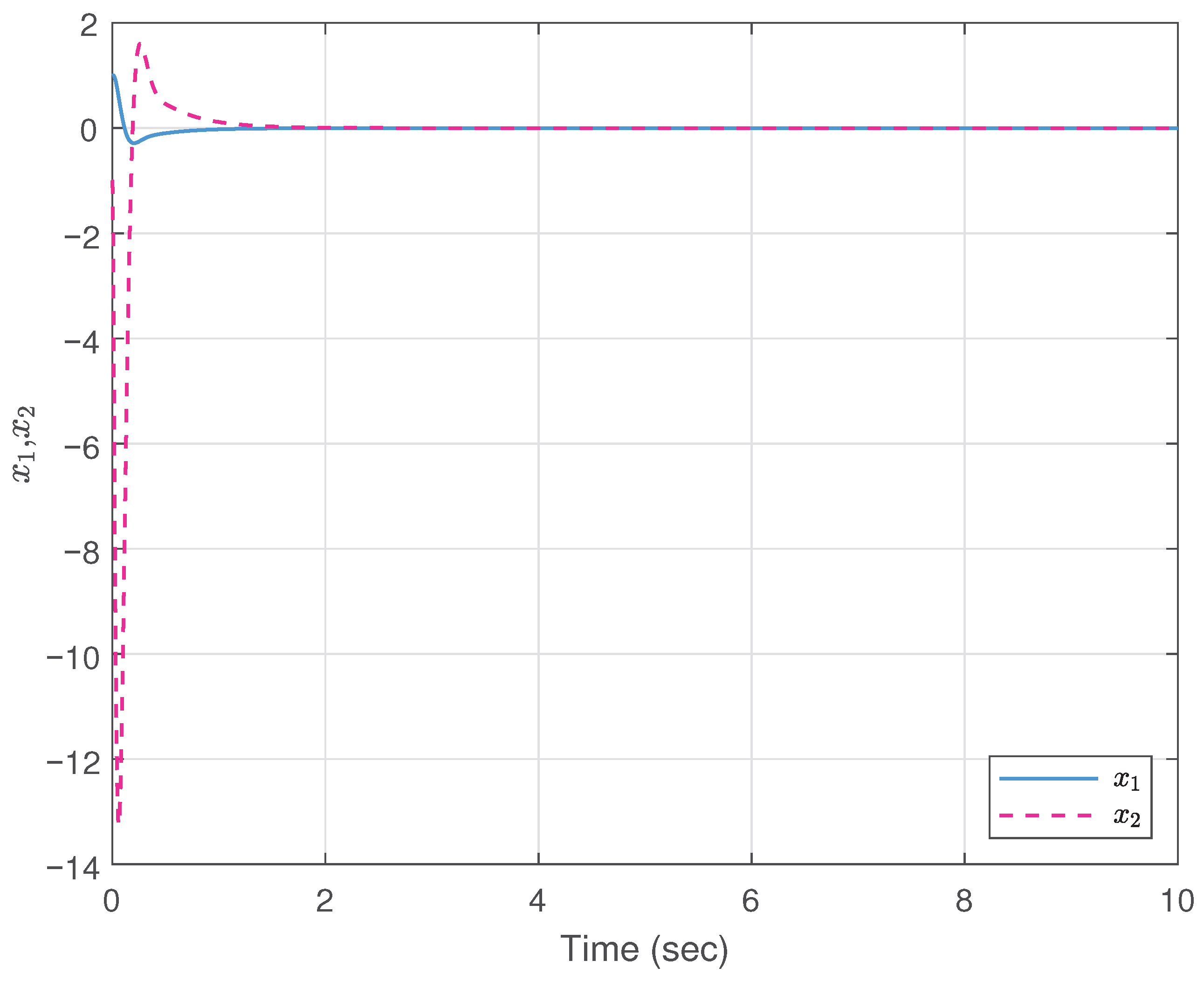
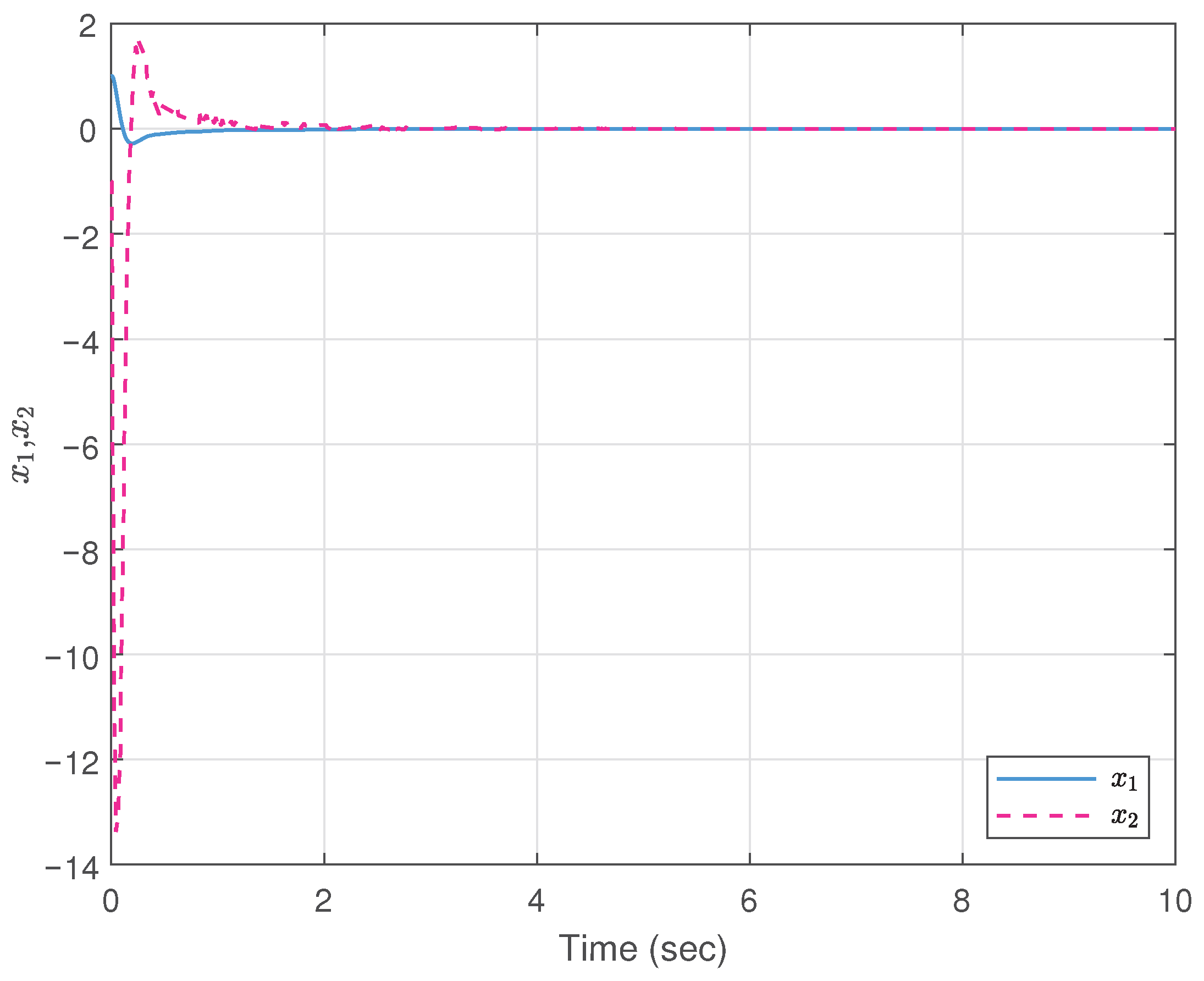
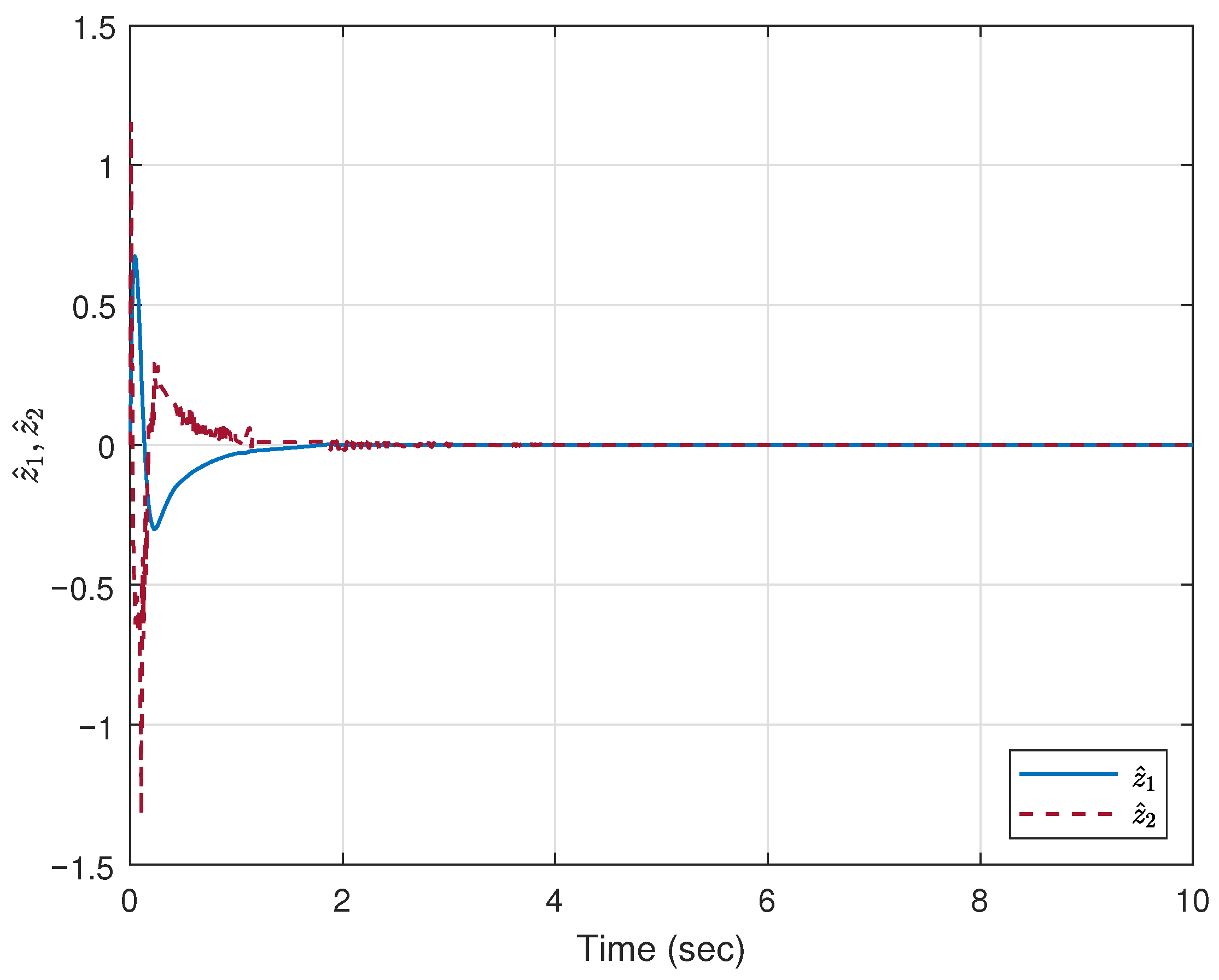
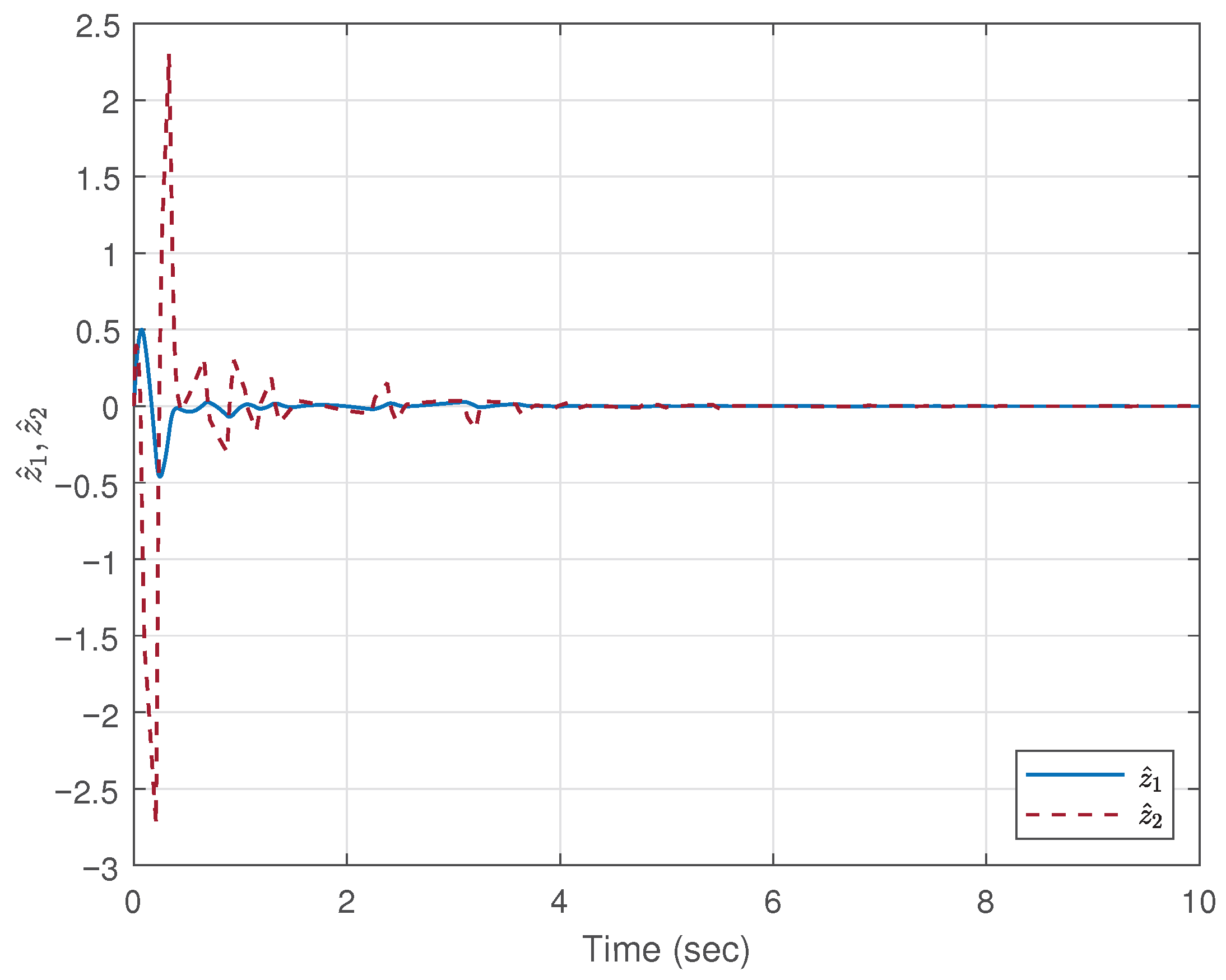
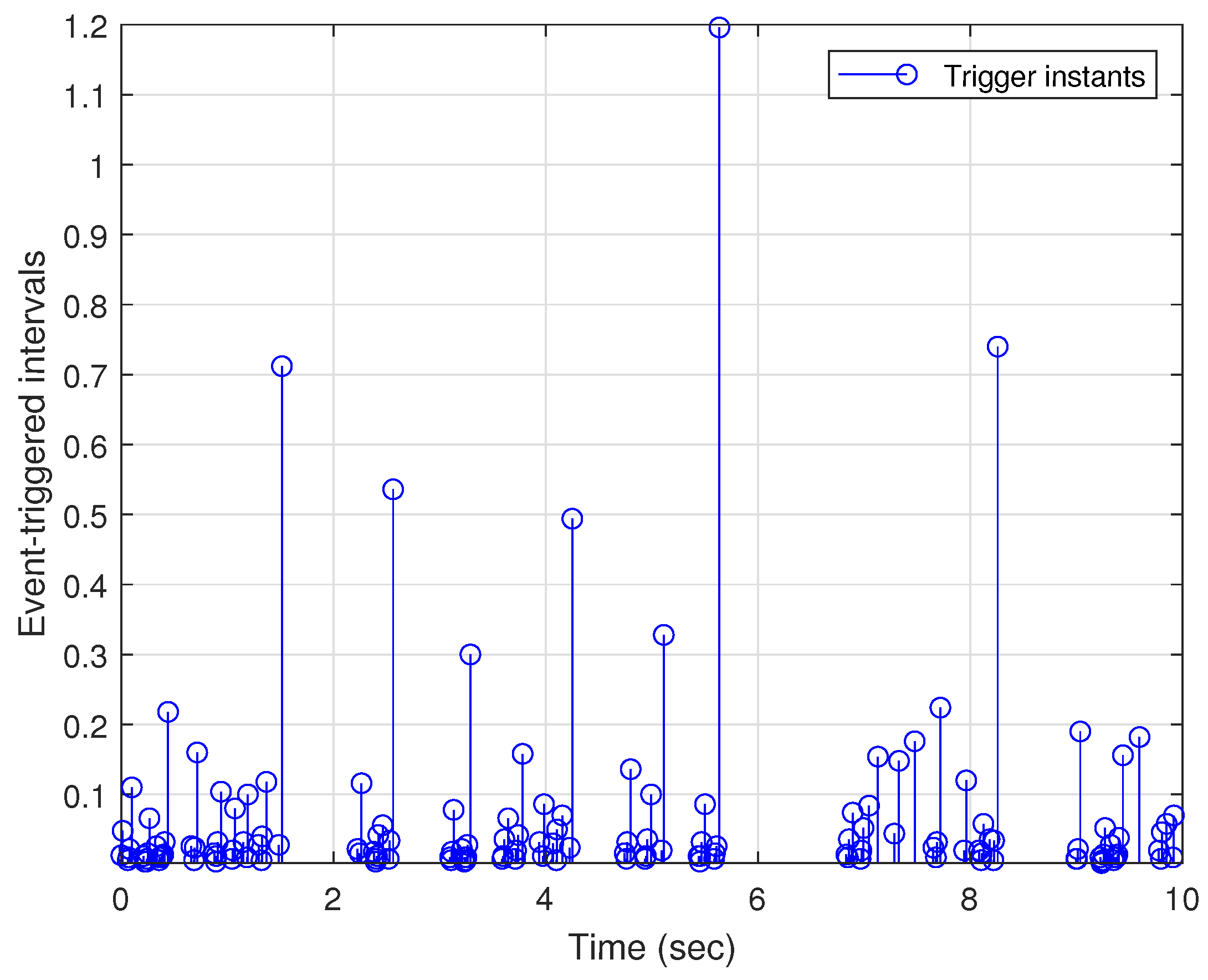
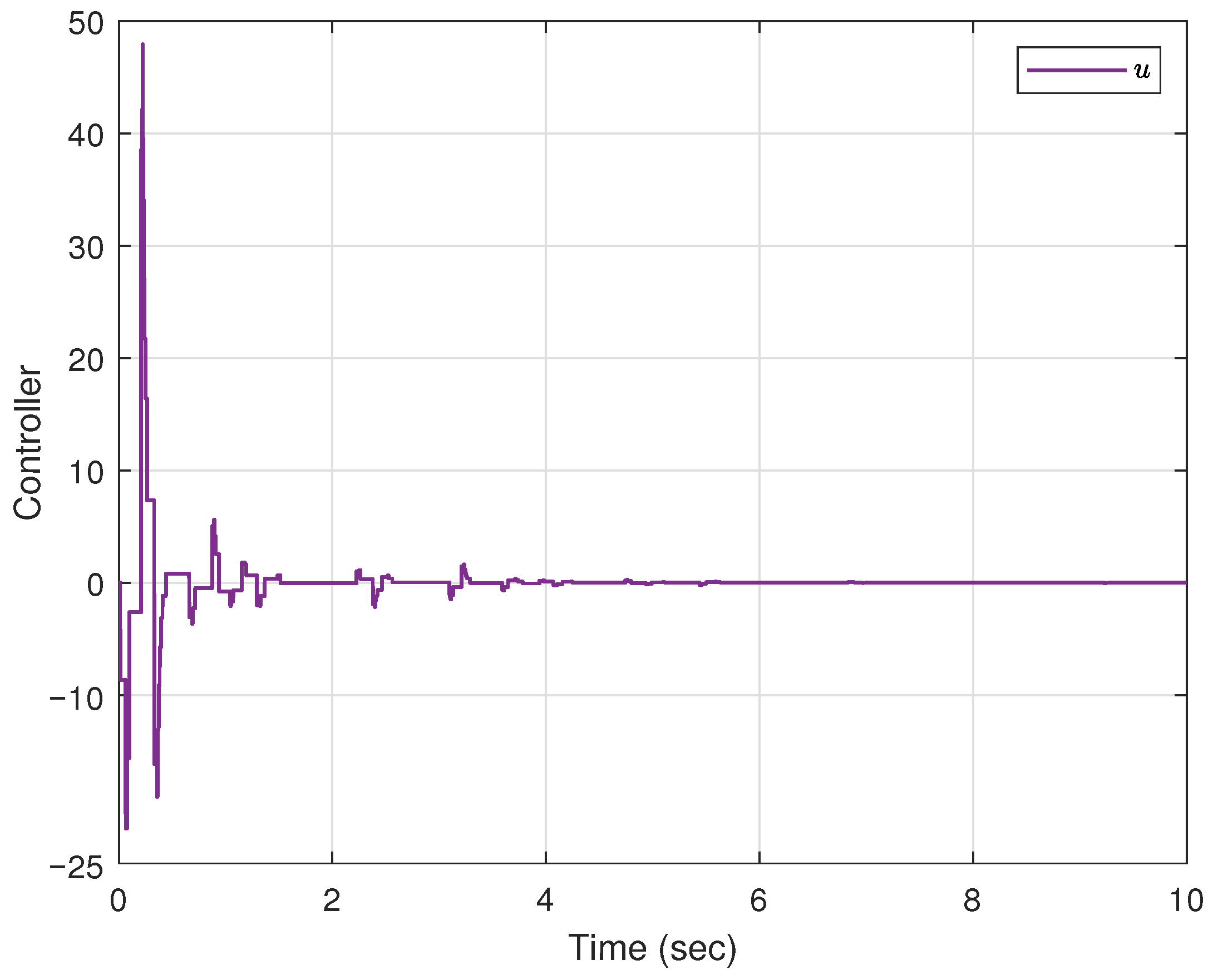
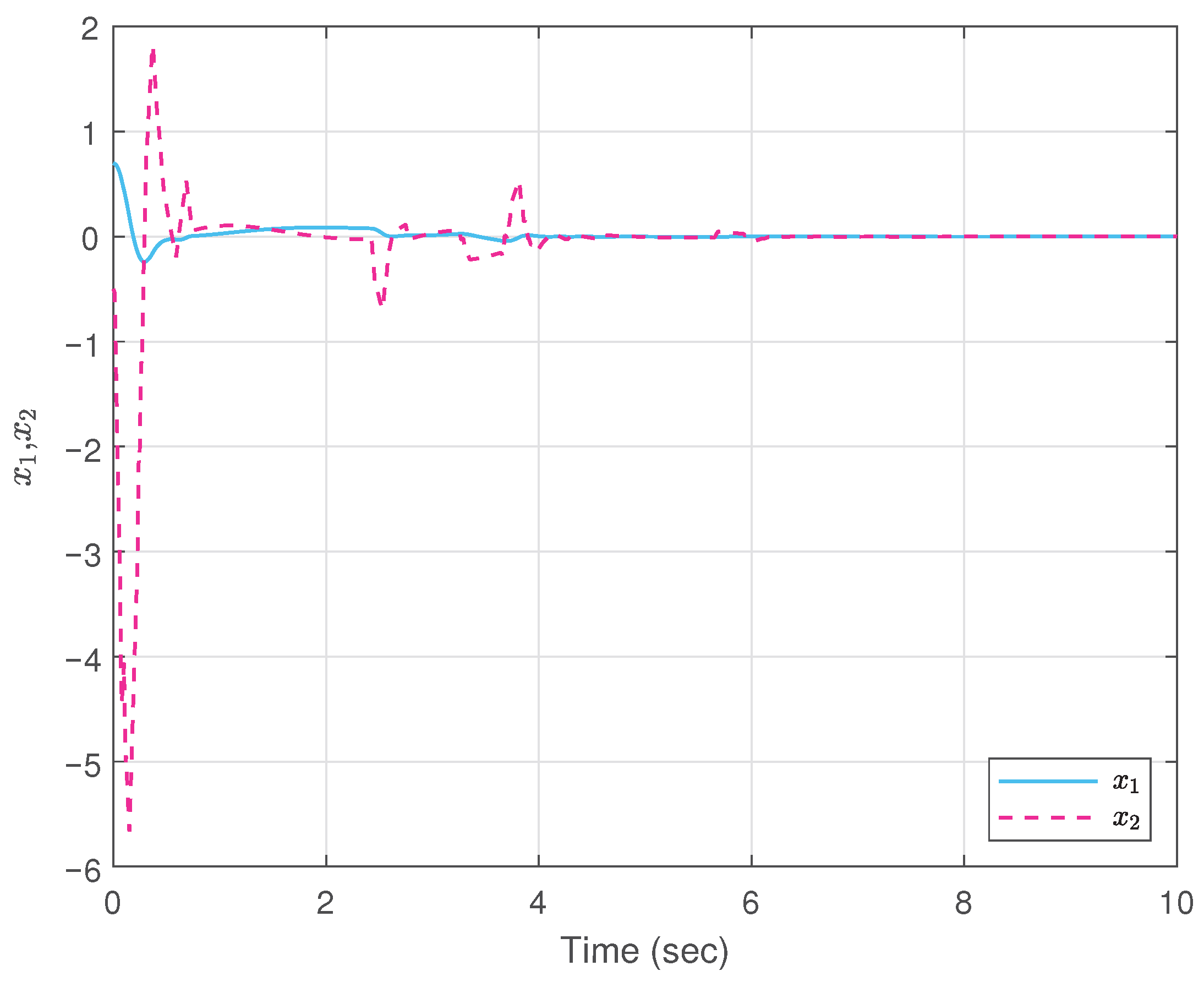
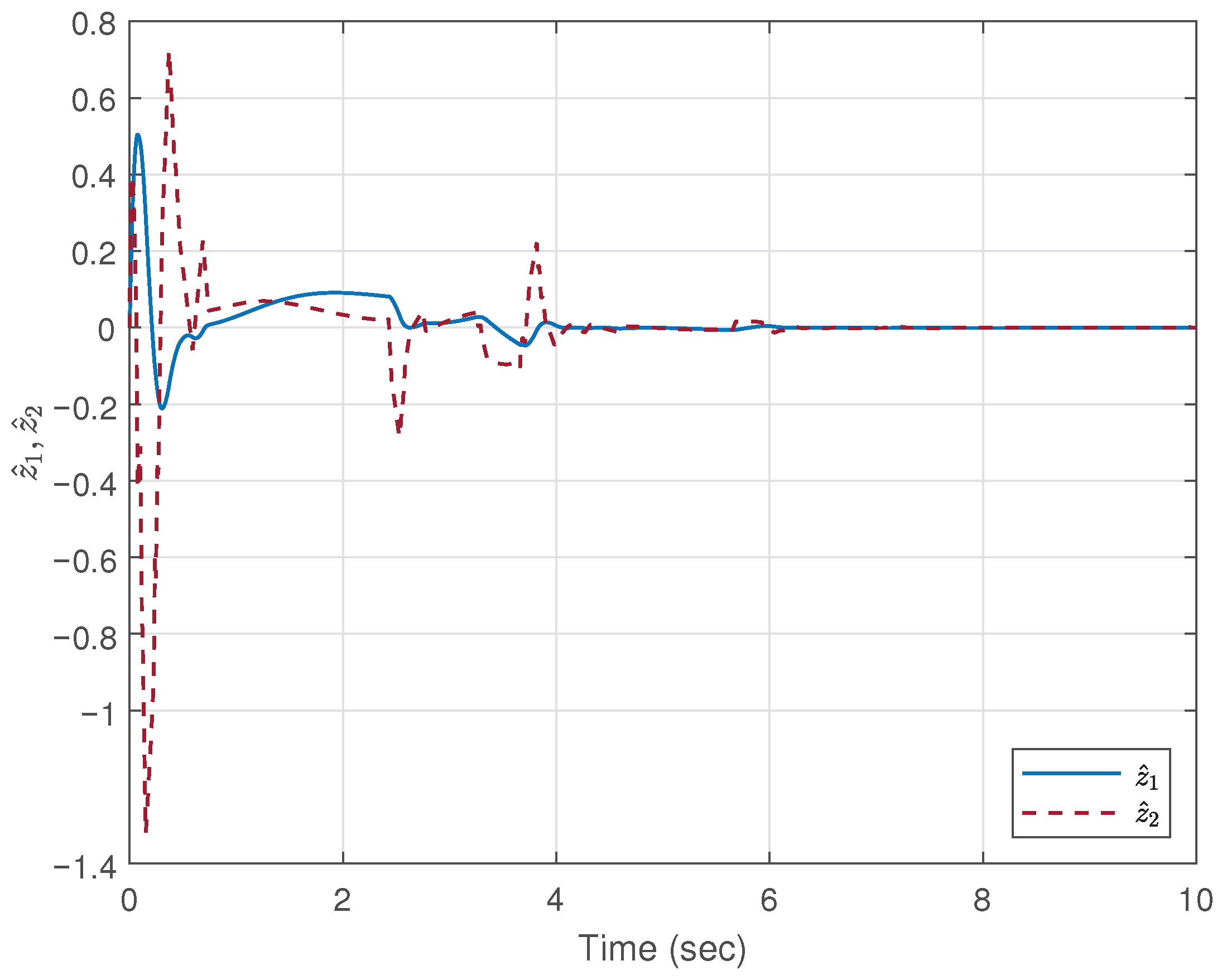
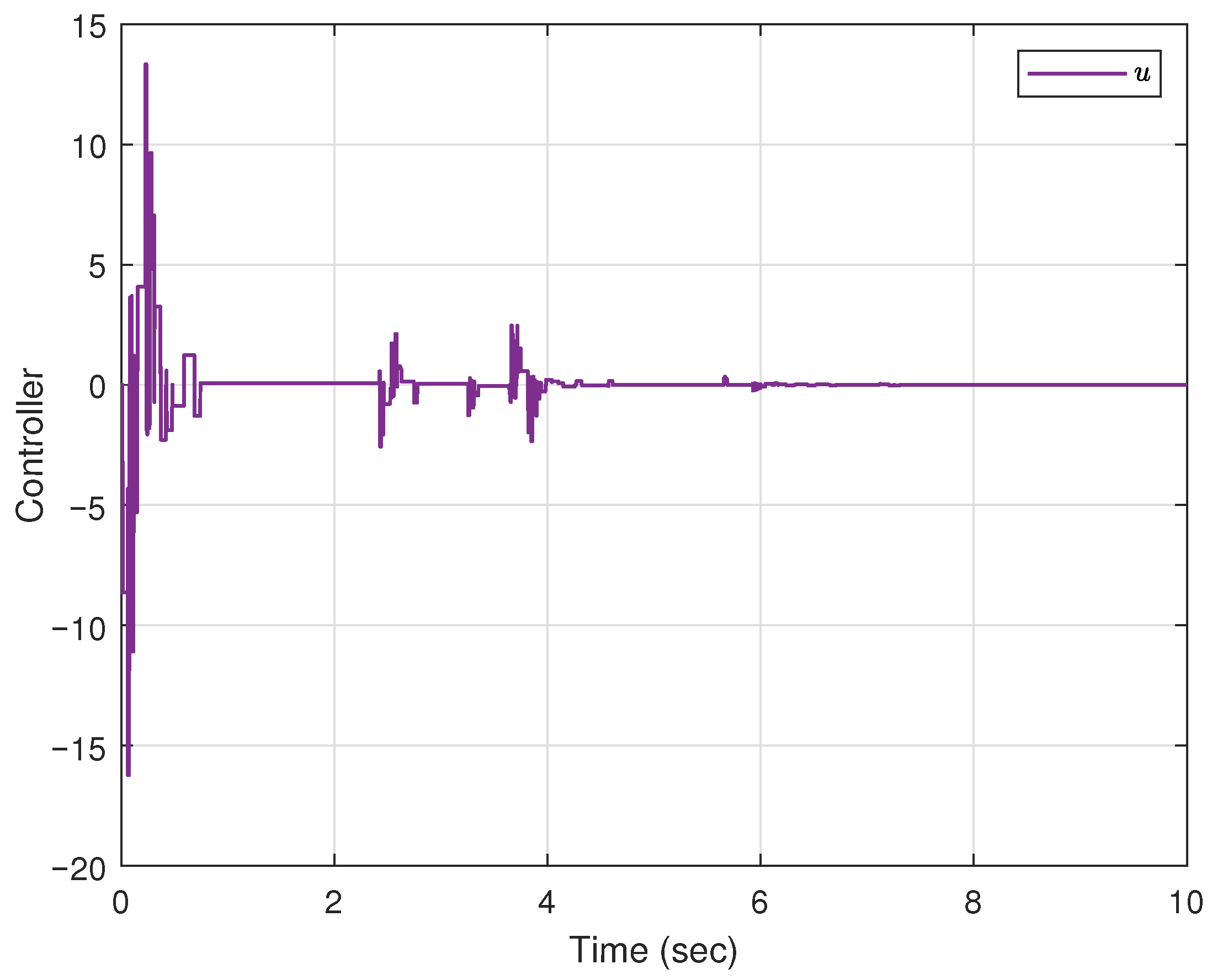
5. Simulation Example
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Song, J.; Wang, Y.; Niu, Y.; Lam, H.; He, S.; Liu, H. Periodic event triggered terminal sliding mode speed control for networked PMSM system: A GA-optimized extended state observer approach. IEEE/ASME Trans. Mechatron. 2022, 27, 4153–4164. [Google Scholar] [CrossRef]
- Fu, A.; McCann, J.A. Dynamic decentralized periodic event-triggered control for wireless cyber-physical systems. IEEE Trans. Control Syst. Technol. 2021, 29, 1783–1790. [Google Scholar] [CrossRef]
- Wang, L.; Hu, M.; Bian, Y.; Guo, G.; Li, S.; Chen, B.; Zhong, Z. Periodic event-triggered fault detection for safe platooning control of intelligent and connected vehicles. IEEE Trans. Veh. Technol. 2024, 73, 5064–5077. [Google Scholar] [CrossRef]
