Anonymous and Traceable: A Dynamic Group Signature-Based Cross-Domain Authentication for IIoT
Abstract
1. Introduction
- We propose a cross-domain authentication scheme based on group signatures, in which the group signature is constructed using zero-knowledge proofs and dynamic accumulators. This allows devices to authenticate anonymously while enabling the group manager to identify and revoke the access rights of malicious devices as needed.
- Our scheme enables efficient dynamic membership management. It achieves O(1) time complexity for device enrollment and revocation. A lazy witness update algorithm is introduced to reduce the frequency of witness updates and computational overhead. Furthermore, we have designed a non-membership proof mechanism based on blacklists to verify the legitimacy of devices using fixed-size group elements, which significantly reduces storage and communication costs.
- We perform a security analysis of the proposed scheme to demonstrate its security and privacy-preserving properties. The experimental results show that our scheme has lower computational overhead and stronger dynamic adaptability than other schemes.
1.1. Related Work
1.1.1. Cross-Domain Authentication Based on PKI/IBC
1.1.2. Blockchain-Based Cross-Domain Authentication
1.1.3. Group Signature-Based Cross-Domain Authentication
1.2. Paper Outline
2. Preliminaries
2.1. Bilinear Mappings
- Bilinearity: For all , , and , the following holds:
- Computability: For any and , can be efficiently computed.
- Non-degeneracy: There exist and such that .
2.2. Dynamic Accumulator
2.3. Non-Interactive Zero-Knowledge Proof (NIZK)
- Proof Generation: The prover first selects a random number and computes the commitment . Subsequently, a hash-based challenge is generated using a cryptographic hash function . The prover then calculates the response and generates the signature for transmission to the verifier.
- Verification: Upon receiving , the verifier extracts components R and s. The verification consists of two sequential checks: First, the hash equivalence must hold, ensuring the challenge consistency. Then, the algebraic relationship is verified to confirm the validity of the proof without requiring interaction.
2.4. Group Signatures
- : On input security parameter , generate a group public key and a group manager’s secret key .
- : Enable the group manager to enroll user i, issuing them a signing key and a certificate .
- : Produce a group signature on message m using member i’s key .
- :
- : Allow the group manager to reveal the identity i of the signer, if necessary.
3. Enhanced Dynamic Member Management
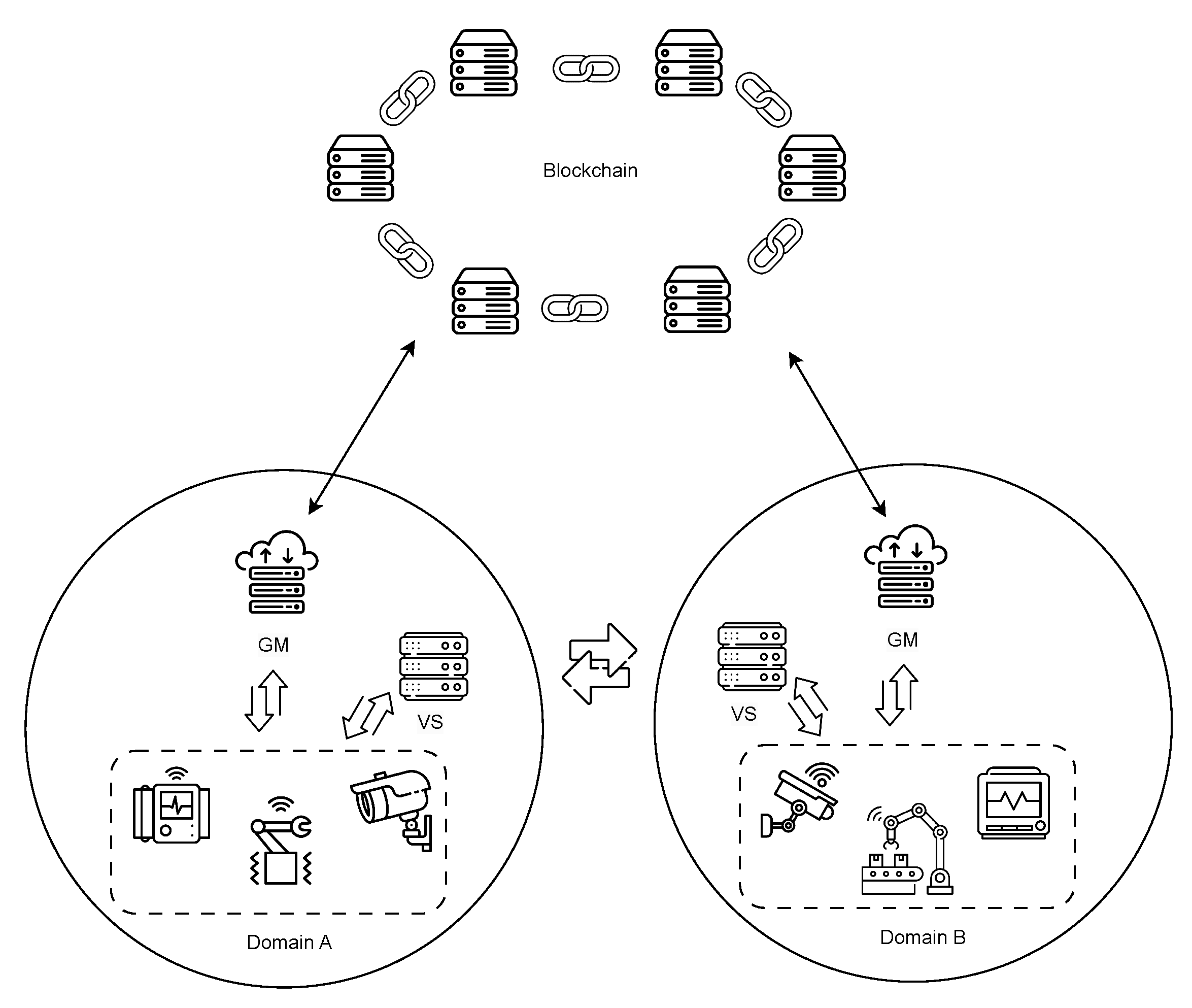
3.1. System Overview