- Wang, F.-Y.; Gao, Y. On frequency sensitivity and mode orthogonality of flexible robotic manipulators. IEEE/CAA J. Autom. Sin. 2016, 3, 394–397. [Google Scholar] [CrossRef]
- Zhang, X.-M.; Han, Q.-L.; Yu, X. Survey on recent advances in networked control systems. IEEE Trans. Ind. Inform. 2016, 12, 1740–1752. [Google Scholar] [CrossRef]
- Ge, X.H.; Yang, F.W.; Han, Q.-L. Distributed networked control systems: A brief overview. Inf. Sci. 2017, 380, 117–131. [Google Scholar] [CrossRef]
- Lu, Q.; Han, Q.-L.; Zhang, B.T.; Liu, D.L.; Liu, S.R. Cooperative control of mobile sensor networks for environmental monitoring: An event-triggered finite-time control scheme. IEEE Trans. Cybern. 2017, 47, 4134–4147. [Google Scholar] [CrossRef]
- Yue, D.; Tian, E.; Han, Q.-L. A delay system method for designing event-triggered controllers of networked control systems. IEEE Trans. Autom. Control 2013, 58, 475–481. [Google Scholar] [CrossRef]
- Peng, C.; Han, Q.-L.; Yue, D. To transmit or not to transmit: A discrete event-triggered communication scheme for networked takagi-sugeno fuzzy systems. IEEE Trans. Fuzzy Syst. 2013, 21, 164–170. [Google Scholar] [CrossRef]
- Choi, Y.H.; Yoo, S.J. Decentralized event-triggered tracking of a class of uncertain interconnected nonlinear systems using minimal function approximators. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 1766–1788. [Google Scholar] [CrossRef]
- Wu, C.; Zhao, X.; Zhao, N.; Xu, N. Periodic and dynamic periodic event-triggered control for nonlinear cyber-physical systems under DoS attacks via a hybrid system approach. IEEE Trans. Control Netw. Syst. 2024, 11, 221–232. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, N.; Li, Y.; Xie, X.; Tian, E.; Cao, J. Learning-based event-triggered tracking control for nonlinear networked control systems with unmatched disturbance. IEEE Trans. Syst. Man Cybern. 2023, 53, 3230–3240. [Google Scholar] [CrossRef]
- Gu, Z.; Huang, X.; Sun, X.; Xie, X.; Park, J.H. Memory-event-triggered tracking control for intelligent vehicle transportation systems: A leader-following approach. IEEE Trans. Intell. Transp. Syst. 2024, 25, 4021–4031. [Google Scholar] [CrossRef]
- Yan, S.; Gu, Z.; Ahn, C.K. Memory-event-triggered H-infinity filtering of unmanned surface vehicles with communication delays. IEEE Trans. Circuits Syst. I Reg. Pap. 2021, 68, 2463–2467. [Google Scholar]
- Ding, F.; Zhu, K.; Liu, J.; Peng, C.; Wang, Y.; Lu, J. Adaptive memory event-triggered output feedback finite-time lane-keeping control for autonomous heavy truck with roll prevention. IEEE Trans. Fuzzy Syst. 2024, 32, 6607–6621. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, H. Adaptive-memory event-triggered load frequency control for multi-input-delay power systems against FDI attacks and sensor faults. IEEE Trans. Circuits Syst. II Exp. Briefs 2024, 71, 4919–4923. [Google Scholar] [CrossRef]
- Sun, J.; Yang, J.; Zheng, W.X.; Li, S. Periodic event-triggered control for a class of nonminimum-phase nonlinear systems using dynamic triggering mechanism. IEEE Trans. Circuits Syst. I Reg. Pap. 2022, 69, 1302–1311. [Google Scholar] [CrossRef]
- He, W.; Xu, B.; Han, Q.-L.; Qian, F. Adaptive consensus control of linear multiagent systems with dynamic event-triggered strategies. IEEE Trans. Cybern. 2020, 50, 2996–3008. [Google Scholar] [CrossRef]