- Devices: Devices play a key role in cross-domain authentication. Devices in different domains perform different tasks. However, most IIoT devices have limited resources, with memory capacities in the kilobyte range and clock frequencies in the megahertz range. These limitations make executing complex cryptographic algorithms infeasible. Each device has a unique and tamper-proof real identity (such as one embedded in a security chip when the device leaves the factory).
- Group Manager (GM): In each domain, group membership is maintained via a dynamic accumulator, and the GM is the sole trusted group administrator. The GM generates the system parameters required for cross-domain identity authentication and issues certificates and membership witnesses to devices when they join the group. Moreover, the GM tracks identities and revokes the access privileges of malicious devices.
- Verification Server (VS): The cross-domain authentication process requires multiple bilinear mappings for verification, but these mappings are computationally expensive and difficult for IIoT devices with limited resources to complete. The VS was introduced to enable devices to efficiently perform authentication and production operations. For multi-user concurrent authentication, VS can use GPU-accelerated bilinear interpolation calculations and asynchronous pipeline processing. It can also cache some fixed parameters to reduce calculations.
3.2. Initialization
3.3. Design Details
| Algorithm 1 JoinGroup Algorithm |
| Input: |
| : Domain A’s device list |
| : Device requesting to join |
| : Public parameters |
| : Non-membership proof from |
| Output: |
| : Group certificate, witness, and sequence number |
| 1: Check |
| 2: if verification passes then |
| 3: Compute |
| 4: Compute |
| 5: Compute group certificate |
| 6: Update accumulator |
| 7: Compute membership witness |
| 8: Set element |
| 9: Add record to : |
| 10: return |
| 11: else |
| 12: return Join request rejected |
| 13: end if |
- uses the value of to quickly locate the corresponding in .
- If , the records in represent the accumulator updates already processed by the device, while are newly added records not yet incorporated into the witness. Partition into two sublists: (entries with flag = 0) and (entries with flag = 1). The computes the update factor as
- Then, updates the value of device to , sets , and returns to . Later updates for will directly start from the n-th record in , ensuring efficient and lazy updates. For revoked devices, if identifies that the witness value , the update request is denied.
4. Complete Cross-Domain Authentication Scheme
4.1. Cross-Domain Authentication
4.2. Tracking and Revoking Malicious Devices
- computes using its private key x and the values from the signature . Then, queries with to retrieve the real identity of the malicious device .
- After obtaining the tracing information, sets in the and inserts the following record into to revoke ’s group membership:
- Then, updates the latest accumulator value as and synchronizes the new to the blockchain.
- Additionally, it as
5. Security Analysis
5.1. Threat Model
5.2. Security Objectives
- Anonymity: The proposed cross-domain scheme should ensure the confidentiality of IIoT devices’ identity information, thereby protecting their identity privacy and ensuring anonymity throughout the authentication process.
- Traceability: The scheme should prevent adversaries from generating untraceable signatures. In other words, all legitimate signatures must be traceable back to their respective signers.
- Unlinkability: The cross-domain authentication scheme should ensure that attackers cannot determine whether two messages originate from the same entity.
- Replay Resistance: The cross-domain authentication scheme should prevent attackers from reusing validated legitimate signatures to forge identities or compromise security.
5.3. Security Assumption
5.4. Security Properties and Proofs
- And continue to calculateTherefore, Equation (3) holds.
- Verification of the equationThe right . According to , we can prove
- We calculate and Thus, Equation (6) holds.
- Based on the values of , the following can be calculated:So, Equation (7) holds.
- Initialization:
- generates system parameters and publishes them.
- receives a q-SDH challenge tuple , where x is unknown.
- Query Phase: adaptively interacts with via the following oracles:
- Device Enrollment: For any device , random selection generates a certificate and updates the accumulator .
- Signature Generation: For any message m and device , generates valid signatures using and .
- Forgery Phase:
- and
6. Experimental Evaluation
6.1. Experimental Setup
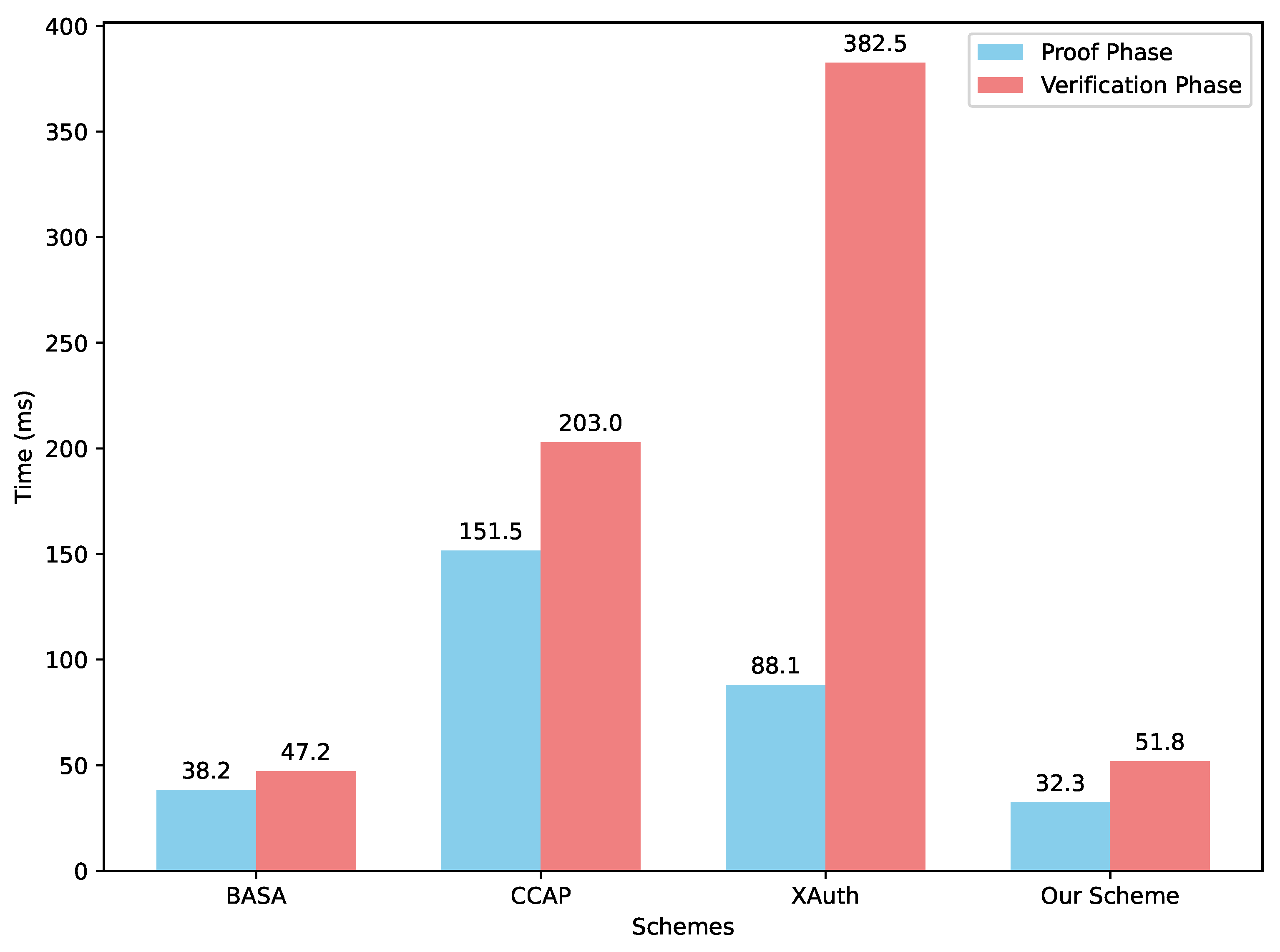
6.2. Computation Cost
6.3. Communication Cost
6.4. Revocation Cost
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Vitturi, S.; Zunino, C.; Sauter, T. Industrial Communication Systems and Their Future Challenges: Next-Generation Ethernet, IIoT, and 5G. Proc. IEEE 2019, 107, 944–961. [Google Scholar] [CrossRef]
- Xu, H.; Yu, W.; Griffith, D.; Golmie, N. A Survey on Industrial Internet of Things: A Cyber-Physical Systems Perspective. IEEE Access 2018, 6, 78238–78259. [Google Scholar] [CrossRef] [PubMed]
- Tong, F.; Chen, X.; Wang, K.; Zhang, Y. CCAP: A Complete Cross-Domain Authentication Based on Blockchain for Internet of Things. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3789–3800. [Google Scholar] [CrossRef]
- Zhang, Q.; Fu, Y.; Cui, J.; He, D.; Zhong, H. Efficient Fine-Grained Data Sharing Based on Proxy Re-Encryption in IIoT. IEEE Trans. Dependable Secure Comput. 2024, 21, 5797–5809. [Google Scholar] [CrossRef]
- Chung, K.C.; Tan, P.J.B. IoT-Powered Personalization: Creating the Optimal Shopping Experience in Digital Twin VFRs. Internet Things 2024, 26, 101216. [Google Scholar] [CrossRef]