- Ge, X.; Xiao, S.; Han, Q.-L.; Zhang, X.-M.; Ding, D. Dynamic event-triggered scheduling and platooning control co-design for automated vehicles over vehicular ad-hoc networks. IEEE/CAA J. Autom. Sin. 2022, 9, 31–46. [Google Scholar] [CrossRef]
- Girard, A. Dynamic triggering mechanisms for event-triggered control. IEEE Trans. Autom. Control 2015, 60, 1992–1997. [Google Scholar] [CrossRef]
- Chen, G.; Dong, J. Data-driven control for discrete-time nonlinear systems with dual-channel dynamic event-triggered mechanism. IEEE Trans. Circuits Syst. II Exp. Briefs 2023, 10, 4439–4443. [Google Scholar] [CrossRef]
- Zhao, Y.; Qin, X.; Niu, B. Dynamic memory event-triggered anti-disturbance control for switched cyber-physical systems and its application to switched RLC circuit. IEEE Trans. Circuits Syst. I Regul. Pap. 2024, 71, 6034–6043. [Google Scholar] [CrossRef]
- Ye, F.; Cheng, Z.; Cao, X.; Chow, M.-Y. A random-weight privacy-preserving algorithm with error compensation for microgrid distributed energy management. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4352–4362. [Google Scholar] [CrossRef]
- Yang, M.; Zhai, J. Predictor-based decentralized event-triggered secure control for nonlinear cyber-physical systems under replay attacks and time delay. IEEE Trans. Control Netw. Syst. 2024, 11, 150–160. [Google Scholar] [CrossRef]
- Ye, F.; Cao, X.; Cheng, Z.; Chow, M.-Y. CASL: A novel collusion attack against distributed energy management systems. IEEE Trans. Smart Grid 2023, 14, 4717–4728. [Google Scholar] [CrossRef]
- Gao, Y.; Niu, B.; Chen, W.; Wang, H.; Mu, C.; Wen, G. Adaptive control of constrained nonlinear CPSs under deception attacks through sensor and actuator networks. IEEE Trans. Circuits Syst. II Exp. Briefs 2024, 71, 1241–1245. [Google Scholar] [CrossRef]
- Peng, C.; Sun, H. Switching-like event-triggered control for networked control systems under malicious denial of service attacks. IEEE Trans. Autom. Control 2020, 65, 3943–3949. [Google Scholar] [CrossRef]
- Wan, Y.; Long, C.; Deng, R.; Wen, G.; Yu, X.; Huang, T. Distributed event-based control for thermostatically controlled loads under hybrid cyber attacks. IEEE Trans. Cybern. 2021, 52, 5314–5327. [Google Scholar] [CrossRef] [PubMed]