- Ju, S.; Park, H.; Son, S.; Kim, H.; Park, Y.; Park, Y. Blockchain-Assisted Secure and Lightweight Authentication Scheme for Multi-Server Internet of Drones Environments. Mathematics 2024, 12, 3965. [Google Scholar] [CrossRef]
- Kim, C.; Kwon, D.; Son, S.; Yu, S.; Park, Y. An Anonymous and Efficient Authentication Scheme with Conditional Privacy Preservation in Internet of Vehicles Networks. Mathematics 2024, 12, 3756. [Google Scholar] [CrossRef]
- Cui, J.; Liu, N.; Zhang, Q.; He, D.; Gu, C.; Zhong, H. Efficient and Anonymous Cross-Domain Authentication for IIoT Based on Blockchain. IEEE Trans. Netw. Sci. Eng. 2022, 10, 899–910. [Google Scholar] [CrossRef]
- Hao, S.-G.; Zhang, L.; Muhammad, G. A Union Authentication Protocol of Cross-Domain Based on Bilinear Pairing. J. Softw. 2013, 8, 1094–1100. [Google Scholar] [CrossRef]
- Zhong, H.; Gu, C.; Zhang, Q.; Cui, J.; Gu, C.; He, D. Conditional Privacy-Preserving Message Authentication Scheme for Cross-Domain Industrial Internet of Things. Ad Hoc Netw. 2023, 144, 103137. [Google Scholar] [CrossRef]
- Hwang, J.-B.; Kim, D.-W.; Lee, Y.-K.; Han, J.-W. Two Layered PKI Model for Device Authentication in Multi-Domain Home Networks. In Proceedings of the 2006 IEEE International Symposium on Consumer Electronics, St. Petersburg, Russia, 28 June–1 July 2006; pp. 1–6. [Google Scholar]
- Liu, C.; Feng, Y.; Fan, M.; Wang, G. PKI Mesh Trust Model Based on Trusted Computing. In Proceedings of the 2008 the 9th International Conference for Young Computer Scientists, Zhangjiajie, China, 18–21 November 2008; pp. 1401–1405. [Google Scholar]
- Millán, G.L.; Pérez, M.G.; Pérez, G.M.; Skarmeta, A.F.G. PKI-Based Trust Management in Inter-Domain Scenarios. Comput. Secur. 2010, 29, 278–290. [Google Scholar] [CrossRef]
- Wang, W.; Hu, N.; Liu, X. BlockCAM: A Blockchain-Based Cross-Domain Authentication Model. In Proceedings of the 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC), Guangzhou, China, 18–21 June 2018; pp. 896–901. [Google Scholar]
- Yuan, C.; Zhang, W.; Wang, X. EIMAKP: Heterogeneous Cross-Domain Authenticated Key Agreement Protocols in the EIM System. Arab. J. Sci. Eng. 2017, 42, 3275–3287. [Google Scholar] [CrossRef]
- Chen, J.; Zhan, Z.; He, K.; Du, R.; Wang, D.; Liu, F. XAuth: Efficient Privacy-Preserving Cross-Domain Authentication. IEEE Trans. Dependable Secure Comput. 2021, 19, 3301–3311. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Zou, Q.; Ruan, Z.; Song, H. Blockchain-Based Message Authentication Scheme for Internet of Vehicles in an Edge Computing Environment. Comput. Syst. Sci. Eng. 2024, 48, 1301–1328. [Google Scholar] [CrossRef]
- Yao, Y.; Chang, X.; Mišić, J.; Mišić, V.B.; Li, L. BLA: Blockchain-Assisted Lightweight Anonymous Authentication for Distributed Vehicular Fog Services. IEEE Internet Things J. 2019, 6, 3775–3784. [Google Scholar] [CrossRef]