- Cheng, Z.; Hu, S.; Yue, D.; Dou, C.; Shen, S. Resilient distributed coordination control of multiarea power systems under hybrid attacks. IEEE Trans. Syst. Man Cybern. 2022, 52, 7–18. [Google Scholar] [CrossRef]
- Tang, Q.; Deng, C.; Fan, S.; Wang, Y.; Yue, D.; Wang, B. A novel cooperative resilient control method for energy storage systems under hybrid attacks. IEEE Trans. Ind. Electron. 2025, 72, 3943–3949. [Google Scholar] [CrossRef]
- Yang, J.; Sun, J.; Zheng, W.X.; Li, S. Periodic event-triggered robust output feedback control for nonlinear uncertain systems with time-varying disturbance. Automatica 2018, 94, 324–333. [Google Scholar] [CrossRef]
- Apostol, T.M. Mathematical Analysis, 2nd ed.; Addison-Wesley: Reading, MA, USA, 1974. [Google Scholar]
- Yang, M.; Zhai, J. Observer-based switching-like event-triggered control of nonlinear networked systems against dos attacks. IEEE Trans. Control Netw. Syst. 2022, 9, 1375–1384. [Google Scholar] [CrossRef]







| Method | Event-Triggered Packets | |
|---|---|---|
| Time-triggered mechanism | 5000 | 100% |