- Li, C.; Wu, Q.; Li, H.; Liu, J. TrustRoam: A Novel Blockchain-Based Cross-Domain Authentication Scheme for Wi-Fi Access. In Wireless Algorithms, Systems, and Applications; Springer: Berlin/Heidelberg, Germany, 2019; pp. 149–161. [Google Scholar]
- Chen, R.; Shu, F.; Huang, S.; Huang, L.; Liu, H.; Liu, J.; Lei, K. BIdM: A Blockchain-Enabled Cross-Domain Identity Management System. J. Commun. Inf. Netw. 2021, 6, 44–58. [Google Scholar] [CrossRef]
- Hwang, J.Y.; Chen, L.; Cho, H.S.; Nyang, D. Short Dynamic Group Signature Scheme Supporting Controllable Linkability. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1109–1124. [Google Scholar] [CrossRef]
- Sudarsono, A.; Nakanishi, T.; Nogami, Y.; Funabiki, N. Anonymous IEEE802.1X Authentication System Using Group Signatures. Inf. Media Technol. 2010, 5, 751–764. [Google Scholar] [CrossRef]
- Sudarsono, A.; Al Rasyid, M.U.H.; Yuliana, M. An Implementation of Anonymous Authentication System in Wireless Sensor Network Using VLR Group Signature. In Proceedings of the 2016 International Electronics Symposium (IES), Denpasar, Indonesia, 29–30 September 2016; pp. 277–282. [Google Scholar]
- Lu, J.; Shen, J.; Vijayakumar, P.; Gupta, B.B. Blockchain-Based Secure Data Storage Protocol for Sensors in the Industrial Internet of Things. IEEE Trans. Ind. Inform. 2021, 18, 5422–5431. [Google Scholar] [CrossRef]
- Esposito, C.; Castiglione, A.; Palmieri, F.; De Santis, A. Integrity for an Event Notification within the Industrial Internet of Things by Using Group Signatures. IEEE Trans. Ind. Inform. 2018, 14, 3669–3678. [Google Scholar] [CrossRef]
- Yuan, W.; Li, X.; Li, M.; Zheng, L. DCAGS-IoT: Dynamic Cross-Domain Authentication Scheme Using Group Signature in IoT. Appl. Sci. 2023, 13, 5847. [Google Scholar] [CrossRef]
- Galbraith, S.D.; Paterson, K.G.; Smart, N.P. Pairings for Cryptographers. Discrete Appl. Math. 2008, 156, 3113–3121. [Google Scholar] [CrossRef]
- Benaloh, J.; De Mare, M. One-Way Accumulators: A Decentralized Alternative to Digital Signatures. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1993; pp. 274–285. [Google Scholar]
- Nguyen, L. Accumulators from Bilinear Pairings and Applications. In Topics in Cryptology—CT-RSA 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 275–292. [Google Scholar]
- Camenisch, J.; Lysyanskaya, A. Dynamic accumulators and application to efficient revocation of anonymous credentials. In Advances in Cryptology—CRYPTO 2002: 22nd Annual International Cryptology Conference, Santa Barbara, California, USA, August 18–22, 2002, Proceedings; Springer: Berlin/Heidelberg, Germany, 2002; pp. 61–76. [Google Scholar]
- Bellés-Muñoz, M.; Whitehat, B.; Baylina, J.; Daza, V.; Muñoz-Tapia, J.L. Twisted Edwards Elliptic Curves for Zero-Knowledge Circuits. Mathematics 2021, 9, 3022. [Google Scholar] [CrossRef]
- Fiat, A.; Shamir, A. How to Prove Yourself: Practical Solutions to Identification and Signature Problems. In Conference on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1986; pp. 186–194. [Google Scholar]
- Chaum, D.; Van Heyst, E. Group Signatures. In Advances in Cryptology—EUROCRYPT’91; Springer: Berlin/Heidelberg, Germany, 1991; pp. 257–265. [Google Scholar]
- Damgård, I.; Triandopoulos, N. Supporting Non-Membership Proofs with Bilinear-Map Accumulators. Cryptol. ePrint Arch. 2008. Available online: https://eprint.iacr.org/2008/538 (accessed on 23 June 2025).
- Abd El-Latif, A.A.; Iliyasu, A.M.; Abd-El-Atty, B. An Efficient Visually Meaningful Quantum Walks-Based Encryption Scheme for Secure Data Transmission on IoT and Smart Applications. Mathematics 2021, 9, 3131. [Google Scholar] [CrossRef]
- Wang, X.; Zhu, C.; Liu, Z. A Universally Composable Linkable Ring Signature Supporting Stealth Addresses. Mathematics 2024, 12, 491. [Google Scholar] [CrossRef]




| Notation | Description |
|---|---|
| Security parameter | |
| p | Large prime number |
| Additive cyclic group | |
| Multiplicative cyclic group | |
| Generator of group | |
| Generator of group | |
| H | Secure hash function |
| Group member certificate | |
| Accumulator member witness | |
| Blacklist non-membership witness | |
| Public key of the group manager | |
| x | Private key of the group manager |
| Properties | BASA [17] | XAuth [16] | CCAP [3] | Our Scheme |
|---|---|---|---|---|
| Dynamic Capability | × | × | × | ✓ |
| Anonymous Authentication | ✓ | ✓ | ✓ | ✓ |
| Identity Traceability | ✓ | × | ✓ | ✓ |
| Unlinkability | ✓ | ✓ | ✓ | ✓ |
| Collision Resistance | × | × | ✓ | ✓ |
| Replay Resistance | × | ✓ | ✓ | ✓ |
| Notation | Definition |
|---|---|
| Bilinear mapping cost: | |
| Hash function cost | |
| Group scalar multiplication cost: | |
| Group modular exponentiation cost: | |
| Large-integer multiplication cost: |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Deng, C.; Zhang, C.; Tan, Q. Anonymous and Traceable: A Dynamic Group Signature-Based Cross-Domain Authentication for IIoT. Mathematics 2025, 13, 2127. https://doi.org/10.3390/math13132127
Deng C, Zhang C, Tan Q. Anonymous and Traceable: A Dynamic Group Signature-Based Cross-Domain Authentication for IIoT. Mathematics. 2025; 13(13):2127. https://doi.org/10.3390/math13132127
Chicago/Turabian StyleDeng, Cunle, Chushan Zhang, and Qiaodan Tan. 2025. "Anonymous and Traceable: A Dynamic Group Signature-Based Cross-Domain Authentication for IIoT" Mathematics 13, no. 13: 2127. https://doi.org/10.3390/math13132127
APA StyleDeng, C., Zhang, C., & Tan, Q. (2025). Anonymous and Traceable: A Dynamic Group Signature-Based Cross-Domain Authentication for IIoT. Mathematics, 13(13), 2127. https://doi.org/10.3390/math13132127