| Conventional ETM | 999 | 19.98% |
| DMETM (7) | 613 | 12.26% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, B.; Zhang, T.; Xi, Z.; Wang, Y.; Yang, M. Estimate-Based Dynamic Memory-Event-Triggered Control for Nonlinear Networked Control Systems Subject to Hybrid Attacks. Mathematics 2025, 13, 2829. https://doi.org/10.3390/math13172829
Zhang B, Zhang T, Xi Z, Wang Y, Yang M. Estimate-Based Dynamic Memory-Event-Triggered Control for Nonlinear Networked Control Systems Subject to Hybrid Attacks. Mathematics. 2025; 13(17):2829. https://doi.org/10.3390/math13172829
Chicago/Turabian StyleZhang, Bo, Tao Zhang, Zesheng Xi, Yunfan Wang, and Meng Yang. 2025. "Estimate-Based Dynamic Memory-Event-Triggered Control for Nonlinear Networked Control Systems Subject to Hybrid Attacks" Mathematics 13, no. 17: 2829. https://doi.org/10.3390/math13172829
APA StyleZhang, B., Zhang, T., Xi, Z., Wang, Y., & Yang, M. (2025). Estimate-Based Dynamic Memory-Event-Triggered Control for Nonlinear Networked Control Systems Subject to Hybrid Attacks. Mathematics, 13(17), 2829. https://doi.org/10.3390/math13172829






